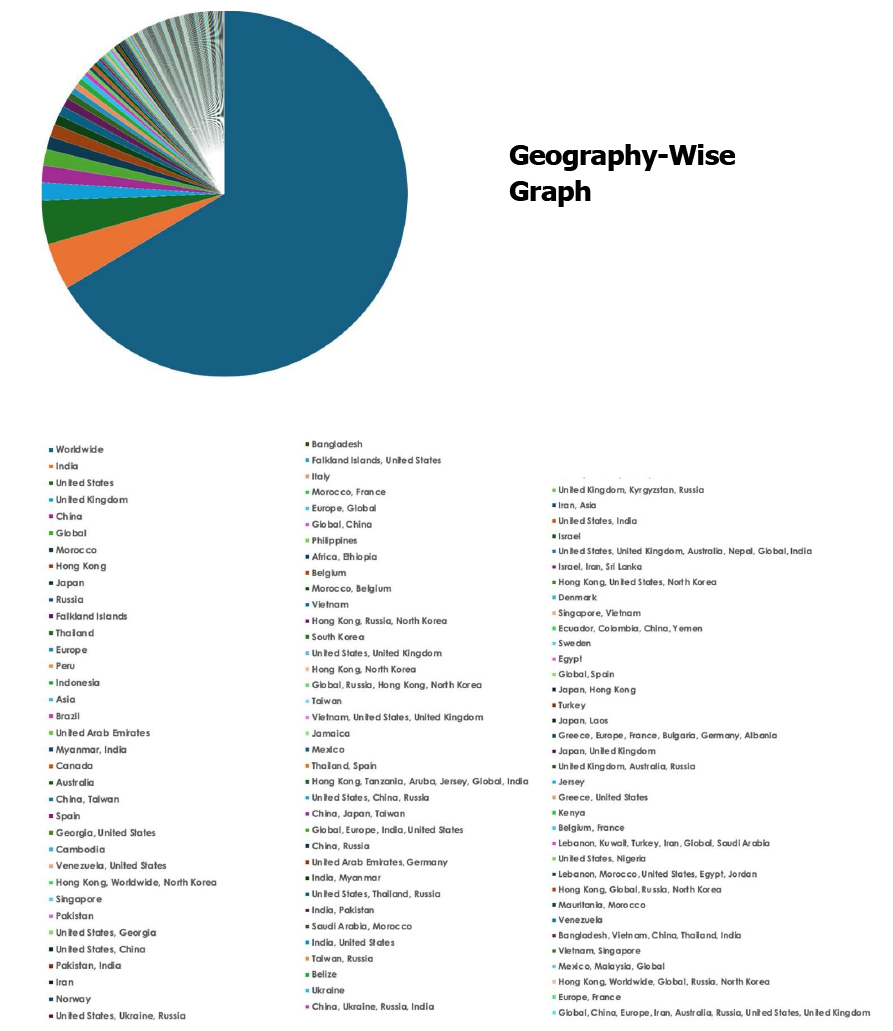
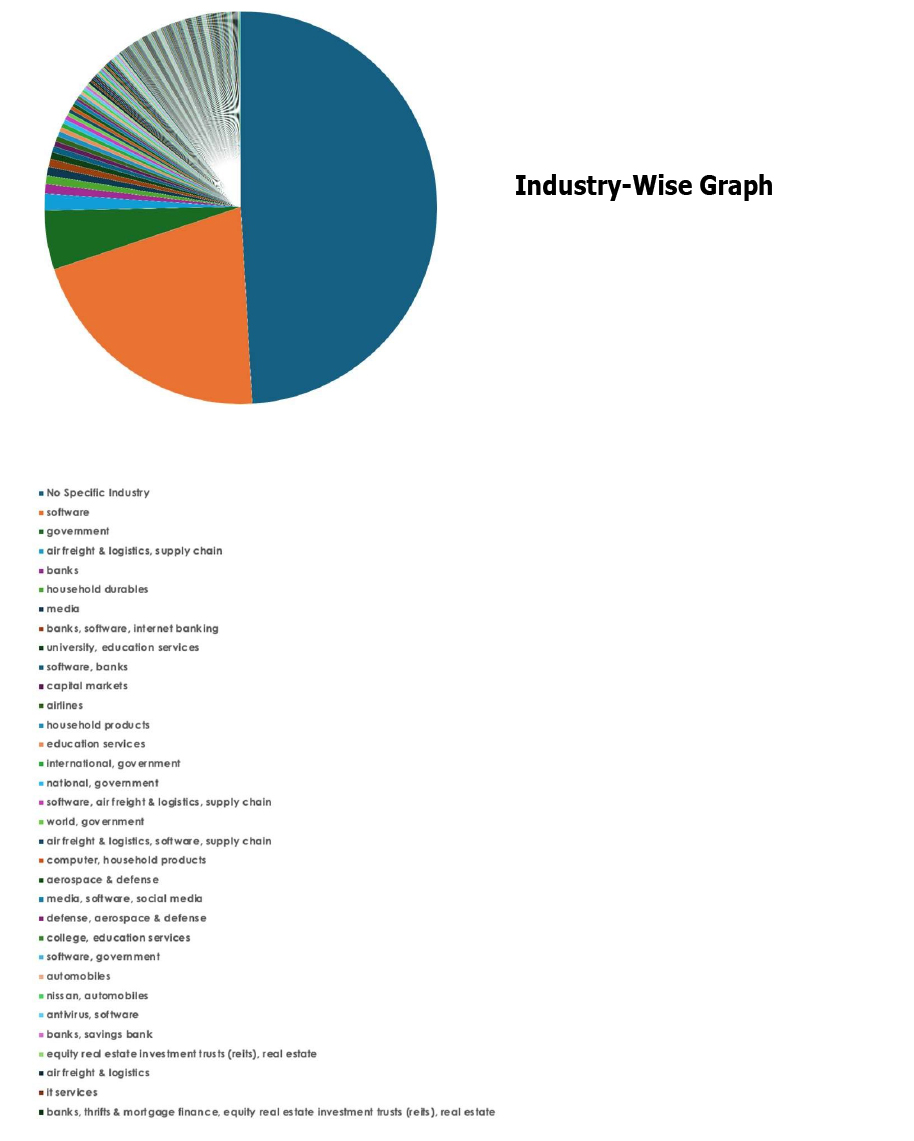
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Happy Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Happy Ransomware
CYFIRMA Research identified Happy (MedusaLocker) as a ransomware variant belonging to the MedusaLocker family. Upon execution on a compromised system, the malware performs file encryption using a combination of RSA and AES cryptographic algorithms, rendering targeted data inaccessible. Encrypted files are appended with a variant- specific extension such as “.happy11.” Following encryption, the ransomware alters the desktop wallpaper and deploys an HTML ransom note named “READ_NOTE.html.” The malware’s activity is limited to encryption and system modification related to extortion; removal of the ransomware prevents further encryption but does not restore already encrypted files.

Screenshot: File encrypted by ransomware (Source: Surface Web)
The ransom note informs victims that their company network has been penetrated and that files have been encrypted, warning against renaming or modifying encrypted files or using third-party recovery tools. It claims that sensitive and confidential data has been exfiltrated and threatens public release or resale of this data if payment demands are not met. The note provides contact email addresses and instructs victims to communicate via a newly created ProtonMail account. It also offers free decryption of up to three non-critical files as proof of capability and states that failure to initiate contact within 72 hours will result in an increased ransom amount.
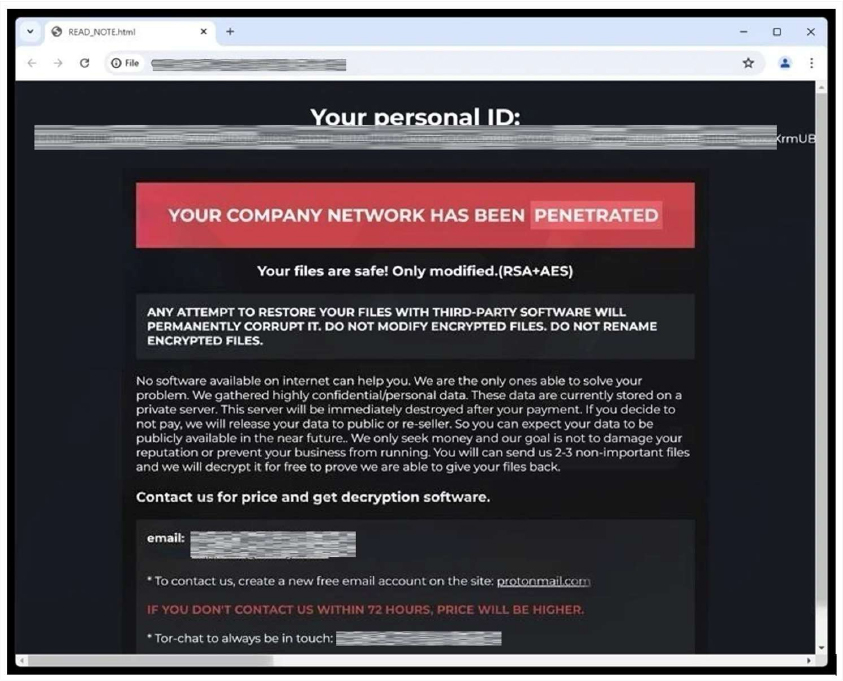
The appearance of the Happy ransom note (READ_NOTE.html) (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
Relevancy and Insights
ETLM Assessment
CYFIRMA’s assessment indicates that Happy operates as a structured enterprise- focused ransomware, designed to disrupt network operations by systematically encrypting business-critical data and enforcing coercive pressure on victims. Its functionality reflects a mature ransomware framework that combines strong cryptography with post-compromise actions such as visual system modification and explicit operational warnings to deter remediation attempts. The behavior of malware suggests controlled execution, likely following prior network access, with a focus on maximizing impact across organizational environments rather than indiscriminate infection.
Hypothetically, this ransomware could evolve to incorporate more adaptive capabilities, such as automated lateral movement, enhanced privilege escalation, and deeper integration with data exfiltration frameworks to strengthen double- extortion tactics. Future iterations may also adopt more evasive techniques, including improved obfuscation, disabling security tools, and selective targeting based on asset value. Additionally, the ransomware could expand its communication mechanisms beyond email to include more resilient, anonymized channels and implement modular updates that allow operators to customize payload behavior per victim environment, thereby increasing operational efficiency and pressure during extortion campaigns.
Sigma rule:
title: New RUN Key Pointing to Suspicious Folder tags:
– attack.privilege-escalation
– attack.persistence
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: selection_target:
TargetObject|contains:
– ‘\Software\Microsoft\Windows\CurrentVersion\Run’
– ‘\Software\WOW6432Node\Microsoft\Windows\CurrentVersion\Run’
– ‘\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run’ selection_suspicious_paths_1:
Details|contains:
– ‘:\Perflogs’
– :\ProgramData’
– ‘:\Windows\Temp’
– ‘:\Temp’
– ‘\AppData\Local\Temp’
– ‘\AppData\Roaming’
– ‘:\$Recycle.bin’
– ‘:\Users\Default’
– ‘:\Users\public’
– ‘%temp%’
– ‘%tmp%’
– ‘%Public%’
– ‘%AppData%’ selection_suspicious_paths_user_1:
Details|contains: ‘:\Users\’ selection_suspicious_paths_user_2:
Details|contains:
– ‘\Favorites’
– ‘\Favourites’
– ‘\Contacts’
– ‘\Music’
– ‘\Pictures’
– ‘\Documents’
– ‘\Photos’ filter_main_windows_update:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\’ Image|startswith: ‘C:\Windows\SoftwareDistribution\Download\’ Details|contains|all:
– ‘rundll32.exe ‘
– ‘C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32’ Details|contains:
– ‘\AppData\Local\Temp\’
– ‘C:\Windows\Temp\’ filter_optional_spotify:
Image|endswith:
– ‘C:\Program Files\Spotify\Spotify.exe’
– ‘C:\Program Files (x86)\Spotify\Spotify.exe’
– ‘\AppData\Roaming\Spotify\Spotify.exe’ TargetObject|endswith:
‘SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Spotify’ Details|endswith: ‘Spotify.exe –autostart –minimized’
condition: selection_target and (selection_suspicious_paths_1 or (all of selection_suspicious_paths_user_* )) and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Software using weird folders for updates level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: LotusLite Backdoor | Objectives: Spear Phishing| Target Technology: Windows OS | Targeted Sector: Government & Civic | Target Geography: USA.
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “LotusLite” is trending.
Overview of Operation LotusLite
A targeted cyber-espionage campaign has been identified involving malicious activity directed at U.S. government and policy-related entities. The operation leveraged politically themed content tied to contemporary geopolitical developments to social engineer selected recipients into executing malicious files. The narrow scope of targeting indicates a deliberate and intelligence-driven objective rather than indiscriminate or financially motivated activity.
The campaign employed a simple, yet effective delivery mechanism designed to ensure dependable execution rather than technical sophistication. While the tooling demonstrated limited complexity and minimal evasion features, it could maintain unauthorized access and facilitate the covert extraction of sensitive information. This approach reflects an emphasis on operational reliability and rapid deployment.
Analysis of operational behaviors and infrastructure usage reveals notable alignment with techniques historically associated with the Mustang Panda threat actor. Attribution is assessed with moderate confidence and is based on observed deployment patterns, execution methods, and infrastructure characteristics rather than direct reuse of malicious code.
Although the overall scale of the activity appears limited, the sensitive nature of the targeted entities significantly increases its potential strategic impact. This campaign underscores the continued use of geopolitical narratives in targeted cyber operations and highlights the persistent risk posed by focused espionage efforts against government and policy-oriented organizations.
Attack Method
The attack is initiated through a targeted spear-phishing email that delivers a politically themed ZIP archive containing a legitimate executable and a concealed malicious DLL. When executed, the legitimate binary is abused to sideload the DLL, enabling covert execution of the malware without relying on exploits or elevated privileges.
The malicious DLL operates as a custom backdoor that initializes critical functionality during early runtime, including configuration of persistence parameters and command- and-control (C2) details. Communication with the C2 server is conducted over HTTPS using standard Windows APIs, with traffic crafted to resemble benign web activity through spoofed headers and minimal payload sizes.
Following initial beaconing, the backdoor performs basic system profiling and supports remote command execution, file enumeration, and file manipulation. Persistence is achieved by relocating the loader executable and registering it for automatic execution via a user-level registry Run key.
Overall, the attack prioritizes execution reliability and operational simplicity, reflecting a focused espionage-driven campaign rather than large-scale or financially motivated activity.
The following are the TTPs based on the MITRE Attack Framework
| Tactic (ID) | Technique ID | Technique Name |
| Initial Access | T1566.001 | Spear phishing Attachment |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys |
| DefenseEvasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Command and control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and control | T1090 | Proxy |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
The observed activity highlights how contemporary cyber-espionage operations increasingly rely on contextual relevance rather than technical sophistication. By embedding malware delivery within politically charged narratives tied to real-world events, the attackers demonstrate an understanding of how credibility and timing can outweigh advanced engineering. This approach reflects a broader pattern in which influence, relevance, and perceived authenticity play a central role in gaining initial access to carefully selected targets.
A notable aspect of the campaign is the emphasis on controlled scale and precision. The limited distribution and narrow victim profile indicate an operation designed for selective access rather than widespread compromise. Such restraint suggests a preference for maintaining operational discretion and minimizing exposure, reinforcing the interpretation of this activity as intelligence-oriented rather than opportunistic or profit-driven.
The presence of deliberate stylistic and behavioral elements within malware points to the role of operational identity in threat activity. Subtle markers embedded in tooling and infrastructure choices appear to function as distinguishing characteristics rather than functional necessities. These traits contribute to how analysts cluster activity over time and illustrate how threat actors often leave consistent behavioral signatures even when introducing new or previously unseen malware.
ETLM ASSESSMENT
From an ETLM perspective, this activity signals a future environment in which trusted communication platforms increasingly serve as indirect conduits for threat exposure rather than overt attack surfaces. As employees rely more heavily on consumer messaging tools for routine coordination, organizations may experience heightened residual risk originating outside formal enterprise controls. Over time, this dynamic is likely to blur the separation between personal and professional digital spaces, expanding the scope of organizational risk while increasing the potential for employee-driven propagation, reputational impact, and operational disruption without clear indicators of compromise.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule LOTUSLITE_MustangPanda
{
meta:
description = “Detects LOTUSLITE malware using known hashes and C2 indicators” author = “CYFIRMA”
date = “2026-01-19”
strings:
/* File Hash Indicators (SHA256 as embedded strings) */
$h1 = “819f586ca65395bdd191a21e9b4f3281159f9826e4de0e908277518dba809e5b”
$h2 = “2c34b47ee7d271326cfff9701377277b05ec4654753b31c89be622e80d225250”
/* File Name Indicators */
$f = “kugou.dll”
/* Persistence Path Indicator */
$p1 = “C:\\ProgramData\\Technology360NB”
/* Mutex Indicator */
$m1 = “Global\\Technology360-A@P@T-Team”
/* C2 IP Address Indicator */
$ip1 = “172.81.60.87”
condition:
any of ($h*) or any of ($ip*) or
( any of ($f*) and any of ($m*, $p*))
}
Recommendations
Management Recommendations
Tactical Recommendations
Key Intelligence Signals:
APT37 Operational Shift: From Traditional Targets to Google Ads-Based Delivery
About the Threat Actor
Reaper, also known as APT37, is a suspected North Korean cyber-espionage group active since 2012 and known for its sophisticated tactics, techniques, and procedures (TTPs) as well as advanced malware development capabilities. Initially focused on targets in South Korea, the group has steadily expanded its operational scope and is now actively targeting organizations in Japan, Vietnam, and the Middle East.
APT37 is a long-running, state-aligned threat actor known for sustained espionage campaigns primarily targeting government, defense, diplomatic, and policy- focused organizations. APT37 consistently leverages spear-phishing as its primary access vector, often using socially engineered lures tied to regional geopolitics and current events. Its infrastructure and malware families, most notably the Konni toolkit, are reused across campaigns with incremental modifications, allowing the actor to maintain operational continuity while evading simple signature-based detection.
Its targeting reflects sustained interest in political, military, and diplomatic intelligence, particularly across the Korean Peninsula and allied regions.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2018-4878 | Adobe Flash Player | 9.8 | link |
| CVE-2022-41128 | Windows Scripting Languages | 8.8 | – |
| CVE-2024-38178 | Scripting Engine Memory | 7.5 | – |
| CVE-2020-1380 | Internet Explorer | 8.8 | Link |
| CVE-2017-8291 | Artifex Ghostscript | 7.8 | link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1106 | Native API |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1055 | Process Injection |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Collection | T1123 | Audio Capture |
| Collection | T1005 | Data from Local System |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1529 | System Shutdown/Reboot |
Latest Developments Observed
The threat actor is suspected of conducting spear-phishing campaigns that abuse Google Ads redirection mechanisms as part of an operation referred to as Operation Poseidon. The activity is assessed to target North Korean human rights organizations and South Korean financial institutions. The infection chain involves the delivery of EndRAT via an AutoIt script disguised as a PDF document. The primary objective appears to be the exfiltration of sensitive information.
ETLM Insights
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule APT37_Reaper_EndRAT_Activity
{
meta:
description = “Detects APT37 (Reaper / Group123) malware and infrastructure indicators associated with EndRAT and recent campaigns”
author = “CYFIRMA”
threat_actor = “APT37 / Reaper / Group123” malware_family = “EndRAT / AutoItRAT”
reference = “Operation Poseidon / Konni-linked activity” date = “2026-01-18”
strings:
/* Known malicious file names */
$fname1 = “errorsweeper.exe” nocase
$fname2 = “AFAC7896CF21983233C533EAE8C70610856969D98218.exe” nocase
$fname3 =”exe:afac7896cf21983233c533eae8c70610856969d98218.exe” nocase
$fname4 = “b10d7186f4a2d0655f2f6a38e4eb9c6e.exe” nocase
$fname5 = “exe:b10d7186f4a2d0655f2f6a38e4eb9c6e.exe” nocase
/* C2 / Infrastructure domains */
$dom1 = “fafhoafouhfuh.su” nocase
$dom2 = “nexun.online” nocase
$dom3 = “iplogger.org” nocase
$dom4 = “mygametoa.com” nocase
$dom5 = “okkids.kr” nocase
/* C2 IP addresses */
$ip1 = “109.234.36.135”
$ip2 = “94.103.87.212”
$ip3 = “93.183.93.185”
$ip4 = “91.107.208.93”
$ip5 = “89.110.83.245”
/* CVE references commonly abused by the actor */
$cve1 = “CVE-2018-4878”
$cve2 = “CVE-2022-41128”
$cve3 = “CVE-2024-38178”
$cve4 = “CVE-2020-1380”
$cve5 = “CVE-2017-8291”
condition:
1 of ($cve*) or
1 of ($fname*) or 1 of ($dom*) or 1 of ($ip*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Venezuela operation demonstrated US cyber capabilities, China tries to piggyback
After the January 3rd operation to capture Venezuelan President Nicolás Maduro, who faces drug trafficking charges in the US, reports are emerging that the United States used cyberattacks to cut power across Caracas and disrupt Venezuelan radar during the daring raid. U.S. officials familiar with the operation, speaking anonymously to the press, revealed that the cyber operation was designed to rapidly restore power afterward and to minimize any unintended harm.
At the same time, Venezuela’s state-owned oil company Petróleos de Venezuela SA (PDVSA) has been forced to manage its daily operations using only phone calls and handwritten reports, completely cut off from its own digital systems since a cyberattack struck on December 15. Multiple sources familiar with the situation, who spoke on condition of anonymity, confirmed that the shutdown has severely disrupted contractor and employee payments, as well as the tracking and reporting of production figures. The identity of the attackers remains unknown.
The United States–which has been working to indefinitely control future Venezuelan oil sales following the capture of President Nicolás Maduro and is the main suspect–has not claimed responsibility for the incident. The breach underscores the extreme fragility of Venezuela’s technological infrastructure, even in the sector that generates the vast majority of the country’s revenue. Years of chronic underinvestment, widespread corruption, and U.S. sanctions have prevented PDVSA from acquiring the necessary technology to modernize and secure its systems. The attack also crippled PDVSA’s SCADA operational platform, which controls critical processes in refineries, compression stations, and pipelines. The company’s SAP enterprise software remains offline, forcing employees to handle many tasks manually. Access to the platforms that manage accounting, payments, and production data is still blocked. Internal email services are also down, severely limiting official communication. Staff in legal, finance, engineering, and health departments in Caracas, Barinas, Puerto La Cruz, and El Tigre are now relying on WhatsApp and Telegram for internal coordination. In the Orinoco Belt operations, employees are using Telegram and Gmail as temporary workarounds.
Meanwhile, researchers have discovered that the Chinese threat actor known as Mustang Panda is targeting U.S. government organizations through a sophisticated spear-phishing operation with emails that reference American policy toward Venezuela. These emails include ZIP archives crafted to deploy a backdoor called LOTUSLITE. The malware is a custom C++-based implant that connects to a hardcoded IP address used as its command-and-control (C2) server. It enables basic remote command execution, data theft, and employs a fairly advanced persistence mechanism. All indicators point to an espionage-driven operation rather than one motivated by financial gain.
ETLM Assessment
While specifics about the operations that struck Venezuela remain limited, the raid and cyberattack on PDVSA can be described as one of the most visible demonstrations of U.S. offensive cyber capabilities in recent years. It further highlighted that, at least against a country like Venezuela–whose military lacks advanced defenses against cyberattacks–the United States can deploy cyberweapons with significant, targeted impact and that offensive cyber operations are becoming a mainstay of any multidomain military action.
Poland Blames Russia for Cyberattack on Energy Facilities; ECB says Europe Is Already ‘at War’ With Russia
The Polish government announced that Poland successfully repelled a series of Russian-linked cyberattacks aimed at the country’s energy infrastructure in December.
The attacks, which occurred in the final days of the month, targeted two conventional power plants and several renewable energy installations. Although the assaults were not large-scale and would not have triggered a nationwide blackout, the prime minister stated that if they had succeeded, approximately 500,000 households would have been left without electricity.
According to the government: “There are numerous signs pointing to the fact that these operations were orchestrated by groups closely tied to Russian special services.” Meanwhile, the European Central Bank Governing Council warned policymakers against being “naive” and urged them to recognize that Europe is already “at war” with Russia. The ECB emphasized that central banks must prepare for possible further escalation and stated that while the conflict is not taking place “physically on our territory,” Europe is already facing serious threats through cyberattacks like those in Poland and sabotage of undersea cables in the Baltic Sea.
ETLM Assessment:
Poland, as a key frontline NATO and EU member bordering both Russia and its ally Belarus, faces heightened risks from Moscow’s hybrid warfare tactics. The country has been one of the strongest supporters of Ukraine since Russia’s full-scale invasion in 2022, serving as a major transit hub for military aid to Kyiv. In recent years, hacker groups frequently linked by Polish authorities to the Kremlin have repeatedly struck critical infrastructure in Poland, including hospitals, water treatment plants, and sewage systems. Tensions further intensified last September when multiple Russian drones violated Polish airspace, raising serious concerns about Moscow’s readiness to challenge NATO’s defenses. In November, Poland publicly blamed Russia for orchestrating explosions that damaged a crucial railway line used for transporting aid to Ukraine. Poland currently ranks among the most targeted nations worldwide for cyberattacks.
Qilin Ransomware Impacts Neo Group
Summary:
CYFIRMA observed in an underground forum that a company from Singapore, Neo Group (https[:]//www[.]neogroup[.]com[.]sg/), was compromised by Qilin Ransomware. Neo Group is a Singapore-based company specializing in food and catering solutions, recognized as the top events caterer since 2011. It operates across multiple segments, including catering, manufacturing, retail, supplies, trading, and property, with a trading network spanning over 30 countries. The compromised data contains confidential and sensitive information belonging to the organization.

Source: Dark Web
Relevancy & Insights
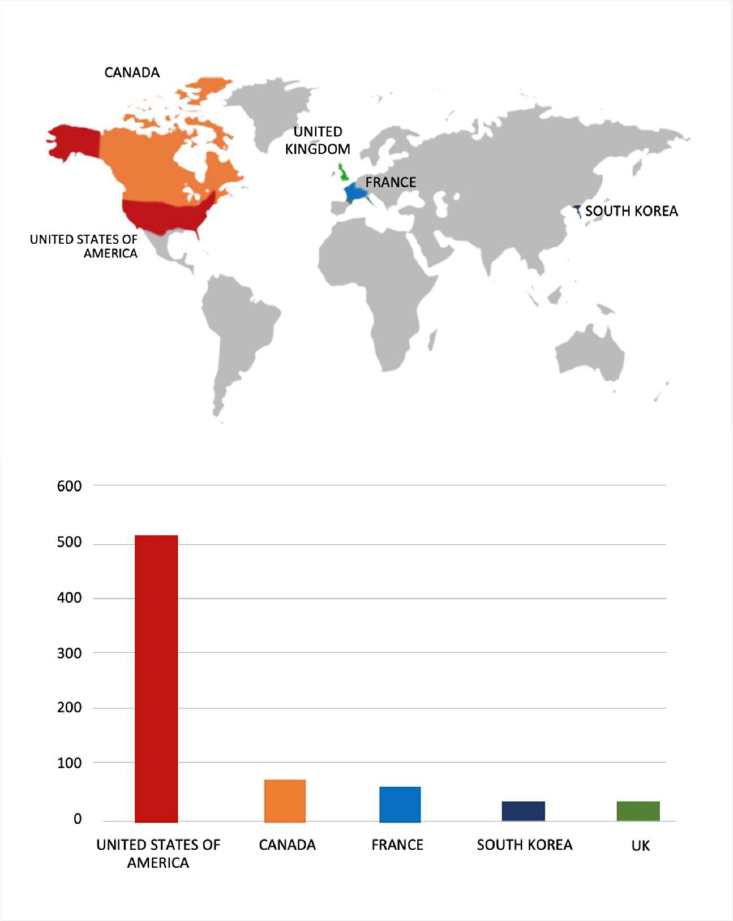
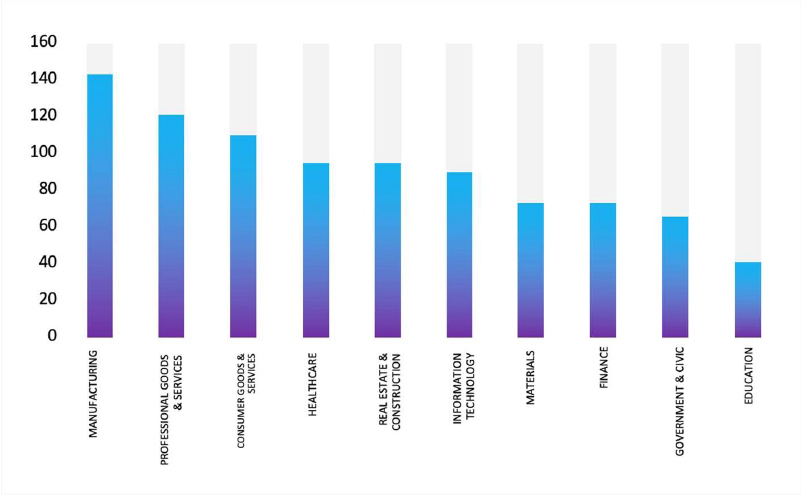
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Tengu Ransomware Impacts Charoenchai Transformer Co., Ltd
Attack Type: Ransomware
Target Industry: Manufacturing Target Geography: Thailand Ransomware: Tengu Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary
CYFIRMA observed in an underground forum that a company from Thailand, Charoenchai Transformer Co., Ltd(www[.]charoenchai[.]com), was compromised by Tengu Ransomware. Charoenchai Transformer Co., Ltd is a manufacturer and supplier of electrical transformers based in Thailand. They manufacture and distribute various types of electrical power transformers both domestically and for export. The compromised data reportedly includes internal documents such as personal identification cards, financial records, and other sensitive materials, collectively amounting to approximately 60 GB of data.
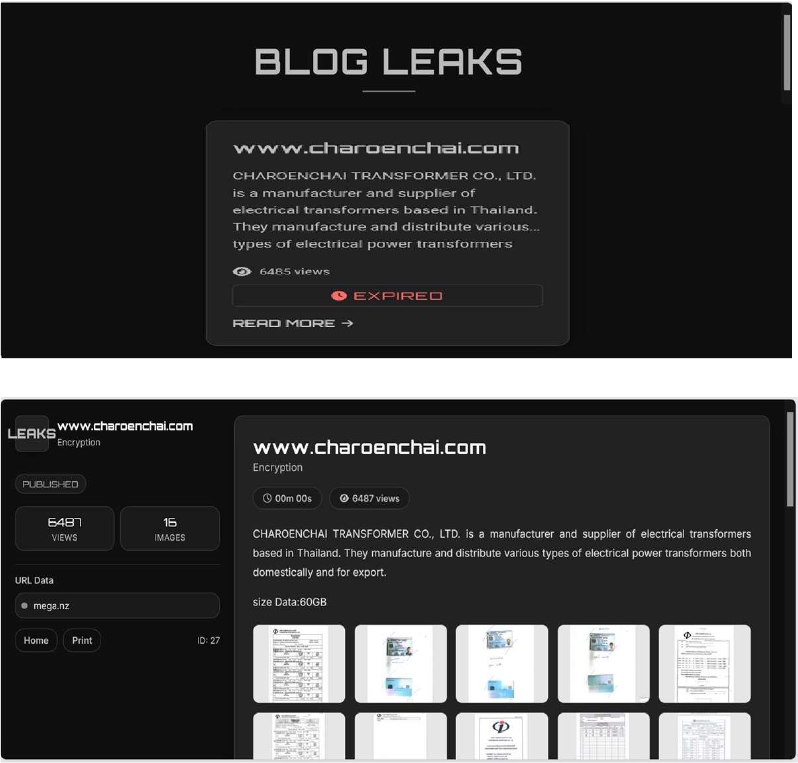
Source: Dark Web
Relevancy & Insights:
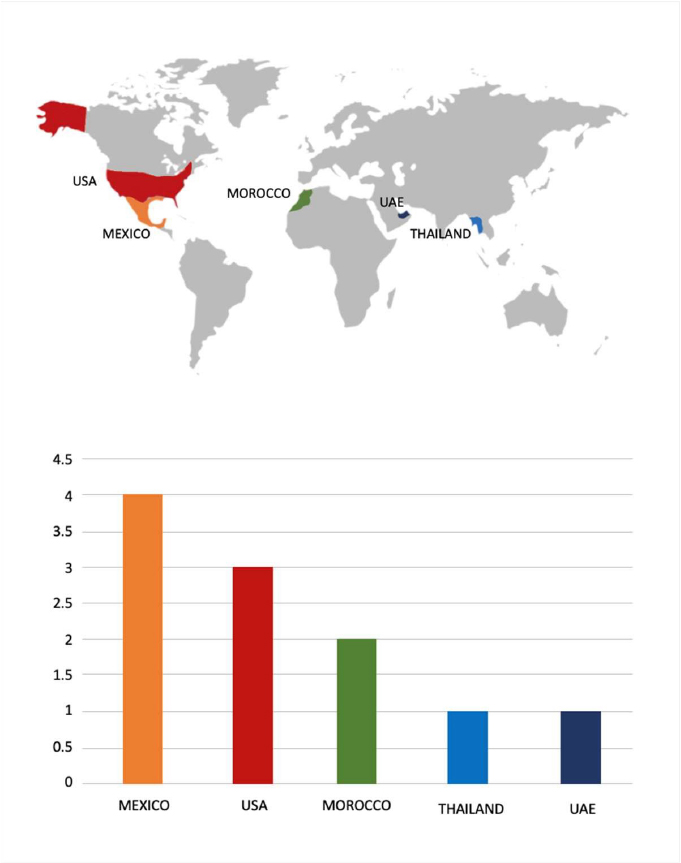
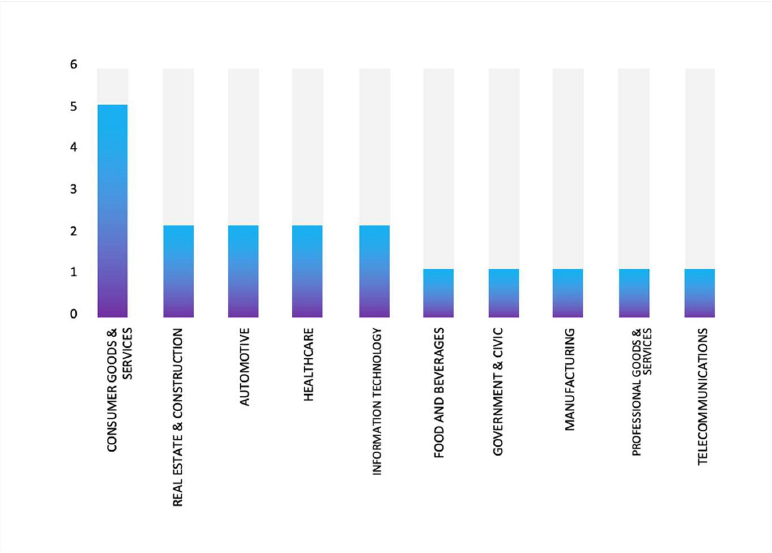
ETLM Assessment:
According to CYFIRMA’s assessment, Tengu Ransomware has emerged as a rapidly escalating threat in the 2026 ransomware landscape, evolving from its initial debut in October 2025 into a prolific Ransomware-as-a-Service (RaaS) operation with a global reach. To counter Tengu’s commonly observed initial access vectors, organizations should prioritize the enforcement of multi-factor authentication, conduct regular phishing simulations, and strengthen endpoint detection capabilities.
Vulnerability in Rocket.Chat
Relevancy & Insights:
The vulnerability exists due to improper authorization checks within the GET /api/v1/oauth-apps.get API endpoint.
Impact:
A remote user can gain unauthorized access to sensitive information on the system.
AffectedProducts:
https[:]//github[.]com/RocketChat/Rocket.Chat/security/advisories/GHSA-g4wm- fg3c-g4p2
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
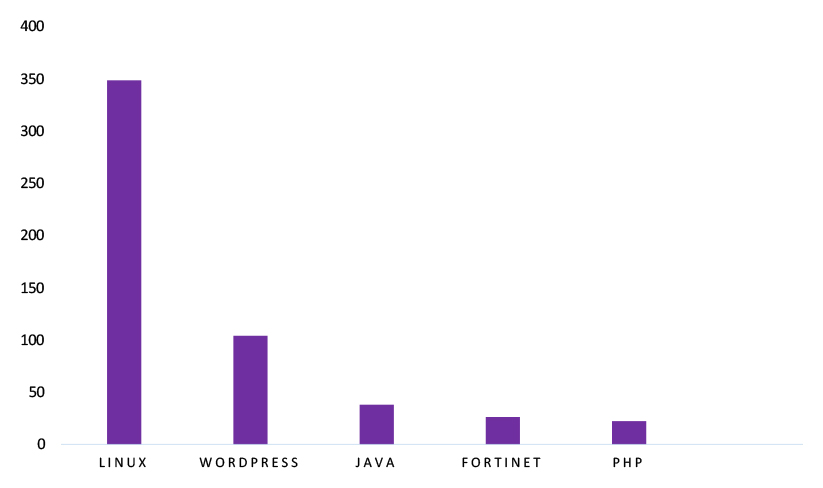
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Rocket.Chat can pose significant threats to application security and communication platform integrity. This can impact various industries globally, including enterprises, government organizations, customer support platforms, and collaboration-driven environments that rely on Rocket.Chat for secure messaging and team communication. Ensuring the security of Rocket.Chat is crucial for maintaining the integrity and protection of user data, authentication workflows, and access-controlled resources across deployments. Therefore, addressing these vulnerabilities is essential to safeguarding confidential communications, platform reliability, and secure collaboration management across different geographic regions and sectors.
Dire Wolf Ransomware attacked and published the data of Perdana Petroleum Berhad
Threat Actor: Dire Wolf Ransomware
Attack Type: Ransomware
Objective: Data Leak, Financial Gains Target Technology: Web Applications Target Industry: Energy, Utilities & Waste Target Geography: Malaysia
Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that Dire Wolf Ransomware attacked and published the data of Perdana Petroleum Berhad (https[:]//www[.]perdana[.]my) on its dark web website. Perdana Petroleum Berhad is a Malaysia-based company that provides offshore marine support services to the upstream oil and gas sector. The company operates a diversified fleet comprising anchor handling tug supply vessels, accommodation workboats, and work barges. Through its subsidiaries, including Intra Oil Services and Perdana Marine Offshore, Perdana supports a wide range of offshore activities such as exploration, development, installation, hook-up, commissioning, production, and maintenance. Its fleet capabilities enable the company to deliver services across both domestic and international offshore markets. The ransomware incident resulted in the compromise of approximately 150 GB of data, encompassing Financial Documents, Legal Documents, Supplier Documents, and Customer Data.
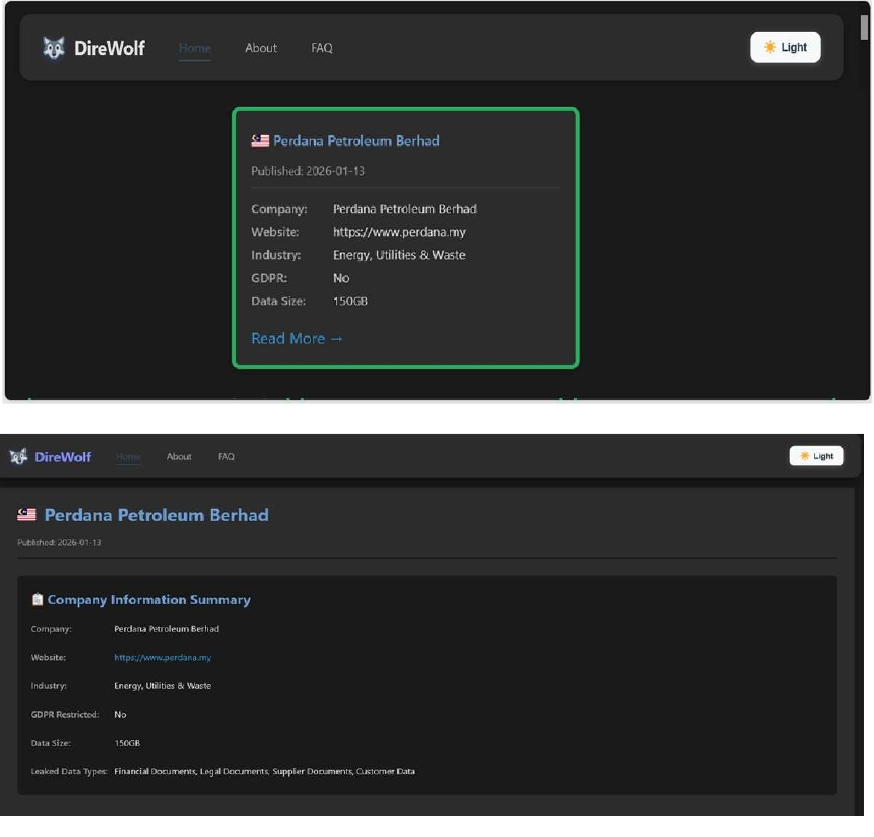
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics, combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
VietISO Data Advertised on a Leak Site
Summary
The CYFIRMA research team has observed claims by a threat actor using the alias “Solonik,” who asserts responsibility for a security breach involving VietISO, a Vietnam-based provider of travel platform and CRM solutions. The alleged incident is said to target VietISO’s customer database, with the actor claiming access to a complete CRM dataset reportedly current through 2026.
According to the threat actor, the exposed data includes verified KYC information pertaining to more than 209,000 individuals, predominantly domestic customers. The purportedly compromised dataset is described as containing the following information:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.Top of FormBottom of Form
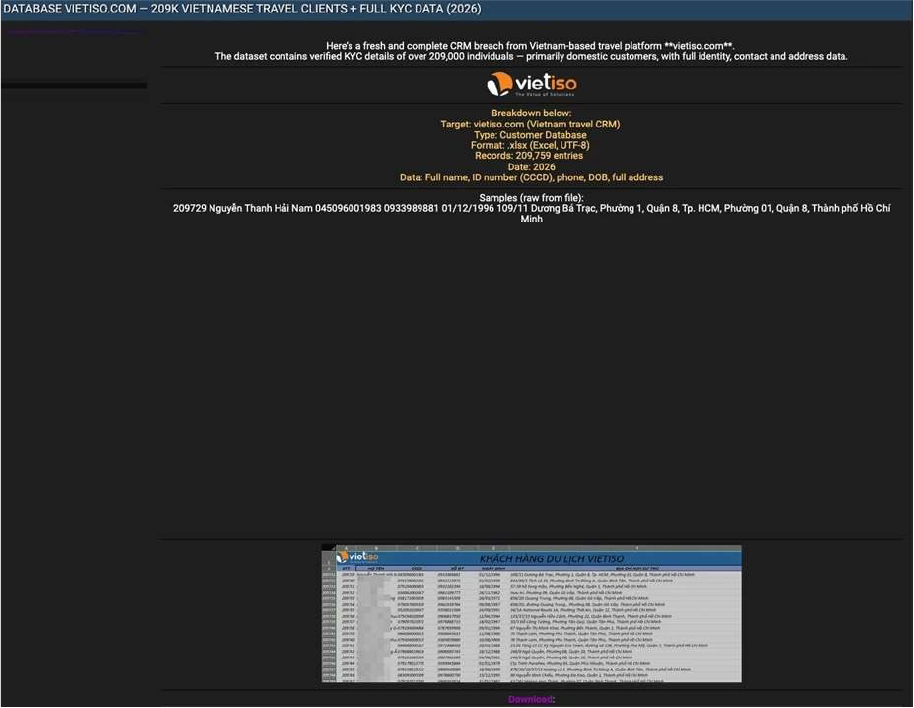
Source: Underground Forums
Mastertech International Data Advertised on a Leak Site
Summary
The CYFIRMA Research team has observed that Mastertech International Co., Ltd., a Thailand-based manufacturer and distributor specializing in time recording and attendance systems, has allegedly been compromised. A threat actor posted the dataset on a dark web forum, claiming the information was updated as of December 2025. The company, which primarily serves a Business-to-Business (B2B) market, is now facing the potential exposure of sensitive records linked to its internal systems or client databases.
According to the actor, the compromised data contains significant amounts of Personal Identifiable Information (PII). A sample of the SQL database provided by the attacker reveals highly specific personal details, suggesting the data may come from detailed HR or security identification records. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
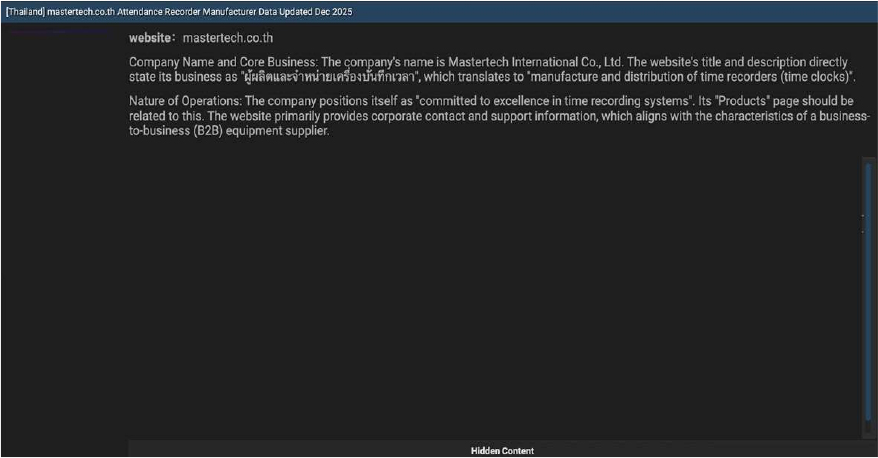
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor operating under the alias “Solonik” is assessed to be a newly emerged yet highly active and capable group, primarily focused on data-leak operations. Multiple credible sources have linked Solonik to a series of security incidents involving unauthorized access to organisational systems. The actor’s activities reflect the persistent and rapidly evolving cyber-threat landscape fueled by underground criminal ecosystems and underscore the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, enhanced threat-intelligence capabilities, and proactive defensive measures to safeguard sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that Sagolink (sagolink[.]ai), a South Korean insurance and accident compensation platform, has allegedly been compromised in a significant data breach. The incident, occurring in January 2026, reportedly resulted in the exposure of approximately 12,000 records belonging to customers and insurance adjusters. The compromised data appears to stem from the platform’s database, revealing sensitive personal information and detailed insurance claim documentation.
According to the samples provided, the allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Source: Underground Forums
The CYFIRMA Research team has identified that Aforeserve[.]co[.]in, a prominent information technology services provider based in India, has allegedly been compromised. The company, which specializes in IT infrastructure support, hardware maintenance, and technical assistance for businesses and organizations, had a full database listed for sale on a cybercrime forum. Samples provided by the threat actor suggest a significant leak of customer service logs and personal contact information.
The allegedly compromised data includes detailed records of technical support tickets and customer profiles. Based on the samples provided, the exposed information includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
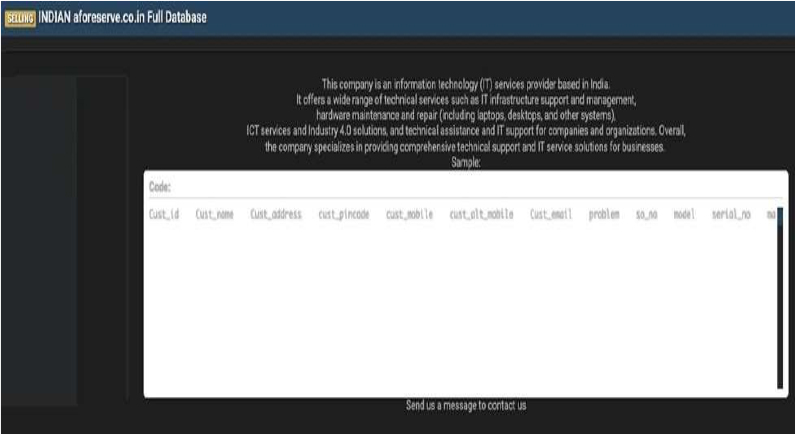
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.