



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industry: Apparel, Biochemical, Electrical, Health, Manufacturing, Real estate and Retail
Target Geography: Israel, United States, United Kingdom.
Introduction
CYFIRMA Research and Advisory Team has found Alpha ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Alpha Ransomware
Alpha, a ransomware that emerged in February 2023, has intensified its operations in the past few weeks. Researchers have recently identified significant resemblances between the Alpha ransomware and the long-defunct NetWalker ransomware, which vanished in January 2021 following an international law enforcement operation.
Initially, the group employed “random numbers” as extensions for the infected files. However, in subsequent revisions, they transitioned to an “alphanumeric 8-character” extension.
Following numerous iterations of ransom notes, the latest version now provides instructions for victims to contact the threat actor through a messaging service.
Connection with the NetWalker ransomware.
When analyzing Alpha, researchers discovered notable similarities with the outdated NetWalker ransomware. Both threats employ a similar loader based on PowerShell to deliver their payloads.
Furthermore, there is a substantial overlap in code between the payloads of Alpha and NetWalker. This includes:
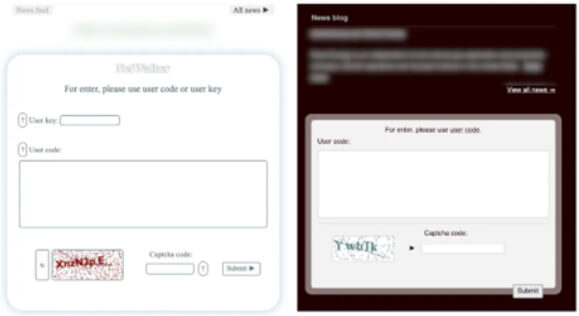
Payment portals for NetWalker (left) and Alpha (right). Both contain the same message. (Source: Surface web)
NetWalker and Alpha have virtually identical lists of processes to kill as given below.
| NetWalker | Alpha |
|---|---|
| nslsvice.exe | nslsvice.exe |
| pg* | pg* |
| nservice.exe | nservice.exe |
| cbvscserv* | cbvscserv* |
| ntrtscan.exe | ntrtscan.exe |
| cbservi* | cbservi* |
| hMailServer* | hMailServer* |
| IBM* | IBM* |
| bes10* | bes10* |
| black* | black* |
| apach* | apach* |
| bd2* | bd2* |
| db* | db* |
| ba* | ba* |
| be* | be* |
| QB* | QB* |
| oracle* | oracle* |
| wbengine* | wbengine* |
| vee* | vee* |
| postg* | postg* |
| sage* | sage* |
| sap* | sap* |
| b1* | b1* |
| fdlaunch* | fdlaunch* |
| msmdsrv* | msmdsrv* |
| report* | report* |
| msdtssr* | msdtssr* |
| coldfus* | coldfus* |
| cfdot* | cfdot* |
| swag* | swag* |
| swstrtr* | swstrtr* |
| jetty.exe | jetty.exe |
| wrsa.exe | wrsa.exe |
| team* | team* |
| agent* | agent* |
| store.exe | store.exe |
| sql* | sql* |
| sqbcoreservice.exe | sqbcoreservice.exe |
| thunderbird.exe | thunderbird.exe |
| ocssd.exe | ocssd.exe |
| encsvc.exe | encsvc.exe |
| excel.exe | excel.exe |
| synctime.exe | synctime.exe |
| mspub.exe | mspub.exe |
| ocautoupds.exe | ocautoupds.exe |
| thebat.exe | thebat.exe |
| dbeng50.exe | dbeng50.exe |
| *sql* | *sql* |
| mydesktopservice.exe | mydesktopservice.exe |
| onenote.exe | onenote.exe |
| outlook.exe | outlook.exe |
| powerpnt.exe | powerpnt.exe |
| msaccess.exe | msaccess.exe |
| tbirdconfig.exe | tbirdconfig.exe |
| wordpad.exe | wordpad.exe |
| ocomm.exe | ocomm.exe |
| dbsnmp.exe | dbsnmp.exe |
| thebat64.exe | thebat64.exe |
| winword.exe | winword.exe |
| oracle.exe | oracle.exe |
| xfssvccon.exe | xfssvccon.exe |
| firefoxconfig.exe | firefoxconfig.exe |
| visio.exe | visio.exe |
| mydesktopqos.exe | mydesktopqos.exe |
| infopath.exe | infopath.exe |
| agntsvc.exe | agntsvc.exe |
| notepad.exe | |
| genshinimpact.exe |
The only difference is the addition of Notepad and the Genshin Impact on Alpha’s list.
In recent Alpha-related attacks, the attackers heavily utilized various living-off-the-land tools, such as:
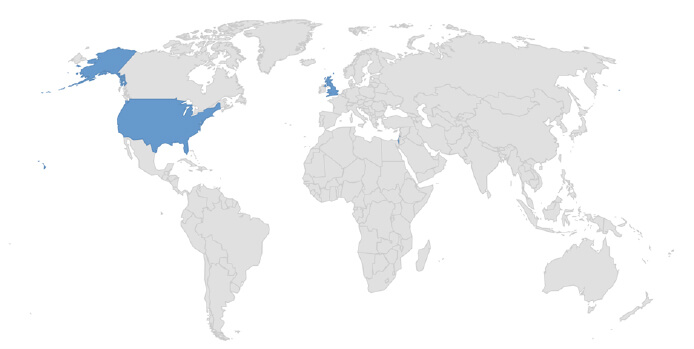
Countries targeted by Alpha ransomware. Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
|---|---|---|
| 1 | TA0002: Execution | T1129: Shared Modules |
| 2 | TA0006: Credential Access | T1056: Input Capture |
| 3 | TA0007: Discovery | T1082: System Information Discovery |
| 4 | TA0009: Collection | T1056: Input Capture |
| 5 | TA0040: Impact | T1486: Data Encrypted for Impact |
ETLM Assessment:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Sigma Rule
Title: Change PowerShell Policies to an Insecure Level Tags:
– attack.execution
– attack.t1059.001 logsource:
product: windows category: process_creation
detection: selection_img:
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’ selection_option:
CommandLine|contains:
– ‘-executionpolicy ‘
– ‘ -ep ‘
– ‘ -exec ‘ selection_level:
CommandLine|contains:
– ‘Bypass’
– ‘Unrestricted’ condition: all of selection_*
falsepositives:
– Administrator scripts level: medium
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Financial theft, Remote Access, Credential Stealing
Threat Actor: GoldFactory
Target Technologies: iOS & Android OS
Target Geographies: Asia pacific (Thailand, Vietnam)
Target Industries: Financial Sector, Banks, and Government
Active Malware of the Week
This week “GoldPickaxe” is trending.
Summary
Researchers have discovered an exceptionally rare mobile malware, named GoldPickaxe.iOS, specifically targeting iOS users. This sophisticated malware belongs to the GoldPickaxe family, which also includes Android versions. Derived from the GoldDigger Android malware, it undergoes regular updates to enhance capabilities and evade detection, posing a significant threat to iOS users. Researchers attribute the entire threat cluster to a single threat actor named GoldFactory, responsible for creating an advanced suite of mobile banking malwares. The primary victims of this malicious activity are concentrated in the Asia-Pacific (APAC) region, with a notable focus on two countries (Thailand and Vietnam). However, there are emerging indications that GoldFactory’s operations may extend beyond these two countries.
GoldPickaxe
GoldFactory, a well-organized Chinese-speaking cybercrime group, has been active since mid-2023. Employing a combination of smishing and phishing techniques, the gang utilizes social engineering as the primary method to deliver malware. Victims, primarily located in Vietnam and Thailand, face sophisticated tactics where GoldFactory’s Android malwares abuse accessibility services to capture screen content information. These Malwares then display fake web forms resembling legitimate banking interfaces, allowing the attackers to capture user credentials, even bypassing two-factor authentication (2FA).

Researchers have identified four malware families employed by cybercriminals, all sharing a naming convention with the prefix “Gold.” This consistent naming strategy symbolizes that these newly discovered malware variants have been developed by the same threat actor.
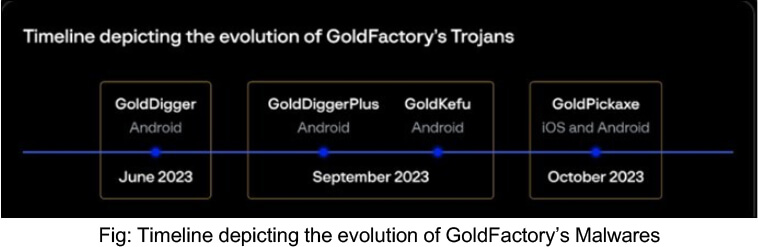
GoldPickaxe Family
GoldPickaxe.iOS, identified as a new family separate from GoldDigger, employs a sophisticated distribution scheme. Initially using Apple’s TestFlight, the threat actor later adopted a multi-stage social engineering approach, convincing victims to install a Mobile Device Management (MDM) profile, granting complete control. Despite being initially thought to be an iOS modification of GoldDigger, the iOS malware’s distinct functionalities led researchers to classify it as a separate family.
In February 2024, reports surfaced of a Vietnamese citizen falling victim to a malicious mobile application, GoldPickaxe. The victim, unknowingly participating in operations instructed by the app, conducted a facial recognition scan, leading to cybercriminals withdrawing over 40,000USD. While there’s no current evidence of GoldPickaxe distribution in Vietnam, the unique feature of facial scanning aligns with GoldFactory’s activity in the region, suggesting a potential utilization of GoldPickaxe in Vietnam. The State Bank of Vietnam’s plan to mandate facial authentication for money transfers from April 2024 raises concerns about more GoldPickaxe instances emerging in the country.
Both GoldPickaxe versions, available on iOS and Android, deploy fake login pages for a Digital pension application. The purpose of gathering user credentials remains unclear, but it’s speculated to aid in avoiding detection and distinguishing between real users and security researchers. GoldPickaxe’s creation of a SOCKS5 proxy server and Fast Reverse Proxy (FRP) using Golang mobile binding for Android and iOS facilitates bypassing anti- fraud measures during transactions. Researchers suggest that phone number requests help the threat actor gather additional victim details, enabling targeted installation of specific banking apps during the money theft stage, reminiscent of tactics used in Gigabud.RAT/Loan.
GoldPickaxe.iOS
The GoldPickaxe.iOS variant, though exhibiting limited functionality compared to its Android counterpart, shares communication methods with C2 servers, identical credentials, and HTTP API endpoints, establishing its association with the GoldPickaxe malware family. The detected malicious application, displaying messages in Thai, suggests a focus on targeting victims in Thailand. The capabilities of GoldPickaxe extend beyond photo extraction from device libraries. Both the Android and iOS versions can collect SMS messages, capture the victim’s face, and proxy network traffic through the victim’s device. Employing a web socket for command reception, HTTP API for command results, and cloud bucket communication for information exfiltration, the malware allows cybercriminals to request additional victim information, including photos of ID cards.
The malware’s operational phases involve the creation of recurring tasks, such as sending heartbeats for device activity, assessing WiFi connection status, and measuring connection speed. GoldPickaxe utilizes a WebSocket connection and a SOCKS5 server for proxy functionality, enabling communication without blocking. The malware uniquely identifies infected devices using Identifiers for Advertisers (IDFA) and issues commands, including a request for ID card uploads and capturing the victim’s face. Additionally, GoldPickaxe includes an iOS app extension exploiting message filtering functionality. Originally introduced for SMS spam prevention, the extension allows the harvesting of messages from victims’ devices. While Apple imposes restrictions on custom message filters and manual victim enablement, the threat actors may deceive victims into enabling these features. The API enables the threat actor to specify a relay in the app extension’s info.plist, facilitating the transmission of all messages to an external server, showcasing the malware’s intricate and multifaceted nature.
Distribution Method
GoldPickaxe.iOS employs a distinct distribution strategy to infiltrate Apple devices. While Apple has a robust system designed to prevent malware distribution through its store, cybercriminals exploit specific features intended to enhance user experience. Similar deceptive tactics have been observed in previous campaigns, such as the CryptoRAM scheme, where TestFlight, Apple’s platform for distributing and beta testing iOS applications, was exploited to disseminate fake cryptocurrency apps. Another method involves manipulating Apple devices through Mobile Device Management (MDM), a centralized solution for managing and securing mobile devices. GoldFactory adeptly utilizes both tactics to distribute its iOS malware. Abusing TestFlight results in victims receiving seemingly innocent URLs under the Apple domain, leading users to install seemingly legitimate software and unknowingly exposing their devices to threats. A more sophisticated approach involves manipulating victims into interacting with fraudulent websites, prompting the installation of an MDM profile. Despite the complexity and suspicious nature of these steps, successful execution grants cybercriminals complete control over the victim’s device, showcasing the multifaceted and sophisticated scheme employed by GoldFactory to deploy GoldPickaxe.iOS.
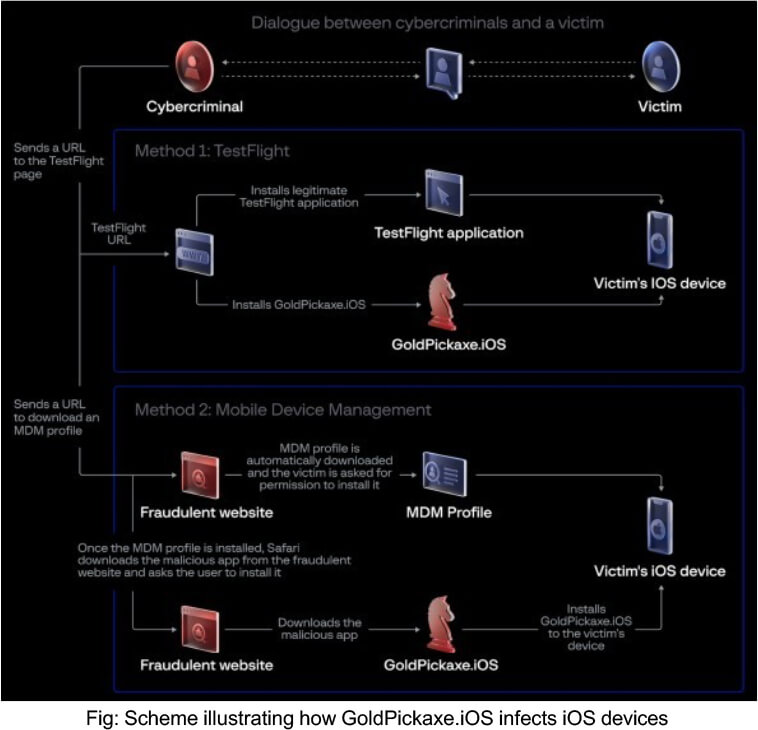
From TestFlight to MDM: GoldFactory’s iOS Exploits
GoldFactory employs TestFlight as a method to exploit users, utilizing its versatility for testing purposes and bypassing regional restrictions. This approach, however, is not without challenges, as TestFlight’s usage is subject to Apple’s review process, potentially leading to the detection and blocking of malicious applications. In response, GoldFactory strategically shifted to using Mobile Device Management (MDM), recognizing the limitations associated with TestFlight. MDM provides a more adaptable and less scrutinized avenue for distributing their malicious applications, showcasing the agility and resilience of cybercriminals. Researchers have notified Apple about the activities linked to GoldFactory.
Researchers monitoring GoldFactory’s activity observed changes in the infection chain, identifying fraudulent domains designed to download Mobile Device Management (MDM) profiles. This discovery aligns with an alert from the Thai Cyber Police, who reported a scam in November 2023. Cybercriminals impersonating officials from the Ministry of Finance targeted individuals, claiming their elderly relatives were eligible for additional pension benefits. Victims, following the provided links, unknowingly downloaded MDM profile settings, granting remote control of their mobile devices to the criminals. The fraudulent websites offer detailed instructions, written in Thai, on how to install malicious applications.
Upon installing the MDM profile, cybercriminals acquire unauthorized control over the device, exploiting features like remote wipe, device tracking, and application management. This control allows them to install malicious applications and gather the necessary information. Notably, the GoldPickaxe.iOS malware, integrated into the MDM abuse scheme, masquerades as a Thai government service app, adding a layer of deception to its malicious activities.
GoldPickaxe.Android
The GoldPickaxe Android variant exhibits greater functionality compared to its iOS counterpart, masquerading as over 20 different applications from various sectors in Thailand, enabling the theft of login credentials from government, financial, and utility services. This variant, potentially an evolved form of GoldDiggerPlus, retains unused functions. Upon entering the username and phone number on the initial login page, victims set a password for the Digital Pension app, undergoing password validation. Subsequently, the application prompts users to enable Accessibility Service in the Settings page.
Commands from the C2 via the websocket lack encryption, while results sent to the HTTP API endpoint are encrypted using RSA encryption. Similar to the iOS version, the Android variant initiates a SOCKS5 proxy server (127.0.0.1:1081) and FRP. Configuration values for the reverse proxy are requested from the C2 and stored in `config.ini`. The Malware can download and install a separate ‘B’ APK, although its specific functionalities remain unknown.However, researchers believe that it could be similar to GoldKefu. Drawing parallels with GoldKefu, an embedded APK in GoldDiggerPlus performing web fakes and real-time voice calls, provides insight into the potential capabilities of the ‘B’ APK for GoldPickaxe.
Distribution Method
GoldDigger, GoldDiggerPlus, and GoldPickaxe.Android employ a common distribution method by spreading through fake websites. These deceptive sites often pose as Google Play Store pages or counterfeit corporate websites, specifically targeting victims in Vietnam. The objective of this strategy is to facilitate the successful installation of the malware on the victim’s device, indicating a shared distribution scheme among these related threats.
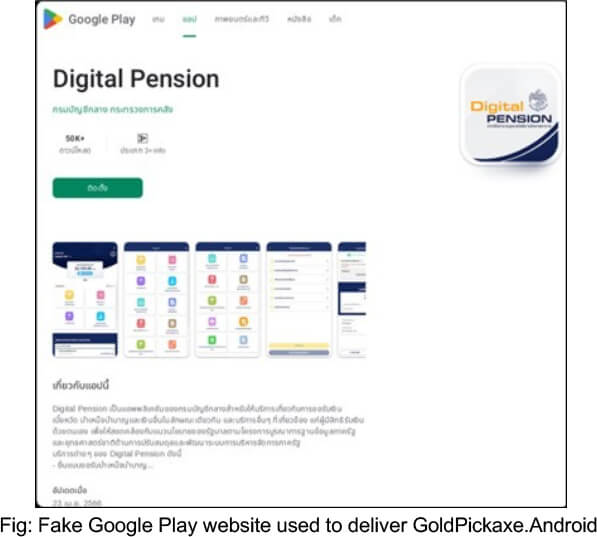
GoldPickaxe: Unveiling Advanced Features Exploiting iOS and Android Banking Security
GoldFactory effectively targets both iOS and Android mobile operating systems, successfully bypassing stringent security controls. In Android malware, the user is deceived into installing a malicious application, granting necessary permissions that allow GoldFactory’s sophisticated malwares to operate autonomously, manipulating the victim’s device discreetly. The Android malwares exploit accessibility services to capture screen content and display fake web forms mimicking legitimate banking interfaces, even circumventing two-factor authentication. Recent developments in Thailand, introducing facial recognition for transaction confirmation, prompted a security measure to counter fraudulent activities. However, GoldFactory has adapted by developing the advanced
GoldPickaxe malware family. GoldPickaxe prompts victims to record a video for confirmation, utilizing the recorded material for deepfake videos through face-swapping AI services.
Both iOS and Android versions of GoldPickaxe possess additional capabilities, such as requesting ID documents, intercepting SMS, and proxying traffic through the victim’s device. Although GoldPickaxe doesn’t directly perform unauthorized transactions, it autonomously collects information to access the victim’s banking application. The combination of facial recognition video capture, SMS interception, and ID document retrieval raises concerns about unauthorized access to bank accounts. While there are no documented cases of such access, it’s hypothesized that cybercriminals use their devices to log in, bypassing facial recognition checks with captured face scans, a strategy confirmed by the Thai police.
Thailand’s Cyber Threat: GoldFactory’s Deceptive Tactics
In the cyber threat landscape of Thailand, cybercriminals adopt deceptive tactics by posing as government authorities and manipulating victims into using LINE, a widely popular messaging application in the country. To initiate contact, the LINE user is required to add the impersonator as a friend. The Thailand Banking Sector CERT (TB-CERT) has reported the distribution of malicious links through messengers, enticing victims to install a fraudulent application masquerading as a ‘Digital Pension’ app.
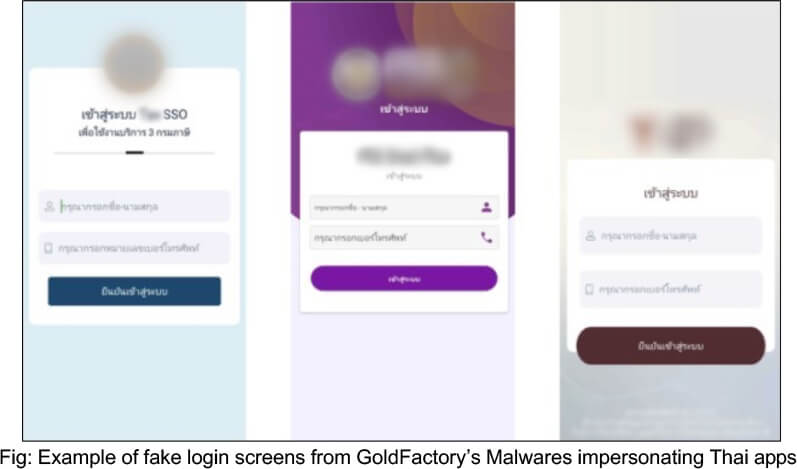
This deceptive app claims to facilitate digital pension transactions, adding a layer of credibility to the cybercriminals’ schemes. TB-CERT’s (Thailand Banking Sector CERT) alert raises concerns as the attackers possess credible personal information about the victims, enhancing the effectiveness of their fraudulent tactics. Researchers, delving into the investigation, have discovered multiple versions of GoldPickaxe with identical functionality, each disguised as various official Thai government services. Notably, GoldFactory’s malicious campaigns involve mimicking legitimate government applications, including Digital Pension for Thailand, other Thai government services, and the Vietnamese government information portal. It’s noteworthy that some of the applications impersonated by GoldPickaxe overlap with those targeted by the Gigabud malware.
Cybercriminals employ a deceptive scheme involving fake messages promising tax refunds on electricity bills. Upon opening the provided link, recipients are redirected to LINE, where they are prompted to add the cybercriminal as a friend. Using social engineering tactics within the LINE messenger, the cybercriminal persuades victims to follow specific steps and install a malicious application. Unfortunately, retrieving any messages is challenging, as the cybercriminals routinely clear the chat history on the infected devices.
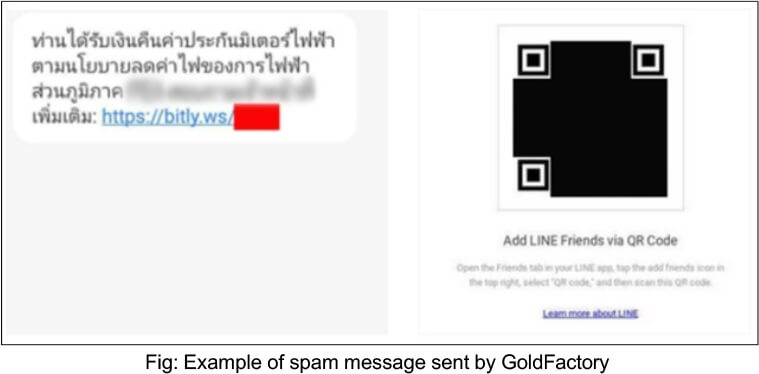
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the GoldPickaxe threat, orchestrated by the sophisticated GoldFactory, is likely to evolve with enhanced tactics and capabilities. The impact of GoldPickaxe and its variants may intensify, expanding its geographical reach beyond the Asia-Pacific region. Anticipate continued targeting of financial systems, with a focus on refining evasion techniques, integrating emerging technologies, and potential collaboration with other threat actors. The multifaceted nature of GoldPickaxe, with its emphasis on personal information harvesting and banking credential theft, could lead to an increased threat to employees worldwide, especially in the financial sector and government.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Unveiling Turla: A Persistent Cyber-Espionage Adversary
Summary:
In a recent observation, the Turla APT group; a Russian state-sponsored threat group, has been linked to targeting a Polish non-governmental organization. This activity comes amid growing concerns over cybersecurity threats. Additionally, the emergence of TinyTurla-NG (TTNG), a sophisticated backdoor associated with the notorious Turla APT group is being used.
TinyTurla-NG made its debut as early as December 2023 and was still active as recently as Jan. 27, 2024, with its primary target being a Polish non-governmental organization (NGO) dedicated to supporting Ukrainian democracy during the Russian invasion. This revelation underscores the geographical focus of Turla’s operations.
The targets of TinyTurla-NG signify a deliberate effort by Turla to infiltrate organizations working towards promoting democracy and aiding regions affected by conflict. By targeting Polish NGOs involved in supporting Ukraine, Turla aims to gain access to valuable information and potentially influence aid packages for victims of ongoing conflicts.
Turla’s modus operandi involves exploiting vulnerabilities in WordPress-based websites to establish command and control (C2) endpoints for the TinyTurla-NG backdoor. The malware utilizes PowerShell and cmd.exe for command execution, employs evasion techniques, and ensures persistence through registry manipulation. Additionally, the inclusion of TurlaPower-NG underscores the group’s concerted effort to steal login credentials and exfiltrate sensitive data.
TinyTurla-NG serves as a powerful tool for espionage and data theft, enabling Turla to infiltrate systems, execute commands, and exfiltrate valuable information. By targeting Polish NGOs supporting Ukraine, Turla aims to monitor aid efforts and potentially manipulate aid packages for strategic gains. The motive behind Turla’s actions aligns with its overarching objective of furthering Russian interests through covert cyber operations.
Relevancy & Insights:
Turla; a highly sophisticated Advanced Persistent Threat (APT) group linked to a Russian intelligence service and active since 2004, has a history of using malware like TinyTurla to target countries of interest, including Germany and Afghanistan, to serve Russian interests. Recently, they’ve adapted and enhanced TinyTurla into TinyTurla- NG, incorporating new modules and capabilities for stealthy infiltration, data exfiltration, and command execution. The group’s continued evolution and persistence underscore the ongoing threat they pose to global cybersecurity, highlighting the need for robust defences against such advanced adversaries.
ETLM Assessment:
The evolving landscape of external threats demands vigilant management to mitigate risks effectively. Turla; an advanced and persistent threat group, hailing from Russia, has long been recognized for its sophisticated cyber operations. Notably, Turla has targeted a Polish non-governmental organization supporting Ukraine during the Russian invasion, exemplifying a concerning trend where threat actors align their attacks with geopolitical agendas. This incident underscores the emergence of a new breed of threat actors, leveraging cyber warfare to advance state interests, highlighting the need for heightened awareness and proactive defences. Furthermore, the involvement of Turla in such operations suggests a potential ripple effect, with other threat actors possibly following suit to support Russian objectives.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US disrupts Russian Government’s Botnet
The US Federal Bureau of Investigation (FBI) announced that it had disrupted a botnet controlled by Russia’s APT28 (also known as “Fancy Bear”); a threat actor attributed to the Russian Military Intelligence (GRU) Unit 26165. According to the statement, the botnet was composed of hundreds of small office/home office (SOHO) routers and was used to conduct vast spear phishing and similar credential harvesting campaigns against targets of intelligence interest to the Russian government, such as U.S. and foreign governments and military, security, and corporate organizations.
Based on the agency’s assessment, this botnet was distinct from prior GRU and Russian Federal Security Service (FSB) malware networks, disrupted by the Department in that it was not created from scratch. Instead, the Russian hackers relied on the ‘Moobot’ malware, which is associated with a known criminal group. Non-GRU cybercriminals installed the Moobot malware on Ubiquiti Edge OS routers that still used publicly known default administrator passwords. GRU hackers then used the Moobot malware to install their own bespoke scripts and files that repurposed the botnet, turning it into a global cyber espionage platform.
ETLM Assessment:
In a report last fall, we warned that Russia seems to be increasingly employing privateering actors, motivated by financial gains to bolster its cyber capability. Such a trend is expected to continue as privateers are offered even more leniency. In the eyes of the Kremlin, the more global instability, the better. Any campaign that helps to divert attention from Moscow’s war on Ukraine means fewer resources available to oppose it.
Reported US cyberattack against Iranian military ship
According to media reports, the US launched a cyberattack against an Iranian military ship that had been gathering intelligence on cargo vessels in the Red Sea and the Gulf of Aden. News quote unnamed US officials stating that the operation was intended to inhibit the Iranian ship’s ability to share intelligence with Houthi rebels in Yemen, who have been firing missiles and drones at cargo ships in the Red Sea.
ETLM Assessment:
The recent acceleration in hostilities involving Iran-backed militias and the United States, coupled with a surge in Israeli strikes on Iranian positions in Syria, seems to have compelled Tehran to reassess elements of its regional strategy. The escalation comes at an inopportune time for Iran and we assess Iran will diminish its overt military footprint and focus more on activity in cyberspace. The US will naturally try to inhibit this course of action by its own countermeasures. In a recent example of the Iranian campaign, one of the Tehran-affiliated groups, dubbed GREATRIFT (also known as Plaid Rain), is suspected to have propagated malware via fake “missing persons” site, targeting visitors seeking updates on abducted Israelis. The threat actor also utilized blood donation-themed lure documents as a distribution vector.
The Cl0p Ransomware impacts the Bronstein & Carmona
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]bronstein-carmona[.]com), was compromised by the Cl0p Ransomware. Founded by lawyers with significant insurance defense and trial experience, Bronstein & Carmona, P.A. has garnered the acclaim of the insurance industry with service excellence, and a strong reputation for cost-effective results. The compromised data may encompass potentially sensitive and confidential information associated with the organization.
The following screenshot was observed published on the dark web:
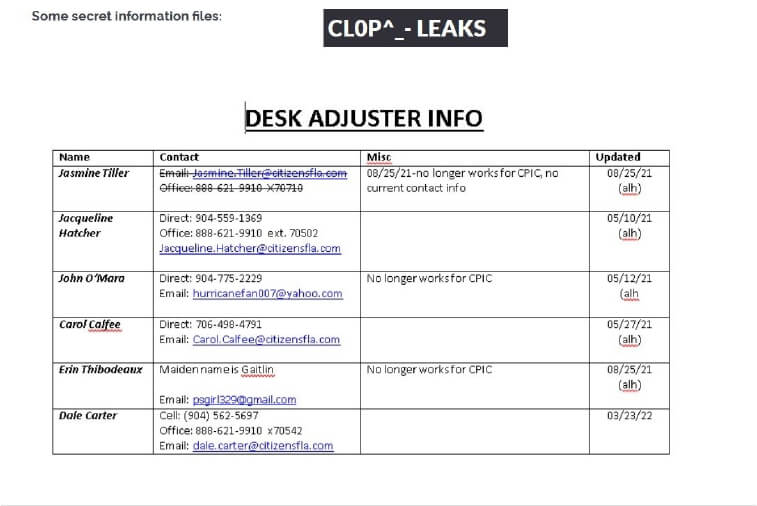

Source: Dark Web
Relevancy & Insights:
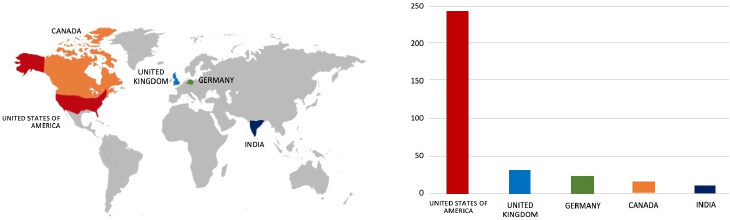
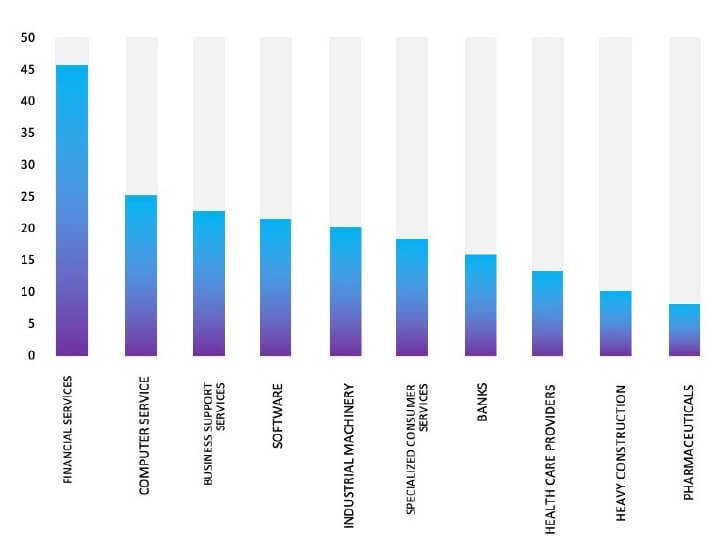
ETLM Assessment:
Cl0p is a notorious Russian-speaking ransomware syndicate employing a ransomware-as-a-service (RaaS) model, where malevolent actors lease their malware for a percentage of the earnings. Initially emerging in 2019 as a derivative of the CryptoMix ransomware, the group has evolved from spear-phishing tactics to exploiting critical vulnerabilities such as those found in SolarWinds and MOVEit. According to CYFIRMA’s analysis, Cl0p Ransomware is anticipated to persist in its targeting of multinational corporations and affiliated entities, which harbour substantial quantities of Personally Identifiable Information (PII), financial records, or other confidential data. Nonetheless, the recent breach at Bronstein & Carmona serves as a stark reminder of the significant threat Cl0p Ransomware poses to enterprises in developed economies.
Vulnerability in SolarWinds Orion Platform
Summary:
The vulnerability allows a remote attacker to execute arbitrary SQL queries in database.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data within the update statement. A remote user can send a specially crafted request to the affected application and execute arbitrary SQL commands within the application database.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to read, delete, modify data in database and gain complete control over the affected application.
Affected Products: http[:]//www[.]solarwinds[.]com/trust-center/security-advisories/cve- 2023-50395
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
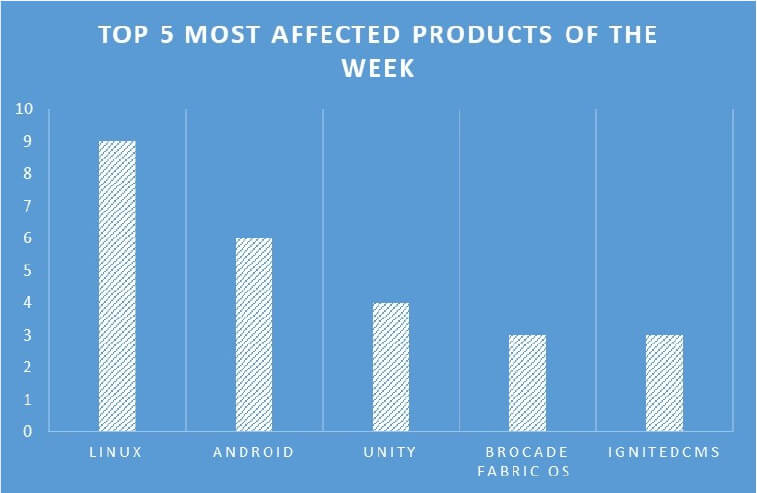
Cactus Ransomware claims to steal 1.5TB of Schneider Electric data
Summary:
The Cactus ransomware group claims responsibility for pilfering 1.5TB of data from the Energy management and industrial automation giant Schneider Electric. Schneider Electric is a multinational company that specializes in energy management, industrial automation, and digital transformation. 25MB of allegedly stolen data was also leaked on the operation’s dark web leak site as proof of the threat actor’s claims, together with snapshots showing several American citizens’ passports and non-disclosure agreement document scans. The ransomware group gained access to the energy management and automation giant’s Sustainability Business division on January 17th. The gang is now extorting the company, threatening to leak all the allegedly stolen data if a ransom demand is not paid. The data stolen from its compromised systems could include sensitive information about customers’ industrial control and automation systems and information about environmental and energy regulations compliance. Schneider Electric’s Sustainability Business provides sustainability consulting services to large organizations worldwide, including Clorox, DHL, Hilton, and PepsiCo. However, it is unclear how many of these clients were affected by the incident.
Relevancy & Insights:
Active since at least March 2023, Cactus garnered significant attention in November, when security operations firm, Arctic Wolf, attributed it to the exploitation of vulnerabilities in a product from business analytics firm, Qlik. Additionally, it was noted for exploiting Fortinet VPN flaws for initial access, establishing an SSH backdoor for persistence, utilizing remote access tools, pilfering credentials, and encrypting data on all accessible systems. Cactus has demonstrated heightened activity in recent months, currently boasting listings from over 100 companies on its leak site.
ETLM Assessment:
Cactus ransomware emerged as a new threat in March 2023, introducing double- extortion tactics. Its operators infiltrate corporate networks via purchased credentials, partnerships with malware distributors, phishing schemes, or exploiting security vulnerabilities. Once inside a target’s network, they traverse laterally, exfiltrating sensitive data for use as leverage during ransom negotiations. CYFIRMA assessments suggest a high probability of Cactus ransomware continuing its global campaign, seeking significant financial gains through ransomware operations.
ALL INDIA SUPERMART PTE LTD data advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to ALL INDIA SUPERMART PTE LTD, {www[.]allindiasupermart[.]com[.]sg}. All India Supermart Pte Ltd. is a leading shopping store, offering a variety of premium quality Indian groceries, vegetables, and consumer products under a single roof. The data available for sale includes first name, last name, email, telephone number, password salt, address, unit number, city, and other confidential details. The asking price for this data is 150 USD.
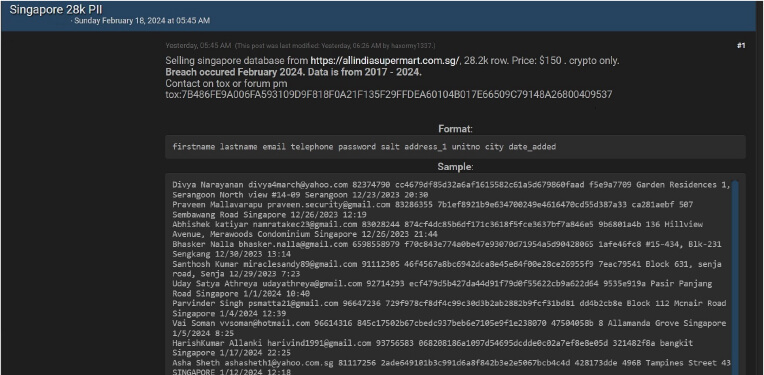
Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial incentives are constantly seeking out exposed and vulnerable systems and applications. Many of these attackers’ frequent underground forums where they discuss and trade stolen digital assets. Unlike ransomware or extortion groups, who often publicize their attacks, these cybercriminals prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications to gain access and pilfer valuable data. This stolen data is then advertised for sale in underground forums, where it may be resold and repurposed by other attackers for their own nefarious purposes.
ETLM Assessment:
Haxormy1337 is an emerging threat actor primarily motivated by financial gains. Presently, they are actively engaged in trading sensitive data, including personally identifiable information (PII), financial records, and other confidential information belonging to ALL INDIA SUPERMART PTE LTD, within illicit online forums. According to CYFIRMA’s assessment, based in Singapore, institutions with insufficient security measures and infrastructure are at an elevated risk of potential cyberattacks from this threat actor.
CYFIRMA Research team observed a potential data sale related to MECHEMA CHEMICALS INT CORP, {www[.]mechema[.]com}. MECHEMA CHEMICALS INT
CORP. is a Taiwan-based company principally engaged in the manufacturing, trading, import, and export of oxidation catalysts. The Company’s principal products include cobalt acetates, manganese acetates, cobalt compounds, manganese compounds, cobalt bromides, manganese bromides, cobalt metals, and manganese metals. The Company is also engaged in the production and trading of magnetic materials and raw materials of batteries, as well as the cyclic utilization of waste oxidation catalysts. The Company mainly distributes its products in the domestic market and overseas markets, including the People’s Republic of China (the PRC), Korea, Thailand, Malaysia, and Indonesia. The information provided contains sensitive and confidential data related to servers. The total size of the data available for sale is 1.2 terabytes (TB).
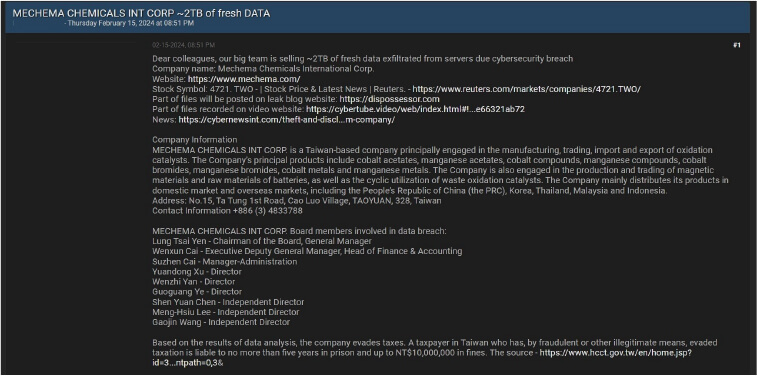
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS