



Key Intelligence Signals:
Summary:
TA453 is active since 2020 and deployed under the IRGC intelligence organization. TA453 has been targeting diplomats, human rights workers, policymakers, journalists, and researchers with expertise in the Middle Eastern region. The group chooses to communicate for weeks with the victim and deliver the malware when they feel the time is right, during the year 2022 out of 60 attacks more than half were initiated with week-long conversations, and few attacks saw the immediate dropping of the malware. The threat actor mostly delivered credential harvesting links to gain access to the inbox for the exfiltration of data from email. Recently, the threat researchers detected a persona named Samantha active since April. The targeting region being the U.S., threat actor-controlled Samantha’s email account reached out to the US-based insurance company for the claim to her damaged car. The attached document with the mail was injected with the remote template injection to download multiple .dotm files from office-updates[.]info. Upon execution of the malware, a PowerShell backdoor called GhostEcho gets executed.
Insight:
Some Russian cities are experiencing GPS jamming. Russian electronic warfare capabilities have been disrupting GPS signals during the current war in Ukraine, however, signal interference has not been widely reported deeper on Russian territory in recent days. Multiple major Russian cities appear to have had GPS disruptions recently. The signal interference follows Ukraine launching long-range drone attacks deep into Russian territory, and it may act as a way to potentially stop drones that rely upon GPS for navigation. Jamming bubbles have been reported to cover hundreds if not thousands of kilometers around cities with important operational assets like railway hubs, military plants, and installations or oil storage facilities.
Researchers have recently spotted a new supply-chain attack in Ukraine, in which Windows 10 installers with embedded Trojans are being distributed to targets in Ukraine. The researchers report there seems to be an overlap between this round of attacks and the victims targeted by Russian military intelligence with wiper malware earlier this year. The deployed malware has anti-detection capabilities, and the campaign seems to be actively targeting the same organizations and the same type of organizations against which the Fancy Bear APT group probably campaigned early in the war.
US NSA Cybersecurity Director Rob Joyce warns against complacency concerning Russian cyber operations. During a press briefing on the release of the NSA’s 2022 retrospective, Mr. Joyce warned that he would not encourage anyone to be complacent or be unconcerned about the Russian threats, especially to the energy sector, globally. In that, he expressed a sentiment long held and repeatedly expressed by CYFIRMA researchers, who have also been warning about the Russian threat to the energy sector for the coming months and years. Mr. Joyce then followed “As the war progresses there’s certainly the opportunities for increasing pressure on Russia at the tactical level, which is going to cause them to reevaluate, try different strategies to extricate themselves.”
The Exchange Bank Impacted by Black Basta Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective CYFIRMA observed The Exchange Bank – a community bank offering personal and business banking services including mortgages, home loans, lines of credit, and SBA loans – being impacted by the Black Basta ransomware group. The ransomware group claimed The Exchange Bank (www[.]exb-ok[.]com) as one of their victims by disclosing the update on their dedicated leak site. It is suspected that a large amount of clients’ information, financial data, PII, and many other business-critical and sensitive data has been exfiltrated.
Insights:
The group’s first known attack using the Black Basta ransomware occurred in the second week of April 2022. Like other enterprise-focused ransomware operations, Black Basta employs a double extortion scheme that involves exfiltrating confidential data before encryption to threaten victims with the public release of the stolen data. According to the ransomware message, victims are given seven days to pay else the stolen content will be publicized.
Researchers observed that the Black Basta ransomware group is using QBot as its first entry point to move laterally on compromised networks. QBot, also known as Qakbot, is a Windows malware strain that began as a banking Trojan and progressed to become a malware dropper. Other ransomware groups have used it as well, including MegaCortex, ProLock, DoppelPaymer, and Egregor. While the other ransomware groups used QBot for initial access, the Black Basta group used QBot for both initial access and side-network distribution.
BlackBasta ransomware made significant updates in November 2022, including file encryption algorithms, stack-based string obfuscation, and per-victim file extensions.
On December 14th, the US Department of Justice announced that it had seized 48 domains related to “booters” or “stress testers” for DDoS attacks in collaboration with EUROPOL. Six people have been charged as part of the ‘PowerOFF’ operation.
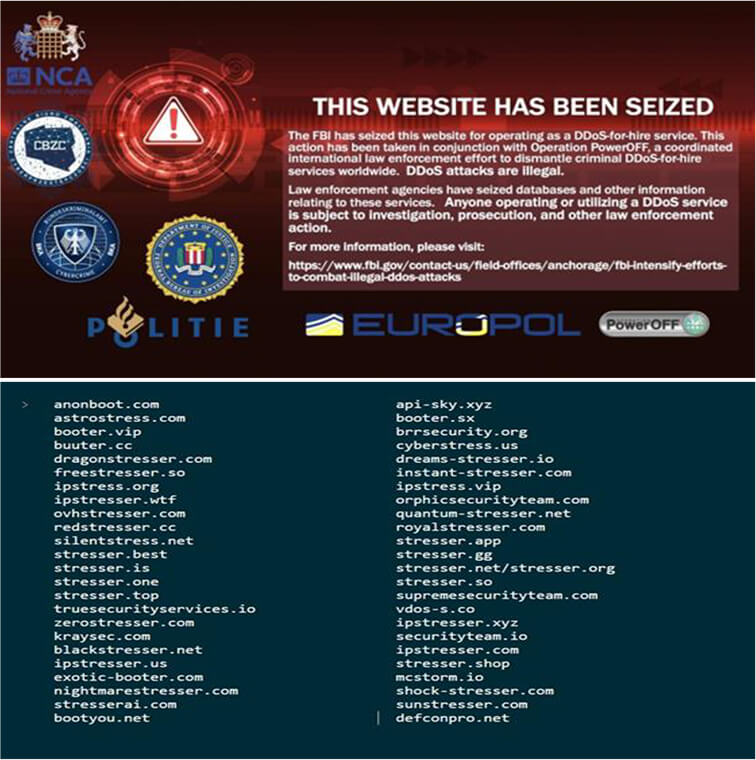
Source: Darkweb, Telegram
Indian internet service provider data was on sale. Data includes cust_id, mobile number, city, name of the person, and status of the account. Leaked data can be used for scamming and phishing purposes.
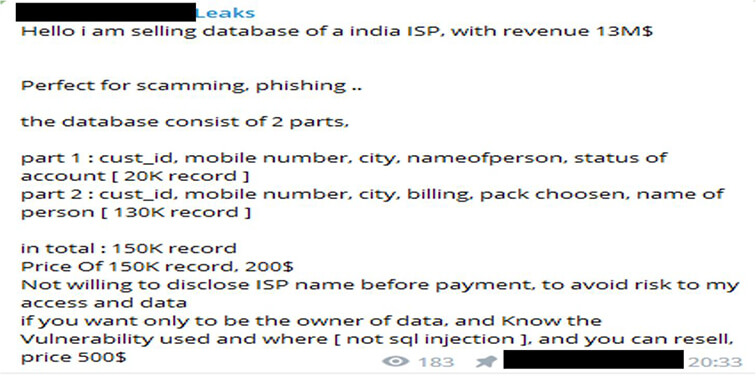
Source: Telegram
Interview with Lockbitsupp – The first interview was conducted with Lockbitsupp. Leader of one of the largest cybercrime gangs currently existing. The questions were compiled in an “Ask Me Anything” style, in which a community of people could submit various questions.