



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Blue ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Blue
Researchers have uncovered a new ransomware variant from the Phobos family, known as Blue. This ransomware encrypts files and renames them by appending the victim’s ID, the email address, and the “.blue” extension. Additionally, Blue generates “info.hta” and “info.txt” files, which contain the ransom note, demanding payment for the decryption key.
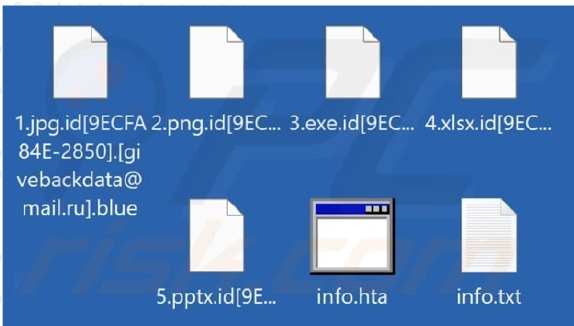
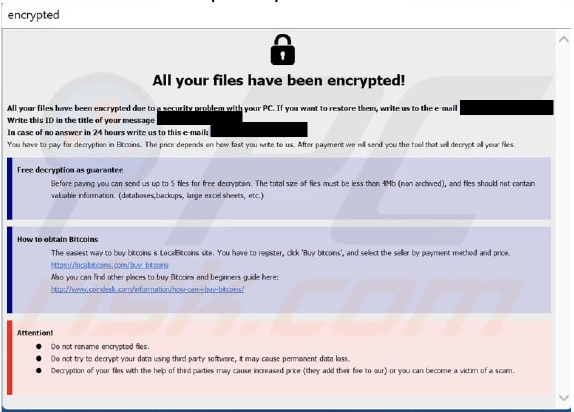
The Blue ransomware’s ransom note informs victims that their files have been encrypted due to a security issue with their computers. To restore access, victims are instructed to pay ransom. The note specifies that payment must be made in Bitcoin, with the amount depending on how quickly victims reach out to the threat actors. Upon payment, victims will receive a decryption tool. Before making the payment, they are allowed to send up to five files (under 4MB) for free decryption. The note strongly cautions against renaming encrypted files or using third-party decryption tools, warning that doing so may lead to data loss or increased decryption costs.
Blue ransomware encrypts both local and network-shared files, disables the firewall, and deletes Volume Shadow Copies to hinder recovery efforts. Additionally, it collects location data and can exclude specific predetermined locations from its attacks.
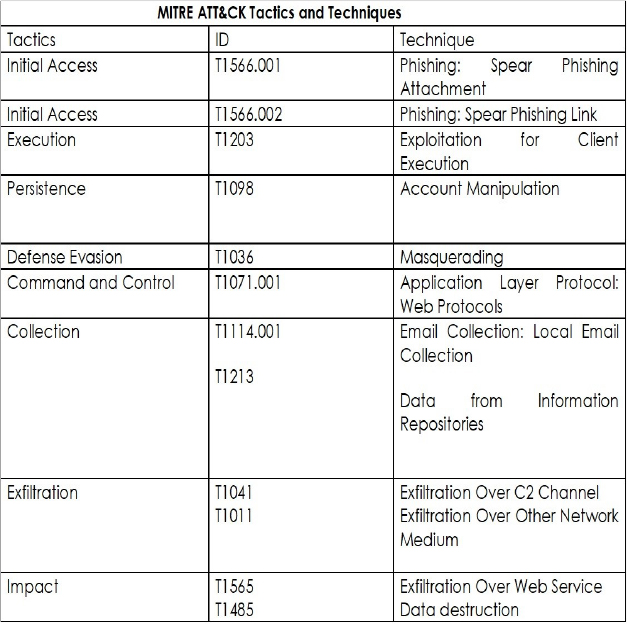
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side – Loading | ||
| 3 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1070: Indicator Removal | ||
| T1112: Modify Registry | ||
| T1134: Access Token Manipulation | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| T1555.003: Credentials from Password Stores: Credentials from Web Browsers | ||
| 6 | TA0007: Discovery | T1012: Query Registry |
| T1016: System Network Configuration Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1518: Software Discovery | ||
| T1614: System Location Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1074: Data Staged | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that Blue ransomware, a variant of the Phobos family, is likely to target economically developed regions such as the US, UK, Southeast Asia, Europe, and others, aiming to maximize ransom demands. Given the historical behavior of Phobos, which has consistently targeted industries like Manufacturing, Finance, FMCG and others due to their data sensitivity and financial capacity to pay significant ransoms, there is medium confidence that Blue ransomware will continue this trend. The ransomware’s advanced capabilities, including disabling firewalls, deleting Volume Shadow Copies, and selectively targeting locations, further indicate its potential to expand globally, affecting various sectors across different regions.
SIGMA Rule:
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Stealer
Objective: Data theft, Data exfiltration
Target Technologies: macOS, Browsers, Cryptocurrency wallets
Active Malware of the Week
This week “BANSHEE Stealer” is trending.
BANSHEE Stealer
Researchers have identified a new macOS-specific malware named BANSHEE Stealer, developed by Russian threat actors and introduced on an underground forum. This sophisticated stealer, designed for both macOS x86_64 and ARM64 architectures, targets critical system information, a wide range of browsers, cryptocurrency wallets, and around 100 browser extensions, making it highly versatile and dangerous. With a notable monthly subscription fee of $3,000, BANSHEE Stealer highlights the growing market for macOS- targeted threats, signaling a concerning trend as macOS continues to gain attention from cybercriminals.
Technical Analysis
The malware examined in this analysis retained all C++ symbols, which is notable because it allows researchers to infer the project’s code structure based on these source code file names. By analyzing the C++-generated global variable initialization functions, they could identify values configured during the build process, such as the remote IP, encryption key, and build ID, either automatically or manually.
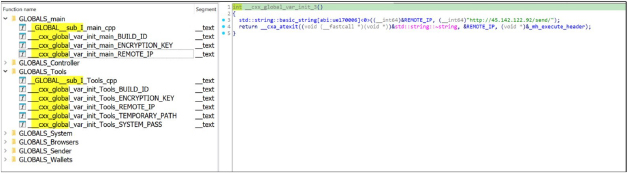
The following lists the leaked .cpp file names identified through the symbols in the binary.
Evasion Techniques
BANSHEE Stealer uses basic techniques to evade detection.
System information collection
User Password – The malware generates an Osascript password prompt that displays a message stating that updating system settings is required to launch the application. It then requests that the user enter their password. It then validates the entered password using the dscl command. If valid, the password is saved to a file (/Users/<username>/password- entered) and can be used to decrypt the keychain data, giving access to all saved passwords.
File, software, and hardware information collection
The `System::collectSystemInfo` function gathers system information and serializes it into a JSON object. using the `system_profiler` command for software and hardware details and obtaining the machine’s public IP from freeipapi.com via macOS’s cURL. The JSON file is saved as `<temporary_path>/system_info.json`. BANSHEE Stealer also executes AppleScripts, writing them to `/tmp/tempAppleScript`. The first script mutes the system sound and then collects various files, including Safari cookies, the Notes database, and files with specific extensions (.txt, .docx, .rtf, .doc, .wallet, .keys, .key) from the Desktop and Documents folders.
Dump keychain passwords – It copies the system keychain file from /Library/Keychains/login.keychain-db to <temporary_path>/Passwords.
Browser collection
BANSHEE collects data, including browser history, cookies, and logins, from 9 different browsers.
For Safari, only cookies are collected by the AppleScript script for the current version. Additionally, data from around 100 browser plugins is gathered. The collected files are stored in `<temporary_path>/Browsers`.
Wallet collection
BANSHEE collects data from various cryptocurrency wallets and saves the gathered information in <temporary_path>/Wallets.
Exfiltration
After collecting data, the malware compresses the temporary folder into a ZIP file using the `ditto` command. The ZIP file is then XOR encrypted, base64 encoded, and sent via a POST request to http[:]//45[.]142[.]122[.]92/send/ using the built-in cURL command.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as macOS gains traction in countries like Japan and South Korea, as well as in the broader region of Southeast Asia, it’s becoming a more appealing target for cybercriminals. Historically, macOS usage in Asia has lagged behind North America and Europe, its growing adoption across various industries is likely to change this dynamic. The rise of threats like BANSHEE Stealer suggests that cybercriminals are beginning to focus on these regions, where macOS is often trusted for its security and reliability. Looking ahead, the increasing macOS user base in Asia, particularly in industries reliant on the operating system, is likely to face elevated risks. As cyber threats evolve, organizations in these areas must proactively strengthen their cybersecurity defenses, anticipating a rise in macOS-targeted attacks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Macos_Infostealer_Banshee { meta:
creation_date = “2024-08-13”
last_modified = “2024-08-13” os = “MacOS”
arch = “x86, arm64” category_type = “Infostealer” family = “Banshee”
threat_name = “Macos.Infostealer.Banshee” license = “Elastic License v2”
strings:
$str_0 = “No debugging, VM, or Russian language detected.” ascii fullword
$str_1 = “Remote IP: ” ascii fullword
$str_2 = “Russian language detected!” ascii fullword
$str_3 = ” is empty or does not exist, skipping.” ascii fullword
$str_4 = “Data posted successfully” ascii fullword
$binary_0 = { 8B 55 BC 0F BE 08 31 D1 88 08 48 8B 45 D8 48 83 C0 01 48 89 45 D8
E9 }
$binary_1 = { 48 83 EC 60 48 89 7D C8 48 89 F8 48 89 45 D0 48 89 7D F8 48 89 75
F0 48 89 55 E8 C6 45 E7 00 }
condition:
all of ($str_*) or all of ($binary_*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Iranian Cyberattacks Targeting Presidential Campaigns
Summary:
APT42, an Iranian state-backed threat actor, is targeting individuals connected to the Harris and Trump Presidential campaigns through spear phishing attacks. In May and June, APT42 attempted to compromise the personal email accounts of about a dozen individuals affiliated with both President Biden and former President Trump, including current and former U.S. government officials. These efforts have resulted in several successful breaches, notably including the Gmail account of a prominent political consultant. APT42 continues to make unsuccessful attempts to breach personal accounts associated with President Biden, Vice President Harris, and former President Trump, reflecting the group’s ongoing focus on military and political figures to advance Iran’s geopolitical objectives. it has been reported that APT42 has significantly increased its cyberattacks against users in Israel since April 2024. These attacks have mainly targeted individuals linked to the Israeli military, defence sector, diplomats, academics, and NGOs. analysis reveals that between February and July 2024, the U.S. and Israel comprised approximately 60% of APT42’s geographic targeting. This surge in activity illustrates the group’s aggressive and adaptable strategy to align its operations with Iran’s political and military objectives. APT42 employs sophisticated and diverse phishing tactics to target users, utilizing methods such as malware, phishing pages, and malicious redirects. The group is known for creating fraudulent accounts and domains that mimic legitimate organizations, including political think tanks, and registering typo squat domains to enhance their credibility. Their phishing efforts often involve sending malicious links directly in emails or through seemingly innocuous PDF attachments. APT42 also uses social engineering to persuade targets to engage via platforms like Signal, Telegram, or WhatsApp, where they distribute phishing kits to capture credentials. These kits are designed to harvest login information from various services, including Google, Hotmail, and Yahoo, and are often delivered using advanced techniques, such as browser-in-the-browser phishing. APT42 meticulously researches target email security settings and uses social media to identify vulnerable addresses, often targeting those without multi-factor authentication (MFA) or other protective measures.
Relevancy & Insights:
APT42, an Iranian state-backed threat actor, has a history of targeting political and military figures to further Iran’s geopolitical goals. Historically, APT42 has been involved in sophisticated phishing campaigns and cyber-espionage operations aimed at gathering intelligence from high-value targets. This includes attacks on military personnel, diplomats, and political figures to undermine adversaries and gain strategic advantage.
In the current incident, APT42’s tactics align with their past behavior. Their recent focus on U.S. Presidential campaigns, including individuals affiliated with President Biden and former President Trump, reflects their ongoing strategy to influence political processes and gather sensitive information. The group’s recent intensified targeting of the Israeli military, defence, and diplomatic sectors further emphasizes their pattern of focusing on high-impact targets that support Iran’s strategic interests. This continuity in targeting high-profile political and military figures is consistent with their previous operations, where they aimed to leverage cyber espionage for geopolitical leverage.
ETLM Assessment:
APT42 reveals a sophisticated and persistent Iranian state-backed threat actor with a strategic focus on political and military targets. APT42 has historically targeted high- value individuals and sectors that align with Iran’s geopolitical interests. Geographically, their focus has spanned across the United States and Israel, with recent intensification in these regions. Their target industries include military, defense, and diplomatic sectors. Technologically, APT42 employs advanced phishing techniques, often leveraging social engineering, fraudulent domains, and malicious redirects to exploit targeted vulnerabilities in email systems. They have utilized various forms of malware in the past, including phishing kits designed to harvest credentials from services like Google, Hotmail, and Yahoo. Current trends indicate a sustained effort to infiltrate sensitive communications and gather intelligence. At the same time, their past use of tools such as browser-in-the-browser phishing kits highlights their evolving approach. Looking forward, APT42’s persistent and evolving tactics suggest an ongoing threat, necessitating heightened vigilance and enhanced cybersecurity measures to counteract their sophisticated attacks and protect against future espionage activities.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers attacking Russia
Chinese hackers have reportedly targeted numerous systems used by government agencies and IT companies in Russia. Researchers identified that the backdoor malware employed in these attacks, known as “GrewApacha,” is a Trojan that has been utilized by the Chinese cyber-espionage group APT31 since at least 2021. APT31 is believed to be connected to China’s civilian intelligence agency, the Ministry of State Security (MSS). Earlier this year, the U.S. Department of Justice indicted several Chinese nationals and a company for allegedly conducting APT31 operations. The hackers carried out these attacks by sending phishing emails with malicious shortcut files as attachments.
ETLM Assessment:
Despite the proclaimed partnership with no limits, Beijing and Moscow do not see eye to eye on many issues and China considers Russia very much a junior partner in the relationship, which is based not on common values but solely on a common interest in undermining the Western-led rules-based order. Chinese state-backed hackers are highly opportunistic and do not respect any boundaries and have been notorious for attacking friends and foes alike. Last year, the intelligence chiefs of the Five Eyes intelligence alliance – the U.S., the U.K., Canada, Australia, and New Zealand – warned of the threat posed by China’s use of cutting-edge technology to carry out hacking and intellectual property theft on a large scale.
The Hunters International Ransomware impacts the Hanon Systems
Summary:
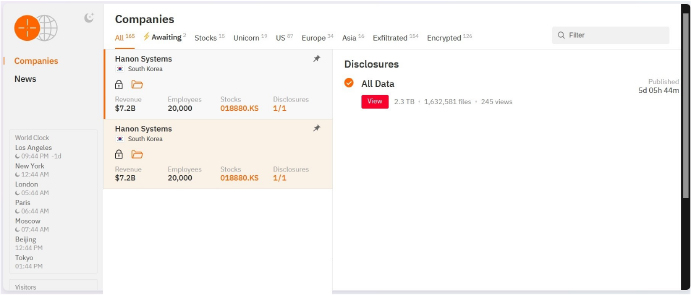
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from South Korea; Hanon Systems (www[.]hanonsystems[.]com), was compromised by the Hunters International Ransomware. Hanon Systems is a global leader in automotive thermal and energy management solutions. Hanon Systems offers a wide range of products and services, including HVAC systems, compressors, thermal and emissions products, and battery thermal management solutions. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. Specifically, the scale of the data exposure measures approximately 2.3 Terabytes, comprising a total of 1,632,581 discrete files.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Hunters International ransomware group is expected to continue targeting a wide range of industries globally, with a particular focus on the United States, Europe, and Asia. A recent attack on Hanon Systems, a leading manufacturing company in South Korea, highlights the significant threat this ransomware poses in the East Asia region. This incident highlights the growing risk to critical industries in the area and the importance of strengthening cybersecurity
Vulnerability in Flatpak
Summary:
The vulnerability allows a local user to escalate privileges on the system.
Relevancy & Insights:
The vulnerability exists due to a symlink following issue when mounting persistent directories.
Impact:
A local user can create a specially crafted symbolic link and escape the sandbox.
Affected Products: https[:]//github[.]com/flatpak/flatpak/security/advisories/GHSA-7hgv-f2j8- xw87
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
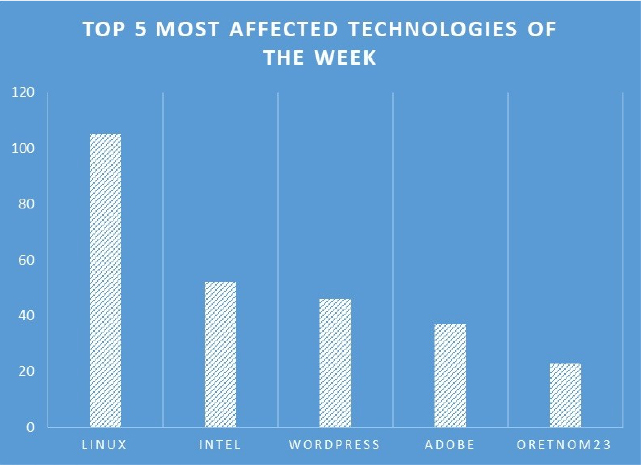
ETLM Assessment:
Vulnerability in Flatpak can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Flatpak is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding software deployment and package management activities, especially within sandboxed environments on Linux systems, across different geographic regions and sectors.
RansomHub Ransomware attacked and Published data of The Investment Dar (TID)
Summary:
Recently we observed that RansomHub Ransomware attacked and published data of The Investment Dar (TID) (www[.]inv-dar[.]com) on its dark web website. The Investment Dar (TID) is a prominent Islamic investment company based in Kuwait. The Investment Dar (TID) operates as a shareholding company, adhering to the principles of Islamic Shariah. It is one of the largest Islamic finance institutions in the MENA (Middle East and North Africa) region, involved in various sectors such as real estate, finance, asset management, and more. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization. The total size of the compromised data is 15GB.
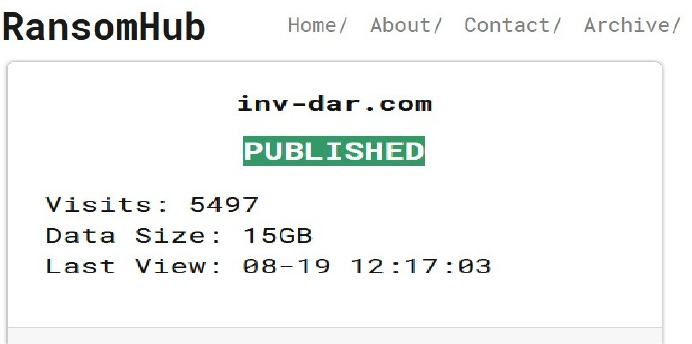
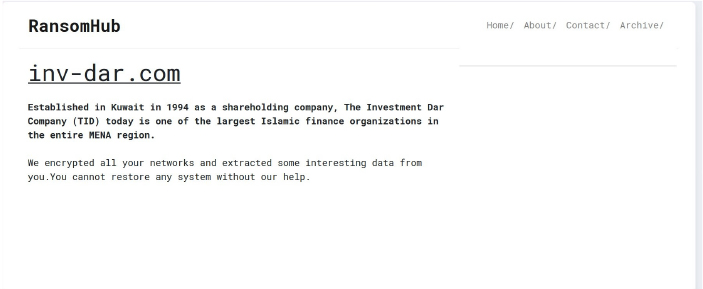
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, RansomHub Ransomware is expected to continue its global targeting across various industries, with a particular focus on the United States, Europe, and Asia. A recent attack on The Investment Dar (TID), a leading finance company in Kuwait, highlights the significant threat this ransomware poses in the Middle East. This incident highlights the broader risk RansomHub presents to organizations worldwide, particularly those in regions with growing cyber threats.
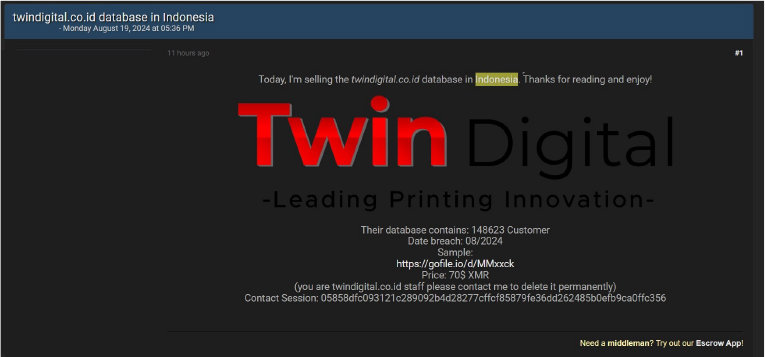
Twin Digital Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Twin Digital (www[.]twindigital[.]co[.]id) in an underground forum. Twin Digital is a digital printing company based in Indonesia that offers a range of products and services tailored to meet the needs of its customers. The data available for sale includes sensitive and confidential information pertaining to 148,623 customers. The asking price for this data is 70$ XMR.
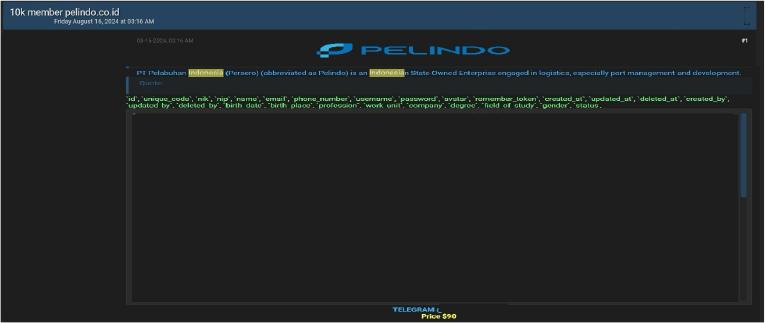
Pelindo(PT Pelabuhan Indonesia ) data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Pelindo(PT Pelabuhan Indonesia ) (www[.]Pelindo[.]co[.]id) in an underground forum. PT Pelabuhan Indonesia (Persero), commonly known as Pelindo, operates within the maritime and port services industry in Indonesia. It is a state-owned enterprise (BUMN) involved in managing and operating ports across Indonesia. Pelindo was formed through the merger of four state-owned port companies (Pelindo I, II, III, and IV), with the aim of optimizing port operations and enhancing Indonesia’s maritime connectivity. The dataset available for sale includes various personal and professional details, such as ID, unique code, NIK (national identification number), NIP (employee identification number), name, email address, phone number, username, password, avatar, and remember token. It also contains timestamps for when the data was created, updated, or deleted, as well as details about who performed these actions. Additional information includes birth date, birthplace, profession, work unit, company, academic degree, field of study, gender, and status. The asking price for this data is $90. The data breach has been attributed to a threat actor identified as “doxbit3306”.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s assessment, the threat actor known as “doxbit3306” poses a serious risk to organizations due to its financial motivations and ability to exploit vulnerable institutions. This actor is notorious for infiltrating organizations with weak security measures and profiting by selling stolen sensitive data on the dark web or underground forums. The typical targets of “doxbit3306” are institutions with inadequate cybersecurity defenses, making them particularly susceptible to the sophisticated cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data leak related to a South Korean career platform. A threat actor has allegedly breached the database of career.go.kr, a prominent South Korean career platform, compromising the personal information of 1.6 million users. The breach, purportedly carried out by “IntelBroker” and “EnergyWeaponUser”, has exposed a wide range of sensitive data, including usernames, encrypted passwords, contact information, career details, and more. The data was reportedly obtained in August 2024, with the threat actor claiming that the information was secured using Base64(md5) hashing.
According to the threat actor, the compromised data includes user details, such as member numbers, job codes, educational backgrounds, and login information, among other critical personal identifiers. The alleged breach has raised serious concerns about the security measures in place on the platform, as the exposure of such information could lead to identity theft, fraud, and other malicious activities.
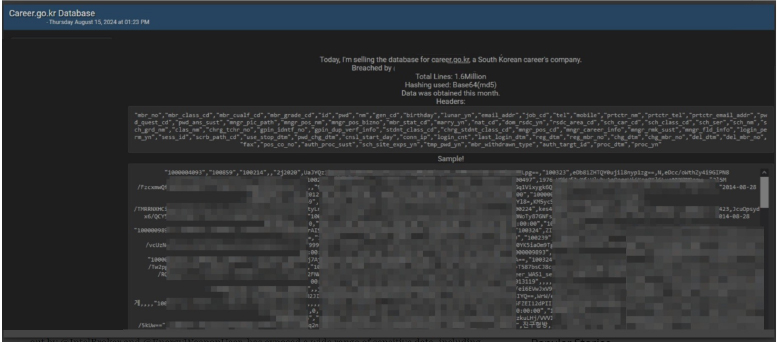
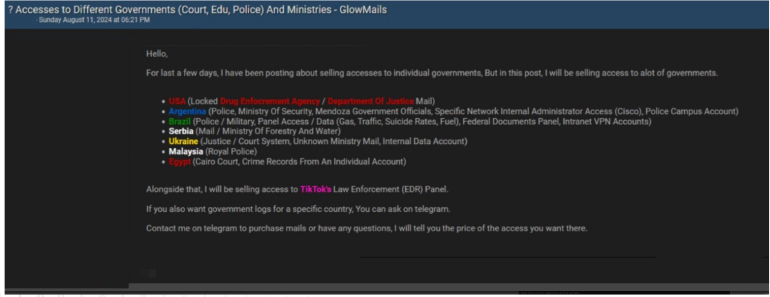
The CYFIRMA Research team observed a potential access sale related to government systems and ministries across several countries. A threat actor has made a bold claim of having unauthorized access to a variety of government systems and ministries across several countries. The actor alleges that they can provide access to sensitive databases and internal networks of major institutions, including:
USA: Locked access to the Drug Enforcement Agency (DEA) and the Department of Justice’s email systems.
Argentina: Access to police systems, the Ministry of Security, and internal government networks.
Brazil: Military, police, federal documents panels, and Intranet VPN accounts. Serbia: Ministry of Forestry and Water and email systems.
Ukraine: Court system and unknown ministry emails. Malaysia: Royal Police systems.
Egypt: Cairo Court and crime records.
In addition, the threat actor is offering access to TikTok’s Law Enforcement (EDR) Panel, which handles sensitive information requests from law enforcement agencies. The actor is inviting interested buyers to reach out via Telegram to negotiate prices and discuss specific government logs or access requirements.
ETLM Assessment:
The “IntelBroker” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
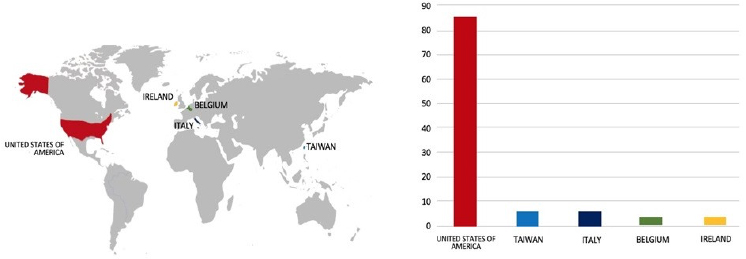
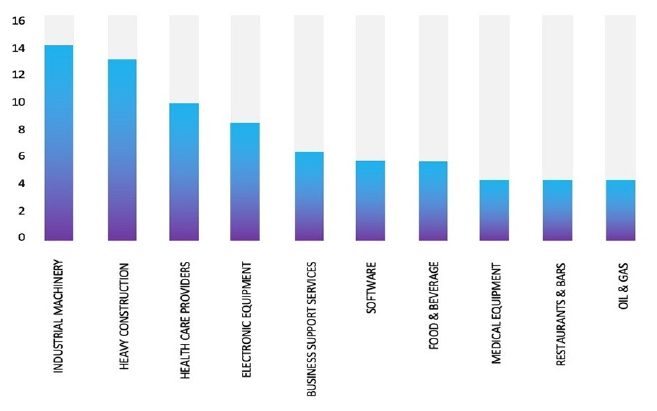
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.