



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found FIOI Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
FIOI Ransomware
Researchers have uncovered FIOI, a new ransomware variant from the Makop family. FIOI encrypts files and appends the “.FIOI” extension, random characters, and an email address to filenames. It also modifies the desktop wallpaper and generates a ransom note titled “+README-WARNING+.txt”.
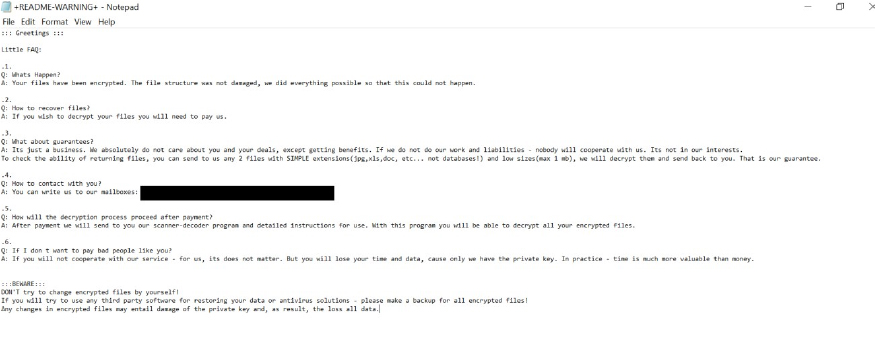
FIOI’s ransom note informs victims that their files have been encrypted. To restore access, victims are instructed to pay a ransom. As proof of their decryption capability, attackers offer to decrypt two small files.
The note provides two contact email addresses through which victims can communicate with the attackers and receive the decryption tool after payment. Additionally, it warns that non-cooperation or attempts to use third-party decryption tools may lead to irreversible data loss.
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job |
| T1059.003: Command and Scripting Interpreter: Windows Command Shell | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027.002: Obfuscated Files or Information: Software Packing |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 6 | TA0009: Collection | T1115: Clipboard Data |
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 8 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
According to the assessment from CYFIRMA, Makop ransomware has been targeting industries including software, IT, finance, and others globally. This new variant is anticipated to concentrate on these sectors due to their lucrative financial opportunities. Cybercriminals will likely exploit these industries’ vulnerabilities to disrupt operations, steal sensitive data, and demand substantial ransoms. This highlights the critical need for enhanced defensive measures to protect these high-value sectors from potential ransomware attacks.
Sigma Rule
title: Delete shadow copy via WMIC status: experimental
threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information stealer | Objectives: Information stealing, Data Exfiltration | Target Technologies: Windows OS, Browsers, VPN Clients, Cryptocurrency Wallets, Gaming Software, FTP Clients, Messaging Platforms | Target Industries: Government & Education Sector | Target Geographies: Europe (Sweden, Denmark) & Asia (India)
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “PXA Stealer” is trending.
PXA Stealer
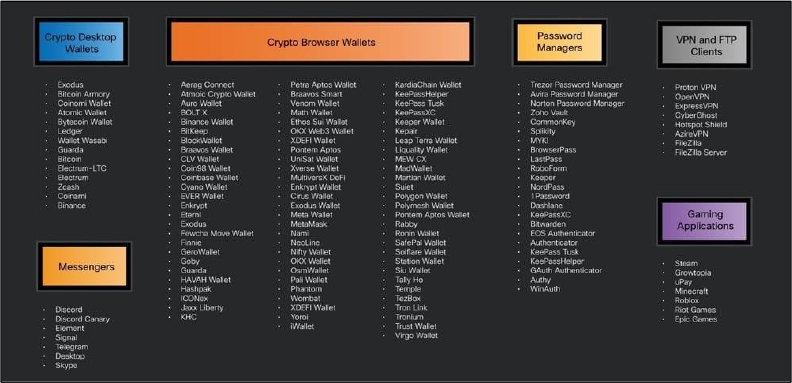
Researchers have identified PXA Stealer, a Python-based malware, as part of a new information-stealing campaign led by a Vietnamese-speaking threat actor focusing on government organizations in Europe, including Sweden and Denmark, and the education sector in India. PXA Stealer is designed to steal sensitive information such as login credentials, browser data, credit card details, cryptocurrency wallet information, and data from VPN clients, gaming software, chat messengers, and FTP clients. The malware demonstrates advanced capabilities, including decrypting browser master passwords, and employs sophisticated obfuscation techniques in its scripts to evade detection.
Attack Method
The attacker initiates the campaign through phishing emails containing a ZIP file attachment. This ZIP file includes a malicious Rust-based loader executable, and a hidden folder named Photos, which houses obfuscated Windows batch scripts and a decoy PDF document.
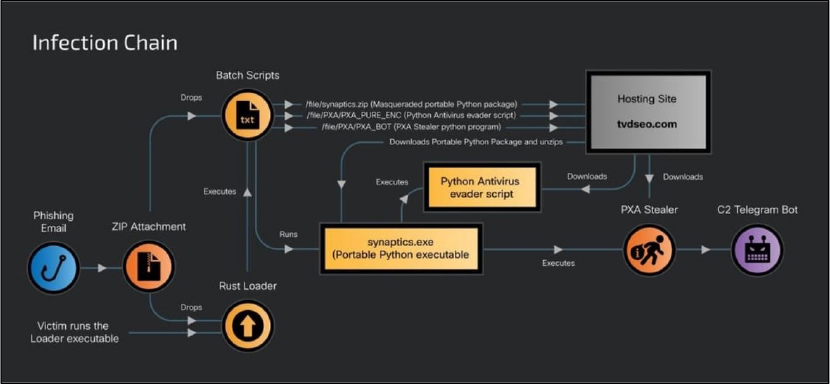
When victims extract the ZIP file, the hidden folder and loader executable are dropped onto their systems. When executable runs, it triggers the execution of multiple obfuscated batch scripts from the hidden folder. Researchers successfully deobfuscated these scripts through a meticulous process, employing regular expressions to filter out random characters and special symbols. By systematically removing obfuscation layers, they uncovered PowerShell commands embedded in the scripts, revealing the malware’s functionality. The batch scripts execute PowerShell commands simultaneously, carrying out following activities on the victim machine:

They first open a decoy PDF document of a Glassdoor job application form and then download a portable Python 3.10 package masquerading as “synaptics.zip” from an attacker-controlled domain, saving it in both the user’s temporary and public folders with random filenames before extracting it. The scripts create and run a Windows shortcut file named “WindowsSecurity.lnk,” which contains a base64-encoded command and is configured to run via the “Run” registry key, ensuring persistence. This shortcut file executes a Python script that downloads a base64-encoded program designed to disable antivirus software. The batch script then downloads and executes the PXA Stealer Python program using the disguised portable Python executable “synaptics.exe.” Additionally, a batch script named “WindowsSecurity.bat” is dropped into the Windows startup folder to maintain persistence and facilitate the execution of PXA Stealer.
Technical Analysis
PXA Stealer is a Python-based malware with extensive capabilities designed to target various types of sensitive data on the victim’s machine. Upon execution, it terminates a range of processes from a hardcoded list, including endpoint detection software, VPN clients, cryptocurrency wallet applications, file transfer clients, and web browser and messaging processes, using “task kill” commands. The malware also decrypts the browser master key, a cryptographic key used by browsers like Google Chrome to protect sensitive data. By accessing the “Local State” file in the user’s browser profile, which contains the encryption key for stored data, and using the “CryptUnprotectData” function, PXA Stealer decrypts the master key. This enables the attacker to retrieve stored credentials, cookies, and other sensitive browser information.
PXA Stealer also tries to decrypt the master key stored in the key4.db file, a database used by Firefox and other Mozilla-based browsers to store encryption keys, including those that protect sensitive data like saved passwords. The stealer uses the “getKey” function to extract and decrypt keys from the key4.db file, utilizing either AES or 3DES encryption methods, depending on the encryption type. It also retrieves user profile paths from the profiles.ini file of various browsers, including Firefox, Pale Moon, SeaMonkey, and others, to further extract saved passwords and other sensitive user data. PXA Stealer collects extensive login and personal data from the victim’s browser. It extracts login credentials—URLs, usernames, and passwords—from the browser’s “login_db” file using the “get_ch_login_data” function. If the URL matches any hardcoded keywords, the login information is saved in a file named “Important_Logins.txt,” while all other login data is stored in “All_Passwords.txt.” The stealer also extracts and decrypts cookies from the browser’s cookie database through the “get_ch_cookies” function, saving the results in browser-specific text files. If Facebook cookies are found, they are processed and stored in “Facebook_Cookies.txt.”
The malware also steals credit card information stored in the “webappsstore.sqlite” database, extracting details like card number, expiration date, and name on the card. It decrypts this data using the master key and stores it in a text file. Autofill form data is extracted and saved in browser-specific files. Additionally, PXA Stealer targets Discord tokens, searching for encrypted or unencrypted tokens stored in browser and Discord application files. Once found, the tokens are decrypted and validated, and the valid ones are stored with the associated browser name.
PXA Stealer expands its data theft capabilities by targeting the MinSoftware application database, searching for “db_maxcare.sqlite” across common directories and logical drives. Once located, it extracts sensitive user information, including IDs, passwords, email credentials, cookies, tokens, and account details. Additionally, it leverages Facebook Ads Manager and Graph API by authenticating sessions through stolen cookies to access ad account data, page details, and Business Manager IDs, while extracting session tokens for authenticated requests. After harvesting comprehensive data, including browser credentials, cookies, credit card details, Discord tokens, cryptocurrency wallets, and MinSoftware records, the stealer compresses the stolen files into a ZIP archive labeled with the victim’s public IP and device name. The archive excludes specific directories to optimize the process, renames files, and exfiltrates the package to the attacker’s Telegram bot. To cover its tracks, the stealer deletes all folders containing the stolen data post-exfiltration.
A Vietnamese Threat Actor’s Operations
Researchers discovered that the attacker used the domain tvdseo[.]com, associated with a Vietnamese SEO service provider, to host malicious scripts and the stealer program. It remains unclear if the domain was compromised or accessed legitimately for malicious purposes. The attacker uses Telegram bots for exfiltrating stolen data, with bot tokens and chat IDs embedded in the stealer. Further investigation revealed the attacker’s Telegram account, “Lone None,” featuring symbols of Vietnam and a private antivirus checker link, suggesting a high level of sophistication and Vietnamese origins.
The attacker is active in underground Telegram groups like “Mua Bán Scan MINI” and “Cú Black Ads – Dropship,” engaging in activities such as selling stolen credentials, social media accounts, SIM cards, and money laundering data. Tools shared in these groups include batch account creators, cookie modification tools, and email mining utilities, often bundled with source codes for customization. Some tools require activation keys, ensuring controlled distribution among vetted users. Beyond Telegram, these tools are marketed on platforms like aehack[.]com and accompanied by YouTube tutorials, highlighting the organized efforts to promote and educate users on deploying them.
While connections to other Vietnamese cybercrime groups like CoralRaider are observed, affiliations remain uncertain. This activity underscores a well-coordinated operation blending technical sophistication and underground community engagement.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that PXA Stealer is likely to continue evolving, with its impact spreading across both individuals and organizations. As cybercriminals refine their techniques, this malware is expected to target a broader range of industries and geographies. The malware’s ability to bypass traditional security measures and exfiltrate data through encrypted communication channels like Telegram increases the risk of prolonged attacks, making detection and mitigation more challenging. With the continued rise of digital platforms and remote work, organizations may face greater exposure to breaches, resulting in potential financial losses, regulatory scrutiny, and long-term reputational damage. Additionally, as cybercriminals improve their operational tactics, victims may experience more sophisticated follow-up attacks, further complicating recovery efforts and escalating the overall threat landscape.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Stealth Tactics of APT Lazarus Group: Bypassing Detection through Extended Attributes
SUMMARY
A new malware technique used by APT Lazarus Group involves smuggling malicious code within custom extended attributes (EAs) on macOS systems to conceal and execute malicious code, a technique known as code smuggling. Extended attributes are metadata associated with files or directories that can hold additional information beyond standard file properties. These attributes are not visible in Finder or the Terminal by default, however, they can be accessed via the xattr command. The malware, identified as RustyAttr, is developed using the Tauri framework, which allows for the creation of lightweight desktop applications with a web frontend (HTML, CSS, JavaScript) and a backend in Rust. The malicious application fetches and executes a shell script stored in an extended attribute named “test” from the file itself. When the application is run, it checks for the presence of this attribute: if the attribute exists, the script is executed without displaying a user interface; if absent, a decoy webpage or dialog is shown to mislead the user. The malicious payload is downloaded and executed through a sequence involving a WebView that loads an HTML template with an embedded JavaScript file, preload.js. This script invokes backend functions in Rust, specifically calling the get_application_properties API to retrieve the malicious script stored in the file’s extended attribute and then running it via run_command. The applications were originally signed with a leaked certificate, but the certificate was revoked by Apple, leaving the files unnotarized. Despite this, the files remain undetected by antivirus tools, likely because the malicious code is hidden in the extended attributes, bypassing signature-based detection.
Additionally, macOS Gatekeeper, which prevents unsigned applications from running, can be bypassed by users who manually override the security settings. This technique of hiding code within extended attributes is a new method for evading traditional detection mechanisms and is associated with the APT Lazarus Group, though attribution is only moderately confident. The attack appears to be part of an ongoing experimentation by Lazarus to refine its malware for future campaigns, with potential use of code signing, notarization, and advanced evasion tactics.
Relevancy & Insights:
Lazarus Group has a history of high-profile attacks, carrying out numerous financial heists targeting banks and cryptocurrency exchanges. Their past tactics often involved exploiting system vulnerabilities, using sophisticated malware, and leveraging social engineering techniques.
In the RustyAttr attack, Lazarus Group has evolved its methods by hiding malicious code within macOS extended attributes, a novel approach to evade traditional detection mechanisms. This mirrors their earlier use of RustBucket malware, which also targeted cryptocurrency and financial assets.
Similar to past operations, the threat actor employs social engineering tactics, such as using decoy files related to investment and cryptocurrency, to trick users into bypassing security protections. The use of the Tauri framework to develop lightweight, cross- platform applications further reflects Lazarus’ trend of refining their tools for better stealth and evasion. The RustyAttr attack aligns with their longstanding focus on financial and geopolitical targets, while also showcasing their adaptability and continued evolution of cyberattack techniques.
ETLM Assessment:
Lazarus Group, a North Korean state-sponsored cyber espionage group, is known for its sophisticated attacks, often targeting financial institutions, critical infrastructure, and government agencies globally, with a strong focus on South Korea, the U.S., and Japan. The threat actor is continuously evolving its tactics, using novel techniques like code smuggling via extended attributes (EAs) on macOS to bypass traditional security mechanisms. Lazarus leverages the Tauri framework to create lightweight, cross- platform applications, combining JavaScript with a Rust backend to execute payloads hidden in file metadata. Historically, the threat actor has targeted multiple industries predominantly finance (especially cryptocurrency), defense, and technology, and it has used various malware strains, including RustBucket and WannaCry, to steal financial assets and conduct espionage. In this latest campaign, they exploited social engineering, including deceiving users into disabling macOS Gatekeeper protections, and used decoy files related to investment and finance. With its ability to adapt quickly, Lazarus Group will likely continue refining its evasion tactics, potentially expanding its targeting to other platforms and increasing its focus on critical infrastructure. The threat actors’ ongoing use of legitimate tools and infrastructure to mask their activities, combined with its growing sophistication, suggests an evolving and persistent threat that will require continuous defense innovations.
Strategic Recommendations
Focus on Endpoint Detection and Response (EDR) and File Integrity Monitoring: As Lazarus Group has shown the ability to leverage new delivery methods (like macOS extended attributes), it is crucial to implement robust EDR solutions that provide deep visibility into endpoint activity. The ability to detect unusual file modifications, access to extended attributes, and unusual application behaviors will be key in identifying covert malware like RustyAttr. In addition, ensure that file integrity monitoring (FIM) is in place to track unauthorized changes to file systems, especially those that are not immediately visible through traditional file paths.
Tactical Recommendations
Operational Recommendations
Future Considerations
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique / Sub technique |
| Execution | T1059.002 | Command and Scripting Interpreter: AppleScript |
| Execution | T1059.004 | Command and Scripting Interpreter: Unix Shell |
| Defense Evasion | T1564 | Hide Artifacts |
| Command and Control | T1105 | Ingress Tool Transfer |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers targeting US telecoms
The US FBI and the Cybersecurity and Infrastructure Security Agency (CISA) have confirmed that Chinese government hackers conducted a “broad and significant cyber espionage campaign” that compromised several US telecom companies. Media reported last month that the breached companies include AT&T, Lumen, and Verizon. The hackers targeted systems used by the Federal government to carry out court-authorized network wiretapping requests.
The U.S. authorities have identified that PRC-affiliated actors have compromised networks at multiple telecommunications companies to enable the theft of customer call records data, the compromise of private communications of a limited number of individuals who are primarily involved in government or political activity, and the copying of certain information that was subject to U.S. law enforcement requests pursuant to court orders. We expect our understanding of these compromises to grow as the investigation continues.
ETLM Assessment:
The campaign seems to be a classic state-driven espionage with many similar campaigns like it probably underway at the same time. The Chinese government was probably intending to piggyback on domestic wiretapping efforts in order to gain intelligence that would be usable in blackmailing U.S. nationals into cooperating with Chinese intelligence agencies.
Iranian hackers targeting the aerospace industry
A subgroup of the Iranian threat actor Charming Kitten has been leveraging fake job offers to deliver malware, specifically targeting individuals in the aerospace sector, according to researchers. Interestingly, some security firms initially identified the malware files as linked to North Korea’s Lazarus Group. ClearSky suggests this could mean that either Charming Kitten is mimicking Lazarus to conceal its activities, or that North Korea and Iran have shared tools and attack methods.
The Charming Kitten subgroup, designated “TA455,” employs fraudulent recruitment websites and LinkedIn profiles to distribute the SnailResin malware. The group’s infrastructure and campaign patterns align with previous Iranian state-sponsored efforts but have evolved to evade current security defenses, utilizing sophisticated techniques to maintain persistence within targeted networks.
ETLM Assessment:
Iran’s international pariah status stemming from its aggressive power projection in the region means its economy is heavily sanctioned, with possible further sanctions coming under the new Trump administration. Iran is among world leaders in terms of using cyber warfare as a tool of statecraft. Iranian hackers have been repeatedly successful in gaining access to emails from an array of targets, including government staff members in the Middle East and the US, militaries, telecommunications companies, or critical infrastructure operators. The malware used to infiltrate the computers is increasingly more sophisticated and is often able to map out the networks the hackers had broken into, providing Iran with a blueprint of the underlying cyberinfrastructure that could prove helpful for planning and executing future attacks. This effort seems to be aimed at industrial intellectual property that Tehran intends to steal, as it is the only way it can obtain it.
The KillSec Ransomware impacts Dragon Capital
Summary
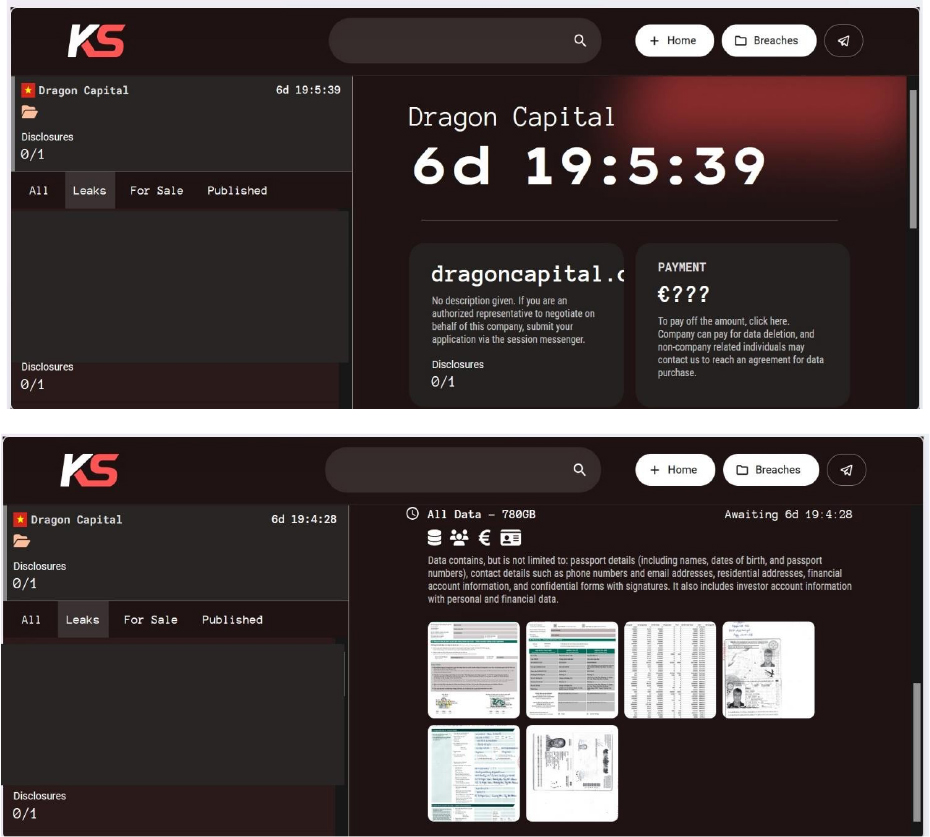
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Vietnam; Dragon Capital (www[.]dragoncapital[.]com[.]vn), was compromised by KillSec Ransomware.
Dragon Capital Group is a prominent investment management firm focused on Vietnam and Southeast Asia. The group offers a diverse range of investment products, including equity funds, fixed-income funds, and segregated accounts, with a strong emphasis on sustainability and ESG (Environmental, Social, and Governance) principles. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data contains passport details (including names, dates of birth, and passport numbers), contact details such as phone numbers and email addresses, residential addresses, financial account information, and confidential forms with signatures. It also includes investor account information with personal and financial data. The total size of compromised data is approximately 780 GB.
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
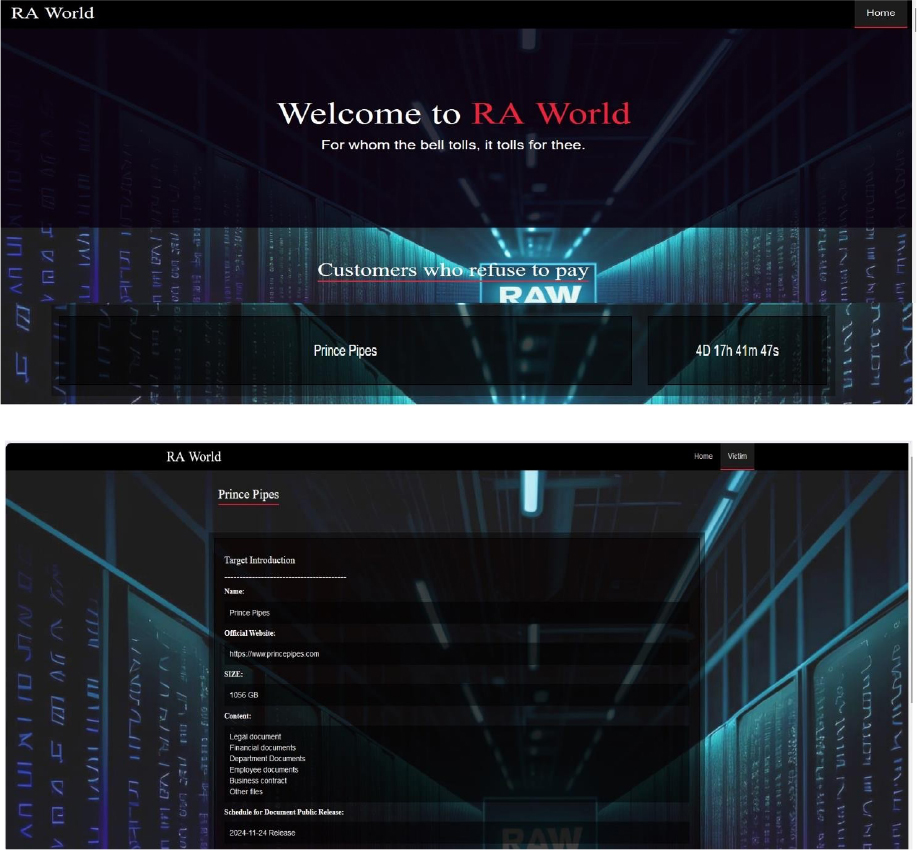
The RaWorld Ransomware Impacts Prince Pipes
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; Prince Pipes (www[.]princepipes[.]com) was compromised by RaWorld Ransomware. Prince Pipes and Fittings Limited, based in India, is a leading manufacturer specializing in polymer- based piping systems and fittings. Its product range includes CPVC, UPVC, PPR, HDPE, and LLDPE pipes and fittings, designed to serve a variety of industries, such as plumbing, agriculture, sewerage, and industrial applications. Additionally, the company produces water storage tanks and advanced solutions for surface and underground drainage systems, meeting diverse infrastructure and utility needs. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data contains Legal documents, Financial documents, Department documents, Employee documents, Business contracts, and other files. The total size of compromised data is approximately 1056 GB.
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RA World ransomware represents a growing threat in the cyber landscape, characterized by its sophisticated tactics and aggressive extortion strategies. Organizations are urged to enhance their cybersecurity measures, including regular updates, employee training on phishing awareness, and robust incident response plans to mitigate risks associated with this evolving threat actor. As their activities continue to expand, vigilance will be essential for organizations across various sectors.
Vulnerability in Palo Alto Networks PAN-OS
Relevancy & Insights:
The vulnerability exists due to a NULL pointer dereference error.
Impact:
A remote attacker can send specially crafted packets to the device and crash the GlobalProtect service.
Affected Products:
https[:]//security[.]paloaltonetworks[.]com/CVE-2024-2550
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
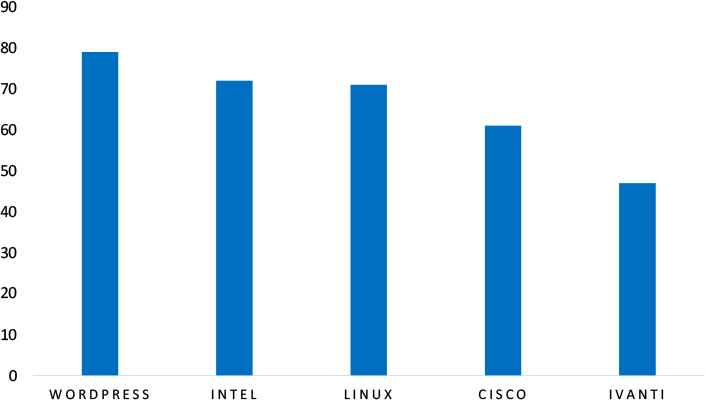
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
TOP 5 MOST AFFECTED TECHNOLOGIES OF THE WEEK
ETLM Assessment
Vulnerability in PAN-OS, the software powering Palo Alto Networks’ next-generation firewalls, can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of PAN-OS is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding firewall operations, including application identification, user identification, and threat prevention, across different geographic regions and sectors.
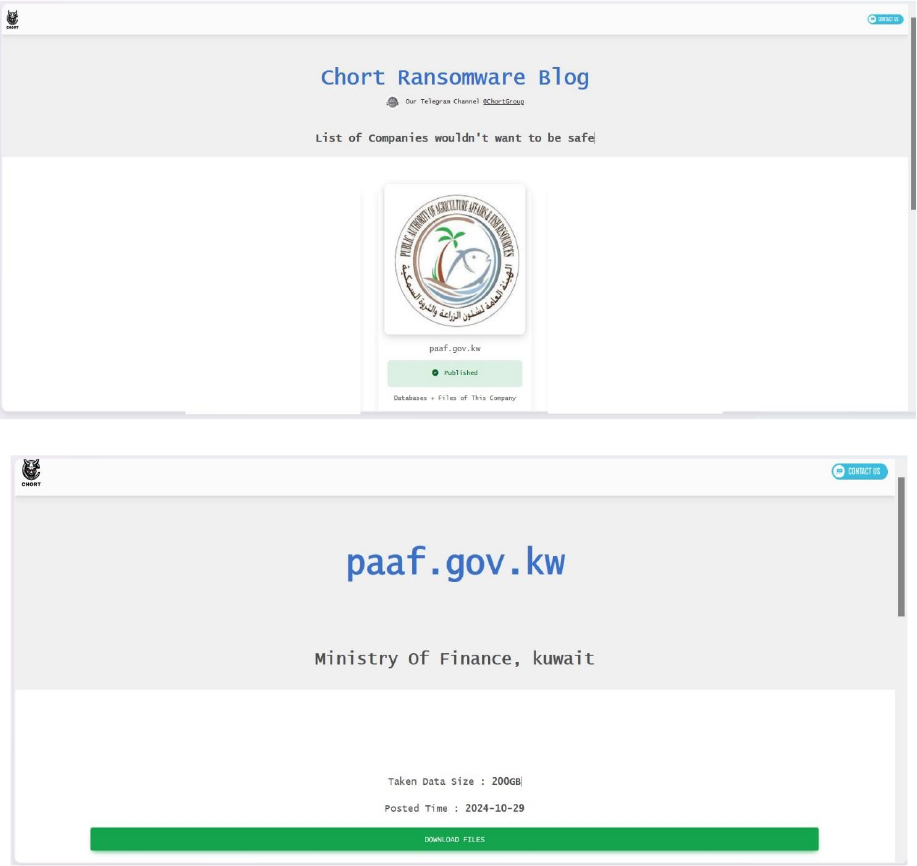
Chort Ransomware attacked and published the data of the Public Authority for Agriculture Affairs and Fish Resources (PAAF) Kuwait
Summary
Recently, we observed that Chort Ransomware attacked and published the data of Public Authority for Agriculture Affairs and Fish Resources (PAAF) Kuwait (www[.]paaf[.]gov[.]kw) on its dark web website. The Public Authority for Agriculture Affairs and Fish Resources (PAAF) is a government agency in Kuwait responsible for managing and promoting the development of agriculture and fisheries. It plays a significant role in enhancing food security, ensuring sustainable resource utilization, and supporting Kuwait’s environmental and economic objectives. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The scale of the data exposure measures approximately 200GB.
Relevancy & Insights:
ETLM Assessment:
Chort Ransomware represents a significant threat within the current cyber threat landscape, characterized by its aggressive tactics and focus on double extortion. Organizations are urged to enhance their cybersecurity defenses against such threats by implementing robust security measures, conducting regular vulnerability assessments, and training employees on recognizing phishing attempts. As the situation evolves, ongoing vigilance will be necessary to mitigate risks associated with this emerging ransomware group.
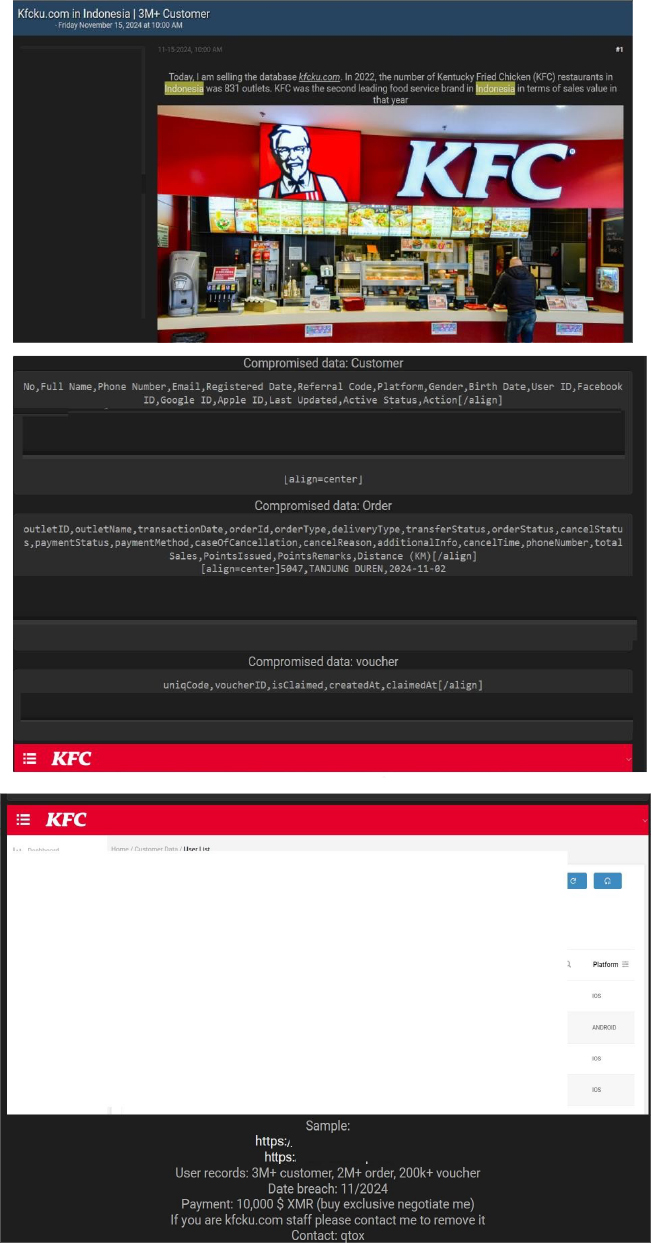
Kentucky Fried Chicken (KFC) Indonesia Data Advertised on a Leak Site
Summary
The CYFIRMA Research team observed a potential data sale related to Kentucky Fried Chicken (KFC)Indonesia (https[:]//kfcku[.]com) in an underground forum.
KFC Indonesia, operated by PT Fast Food Indonesia Tbk, serves as the exclusive franchisee of the KFC brand in the country. The platform provides customers with access to KFC’s menu, promotional offers, and convenient options for ordering, including delivery, drive-thru, and takeout services. The website reflects KFC’s dedication to delivering high-quality food and excellent service, fostering strong engagement with its Indonesian customer base.
A reported data breach of KFC Indonesia’s system exposed sensitive customer information. The leaked database includes details such as customer numbers, full names, phone numbers, email addresses, registration dates, referral codes, platforms used, gender, birthdates, user IDs, and linked accounts (e.g., Facebook, Google, and Apple IDs). It also contains status updates and other confidential records. The data breach has been attributed to a threat actor identified as “Thaihub”. The asking price for the compromised data has been set at $10,000 in Monero (XMR).
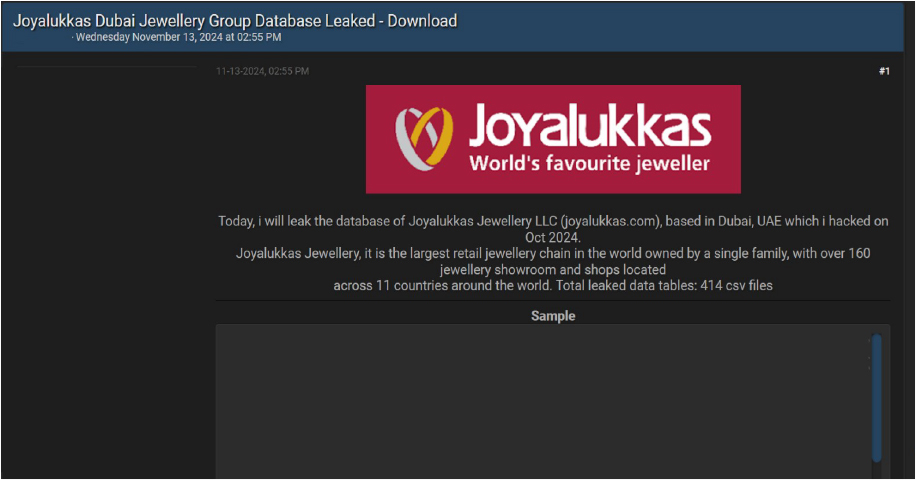
Joyalukkas Data Advertised on a Leak Site
Summary:
A data breach has exposed the database of Joyalukkas, a prominent Dubai (United Arab Emirates)-based jewelry group. The leaked database, now circulating on the dark web, contains sensitive customer and business information, raising concerns about identity theft, fraud, and the misuse of financial data. This breach highlights the need for stronger cybersecurity in high-value industries like jewellery and luxury goods. The data breach has been attributed to a threat actor identified as “0mid16B”.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat actor “Thaihub” represents a notable threat within the cybersecurity landscape. Organizations are advised to strengthen their cybersecurity measures, including regular updates and employee training on recognizing phishing attempts, to mitigate risks associated with this emerging threat actor. Continuous monitoring and intelligence sharing will be essential for understanding and countering the activities of Thaihub and similar groups.
Recommendations: Enhance the cybersecurity posture by:
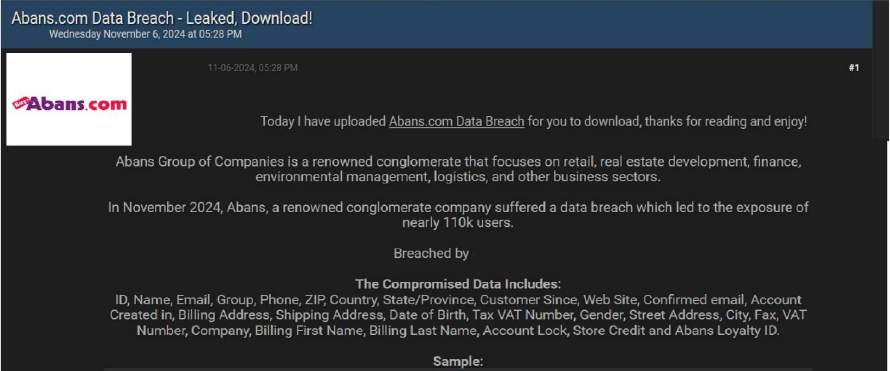
The CYFIRMA Research team observed a potential data leak related to the Abans Group of Companies in an underground forum. Abans Group of Companies is a renowned conglomerate that focuses on retail, real estate development, finance, environmental management, logistics, and other business sectors. The Compromised Data contains ID, Name, Email, Group, Phone, ZIP, Country, State/Province, Customer Since, Web Site, Confirmed email, Account Created in, Billing Address, Shipping Address, Date of Birth, Tax VAT Number, Gender, Street Address, City, Fax, VAT Number, Company, Billing First Name, Billing Last Name, Account Lock, Store Credit, and Abans Loyalty ID. The data breach has been attributed to a threat actor identified as “888”.
ETLM Assessment
The “888” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted the Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, and Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
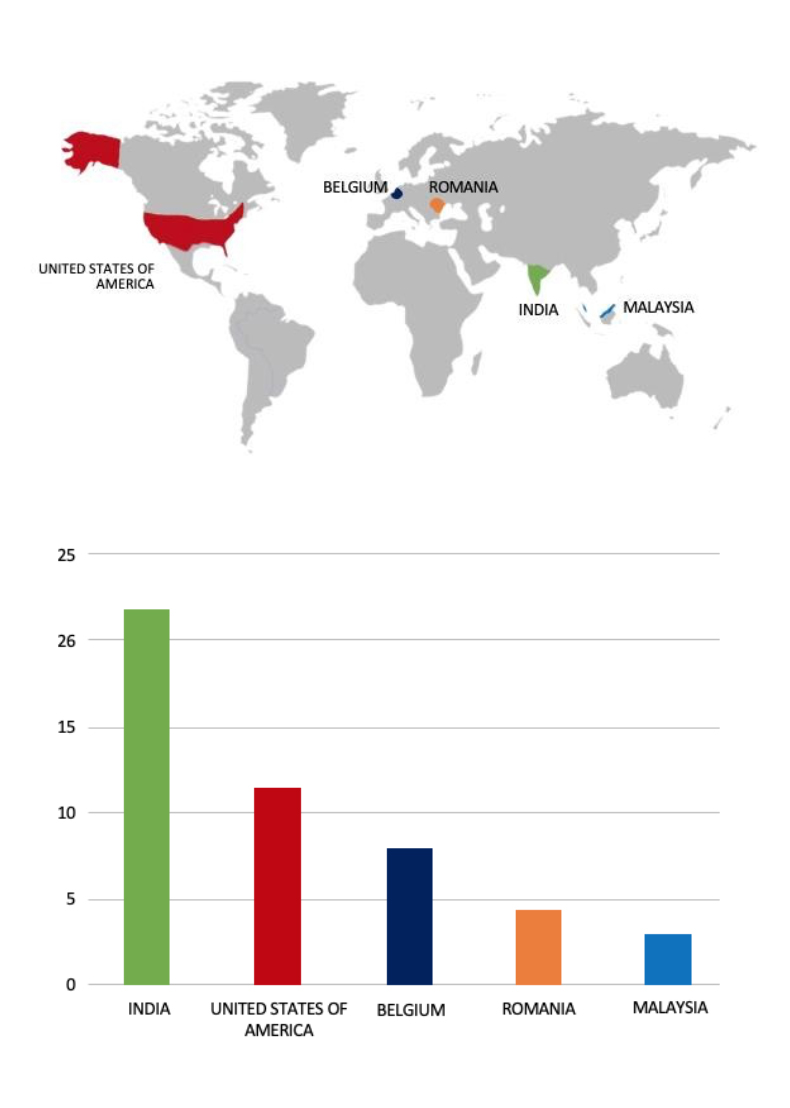
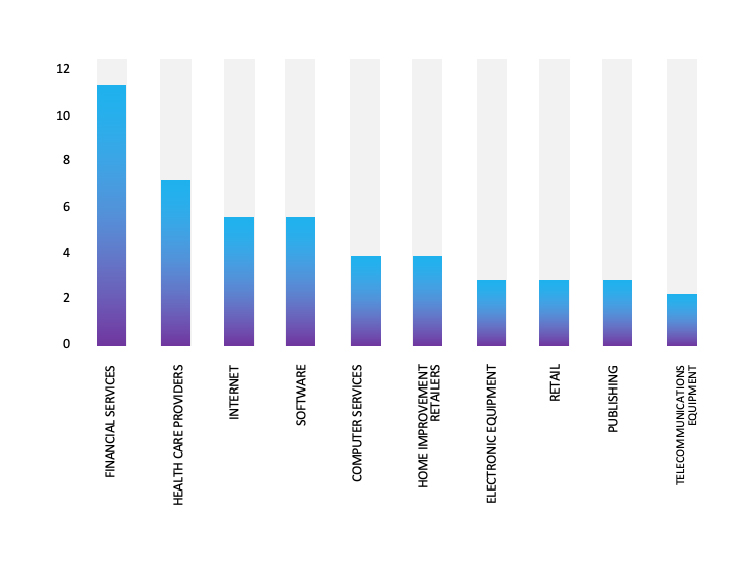
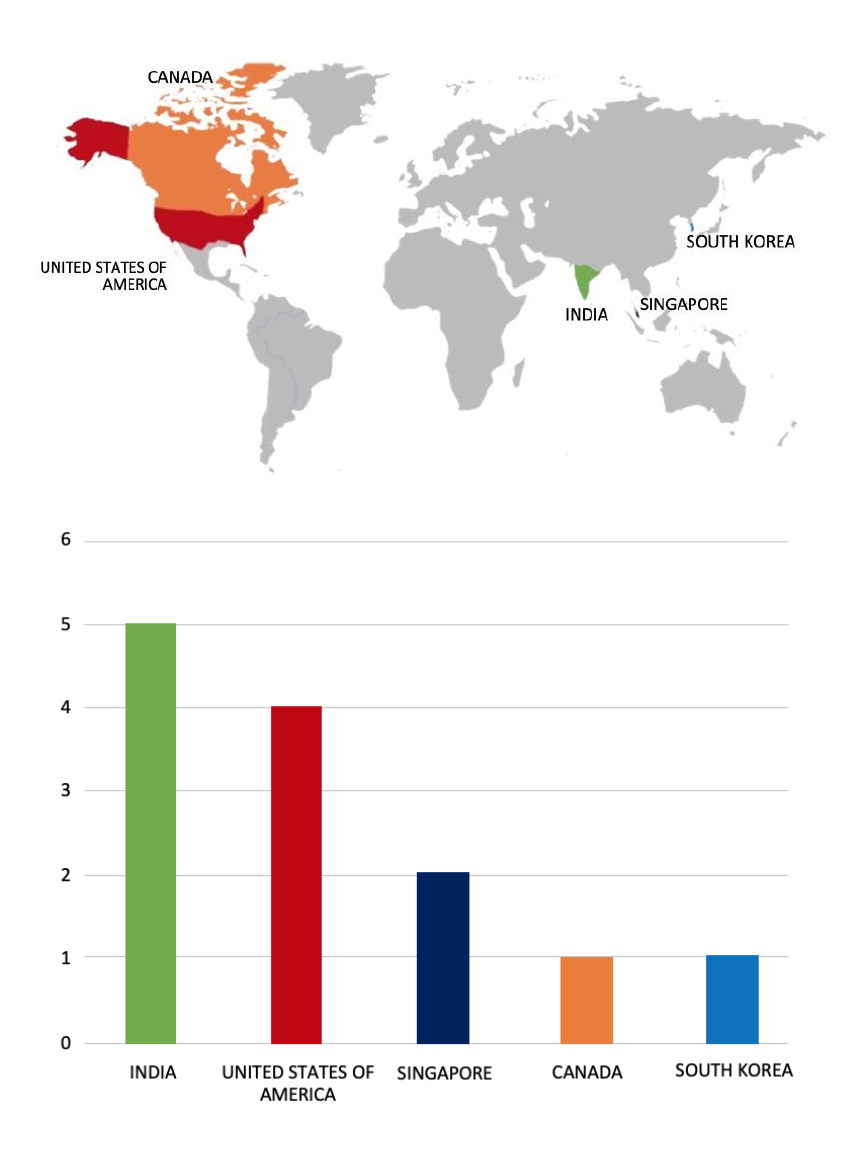
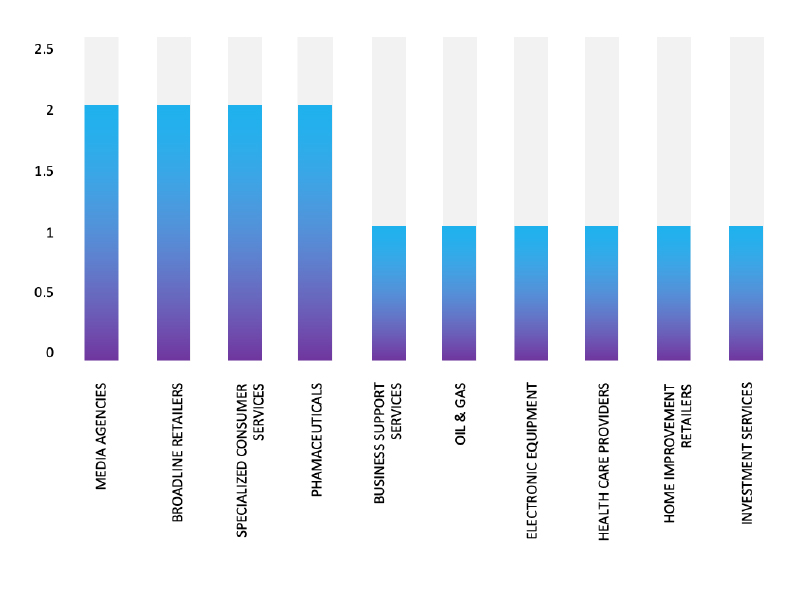
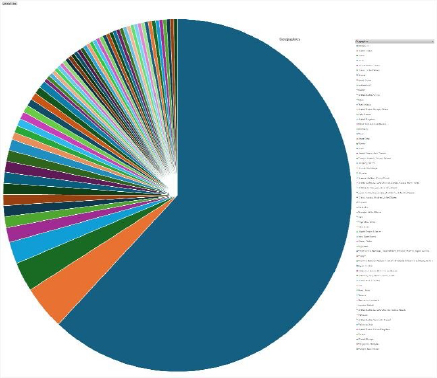
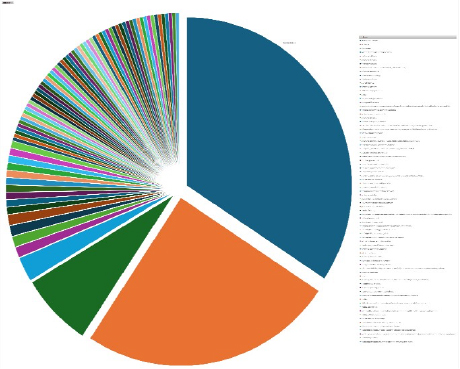
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.