



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found Wing ransomware as a service while monitoring various underground forums as part of our Threat Discovery Process.
Wing ransomware
Wing ransomware was discovered in the wild at the end of January 2024, coinciding with the launch of their Ransomware-as-a-Service (RaaS) platform during the same month.

Screenshot of a hacker forum post seeking partners for Wing ransomware (Source: Surface Web)
Researchers discovered and tested a ransomware sample designed to encrypt files and demand ransom for recovery. It adds the “.wing” extension to encrypted files and leaves a ransom note titled “Readme.txt” after encryption.
Notably, there have been instances of spam emails and posts on hacker forums where Wing’s developers actively seek partners, indicating an attempt to establish a Ransomware-as-a-Service (RaaS) model business.

Screenshot of files encrypted by Wing ransomware (Source: Surface Web)
The ransomware employs robust cryptographic algorithms such as RSA-4096, AES-256, and ChaCha20 for data encryption.
It targets local and network-shared files, excluding critical system files and those likely to impede efficient encryption.
Wing can terminate processes running in the Windows Task Manager. Additionally, it eradicates Volume Shadow Copies, eliminating a potential recovery option.
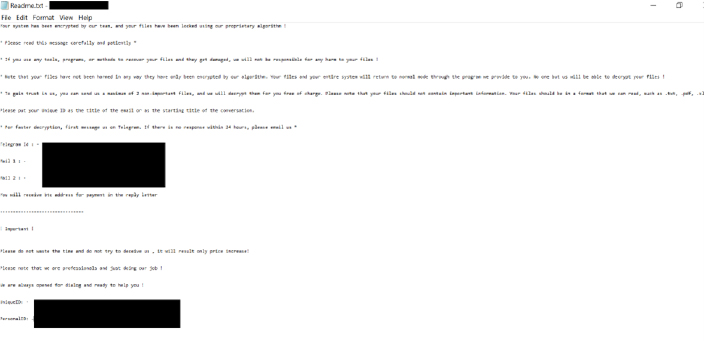
Ransom note. (Source: Surface Web)

Screenshot of a spam email seeking partners for Wing ransomware (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1106: Native API |
| T1569.002: System Services: Service Execution | ||
| 2 | TA0003: Persistence | T1176: Browser Extensions |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1112: Modify Registry | ||
| T1222: File and Directory Permissions Modification | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| 5 | TA0007: Discovery | T1012: Query Registry |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 6 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 7 | TA0009: Collection | T1185: Browser Session Hijacking |
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Based on CYFIRMA’s assessment, Wing ransomware is expected to advance, adopting more sophisticated tactics and collaboration via Ransomware-as-a-Service. Expect heightened evasion methods and targeting of critical system elements, posing increased risks across industries. Organizations should remain vigilant, continuously update cybersecurity measures, and monitor threat intelligence for proactive defense against emerging ransomware threats.
Sigma Rule
title: Suspicious desktop.ini Action tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Espionage, Credential Stealing, Financial theft, Remote Access
Target Technology: Android OS, Pix (Payment Platform)
Target Industries: Banks, Financial Sector
Target Geography: Brazil
Active Malware of the Week
This week “PixPirate” is trending.
PixPirate
Researchers have identified PixPirate, a sophisticated financial remote access trojan (RAT), employing anti-research techniques to evade detection. It spreads through two malicious apps: a downloader and a droppee, operating together to execute fraud.
Remarkably, the downloader not only downloads and installs the droppee but also actively participates in its execution, facilitating communication and command transmission between the two components. PixPirate is primarily targeting banks in Brazil.
Traditionally, banking malware concealed its presence on mobile devices by hiding its launcher icon using the SetComponentEnabledSetting API. However, this method became ineffective with the introduction of new restrictions in Android 10 by Google. In response to this challenge, PixPirate has introduced a novel technique to conceal its icon, unprecedented in financial malware. This innovative approach allows PixPirate to execute reconnaissance and attacks without the victim being aware of the malicious activities occurring in the background.
Modus Operandi
PixPirate campaigns primarily target customers of banks in Brazil, with a focus on the Brazilian payment service, Pix. Pix is the standard instant payment platform in Brazil, widely adopted by banks, which often integrate the Pix API into their banking apps to facilitate Pix transactions directly within the app.
PixPirate’s Innovative Technique
Researchers discovered a novel technique used by PixPirate to hide the malware from victims across all Android versions. Unlike traditional methods, PixPirate’s droppee lacks a main activity, meaning it lacks an icon on the victim’s home screen. This poses a challenge: without an icon, how does the victim launch the app? PixPirate addresses this by employing two applications – the downloader and the droppee – that collaborate. The downloader initiates and executes the droppee, ensuring its operation despite the absence of an icon.
Attack Method
PixPirate initiates its attack by luring victims to download its downloader through malicious links sent via WhatsApp or SMS phishing messages. Disguised as a legitimate banking app, the downloader convinces victims to install it. Upon launch, victims are prompted to install an “updated version,” which is actually the PixPirate malware (the droppee). After the victim approves this update, the downloader either embeds the droppee within its APK file or downloads it from the PixPirate command and control (C2) server. If embedded within the downloader’s APK, the droppee is encrypted and encoded within the “/assets/” folder, camouflaging itself as a JPEG file to minimize suspicion.
Subsequently, the downloader commands the droppee to activate and execute. During its initial run, the droppee requests accessibility service permissions from the victim, which are exploited by PixPirate to gain necessary permissions for financial fraudulent activities.
Once equipped with the requisite permissions, PixPirate collects device information to assess its suitability for fraud, including anti-VM/anti-emulator measures and installed banking apps, transmitting this data to the PixPirate C2.

Fig: Infection Chain of PixPirate
PixPirate’s Droppee Execution
PixPirate employs a mechanism to initiate the droppee’s execution based on specific events occurring on the device. Unlike traditional methods using activities, PixPirate utilizes a service to launch the droppee, which is exported and can be invoked by other processes on the device. This service features a custom action triggered by binding to it, allowing the downloader to create and bind to this service, consequently running the droppee as needed. The method works as follows:
The BindService API has the following parameters:
The downloader successfully triggers the droppee to execute by establishing communication through the ServiceConnection object, facilitating message exchange between them. The code within the downloader APK creates and binds to the droppee APK’s exported service, initiating droppee execution and issuing commands. This process occurs during the initial installation of the droppee by the downloader. Subsequently, to maintain persistence, the droppee is triggered by registered receivers responding to various system events, not solely reliant on the downloader. This innovative technique enables PixPirate to run and conceal its presence, even if the victim removes the downloader. It marks the first instance observed by researchers of financial malware employing such a tactic to evade detection and hide its launcher icon from victims.
PixPirate: Executing Pix Fraud with Capabilities
PixPirate conducts fraudulent Pix transactions by either initiating new transactions to the fraudster’s Pix account or by altering the recipient details of legitimate transactions initiated by the victim to divert funds to the fraudster’s Pix account. PixPirate executes Pix fraud through its RAT capabilities, abusing the Android accessibility service. The malware monitors the victim’s device activities, particularly waiting for the launch of specific banking applications. Upon detecting relevant events, it examines the event type, particularly focusing on “TYPE_WINDOW_STATE_CHANGED.” If the event corresponds to this type and matches a targeted banking app, the malware initiates its malicious activities.
Upon the victim launching their bank app, the malware covertly captures user credentials and account information as they are entered. Subsequently, this stolen data is transmitted to the attacker’s C2 server without the victim’s awareness, facilitated by the malware operating discreetly in the background. When the malware initiates fraudulent activities, it overlays a new screen atop the device interface, concealing its malicious actions from the victim. Programmatically navigating to the Pix page within the bank app, the malware executes Pix money transfers seamlessly, further obscuring its activities.
Functions of PixPirate
Researchers observed various functions utilized by the malware to input relevant details and execute Pix money transfers seamlessly, including Pix details, transaction amounts, passwords, and more.

Fig: Different functions of the PixPirate
The primary function responsible for executing the fraud is “strictPay_js.action.transfer,” which automates the fraudulent process. Initially, it invokes SendPageNode(1) to navigate to the Pix page in the banking app. Subsequently, the sendBalance() function, comprising three subfunctions:
PixPirate employs the same technique for intercepting victim operations and altering Pix details unnoticed during transactions, manipulating both target accounts and transaction amounts. Additionally, if 2FA is required, the malware can intercept SMS messages from the bank.
Capabilities of PixPirate
PixPirate utilizes the accessibility service to acquire remote access trojan (RAT) capabilities, enabling it to monitor the victim’s activities and pilfer crucial data such as online banking credentials, credit card details, and login information from targeted accounts. Additionally, if two-factor authentication (2FA) is required, the malware can manipulate the victim’s SMS messages, including those from the bank. With its modern capabilities, PixPirate poses a significant threat to victims, showcasing a range of malicious abilities. Following is a list of PixPirate’s main malicious capabilities:
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the ongoing evolution of malware such as PixPirate presents significant challenges for both organizations and individuals. With cybercriminals continuously refining their tactics, the severity and reach of these threats are expected to increase. Looking ahead, it’s evident that malware will persistently evolve, adapting to security measures and exploiting vulnerabilities. As a result, organizations may face heightened risks of security breaches, data theft, and financial losses, leading to disruptions in business operations, reputational damage, and loss of customer trust. Moreover, the impact of malware attacks like PixPirate is anticipated to extend beyond financial ramifications, affecting privacy, trust, and overall digital resilience.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Unveiling Earth Krahang: A Sophisticated Cyber Threat Targeting the Globe
Summary:
In the complex landscape of cyber warfare, a new adversary has emerged – Earth Krahang. This Chinese-origin Advanced Persistent Threat (APT) group has orchestrated a sophisticated and multi-pronged cyber assault, targeting government entities across the globe. Their tactics reveal a comprehensive strategy designed to infiltrate, exploit, and extract sensitive information with precision.
Governments worldwide find themselves in Earth Krahang’s crosshairs, with targets spanning 45 countries across continents. From Foreign Affairs ministries to telecommunications providers, the breadth of their operation underscores the gravity of their threat. No industry or region is immune to their cyber assault. Earth Krahang employs a multi-pronged approach to infiltrate target networks. The threat actors’ favourite tactic is scanning public-facing servers to gain access to government infrastructure, followed by Spear phishing campaigns, meticulously crafted with geopolitical themes, to attack other government entities using earlier compromised government email accounts. Once inside the network, they establish persistence using post-exploitation techniques like maintaining backdoor access and escalating privileges through tools like BadPotato and SweetPotato. The threat actor exploited CVE-2023-32315 and CVE-2022-21587 during the initial access phase.
The motive behind Earth Krahang’s aggressive cyber campaign appears to be rooted in cyber espionage. By infiltrating government networks and extracting sensitive information, they seek to gain intelligence and exert influence on a global scale. The deployment of advanced malware like Cobalt Strike and XDealer underscores their calculated intent to maintain long-term control within victim networks. As Earth Krahang’s cyber assault intensifies, the imperative for proactive cybersecurity measures becomes increasingly evident. Organizations and governments must bolster their defences against this formidable threat, leveraging advanced detection systems and employee training to mitigate risks. Collaboration among international cybersecurity agencies is crucial to thwart the ambitions of Earth Krahang and safeguard global security in the digital age.
Relevancy & Insights:
Earth Krahang; also known as Earth Lusca, is a sophisticated threat actor originating from China, emerging since 2019. Their tactics involve meticulous reconnaissance, social engineering, and technical exploits, targeting entities across 45 countries. Their motive, primarily cyber espionage, poses grave concerns for national security, necessitating enhanced cybersecurity measures. The extensive reach of their operations underscores the imperative for international cooperation among cybersecurity agencies and governments to combat such threats effectively.
ETLM Assessment:
Earth Krahang operates with a global footprint, targeting victims across 45 countries spanning Asia, America, Europe, and Africa. Its primary focus lies within government organizations, notably Foreign Affairs ministries and departments, alongside an interest in the education sector. Additionally, Earth Krahang has shown targeting efforts towards the communications industry, post offices in multiple countries, logistics platforms, and job services. While government entities remain the prime targets, Earth Krahang has also infiltrated industries such as finance, healthcare, IT, manufacturing, media, military, real estate, retail, sports, and tourism, albeit on a smaller scale. The threat actor’s modus operandi centers on cyberespionage, with a specific goal of exfiltrating victim emails, indicating a sophisticated and persistent threat with far- reaching implications for targeted entities and global cybersecurity. Furthermore, suspicions of a connection between Earth Krahang and Earth Lusca suggest a potentially intricate web of coordinated malicious activity.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems
North Korean hackers launch a new malware campaign in South Korea
Researchers have recently reported on a new campaign tracked as DEEP#GOSU that’ tied with a very high degree of probability to the North Korean APT known as Kimsuky. While the targeting of South Korean victims by the Kimsuky group has happened before, from the tradecraft observed it’s apparent that the group has shifted to using a new script-based attack chain that leverages multiple PowerShell and VBScript stagers to quietly infect systems. The later-stage scripts allow the attackers to monitor the clipboard, keystroke, and other session activity. The APT is trying to lure victims to click a subverted PDF file in Korean that appears to be a funeral announcement regarding the family of the Korean Airlines CEO.
ETLM Assessment:
It is well known that this group engages in resource-intensive efforts aimed at academics, researchers, think tanks, industry, nuclear power operators, the Ministry of Unification for espionage purposes, or other people who may have perspectives or insights into security and policy matters of importance to Pyongyang. These individuals are attractive targets for intelligence gathering for the North Korean regime, as they are perceived to be close to policy-making circles and are thus in a position to influence the intelligence and policy communities. This campaign should be regarded as a classic case of state-driven espionage with many similar ones possibly underway.
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
The LockBit 3.0 Ransomware impacts the McKim & Creed
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]mckimcreed[.]com), was compromised by the LockBit 3.0 Ransomware. McKim & Creed, Inc. is a company that focuses on civil, environmental, mechanical, electrical, plumbing, and structural engineering; industrial design-build services, airborne and mobile LiDAR/scanning, unmanned aerial systems, subsurface utility engineering, and hydrographic and conventional surveying services for the energy, transportation, federal, land development, water and building markets. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
CYFIRMA’s assessment underscores the persistent and widespread threat posed by LockBit 3.0 Ransomware to companies worldwide. Our observations reveal an escalating pattern, wherein LockBit 3.0 Ransomware exploits vulnerabilities in diverse products to infiltrate systems, facilitating lateral movement within organizational networks. The recent cyber incident involving the McKim & Creed; The United States of America -based construction company, highlights the pervasive global danger associated with this ransomware variant.
Vulnerability in FitNesse
Summary:
The disclosed vulnerability allows a remote attacker to perform cross-site scripting (XSS) attacks.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data. A remote attacker can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in the user’s browser in context of a vulnerable website.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change the appearance of the web page, and perform phishing and drive-by-download attacks.
Affected Products:
https[:]//jvn[.]jp/en/jp/JVN94521208/index.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

APT28 Hacker Group Targeting Europe, Americas, and Asia in Widespread Phishing Scheme
Summary:
The threat actor APT28, associated with Russia, has been implicated in numerous ongoing phishing campaigns across Europe, the South Caucasus, Central Asia, and North and South America. These campaigns utilize lure documents mimicking both government and non-governmental organizations (NGOs). The lures, which consist of a combination of internal documents, publicly available files, and potentially actor- generated content, span various sectors including finance, critical infrastructure, executive engagements, cybersecurity, maritime security, healthcare, business, and defense industrial production. The phishing attacks impersonate entities from countries such as Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the U.S. They leverage a mix of authentic publicly available documents to initiate the infection chains. Furthermore, the threat actors employ the hosting provider firstcloudit[.]com to stage payloads for ongoing operations. The ultimate objective of these phishing campaigns is to execute MASEPIE, OCEANMAP, and STEELHOOK, which aim to exfiltrate files, run arbitrary commands, and pilfer browser data, respectively.
Relevancy & Insights:
FANCY BEAR (also known as APT 28) exhibits sophisticated tactics in targeting conventional computers and mobile devices. Their modus operandi involves leveraging phishing messages and spoofed websites for credential harvesting. Notably, FANCY BEAR demonstrates the capability to conduct multiple intrusion operations concurrently. Recent observations indicate that APT 28 has exploited vulnerabilities within Microsoft Outlook, such as CVE-2023-23397 (CVSS score: 9.8), to extract NT LAN Manager (NTLM) v2 hashes. This raises concerns about the potential exploitation of other weaknesses to extract NTLMv2 hashes for subsequent relay attacks.
ETLM Assessment:
FANCY BEAR, also referred to as APT28 or Sofacy, has been active since at least 2008, posing a persistent threat to numerous organizations worldwide. Their targets span diverse sectors, including aerospace, defense, energy, government, media, and dissident groups. Employing sophisticated cross-platform implants, FANCY BEAR has demonstrated a capability to infiltrate various networks. According to CYFIRMA’s ongoing assessment, it is anticipated that threat actors with Russian affiliations will persist in targeting organizations globally, with objectives ranging from financial fraud to unauthorized access.
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Sabella data advertised on the Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to Sabella, {www[.]sabella[.]com[.]my}. Sabella operates as an e-commerce fashion brand, where its signature products offer the taste of exclusivity and luxury. The data available for sale includes identifiers such as IDs, usernames, email addresses, passwords, tokens, email verification status, email triggering status, and other confidential and sensitive information. The asking price for this data is $250.

Source: Underground forums
Relevancy & Insights:
In the realm of cybersecurity, opportunistic cybercriminals driven by financial motives constantly scour the digital landscape for exposed and vulnerable systems and applications. A significant portion of these threat actors convene within underground forums, where discussions revolve around the exchange of stolen digital assets. Unlike ransomware or extortion groups, who often publicize their exploits, these perpetrators prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications to illicitly gain access and pilfer valuable data. Subsequently, this stolen data finds its way into underground markets, where it is advertised, resold, and repurposed by other malicious actors to fuel their nefarious activities.
ETLM Assessment:
The threat actor “haxormy1337” has recently emerged as a significant player in the cyber landscape, motivated primarily by financial gains. They are currently engaged in the illicit trade of sensitive data, including personally identifiable information (PII), financial records, and other confidential data obtained from Sabella. CYFIRMA’s assessment reveals that institutions in Malaysia with inadequate security measures and infrastructure are particularly susceptible to potential cyberattacks orchestrated by this threat actor.
CYFIRMA Research team observed a potential data leak related to PYLC Insurance, {www[.]pylc[.]com[.]mx}. PYLC focuses on providing insurance and bond services within the financial sector. The company offers solutions aimed at protecting assets and ensuring financial security for its clients. The compromised data set includes sensitive information, such as IDs, quote numbers, policy numbers, net premiums, charges, total premiums, policy fees, discounts, taxes, progress status, start and end dates, user IDs for various roles (insured, agent, executive, main, seller), date of printing, insurance IDs, category IDs, and other confidential details. This data breach has appeared on a hacking forum and is attributed to the notorious threat actor known as IntelBroker.
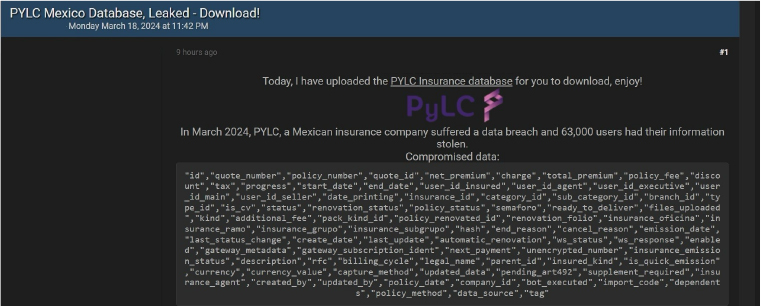
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS