



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industries: Apparel Retailers, Business Support Services, Chemicals, Construction, Food, IT, Manufacturing, Oil & Gas, Retail, Semiconductors, and Transportation.
Target Geography: Austria, Brazil, Denmark, France, India, Indonesia, Portugal, South Korea, Spain, Turkey, United States of America, Vietnam.
Introduction
CYFIRMA Research and Advisory Team has found a Mallox ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Mallox ransomware:
Mallox is a ransomware threat that has been operational since its appearance in 2021.
Mallox ransomware typically gains initial access by exploiting vulnerabilities in publicly exposed services, with a specific emphasis on MS-SQL (Microsoft SQL Server) and ODBC (Open Database Connectivity) interfaces. It specifically targets vulnerabilities such as unpatched instances of older remote code execution (RCE) vulnerabilities like CVE-2019-1068 in Microsoft SQL Server and CVE-2020-0618 in Microsoft SQL Server Reporting Services.
Furthermore, the group effectively employs brute force attacks against services and applications that are inadequately configured and exposed to the public internet. In recent campaigns, Mallox actors obtained initial access through dictionary-based brute-force attacks targeting vulnerable MS-SQL interfaces. However, Mallox affiliates are also known to utilize other vectors, such as phishing emails, to deliver attack frameworks.
Once Mallox threat actors gain entry, they usually use PowerShell commands to trigger batch scripts and fetch the ransomware payload. They employ scripts like Kill-Delete.bat or Bwmeldokiller.bat to stop or delete active processes that could hinder or stop the ransomware’s encryption process.
Commands are executed to download and launch the ransomware payloads.
The sequence of commands starts by creating a PowerShell script in the temporary directory of the system. It uses the WebClient class to download an executable from a remote server. The PowerShell script, named updt.ps1, is then executed by bypassing execution policy restrictions, allowing it to run without limitations. Following this, the script utilizes Windows Management Instrumentation (WMIC) to execute the ransomware payload.
The payloads of Mallox, spanning from 2021 to the present, consistently demonstrate a set of core functions. This suggests that threat actors have found success using a reliable approach. The latest payloads are named “Mallox.Resurrection”.
Certain file types and processes are deliberately excluded from encryption through predefined rules. These exclusions are coded directly into the malware and spare specific file types based on their extensions.
Files types excluded based on extensions,
.386, .adv, .ani, .avast, .bat, .bin, .cab, .cmd, .com, .cpl, .cur, .deskthemepack, .diagcfg, .diagpkg, .diangcab, .dll, .drv, .exe, .Globeimposter-Alpha865qqz .hlp, .hta, .icl, .icns, .ico, .ics, .idx, .key, .lnk, .lock, .mallox, .mallox, .mod, .mpa, .msc, .msi, .msp, .msstyles, .msu, .nls, .nomedia, .ocx, .prf, .ps1, .rom, .rtp, .scr, .shs, .spl, .sys, .theme, .themepack, .wpx
Upon launch, the ransomware spawns the following commands:
bcdedit.exe /set {current} bootstatuspolicy ignoreallfailures
bcdedit.exe /set {current} recoveryenabled no
These actions aim to modify the Boot Configuration Data (BCD) settings, impacting the operating system’s capacity to recover from failures and hindering administrators from restoring the system using Windows’ built-in tools.
Files that have been encrypted by Mallox are marked with the “.mallox” extension. Additionally, a ransom note named “HOW TO BACK FILES.TXT” is deposited in each folder containing the encrypted files. This note provides instructions on obtaining a decryption tool via TOR and includes a unique identifier for the victim known as the TargetID. Notably, there was an observed shift in the contact email within Mallox ransom notes, changed from “mallox@onionmail” to “[email protected].”
In addition to the ransom notes, a file named “Targetinfo.txt” is placed on the user’s Desktop. This file includes the TargetID and provides basic details about the host’s environment, such as the operating system version, architecture, and hostname.
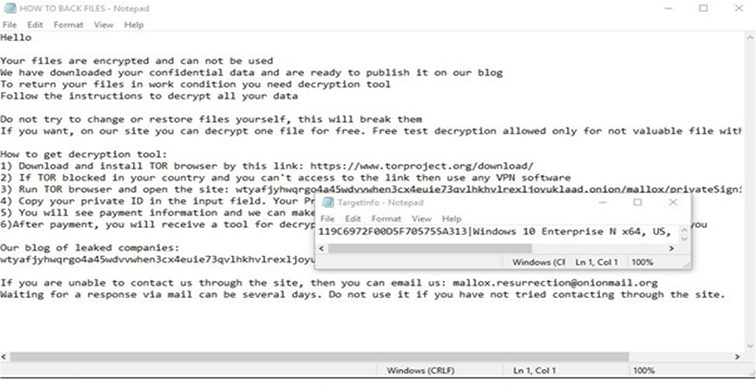
Screenshot of Mallox ransom note(Source: Surfaceweb)

Screenshot of Files Encrypted by Mallox ransomware (Source: Surfaceweb)
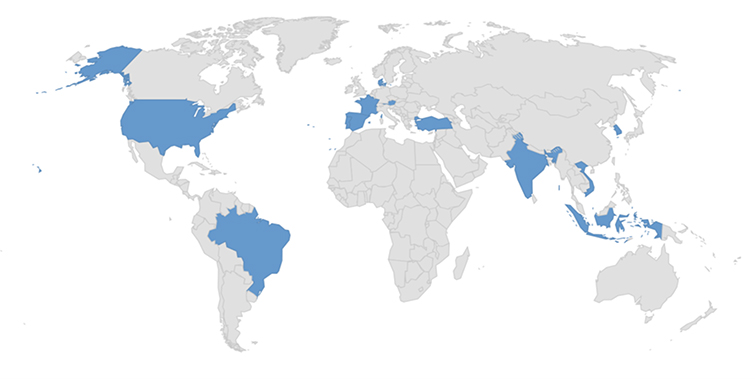
Countries targeted by Mallox Ransomware.
Following are the TTPs based on the MITRE Attack Framework.
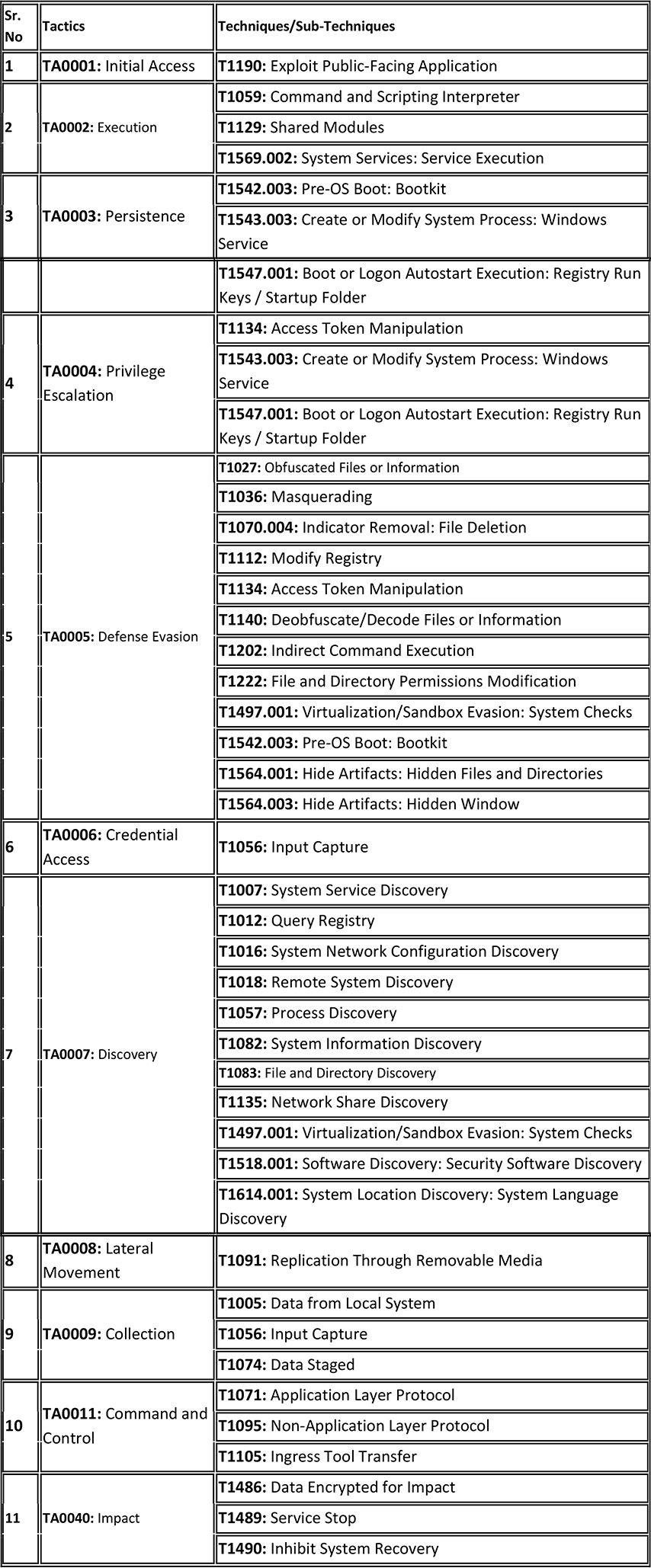
Relevancy and Insights:
ETLM Assessment:
Cyfirma’s assessment based on the available information suggests that Mallox ransomware will likely evolve its tactics to exploit new vulnerabilities and diversify initial access methods, possibly incorporating more sophisticated evasion techniques. It may continue targeting Windows systems across various industries. Additionally, ransomware’s persistence through altering registry keys indicates a focus on prolonged control. Staying vigilant against evolving tactics is crucial, emphasizing the need for robust backup solutions, regular software updates, and user education to mitigate potential impacts.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule:
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490
logsource:
category: process_creation
product: windows
detection:
selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’
selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet
selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’
selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’
CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*)
fields:
– CommandLine
– ParentCommandLine
falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high
(Source: Surface web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan
Objective: Infiltration, Malware implant
Suspected Threat Actor: TA577
Target Technology: Windows
Active Malware of the Week
This week “PikaBot” is trending.
PikaBot
Over the recent days, researchers have detected PikaBot, a fresh malware family that surfaced in early 2023. Its distribution method has shifted to malvertising, marking a departure from its previous mode of dissemination through malspam campaigns.
In earlier attacks, the typical PikaBot distribution chain involves an email with a link to an external website, leading users to download malicious JavaScript from a zip archive. The JavaScript establishes a random directory structure, retrieves the payload via the curl utility, and executes it (DLL) through rundll32. PikaBot’s core module is injected into the legitimate SearchProtocolHost.exe process, and its loader employs indirect syscalls to conceal the injection, enhancing the malware’s stealthiness. However, in this latest campaign, PikaBot has shifted tactics, leveraging malvertising to target Google searches related to the remote application AnyDesk.
PikaBot’s Origin and TA577’s Affiliation
PikaBot was initially identified in February 2023 as a potential Matanbuchus drop from a Malspam campaign. Matanbuchus is considered to be a loader type of malware used to download and execute malware payloads on the targeted environments. It was later attributed to the threat actor TA577, known for distributing various payloads like QakBot, IcedID, SystemBC, and Cobalt Strike, has links to ransomware distribution. Unlike its past distribution solely through malspam campaigns, PikaBot has evolved into one of the preferred payloads for the threat actor TA577.
Attack method
The campaign focuses on Google searches related to the remote application AnyDesk. Security researchers traced the distribution chain and confirmed the payload as PikaBot. Another aspect of the campaign involves a different ad impersonating the AnyDesk brand under the fake persona “Manca Marina.”
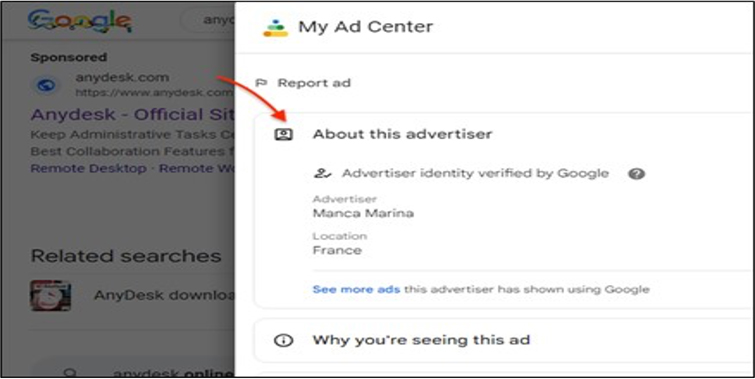
Upon clicking the impersonate link, users are redirected to a decoy website at anadesky[.]ovmv[.]net.
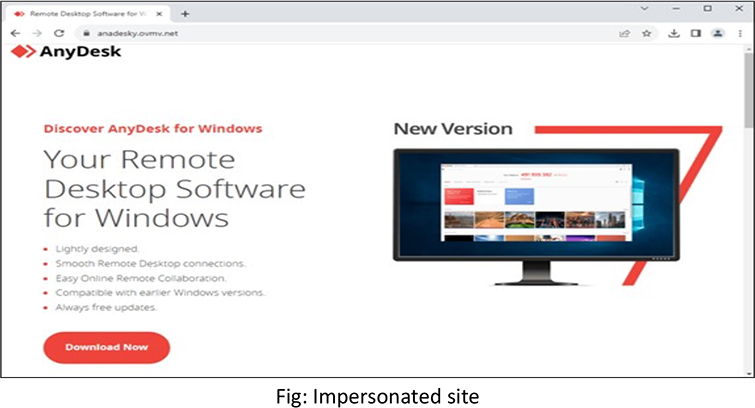
The download is a digitally signed MSI installer, which, at the time of collection, showed zero detection on VirusTotal. Notably, its intriguing feature lies in its ability to evade detection upon execution. Following the attached execution flow of the PikaBot.
[MISSING IMAGE:,]
Evasion: Stealthy Tactics
To outsmart Google’s security, the threat actors are using a tricky method. They send a tracking URL through a normal marketing platform, then shift to their own secret domain hidden behind Cloudflare. Here’s the catch: only clean IP addresses move forward in the plan. They use JavaScript to check if you’re using a virtual machine. If everything checks out, you get redirected to their main fake AnyDesk site.
What’s even sneakier? There’s a second check when you click the download button. It’s like a double-check to make sure the download link doesn’t work if you’re in a virtual environment.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolution of PikaBot suggests a trajectory towards more sophisticated and adaptable cyber threats. Its demonstrated agility and integration into various campaigns, combined with advanced evasion techniques, indicate a potential for increased complexity in future iterations. Looking ahead, the emphasis on targeting popular platforms like AnyDesk through Google searches suggests a future trend where cyber threats will increasingly focus on widely used applications. This poses potential risks for organizations heavily dependent on such platforms, indicating a need for heightened cybersecurity measures. The incorporation of deceptive ads and impersonation tactics in attack methods introduces a new level of complexity, underscoring the importance of organizations adopting proactive defense strategies. In the evolving landscape of threats like PikaBot, future cybersecurity efforts should prioritize increased awareness and adaptive defense measures to effectively counter the dynamic and sophisticated nature of these emerging risks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
Gaza Cyber Gang Employed Modified Version of Pierogi Malware to Target Palestine and Israel
Threat Actors: Gaza Cyber Gang
Attack Type: Spear Phishing
Objective: Espionage
Target Technology: Windows
Target Geographies: Palestine and Israel
Target Industries: Unknown
Business Impact: Data Loss, Data exfiltration
Summary:
Recently the Gaza Cyber Gang, a pro-Hamas threat actor, has been observed targeting Palestinian entities using an updated backdoor called Pierogi++. This updated malware, named by researchers, differs from its predecessors by being implemented in C++ rather than Delphi or Pascal. Security researchers observed a consistent targeting pattern of Palestinian entities in the group’s recent activities, unchanged since the onset of the Israel-Hamas conflict. The group is active since at least 2012. The Gaza Cyber Gang has a history of targeting the Middle East, specifically Israel, and Palestine, employing spear-phishing as a primary method for initial access. Their arsenal includes various malware families like BarbWire, DropBook, LastConn, Micropsia, and more. In recent months, the group has been tied to a series of attacks deploying modified versions of Micropsia and Arid Gopher implants, along with a new initial access downloader named IronWind. The most recent breaches attributed to the Gaza Cyber Gang involve the utilization of Pierogi++ and Micropsia. The initial deployment of Pierogi++ dates back to late 2022. The Gaza Cyber Gang’s attack methodology involves the use of decoy documents, written in Arabic or English and relevant to Palestinian interests, as a means to introduce these backdoors. Previously known as Pierogi from February 2020, it was an implant enabling attackers to spy on targets. The researchers highlighted that the communication commands and code strings within the binary were previously written in Ukrainian. The backdoor might have been acquired from underground networks rather than being internally developed. Both Pierogi and Pierogi++ possess capabilities to capture screenshots, execute commands, and retrieve files provided by the attackers.
Relevancy & Insights:
Both Pierogi and Pierogi++ possess capabilities to capture screenshots, execute commands, and retrieve files provided by the attackers. An interesting update is the absence of Ukrainian code strings in the newer versions of these artifacts. Despite sustained attention to Palestine, the development of Pierogi++ underscores the group’s continuous efforts to enhance malware for successful network compromise and persistence access.
ETLM Assessment:
The team at CYFIRMA observed a surprising cyber-attack by the Gaza Cyber gang. The group is pro-Hamas that chose to target Palestinian entities revealing the group’s aim to zero down moles working for the Israeli government and get rid of internal threats that could leave damage in the ongoing conflict. Simultaneously, the group was observed targeting Israeli entities, and these cyber-attacks will continue as gathering intel against Israel and removing inside moles, favouring Hamas in the ongoing conflict.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Cyber-attack paralyzes majority of gas stations in Iran
About seventy percent of Iran’s gasoline stations went out of operation due to what Iranian media at first described as a “software problem” but which was subsequently described as a large-scale cyber-attack targeting the payment systems of the impacted gas stations, as well as management systems, as reported by researchers and later also Iran’s Oil Ministry. The attack has been claimed by Predatory Sparrow, a group that Iran attributes to Israel and about which Israel does not offer any comment. The group issued a statement in which it claimed the cyberattack came in response to the aggression of the Islamic Republic and its proxies in the region.
ETLM Assessment:
The attack is just another blow in the ongoing cyber war between Iran and Israel. Israel’s National Cyber Directorate previously stated that the prospect of an intensified Iranian cyber campaign is deeply worrying, since Iran “knows that they can act there [in cyberspace] more freely than in physical space”. An attack such as this one is likely meant to show Iran, that it too is vulnerable to cyber-attacks and that it should not overstep certain boundaries.
Alexander Dennis is Impacted by the Black Basta Ransomware
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: United Kingdom
Ransomware: Black Basta Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Kingdom, (www[.]alexander-dennis[.]com), was compromised by Black Basta Ransomware. Alexander Dennis is a British bus manufacturing company based in Larbert, Scotland. Alexander Dennis is the largest bus and coach manufacturer in the United Kingdom. It has manufacturing plants and partnerships in Canada, China, Europe, Hong Kong, Malaysia, New Zealand, Singapore, South Africa, and the United States. The data breach comprises information from various departments, such as Group data, HR, Finance, Legal, Engineering, and among others. The overall volume of compromised data amounts to 507 gigabytes.
The following screenshot was observed published on the dark web:

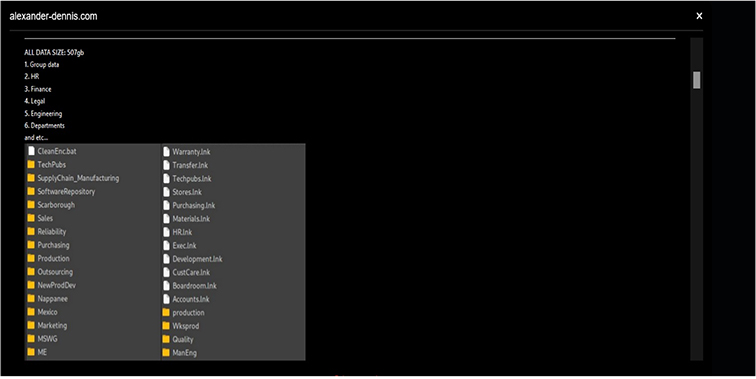
Source: Dark Web
Relevancy & Insights:
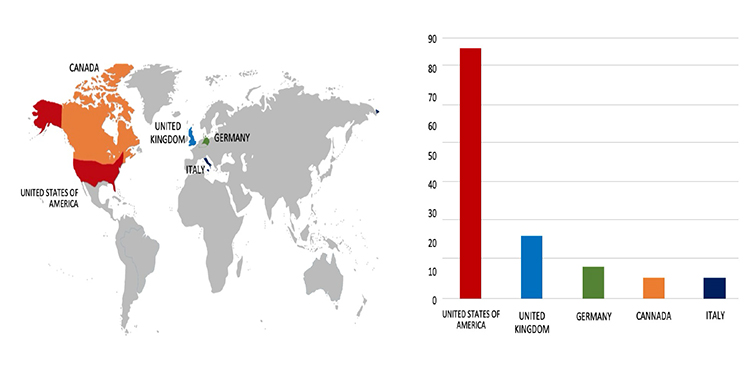
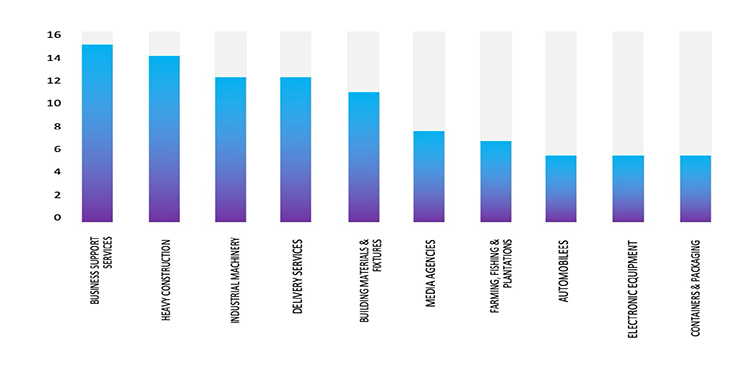
ETLM Assessment:
CYFIRMA assesses Black Basta Ransomware will continue to focus on American businesses and related entities that hold significant amounts of Personally Identifiable Information (PII), financial information, or other sensitive data. However, the recent assault on Alexander Dennis highlights the dangers posed to companies, in advanced economies by the Black Basta Ransomware.
Vulnerability in 3CX CRM Integration
Attack Type: Vulnerabilities & Eploits
Target Technology: Hardware Solutions
Vulnerability: CVE-2023-49954 (CVSS Base Score 6.5)
Vulnerability Type: SQL Injection
Summary:
The vulnerability allows a remote user to execute arbitrary SQL queries in database.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data within 3CX CRM Integration. A remote user can send a specially crafted request to the affected application and execute arbitrary SQL commands within the application database.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to read, delete, modify data in database and gain complete control over the affected application.
Affected Products: https[:]//cve-2023-49954[.]github[.]io/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
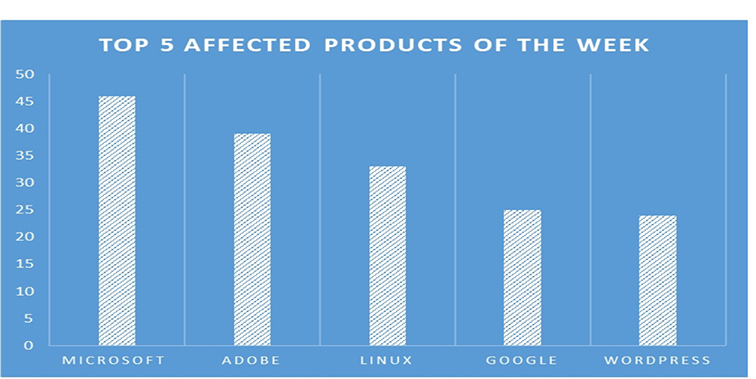
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
8220 Gang Exploiting Oracle WebLogic Server Vulnerability to Spread Malware
Threat Actors: 8220 Gang
Attack Type: Vulnerability Exploitation
Objective: Espionage
Target Technology: Unknown
Target Geographies: U.S.A, South Africa, Spain, Columbia, and Mexico.
Target Industry: Healthcare, Telecommunications, and Financial services
Business Impact: Operational Disruption
Summary:
Recently we observed that the threat actors affiliated with the 8220 Gang have been detected leveraging a critical vulnerability within the Oracle WebLogic Server to spread their malicious software. The identified security vulnerability is CVE-2020-14883 (CVSS score: 7.2), representing a remote code execution flaw. Authenticated attackers could potentially exploit this vulnerability to gain control over vulnerable servers. The attack chains entail the exploitation of CVE-2020-14883 to specially craft XML files and ultimately run code responsible for deploying stealer and coin mining malware such as Agent Tesla, rhajk, and nasqa. The campaign’s targets encompass sectors such as healthcare, telecommunications, and financial services, spanning across the U.S., South Africa, Spain, Colombia, and Mexico. The group employs straightforward, readily available exploits to exploit widely known vulnerabilities, targeting vulnerable entities for their objectives. Despite being characterized as unsophisticated, they consistently adapt and refine their tactics and techniques to evade detection.
Relevancy & Insights:
8220 Gang also known as “8220 Mining Group,” is derived from their use of port 8220 for command and control or C&C communications exchange. The 8220 Gang has a history of leveraging known security flaws to distribute their malware. Along with Oracle WebLogic Server Authenticated RCE (CVE-2020-14883), researchers observed Oracle WebLogic Server RCE (CVE-2017-3506), Oracle WebLogic Server Authenticated Deserialization (CVE-2019-2725), Atlassian Confluence Server OGNL Injection RCE (CVE-2021-26084), CVE-2021-44228 – Apache Log4j JNDI RCE (CVE-2021-44228), Atlassian Confluence Server RCE (CVE-2022-26134) vulnerabilities getting exploited by 8220 Gang.
ETLM Assessment:
The 8220 Gang, a profit-driven threat group from China, predominantly focuses on cloud providers and inadequately secured applications. They deploy a tailored crypto miner and IRC bot for their activities. The primary sectors in their crosshairs include healthcare, telecommunications, and financial services in the U.S., South Africa, Spain, Colombia, and Mexico. Based on the ongoing campaign, CYFIRMA emphasizes the critical need to patch a high-severity vulnerability in the Oracle WebLogic Server to prevent potential exploitation by various threat actors.
ViTrox Data Advertised in Leak Site
Attack Type: Data Leaks
Target Industry: Manufacturing
Target Geography: Malaysia
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to ViTrox {www[.]vitrox[.]com}. ViTrox Corporation is a Malaysian technology company with a strong focus on machine vision and electronics. It specializes in the design and development of automated vision inspection systems and equipment for semiconductors, printed circuit board assemblies, and electronics communication industries. ViTrox’s products include the Machine Vision System (MVS), Automated Board Inspection (ABI), Integrated Industrial Embedded Solutions, and Industry 4.0 Manufacturing Intelligence Solution – V-ONE. The compromised data consists of personal details like name, company information, email address, username, password, and other confidential data.
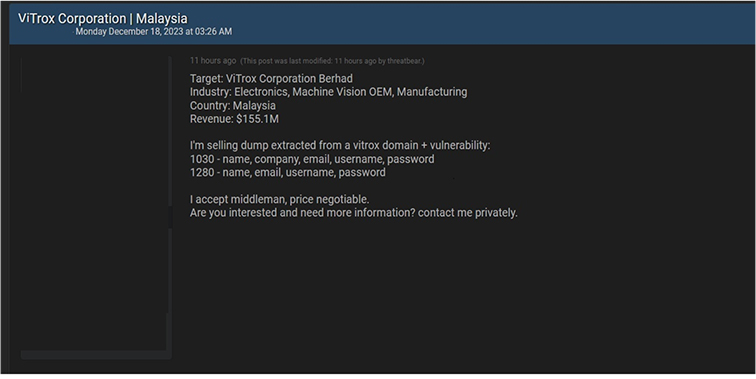
Source: Underground forums
Relevancy & Insights:
Opportunistic cybercriminals driven by financial motives are consistently seeking out exposed and vulnerable systems and applications. The primary arena for these attackers is underground forums, where they participate in discussions and trade stolen digital assets. In contrast to other financially motivated threat actors like ransomware or extortion groups, who tend to publicize their attacks, these opportunistic individuals prefer to operate discreetly. They infiltrate and pilfer valuable data by capitalizing on unpatched systems or exploiting vulnerabilities in applications and systems. The purloined data is subsequently advertised for sale within underground forums, being resold and repurposed by other attackers in their illicit activities.
ETLM Assessment:
CYFIRMA assesses that financially motivated cybercriminals consider Malaysia and other developed economies in Asia as attractive targets. Therefore, CYFIRMA considers there to be a continual and ongoing risk to companies in technologically advanced nations, such as Malaysia. Manufacturing and other industries will continue to be targeted by financially motivated threat actors.
CYFIRMA Research team observed a potential data leak related to Yipeedia, {www[.]Yipeedia[.]com} Yipeedia is an online E-Marketplace that offers exceptional international products, groceries, and food accessible at low prices. It is a platform for shoppers to shop endless products from International Sellers of more than 200 Countries, all at the convenience of Mobile devices. The sellers advertise Web-Shell Access to the Yipeedia Shopping App website, High privileges /edit/download/upload for USD 50.

Source: Underground forums
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION