


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Charon Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Charon Ransomware
Researchers identified a new ransomware variant named Charon, which demonstrates a technically consistent encryption-and-renaming cycle across compromised environments. Once executed, the malware traverses local and shared directories, systematically encrypting accessible files with strong cryptographic algorithms. To mark its activity and prevent redundant operations, each locked file is appended with the distinctive “.Charon” extension.

This encryption process is tightly coupled with the malware’s renaming logic, ensuring that all targeted file types follow a uniform post-compromise structure. Importantly, executables and dynamic libraries are excluded from encryption to avoid destabilizing the payload itself or preventing victim systems from remaining operational enough to view ransom instructions.
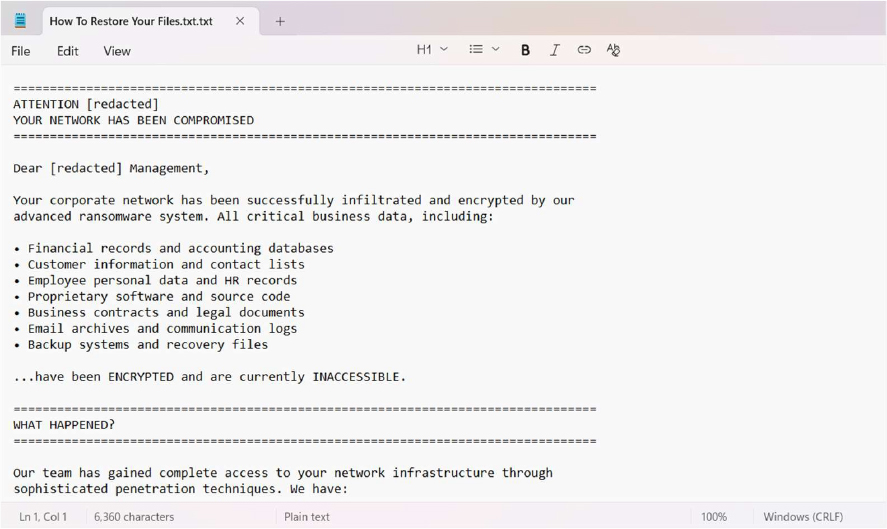
The ransom note files, consistently dropped as “How To Restore Your Files.txt” across directories, serve as both a persistent reminder of the compromise and an enforced communication channel between the attackers and the victim. This technical workflow demonstrates Charon’s dual focus on operational effectiveness and psychological impact, optimizing both disruption and visibility of the attack.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Execution | T1569 | System Services |
| Execution | T1569.002 | System Services: Service Execution |
| Persistence | T1543 | Create or Modify System Process |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1543 | Create or Modify System Process |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1518 | Software Discovery |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Collection | T1074 | Data Staged |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis assesses that Charon ransomware operations are likely to progress toward more sophisticated extortion frameworks, combining encryption with structured data theft to amplify leverage over victims. Its reliance on stealth-oriented techniques and system disruption methods indicates a trajectory where evasion and persistence will remain central themes, with potential enhancements toward automation of lateral movement and self-propagation. Future variants may also incorporate more resilient communication channels and negotiation mechanisms, signaling a shift toward professionalized and highly adaptive ransomware campaigns.
Sigma rule:
title: Suspicious Volume Shadow Copy Vssapi.dll Load tags:
– attack.defense-evasion
– attack.impact
– attack.t1490 logsource:
category: image_load product: windows
detection: selection:
ImageLoaded|endswith: ‘\vssapi.dll’ filter_windows:
– Image:
– ‘C:\Windows\explorer.exe’
– ‘C:\Windows\ImmersiveControlPanel\SystemSettings.exe’
– Image|startswith:
– ‘C:\Windows\System32\’
– ‘C:\Windows\SysWOW64\’
– ‘C:\Windows\Temp\{‘ # Installers
– ‘C:\Windows\WinSxS\’ filter_program_files:
# When using this rule in your environment replace the “Program Files” folder by the exact applications you know use this. Examples would be software such as backup solutions
Image|startswith:
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_programdata_packagecache:
# The following filter is required because of many FPs cause by:
# C:\ProgramData\Package Cache\{10c6cfdc-27af-43fe-bbd3- bd20aae88451}\dotnet-sdk-3.1.425-win-x64.exe
# C:\ProgramData\Package Cache\{b9cfa33e-ace4-49f4-8bb4- 82ded940990a}\windowsdesktop-runtime-6.0.11-win-x86.exe
# C:\ProgramData\Package Cache\{50264ff2-ad47-4569-abc4- 1c350f285fb9}\aspnetcore-runtime-6.0.11-win-x86.exe
# C:\ProgramData\Package Cache\{2dcef8c3-1563-4149-a6ec- 5b6c98500d7d}\dotnet-sdk-6.0.306-win-x64.exe
# etc.
Image|startswith: ‘C:\ProgramData\Package Cache\’ condition: selection and not 1 of filter_*
falsepositives:
– Unknown level: high
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan| Objectives: Stealing Sensitive Information, Financial Fraud, Data Exfiltration | Threat Actor: Go1ano developer | Target Technologies: Android OS, Mobile Payment Systems | Target Industry: Banks |Target Geography: Brazil CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “PhantomCard” is trending.
About the Malware PhantomCard
Researchers uncovered PhantomCard, a newly emerging Android banking trojan in Brazil that exploits NFC technology to steal payment card information. Masquerading as a fake “Card Protection” app on counterfeit Google Play pages with fabricated reviews, once installed, it secretly relays sensitive information from victims’ cards to cybercriminals for fraudulent transactions. The campaign is linked to the “Go1ano developer” threat actor, known for distributing Android malware in Brazil, who recently promoted a tool called GHOST NFC CARD. Unlike ghost card fraud, which relies on fabricated numbers, PhantomCard directly transmits live NFC data, making it more dangerous. Though currently focused in Brazil, its use of NFC relay techniques signals the potential for global expansion, posing growing risks as contactless payments become more widespread.
Attack Method
PhantomCard employs a deceptive delivery method by posing as a “Card Protection” app on fake Google Play pages, reinforced with fabricated positive reviews to build credibility. Once installed, it immediately activates without requiring extra permissions, prompting the victim to scan their payment card. The malware then relays the captured NFC data to a criminal-controlled server, where it is transmitted to a terminal or ATM. To complete fraudulent transactions, PhantomCard also requests the victim’s PIN, effectively allowing attackers to use the card remotely as though it were physically present.
Operational Breakdown
PhantomCard reveals that the malware is not an original creation of the actor promoting it, but rather a customised version of the NFU Pay Malware-as-a-Service, a Chinese-origin platform known in underground markets alongside others like SuperCardX and KingNFC. Evidence such as debug strings in Chinese and references to NFU Pay in the source code confirm this link. The campaign’s tailoring to Brazil is evident in a command-and-control endpoint containing baxi, the Chinese term for Brazil, suggesting deliberate regional targeting. While currently configured for Brazilian banking users, the service’s adaptable design allows PhantomCard to be repackaged for other markets, broadening its global risk potential.
Technical Capabilities
PhantomCard’s core strength is its ability to relay NFC card data from a victim’s device to an attacker’s system in real time. Unlike earlier tools like NFCGate, PhantomCard is narrowly built to target the ISO-DEP (ISO 14443-4) standard used in EMV payment cards. When a victim scans their card, the malware sends commands to identify available applications and extract metadata. If the card is EMV-compatible, PhantomCard forwards the extracted data to its server, signaling it is ready for exploitation. A companion tool on the attacker’s side then mirrors the victim’s card activity, establishing a live bridge to a terminal or ATM, enabling fraudulent use as though the attacker held the card physically.
Following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| InitialAccess | T1660 | Phishing |
| Persistence | T1541 | Foreground Persistence |
| Defense Evasion | T1655 | Masquerading |
| Defense Evasion | T1628 | Hide Artifacts |
| Defense Evasion | T1633.001 | Virtualization/Sandbox Evasion: System Checks |
| Credential Access | T1417 | Input Capture |
| Discovery | T1426 | System Information Discovery |
| Collection | T1417 | Input Capture |
| Command andControl | T1437 | Application Layer Protocol |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that PhantomCard’s arrival signals a new challenge for organizations in securing mobile and contactless payments. As NFC- based banking becomes more common, companies may face increased pressure to monitor and mitigate threats stemming from seemingly legitimate applications, even from widely trusted sources. Employees who rely on mobile banking for work-related transactions could inadvertently become entry points for financial fraud, increasing operational risk. Moreover, the rise of resellers and tailored malware campaigns may allow threat actors to adapt rapidly to specific regional practices, potentially bypassing standard corporate defenses. This could force organizations to reassess internal policies on employee use of personal devices for financial interactions, as well as the reliance on mobile devices for transaction approvals or account management. Over time, the growing sophistication and accessibility of such malware could erode confidence in mobile payment tools, requiring more stringent risk assessment and monitoring protocols for staff interactions with banking apps.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule PhantomCard_Indicators
{
meta:
description = “Detects PhantomCard malware indicators” author = “CYFIRMA”
malware_family = ” PhantomCard” strings:
// SHA256 hashes
$sha256_1 = “a78ab0c38fc97406727e48f0eb5a803b1edb9da4a39e613f013b3c5b4736262f”
$sha256_2 = “cb10953f39723427d697d06550fae2a330d7fff8fc42e034821e4a4c55f5a667”
condition:
any of ($sha256*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
ShinyHunters – Advanced Sophistication Techniques and Potential Collaboration with Scattered Spider
About the Threat Actor
ShinyHunters is a prominent cybercriminal group, active since at least 2020, and primarily motivated by financial gains. The group has been associated with multiple high-profile data breaches impacting organizations worldwide. Their operations typically involve exploiting security vulnerabilities, and advanced social engineering attacks to gain unauthorized access to corporate databases. Following intrusion, they systematically exfiltrate sensitive information, including personally identifiable information (PII), login credentials, and financial records, which is subsequently monetized through sale or exposure on dark web platforms, and underground forums.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2024- 6387 | OpenSSH | 8.1 | Link |
| CVE-2025- 31324 | SAP NetWeaver | 10.0 | Link |
TTPs based on MITRE ATT&CK Framework for Enterprise & Mobile
| Tactic | ID | Technique |
| Reconnaissance | T1589.001 | Gather Victim Identity Information: Credentials |
| Reconnaissance | T1598 | Phishing for Information |
| Reconnaissance | T1598.001 | Phishing for Information: Spear phishing Service |
| Reconnaissance | T1598.004 | Phishing for Information: Spear phishing Voice |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access (Mobile) | T1451 | SIM Card Swap |
| Initial Access (Mobile) | T1660 | Phishing |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566.004 | Phishing: Spear phishing Voice |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1204 | User Execution |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1556.006 | Modify Authentication Process: Multi- Factor Authentication |
| Persistence | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Persistence | T1133 | External Remote Services |
| Persistence | T1136 | Create Account |
| Persistence | T1098.005 | Account Manipulation: Device Registration |
| Persistence | T1098.003 | Account Manipulation: Additional Cloud Roles |
| Persistence | T1098.001 | Account Manipulation: Additional Cloud Credentials |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1098.001 | Account Manipulation: Additional Cloud Credentials |
| Privilege Escalation | T1098.003 | Account Manipulation: Additional Cloud Roles |
| Privilege Escalation | T1098.005 | Account Manipulation: Device Registration |
| Privilege Escalation | T1484.002 | Domain or Tenant Policy Modification: Trust Modification |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1564.008 | Hide Artifacts: Email Hiding Rules |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1484.002 | Domain or Tenant Policy Modification: Trust Modification |
| Defense Evasion | T1656 | Impersonation |
| Defense Evasion | T1556.006 | Modify Authentication Process: Multi- Factor Authentication |
| Defense Evasion | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Defense Evasion | T1578.002 | Modify Cloud Compute Infrastructure: Create Cloud Instance |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1556.006 | Modify Authentication Process: Multi- Factor Authentication |
| Credential Access | T1556.009 | Modify Authentication Process: Conditional Access Policies |
| Credential Access | T1621 | Multi-Factor Authentication Request Generation |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.006 | OS Credential Dumping: DCSync |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Credential Access | T1552.004 | Unsecured Credentials: Private Keys |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1538 | Cloud Service Dashboard |
| Discovery | T1580 | Cloud Infrastructure Discovery |
| Discovery | T1217 | Browser Information Discovery |
| Discovery | T1087.004 | Account Discovery: Cloud Account |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1087.003 | Account Discovery: Email Account |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1069.003 | Permission Groups Discovery: Cloud Groups |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1021.007 | Remote Services: Cloud Services |
| Collection | T1530 | Data from Cloud Storage |
| Collection | T1213.002 | Data from Information Repositories: Sharepoint |
| Collection | T1213.003 | Data from Information Repositories: Code Repositories |
| Collection | T1213.005 | Data from Information Repositories: Messaging Applications |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1102 | Web Service |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1572 | Protocol Tunneling |
| Command and Control | T1090 | Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1657 | Financial Theft |
Latest Developments Observed
The threat actor is suspected of launching a wave of attacks against Salesforce, targeting high-profile organizations across multiple sectors through the use of coordinated ticket- themed phishing domains and Salesforce credential-harvesting pages, likely developed for recurring campaigns. The attack techniques appear consistent with past operations attributed to the Russian cybercriminal group Scattered Spider, suggesting potential collaboration between the two threat actor groups. Domain analysis indicates that financial services and technology service providers are the most probable targets in upcoming campaigns. The primary objective appears to be the exfiltration of sensitive data for subsequent monetization.
ETLM Insights
ShinyHunters are a sophisticated cybercriminal collective known for orchestrating data breaches. The group leverages advanced intrusion techniques to exfiltrate sensitive information from compromised organizations, subsequently monetizing the stolen data through underground markets and extortion schemes. Historically, the group has leveraged insecure APIs, misconfigured cloud environments, and credential-stuffing techniques to gain unauthorized access to targeted organizations.
Recent intelligence suggests a possible collaboration between ShinyHunters and Scattered Spider, amplifying both groups’ capabilities. Such cooperation indicates the use of highly advanced techniques and a clear strategy in defining targets and operational objectives, primarily focused on maximizing financial gain and reputational damage to victims.
The group’s evolving tactics highlight the need for heightened vigilance across industries, particularly for organizations that hold high-value customer or corporate data. Looking ahead, their operations may pivot towards more persistent and covert methods, including session hijacking or even insider recruitment. The group’s growing emphasis on exploiting the human element—through deception, impersonation, and other social engineering tactics – indicates a likely trajectory where social engineering becomes a primary attack vector, reinforced by the technical exploitation of cloud-integrated business ecosystems.
YARA Rules
rule ShinyHunters_CVE2024_6387_Targeting
{
meta:
author = “CYFIRMA”
description = “Detects indicators related to ShinyHunters targeting CVE-2024-6387 and specific domains”
date = “2025-08-19”
threat_actor = “ShinyHunters” strings:
$cve = “CVE-2024-6387”
$domain1 = “havenly.com”
$domain2 = “promo.com” condition:
any of ($cve, $domain1, $domain2)
}
Strategic
Management
Tactical
Poland failed a cyberattack on a big city’s water supply, and a Norwegian dam was sabotaged
A large Polish city could have had its water supply cut off as a result of a cyberattack, according to the country’s digital affairs ministry. Warsaw did not specify who was behind the attack or which city was targeted. The intrusion was detected and neutralized at the last moment, preventing any disruption to the water supply or sewage management.
According to the government, Poland successfully thwarts 99% of such attacks, and Warsaw emphasizes ongoing investments in cybersecurity, including nearly USD 2.7 billion allocated for 2025 and 2026 to bolster digital infrastructure.
This incident is part of a broader pattern of cyberattacks targeting Polish critical infrastructure, in what CYFIRMA describes as an ongoing cyber war with Russia. While the Polish government did not disclose the city or the perpetrators, it has hinted at Russian involvement, noting that Poland’s role as a hub for aid to Ukraine makes it a prime target for Russian cyberattacks.
Meanwhile, a similar but more serious case has been made public in Norway. The Norwegian Police Security Service (PST) linked a cyberattack on a Bremanger dam earlier this spring to pro-Russian hackers. In the incident, the attackers seized control of the dam’s systems, opening its floodgate and releasing over seven million gallons of water before the breach was detected and resolved within four hours. With the river well below flood levels, no damage occurred. PST has recently described the attack as a demonstration of the hackers’ capabilities rather than an intent to cause harm.
In other news, a recent report details a newly identified Russia-aligned advanced persistent threat (APT) group, dubbed “Curly COMrades,” targeting critical organizations in geopolitically sensitive regions. The group has attacked judicial and government institutions in Georgia and an energy distribution firm in Moldova, focusing on establishing persistent access and stealing credentials.
ETLM Assessment:
Since Russia’s invasion of Ukraine in 2022, Russian cyberattacks have surged across both Poland and Norway and Europe, largely as part of a broader pressure campaign to destabilize Ukraine’s allies. Poland, a key hub for military and humanitarian aid to Ukraine, has faced frequent targeting of its critical infrastructure. These attacks, often attributed to Russian state-sponsored groups like APT28 and Sandworm, aim to sow chaos, undermine public confidence, and strain NATO unity. Across Europe, energy grids, government networks, and financial systems have been hit with ransomware, data breaches, and disinformation campaigns, with incidents reported in Germany, Estonia, the Czech Republic, Moldova, Sweden, and Finland.
Ransomware based on Chinese APT
Researchers have issued a warning about a new ransomware family named “Charon,” deployed in a targeted attack against the Middle East’s public sector and aviation industry. The threat actor employed tactics, techniques, and procedures (TTPs) previously linked to the Chinese cyberespionage group Earth Baxia, though the researchers stop short of attributing the attack directly to them. The overlap in TTPs could indicate direct involvement, intentional mimicry, or independent development of similar methods. The report emphasizes a rising trend among ransomware operators adopting advanced techniques typically associated with state-sponsored actors.
ETLM Assessment:
Chinese Advanced Persistent Threat (APT) groups have traditionally focused on cyberespionage but have increasingly been observed adopting ransomware to enrich themselves while masking their primary objectives. Groups like ChamelGang and Bronze Starlight have been previously observed deploying ransomware strains such as CatB, LockFile, and RA World in targeted attacks against organizations in sectors like government, healthcare, and manufacturing across East Asia, India, and the Americas. These attacks often involve sophisticated tactics, such as using custom tools like HUI Loader and PlugX, previously exclusive to Chinese state-sponsored groups, to exfiltrate data and deploy ransomware for financial gain. By blending espionage with ransomware, these groups not only secure financial rewards but also use the disruptive nature of ransomware to obscure their data theft and maintain plausible deniability, complicating attribution efforts.
Qilin Ransomware Impacts Welcome Financial Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from South Korea, Welcome Financial Group (https[:]//www[.]welcomefg[.]co[.]kr/), was compromised by Qilin Ransomware. Welcome Financial Group, Korea is a huge ecosystem operating in the finance industry. The group provides banking, digitalization, payments, integrated asset management, distressed loans, residential leasing, and startup financing services to its clients. The exposed data reportedly includes the full database of all clients, containing names, dates of birth, residential and office addresses, bank account details, email addresses, and a wide range of other sensitive information. The total volume of compromised data is estimated to be around 1,024 GB.
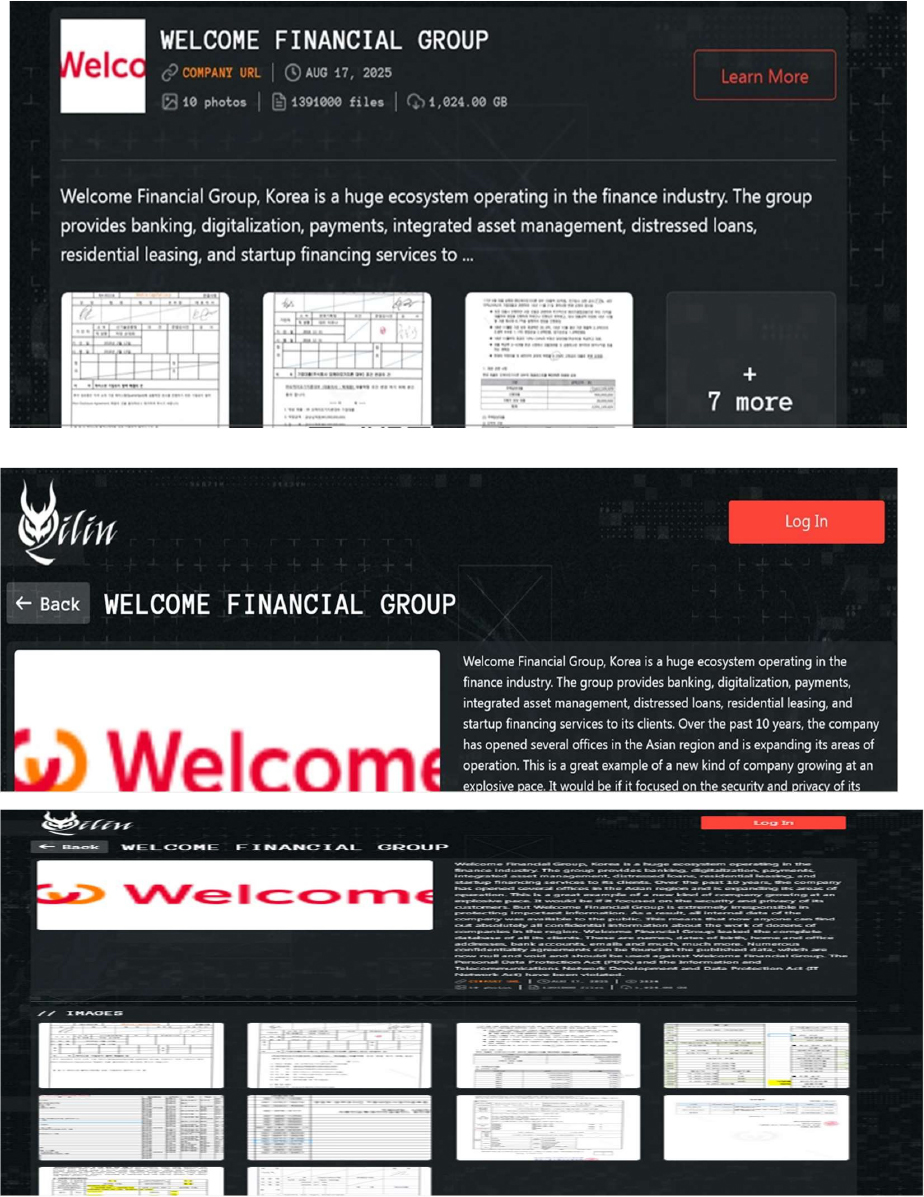
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Blacknevas Ransomware Impacts CK Power Public Company Limited
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, CK Power Public Company Limited (www[.]ckpower[.]co[.]th), was compromised by Blacknevas Ransomware. CK Power Public Company Limited, through its subsidiaries, generates and sells electricity and steam in Thailand and the Lao People’s Democratic Republic. The compromised data consists of confidential and sensitive information related to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, BlackNevas ransomware is a sophisticated and multifaceted threat with extensible capabilities and a partnership model to maximize the impact and profitability of their attacks.
Vulnerability in Intel Driver & Support Assistant Tool
Relevancy & Insights:
The vulnerability exists due to an uncontrolled search path element.
Impact:
A local user can gain elevated privileges.
Affected Products:
https[:]//www[.]intel[.]com/content/www/us/en/security- center/advisory/intel-sa-01321.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
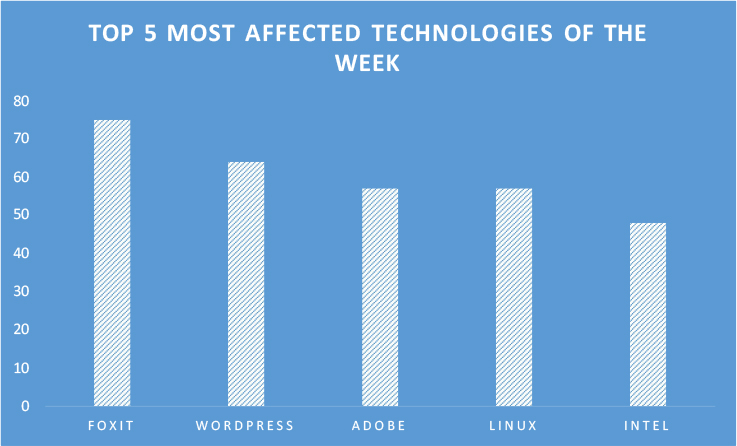
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerabilities in the Intel Driver & Support Assistant (DSA) Tool can pose significant risks because the tool runs with high privileges to scan hardware, detect outdated drivers, and install updates. Exploitation could allow attackers to escalate privileges, execute arbitrary code, or tamper with driver installations, potentially compromising the entire system. This impacts a wide range of users across industries where Intel- based devices are used, including enterprise IT environments, personal computing, and critical infrastructure relying on Intel hardware. Ensuring timely patching of the Intel DSA Tool, applying Intel security advisories, and restricting unnecessary administrative access are crucial steps to minimize exposure.
Dire Wolf Ransomware attacked and published the data of the Kingsford Development & LEADBUILD Construction Pte Ltd
Summary:
Recently, we observed that Dire Wolf Ransomware attacked and published the data of the Kingsford Development & LEADBUILD Construction Pte Ltd (https[:]//kingsford[.]com[.]sg) on its dark web website. Kingsford Development Pte Ltd, based in Singapore, is a subsidiary of the Kingsford Group. The group is engaged in real estate development, property management, and manufacturing, with operations extending across Singapore, China, and Australia. The ransomware attack has compromised approximately 200 GB of data, including financial records, sales information, project drawings, and other sensitive and confidential data extracted from the organization’s database.
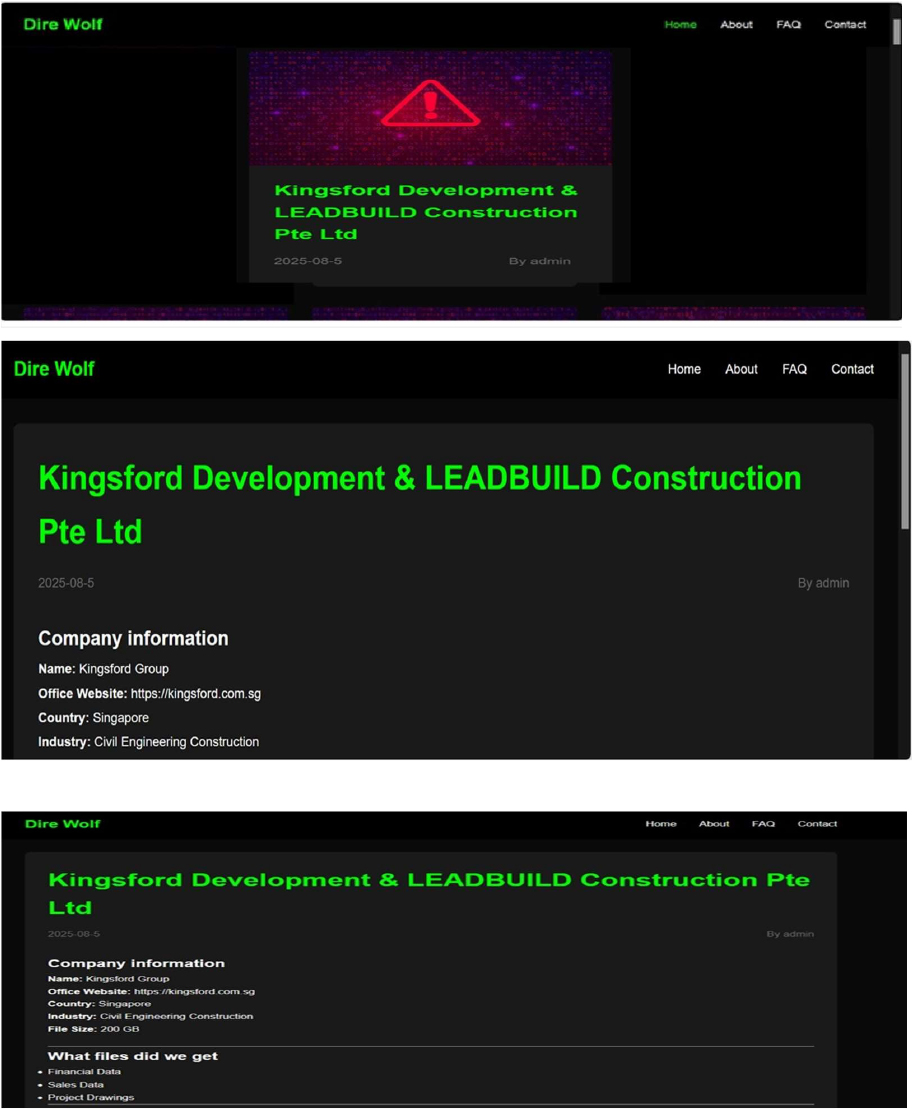
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
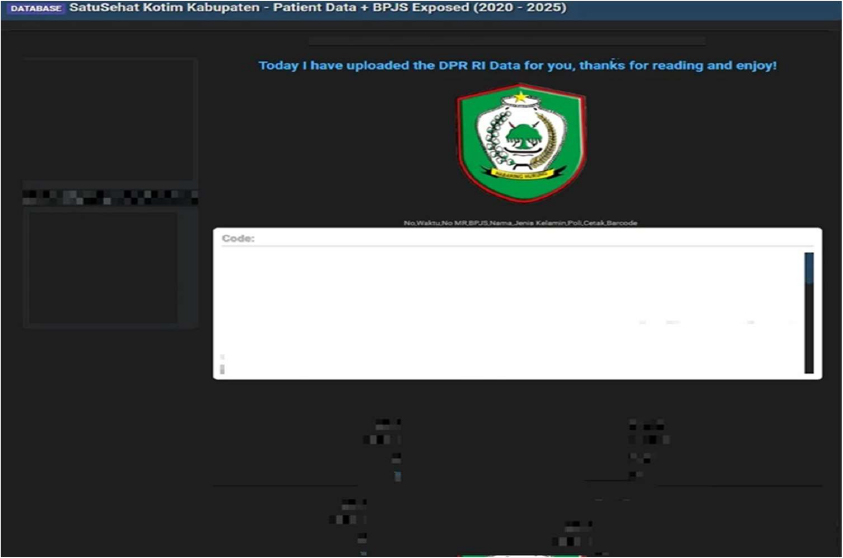
Indonesian Health Platform SatuSehat Kotim Kabupaten Data Advertised on a Leak Site
Summary: The CYFIRMA Research team has identified a threat actor allegedly leaking and attempting to sell a database linked to SatuSehat for the East Kotawaringin Regency (Kotim Kabupaten) in Indonesia. The database, reportedly containing sensitive patient information, was advertised on a dark web forum. As SatuSehat is Indonesia’s national health platform that consolidates patient records from multiple healthcare providers into a unified system, this incident represents a potentially serious data breach impacting a large number of individuals.
The post, made by a new user on the forum, includes a sample of the allegedly stolen data, which seems to span from 2020 to 2025. The database purportedly contains records from the Indonesian Social Security Administering Body for Health (BPJS Kesehatan). The threat actor is offering the full database for sale and has provided cryptocurrency wallet addresses for the transaction. This incident raises serious concerns about the security of citizen data within the national health system and the potential for misuse of the leaked information.
The leaked data sample includes the following types of information:
Thai retail company Data advertised on a Leak Site
Summary:
The CYFIRMA Research team has identified that the threat actor “Omerta” is allegedly offering for sale a complete customer and order database belonging to a Thai retail company with annual revenues exceeding $6 million. The dataset reportedly covers the period from 2021 to the present and contains around 2.3 million records with detailed customer and transactional information. The exposed fields include full names, contact details, residential addresses, payment data, order history, discount amounts, product information, and company account identifiers. The listing indicates a starting price of $50,000, bidding increments of $500, and a blitz price of $75,000.
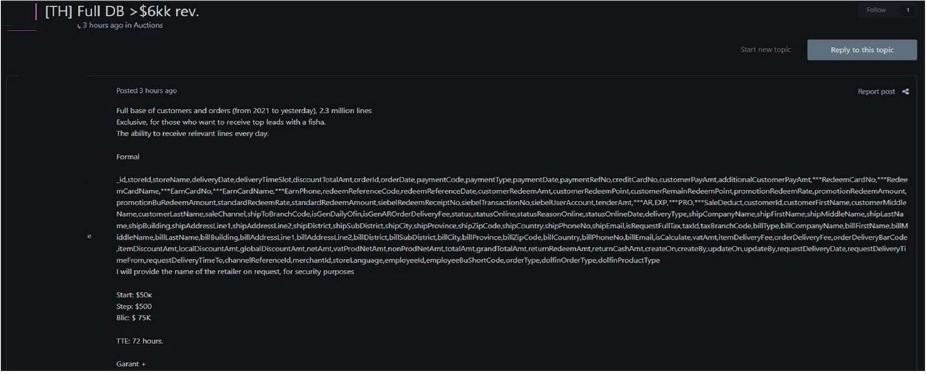
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Omerta” has recently surfaced as a highly active entity involved in data leak operations. Trusted sources have linked the group to several security breaches, including unauthorized system intrusions and efforts to monetize stolen data on dark web marketplaces. Their ongoing activities reflect the persistent and growing cyber threats emerging from underground forums. These incidents emphasize the pressing need for organizations to enhance cybersecurity through continuous monitoring, robust threat intelligence, and proactive defense strategies to safeguard sensitive information and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
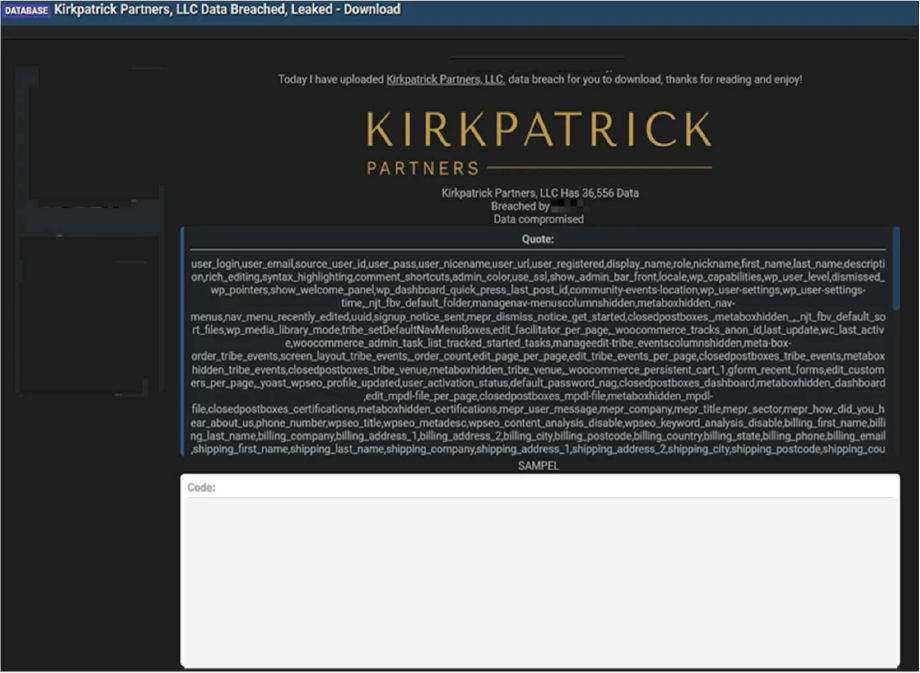
The CYFIRMA Research team observed that a threat actor has allegedly breached and leaked the database of Kirkpatrick Partners, LLC, a well-known firm specializing in providing training evaluation models and consulting services worldwide. The data, which was posted on a dark web forum, reportedly contains 36,556 user records. Kirkpatrick Partners is a significant player in the corporate and organizational training sector, utilized by numerous multinational corporations, government agencies, and even military entities to measure the effectiveness of their educational programs. The exposure of their user database could have wide- ranging implications for their clients and the individuals whose information has been compromised.
The leaked dataset appears to be comprehensive, containing a vast amount of both personal and professional information. An analysis of the data structure and samples provided by the threat actor indicates that sensitive user details have been exposed. The breach could potentially affect individuals from various high-profile organizations who have engaged with Kirkpatrick Partners’ services, including employees from government, military, and corporate sectors. This incident highlights the persistent threat of data breaches against service providers that hold valuable information on behalf of a diverse and important client base.
The compromised data allegedly includes a wide array of user information. Among the exposed data fields are:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
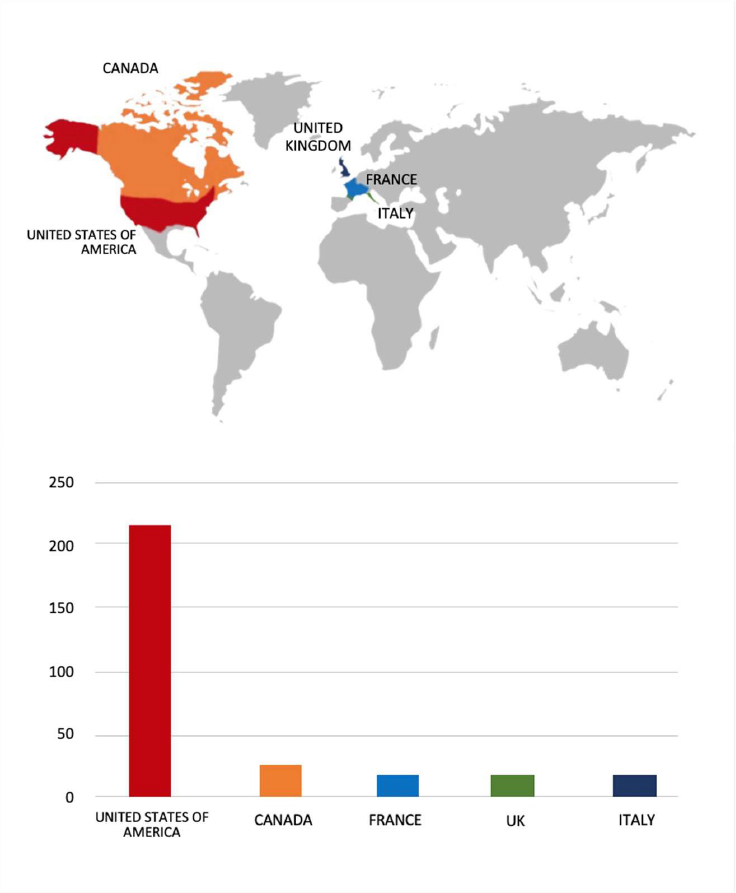
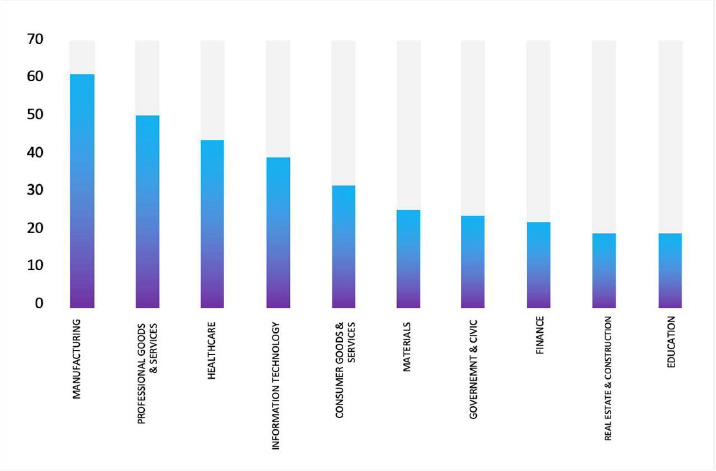
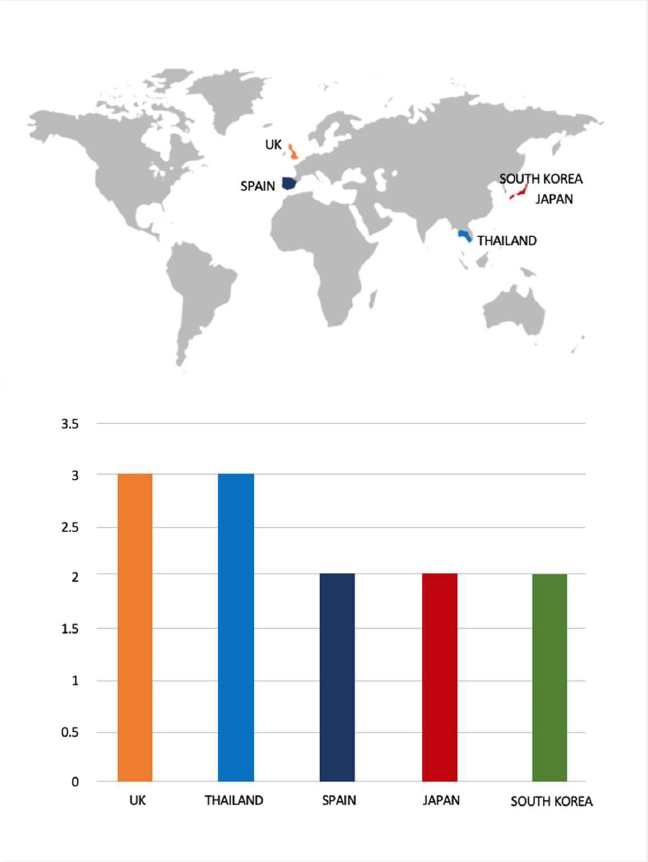
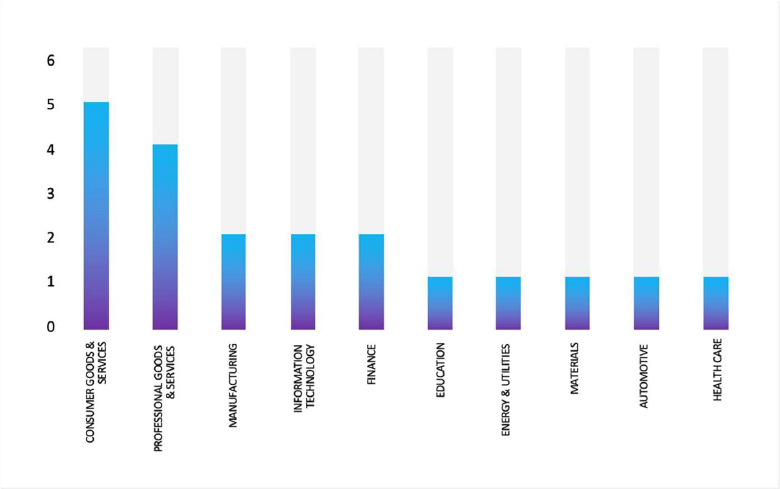
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness, intelligence, and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.