



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industries: Business Support Services, Heavy Construction.
Target Geography: United States of America.
Introduction
CYFIRMA Research and Advisory Team has found ransomware known as 3AM while monitoring various underground forums as part of our Threat Discovery Process.
1 3AM:
3AM is a new ransomware that has been coded using the Rust programming language. Its primary objective is to encrypt files stored on a victim’s computer. In addition to encryption, 3AM alters the filenames of the encrypted files by adding the “.threeamtime” extension. To communicate with the victim and demand a ransom for file decryption, the ransomware creates a ransom note titled “RECOVER-FILES.txt.”
It was employed in a ransomware attack by a threat actor who initially tried to deploy LockBit on a target’s network. However, when the attempt to deploy LockBit was thwarted or blocked, the threat actor swiftly switched to using 3AM.
There is still uncertainty surrounding any potential connections between the developers of 3AM and established cybercriminals.
The initial suspicious activity by the threat actor involved the utilization of the “gpresult” command to extract policy settings applied to a specific user on the computer. Additionally, the attacker executed various Cobalt Strike components and tried to elevate privileges using “PsExec.”
Subsequently, the attackers conducted reconnaissance through commands such as “whoami,” “netstat,” “quser,” and “net share.” They also sought to enumerate other servers for lateral movement using the “quser” and “net view” commands. Furthermore, they established persistence by creating a new user and employed the “Wput” tool to exfiltrate victims’ files to their FTP server.
Ransomware Analysis:
The ransomware is a 64-bit executable coded in the Rust programming language and is designed to recognize the following command-line parameters.
The command-line parameters “-m” and “-h” are exclusive options, and they cannot be used together. The usage of these parameters, with their respective values of “local” and “net,” closely resembles arguments utilized by the Conti ransomware group.
When the malware is executed, it attempts to run the following commands, most of which attempt to stop various security and backup related software:
Subsequently, the ransomware conducts a disk scan, encrypting any files that meet predefined criteria while simultaneously erasing the original files.
Following the encryption process, the malware tries to execute the command to delete volume shadow backup copies.
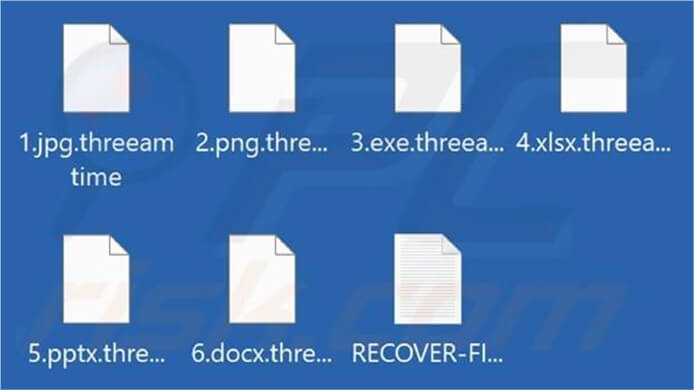
Screenshot of a Files Encrypted by 3AM Ransomware. (Source: Surface Web)
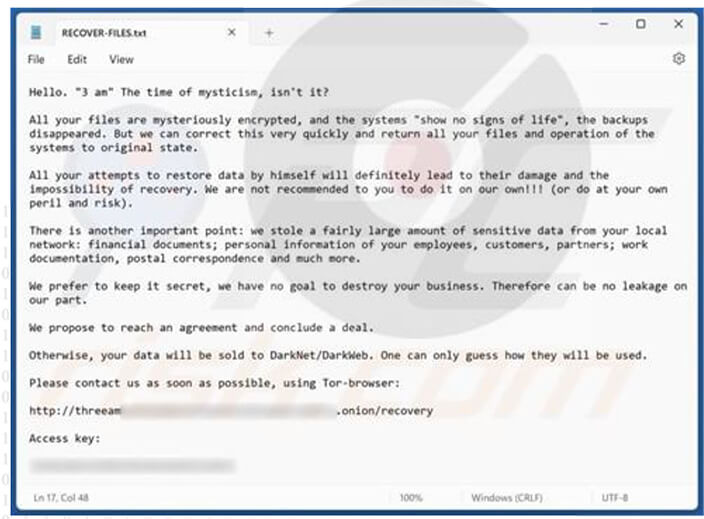
Ransom Note of 3AM (Source: Surface Web)
Geography targeted by 3AM Ransomware.
Relevancy and Insights:
ETLM assessment
CYFIRMA’s Assessment based on available information states that, the emergence of the 3AM ransomware, coded in Rust, and its deployment as a fallback option after the initial LockBit attempt highlights a growing trend of ransomware operating with a degree of independence and adaptability. The fact that 3AM was deployed in an actual attack suggests it may gain traction among threat actors. As for predictions, we can anticipate an increase in the usage of Rust-based ransomware variants like 3AM, as this programming language offers certain advantages to attackers. Moreover, the ability of threat actors to quickly switch to alternative ransomware strains poses a significant challenge for cybersecurity defenders. While all sectors and technology users face risks, organizations in sectors with valuable data should be particularly vigilant in strengthening their defenses against these evolving threats.
We will continue to monitor and provide a more comprehensive assessment when further information becomes available.
Following are the TTPs based on MITRE Attack Framework.
| Sr.No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002:Execution | T1059: Command and Scripting Interpreter |
| T1053: Scheduled Task/Job | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1548.002: Abuse Elevation Control Mechanism: Bypass User Account Control | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 5 | TA0007:Discovery | T1033: System Owner/User Discovery |
| T1049: System Network Connections Discovery | ||
| T1057: Process Discovery | ||
| T1087: Account Discovery | ||
| 6 | TA0011: Exfiltration | T1020: Automated Exfiltration |
| 7 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Cyber espionage, Stealing sensitive Information Threat Actor: Transparent Tribe (aka APT36)
Target Technology: Android OS
Target Entities: Military, Diplomat, Activist
Target Geographies: India & Pakistan
Active Malware of the Week
This week “CapraRAT” is trending
CapraRAT
The threat actor APT36, also known as Transparent Tribe, is a suspected Pakistani threat actor that targets military, diplomatic personnel, and the Indian Education sector. They distribute Android apps through their own websites and use social engineering to avoid the Google Play Store. Recently, researchers observed they are using Android apps resembling YouTube to distribute their ‘CapraRAT’, which acts as spyware, collecting data and accessing sensitive information.
Three packages associated with CapraRAT employ various deceptive tactics. Two packages impersonate the legitimate YouTube app to deceive users, while the third engages in romance-based social engineering by connecting to a YouTube channel attributed to a persona named “Piya Sharma.” This channel contains short clips featuring a woman in diverse locations. These tactics are used to entice users into downloading malicious content while masquerading as legitimate applications.
Attack Method
Initially, the malicious APKs are distributed outside of Google Play (Android’s official app store). This distribution method strongly suggests that victims are likely to be first enticed through social engineering to download and install them.
Connection to a YouTube Channel
A noteworthy discovery in researchers’ investigation involves a newly identified APK that establishes a connection with a YouTube channel owned by an individual named Piya Sharma. This YouTube channel features a collection of short clips featuring a woman in various locations. What makes this finding particularly intriguing is that the APK adopts both the persona and the name of Piya Sharma. This observation underscores the threat actor’s persistent use of romance-based social engineering techniques to entice and convince targets to install these applications. It is highly likely that Piya Sharma’s identity is being exploited as a linked persona within this scheme.
Analysis of CapraRAT
Researchers performed static analysis on two distinct YouTube-themed CapraRAT APKs.
Once the CapraRAT is up and running on the device, it performs the following actions:
Analysis of CapraRAT’s Configuration and Functionality
Upon launching the app, the ‘MainActivity’ utilizes a ‘load_web’ method to initiate a WebView object, loading the YouTube website. This approach results in a user experience distinct from the native Android YouTube app, resembling the viewing of YouTube through a mobile web browser within the trojanized CapraRAT app’s window. Because CapraRAT is a framework inserted into a variety of Android applications, the files housing malicious activity are often named and arranged differently depending on the app. Researchers have analysed the CapraRAT APKs, which contain the following files:
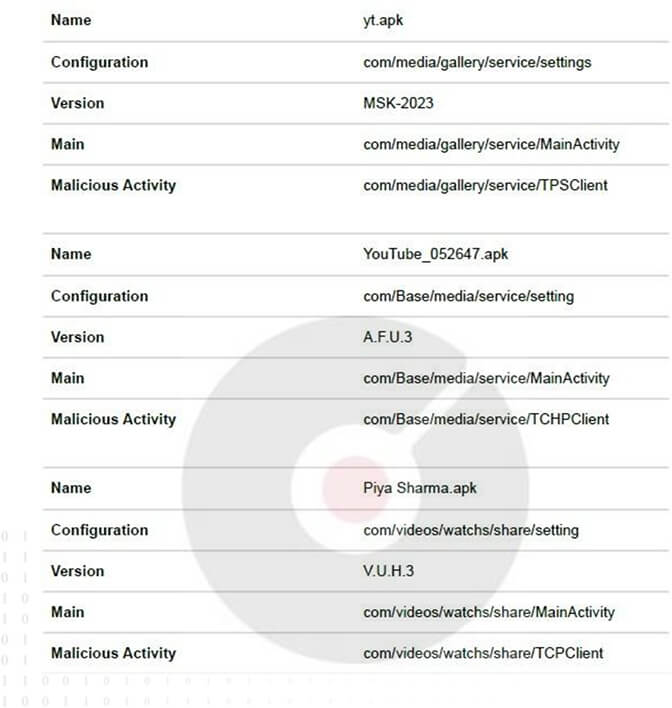
The CapraRAT configuration file, referred to interchangeably as “setting” or “settings,” contains default configuration data and versioning metadata. Notably, the version syntax in CapraRAT, such as “A.F.U.3” in YouTube_052647.apk and “V.U.H.3” in Piya Sharma.apk. However, it’s essential to note that these version numbers do not exhibit a clear connection to the C2 domains.
The ‘MainActivity’ plays a pivotal role in driving the application’s key features. This activity ensures persistence through the ‘onCreate’ method, utilizing ‘Autostarter,’ an open-source project that allows developers to automatically launch an Android application. It initializes the ‘TPSClient’ class as an object named ‘mTCPService.’ Subsequently, this method calls the ‘serviceRefresh’ method, creating an alarm at the interval specified in the settings file’s ‘timeForAlarm’ variable. In this case, the value ‘0xea60′ corresponds to 60,000 milliseconds, resulting in the alarm and persistence launcher running once per minute.’TPSClient’ contains CapraRAT’s commands, invoked through the ‘run’ method using a series of switch statements that map the string command to a related method. TPSClient has a method check_permissions() that is not in Extra_Class. This method checks the following series of Android permissions and generates a string with a True or False result for each:
C2 & Infrastructure
CapraRAT’s configuration file holds the C2 server address and port information. The domains used by the malware are associated with Transparent Tribe, and they appear to use Windows Server infrastructure for C2. Additionally, an IP address linked to one of the domains has a history of DNS tunneling lookups, suggesting possible prior infections or connections to other campaigns. The exact relationship between these campaigns remains unclear.
INSIGHTS
ETLM ASSESSMENT
From the ETLM Perspective CYFIRMA believes that CapraRAT is likely to continue evolving as a sophisticated and persistent threat, targeting organizations across various sectors. As organizations enhance their cybersecurity defences, CapraRAT may attempt to exploit emerging vulnerabilities or leverage social engineering tactics more effectively to gain access. CapraRAT’s specific capability to record audio and video, as well as access communication data, adds an additional layer of concern, as it may compromise the privacy of both employees and clients. This, in turn, could lead to complex legal and compliance challenges for organizations to navigate in the future.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Earth Lusca Deploys New Linux-based Malware SPRYSOCKS
Threat Actors: Earth Lusca
Attack Type: Web Attack
Objective: Espionage
Target Technology: Linux
Target Geographies: Asia and the Balkans
Target Industries: Government Sector
Business Impact: Operational Disruption
Summary
The China-based cyber threat group; Earth Lusca, has been identified as targeting government entities worldwide, using a new Linux backdoor called SprySOCKS. This group was first reported by researchers in January 2022 for its cyberattacks on public and private sector organizations across Asia, Australia, Europe, and North America. Earth Lusca, active since 2021, employs spear-phishing and watering hole attacks for cyber espionage. Recent cybersecurity findings confirm Earth Lusca’s ongoing activities, with an expanded focus on foreign affairs, technology, and telecommunications government departments, primarily in Southeast Asia, Central Asia, and the Balkans. The group initiates infections by exploiting known security vulnerabilities in various servers, allowing them to deploy web shells and execute Cobalt Strike for lateral movement. Their goals include document and email credential exfiltration, as well as deploying advanced backdoors like ShadowPad and a Linux version of Winnti for long-term espionage. SprySOCKS, the newly discovered Linux backdoor, is delivered alongside Cobalt Strike and Winnti. This backdoor has its origins in the open-source Windows backdoor Trochilus and is loaded using an ELF injector component called mandibule. It can gather system information, initiate an interactive shell, create and terminate SOCKS proxies, and perform file and directory operations. Earth Lusca’s SprySOCKS communication uses the Transmission Control Protocol (TCP) and appears to mirror the structure of a Windows-based trojan called RedLeaves, which itself is based on Trochilus. Multiple versions of SprySOCKS have been identified, indicating ongoing development and modification by the threat actors.
Relevancy & Insights:
To date, researchers have identified at least two distinct versions of SprySOCKS, denoted as versions 1.1 and 1.3.6. This discovery implies an ongoing process of modification and enhancement of the malware by the threat actors, as they continually introduce new features and updates
ETLM Assessment:
SprySOCKS is a recently discovered malware deployed by Earth Lusca to infiltrate government departments in Asia. Notably, Chinese threat actors, including Earth Lusca, have a history of employing malware like ShadowPad in cyber espionage campaigns across diverse industries. As these Chinese threat actors tend to utilize successful malware repeatedly, there’s a possibility that SprySOCKS may see increased adoption among other threat actors from China if it proves effective in achieving their objectives. This underscores the potential for SprySOCKS to become a more widespread tool in the arsenal of Chinese threat actors, following a similar trajectory to previously successful malware like ShadowPad.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Colombian government affected by a telecom provider cyberattack
A reported cyberattack has hit Colombian telecommunication provider; IFX Networks, and has affected the company’s customers, which include, according to statements by Colombia’s ICT Ministry at least twenty Colombian government agencies, as well as more than 700 companies in Latin America. The Colombian governmental agencies include the health ministry, the health regulator, and the superior council of the judiciary. Colombia’s cybersecurity unit (PMU Ciber) has established a command post to cope with the emergency. Many courts had to cease operations and the judiciary appears to have been particularly heavily struck.
Colombia’s President Gustavo Petro, while visiting New York for this week’s UN General Assembly, has been quoted that more than fifty government agencies were affected by a ransomware attack on a widely used telco provider (without direct reference to IFX), and stated that the attack’s widespread impact showed the company didn’t have the right cybersecurity measures in place and suggested this placed the company in breach of its contracted responsibilities. The Colombian government is now reportedly considering civil lawsuits and possibly criminal prosecution of IFX Networks over what Information and Telecommunications Minister Mauricio Lizcano characterized as failures in security protocols.
ETLM Assessment:
According to a preliminary assessment, the reported attack has been the work of a ransomware gang, probably motivated by financial gains. At this stage, however, a traditional cyberespionage operation covered by a ransomware attack cannot be ruled out.
A new Iranian cyberespionage campaign
Researchers are warning against a widespread campaign by Iranian state-sponsored actor; Peach Sandstorm (also known as HOLMIUM). The threat actor has been launching password-spraying campaigns against thousands of organizations since the beginning of the year, with a particular focus on the satellite, defense, and pharmaceutical sectors. According to researchers, Peach Sandstorm has succeeded in breaching at least several organizations and exfiltrating data and according to the researchers the capabilities observed in the campaign are concerning, as the attackers have been observed using legitimate credentials to authenticate to targets’ systems, persistent in targets’ environments, and deploy a range of tools to carry out additional activity.
ETLM Assessment:
The campaign seems to be a part of a widespread Iranian attempt to gain access to technologies and intellectual property, the country has been cut off by the international sanctions on the regime. There are likely more similar campaigns by other Iranian actors pursuing the same goals.
TSC is Impacted by Play Ransomware
Attack Type: Ransomware
Target Industry: Construction
Target Geography: The United States of America
Ransomware: Play Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]t-s-c[.]com), was compromised by Play Ransomware. TSC Services is a drilling contractor with equipment for their new builds and upgrades, including semisubs, drillships, jackups, and platforms. The data that was compromised has not yet been made public on the leak site, Play Ransomware leak site claims that the compromised data consists of confidential private and personal information, documents related to clients and employees, contracts, identification records, project details, financial information, and more.
The following screenshot was observed published on the dark web:
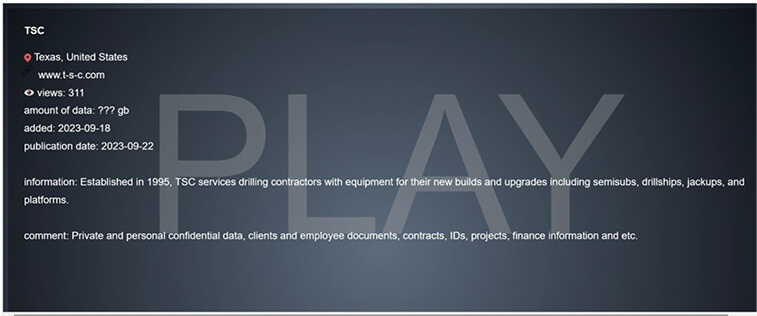
Source: Dark Web
Relevancy & Insights:
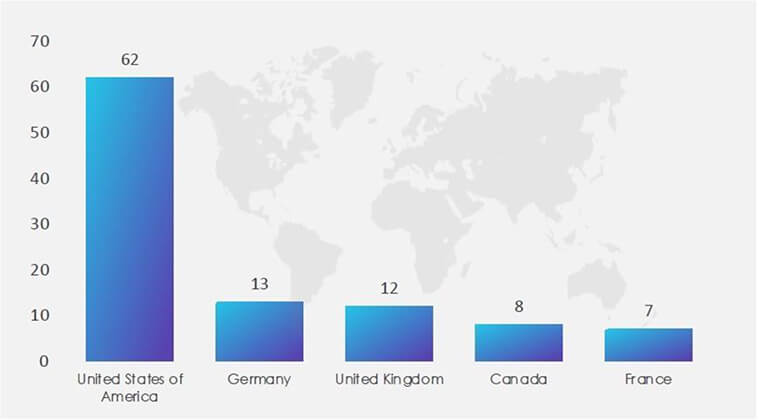
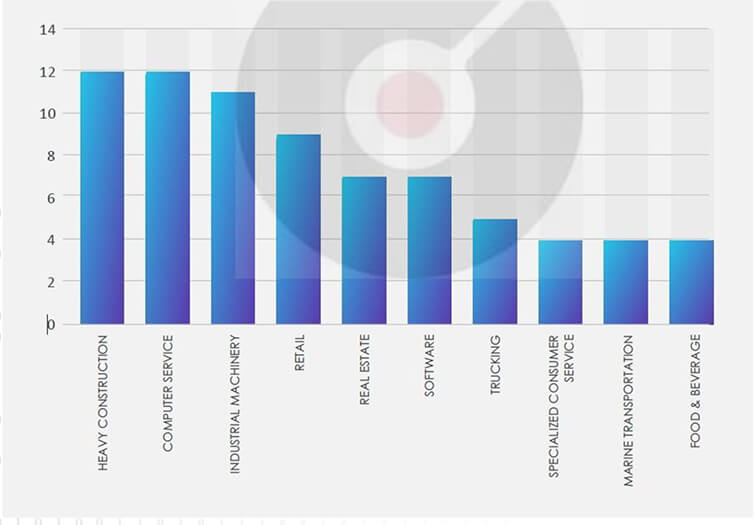
ETLM Assessment:
CYFIRMA’s assessment remains consistent: we anticipate that the Play ransomware will continue to target US-based companies, as illustrated in the graph above. Nevertheless, recent incidents like the TSC attack demonstrate that other major construction corporations are not immune to potential targeting.
Vulnerability in Trend Micro Endpoint Security Products
Attack Type: Vulnerabilities & Exploits
Target Technology: Antivirus software/Personal firewalls
Vulnerability: CVE-2023-41179 (CVSS Base Score 9.1)
Vulnerability Type: OS Command Injection
Summary:
The vulnerability allows a local user to escalate privileges on the system.
Relevancy & Insights:
The vulnerability exists due to improper input validation within the third-party AV uninstaller module shipped with the software.
Impact:
A local user can execute arbitrary commands with elevated privileges.
Affected Products:
https[:]//success[.]trendmicro[.]com/dcx/s/solution/000294994?language=en_US
Recommendations:
Apply the Vendor Patch: Ensure that the recommended patches and updates provided by Trend Micro are promptly applied to the affected systems.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 products most affected.
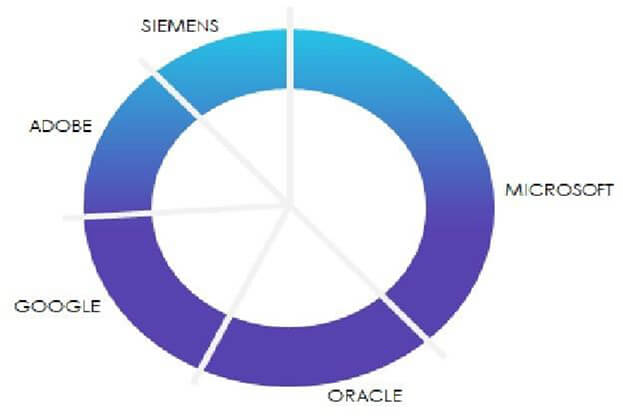
Pro-Russian DDoS attacks impact Canada
Threat Actors: NoName057(16)
Attack Type: DDoS
Objective: Operational Disruption
Target Technology: Web Application
Target Geographies: Canada
Target Industries: Government, Banking, and Transportation
Business Impact: Operational Disruption
Summary:
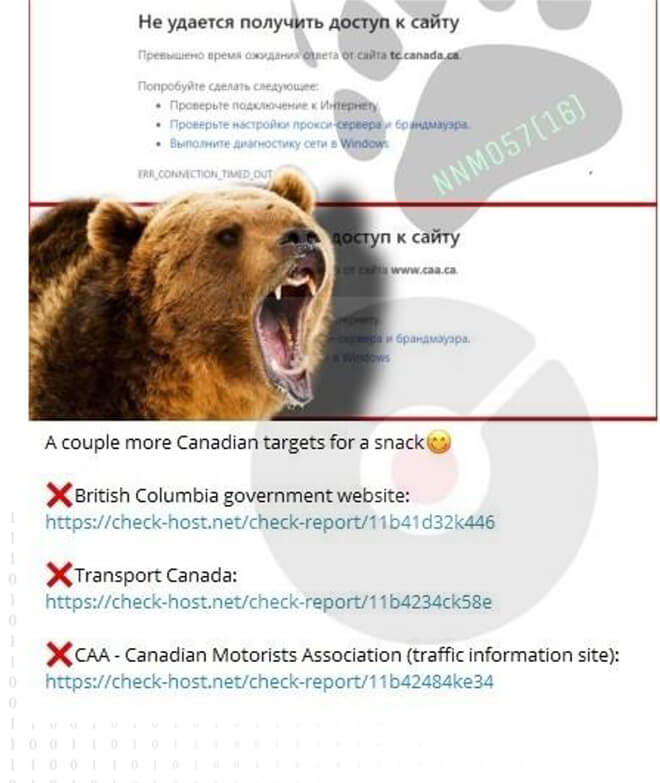
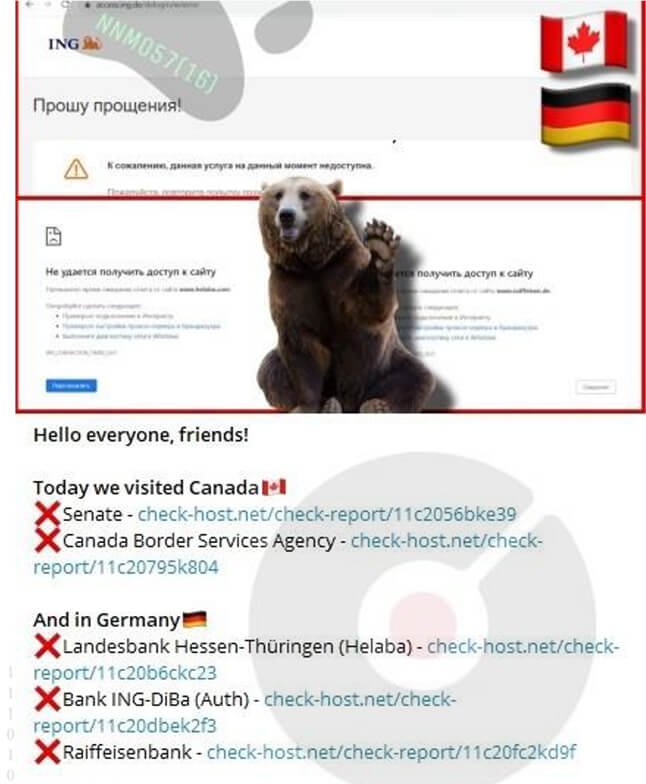
Lately, the Canadian government, banking sector, and transportation industries have experienced a surge in distributed denial of service (DDoS) attacks directed towards them. These illicit actions have been attributed to state-backed cyber threat actors affiliated with Russia. Starting in March 2022, NoName057(16), a hacktivist operator or group with pro-Russian leanings, has asserted accountability for numerous Distributed Denial of Service (DDoS) campaigns targeting entities in countries perceived as anti- Russian. The underlying infrastructure supporting NoName057(16) is hosted within Russia and is likely managed by individuals with expertise in system design and upkeep. Organizations’ web servers have been targeted by NoName057(16) using a botnet. The Canadian Centre for Cyber Security issued an advisory aimed at alerting the public to these incidents, raising awareness of potential impacts on government services, and providing guidance to organizations that may become targets of such illicit actions.
Source: Telegram
Relevancy & Insights:
Canada has experienced a series of distributed denial-of-service (DDoS) attacks on its government agencies, financial institutions, and transportation industries, and these attacks have been attributed to the pro-Russian cybercrime group; NoName057(16). The Canadian Centre for Cyber Security has confirmed that NoName057(16) has been targeting organizations’ web servers with the use of a botnet. Additionally, the alert highlighted the ongoing Russia-Ukraine conflict, noting persistent state-backed Russian cyberattacks against Ukraine and its allies.
ETLM Assessment:
CYFIRMA assesses there will be continued DDoS attacks on government, banking, and transportation sectors against NATO countries, by pro -Russian hacktivists.
Classblue Data Advertised in Leak Site
Attack Type: Data Leaks
Target Industry: Software
Target Geography: India
Target Technology: SQL Database
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
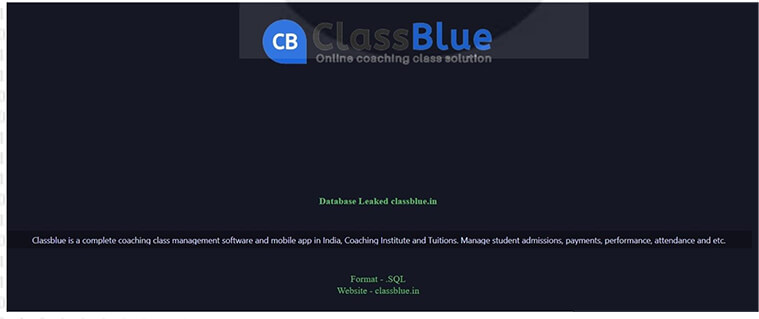
CYFIRMA Research team observed a potential data leak related to Classblue, {www[.]classblue[.]in}. Classblue is a complete coaching class management software and mobile app in India, that manage student admissions, payments, performance, attendance, etc. The compromised data comprises confidential information belonging to Classblue in SQL format.
Source: Underground forums
Relevancy & Insights:
Opportunistic cybercriminals driven by financial incentives are continually searching for exposed and susceptible systems and applications. Most of these attackers conduct their activities in clandestine online forums, where they engage in discussions related to their illicit pursuits, including the buying and selling of pilfered digital assets. In contrast to financially motivated groups like ransomware or extortion outfits, who often publicize their attacks, these cybercriminals prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications and systems to gain access and pilfer valuable data. Subsequently, the stolen data is advertised for sale in underground forums, circulated among other attackers, and repurposed for use in various illicit activities.
ETLM Assessment:
India remains one of the most targeted countries in the world by cybercriminals. CYFIRMA assesses that Indian institutions that do not have robust security measures and infrastructure will remain at high risk of potential attack.
CYFIRMA Research team observed a potential data leak related to the OTRS Group, {www[.]otrs[.]com}. The OTRS Group is a vendor and world’s leading provider of open- source help desk software; OTRS Help Desk, and the open-source IT Service Management (ITSM) software; OTRS ITSM. The data that has been compromised is in SQL format and includes both sensitive and confidential information, totalling 3GB.

Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS