



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
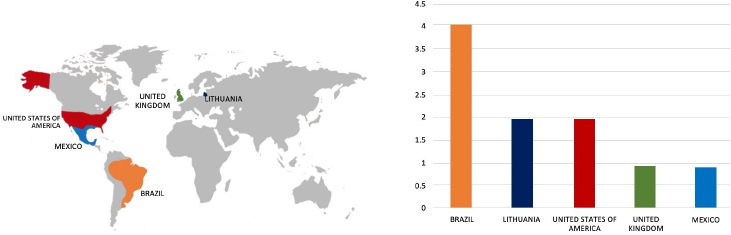
Target Geographies: Congo, Croatia, Italy and United States
Target Industries: Business Services, Construction, Education, Government, Manufacturing, Retail, Software, Telecommunications, and Transportation.
Introduction
CYFIRMA Research and Advisory Team has found El Dorado Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
El Dorado Ransomware
By the mid of June 2024 researchers discovered a new ransomware group called El Dorado, a ransomware variant originating from the LostTrust ransomware. It encrypts files, appends the “.00000001” extension to the filenames, and generates a ransom note titled “HOW_RETURN_YOUR_DATA.TXT”.

Screenshot of files encrypted by ransomware (Source: SurfaceWeb)
The ransom note informs victims of a network breach caused by vulnerabilities, leading to unauthorized access, data theft, and file encryption. It advises against terminating unknown processes, shutting down servers, or unplugging drives, as these actions could result in partial or complete data loss.
The note offers to decrypt a couple of files (up to 5 megabytes) for free, with the remainder decrypted upon payment. It warns that if the ransom is not paid, the stolen data will be published or sold to third parties.
Additionally, the ransom note includes instructions on how to contact the attackers via a live chat.

The appearance of El Dorado’s Ransom note (“HOW_RETURN_YOUR_DATA.TXT”) (Source: SurfaceWeb)

Countries targeted by El Dorado
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1547.009: Boot or Logon Autostart Execution: Shortcut Modification |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1547.009: Boot or Logon Autostart Execution: Shortcut Modification | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1112: Modify Registry | ||
| T1134: Access Token Manipulation | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 8 | TA0009: Collection | T1115: Clipboard Data |
| T1125: Video Capture | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis, based on available data, suggests that El Dorado ransomware is targeting economically affluent geographies such as the US, Asia, and Europe, while also expanding its reach globally. Given its sophisticated propagation methods through USB devices and exploitation of Windows Management Instrumentation (WMI), the ransomware is likely to continue evolving to bypass enhanced cybersecurity measures. It poses a persistent threat to industries like construction, software, and others with substantial revenues, emphasizing the need for heightened vigilance and proactive defence strategies.
Sigma
title: Suspicious Execution of Systeminfo tags:
– attack.discovery
– attack.t1082 logsource:
category: process_creation product: windows
detection: selection:
– Image|endswith: ‘\systeminfo.exe’
– OriginalFileName: ‘sysinfo.exe’ condition: selection
falsepositives:
– Unknown level: low
(Source: SurfaceWeb)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Espionage, Data Exfiltration Threat Actor: UTA0137
Target Geography: India Target Industry: Government
Target Technology: Linux OS (specifically the BOSS distribution)
Exploited Vulnerability: CVE-2022-0847 (DirtyPipe)
Active Malware of the Week
This week “DISGOMOJI” is trending.
DISGOMOJI
In 2024, a cyber espionage campaign targeting Indian government entities has been attributed to a suspected threat actor based in Pakistan, identified as UTA0137. This threat actor exclusively deploys a malware named DISGOMOJI. This malware, written in Golang, is specifically designed to infect Linux operating systems. This malware is a modified version of Discord-C2, leveraging Discord for command and control (C2) operations and using emojis for communication. This campaign involves using Linux malware to gain initial access, complemented by decoy documents targeted at Linux desktop users, a tactic uncommon in such attacks. It specifically targets Indian government entities relying on the BOSS Linux distribution for their desktop environments. Researchers have identified UTA0137 exploiting the DirtyPipe (CVE-2022-0847) privilege escalation vulnerability on “BOSS 9” systems, which remain susceptible to this aging exploit.
Technical Analysis
Researchers began their analysis with a UPX-packed ELF written in Golang, which arrived enclosed in a ZIP file. This ELF variant downloads a benign lure file named DSOP.pdf, presented to the victim during the attack. “DSOP” stands for India’s Defence Service Officer Provident Fund.

Fig: A portion of the PDF
Following its initial execution, the malware proceeds to fetch a subsequent payload named vmcoreinfo from the remote server clawsindia[.]in. This payload, identified as DISGOMOJI malware, is deposited into a concealed directory named .x86_64-linux-gnu within the user’s home directory.
DISGOMOJI, an UPX-packed ELF written in Golang, utilizes Discord for command and control (C2). It is a customized version derived from discord-c2, embedding a hardcoded authentication token and server ID within the ELF for server access. The malware dynamically creates a unique channel on the Discord server for each victim, enabling the attacker to interact individually through these channels. Channel names follow the format sess-%s-%s, where the first %s represents the victim’s operating system and the second
%s incorporates the victim’s username. Upon startup, DISGOMOJI initiates by sending a check-in message in the channel. This message includes essential information about the victim, such as:
DISGOMOJI achieves persistence on the system by utilizing cron, ensuring it remains active even after reboots with a @reboot entry in its crontab. Additionally, the malware downloads and executes a script called uevent_seqnum.sh. This script’s function is to monitor connected USB devices and copy files from them to a local folder on the system, enabling attackers to retrieve these files later.
Commands
DISGOMOJI monitors the command channel on Discord for new messages, employing an emoji-based protocol for C2 communication. Attackers send commands to the malware using emojis, with additional parameters when necessary. During command processing, DISGOMOJI responds with a “Clock” emoji () to indicate ongoing execution. After completing a command, the “Clock” emoji is replaced with a “Check Mark Button” emoji () to confirm execution.
Emoji commands available to the attacker include:

UTA0137 Post Infection Behavior
Researchers discovered several second-stage tools employed by UTA0137 post-infection, along with their general tactics, techniques, and procedures (TTPs). Key findings include:
In this campaign, researchers observed UTA0137 using the DirtyPipe (CVE-2022-0847) privilege escalation exploit against a system. Curious about the exploit’s relevance, researchers downloaded the latest BOSS operating system ISO from its official website. They discovered, similar to the attacker’s findings, that the DirtyPipe exploit remained effective against the OS, enabling escalation to root privileges.

DISGOMOJI Variations
Over time, UTA0137 has deployed various iterations of the DISGOMOJI malware. In a recent campaign, a new variant surfaced in the form of an UPX-packed ELF written in Golang. This variant initially downloads and displays IPR.pdf and IPR.jpg from ordai[.]quest, although their content remains inaccessible. These files are suspected to resemble “Immovable Property Return” lure documents used previously in Windows- targeted campaigns.
Additionally, the malware downloads and executes LAN_Conf.sh and WAN_Conf from the same domain. LAN_Conf.sh retrieves a copy of DISGOMOJI from ordai[.]quest/vmcoreinfo and adds crontab entries for persistence. It also handles the USB-stealing script uevent_seqnum.sh. Meanwhile, WAN_Conf enhances DISGOMOJI’s persistence by leveraging XDG autostart entries.
The latest DISGOMOJI variant shows advancements over earlier versions:
These enhancements indicate UTA0137’s evolving tactics to maintain operational continuity and evade detection.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolving tactics of UTA0137, particularly their use of DISGOMOJI and exploitation of vulnerabilities like DirtyPipe, pose significant challenges for organizations, especially those relying on Linux distributions such as BOSS. The sophisticated capabilities of DISGOMOJI, including data exfiltration and persistent access, threaten the security and integrity of organizational data on Linux-based systems. Future variants that evade detection and employ advanced social engineering tactics could heighten the risk of unauthorized access and data breaches.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Velvet Ant: A China-Nexus Threat Group’s Persistent Cyber Espionage Campaign
Summary:
In late 2023, researchers conducted a forensic investigation into a significant cyber- attack on a major organization, uncovering a sophisticated campaign orchestrated by a threat group known as Velvet Ant. This China-nexus state-sponsored group exhibited advanced capabilities and a meticulous approach throughout the attack, with their primary objective being to maintain prolonged access to the organization’s network for espionage purposes.
Velvet Ant gained initial access to the target organization’s network through various entry points, demonstrating a profound understanding of the network infrastructure. Leveraging a legacy F5 BIG-IP appliance exposed to the internet, they established a covert Command and Control (C&C) mechanism, facilitating persistent access to the network for over three years. This strategic foothold allowed the threat actors to meticulously execute their objectives without arousing suspicion.
Velvet Ant’s arsenal included the deployment of PlugX malware, a versatile remote access Trojan, utilizing sophisticated DLL hijacking techniques for payload execution. The malware’s modular plugin system afforded the threat actors a plethora of capabilities, enabling them to conduct reconnaissance, harvest credentials, and execute commands stealthily. Additionally, the threat group adeptly tampered with Endpoint Detection and Response (EDR) products to evade detection while moving laterally within the network, showcasing a high level of operational security awareness. Throughout the campaign, Velvet Ant demonstrated remarkable agility and adaptability, swiftly pivoting to new footholds and exploiting overlooked legacy systems. They utilized Impacket’s wmiexec.py tool for remote code execution, enabling seamless lateral movement across the network. Furthermore, the threat actors meticulously manipulated network traffic, utilizing a blend of legitimate and malicious activities to blend in with normal operations and evade detection.
Velvet Ant’s primary motive cantered around espionage, with a relentless focus on exfiltrating sensitive information from the target organization. Despite Researcher’s diligent efforts to remediate compromised systems and enhance security measures, the threat group persisted, employing sophisticated evasion techniques and maintaining a persistent presence within the network.
This detailed analysis underscores the critical importance of robust defence strategies against state-sponsored threats. Organizations must prioritize continuous monitoring, proactive threat hunting, and stringent security practices for both legacy and modern systems to effectively mitigate the persistent threat posed by sophisticated threat actors like Velvet Ant.
Relevancy & Insights:
The cyber-attack on a major organization by the China-linked threat actor ‘Velvet Ant’ underscores the evolving sophistication of state-sponsored cyber threats. Their campaign, focused on maintaining persistent network access for espionage, employed tools like VELVETSTING for command execution, VELVETTAP for data capture, and SAMRID, previously associated with other China-linked APT groups. This suggests coordination among threat actors and emphasizes the critical need for enhanced cybersecurity measures and global collaboration to mitigate such threats effectively.
ETLM Assessment:
Velvet Ant, a sophisticated China-nexus cyber espionage group, strategically targets East Asia, prioritizing industries with valuable data aligned with state interests. Their operations exhibit innovation, utilizing tactics like exploiting legacy systems, leveraging open-source tools for lateral movement, and deploying customized malware for persistent access and data theft. Notably, they employ infrastructure associated with other threat actors to evade detection, posing significant challenges to attribution efforts. The group’s ability to adapt and utilize diverse tactics underscores the evolving threat landscape, necessitating enhanced cybersecurity measures, particularly in monitoring legacy systems and detecting stealthy intrusions, to effectively counter such advanced adversaries.
Recommendations:

IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Europol disrupts jihadist information operations
An international law enforcement operation coordinated by Europol has seized thirteen websites operated by terrorist groups in a joint effort, known as Operation HOPPER II. The operation targeted key assets in the online dissemination of terrorist propaganda, including those of the so-called Islamic State, al-Qaeda, and its affiliates, and Hay’at Tahrir al-Sham. The operation specifically targeted terrorist-operated websites used to disseminate terrorist propaganda, thereby limiting the ability of terrorist organizations to recruit, radicalize, and mobilize recruiters online.
ETLM Assessment:
Disinformation and propaganda have been documented since the Roman empire, but rapid technological innovations in this area arguably have the potential to cause disastrous consequences. Evolutions in digital publishing and AI have enabled perpetrators to mimic the output of mainstream media outlets, pushing their agendas widely, inexpensively, and effectively, as the target audience is unable to differentiate between fake and legitimate reporting. Jihadi terrorists have been among heavy users of these tools and the Islamic State used them to recruit and coordinate perpetrators of its large-scale terrorist attacks in Russia and Iran in recent months.
Pakistani hackers target targets Indian entities
Researchers have recently described a cyberespionage campaign dubbed “Operation Celestial Force” that’s using the GravityRAT Android malware to target Indian entities and individuals belonging to defense, government, and related technology spaces with the operation being credited to a Pakistani nexus of threat actors tracked as “Cosmic Leopard.”
The campaign has been active since at least 2018 and continues to operate today — increasingly utilizing an expanding and evolving malware suite — indicating that the operation has likely seen a high degree of success. Cosmic Leopard (which exhibits some level of tactical overlap with the Transparent Tribe threat actor) has been predominantly observed employing spear-phishing and social engineering to establish trust with prospective targets, before sending them a link to a malicious site that instructs them to download a seemingly innocuous program that drops GravityRAT or HeavyLift depending on the operating system used.
ETLM Assessment:
This campaign constitutes a classic espionage effort enabled by cyber means and follows a campaign from last year when researchers observed SideCopy, a subdivision of Transparent Tribe, targeting the army of India and some organizations in academia. The researchers observed the threat actor using several honeytrap lures, either themed as defense procurement procedures or with a selection of officers for foreign assignments’ themes for the military and scientific conferences in case of academia. At least one Indian scientist was recently arrested for leaking sensitive information to Pakistani agents who honey-trapped him.
The Cactus Ransomware impacts the Sanyo-Shokai
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]sanyo- shokai[.]co[.]jp), was compromised by the Cactus Ransomware. Sanyo Shokai is involved in the design, manufacturing, and distribution of apparel through multiple channels, including department stores, specialty shops, and their own branded retail stores. They have a diverse portfolio of brands that cater to different market segments. The compromised data contains Personal identifying information, financial documents, customer data, engineering information, employee\executives personal files, corporate correspondence, etc. The total size of the compromised data is approximately 248 GB.
The following screenshot was observed published on the dark web:


Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Cactus ransomware is being spread through malvertising campaigns, where malicious ads lead users to compromised websites that download the DanaBot trojan. DanaBot serves as a backdoor for deploying Cactus ransomware, making the initial infection harder to detect. Based on the available information, CYFIRMA’s assessment indicates that Cactus Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Sanyo-Shokai, a prominent Retail company located in Japan, underscores the extensive threat posed by this particular ransomware strain in the Asia Pacific region.
The DarkVault Ransomware impacts the ZeepLive
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates; (www [.]zeeplive[.]co), was compromised by the DarkVault Ransomware. ZeepLive is a mobile application designed to facilitate social interactions through live video chats and streaming. Available primarily on Android, it offers a platform where users can meet new people, make friends, and engage in various live video chat sessions. The compromised data encompasses sensitive and confidential information pertinent to the organization.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:

ETLM Assessment:
The DarkVault ransomware group has honed its approach to deploying ransomware by leveraging a variety of sophisticated techniques. These include phishing emails, which lure victims into clicking on malicious links or attachments and exploiting vulnerabilities in unpatched software to gain initial access to systems. According to CYFIRMA’s assessment, DarkVault is likely to continue its aggressive targeting of a wide array of industries on a global scale. Their focus is particularly intense in the United States, Europe, and Asia. A recent attack on ZeepLive, a leading social media and entertainment company based in the United Arab Emirates, highlights the broad and severe threat posed by DarkVault, especially in the Middle East. This incident underscores the group’s capacity to disrupt operations and underscores the critical need for robust cybersecurity defenses across diverse regions and sectors.
Vulnerability in Dropbox Desktop
Summary:
The vulnerability allows a remote attacker to compromise the target system.
Relevancy & Insights:
The vulnerability exists as the affected application does not apply the Mark-of-the-Web to the local files when syncing files from a shared folder belonging to an untrusted account.
Impact:
A remote attacker can bypass the Mark-of-the-Web protection mechanism and execute arbitrary code on the system.
Affected Products: https[:]//www[.]zerodayinitiative[.]com/advisories/ZDI-24-677/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment:
Vulnerability in Dropbox can pose a significant threat to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Dropbox is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding online activities, including storing and accessing files, documents, and photos across different geographic regions and sectors.
8base Ransomware attacked and Published data of ISETO CORPORATION
Summary:
Recently we observed that 8base Ransomware attacked and published data of ISETO CORPORATION on its darkweb website. Iseto Corporation(www[.]iseto[.]co[.]jp) is a long-standing company based in Kyoto, Japan. Iseto has evolved from a paper wholesaler to a pioneer in information processing and document management services. Key Services include Information Processing, Business Process Outsourcing (BPO), Printing and Mailing, and Digital Solutions. The main trading partners are City banks, trust banks, regional banks, labor banks, credit unions, life insurance, non-life insurance, local governments, government agencies, credit card companies, leasing companies, electricity, gas, and cable television companies. The data leak, following the ransomware attack, encompasses Invoices, Receipts, Accounting documents, Personal data, Certificates, Employment contracts, Confidentiality agreements, Personal files, and Others.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that 8Base Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on ISETO CORPORATION, a prominent Information Technology company located in Japan, underscores the extensive threat posed by this particular ransomware strain in the Asia Pacific region.
DEPHUB.GO.ID (Indonesian Ministry of Transportation) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to DEPHUB.GO.ID (Indonesian Ministry of Transportation), { www[.]dephub[.]go[.]id} in an underground forum. The Ministry of Transportation of the Republic of Indonesia is a ministry in the Indonesian Government in charge of transportation affairs and is led by a Minister of Transportation. The dataset includes information on 30,000 employees. This data encompasses email addresses paired with default passwords and other sensitive and confidential details, formatted in SQL.

Source: Underground Forums
PT. BERCA KAWAN SEJATI data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to PT. BERCA KAWAN SEJATI, {www[.]pt-bks[.]com} in an underground forum. PT Berca Kawan Sejati (PT BKS) is a company based in Malang, East Java, Indonesia, specializing in the distribution of tobacco products. The company is dedicated to building a strong presence both domestically and internationally by offering high-quality tobacco products. The dataset includes detailed information on various records, such as IDs, salesman IDs, salesman names, client names, outlet names, phone numbers, and geographical coordinates (latitude and longitude), along with other sensitive and confidential details. The data breach is allegedly claimed by the threat actor ‘Sedapmalam’.

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s evaluation, the threat actor identified as ‘Sedapmalam’ represents a significant cyber threat to organizations across various sectors. Primarily financially motivated, ‘Sedapmalam’ engages in cyberattacks with the intent of exfiltrating sensitive data, which is subsequently sold on dark web marketplaces and underground forums. The typical targets of this threat actor are organizations with inadequate security frameworks, making them particularly susceptible to these attacks. Such vulnerabilities are exploited by ‘Sedapmalam’ to infiltrate systems, harvest confidential information, and monetize it through illicit channels.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data breach related to CBRE Group (www[.]cbre[.]com)(USA). CBRE Group, Inc. operates as a commercial real estate services and investment company worldwide. It operates through America, Europe, the Middle East, Africa, and Asia Pacific in Global Investment Management and Development Services segments. CBRE was breached by exploiting a recently found Atlassian Jira zero-day and was leaking its AWS config settings in the Jira. Compromised data contains Email Addresses, Passwords, Full names, IP addresses, and Dates.

Source: Underground forums
CYFIRMA Research team observed a potential data sale related to AMD ( The United States of America). A threat actor, IntelBroker, claims to be selling data obtained from a June 2024 breach of AMD, a major player in the computing industry. The compromised data reportedly includes a wide array of sensitive information, ranging from future product details to employee and customer databases. The alleged breach encompasses information on future AMD products, detailed technical specifications, employee and customer databases, property-related documents, ROMs, source code, firmware, and financial records. The hacker claims that the employee database includes personal and professional information such as user IDs, first and last names, job functions, business phone numbers, email addresses, and employee status.

Source: Underground forums
ETLM Assessment:
Threat Actor ‘IntelBroker’ group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.