



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware,
Target Technologies: MS Windows, Linux, and VMware ESXi servers.
Target Geography: Belgium, Colombia, France, Italy, Jordan, Lebanon, Mauritius, Netherlands, United States, United Kingdom.
Target Industry: Engineering, Education, Freight & Logistics Services, Health Care, Hospitality Manufacturing.
Introduction
CYFIRMA Research and Advisory Team has found a new NoEscape ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy
From the onset of its operation, the ransomware has targeted various industries, recent victims include:
This ransomware targets the widely used Windows Operating System, Linux, and VMware ESXi servers, which are prevalent across numerous industries and organizations.
NoEscape:
NoEscape ransomware functions as a Ransomware-as-a-Service (RaaS) platform, allowing other criminals to utilize it as affiliates or customers. The ransomware is written in C++, and around June 2023, used Chacha20 and RSA encryption algorithms.
It is speculated that the ransomware operation is a rebranding of Avaddon, a notorious ransomware gang that ceased its activities and publicly disclosed its decryption keys in 2021.
NoEscape ransomware and Avaddon’s ransomware share a nearly identical encryptor with only one significant change in encryption algorithms. While Avaddon used AES for file encryption, NoEscape has switched to the Salsa20 algorithm. The encryptors have similar encryption logic and file formats, including a distinct method called “chunking of the RSA encrypted blobs.”
There is a possibility that the NoEscape threat actors may have acquired the encryptor’s source code from Avaddon, as researchers believe that some key members of Avaddon are now involved in the new ransomware operation.
Upon execution, NoEscape ransomware is designed to delete Windows Shadow Volume Copies and local Windows backup catalogs. Additionally, it attempts to disable Windows’ automatic repair functionality.
The encryptor will then begin to terminate the following processes, including those associated with security software, backup applications, and web and database servers.
It will also stop the following Windows services associated with databases, QuickBooks, security software, and virtual machine platforms.
By terminating these applications, the ransomware aims to unlock files that might be currently open and prevented from being encrypted. This allows the ransomware to have unrestricted access to all targeted files for encryption.
In cases where files are locked and inaccessible, the NoEscape encryptor employs the Windows Restart Manager API to forcefully close processes or terminate Windows services that might be keeping a file open and obstructing encryption. This mechanism ensures that all targeted files can be encrypted without any hindrance.
During the file encryption process, the ransomware skips all files that have the following file extensions.
It will also skip files in folders whose names contain the following strings:
During encryption, researchers found that ransomware could be configured to use three modes:
NoEscape ransomware offers a configuration option that allows the encryptor to fully encrypt files with extensions such as accdb, edb, mdb, mdf, mds, ndf, and sql. The encryption process involves utilizing the Salsa20 algorithm, with the encryption key itself encrypted using an included RSA private key.
Encrypted files undergo a modification in their filenames, with a distinct 10-character extension appended to indicate encryption. This extension varies for each victim, ensuring uniqueness in file identification.
To maintain persistence on the compromised device and ensure automatic execution upon Windows login, the NoEscape encryptor creates a scheduled task named ‘SystemUpdate’. This task is configured to launch the encryptor, enabling it to continue its malicious activities in subsequent sessions.
For enterprise victims utilizing VMware ESXi, NoEscape offers a shell script specifically designed to restore the original /etc/motd file and facilitate the decryption process using the Linux decryptor.
The ransom demands associated with NoEscape ransomware range from hundreds of thousands of dollars to exceeding $10 million.
NoEscape strictly prohibits its members from targeting CIS (ex-Soviet Union) countries. If victims from those countries are affected, they receive free decryptors along with detailed information about the breach methods used against them.

Screenshot of files encrypted by NoEscape Ransomware. (Source: Surface Web)
The ransomware will also change the Windows wallpaper to an image telling victims they can find instructions in the ransom notes named HOW_TO_RECOVER_FILES.txt.

Screenshot of NoEscape’s desktop wallpaper. (Source: Surface Web)
On Linux systems, the NoEscape ransomware replaces the /etc/motd (Message of the Day) file with the ransom note. Consequently, when victims log in to their Linux-based devices, they are greeted with the ransom note displayed in place of the typical message.

Screenshot of Ransomnote of NoEscape Ransomware. (Source: Surface Web)

Countries Targeted by NoEscape Ransomware
Insights:
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques / Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1053: Scheduled Task/Job | ||
| T1053.005: Scheduled Task/Job: Scheduled Task | ||
| T1059: Command and Scripting Interpreter | ||
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 3 |
TA0003: Persistence |
T1053: Scheduled Task/Job |
| T1053.005: Scheduled Task/Job: Scheduled Task |
||
| T1543.003: Create or Modify System Process: Windows Service |
||
| T1574.002: Hijack Execution Flow: DLL Side- Loading |
||
| 4 |
TA0004: Privilege Escalation |
T1053: Scheduled Task/Job |
| T1053.005: Scheduled Task/Job: Scheduled Task |
||
| T1134: Access Token Manipulation | ||
| T1543.003: Create or Modify System Process: Windows Service |
||
| T1574.002: Hijack Execution Flow: DLL Side- Loading |
||
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.009: Obfuscated Files or Information: Embedded Payloads | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information |
||
| T1497: Virtualization/Sandbox Evasion | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks |
||
| T1562.001: Impair Defenses: Disable or Modify Tools |
||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0006: Credential Access | T1056: Input Capture |
| 7 | TA0007: Discovery | T1007: System Service Discovery |
| T1012: Query Registry | ||
| T1016: System Network Configuration Discovery | ||
| T1049: System Network Connections Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| T1614.001: System Location Discovery: System Language Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056: Input Capture |
| 10 | TA0011: Command and Control |
T1105: Ingress Tool Transfer |
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery | ||
| T1529: System Shutdown/Reboot |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
SIGMA Rule
title: Change PowerShell Policies to an Insecure Level – PowerShell tags:
– attack.execution
– attack.t1059.001
logsource:
product: windows
category: ps_script
definition: ‘Requirements: Script Block Logging must be enabled’
detection:
cmdlet:
ScriptBlockText|contains: ‘Set-ExecutionPolicy’
option:
ScriptBlockText|contains:
– ‘Unrestricted’
– ‘bypass’
– ‘RemoteSigned’
filter:
# – ParentImage: ‘C:\ProgramData\chocolatey\choco.exe’ Powershell event id 4104 do not have ParentImage
ScriptBlockText|contains:
– “(New-Object System.Net.WebClient).DownloadString(‘https://community.chocolatey.org/install.ps1’)”
– “(New-Object System.Net.WebClient).DownloadString(‘https://chocolatey.org/install.ps1’)”
– ‘\AppData\Roaming\Code\’
condition: cmdlet and option and not filter
falsepositives:
– Administrator script
level: medium
(Source: Surface Web)
Type: Remote Access Trojan (RAT)
Objective: Espionage, Digital Advertising Fraud & Password spraying Target Technology: Routers
Active Malware of the Week
This week “AVrecon” is trending.
AVrecon
Researchers have uncovered a sophisticated, multi-year cyber campaign that targets small-office/home-office (SOHO) routers worldwide. The campaign involves infecting routers with a Linux-based Remote Access Trojan (RAT) known as “AVrecon.” This malware has remained undetected for over two years, with a single instance of highlight in May 2021.
Additionally, they uncovered a massive botnet attacking SOHO routers, making it one of the largest in recent history. The attackers collect information about the victim’s router, transmit it to an embedded C2 domain, and then connect the infected system to a set of second-stage C2 servers. Using commercial telemetry analysis, the researchers identified 15 distinct second-stage C2s. By analysing the information connected to their x.509 certificates, they concluded that some of these second-stage C2s have been operational since at least October 2021. During a 28-day investigation, over 70,000 distinct IP addresses communicated with these servers, and 41,000 nodes were persistently infected, interacting with the second-stage servers for at least two days within the 28-day period.
Attack Method
The research analysis on AVrecon revealed that it was written in C and designed to target ARM-embedded devices, providing portability across different architectures. Once deployed on an infected system, AVrecon performs three main actions:
Checking for other instances
The malware, AVrecon, follows a specific sequence of actions during its installation process on the host machine. First, it checks for existing instances of itself by searching for processes on port 48102 and creates a listener on that port. If successful, it records the process ID in the file “jid.pid” in the tmp directory. If there’s already a service on port 48102, it terminates any processes that don’t match the current ID and then kills any process bound to the port. The malware does not use any other ports during installation. If all previous attempts fail, AVrecon is programmed to delete itself entirely from the host machine.
Gathering host-based information
AVrecon gathers host-based information from the infected machine, such as kernel details (uname), CPU information, memory usage, the bin path of its location, and the hostname. Once it obtains this data, the malware utilizes pre-built functions to create a remote shell for executing commands, downloading additional binaries, and setting up a proxy. The complete list of actions performed by AVrecon is organized and identified by command numbers. The following screenshot shows the command numbers and their functionality.

Fig: Command numbers and their functionality
Building C2 parameters
Once AVrecon gains freedom of movement on the infected system, it starts building the parameters for its C2 (command and control) communications. The malware is equipped with an embedded C2 configuration, but it checks if any prior C2 configurations already exist on the infected host. If none are found, it uses the C2 parameters provided in the malware’s configuration.
To check for existing C2 configurations, AVrecon searches for legitimate files named “nvram” or “xmldbc” in the “bin” and “sbin” directories. It then looks for specific variables (memasik, domik, urlik, and portik) previously set by the malware within these files. If any of these programs are found with the respective variables, the malware extracts the encrypted C2 components, which include session cookies from previous sessions, domain, URL, and port information. If any of the four variables are not found, AVrecon attempts to read and decrypt the configuration from the file “/tmp/dnssmasq.pid.” If this fails as well, it decrypts the hardcoded domain, URL, and port information from the embedded C2 configuration.
Observed Activity
The research analysis shows that the threat actor employed the infected machines for two main purposes: clicking on Facebook and Google ads, likely for advertising fraud, and interacting with Microsoft Outlook, possibly for password spraying and data exfiltration.
Cybercriminals are able to bypass certain standard network-based detection tools, especially those relying on geolocation, autonomous system-based blocking, or IP address-based rate limiting, due to the use of a global network of compromised SOHO routers. This network grants them increased anonymity and enables them to carry out their malicious activities with reduced detection risks.
Global Telemetry Analysis
Bot Analysis – The researchers analysed second-stage IP addresses associated with AVrecon and looked for connections over specific ports (e.g., 80, 8000, 5178). They identified around 70,000 unique IP addresses that made connections to 15 servers. Upon further examination, they found that more than 45,000 IPs only communicated with one of the C2s for one to two days, suggesting that these devices might have been infected and then either fixed or abandoned. Devices communicating with the C2s for more than two days were considered persistent, resulting in a botnet size of about 41,100 devices. The average lifespan of a bot in this network was approximately seven days, indicating a substantial botnet where any device could be used for malicious activities at any time.
Command and Control Analysis – During the analysis, the researchers observed traffic patterns from the bot level and examined telemetry associated with a core set of 15 second-stage servers. Out of these, 12 servers communicated with a higher-tier server located at IP address 51.15.19[.]245 for 30 consecutive days. The use of a tiered architecture in the backend is a common tactic seen in other well-known botnets like Emotet and Qakbot.
A notable finding was when the researchers scanned the higher-tier IP address on ports 25 and 465, they discovered the domain zerophone[.]cc. This domain was previously mentioned in a historical analysis of AVrecon from 2021. The domain had a sample associated with it that was compiled for multiple router architectures (ARM, MIPS, and MIPSEL), indicating that the threat actor was targeting various SOHO router architectures prevalent in the market.
INSIGHTS
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
Lazarus Group Distributes Malware by Exploiting a Vulnerable IIS Server
Summary:
In a recent observation, it was found that the Lazarus APT group has been actively targeting Microsoft Internet Information Services (IIS) servers to gain unauthorized access and carry out malicious activities. Researchers have confirmed that Lazarus operators are using vulnerable Windows servers as malicious code distribution servers. The group employs techniques such as watering hole attacks, manipulation of domestic websites, and exploitation of INISAFE CrossWeb EX V6 vulnerabilities for malware distribution. Despite patches for the INITECH vulnerability, recent exploits continue to leverage compromised IIS servers for malware distribution. In their attacks on IIS servers, Lazarus targets insecure web servers and attempts lateral movement via Remote Desktop Protocol (RDP). They exploit vulnerable web servers by installing web shells or executing malicious commands through the IIS web server process, w3wp.exe. The attackers use privilege escalation malware, specifically JuicyPotato, to overcome limitations and execute desired malicious actions within the process.
JuicyPotato is used to execute Loader malware, which decrypts and executes encoded data files in memory. The final executed malware is typically a downloader or backdoor. Lazarus also exploits the INISAFE vulnerability to install additional malicious code, such as “SCSKAppLink.dll,” which serves as a download source for the IIS web server.
Insights:
Lazarus frequently exploits vulnerable IIS servers to distribute malware, indicating a strong preference for this type of attack. It is relatively easy to use IIS-based exploits, without being detected so Lazarus employs this attack method very frequently. Detecting these exploits can be challenging, as they are less common compared to web-shell-based attacks. The backdoors are concealed within legitimate modules within directories, and their code structure often mimics that of clean modules. To defend against IIS-based attacks, network defenders should implement best security practices, including regular updates of security procedures, stringent management of highly privileged accounts, and the utilization of anti-virus software.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Reports of Russia’s Troll Factory Demise Found Premature.
The Internet Research Agency’s demise as reported on by mainstream media in recent weeks now seems premature. The agency was founded by Yevgeny Prigozhin, a Russian businessman who made headlines recently after he led a mutiny via his other business – the private military company Wagner – against the Russian Ministry of defense during its war with Ukraine – You can read the full report on the mutiny here – https[:]//www[.]cyfirma[.]com/outofband/who-are-the-wagner-pmcs-of-russia-is-there-a- risk-of-a-cyber-fallout/
The agency, known as The Troll Factory plays an important role in influencing domestic public opinion and vilifying the opposition, as ordered by the Kremlin, such as meddling in elections in countries deemed hostile to Kremlin, undermining social cohesion, and promoting pro-Russian narratives or supplying autocrat support packages, which are a combination of traditional tools of political marketing services with fake social media activity, used to support the power of various autocrats from Africa and Asia or projecting false image of popular support to third country audiences.
It appears that the blackout of Mr. Prigozhin’s own media properties was both temporary and exaggerated. The Internet Research Agency is among those companies of Prigozhin’s media empire that have remained in business, despite earlier reports to the contrary. As predicted by CYFIRMA analysts earlier, the core information operations and psy-op part of the media group was too important for the Kremlin to be shut down. It is yet not clear whether the company remained in operation or is being restructured and resurrected, possibly under the leadership of a different pro-Kremlin oligarch. Analysts mostly speculate about the banker Yuri Kovalchuk, who owns most of the privately operated media in the country and who is one of the closest friends and allies of Vladimir Putin, since his initiation of the Ukraine war. The Kremlin-sponsored information operations on social media, most notably Twitter and facebook seem to be back almost on the pre-mutiny level and are not likely to die down soon.
Chinese State Hackers Targeting British MPs
The British Parliament’s Intelligence and Security Committee (ISC) has recently reported on Chinese cyber espionage activities in the UK. According to the committee, “In relation to the cyber approach, whilst understanding has clearly improved in recent years, China has a highly capable cyber – and increasingly sophisticated cyberespionage – operation: however, this is an area where the ‘known unknowns’ are concerning. Work on continuing coverage of its general capabilities must be maintained, alongside further work on Chinese offensive cyber and close-proximity technical operations.” The 200+ pages report which concludes on an inquiry started in 2019, also found that “China frequently targeted Parliamentarians in their cyber operations” and that given the sophistication of Chinese state-sponsored hackers “the level of resource dedicated to tackling the threat has been completely inadequate.”
The warning about China’s operations being “increasingly sophisticated” was written months ago, but coincidentally published on the same day Microsoft announced a Chinese hacking group had exploited a bug in its cloud email service to spy on more than two dozen organizations and government agencies in the U.S. and Europe.
The committee echoed warnings by security researchers and other Western governmental bodies as well as intelligence experts that China’s large and highly effective cyber espionage capability has had considerable success penetrating foreign government and private sector IT systems to gain intelligence or steal intellectual property. CYFIRMA has recently reported on the Chinese IP theft strategy, You can read the full report here – https[:]//www[.]cyfirma[.]com/outofband/china-ip-theft-report/
Aspen Technology is Impacted by Cl0p Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]aspentech[.]com), was compromised by Cl0p Ransomware. Aspen Technology, together with its subsidiaries, provides software & services in the United States, Europe, and worldwide. It operates through two segments, Subscription and Software, and Services. The compromised data might contain sensitive and confidential information concerning the organization, totalling approximately 46 GB in size.
The following screenshot was observed published on the dark web:

Source: Dark Web
Insights:
Recently, the Cl0p ransomware gang has acknowledged its role in the data-theft incidents involving MOVEit Transfer, where servers belonging to numerous companies were compromised through the exploitation of a zero-day vulnerability. This confirmation aligns with Microsoft’s attribution of these activities to the hacking group known as ‘Lace Tempest,’ also recognized as TA505 and FIN11.
Recently creators of Cl0p ransomware have been observed to have developed a version that specifically targets Linux operating systems. In comparison to the Windows version, this variant differs in several ways. For instance, it does not exempt any particular files or folders (along with their extensions) from encryption. Moreover, it employs the same techniques for reading and writing data, unlike its Windows counterpart, which opts for distinct approaches. Additionally, the ransom note generated by the Linux variant is in plain text, and it does not conduct validation, while creating an RC4 key. The Linux variant is not compatible with command line parameters and utilizes flawed logic for generating an RC4 key.
Summary:
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Insights:
GE CIMPLICITY is vulnerable to a heap-based buffer overflow, caused by improper bounds checking. By persuading a victim to open a specially crafted file, a remote attacker could overflow a buffer and execute arbitrary code on the system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable systems.
Affected Products: https[:]//www[.]cisa[.]gov/news-events/ics-advisories/icsa-23-199-06
Anonymous Sudan alleges responsibility for executing a ‘warning’ Distributed Denial of Service (DDoS) cyberattack against PayPal.
Summary:
Recently, the hacktivist collective known as “Anonymous Sudan” asserted that it conducted a preliminary “test attack” targeting PayPal. In a Telegram message attributed to this cybercrime group, a warning was issued, indicating their intention to intensify their assaults on various organizations, including those within the UAE, utilizing their preferred method of Distributed Denial of Service (DDoS) attacks. Subsequent reports reveal that the group has indeed targeted multiple UAE websites, including the government portal and Dubai Electricity
In a brief 30-second test attack on PayPal, the group asserted that it successfully caused the online payment gateway to exhibit an error message, specifically stating “User reports indicate problems at PayPal.” Following this incident, the group shared a post on Telegram, declaring their intention to meet with PayPal again soon, suggesting further confrontations are planned.
Insights:
Anonymous Sudan asserts collaboration with hacker collectives such as KillNet and Revil to execute more extensive cyberattacks, notably employing DDoS techniques. These hacktivists purport that their endeavors are aimed at combatting anti-Islamic sentiments. However, there are suspicions that they receive support from Russian state-controlled entities. Additionally, they proclaim their intention to utilize PayPal as a means to confront organizations in the United States and the United Arab Emirates
The purported assault on PayPal, assuming it took place, is not the initial occurrence of such an incident. In a previous instance this year, the company alerted 35,000 users about brute force attacks aimed at pilfering login credentials. Furthermore, in December of the preceding year, unauthorized access to the system by a different group resulted in a data breach.
IndiHome Data Advertised in Leak Site
Attack Type: Data Leak
Target Industry: Media and Telecommunication
Target Geography: Indonesia
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to IndiHome, {www[.]indihome[.]co.[id]}. IndiHome as a leading fixed broadband service, owned by PT Telkom Indonesia (Persero) provides three main services, Internet, Telephone, and Interactive TV. IndiHome is the market leader for fixed broadband services in Indonesia with more than 8.5 million subscribers. The leaked information consists of IP addresses, genders, first names, national identification numbers (NIK), and email addresses.
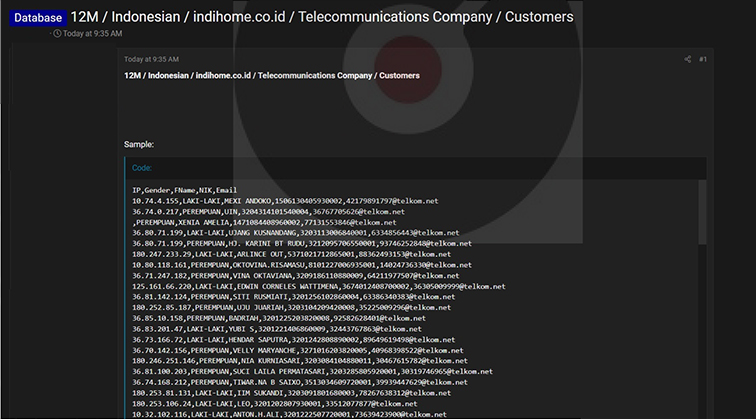
Source: Underground forums
Insights:
There are constantly vigilant cybercriminals driven by financial motives, who actively seek out exposed and vulnerable systems and applications. Most of these attackers operate in clandestine online communities, engaging in discussions and trading stolen digital assets. Unlike ransomware or extortion groups that often publicize their attacks, these attackers prefer to work discreetly. They exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. The stolen information is subsequently advertised, sold, and repurposed by other attackers for their own malicious purposes.
CYFIRMA Research team observed a potential data leak related to Atspace, (www[.]atspace[.]com) Atspace is a web hosting company that provides hosting services for websites. It offers various hosting plans, including free hosting with limited features and premium hosting with more advanced options. The data made available to the public includes a customer database containing names, email addresses, and other sensitive information.
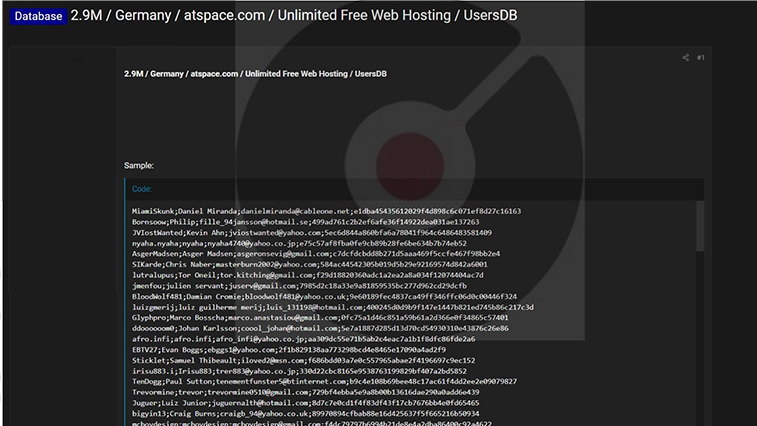
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS