



Key Intelligence Signals:
Transparent Tribe aka APT36 Targets Education Industry in India
Summary:
In recent activity, APT 36 also known as the Transparent Tribe, targeted India’s Education sector with a spear phishing attack. The threat actor is known for targeting the Military and Indian Embassies in different countries. In this event, the threat actor was seen targeting the Indian education sector by employing spear phishing attacks. The observed attack is not very sophisticated and resembles the previous campaign. The malicious document carried by phishing mail stages Crimson RAT using Microsoft Office macros or OLE embedding. Upon opening the malicious document macro code gets executed. The macros create and decompress an embedded archive file in the %ALLUSERSPROFILE% directory (C:\ProgramData) and then execute the final payload of Crimson RAT. A few macros inserted text in the document posing as education-themed- content about India. In another technique, the threat actor used Microsoft’s Object Linking and Embedded technology. The threat actor uses a “View Document” graphic to suggest that the document content is inaccessible. This manipulates innocent users to click on the graphic, triggering an OLE package that stores and executes Crimson RAT disguised as a software update.
Insights:
It is not confirmed which educational institution was targeted. Another same-lookalike campaign was observed in the previous year using the same RAT, tactic, and techniques. However, the employing of the old OLE embedding technique was observed in this attack.
The motive of the threat actors in their past campaigns has been to acquire valuable intelligence and establish dominance over India. It is likely that their current operation aims to infiltrate prestigious academic institutions such as the Indian Institute of Technology which has sensitive research programs running across the branches.
DeathNote, a subgroup of North Korea’s Lazarus Group, is running an ongoing remote access Trojan (RAT) campaign. Since 2022, this campaign appears to have a particular focus on the African defense industry and targets the defense sector. Researchers report that DeathNote’s campaigns initially breached the defense companies via a Trojanized, open-source PDF reader sent via Skype messenger. Once executed, the PDF reader creates a legitimate file and a malicious file in the same directory on the infected machine. DeathNote then used a technique known as DLL side loading to install malware for stealing system information and downloaded a sophisticated second-stage remote access Trojan (RAT) called Copperhedge from an attacker-controlled command-and-control server (C2).
The same group is also believed by researchers to be behind the 2020 campaign targeting European aerospace and defense contractors, in which the threat actor utilized social media, especially LinkedIn, to deliver malicious software disguised as job descriptions or applications to gain the trust of unwitting employees. In both cases, the motive seems to be traditional and industrial espionage.
Researchers have recently commented on the observations that Russia’s military intelligence GRU has lately increasingly turned to ransomware as a tool of cyber warfare against the neighboring country. Researchers present the finding as a sign of weakness since GRU is the main cyber operator on behalf of the Kremlin and its tooling shift probably means it doesn’t have the resources to rely on writing or modifying custom malware.
An increase in disruptive ransomware attacks in Ukraine during the most recent phase of operations was a defining feature. This fresh wave of disruptive attacks seemed to depart from the historical pattern, even though some of the attacks resembled disruptive attacks observed in earlier rounds. The assaults conducted from October to December used GRU clusters to deploy ransomware variants on targeted networks, in contrast to earlier attempts that focused on quick turnaround operations employing CADDYWIPER variants. This change is compatible with IRIDIUM’s (Russian APT operating under GRU) Prestige ransomware distribution in Poland.
CERT Polska, Poland’s cybersecurity authority, has recently warned that a unit of Russia’s SVR foreign intelligence service known as Cozy Bear or APT29 is actively pursuing diplomatic targets in many nations, principally European NATO members with traditional espionage goals in mind. In all observed cases, APT29 hackers used spear phishing techniques, sending emails impersonating embassies of European countries to select personnel at diplomatic posts. An invitation to a meeting or to collaborate on documents was included in the letter. An apparent link to the ambassador’s schedule, meeting information, or a downloaded file was included in the message body or in an attached PDF document. Polish authorities advise organizations to adjust their configuration to safeguard themselves from Cozy Bear’s meddling.
The Russian hacktivist auxiliary NoName057 has recently claimed responsibility for a distributed denial-of-service (DDoS) attack against Hydro-Québec, the largest power generation company in the province and huge exporter of electricity to the neighboring state of New York. The website of the power generation and distribution company in Québec has shut down as well as the company’s mobile app. Power generation and distribution, however, were unaffected, nor were customer data compromised. This attack was one in a series recently, where Russian cyber auxiliaries hit Canadian targets as a means of punishment for Canadian defense material support of Ukraine in its defense against Russian aggression.
CYFIRMA Research team observed a potential data leak related to (www[.]calamp[.]com)-CalAmp offers a range of services and products in the field of IoT, including software applications, cloud-based solutions, data analytics, telematics products, and networked services. It is headquartered in the United States of America. The leaked data includes client information, card details, and other related data.
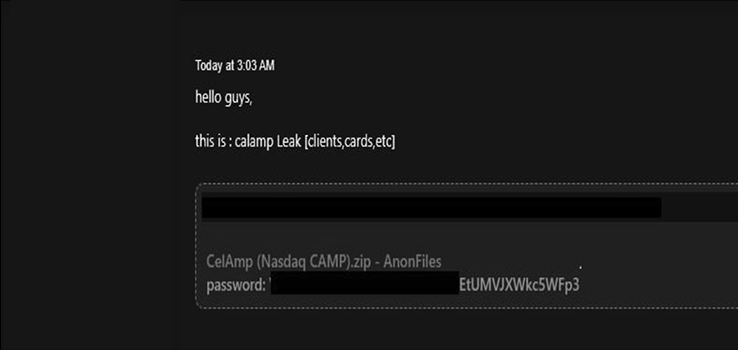
Source: Underground forums