



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found blackZluk ransomware while monitoring various underground forums as part of our Threat Discovery Process.
blackZluk
Researchers recently uncovered a new ransomware strain called blackZluk. blackZluk is a ransomware variant that encrypts files on compromised systems.
Once executed ransomware will encrypts files and append their filenames with a “.blackZluk” extension. Post the encryption a ransom note titled “#RECOVERY#.txt” was created.
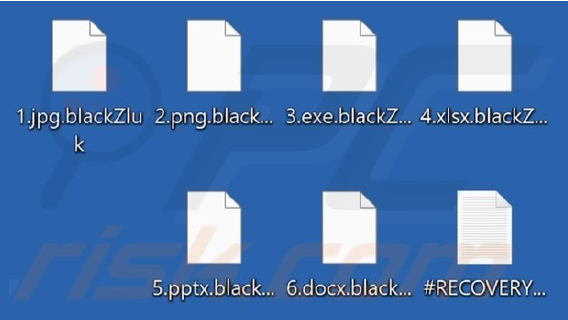
Screenshot of files encrypted by this ransomware (Source: SurfaceWeb)
The blackZluk ransomware note tells the victim that their company network has been hacked. Because of this, files were locked and important data was stolen.
The note warns that using anti-virus software, changing the locked files, trying to unlock them yourself, or asking others for help – could lead to losing the data forever.
To get the files back, the victim must pay a ransom. If they don’t, the stolen data (like company secrets, financial info, and personal details of employees and customers) will be made public. The note also explains the possible consequences of this data being leaked.
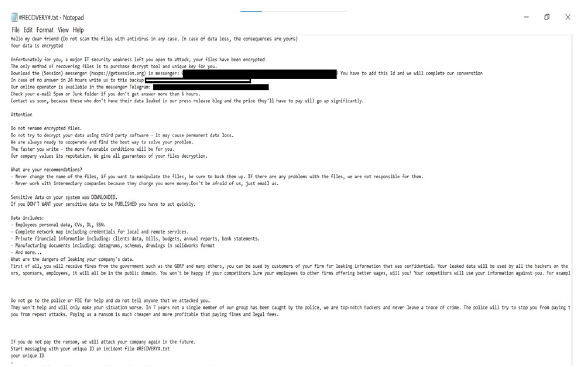
Appearance of blackZluk ransomware’s text file “#RECOVERY#.txt” (Source: SurfaceWeb)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1574.002: Hijack Execution Flow: DLL Side- Loading |
| 3 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1202: Indirect Command Execution | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| T1555.003: Credentials from Password Stores: Credentials from Web Browsers | ||
| 6 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614.001: System Location Discovery: System Language Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System |
| T1056: Input Capture | ||
| T1119: Automated Collection | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1105: Ingress Tool Transfer | ||
| 10 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
Based on available data, CYFIRMA’s assessment reveals that the BlackZluk ransomware strain poses a significant threat to sectors such as manufacturing, finance, healthcare, and others, with a clear focus on targeting enterprises rather than individuals. BlackZluk deletes Volume Shadow Copies to obstruct data recovery and modifies registry settings to ensure persistence. The ransom note emphasizes that beyond file encryption, BlackZluk leverages data theft and threatens to expose sensitive corporate information to pressure victims into paying. To counter these risks, organizations must implement robust cybersecurity strategies and stay informed with the latest threat intelligence to defend against such attacks.
SIGMA Rule:
title: Boot Configuration Tampering Via Bcdedit.EXE tags:
– attack.impact
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection_img:
– Image|endswith: ‘\bcdedit.exe’
– OriginalFileName: ‘bcdedit.exe’ selection_set:
CommandLine|contains: ‘set’ selection_cli:
– CommandLine|contains|all:
– ‘bootstatuspolicy’
– ‘ignoreallfailures’
– CommandLine|contains|all:
– ‘recoveryenabled’
– ‘no’
condition: all of selection_* fields:
– ComputerName
– User
– CommandLine falsepositives:
– Unlikely level: high
(Source: SurfaceWeb)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing Financial Information, Remote Access, Data Exfiltration
Target Technology: Android OS
Target Industries: Banks and Financial Institutions
Active Malware of the Week
This week “TrickMo” is trending.
TrickMo
In the evolving landscape of mobile threats, TrickMo stands out for its advanced techniques and severe impact. Researchers have identified a new variant of the TrickMo banking Trojan targeting Android devices, which incorporates sophisticated anti-analysis features such as malformed ZIP files, JSONPacker, and dropper apps. These updates make detection and analysis more challenging. TrickMo, which evolved from TrickBot, allows threat actors to expand their reach in the Android environment. The analysis also uncovered critical command-and-control (C2) structures and exfiltrated sensitive data such as credentials and pictures. This compromise poses risks beyond banking fraud, including potential identity theft and exposure to multiple attackers due to unprotected access to the stolen data.
Evolution of TrickMo
TrickMo was first identified in 2019 as a malware designed to facilitate financial fraud by intercepting one-time passwords (OTPs) and two-factor authentication (2FA) used in secure banking transactions. Primarily targeting European banking apps, particularly in Germany, TrickMo represents the mobile adaptation of the TrickBot group’s malicious activities, which originally focused on Windows systems. As cybersecurity defenses improved, TrickMo emerged to exploit Android devices, evolving with advanced obfuscation and anti-analysis techniques to evade detection and hinder cybersecurity professionals’ efforts.
Key Features of TrickMo
Technical Analysis
TrickMo is distributed via a dropper app disguised as Google Chrome. After installation, it prompts users to update Google Play services. If the update is confirmed, an APK containing TrickMo is installed under the name “Google Services.” The app then asks users to enable Accessibility services through social engineering tactics, exploiting trust in familiar names. Once granted elevated permissions, TrickMo intercepts SMS messages, hides authentication codes, and performs overlay attacks to steal credentials. It can also bypass security features, making it highly effective for financial fraud and difficult to detect or remove.
Anti-analysis Mechanisms Dropper
Android droppers are apps designed to install additional applications on a device, often under the guise of legitimate updates. Threat actors exploit this update functionality to deceive users into installing a second, potentially malicious app. In this case, the dropper poses as a fake Chrome Browser APK and contains the TrickMo malware hidden in its assets. Droppers are effective in attacks due to their minimal fingerprinting and low permission requests, reducing detection chances. This particular dropper also incorporates anti-analysis techniques to further evade detection.
Malformed ZIP
The latest TrickMo variant employs malformed ZIP files as an anti-analysis tactic. This involves manipulating the APK by adding directories with names matching crucial files like AndroidManifest.xml and classes.dex. This obfuscation can cause errors or incomplete extractions during analysis, complicating the examination process and helping TrickMo evade detection. Despite these challenges, tools like apktool can still retrieve the AndroidManifest.xml file, revealing suspicious permissions and activities associated with Android banking trojans. These permissions allow the malware to intercept communications, access sensitive data, and alter device settings, with additional suspicious elements related to the package dreammes.ross431.in.
Unpacking
The application’s Manifest File references the package dreammes.ross431.in, which is absent from the original APK, indicating the use of a packing technique to obscure malicious components. Specifically, JSONPacker is employed to hide the malicious DEX file containing critical code for various functions. Upon launching the app, the payload is unpacked by the class com.turkey.inner.Uactortrust, which retrieves, decrypts, and loads the malicious DEX file from the path /data/user/0/dreammes.ross431.in/app_inflict/wF.json.
Capabilities of TrickMo
The unpacked DEX file of the TrickMo malware reveals its malicious capabilities, which include:
Additionally, TrickMo can execute HTML Overlay Attacks. It retrieves a list of installed apps, and upon receiving this list, the C2 server sends a “SaveHtml” command with a package name and overlay URL. This URL points to an HTML file used for overlay attacks, enabling the malware to inject deceptive pages into the device.
Command-and-Control (C2) Server Communication
The TrickMo Android banking trojan uses HTTP to communicate with its command-and- control (C2) server via a domain specified in its configuration. This channel allows attackers to send commands, exfiltrate data, and manage the malware’s operations. The initial HTTP POST request to the endpoint /c includes a JSON file detailing the infected device’s phone number, model, and installed apps. This information helps attackers customize their activities for each device. The malware also requests the Clicker configuration from the C2 server, maintaining ongoing control and adapting its tactics.
Clicker configuration
The Clicker configuration in TrickMo leverages the Accessibility Service to control infected devices through a combination of a Clicker class and a clicker.json file stored in the asset’s directory. This file can be updated from the C2 server and contains package names for which the malware can perform automated actions, such as accepting permissions. The Clicker configuration enables TrickMo to execute various operations, including blocking system updates, disabling security features, and preventing app uninstallation. The JSON file includes text in both German and English. Phrases like “Aktivieren,” “App-info,” and “Deinstall” indicate that the malware is designed to interact with devices set to German, hinting at potential victim geolocations in Germany, Austria, or Switzerland. Similarly, English phrases such as “Activate,” “App info,” and “Uninstall” suggest that the malware also targets devices set to English, indicating potential victims in the United Kingdom and the United States. Additionally, the same infrastructure used for botnet control and configuration retrieval also stores exfiltrated data like logs, credentials, and photos, which can be accessed by third parties due to a lack of effective authentication on the C2 server.
Data leak from C2 Server
The analysis of TrickMo’s Command and Control (C2) infrastructure reveals several critical misconfigurations that expose extensive sensitive data from infected devices. The C2 server contains around 12 GB of personal information, including photos, documents, connection logs, and credentials. The analysis reveals several critical endpoints:
The data leak exposes victims to significant risks, including financial theft, unauthorized account access, and identity theft. Compromised credentials and sensitive photos can lead to direct financial losses, fraudulent activities, and targeted phishing attacks. The breach also opens opportunities for social engineering, blackmail, and long-term damage to victims’ privacy and security.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that TrickMo’s evolving capabilities will likely pose increasingly significant threats to organizations and their employees. As banking malware becomes more sophisticated, TrickMo’s advanced features may lead to a rise in targeted attacks on corporate financial systems, potentially resulting in substantial financial losses and operational disruptions. Organizations could face heightened risks of data breaches and identity theft as employees’ personal and professional information becomes a prime target. The malware’s ability to bypass security measures and execute fraudulent transactions means that companies may need to adopt more robust multi-layered defenses and proactive threat detection strategies. Additionally, TrickMo’s potential to exploit evolving obfuscation techniques suggests that cybersecurity teams will need to invest in advanced analysis tools and stay ahead of emerging threats to safeguard sensitive information effectively.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
Security Awareness training should be mandated for all company employees. The training should ensure that employees:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Iranian Attacks Strike on Iraqi Government Infrastructure
Summary:
A recent cyber campaign targeting the Iraqi government has been linked to APT34, an Iranian threat actor associated with Iran’s Ministry of Intelligence and Security (MOIS). This operation employs a sophisticated toolkit, introducing two new malware families, Veaty and Spearal and uses specialized Command and Control (C2) methods like DNS tunneling and compromised email accounts. The malware spreads through clever social engineering, disguising malicious attachments as legitimate documents. Veaty uses hacked Iraqi government email accounts to exchange commands, while Spearal communicates via DNS tunneling to steal data. An evolved IIS backdoor, CacheHttp.dll, has also been identified, further linking this campaign to APT34’s known tactics. This discovery, along with similarities to malware clusters like Karkoff, Saitama, and IISGroup2, strengthens the connection to APT34. The campaign highlights APT34’s persistent focus on Middle Eastern governments, showcasing advanced techniques to maintain a foothold and evade detection.
Relevancy & Insights:
APT34, an Iranian cyber-espionage group, has a history of targeting Middle Eastern governments and critical sectors like energy and telecommunications. Their past attacks often relied on spear-phishing and exploiting web server vulnerabilities, similar to the current campaign against the Iraqi government. This operation involves advanced techniques like DNS tunneling and email-based Command and Control (C2), with custom malware, such as Veaty and Spearal. The motive remains espionage, focused on gathering sensitive political and economic intelligence. Government bodies and critical infrastructure, especially in the Middle East, need to be vigilant.
ETLM Assessment:
APT34, an Iranian threat actor affiliated with the Ministry of Intelligence and Security (MOIS), focuses on Middle Eastern governments and organizations. It targets critical industries such as government, energy, and telecommunications, primarily within Iraq and neighbouring countries. APT34 is known for using advanced Command and Control (C2), techniques like DNS tunneling and email-based channels, exploiting vulnerabilities in technologies such as IIS servers and misconfigured email systems. The group’s malware arsenal includes Veaty and Spearal, recently used in this campaign and earlier tools like Karkoff and Saitama. By leveraging social engineering and persistent backdoors, APT34 continues to refine its attack methods to maintain long-term access to high-value targets. In the future, the group is likely to expand its capabilities, focusing on new vulnerabilities and evolving its tactics to evade detection, posing a sustained threat to regional governments and critical infrastructure.
Recommendations:
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Persistence | T1136 | Create Account |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hacker charged by US Justice Department over a spearphishing operation
The US Justice Department has charged a Chinese national, Song Wu, for allegedly sending spearphishing emails to employees at the US Air Force, Navy, Army, NASA, and the Federal Aviation Administration, as well as major research universities in Georgia, Michigan, Massachusetts, Pennsylvania, Indiana, and Ohio. According to the Justice Department, Song participated in the campaign in his capacity as an employee of the Aviation Industry Corporation of China (AVIC), a Beijing-headquartered aerospace and defense conglomerate, owned by the Chinese government.
The Chinese national allegedly engaged in a multi-year ‘spear phishing’ email campaign in which he created email accounts to impersonate U.S.-based researchers and engineers and then used those imposter accounts to obtain specialized restricted or proprietary software used for aerospace engineering and computational fluid dynamics. This specialized software could be used for industrial and military applications, such as the development of advanced tactical missiles and aerodynamic design and assessment of weapons.
ETLM Assessment:
As we have outlined in our report on the matter last year, China is a global champion in using cyber-attacks as a tool of statecraft, and the hands-on role of the government in the economy only reinforces the drive to use cyber-attacks for IP theft, especially in matters that are of military or dual use. China has a bigger hacking program than that of every other major nation combined, and any large company in industries outlined in Chinese development plans will need to invest into external threat landscape management solutions to stay ahead of relentless and repeated assaults by Chinese hackers.
Iranian hackers deploy a new malware across the Middle East
Researchers have recently published details on a cyberespionage campaign initiated by Scarred Manticore, a threat actor affiliated with Iran’s Ministry of Intelligence and Security (MOIS). The threat actor is using a new malware framework dubbed “LIONTAIL” to target the government, telecommunications, military, and financial sectors in Saudi Arabia, the UAE, Jordan, Kuwait, Oman, Iraq, and Israel.
ETLM Assessment:
While the goal of this campaign is espionage, the researchers note that some of the same tools were used in an MOIS-sponsored destructive cyberattack against the Albanian government in 2022. According to our assessment, Iran is now more likely than ever to use its cyber capabilities to attack critical infrastructure, especially in countries deemed supportive of the USA and Israel and on infrastructure important for international commerce. Further, as we have observed in this report, Iran can direct hacktivists into preparing further attacks, with them having already targeted the USA, Israel, Saudi Arabia, or the UK.
Hundreds of Hezbollah members were injured by sudden pager explosions
In Lebanon, hundreds of Hezbollah members were injured in unexpected explosions. According to current information, this was a coordinated campaign of exploding communication devices – pagers, widely used by the organization. The terror movement subsequently confirmed that three of its members had been killed. The Lebanese Ministry of Health said that the explosions killed nine people and injured 2,750, with 200 being wounded seriously. The explosions took place in the capital Beirut and in southern Lebanon. Sources there attributed the matter to Israel. Its officials have not commented on the matter. According to some preliminary assessments, the explosions were caused by an Israeli hacking operation that caused the batteries of the devices to overheat and detonate.
ETLM Assessment:
After a lull in online activity, the killing and injuring of so many Hezbollah members in Lebanon by Israel, sparked a storm of strong reactions on social media with many threats to carry out retaliatory hacktivist activities. As we noted in a recent report, the shadow cyber war between Israel, Western allies in the region, and Iran with its various proxies and affiliates is likely to intensify. The Israeli pressure on Gaza and the dire humanitarian situation there will continue to fuel pro-Palestinian sentiment and inspire further hacktivist action, while the actors in the international arena are weighing their options for escalation. Our researchers will continue to watch this space and bring your fresh analysis in the coming weeks and months.
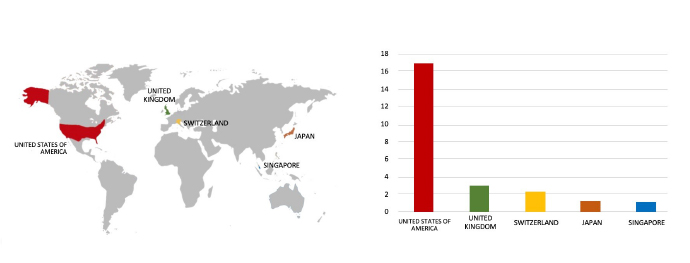
The RansomHub Ransomware impacts the Sanyo-AV
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; Sanyo-AV (www[.]sanyo-av[.]com), was compromised by the RansomHub Ransomware. Sanyo- AV Taiwan is a company specializing in audio-visual products and solutions. They offer a range of electronics, including projectors, televisions, and home theater systems. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 500 GB.
The following screenshot was observed published on the dark web:
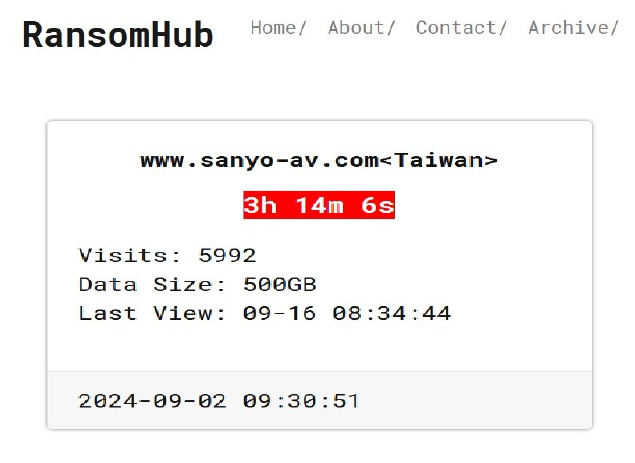
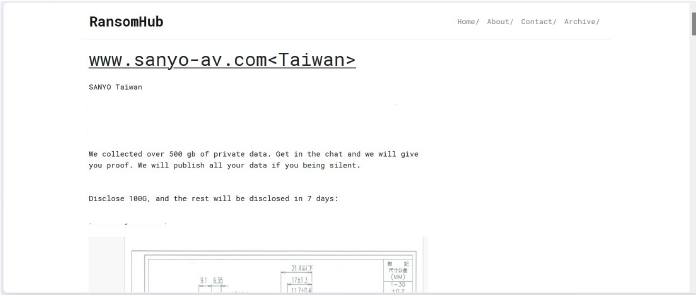
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Sanyo-AV, a prominent Manufacturing company from Taiwan, highlighting RansomHub’s significant threat presence in the East Asia region.
The Cicada 3301 Ransomware Impacts the Miyaki Co., Ltd.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; MIYAKI (www[.]kashima-coat[.]com), was compromised by Cicada 3301 Ransomware. Miyaki Co., Ltd. is a Japanese company known for its development, manufacturing, and distribution of cleaning and coating agents for various materials, including stone, wood, metal, and fiberglass-reinforced plastic (FRP). The Kashima coating process was invented by Miyaki Co., Ltd. It involves depositing lubricating molybdenum disulfide into the micro-pores of hard-anodized aluminum, resulting in a smooth and durable surface. Kashima Coat represents a significant advancement in surface treatment technology, providing superior lubrication and protection for aluminum components in demanding applications. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 100 GB.
The following screenshot was observed published on the dark web:
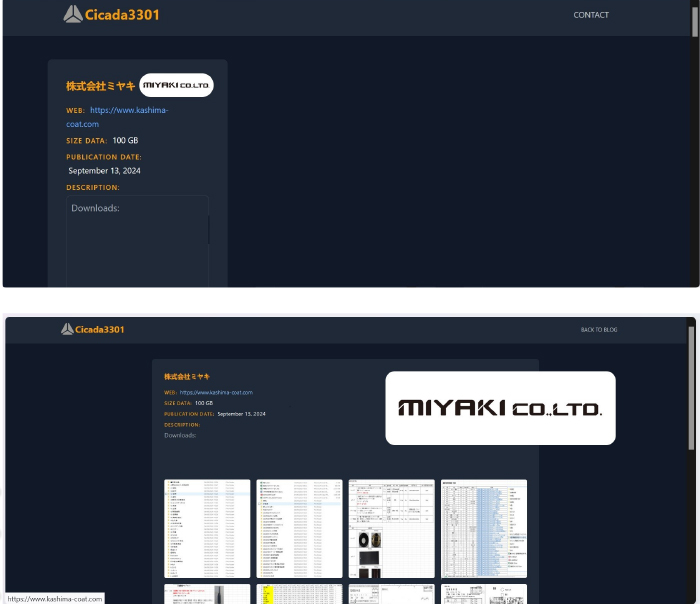
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Cicada 3301 Ransomware uses sophisticated methods to maintain access to infected systems, allowing attackers to run commands remotely and potentially return for future attacks. The ransomware can target both Windows and Linux systems, including VMware ESXi environments. Based on recent assessments by CYFIRMA, Cicada 3301 Ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Miyaki Co., Ltd, a leading Manufacturing company in Japan, highlighting Cicada 3301 Ransomware’s significant threat presence in the Asia Pacific.
Vulnerability in VMware Tanzu Spring
Summary:
The vulnerability allows a remote attacker to perform directory traversal attacks.
Relevancy & Insights:
The vulnerability exists due to input validation error when processing directory traversal sequences in applications serving static resources through the functional web frameworks WebMvc.fn or WebFlux.fn.
Impact:
A remote attacker can send a specially crafted HTTP request and read arbitrary files on the system.
Affected Products: https[:]//spring[.]io/security/cve-2024-38816
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
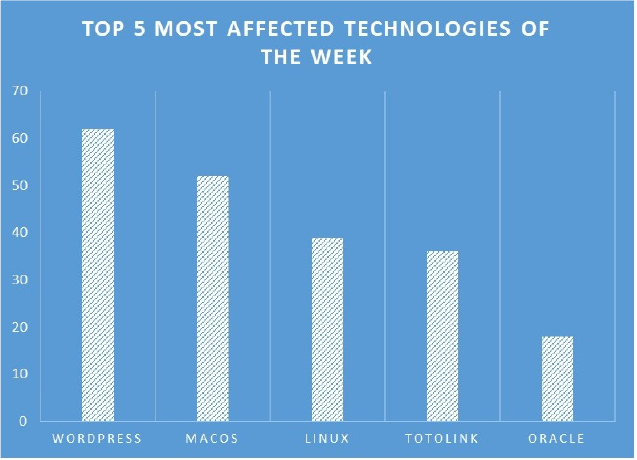
ETLM Assessment:
Vulnerability in VMware Tanzu Spring can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of VMware Tanzu Spring is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguard cloud-native application development and management activities provided by Spring open-source projects and ecosystem benefits, across different geographic regions and sectors.
MadLiberator Ransomware attacked and Published the data of the YCH Group
Summary:
Recently, we observed that the MadLiberator Ransomware attacked and published data of YCH Group (www[.]ych[.]com) on its dark web website. YCH Group is a prominent supply chain and logistics company based in Singapore, known for providing comprehensive supply chain management solutions across Asia. The company operates in multiple countries, including Singapore, China, India, Indonesia, Malaysia, the Philippines, Thailand, Vietnam, and others. It has developed a robust network that supports various industries. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization
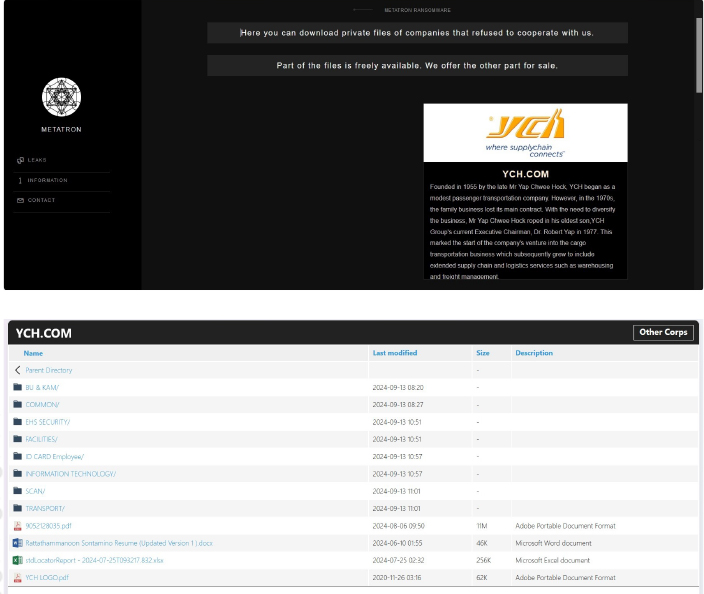
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Mad Liberator Ransomware represents a new threat in the ransomware landscape, particularly through its innovative use of social engineering and remote access tools. Organizations must remain vigilant and proactive in their cybersecurity measures to defend against this evolving threat.
Bookgenville Data Advertised on a Leak Site
Summary:
In a recent post on a dark web forum, a threat actor has alleged that they successfully breached Bookgenville.com, a website reportedly associated with educational services in Indonesia. The post claims that sensitive user data, including personal and academic information, has been compromised.
According to the threat actor, the stolen data includes a range of personal details, such as user ID numbers, names, usernames, email addresses, phone numbers, and permanent residential addresses. Additionally, more sensitive data points are said to have been exposed, such as birth dates, gender, educational certificates, National Education Numbers (NISN), National Identity Numbers (NIK), and even the email addresses of parents or guardians.
The threat actor’s post provided a sample of the compromised data, though the authenticity of this data leak remains unconfirmed.
While no specific demands or ransom requests have been reported as part of this breach, the exposed data could be used in various malicious activities, ranging from identity theft to social engineering attacks.

Source: Underground Forums
Dubai Municipality Data Advertised on a Leak Site
Summary:
In a significant cybersecurity incident, Dubai Municipality, the government body responsible for city services in Dubai, UAE, has allegedly suffered a major data breach. A threat actor posted the claim on a dark web forum, revealing that over 60 GB of sensitive data, including personal and financial records, was compromised.
The threat actor claims that the breach involves a vast range of data, including records from various inspections, customer databases, and payment transactions. The data allegedly includes:
Inspections Data: Over 1 million records, including business inspection details, violations, and hotel inspections. Specific datasets contain information on businesses’ licensing, contact information, and scheduled inspections.
Customer Data: A dataset of more than 1 million customers, with personal identifiers such as names, phone numbers, and emails.
Payment Information: Over 160,000 records detailing payment transactions, voucher numbers, amounts, and company details.
Land Ownership Records: Multiple datasets related to land records, including ownership details, passport numbers, and geographic coordinates.
Employee Data: Almost 30,000 records of employee details, including personal identifiers, job titles, and termination reasons.
Corporate Contacts: 273,000 records including contact information for various companies and individuals.
Additionally, the hacker claims to possess around 60-80 GB of scanned documents, including passports, ID cards, and other personal identification files.
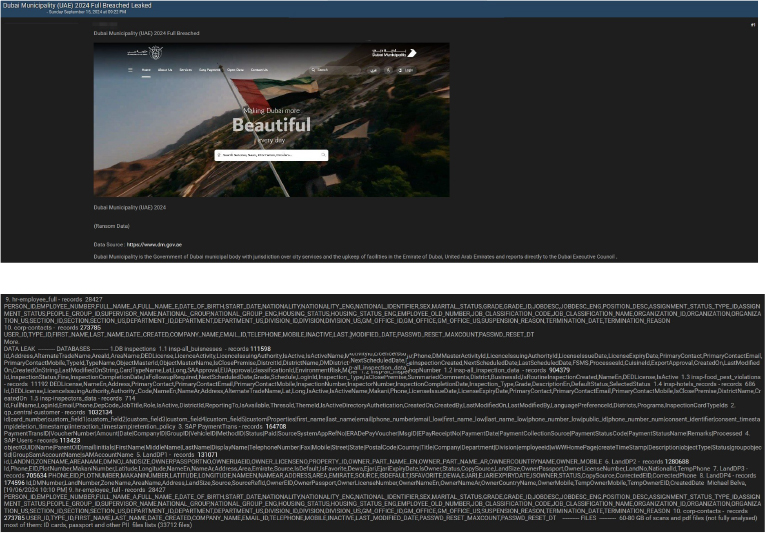
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s assessment, the threat actor known as ” theDbasespremium ” poses a serious risk to organizations due to its financial motivations and the ability to exploit vulnerable institutions. This actor is notorious for infiltrating organizations with weak security measures and profiting by selling stolen sensitive data on the dark web or underground forums. The typical targets of ” theDbasespremium ” are institutions with inadequate cybersecurity defenses, making them particularly susceptible to the sophisticated cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
A threat actor claims to be selling data from Emirates Auction, a field auction company. The alleged database contains 210,000 records, including name, email, password, phone, Code, Nationality ID, ID, last online, UAE Resident, and Nationality.
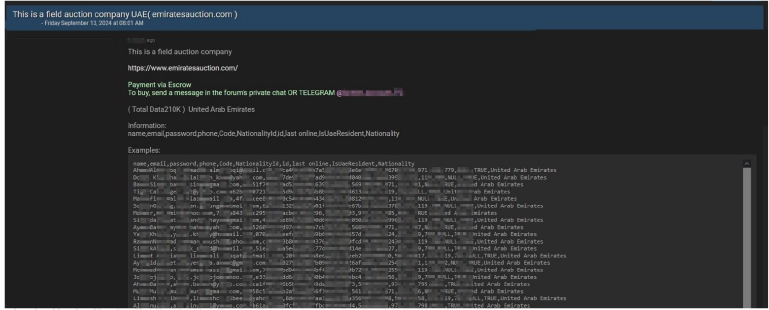
Source: Underground forums
A threat actor, “IntelBroker”, claims to have leaked the data of Rapid e-Suite, a set of solutions for automating Oracle E-Business Suite implementations. The alleged data includes entire source codes, PDFs & hardcoded credentials.
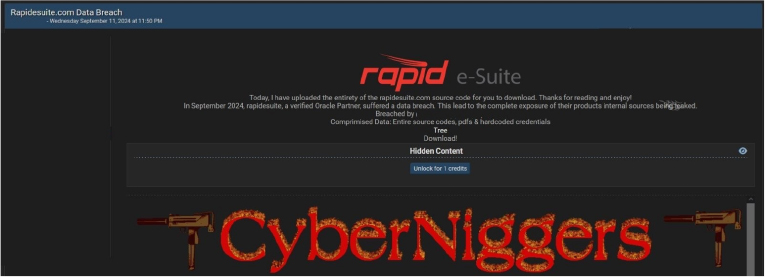
Source: Underground forums
ETLM Assessment:
The “IntelBroker” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
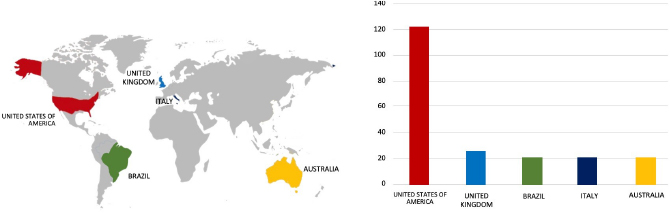
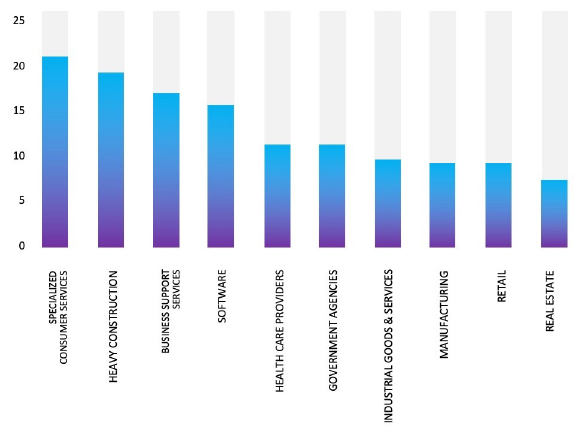
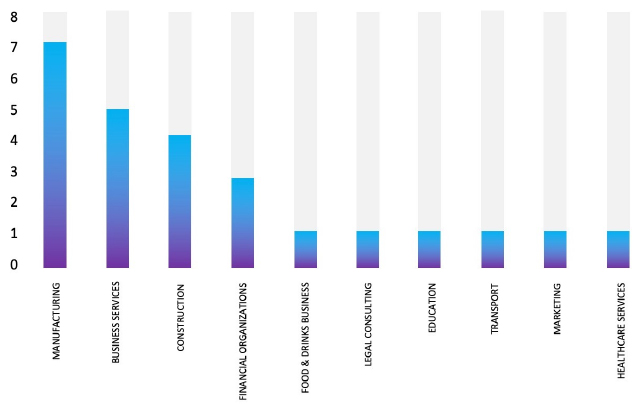
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.