Published On : 2023-10-20
Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology
– which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industries: Business Services, Construction, Law, Manufacturing. Target Geography: Canada, United States.
Introduction
CYFIRMA Research and Advisory Team has found ransomware known as Rancoz while monitoring various underground forums as part of our Threat Discovery Process.
Rancoz Ransomware
Rancoz ransomware was first identified in mid-2023 and has seen a significant increase in its distribution in recent times.
The ransomware shares some code similarities with Vice Society’s custom ransomware, but there is no concrete evidence of a direct connection with any specific group or actor.
Upon execution, Rancoz ransomware scans all local drives and attempts to encrypt relevant file types. Command-line parameters can be used for targeted encryption, while the default behavior is to encrypt all local and accessible volumes. Encrypted files carry the “.rec_rans” file extension.
When the ransomware runs, it displays a visible command window, providing updates on the encryption process and related routines, including volume enumeration and error messages.
Rancoz payloads accept the following command-line parameters:
- /s – Output syntax/arguments
- /f – Targeted file, aka encrypt specific files (provided via path)
- /d – Targeted directory, aka encrypt specific directories (provided via path)
For file encryption, Rancoz uses a combination of NTRUEncrypt (asymmetric encryption) and the ChaChapoly cipher (symmetric encryption). The encryption process employs multiple threads, facilitated by the CreateThread() API, to work on data blocks that are subsequently written back to the affected files. Rancoz ransomware payloads also include lists of file extensions and folder names to exclude from the encryption process.
The following commands are executed when running Rancoz ransomware payloads.
- “C:\Windows\system32\cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet
This command is used to delete all Volume Shadow Copies (VSS) quietly, eliminating potential data recovery options after encryption.
- reg delete “HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default” /va /f
This command deletes all values (/va) within the “Default” registry key for Terminal Server Client, potentially affecting user-specific RDP settings.
- reg delete “HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers” /f
This command deletes the “Servers” registry key under Terminal Server Client settings, potentially impacting stored remote desktop server configurations for the user.
- for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl “%1”
This command clears Windows Event Logs by iterating through the list of event logs obtained from ‘wevtutil.exe el.’ The impact is the deletion of event log data, which can hinder forensic analysis and system monitoring.
Rancoz ransomware goes further by altering the desktop background of infected hosts, making changes to the registry to display their provided “noise.bmp.”
Following the encryption process, affected files are recognizable with the “.rec_rans” extension. To instruct victims on the recovery process, a ransom note titled “HOW_TO_RECOVERY_FILES.txt” is left behind, guiding them to communicate with the attackers through the TOR-based web portal.
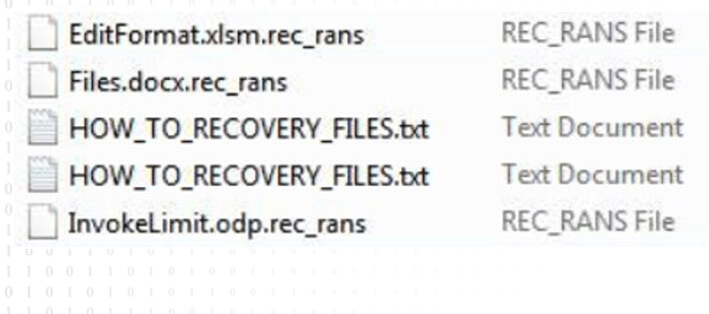
Screenshot of files encrypted by Rancoz Ransomware (Source: Surface Web)

Desktop wallpaper changed by Rancoz ransomware (Source:surface web)
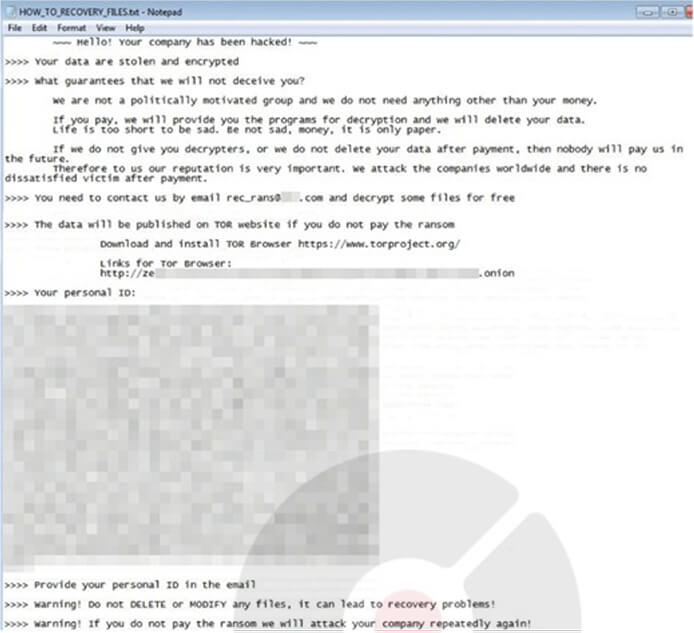
Screenshot of a Ransom note of Rancoz (Source: surface web)
While the submission location may not directly correlate with the infection location, it’s worth noting that Rancoz ransomware samples have been submitted to public file scanning services from various countries, including the United States, India, France, and Lithuania.
Ransomware with potential connections.
Researchers believe that there is a possible connection between Rancoz, Buddy ransomware, and other unidentified ransomware, suggesting a common attacker or malware developer.
Rancoz and Buddy ransomware samples share a common compilation date and time. However, Buddy ransomware employs a distinct file extension for encrypted files, “.buddyransome,” not similar to Rancoz. Interestingly, both ransomware variants use identical ransom note names (along with similar grammatical errors), which adds to the connection between them.
Furthermore, Buddy ransomware, like Rancoz, alters the desktop wallpaper, albeit with varying content. However, they both start with the same opening text in their modified wallpapers.
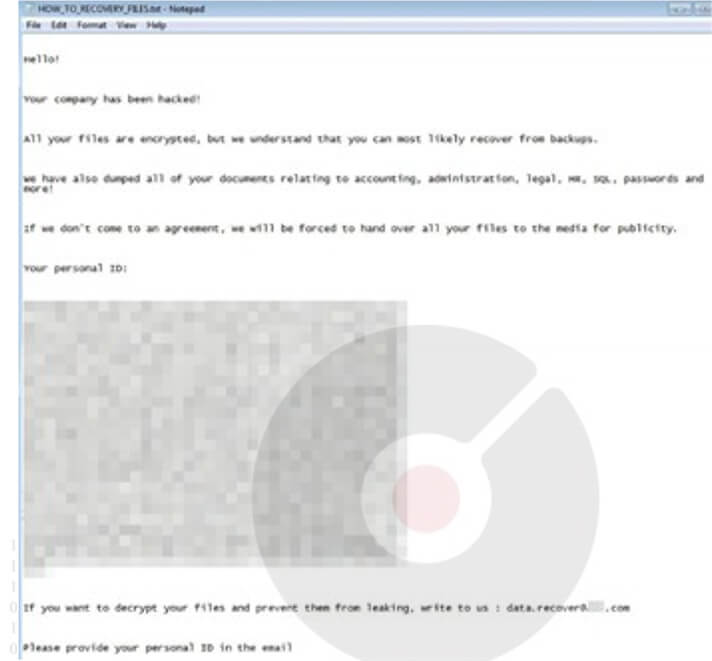
Ransom note of Buddy Ransomware (Source: Surface Web)

Desktop wallpaper modified by Buddy Ransomware. (Source: Surface Web)
The unidentified ransomware sample drops a ransom note that closely resembles Rancoz’s. The key difference is Rancoz’s inclusion of a TOR site link, which is lacking in this unknown ransomware. Moreover, they utilize distinct contact email addresses.
This unidentified ransomware will change the wallpaper, which is like Rancoz and Buddy ransomware.
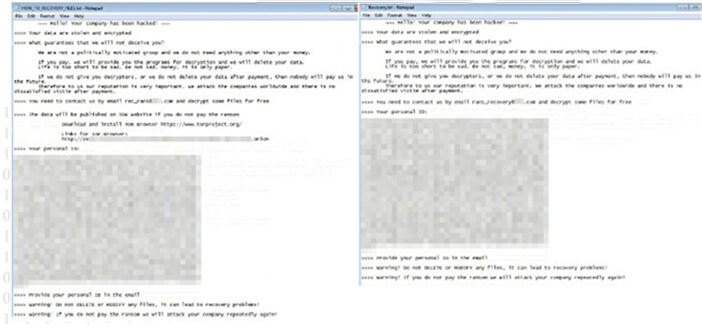
Rancoz ransom note (left) and unidentified ransomware ransom note (right) (Source: Surface Web)

Desktop wallpaper modified by unidentified ransomware. (Source: surface web)
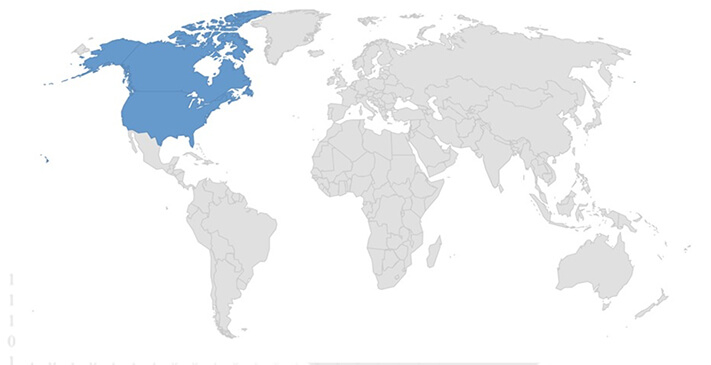
Countries targeted by Rancoz Ransomware.
Relevancy and Insights:
- This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
- Recently targeted industries are:
- Construction and Law sectors in the United States
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. Ransomware that can detect debug environments may have implemented techniques to evade or disable debugging tools.
- Analyzing the list of victims suggests that the United States is the primary geographical target, with the manufacturing industry being the most frequently targeted sector by this ransomware.
- The combination of NTRUEncrypt and ChaChapoly, along with multi-threading, enhances Rancoz’s encryption efficiency and demonstrates an evolving sophistication in ransomware capabilities.
ETLM assessment
- Based on CYFIRMA’s assessment, the analysis of Rancoz ransomware and its potential connections to Buddy ransomware and unidentified ransomware suggests a complex threat landscape. In the future, we can anticipate increased collaborations or shared developments among threat actors targeting Windows-based systems, with a particular focus on industries like manufacturing. Enhanced evasion techniques and stealthy operations are likely to become more prevalent, underscoring the importance of early detection and prevention.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No |
Tactics |
Techniques/Sub-Techniques |
| 1 |
TA0002: Execution |
T1059: Command and Scripting Interpreter |
| T1129: Shared Modules |
| 2 |
TA0005: Defense Evasion |
T1027: Obfuscated Files or Information |
| T1036: Masquerading |
| T1070.001: Indicator Removal: Clear Windows Event Logs |
| T1070.004: Indicator Removal: File Deletion |
| T1222: File and Directory Permissions Modification |
| T1564.003: Hide Artifacts: Hidden Window |
| 3 |
TA0007: Discovery |
T1012: Query Registry |
| T1082: System Information Discovery |
| T1083: File and Directory Discovery |
| 4 |
TA0011: Command and Control |
T1090: Proxy |
| 5 |
TA0040: Impact |
T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Sigma Rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rules for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
Trending Malware of the Week
Type: Information Stealer
Objective: Stealing Sensitive Information, Remote Access
Target Technology: Windows OS, Discord
Active Malware of the Week
This week “Lumma Stealer” is trending.
Summary
Researchers have uncovered a concerning security threat involving the distribution of Lumma Stealer, an information-stealing malware, through Discord, a widely used chat platform for online gamers, content creators, and streamers. The researchers observed that threat actors are exploiting Discord’s content delivery network (CDN) to host and propagate Lumma Stealer. Furthermore, they are leveraging Discord’s application programming interface (API) to develop bots that can communicate with the malware, providing remote control capabilities. These bots are also responsible for transmitting pilfered data to private Discord servers or channels.
Lumma Stealer
Lumma Stealer, a recently identified malware written in C programming language designed to steal user credentials, has been deployed by threat actors through Discord’s content delivery network (CDN). Initially detected in August 2022, Lumma Stealer gained attention earlier this year when operators targeted YouTube users through spear-phishing emails.
Currently, Lumma Stealer is available as a service in underground forums, with prices starting at USD$250 per month. The basic plan permits users to view and upload logs, along with access to log analysis tools. The professional plan includes the same features and adds access to traffic analysis tools. The corporate plan, priced at four times the base cost, offers proactive defense bypass services. The most expensive plan, priced at US$20,000, provides users with access to the source code and the right to sell the info stealer.
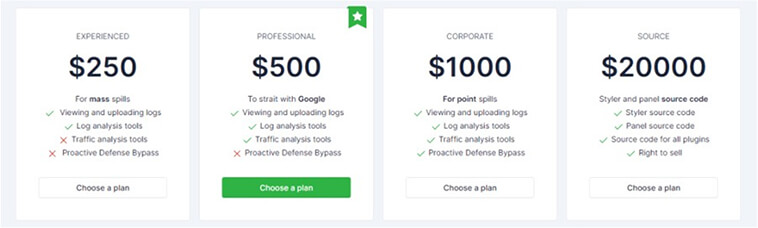
Fig 1: Lumma Stealer service plans available in underground forums.
Technical Analysis of Lumma Stealer
Lumma Stealer operators employ random Discord accounts to send direct messages to victims, and they also target connections of compromised Discord accounts. The attackers use deceptive tactics, posing as individuals seeking help for a project and offering US$10 or a Discord Nitro boost in exchange for the victims’ assistance. Discord Nitro boosts are premium features that users can buy for specific servers. The attackers leverage this enticing offer to persuade victims to play a game and provide a review, a task promised to take only four to five minutes. If the victim agrees, they are prompted to download a file, initiating the malware delivery process.
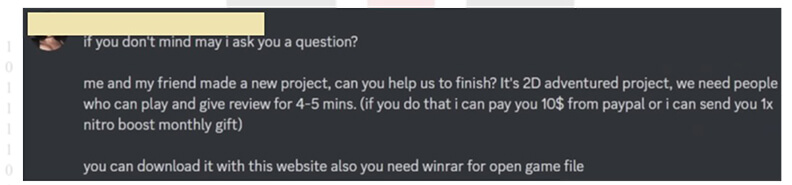
Fig 2: An example of a Discord direct message sent to would-be victims, prompting them to download and execute a file containing Lumma Stealer
Researchers observed the victim accessing the fraudulent Discord message via Google Chrome on a work computer. Upon selecting the malicious link, it triggered multiple downloads of the malicious file “4_iMagicInventory_1_2_s.exe” that contains the Lumma Stealer malware.
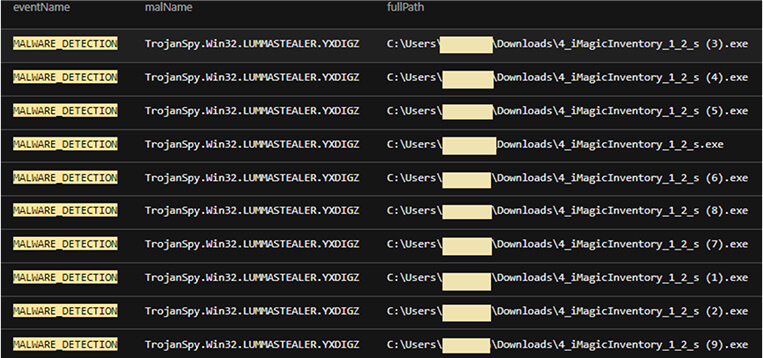
Fig 3: The Lumma Stealer file was downloaded multiple times when the URL sent via the Discord direct message was accessed.
Upon execution, the file establishes a connection with the malicious domain gapi-node[.]io, aiming to exfiltrate cryptocurrency wallets and browser data.
INSIGHTS
- Lumma Stealer, previously known as LummaC2, is a subscription-based information stealer observed in the wild since 2022. It is promoted on dark web forums and a Telegram channel with over a thousand subscribers as of early 2023 and is also available on Lumma’s official seller page for a relatively low price.
- Lumma Stealer’s operations extend beyond underground forums, with the seller leveraging Telegram for updates and user interactions. The Telegram channels are thoughtfully organized, serving distinct purposes such as delivering updated information, providing support, and facilitating bug reporting. This observation underscores the comprehensive strategy employed by threat actors to oversee and improve the functionalities of Lumma Stealer.
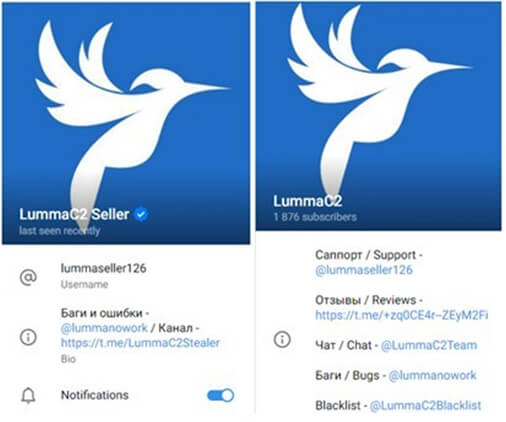
Fig: Telegram channels operated by Lumma Stealer sellers
- Lumma Stealer’s operators, sharing updates in underground forums, have expanded the malware’s capabilities to load additional files, potentially introducing further malware. They claim the malware’s advanced feature of detecting “bots” using artificial intelligence and deep learning is presumed to target researchers, analysis environments, and emulators, allowing selective filtering of unproductive infections from affiliate logs.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA suggests that Lumma Stealer is anticipated to continue its adaptive evolution, incorporating more sophisticated features, and Its impact is not limited, as it can potentially compromise the security of users across various sectors who use Windows Operating Systems and communication platforms like Discord. It may extend its reach and impact more widely, necessitating proactive measures to counter evolving threats in the digital landscape. Organizations relying on Discord for collaboration and communication may face challenges if the platform becomes associated with security vulnerabilities. This could prompt organizations to reconsider their choice of communication platforms, affecting established workflows and collaboration processes.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Establish a robust security posture that is thoughtfully layered with a series of security mechanisms and controls in the network to protect the confidentiality, integrity, and availability of critical data.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATIONS
- Implement real-time website monitoring to analyze network traffic going in and out of the website to detect malicious behaviours.
- Secure your organization’s internet-facing assets with robust security protocols and encryption, including authentication or access credentials configuration, to ensure that critical information stored in databases/servers is always safe.
- Actively monitor the infrastructure for potential exploitation attempts and respond accordingly.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
- Enable Network traffic/security monitoring, security incident detection, notification, and alerting by leveraging SIEM solutions.
Weekly Intelligence Trends/Advisory
Weekly Attack Type and Trends Key Intelligence Signals:
- Attack Type: Malware Implants, Spear Phishing, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gain, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware –BlackCat Ransomware | Malware – Lumma Stealer
- BlackCat Ransomware – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Malware – Lumma Stealer
- Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus
Void Rabisu aka UNC2596 Launched Attacks on Women Leaders Attending the WPL Summit
- Threat Actors: Void Rabisu aka UNC2596
- Attack Type: Spear phishing
- Objective: Espionage
- Target Technology: Windows
- Target Geographies: Europe
- Target Industries: EU military personnel and political leaders
- Business Impact: Operational Disruption and Data Loss
Summary:
In a recent development, the researcher has revealed a recent malicious campaign piloted by the threat actor known as Void Rabisu. Void Rabisu, also known as Storm- 0978, Tropical Scorpius, and UNC2596, operates as a hybrid threat actor engaging in financially motivated and espionage-driven cyberattacks. Initially associated with Cuba ransomware, their shift towards geopolitical targets, including the Ukrainian government and military, demonstrates a broader agenda. In the recently detected campaign, the threat actor specifically targeted female political leaders and attendees of the Women Political Leaders (WPL) Summit held in Brussels in June 2023. Void Rabisu introduced an updated version of its RomCom backdoor, referred to as RomCom 4.0. The backdoor was concealed within a fake WPL Summit website, which advocates for gender equality in politics. In this deceptive way, visitors to the fake website were led to a OneDrive folder containing compressed files and an executable suspected to be malware. This tactic is similar to a previous campaign by Void Rabisu in June, where they utilized major events like the Ukrainian World Congress and the July 2023 NATO summit to deploy a zero-day exploit targeting a vulnerability in Office and Windows HTML, as reported by Microsoft. Additionally, researchers revealed a new technique employed by Void Rabisu in their recent campaigns, involving a TLS- enforcing mechanism by RomCon command-and-control servers. This hinders the automated detection of RomCom infrastructure, exemplifying the group’s evolving tactics.
Relevancy & Insights:
Though there is no strong available evidence or footprints pointing to Void Rabisu being backed by a nation-state, it looks like the group initially operated as a ransomware group with financial motivation and turned into a cyber-espionage group with the tremendous geopolitical shifts resulting from the Ukrainian war, that might have pulled them into cyber espionage endeavors.
ETLM Assessment:
Almost a year after Void Rabisu shifted its focus from ransomware to cyberespionage, the threat actor continued to enhance its primary tool, the ROMCOM backdoor. This backdoor is constantly being updated to bypass security measures set up by the targets with other dangerous features. Void Rabisu has already targeted participants in three notable conferences: the Munich Security Conference, the Masters of Digital Conference, and the WPL Summit. It is highly likely, even expected, that Void Rabisu will extend its targeting to include other conferences and special interest groups in the future. Previously, the threat actor focused on targeting individuals in the Ukrainian region, particularly those who support Ukraine in an ongoing war with Russia. This suggests a likelihood of further attacks on summits attended by leaders from the union.
Recommendations:
- Strengthen endpoint security measures with robust antivirus software, intrusion detection systems, and firewalls. Regularly update and patch all software to defend against known vulnerabilities.
- Conduct thorough cybersecurity training for all employees, emphasizing the dangers of phishing emails and suspicious links. Encourage a culture of vigilance regarding email communications.
- Engage with threat intelligence services to stay updated on emerging threats and vulnerabilities. Utilize continuous monitoring to detect unusual activities and respond swiftly to potential security incidents.
- Partition of the network into isolated segments to contain potential breaches and limit lateral movement within the network, reducing the potential damage from an intrusion.
- Implement MFA across all critical systems and platforms to add an extra layer of authentication, reducing the risk of unauthorized access even if credentials are compromised.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Major Geopolitical Developments in Cybersecurity
A low-level cyber war in the Middle East ensues, threat of spillover imminent
- A wave of hacking attacks on Israeli targets has added a cyber dimension to the conflict, shortly after the surprise attack on Israeli civilians and military personnel was launched on October 7. The most significant measures by the Palestinians may prove to be preparation early in the year, when a Gaza Strip group known as Storm-1133 went after energy, defense and telecommunications companies inside Israel. According to a recent report, the group used fake LinkedIn profiles and posed as software developers or project managers to send malware to employees at those targets and install back doors for later use. Other hacks, mainly by self-proclaimed hacktivist allies of the Palestinians, were aimed at sowing confusion or alarm. For example, pro-Palestinian hackers; AnonGhost, claimed responsibility for an attack on an Israeli app that warns residents of incoming rocket strikes, with the group getting the ability of sending fake rocket alerts to Israeli civilians to help sow chaos in the country. Various groups launched dozens of denial-of-service attacks at government and private websites, knocking them offline but causing no lasting damage.
- One of the most effective DDoS attacks was against the websites of Israeli English- language media like Jerusalem Post or Haaretz, a major source of reporting on the fast-changing conflict and atrocities committed by Hamas in the initial phase of the attack. The particular attack on Jerusalem Post was claimed by Anonymous Sudan, which a recent Cyfirma report identifies as a likely front for Russian intelligence services. The conflict is so far characterized by large scale levels of misinformation, much of it uploaded spontaneously, mostly on X, but also state-driven disinformation campaigns conducted by Hamas and countries sympathetic to Hamas like Iran, Turkey and Qatar. Video game footage has been misrepresented as evidence of Israeli airstrikes, while erroneous and frequently unsubstantiated reports of successful hacks have become widespread. The Hamas and Hamas-aligned camp appears to be centered around disrupting flows of reliable news from the Israeli side and flooding social media with bogus content to drown down indisputable evidence of Hamas atrocities, before the horrific images of civilians suffering from Israeli response will be able to dominate the information sphere.
- At least fifteen well-known hacktivist, ransomware, and cybercriminal groups have declared their active involvement in disruptive operations against both Israeli and Palestinian organizations. Cyberattacks are also targeting foreign backers of both sides in the war. While some of the groups have been supporting Israel or Hamas for a long time, others are intensifying their efforts against a long-standing adversary whose backing is either a pretext or a provocation. While the majority of the activity has been well-known distributed denial-of-service (DDoS) or nuisance-level defacement, there were at least some more sophisticated attacks targeting military command-and-control, specifically Israeli Iron Dome anti-rocket systems, as well as infrastructure, particularly electrical power distribution. It appears that the attacks on C2 and infrastructure have not had much of an impact so far, but this might change as the cyber conflict spills over to other countries. A Palestinian hacker gang named Ghosts of Palestine has invited hackers from around the world to attack private and public infrastructure in Israel and the United States, which is likely to find a response with some ideologically motivated hacking groups. A pro-Hamas group called Cyber Av3ngers targeted the Israel Independent System Operator (Noga), a power grid organization, claiming to have compromised its network and shut down its website. The group also targeted the Israel Electric Corporation, the largest supplier of electrical power in Israel and the Palestinian territories, as well as a power plant.
- The notorious Russian group; Killnet, has launched attacks against Israeli government websites. Nation-state reactions to the conflict have naturally been much more obfuscated and difficult to attribute. However, it is highly likely that Iranian cyber threat groups in particular will have an interest in influencing the conflict via the cyber battlespace; Hamas has publicly stated that its attacks on Israel were backed by Iran. There are a number of Iranian-based internal threat groups that might launch effective assaults against even the most advanced security measures in place at an enterprise. It is conceivable that activity related to Iran-linked cyber threat organizations would rise in reaction to these events given that these groups usually target nations with tense political ties to Iran, such as the US and Israel. Potential assaults, however, would probably be deliberate and focused, affecting Israeli enterprises with ties to the government or those engaged in important infrastructure projects for the government, telecommunications, and defense.
ETLM Assessment:
Israel will seek to eliminate the threat posed by the Palestinian militant group for good, but that will require extensive bombing, followed by boots-on-the-ground fighting in the Palestinian territory itself. This will cause very high collateral damage and civilian casualties in the Gaza strip which could draw in other adversaries, including Hezbollah, al-Qaeda or even Iran. The cyberspace part of the conflict is likely just in its beginning and we are likely to see a spike in the activity of Iranian APTs attacking countries that support Israel. Russia might throw its weight behind some of the activity as well, as intensification of the conflict suits its interest, driving attention from its war in Ukraine, and consuming resources that could otherwise help its western neighbour.
Crypto mining operations in the US suspected as a front for Chinese espionage or a staging area for sabotage
- Researchers are warning against a potential threat to critical infrastructure that could be stemming from Chinese-owned crypto mining operations in at least 12 U.S. states, including Tennessee, Texas, Wyoming, Arkansas, Ohio and Oklahoma. Most of these operations are set up in states with cheap sources of electricity and are mining Bitcoin and other coins on specialized computing machines that together use as much energy as 1.5 million homes. At full capacity one of these operations, set in Cheyenne, Wyoming alone, would require enough electricity to power 55,000 homes. This specific crypto mining site is situated between a big Microsoft data center that supports the US Department of Defense and F.E. Warren Air Force Base; a command center for US intercontinental ballistic missiles.
- The US Treasury Department’s Committee on Foreign Investment in the United States received warning from IT researchers last year of the threat such installations could pose. The mining operations are positioned to be able to collect intelligence on sensitive activity, and their consumption of electrical power is so high that they can stress the power grid, or, by cycling that consumption, upset the balance on which a reliable grid depends. The prospect of destabilizing the grid is probably the more serious of the risks. Crypto mining is notoriously lectrical-and-computational-power- hungy, conducted via what effectively are large, powerful, single-purpose data centers. Some of the mines are owned, sometimes via a series of shell companies, by the Chinese government or Chinese corporations, which is what set the warning signals in the first place.
ETLM Assessment:
The potential for spying in this case could be best described as an example of the Chinese government leveraging its power over the economy, in order to coerce Chinese companies into assisting Chinese intelligence, which is a topic we reported on earlier. Chinese firms have been enlisted to process data for their country’s spy agencies. By co-opting Chinese companies’ data-processing capabilities, Chinese intelligence agencies can rapidly sift through massive amounts of information to find key data points. The state hackers thus can focus on gaining access to targeted networks and exfiltrate data, while one part of private sectors is obligated by law to help process the data, and any processed intelligence can then be transferred via Chinese intelligence to the political leadership for further development and decision making. Previously, Chinese hackers were mainly focusing on defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. Some researchers are also worried China is trying to position itself in a way it could try to paralyze U.S. critical infrastructure in case of eruption of conflict between the two countries.
Rise in Malware/Ransomware and Phishing
Quality Service and Installation (QSI) is Impacted by BlackCat Ransomware
- Attack Type: Ransomware
- Target Industry: Finance
- Target Geography: The United States of America
- Ransomware: BlackCat Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from The United States of America, (www[.]qsibanking[.]com), was compromised by BlackCat Ransomware. Quality Service and Installation (QSI) is a 27-year-old service and installation provider of ATMs, and Traditional and Electrical Security Equipment. The data that has been compromised remains unreleased on the leak site, suggesting the possibility of ongoing negotiations between the victim and the ransomware group. The compromised data includes details related to Finance, Clients, a substantial SQL database (5TB in size), ongoing Developments, Personal information, and various other sensitive data. The following banks have been impacted: Wesbanco Bank, First Financial Bank, Stock Yards Bank & Trust Company, German American Bank, STATE EMPLOYEES CU OF MARYLAND, INC (SECU), First Financial Bank, National Association, Union Savings Bank, National Cooperative Bank, Civista Bank, and Mvb Bank.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
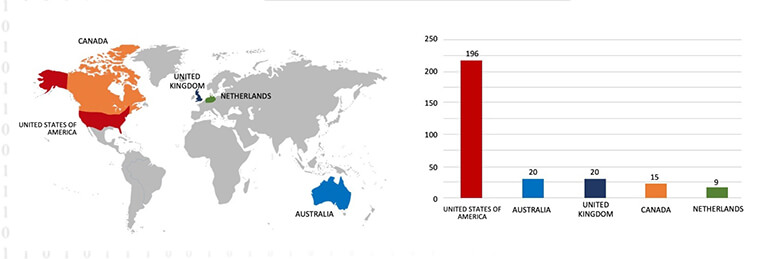
- In 2023, there were 458 documented cases of victimization, cementing the group’s status as one of the most prolific ransomware factions. A scrutiny of their attack strategies highlights a distinct focus on infiltrating organizations, situated within the United States
- Based on the BlackCat Ransomware victims list in 2023, the top 5 Target countries are as follows:
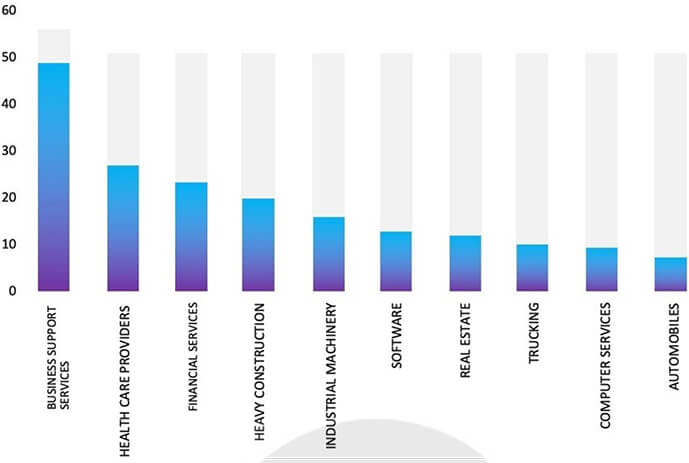
- Ranking the Top 10 Industries, most affected by BlackCat Ransomware
ETLM Assessment:
CYFIRMA’s continued assessment is that BlackCat Ransomware will continue to prioritize American enterprises and affiliated companies housing significant amounts of Personally Identifiable Information (PII). BlackCat Ransomware’s recent targeting of Quality Service and Installation (QSI), indicates the financial industry is of interest to them, and therefore, US financial firms are at heightened risk of attack by Blackcat Ransomware.
Vulnerabilities and Exploits Vulnerability in web2py
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Web Application
- Vulnerability: CVE-2023-45158 (CVSS Base Score 8.1)
- Vulnerability Type: OS Command Injection
Summary:
- The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.
Relevancy & Insights:
- The vulnerability exists due to improper input validation. A remote unauthenticated attacker can pass specially crafted data to the application and execute arbitrary OS commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable system.
Affected Products: http[:]//jvn[.]jp/en/jp/JVN80476432/index.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
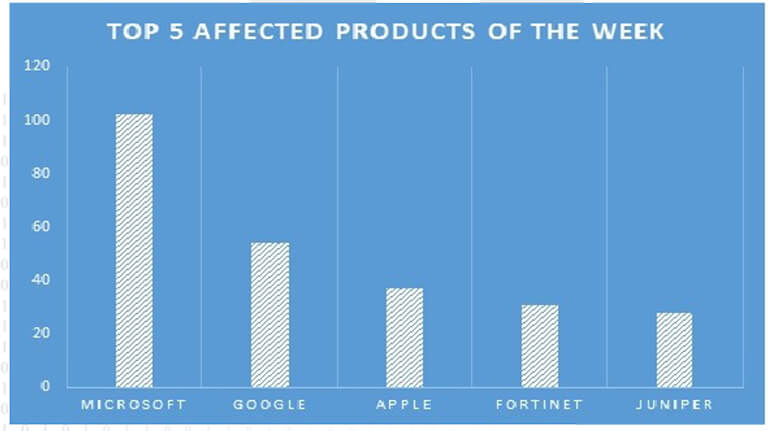
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
Latest Cyber-Attacks, Incidents, and Breaches
Belgian public institution websites hit by DDoS cyberattack.
- Threat Actors: Unknown
- Attack Type: DDoS
- Objective: Operational Disruption
- Target Technology: Web Application
- Target Geographies: Belgium
- Business Impact: Operational Disruption
Summary:
- Belgian public institutions’ websites faced an ongoing cyberattack beginning on Thursday (12 October 2023), likely orchestrated by pro-Russian hackers in response to Belgium’s support for Ukraine. Sites including the Royal Palace, Federal Prime Minister, Chamber of Representatives, and Belgian Senate were temporarily taken offline, with the situation still unresolved. According to Miguel De Bruycker from the Centre for Cybersecurity Belgium (CCB), the attackers constantly shift their techniques, making defense challenging. The attacks are suspected to be DDoS- based, aiming to overwhelm systems with excessive data. A message on the hacked Belgian Prime Minister’s website suggested the motive behind the attack was related to Belgium’s support for Ukraine and President Zelensky’s visit. De Bruycker noted that such attacks tend to follow countries supporting Ukraine, making them predictable occurrences.
- Following a cyber assault on Sunday (15 October 2023), Belgian government websites have been restored and are operational again. This marks the second incident of such attacks on Belgian government websites, within a short span of time. There are no reports of any confidential data being compromised. the websites of the prime minister, the royal family, and the senate were all unattainable. Furthermore, the finance ministry, which was also compromised, published a statement on X, confirming that it had experienced a “hacker attack.” Instead of the home page, a message in English appeared on the websites, referring to Belgian support for Ukraine and the promise to deliver F-16 fighter jets by 2025. Today, that message has disappeared from the websites, and it seems they are functioning normally once again. Miguel De Bruycker of the Centre for Cybersecurity Belgium (CCB) assumes the same attackers were involved twice, but yesterday assured that the damage is limited. “The sites are temporarily more difficult to access, which is annoying, but no information has been stolen. It’s mainly reputational damage,”
Relevancy & Insights:
Several government websites in Belgium were rendered inaccessible due to a substantial cyberattack, likely orchestrated by pro-Russian hackers, as a reaction to Belgium’s backing of Ukraine.
ETLM Assessment:
CYFIRMA assesses that pro-Russian threat actors will continue to target Belgium and other NATO countries in an effort to cause reputational damage and general disruption. As military support for the war in Ukraine continues, and the increase in more sophisticated hardware is transferred e.g., F16, advanced missiles, and combat vehicles, we anticipate a rise in threat actors conducting such attacks, making national institutions consistently appealing targets.
Data Leaks
CarSwitch Data Advertised in Leak Site
- Attack Type: Data Leaks
- Target Industry: Retail
- Target Geography: United Arab Emirates
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to CarSwitch,
{www[.]carswitch[.]com}. CarSwitch, founded in 2016, is an online marketplace for used cars in the U.A.E and Saudi Arabia that handles the entire process for the seller and buyer. The breached data includes names, emails, phone numbers, payment methods, seller information, and various other sensitive details.
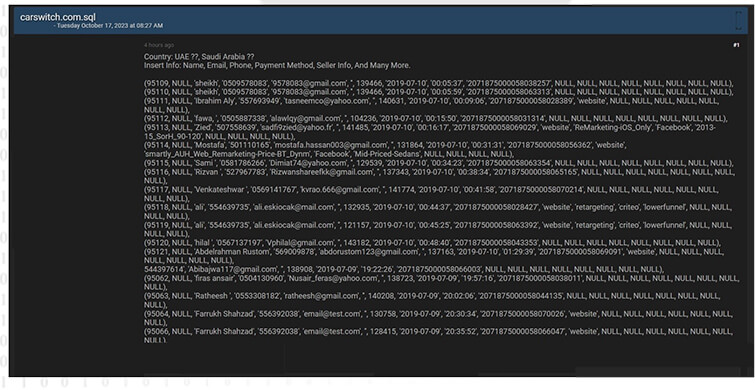
Source: Underground forums
Relevancy & Insights:
Cyber offenders driven by financial incentives persistently seek out vulnerable and poorly secured systems and software programs. A significant portion of these illicit actors operates within concealed online communities, where they participate in discussions concerning cybercrime and the trade of stolen digital assets. Diverging from other financially motivated collectives like ransomware or extortion groups, who often publicize their attacks, these cybercriminals prefer to maintain a discreet presence. They obtain unauthorized entry and make off with valuable information by capitalizing on unpatched systems or weaknesses in software and hardware. Subsequently, they promote the stolen data on clandestine forums, where it is either resold or repurposed by other malicious entities for their own unlawful intentions.
ETLM Assessment:
CYFIRMA assesses United Arab Emirates companies that lack sufficient security measures and infrastructure will continue to remain vulnerable to cyber-attacks. The UAE is a key focus for financially motivated cyber criminals.
Other Observations
CYFIRMA Research team observed a potential data leak related to the Taiba Hospital,
{www[.]taibahospital[.]com}. Taiba Hospital, as part of the network of hospitals and physician clinics in Kuwait, is known for providing a range of medical services and facilities to cater to various healthcare needs. The compromised data includes sensitive information stored in SQL format, and the overall data volume amounts to 2 gigabytes.
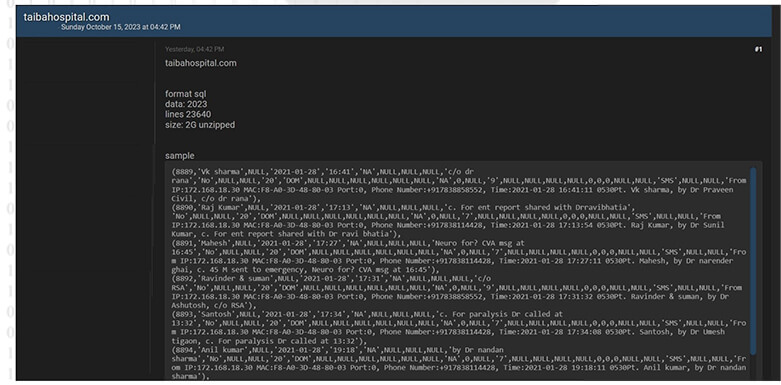
Source: Underground forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improve incident response, increase the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.





















