


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
The CYFIRMA Research and Advisory Team has found Backups Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Backups Ransomware
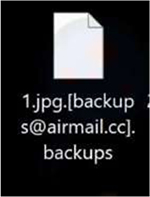
Researchers have identified a new ransomware strain named Backups. Upon execution, Backups encrypts files and appends an email address along with the “.backups” extension to affected filenames.
Additionally, it modifies the desktop wallpaper and drops a ransom note in the form of a text file named “#HowToRecover.txt”.
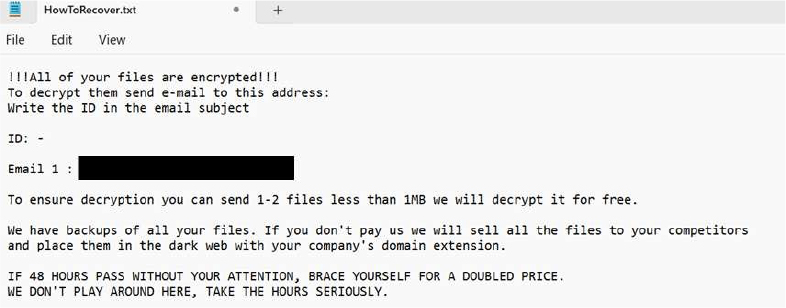
The ransom note informs victims that their files have been encrypted. To initiate decryption, victims are instructed to email including their unique ID in the subject line. The attackers claim to possess backups of all stolen data and threaten to sell the information to competitors or publish it on the dark web if payment is not made. They also warn that the ransom will double if no response is received within 48 hours.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1539 | Steal Web Session Cookie |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Backups ransomware is poised to evolve into a persistent, enterprise-targeting threat. The operators claim to retain full backups of exfiltrated data and leverage this by threatening to sell the information to competitors or publish it on the dark web—an extortion strategy specifically designed to pressure corporate victims. The ransomware’s use of advanced evasion tactics, including WMI abuse and shadow copy deletion, highlights a calculated effort to disrupt recovery mechanisms and amplify damage. Given its strategic execution and global reach, Backups poses a growing risk to critical industries, highlighting the urgent need for robust cybersecurity defences.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’
selection2_cli: CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan| Objectives: Stealing Sensitive Information | Target Technologies: Windows OS, Browsers| Target Geographies: Cuba, Brazil, Mexico, Egypt, South Africa, Nepal, India
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “BrowserVenom” is trending.
BrowserVenom
BrowserVenom is a newly uncovered malware that exemplifies how threat actors are capitalizing on the global surge in interest around AI platforms to deliver sophisticated infostealers. BrowserVenom is delivered through a targeted phishing operation that uses an impersonated version of the Chinese AI model DeepSeek-R1’s official site to deceive users into installing the malware. Victims lured to this fake site are tricked into downloading a trojanized installer, which covertly deploys the malware onto their systems. Functioning as malicious proxyware, BrowserVenom silently reroutes all browser traffic through attacker-controlled servers. This redirection enables the theft of a wide range of sensitive data, including login credentials, session cookies, financial details, personal documents, and email content.
Details observed in the infrastructure indicate that BrowserVenom may originate from Russian-speaking cybercriminals, though the campaign’s impact is global. High infection rates have been observed across regions including Cuba, Brazil, Mexico, Egypt, South Africa, Nepal, and India. As BrowserVenom continues to spread, it serves as a stark reminder of how interest in innovation is being weaponized for exploitation.
Attack Method
BrowserVenom is delivered through a phishing site promoted via malvertising, appearing as the top result in search queries for DeepSeek R1 to exploit growing public interest in AI tools. Victims are lured into a multi-stage infection chain, beginning with a fake CAPTCHA prompt and followed by deceptive installation options for DeepSeek bundled with fraudulent tools like Ollama or LM Studio. Selecting these leads to the stealthy installation of BrowserVenom.
The malware incorporates anti-detection techniques, attempting to add itself to Microsoft Defender Antivirus exclusions. Before proceeding, BrowserVenom checks whether the user has administrative privileges—if not, it terminates execution. If the condition is met, the malware activates its core functionality as proxyware, redirecting browser traffic through attacker-controlled servers. It achieves this by modifying browser configurations and shortcut files across Chromium- and Gecko-based platforms. This enables attackers to intercept sensitive data, monitor activity, and potentially use the infected systems for broader malicious purposes such as account abuse, ad fraud, or secondary infections. Notably, BrowserVenom also includes functionality to fetch additional payloads, indicating the potential for evolving threats in future variants.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Bootkit |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Bootkit |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Keylogging |
| Collection | T1113 | Screen Capture |
| Collection | T1185 | Browser Session Hijacking |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that malware like BrowserVenom is expected to fuel a new wave of stealthy digital manipulation, where attackers exploit public interest in trending technologies to quietly embed themselves into everyday online activity. As search-driven behavior becomes a consistent attack surface, more threats may adopt similar tactics—masquerading as popular tools and leveraging seemingly benign interactions like installations or browser use to hijack traffic, monitor behavior, and extract valuable data. This approach is likely to affect a wider range of geographies and industries, as the tactic relies less on targeted attacks and more on broad user behavior across sectors. Over time, it could lead to widespread misuse of personal and corporate networks, increased fraud through proxy abuse, and the formation of hidden infrastructure that supports larger criminal operations without the victim’s awareness.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule BrowserVenom_IOC_Strings
{
meta:
description = “Detects BrowserVenom malware-related strings (md5, domains, IPs)” author = “CYFIRMA”
malware_family = “BrowserVenom”
strings:
// Domains
$domain1 = “deepseek-platform.com”
$domain2 = “r1deepseek-ai.com”
$domain3 = “app-updater1.app”
$domain4 = “app-updater2.app”
$domain5 = “app-updater.app”
// MD5 hashes
$md5_hash_1 = “d435a9a303a27c98d4e7afa157ab47de”
$md5_hash_2 = “dc08e0a005d64cc9e5b2fdd201f97fd6”
// IP Address
$ip1 = “141.105.130.106”
condition:
any of ($md5_hash_*) or any of ($domain*) or any of ($ip*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
GrayAlpha – possible affiliate of FIN7, having shared infrastructure
About the Threat Actor
FIN7 is a highly sophisticated cybercriminal group known for executing advanced attacks targeting organizations globally, with a primary focus on financial institutions, restaurant & fast-food chains, and retail businesses. The group predominantly employs phishing campaigns as its initial access vector, often crafting highly tailored emails designed to lure specific targets. Their operations have consistently focused on compromising organizations, high-value individuals, and systems that store sensitive personally identifiable information (PII) or financial data, with the intent of conducting targeted information theft.
GrayAlpha is assessed to be a potential affiliate of FIN7, with indications of shared infrastructure, tooling, and tradecraft. The group is known for leveraging highly obfuscated custom malware to execute sophisticated attack campaigns, primarily through fake browser updates, deceptive software download mechanisms, and Traffic Distribution System (TDS)-based delivery methods.
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1053.003 | Scheduled Task/Job: Scheduled Job (via Start-Job) |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Discovery | T1082 | System Information Discovery |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Impact | T1657 | Financial Theft |
Latest Developments Observed
Recently, in June 2025, the threat actor was suspected of using a custom PowerShell loader named PowerNet, which decompresses and executes NetSupport RAT. It identified another custom loader, referred to as MaskBat. It has similarities to FakeBat but is obfuscated, as part of the newly identified infrastructure includes domains used for payload distribution and additional IP addresses. The threat actor is observed to use fake browser update pages, fake 7-Zip download sites, and the traffic distribution system (TDS) TAG-124 as the 3 primary infection methods. The motive appears to be the exfiltration of sensitive information.
ETLM Insights
FIN7 and its affiliated groups, including GrayAlpha, are believed to be financially motivated cybercriminal groups. In recent years, however, this group has significantly evolved—demonstrating a broader digital footprint, acquiring advanced tools and techniques, and developing custom malware, reflecting persistence levels typically associated with nation-state Advanced Persistent Threat (APT) actors.
The group has become increasingly specialized and sophisticated, with indications of collaboration with other threat actors and service-based operators. These include potential groups offering Ransomware-as-a-Service (RaaS), Hacker-as-a-Service (HaaS), and Malware-as-a-Service (MaaS). Such developments have enhanced their ability to evade detection, thereby making attribution and mitigation increasingly challenging.
IOCs
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
YARA Rules
rule GrayAlpha_Toolset_Delivery
{
meta:
author = “CYFIRMA”
description = “Detects GrayAlpha activity using PowerNet loader, NetSupport RAT, MaskBat, and fake browser/software update TDS campaigns”
date = “2025-06-15”
threat_actor = “GrayAlpha”
malware_families = “PowerNet, NetSupport RAT, MaskBat” target_platform = “Windows”
strings:
// PowerNet Loader Indicators
$ps1 = “powershell -enc” ascii nocase
$ps2 = “IEX (New-Object Net.WebClient).DownloadString(” ascii
$ps3 = “FromBase64String” ascii
// NetSupport RAT Indicators
$n1 = “client32.ini” ascii
$n2 = “NetSupport Manager” ascii
$n3 = “C:\\NetSupport\\client.exe” ascii
// MaskBat / FakeBat-like patterns
$m1 = “7zSetup.exe” ascii
$m2 = “browser_update.exe” ascii
$m3 = “schtasks /create /tn” ascii
$m4 = “Software\\Microsoft\\Windows\\CurrentVersion\\Run” ascii
// TDS delivery & fake update lures
$t1 = “GET /chrome_update” ascii
$t2 = “User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)” ascii
$t3 = “Content-Disposition: attachment; filename=” ascii
// Optional shellcode pattern
$x1 = { 60 89 E5 31 C0 64 8B 50 30 } // Shellcode preamble condition:
uint16(0) == 0x5A4D and
(3 of ($ps*, $n*, $m*, $t*) or $x1)
}
Strategic
Management
Tactical
Iranian officials targeted by Israel in a mix of cyber/kinetic integration attacks
According to sources familiar with the operation, Mossad launched a calculated disinformation campaign days before the strike. By sending falsified communications through Iranian channels, they engineered what appeared to be an urgent emergency meeting. The deception succeeded in drawing the entire senior leadership of Iran’s Islamic Revolutionary Guard Corps (IRGC) Aerospace Force—including Commander General Amir Ali Hajizadeh, his deputies, and key technical staff—into a fortified bunker near Tehran.
Just moments before the operation commenced, that bunker was struck with a precision airstrike, effectively decapitating Iran’s top missile command. Israeli officials stated the mission’s objective was clear: to prevent the imminent launch of what they believed to be more than 1,000 ballistic missiles targeting Israeli territory.
In the days following the attack, Iran’s IRGC Cyber Security Command issued urgent directives to officials and their teams, according to Fars News Agency. The warnings came amid Israel’s expanding air campaign against Tehran—part of a broader assault on Iran’s military and nuclear infrastructure launched five days prior.
The directive reflects growing concern within Iran that Israel may be leveraging wireless devices to track and eliminate high-ranking officials—tactics reminiscent of previous operations against Hezbollah. On September 17, during last year’s conflict, thousands of pagers detonated simultaneously across Hezbollah strongholds in southern Beirut, often moments after emitting an alert tone signaling an incoming message.
This shift in Iranian protocol presents a double-edged sword. On one hand, minimizing electronic emissions makes it harder for Israeli intelligence to track and target officials, much like the precautions Ukrainian forces have taken against Russian generals. On the other hand, it severely hampers communication—and forces officials to rely on fixed locations, which can in turn make them easier to target.
ETLM Assessment:
Amid the ongoing hot stage of the war between Israel and Iran, a parallel cyber conflict is unfolding—one that remains largely overshadowed by the spectacle of missile strikes and air raids. Yet this digital battlefield is just as strategically significant. Both nations are using cyber operations to sabotage infrastructure, disrupt military planning, and undermine financial networks. While the physical war dominates headlines so far, cyber war may prove more enduring, with long-term impacts on critical systems and civilian life that are less visible but strongly contributing to the efforts of both nations.
Israeli hackers wipe out an Iranian regime-linked bank
The hacker group Predatory Sparrow—which refers to itself by its Farsi name, Gonjeshke Darande—has claimed responsibility for a destructive cyberattack on Bank Sepah, a financial institution closely tied to the IRGC. The group alleges the bank has played a central role in evading sanctions and funding Iran’s missile programs, nuclear development, and proxy forces. Opposition outlets based outside of Iran reported that several branches of Bank Sepah were closed on Tuesday, bank ATMs were not working and customers were shut out of their accounts.
ETLM Assessment:
Predatory Sparrow has maintained a consistent focus on Iranian targets for years, well before the current escalation in hostilities between Israel and Hamas. While the group publicly presents itself as a grassroots Iranian hacktivist operation, its advanced capabilities have led many analysts to suspect state-level backing. U.S. defense sources told The New York Times in 2021 that the group is likely linked to Israel’s intelligence apparatus.
The Qilin Ransomware Impacts the RMZ Oil Field
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, RMZ Oil Field (https[:]//rmzoilfield[.]com/), was compromised by Qilin Ransomware. RMZ Oil Field is a Singapore-based company that specializes in the design and manufacturing of oilfield Equipment and services providers all over the world. The compromised data consists of confidential and sensitive information related to the organization.

Relevancy & Insights:
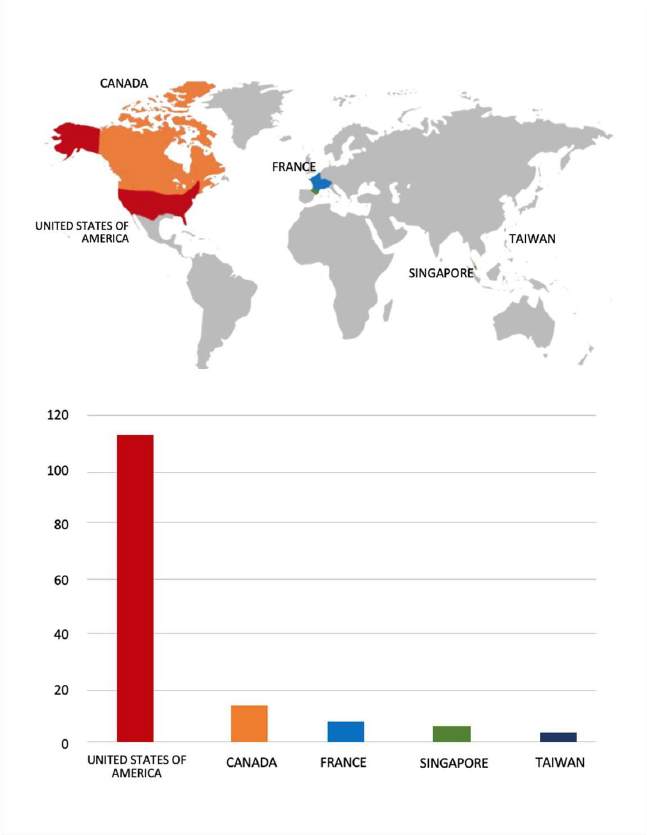
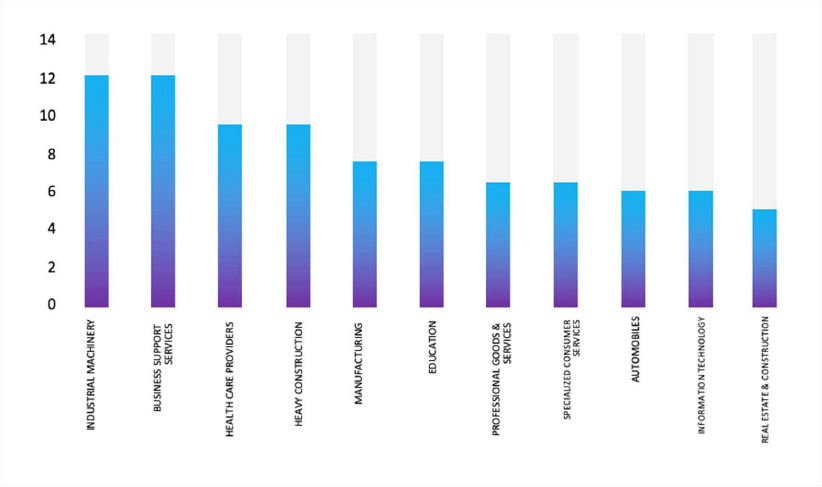
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
The Flocker Ransomware Impacts the Department of Land and Real Estate Regulation in Ajman, United Arab Emirates
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE); the Department of Land and Real Estate Regulation in Ajman, United Arab Emirates (https://ajmanre.gov.ae/), was compromised by Flocker Ransomware.
Ajmanre[.]gov[.]ae is the official website of the Department of Land and Real Estate Regulation in Ajman, United Arab Emirates, responsible for land and real estate regulation in the region. The compromised data consists of confidential and sensitive information related to the organization.
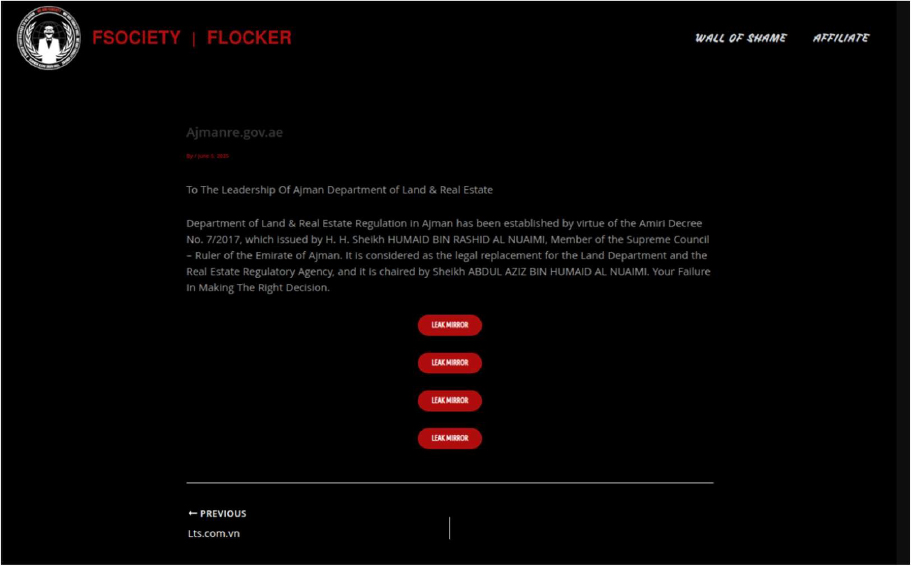
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Flocker ransomware is a rapidly growing, well- organized ransomware threat leveraging double extortion and aggressive tactics to target organizations worldwide. Its collaboration with other cybercriminal groups and use of the RaaS model make it a significant cybersecurity challenge in 2025.
Vulnerability in Liferay Portal and DXP
Relevancy & Insights:
The vulnerability exists because the application does not limit the depth of GraphQL queries.
Impact:
A remote attacker can trigger resource exhaustion and perform a denial of service (DoS) attack.
Affected Products:
https[:]//liferay[.]dev/portal/security/known-vulnerabilities/- /asset_publisher/jekt/content/CVE-2025-3602
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
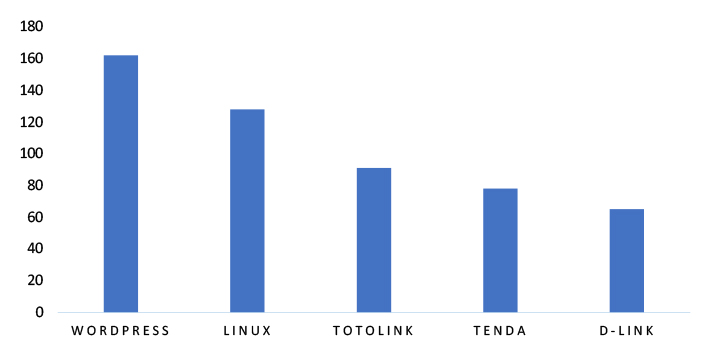
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Liferay Portal and DXP can pose significant threats to user privacy and security. This can impact various industries globally, including government, finance, healthcare, and enterprise digital services. Ensuring the security of Liferay Portal and DXP is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding digital experience platforms, content management systems, and personalized user experiences across different geographic regions and sectors.
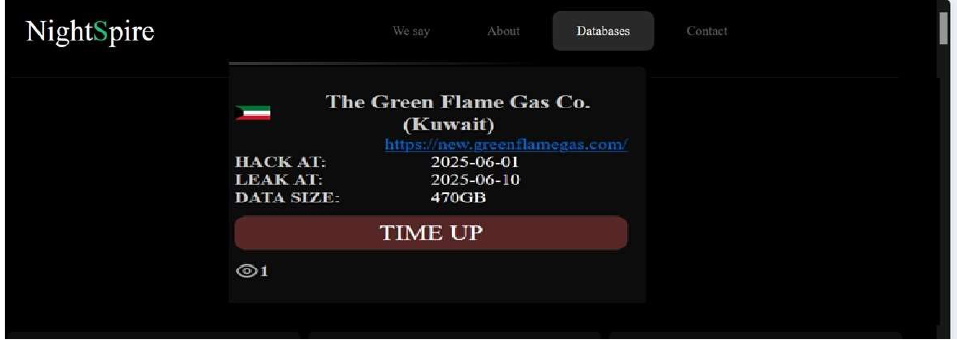
NightSpire Ransomware attacked and published the data of the Green Flame Gas Co
Summary:
Recently, we observed that NightSpire Ransomware attacked and published the data of the Green Flame Gas Co(https[:]//new[.]greenflamegas[.]com) on its dark web website. Green Flame Gas Company is a leading Kuwaiti-owned energy company. The company specializes in supplying gas-related products and services, including LPG, SNG, and specialty gas cylinder regulators, conforming to U.S. and European standards. It is recognized for its quality-driven approach, technical expertise, and integrity in serving a wide range of sectors in Kuwait and the broader Middle East region. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The total size of the data compromised is approximately 470 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
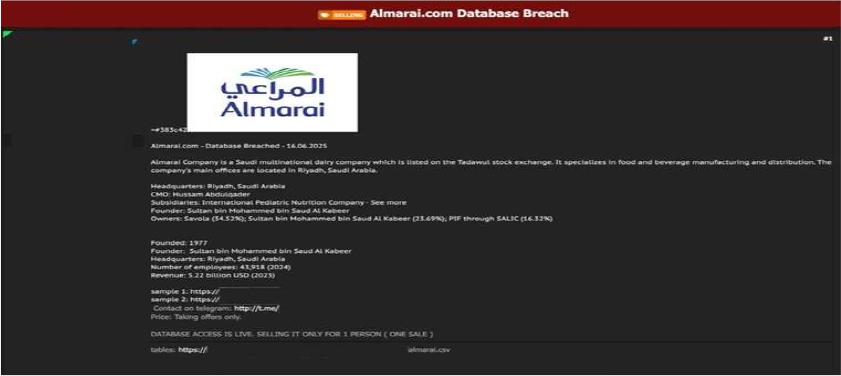
Almarai’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to the Almarai(www[.]Almarai[.]com) in an underground forum. Almarai is one of the largest food and beverage manufacturers in the Middle East. The threat actor “Satanic” has claimed to have breached the database of the Saudi-based multinational dairy company and has put the data up for sale online. Almarai, a publicly traded company on the Tadawul stock exchange with a reported revenue of over $5 billion in 2023, is a household name in Saudi Arabia and a critical part of the region’s food supply chain. The breach was announced on an online forum on June 16, 2025, with the seller claiming to possess live access to the company’s database.
The perpetrator of the alleged breach is offering the data for a single sale, suggesting the information is comprehensive and valuable. According to samples provided by the seller, the compromised database contains a vast amount of sensitive customer and corporate information. The potential exposure of this data could pose significant risks to Almarai’s customers, partners, and business operations, potentially leading to financial fraud, identity theft, and targeted corporate espionage.
The allegedly leaked data includes a wide array of sensitive details, such as:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “Satanic” has recently emerged as a highly active group specializing in data leaks. Credible reports link the group to multiple security breaches involving unauthorized access and the attempted sale of stolen data on dark web marketplaces. The group’s ongoing activity highlights the persistent and evolving nature of cyber threats originating from the dark web. These incidents underscore the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, effective threat intelligence, and proactive defense strategies to protect critical information assets.
Recommendations: Enhance the cybersecurity posture by:
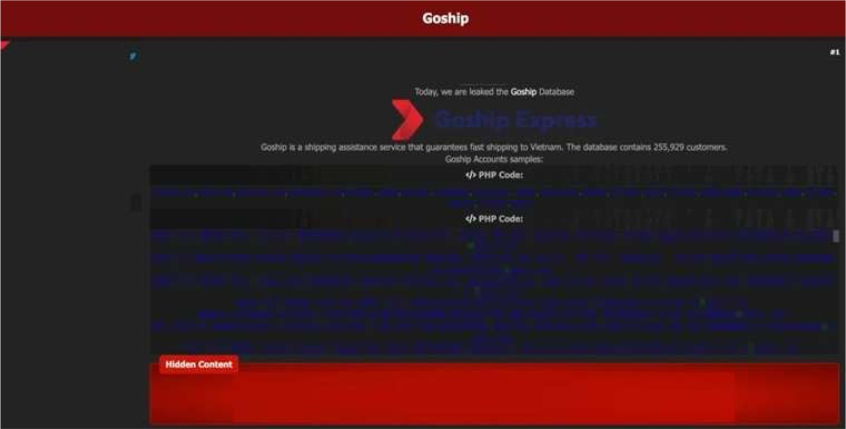
The CYFIRMA Research team observed that a threat actor has allegedly leaked the database of Goship, a prominent shipping assistance service that provides fast delivery services throughout Vietnam. The database, which was posted on a popular dark web forum, reportedly contains the sensitive information of 255,929 customers. Goship is a key player in the Vietnamese logistics and e-commerce sector, connecting online shops with various shipping carriers to streamline the delivery process. The breach could impact a significant number of online businesses and their clients who rely on the service for their daily operations.
The individual who published the post provided samples of the data to substantiate their claims. The alleged leak contains a wide range of personally identifiable information (PII) and client details, which could be exploited by malicious actors for phishing campaigns, identity theft, and other fraudulent activities. The exposure of both client (shop) and receiver (customer) information creates a complex risk for all parties involved in transactions handled by Goship.
The allegedly leaked data includes the following information:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
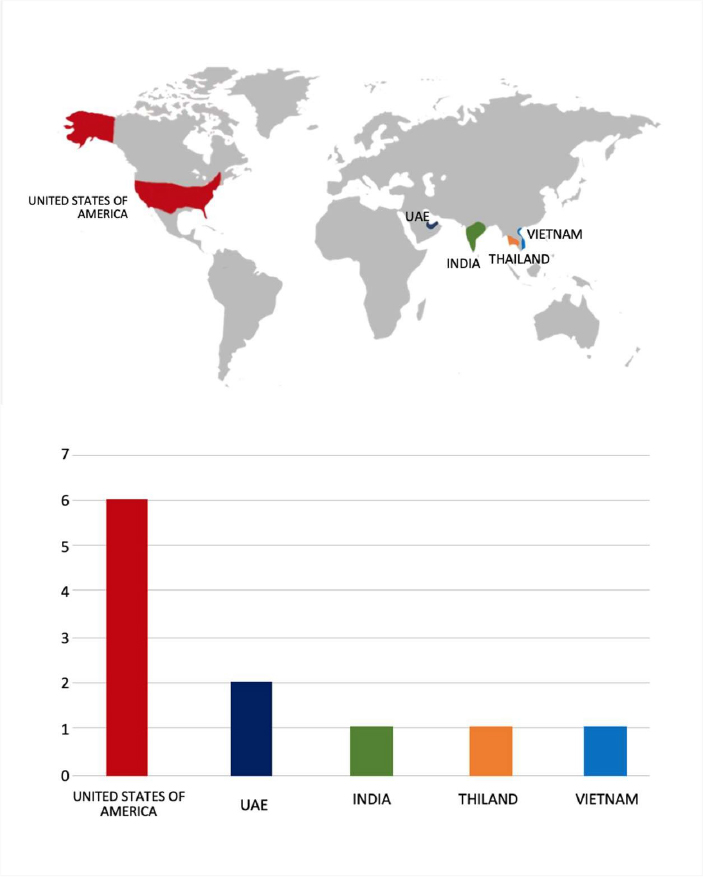
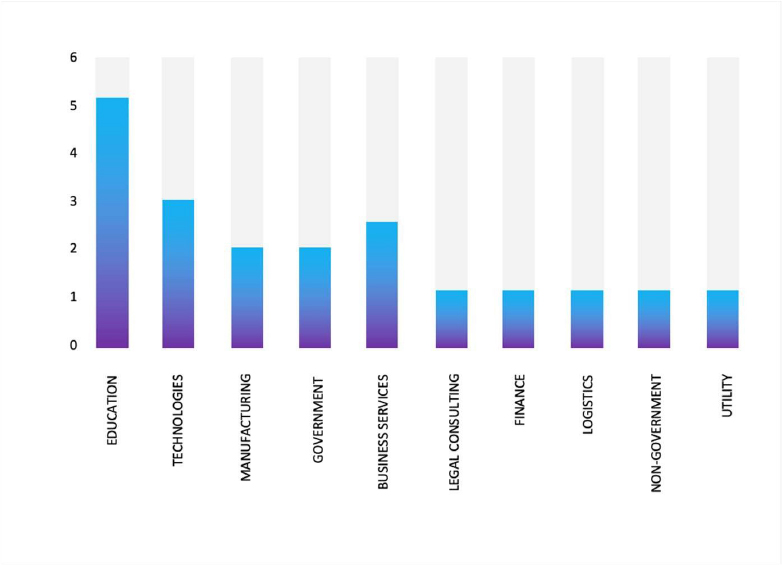
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.