


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Ndm448 Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Ndm448 Ransomware
Researchers identified that Ndm448 is a ransomware strain belonging to the Makop ransomware family. Once executed on a Windows system, Ndm448 performs full file encryption across local and accessible network drives, appending a distinctive extension that includes a unique victim ID, the attacker’s contact email, and the suffix .ndm448. In addition to cryptographic file locking, the malware alters file metadata, drops ransom- related artifacts, and changes the desktop wallpaper to signal compromise. Its behavior aligns with Makop’s established tradecraft, including targeted directory enumeration, rapid encryption to maximize impact, and indicators consistent with double-extortion campaigns where data theft accompanies encryption.

Screenshot of files encrypted by the ransomware (Source: Surface Web)
The ransom note, delivered via a text file such as +README-WARNING+.txt, is written in a coercive and authoritative tone and explicitly claims that sensitive corporate data has been exfiltrated prior to encryption. It instructs victims to contact the attackers via the listed email address or a qTox chat ID, asserting that this is the “only” way to resolve the incident. The note forbids system restarts, file modifications, or the use of third-party software, alleging these actions could irreversibly damage encrypted data statements commonly used to deter investigation or mitigation. It outlines deadlines for payment, threatens public disclosure or sale of stolen information, and claims that decryption keys will be destroyed if demands are not met, reinforcing the pressure typical of Makop’s double-extortion ransomware operations.
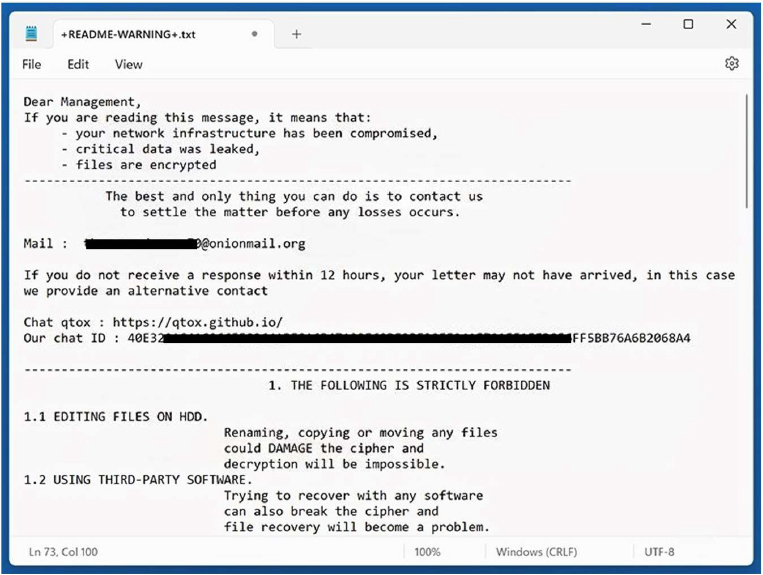
The appearance of the Ndm448 ransom note (+README-WARNING+.txt) (Source: Surface Web)
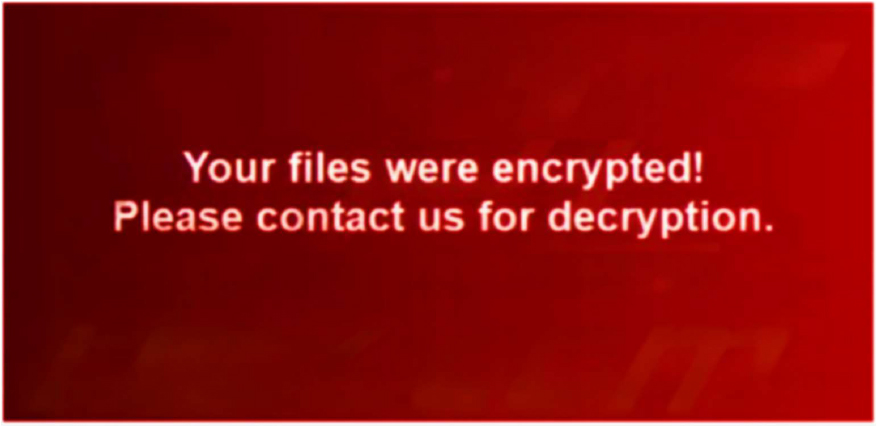
The appearance of the Ndm448 ransomware Wallpaper after encryption (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1129 | Shared Modules |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Collection | T1115 | Clipboard Data |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that this ransomware is actively aligned with enterprise-targeted attack scenarios rather than opportunistic or consumer-grade infections. The process executes within an authenticated user session, systematically accesses user profile directories and shared system paths, and deliberately disables Volume Shadow Copies that are commonly relied upon in corporate backup and recovery workflows. Its interaction with extensive registry structures, execution controls, and system configuration artifacts reflects familiarity with managed Windows environments, enabling the malware to affect a broad spectrum of business-critical data rather than isolated personal files.
CYFIRMA assesses that this ransomware represents a scalable enterprise threat with a clear trajectory toward higher-value and wider-impact operations. Its current behavior already supports disruption across endpoints commonly found in corporate networks, and the underlying execution logic could be readily extended to aggressively target mapped network drives, shared storage, and backup repositories that are prevalent in enterprise environments. The combination of systematic file enumeration, recovery inhibition, and execution through trusted system utilities positions the ransomware well for integration into affiliate-based distribution models or coordinated campaigns against larger organizations. As ransomware ecosystems continue to evolve toward data-centric and operationally disruptive extortion, this variant is likely to adopt more aggressive targeting strategies, focusing on environments where downtime, data inaccessibility, and regulatory exposure significantly amplify ransom pressure.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems. (Source: Surface Web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information stealer (RAT)| Objectives: Data Exfiltration | Target Technology: Windows OS | Target Geography: Cambodia
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “GhostRAT Loader” is trending.
Overview of Operation GhostRAT Loader
Security researchers have identified a sophisticated malware sample known as GhostRAT Loader. Based on our analysis of the sample, this specimen acts as a delivery mechanism that downloads and executes GhostRAT malware, a Windows-based Trojan, which exhibits malicious behavior upon successful execution. After launch, the program silently initiates multiple background processes and deploys additional components across the system, indicating a staged infection rather than a single-step compromise. Several of these activities are designed to appear routine to the user, enabling the malware to blend into the operating environment and establish a foothold without raising immediate suspicion. This approach increases the likelihood of the threat remaining undetected for extended periods.
A notable characteristic of this malware is its emphasis on persistence and operational stability. The threat attempts to maintain functionality even after system restarts by altering system configurations and creating mechanisms that allow automatic relaunch. It also interacts with legitimate processes within Windows environments in a manner that helps conceal its presence, complicating detection efforts. Such behavior indicates that malware is not a simple, isolated infection but part of a more structured framework that sustains long-term access to compromised devices.
Analysis further revealed attempts to communicate with external servers, suggesting the capability for remote command execution or data exchange. Some network activity may initially appear normal, which is a common tactic used by attackers to avoid triggering security alerts while verifying connectivity or establishing control channels. This external communication capability increases the risk that compromised systems could be used for information theft, remote monitoring, or the delivery of additional malicious payloads over time.
Overall, the observed behavior reflects a modern threat model that prioritizes stealth, persistence, and controlled remote interaction. By operating quietly in the background and integrating itself into normal system processes, it creates conditions for prolonged unauthorized access and potential data exposure. These findings reinforce the importance of vigilant security practices and cautious handling of unfamiliar files to minimize the risk of compromise.
Attack Method
The attack begins with the execution of a malicious file that leverages command-line scripting and dynamically loaded modules to initiate its operation. By leveraging built- in system interpreters and shared components, the malware can run code without relying on obvious standalone executables, which helps it blend into normal system activity. During this early phase, the threat may also modify system settings and registry entries to prepare the environment for continued execution while attempting to gain elevated privileges through manipulation of access tokens. These steps allow the attackers to increase control over the system while reducing the likelihood of interruption.
Once the malware is active, it establishes persistence mechanisms to ensure that it can automatically restart when the system boots or a user logs in. This is achieved through changes to configuration settings and startup-related components, enabling long-term presence on the compromised device. At the same time, the threat employs defense-evasion techniques such as obfuscating its files, altering permissions, and further modifying registry data to conceal its activity. These measures make it more difficult for security tools and analysts to identify or remove the infection, allowing the malware to operate quietly in the background.
After securing persistence, the malware performs a series of discovery actions to gather information about the system, including installed applications, files, and operating environment details. It may also monitor user activity by collecting clipboard content or capturing visual data from the system, which can provide sensitive information to the attackers. In certain scenarios, the malware can disrupt normal operations by forcing system restarts or shutdowns, either to cover its tracks or to complete specific stages of the attack. Overall, the method demonstrates a structured intrusion process that combines execution, persistence, evasion, and data collection to maintain control and extract value from the compromised system.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic(ID) | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1115 | Clipboard Data |
| Collection | T1125 | Video Capture |
| Impact | T1529 | System Shutdown/Reboot |
INSIGHTS
This campaign shows how modern malware relies more on user habits and trust than on advanced technical tricks. By spreading through platforms that users already consider familiar or acceptable, attackers make it easier for people to run infected files without hesitation, even when the software comes from unofficial sources.
The long-running nature of the activity suggests it is strategically planned and managed. Instead of trying to cause quick damage, the attackers focus on steady and controlled distribution, allowing the campaign to continue smoothly over time and reach many users.
The operation also highlights a clear focus on staying hidden rather than being disruptive. The malicious code is designed to run quietly alongside normal applications, reducing the probability that users will perceive abnormal behavior. This approach shows that many modern malware campaigns aim to stay active for as long as possible rather than creating immediate, visible problems.
ETLM ASSESSMENT
From an ETLM point of view, this activity shows how malware campaigns are increasingly built around everyday user behavior rather than direct attacks on enterprise systems. As personal and work-related digital use continues to mix, infections that start on home or non-corporate devices can later create ongoing risks for organizations, especially when stolen credentials or digital identities are reused to access business platforms. Because this misuse often happens much later, it becomes harder to detect, investigate, and respond to. Over time, these quiet and gradual compromises can change an organization’s overall risk posture, challenging traditional ideas about where threats begin and placing greater importance on managing user-driven exposure and long-term security risks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems. (Source: Surface Web)
YARA Rules
rule Suspicious_Malware_Indicator_GhostRAT
{
meta:
description = “Detects malware sample related to suspicious campaign” author = “CYFIRMA”
date = “2026-02-17”
severity = “high”
strings:
/* Malware Sample Hash */
$hash_1 = “b0521ad45fd21cdae26afdc74307870c5859421e049bbff2a545852b0ccf0fe6”
condition:
any of ($hash_*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Key Intelligence Signals:
UNC3886 (Volt Typhoon): Strategic Cyber Espionage Operations Impacting Critical Infrastructure
About the Threat Actor
Volt Typhoon is a highly advanced nation-state cyber-espionage threat actor linked to China and assessed to have been operational since 2021. The group consistently demonstrates sophisticated capabilities, including the exploitation of zero-day vulnerabilities and stealth-focused techniques to conduct targeted intrusions across strategic sectors, such as defense, government, telecommunications, and technology.
Volt Typhoon primarily conducts intelligence collection operations against both public sector entities and private enterprises. Its campaigns are marked by meticulous planning, the use of bespoke malware, and covert access methods, positioning the group among the most capable actors in today’s cyber threat landscape.
Historically, Volt Typhoon has focused on compromising network infrastructure and virtualization technologies, reflecting deep expertise in complex enterprise environments. Its toolset includes highly customized and evasive malware designed to maintain persistence and enable long-term data exfiltration.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2024-21762 | Fortinet FortiOS versions | 9.8 | – |
| CVE-2024-21887 | Ivanti Connect Secure | 9.1 | Link |
| CVE-2022-42475 | FortiOS SSL-VPN (All versions) | 9.8 | – |
| CVE-2023-34048 | vCenter Server | 9.8 | – |
| CVE-2023-20867 | VMware Tools | 3.9 | – |
| CVE-2022-41328 | Fortinet FortiOS | 7.1 | – |
| CVE-2022-22948 | vCenter Server | 6.5 | – |
| CVE-2023-27997 | FortiOS | 9.8 | – |
| CVE-2021-40539 | Zoho ManageEngine ADSelfService | 9.8 | Link |
| CVE-2024-23113 | Fortinet FortiOS (All versions) | 9.8 | – |
| CVE-2024-22024 | Ivanti Connect Secure | 8.3 | – |
| CVE-2024-39717 | Versa Director GUI | 7.2 | – |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1596.005 | Search Open Technical Databases: Scan Databases |
| Reconnaissance | T1592 | Gather Victim Host Information |
| Reconnaissance | T1589 | Gather Victim Identity Information |
| Reconn aissance |
T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1590 | Gather Victim Network Information |
| Reconnaissance | T1590.004 | Gather Victim Network Information: Network Topology |
| Reconnaissance | T1590.006 | Gather Victim Network Information: Network Security Appliances |
| Reconnaissance | T1591.004 | Gather Victim Org Information: Identify Roles |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1593 | Search Open Websites/Domains |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1584.003 | Compromise Infrastructure: Virtual Private Server |
| Resource Development | T1584.005 | Compromise Infrastructure: Botnet |
| Resource Development | T1584.008 | Compromise Infrastructure: Network Devices |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1587.004 | Develop Capabilities: Exploits |
| Resource Development | T1588.006 | Obtain Capabilities: Vulnerabilities |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1078.002 | Valid Accounts: Domain Accounts |
| Initial Access | T1078 | Valid Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.004 | Command and Scripting Interpreter: Unix Shell |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Persistence | T1133 | External Remote Services |
| Persistence | T1546 | Event Triggered Execution |
| Persistence | T1112 | Modify Registry |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078.002 | Valid Accounts: Domain Accounts |
| Privilege Escalation | T1546 | Event Triggered Execution |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Privilege Escalation | T1055.009 | Process Injection: Proc Memory |
| Privilege Escalation | T1078 | Valid Accounts |
| Privilege Escalation | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1055.009 | Process Injection: Proc Memory |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1222.002 | File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification |
| Defense Evasion | T1564.013 | Hide Artifacts: Bind Mounts |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1078.002 | Valid Accounts: Domain Accounts |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1070.007 | Indicator Removal: Clear Network Connection History and Configurations |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1218 | System Binary Proxy Execution |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.004 | Unsecured Credentials: Private Keys |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1680 | Local Storage Discovery |
| Discovery | T1654 | Log Enumeration |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1087.001 | Account Discovery: Local Account |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1217 | Browser Information Discovery |
| Discovery | T1069 | Permission Groups Discovery |
| Discovery | T1069.001 | Permission Groups Discovery: Local Groups |
| Discovery | T1069.002 | Permission Groups Discovery: Domain Groups |
| Discovery | T1012 | Query Registry |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1614 | System Location Discovery |
| Discovery | T1016.001 | System Network Configuration Discovery: Internet Connection Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1124 | System Time Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1570 | Lateral Tool Transfer |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1056 | Input Capture |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1573.002 | Encrypted Channel: Asymmetric Cryptography |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1090 | Proxy |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
Latest Developments Observed
The threat actor is suspected of targeting Singapore’s telecommunications organisations with the objective of conducting espionage and maintaining long- term persistence within victim networks. As part of the initial access phase, the actor is believed to have leveraged advanced tools and techniques, including potential zero-day exploits, to infiltrate the networks.
ETLM Insights
UNC3886 is assessed as a state-linked cyber espionage actor whose primary objective is long-term intelligence collection rather than financial gain or short-term disruption. The group’s recent activity displays a focus on gaining and maintaining access to networks that carry sensitive operational and communications data, supporting sustained visibility into critical service environments.
Operationally, UNC3886 prioritizes stealth and long-term presence within complex enterprise and service provider networks. The group demonstrates a preference for maintaining durable access while avoiding service disruption, indicating an emphasis on remaining covert to preserve intelligence collection opportunities over extended periods.
Based on observed activity, UNC3886 is likely to continue targeting high-value service environments to sustain long-term access for intelligence purposes. This positions the group as an ongoing espionage threat to critical service providers, with continued risk to organizational security posture and the confidentiality of sensitive operational information.
YARA Rules
rule UNC3886_IOC_Detection
{
meta:
description = “Detects malware and activity associated with UNC3886 based on known IOCs”
author = “CYFIRMA” date = “2026-02-17”
reference = “CSA Singapore / UNC3886 campaign” confidence = “medium”
false_positive = “low”
strings:
// Domain IOC
$d1 = “pdsguam.biz” ascii nocase
// File name IOCs
$f1 = “systemhelper.exe” ascii nocase
$f2 = “5dciv4.exe” ascii nocase
$f3 = “nkqs0h4b.oeeyscan.exe” ascii nocase
$f4 = “entohyal_spaulder.exe” ascii nocase
$f5 = “yotygg.exe” ascii nocase
// IP address IOCs (as strings commonly embedded in configs)
$ip1 = “3.224.205.25” ascii
$ip2 = “91.132.144.59” ascii
$ip3 = “198.235.24.94” ascii
$ip4 = “103.250.11.84” ascii
$ip5 = “67.195.204.56” ascii
condition:
any of ($d*) or 2 of ($f*) or any of ($ip*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Russia’s hacktivists target the Winter Olympics
Since the 2026 Winter Olympics opened in Milan and Cortina d’Ampezzo on February 6, cybersecurity researchers have tracked a noticeable increase in pro-Russian hacktivist activity. Russia’s exclusion from the Games – stemming from the ongoing war in Ukraine – prompted expectations of digital pushback, echoing the cyberattacks linked to Russian actors during the 2018 PyeongChang Winter Olympics, following a doping-related ban. The prominent pro-Russian group NoName057(16) carried out DDoS (distributed denial-of-service) attacks on Italian targets in the host cities of Milan and Cortina. The group publicly claimed responsibility for strikes against the Lithuanian, Polish, and Spanish national Olympic committees, a tourism website for Cortina d’Ampezzo, and Milan Malpensa Airport.
Other hacktivist collectives reportedly hit websites of two Italian airports and Italian critical infrastructure. Italian authorities confirmed these incidents but stated that defenses successfully mitigated them, resulting in no significant disruptions or lasting effects.
ETLM Assessment:
Unlike the 2018 Olympics, where attacks were directly attributed to Russian state-linked actors, the current wave appears driven by relatively unsophisticated hacktivist outfits rather than government-directed operations. While state-backed groups could be conducting stealthier, persistence-focused intrusions on Olympic-related entities, such efforts would likely rank as lower-priority objectives for the Kremlin compared to more pressing strategic concerns amid the Ukraine conflict. The primary aim seems to be symbolic disruption and propaganda rather than high-impact sabotage.
US National Cyber Director calls for deeper collaboration in Munich
US National Cyber Director Sean Cairncross addressed the Munich Cyber Security Conference, emphasizing the need for stronger international partnerships in cyberspace. Speaking in Munich, Germany, he stated that the United States aims to build deeper cyber cooperation with allies and the private sector to deliver a “coordinated, strategic message” capable of altering adversaries’ risk calculus and decision-making processes. Cairncross stressed that an “America first” policy—echoing language from Secretary of State Marco Rubio—does not equate to “America alone.”
ETLM Assessment:
The U.S. administration, in the face of fractures in the NATO alliance, has lately moved to highlight shared threats from a range of actors, including nation-state operatives (most notably China), espionage networks, ransomware gangs, and scam operations, arguing that these escalating challenges demand collective responses rather than unilateral action. U.S. officials underscored the critical role of the private sector, which shoulders much of the day-to-day burden in defending against cyber threats. Washington continues to advocate for enhanced information sharing and tighter coordination between governments and companies to more effectively counter these dangers and reiterates the current administration’s approach, under which cybersecurity is being elevated as a core strategic domain.
North Korea using elaborate scams and malware to target the crypto sector
Researchers have observed the North Korean threat actor tracked as “UNC1069” using a combination of social engineering techniques alongside seven unique malware families to target the cryptocurrency and DeFi sectors. According to the researchers, the attackers “relied on a social engineering scheme involving a compromised Telegram account, a fake Zoom meeting, a ClickFix infection vector, and reported usage of AI-generated video to deceive the victim.“
ETLM Assessment:
UNC1069 typically targets cryptocurrency startups, software developers, and venture capital firms. As noted in this CYFIRMA report, Pyongyang has spent years systematically refining an ever-expanding toolkit to generate hard currency for its nuclear and ballistic-missile programs, which run the gamut from classic diplomatic cover and ship-to-ship transfers to aggressive cyber theft and, more recently, the large-scale deployment of highly skilled IT workers operating under false identities abroad. But it is cybercrime that has rapidly become a cornerstone of North Korea’s state survival.
Qilin Ransomware Impacts Anabuki Kosan Inc
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Anabuki Kosan Inc (https[:]//www[.]anabuki[.]ne[.]jp/), was compromised by Qilin Ransomware. Anabuki Kosan Inc. is a leading real estate company in Japan focused primarily on condominium development and comprehensive property-related services. It is a core member of the broader Anabuki Group, which operates across multiple sectors, including real estate, renewable energy, senior care, and other lifestyle services both in Japan and internationally. According to the screenshot from the ransomware group’s website, the attack appears to have led to the exposure of several categories of highly sensitive information. The leaked content includes personally identifiable information (PII) such as full names, photographs, dates of birth, gender, residential addresses, and contact details displayed on identification documents. Multiple thumbnails show government-issued ID cards and passport-style documents, suggesting that official identity records were compromised. In addition, the presence of structured spreadsheets and tabulated documents indicates that employee records, payroll data, financial statements, and other internal administrative files may have been disclosed. Architectural floor plans and technical drawings are also visible, pointing to the exposure of operational and infrastructure-related documents. Overall, the breach appears to involve extensive personal, financial, and organizational data, with the total volume of compromised information estimated at approximately 240 GB.
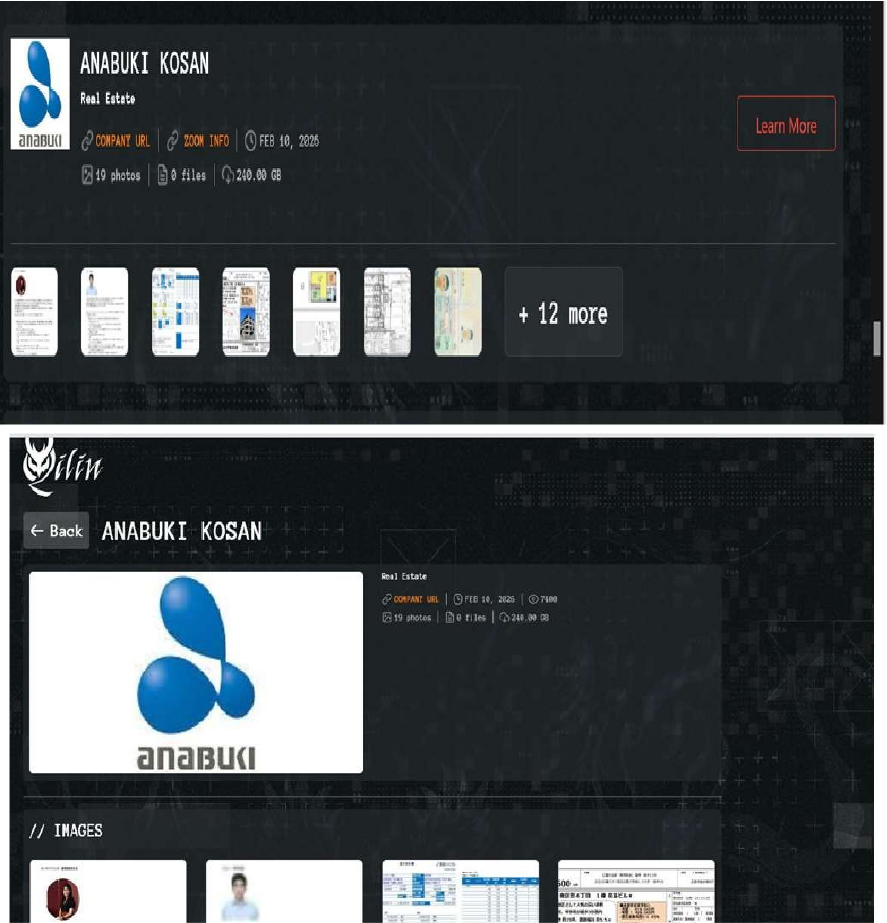
Source: Dark Web
Relevancy & Insights:
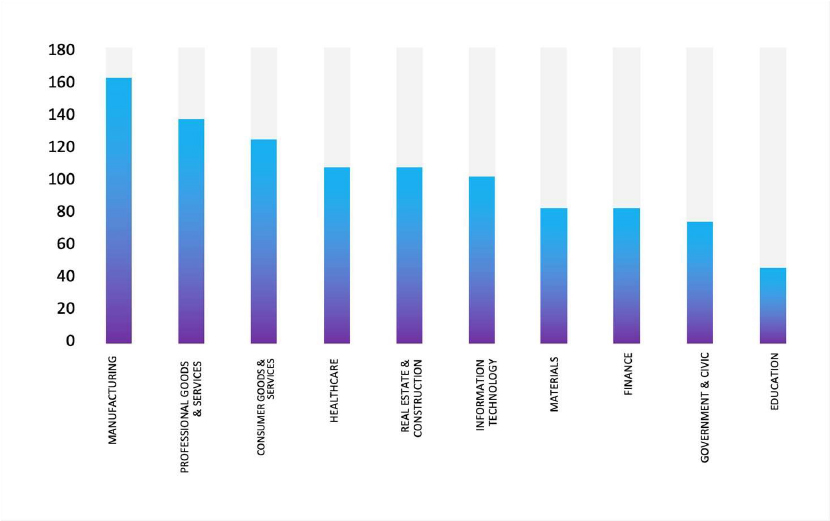
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
The Gentlemen Ransomware Impacts Nishiyama Seisakusho
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Nishiyama Seisakusho Ltd(https[:]//www[.]nishiyama-ss[.]co[.]jp/), was compromised by the Gentlemen Ransomware. Nishiyama Seisakusho Co., Ltd. specializes in the production of precision machinery and components, particularly focusing on high- quality manufacturing. The company offers a range of products, including precision gears and mechanical parts, catering to various industries. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.

Source: Dark Web
Relevancy & Insights:
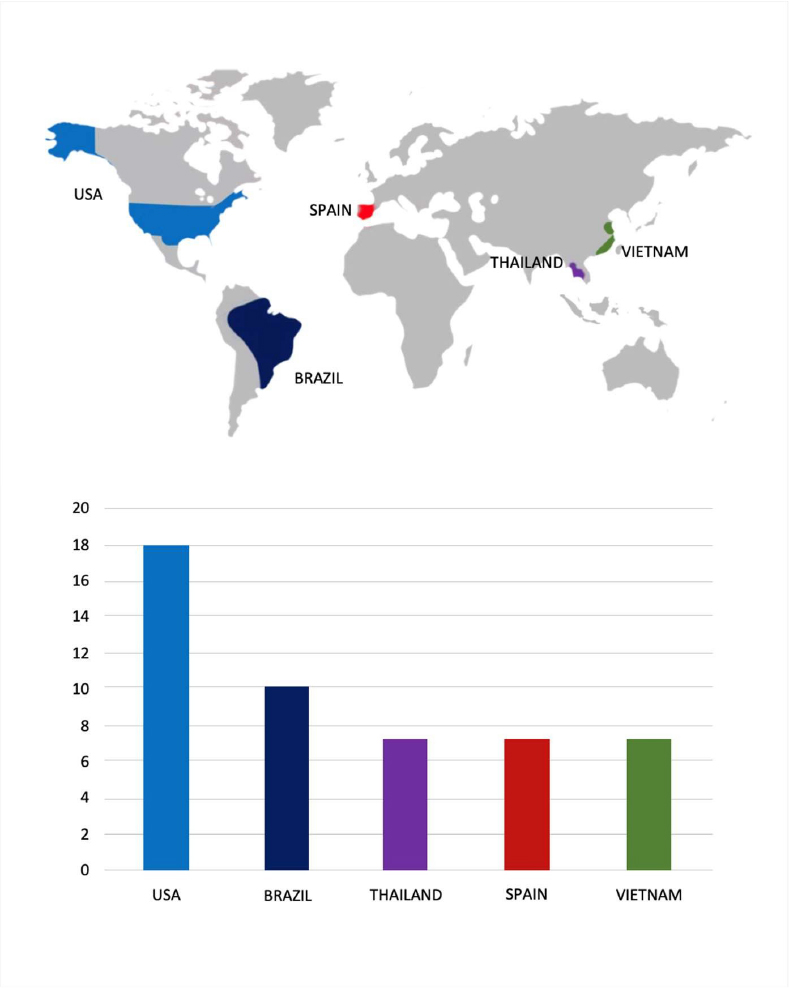
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen Ransomware is a highly adaptive and globally active threat that leverages dual-extortion tactics, combining data theft with file encryption. The group employs advanced evasion and persistence techniques, supports cross-platform and scalable ransomware deployment, and conducts targeted attacks across multiple industries and geographic regions. This combination of capabilities makes it a significant risk to enterprise cybersecurity defenses, particularly for organizations with limited detection and incident-response maturity.
Vulnerability in Intel Memory and Storage Tool (MAS)
Relevancy & Insights:
The vulnerability exists due to incorrect default permissions for files and folders that are set by the application.
Impact:
A local user can gain elevated privileges on the target system.
Affected Products:
https[:]//www[.]intel[.]com/content/www/us/en/security- center/advisory/intel-sa-01414[.]html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
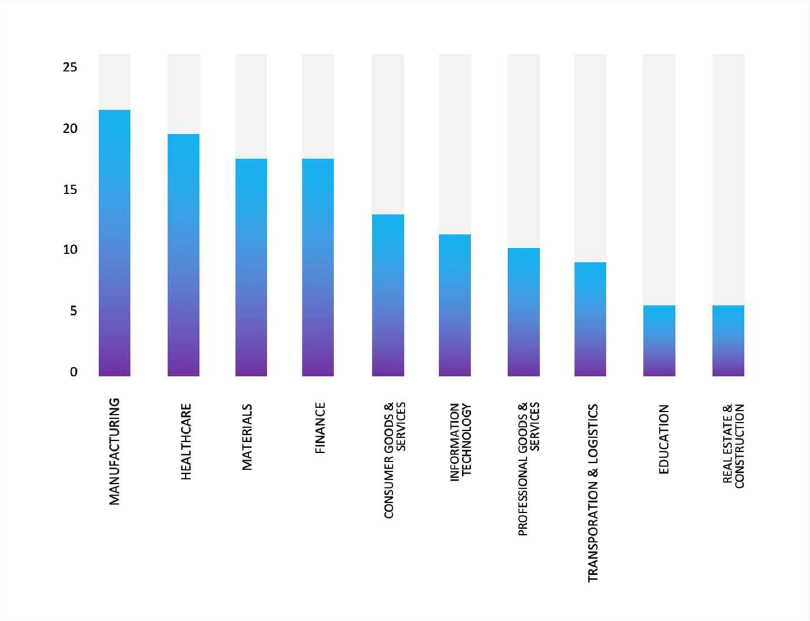
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Intel Memory and Storage Tool introduces potential privilege escalation risks that could impact system stability and trust boundaries within enterprise environments. While exploitation requires local authenticated access and high attacker complexity, incorrect default permissions can undermine the security posture of systems relying on this management tool. This can affect organization infrastructures that use Intel storage management solutions in servers, workstations, and data center environments. Ensuring correct permission configurations and updating to the latest patched versions is essential to prevent unauthorized privilege escalation and protect sensitive storage management operations across deployments.
Space Bears Ransomware attacked and published the data of Texcomp
Summary:
Recently, we observed that Space Bears Ransomware attacked and published the data of Texcomp(https[:]//texcomp[.]com/) on its dark web website. Texcomp is an IT services, consulting, and business solutions company that helps organizations adopt modern technology to enhance efficiency, automation, and digital transformation. It provides a range of software products and technology solutions for businesses across multiple industries. The ransomware incident led to the exposure of an SQL database containing client and partner information, including names, email addresses, physical addresses, phone numbers, and other related contact details.
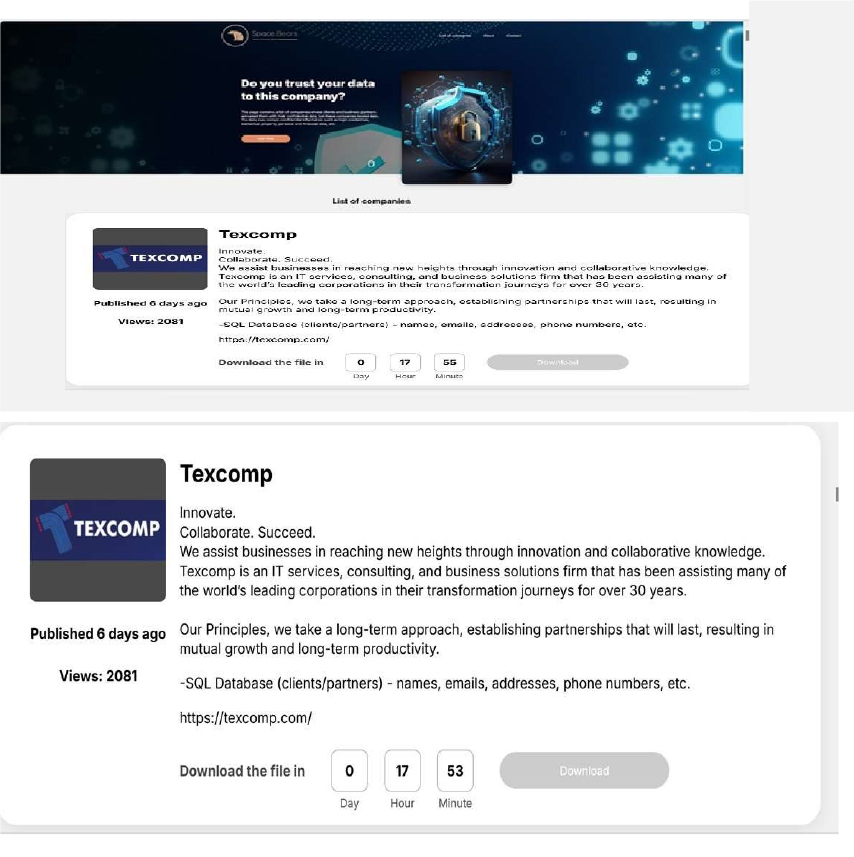
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Space Bears ransomware represents a significant threat in the evolving landscape of cybercrime. With its aggressive tactics, association with established ransomware operations like Phobos, and focus on double extortion, organizations are advised to bolster their cybersecurity measures to mitigate risks associated with such attacks. Continuous monitoring of this group’s activities will be essential for understanding their methods and potential impact on various sectors.
Nippon Medical School Musashi Kosugi Hospital Patient Data Advertised on a Leak Site
Summary:
The CYFIRMA research team has identified a post published on a well-known hacking forum by a threat actor operating under the alias “NetRunnerPR”, claiming responsibility for a data breach involving Nippon Medical School Musashi Kosugi Hospital.
According to the actor, they allegedly breached the hospital’s network and exfiltrated approximately 131,135 unique personally identifiable information (PII) records, along with a full database export. The post suggests that additional data may be released subsequently. The actor also references media coverage by Asahi News and acknowledges reporting by Nikkei regarding the incident.
Based on the sample data shared in the forum post, the allegedly compromised information includes:
The authenticity of the breach claim remains unverified at the time of reporting, as the information currently originates solely from the threat actor’s forum post.
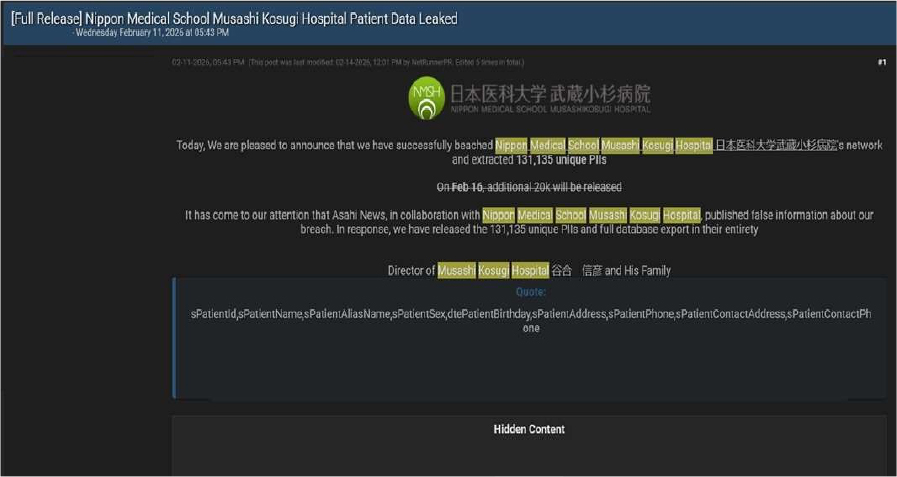
Source: Underground Forums
APGO Taiwan Data Advertised on a Leak Site
Summary:
The CYFIRMA research team identified that APGO Taiwan, a retailer specializing in automotive coating and detailing products, has allegedly been compromised. A threat actor “k0rb3nd4ll4s” has claimed to leak a database containing customer information on a cybercrime forum. The leak reportedly occurred in 2026, with the actor offering the data for download to the community.
According to the actor, the compromised database contains approximately 12,299 customer records. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
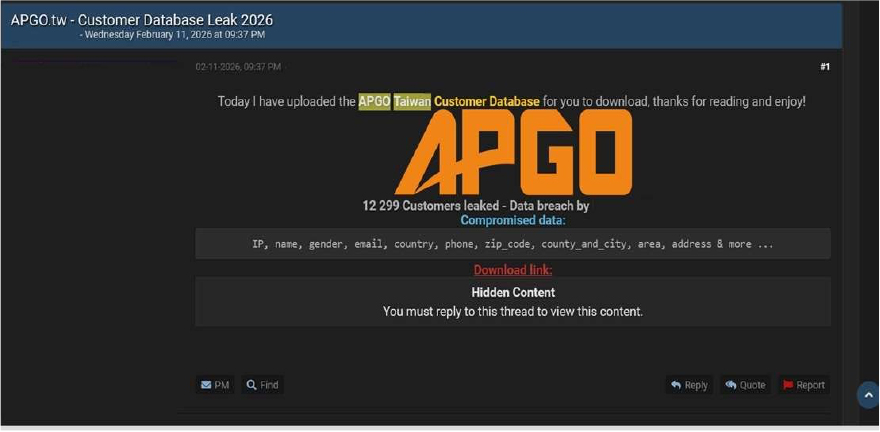
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known by the alias “NetRunnerPR” is assessed to be a recently emerged but highly active and capable entity, primarily engaged in data-leak operations. The group’s activity highlights the persistent and fast-evolving cyber threat landscape, driven by underground criminal ecosystems. This development underscores the urgent need for organizations to reinforce their cybersecurity posture through continuous monitoring, improved threat intelligence capabilities, and proactive defensive strategies to protect sensitive information and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that WormGPT.AI, a platform known for offering uncensored artificial intelligence models for hacking purposes, has allegedly been compromised. Detailed records belonging to the site’s user base were posted on a cybercrime forum by an actor who claims to have uploaded the full database for public download. The leak reportedly affects over 19,000 unique users who utilized the service in February 2026.
According to the actor and the samples provided, the compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
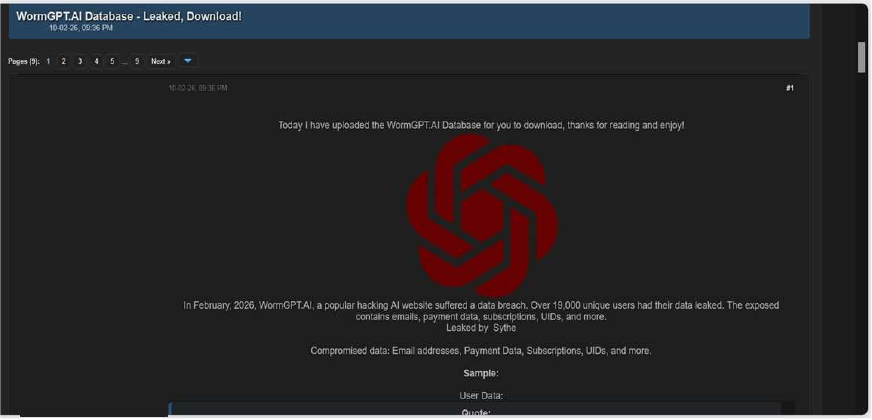
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
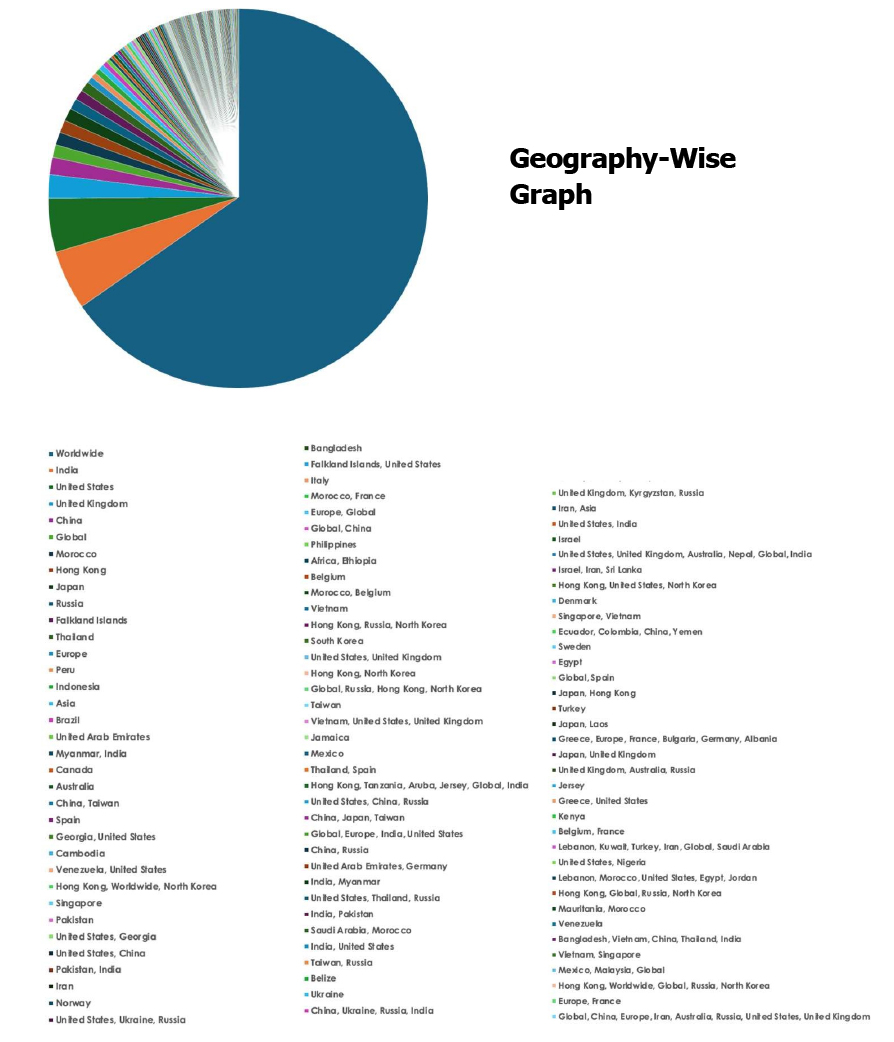

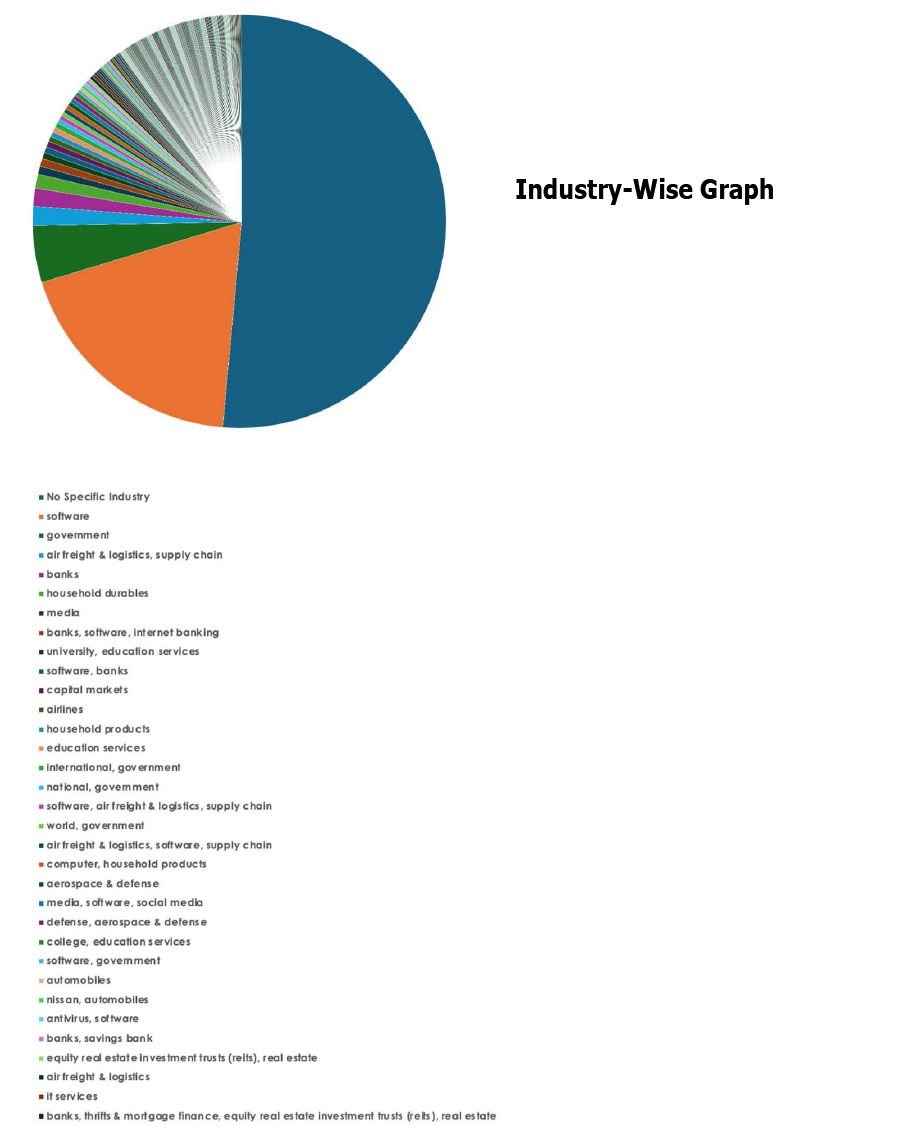
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.