



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Hitler_77777 Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Hitler_77777 Ransomware
Researchers recently identified a new ransomware strain called Hitler_77777. Once it infiltrates a victim’s system, it encrypts files and appends three elements to their names: the victim’s unique ID, a Telegram ID, and a four-character extension.
In addition to encrypting files, Hitler_77777 alters the desktop wallpaper and delivers ransom instructions through two methods—a pop-up window and a text file named “#README-TO-DECRYPT-FILES.txt”.
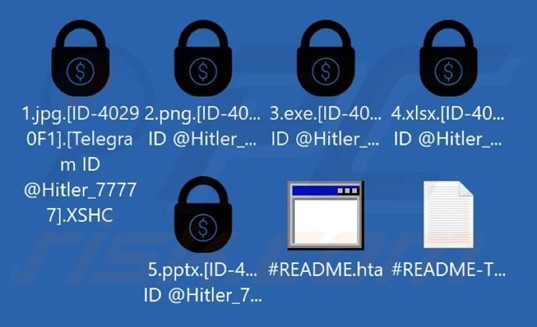
Screenshot of files encrypted by this ransomware (Source: Surface Web)
The ransom note notifies the victim that their network has been breached, critical data has been exfiltrated, and all files have been encrypted. It instructs the victim to contact the attackers via Telegram for resolution. Additionally, it warns against modifying files, using third-party decryption tools, or restarting the system, as these actions could result in permanent data loss.
The note further claims that the attackers have stolen sensitive information, including legal documents and financial records, threatening to sell or publicly disclose the data if the ransom is not paid.
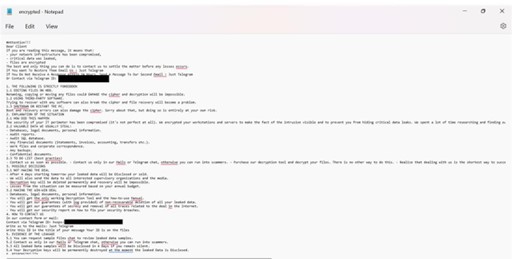
Content of the ransom note in a pop-up window (Source: Surface Web)
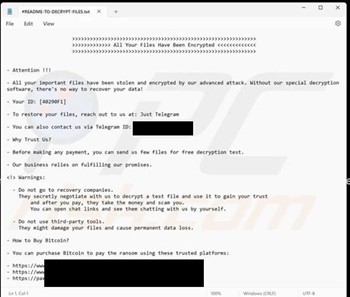
Screenshot of Hitler_77777’s text file (“README-TO-DECRYPT-FILES.txt“): (Source: Surface Web)
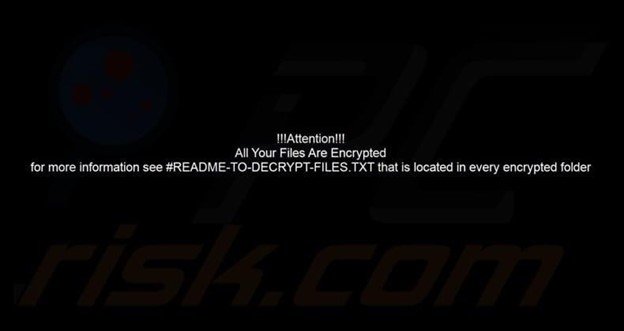
Screenshot of Hitler_77777’s desktop wallpaper: (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Tactics | ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1482 | Domain Trust Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1005 | Data from Local System |
| Collection | T1056 | Input Capture |
| Collection | T1114 | Email Collection |
| Collection | T1560 | Archive Collected Data |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of the available data indicates that the Hitler_77777 ransomware may pose a substantial threat across multiple regions. It primarily targets companies, with financial gain as its main motive, making it a significant risk to industries such as manufacturing, finance, and other critical sectors. Future variants could incorporate stronger encryption algorithms, more advanced evasion tactics, and an expanded range of targeted industries. Maintaining vigilance and implementing robust cybersecurity measures will be critical to mitigating these evolving threats.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
category: process_creation product: windows
detection: selection1_img:
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli: CommandLine|contains|all:
CommandLine|contains|all:
CommandLine|contains|all:
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objectives: Stealing Credit card Information
Target Technology: eCommerce platforms
Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “MageCart” is trending. MageCart
Researchers discovered a credit card-stealing malware, known as MageCart, which specifically targets websites running on eCommerce platforms like Magento, WooCommerce, and PrestaShop. The goal of attackers is to remain undetected for as long as possible, using more complex malware than the typical threats found on other sites. This sophisticated malware is often injected into the site in ways that blend seamlessly with the site’s code, such as being concealed within an <img> tag, making it difficult to detect and allowing the attackers to steal credit card information over extended periods.
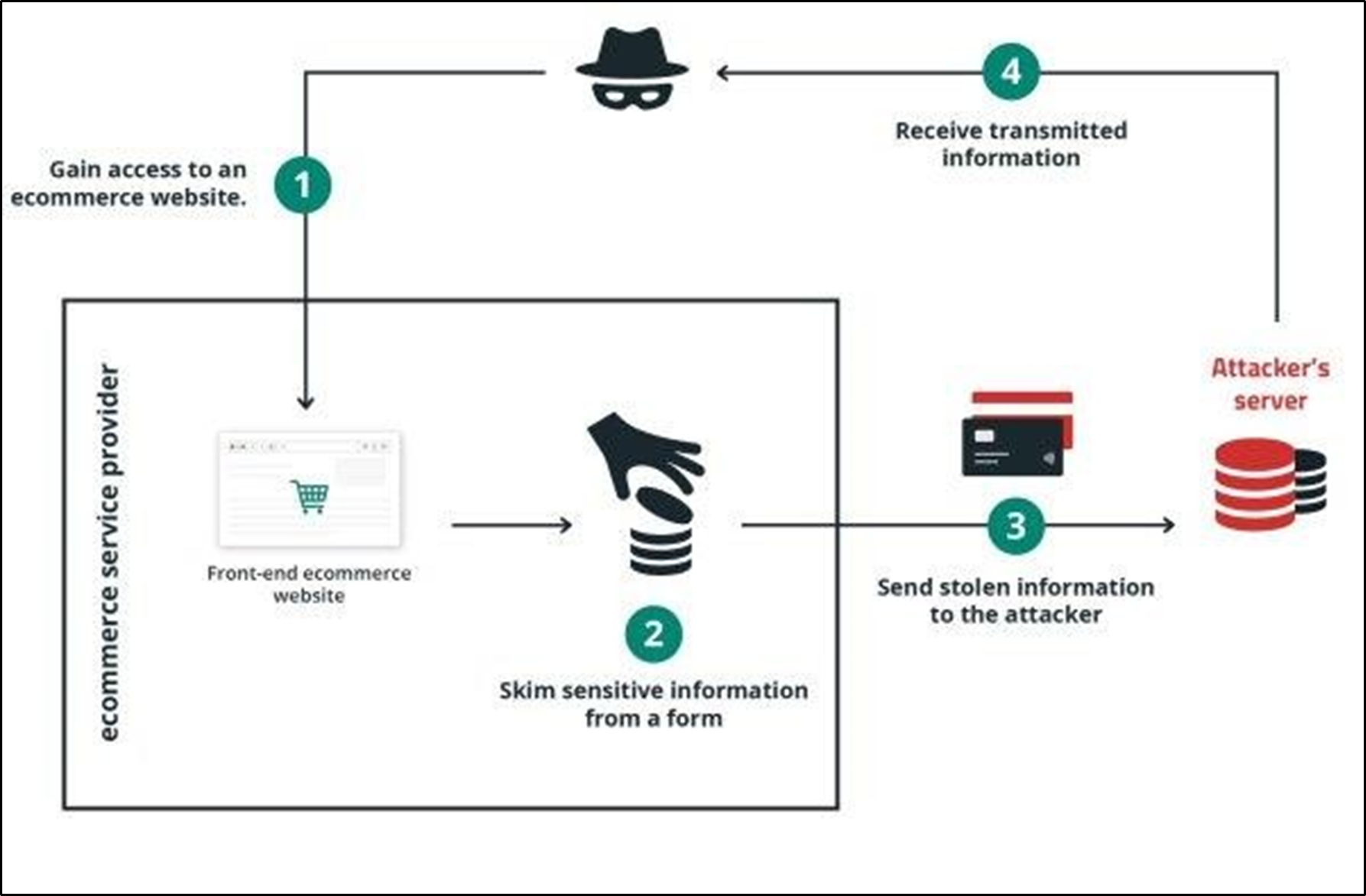
Attack method
While the initial access method remains unclear, attackers may exploit vulnerabilities or security flaws in a website’s infrastructure. This malware activates only during the checkout process, typically on the page where customers enter their credit card details. Researchers observed the page source after an item was added to the cart and payment stage was reached, which is crucial because the malware is designed to load only at this point to avoid detection.
The malicious code often hides within an <img> tag, which typically contains image file paths. However, in this case, it holds a large chunk of Base64-encoded content instead of an actual image. While Base64 can be used for small images, its presence here is suspicious. The tag is specifically placed on the checkout page, suggesting it’s a decoy to hide malicious JavaScript. The trick lies in the use of an “onerror” function, which normally handles image loading errors. However, here it is hijacked to execute the malicious script. This makes the attack harder for security tools to detect, as the browser trusts this function (a standard part of handling errors) and often overlooks the <img> tag, which is why this attack remains undetected.
The malicious script is Base64-encoded and decoded using online tools. Once decoded, the script checks if the user is on the checkout page and if it hasn’t executed yet in the current session. After confirming these conditions, the script waits for user interaction, typically when the submit button is clicked, and monitors the credit card fields. If filled, the script triggers the magictrick() function to collect and send the data to a remote server.
To collect sensitive information like the card number, expiration date, and CVV, the script dynamically inserts a hidden malicious form into the page. It ensures that only numeric characters are accepted, filtering out non-numeric inputs. The encoded data is then sent to a remote server at wellfacing[.]com for malicious use. To avoid detection, the script hides the malicious code within an <img> tag and inserts the form discreetly, ensuring the malware stays undetected and continues harvesting sensitive data. The stolen data is stored and exploited for malicious purposes.
Insights
MageCart is a significant and evolving threat in the realm of eCommerce, where attackers focus on stealing payment information from unsuspecting The campaign primarily targets online stores running on popular eCommerce platforms. Unlike traditional threats, MageCart is highly stealthy, often remaining undetected for long periods while quietly siphoning off sensitive customer data. This persistence is due to the malware’s ability to seamlessly blend into the website’s infrastructure and function without raising any immediate red flags for the website’s visitors or security systems.
One of the unique characteristics of the MageCart campaign is its selective The malware triggers only during specific user interactions, particularly when the user reaches the checkout page, where they input their credit card information. This strategic approach allows MageCart to avoid detection during the browsing experience and significantly limits its exposure. By waiting until the customer is committed to making a purchase, attackers maximize the likelihood of obtaining sensitive information without alarming the user or alerting site administrators to suspicious activity.
The long-term impact of MageCart’s activities extends beyond just immediate data The stolen information is typically used for fraudulent purchases or sold on the dark web, contributing to a broader financial crime ecosystem. Its stealthy nature also complicates remediation efforts for businesses, as they may not notice the compromise until significant damage is done. Given the campaign’s ability to scale across numerous online retailers, MageCart represents an ongoing challenge for cybersecurity, requiring constant vigilance and proactive security measures to mitigate its growing reach and sophistication.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that MageCart’s evolution suggests that future attacks will become even more sophisticated, posing greater risks for organizations and employees handling sensitive financial transactions. As online shopping continues to grow, attackers are likely to refine their methods, making malicious scripts harder to detect and removing visible traces of intrusion. This could lead to prolonged breaches where payment data is stolen for months before organizations realize they’ve been compromised, resulting in widespread financial losses and reputational damage.
Attackers may also expand their targets beyond traditional eCommerce platforms, infiltrating third-party services and payment gateways to maximize their reach. With cybercriminals constantly refining their tactics, MageCart is likely to remain a persistent and evolving threat in the digital landscape.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS:
Key Intelligence Signals:
Analyzing DEEP#DRIVE: North Korean Cyber Actors Exploiting Trusted Platforms for Targeted Attacks
Summary:
Recently, an ongoing cyberattack campaign attributed to Kimsuky, a North Korean Advanced Persistent Threat (APT) group, has been identified, targeting South Korean businesses, government entities, and cryptocurrency users. This attack, known as DEEP#DRIVE, involves sophisticated, multi-stage tactics, with phishing lures in the Korean language being sent via trusted platforms like Dropbox. Malicious payloads are disguised as work logs, insurance documents, and crypto-related files, using formats such as .hwp, .xlsx, and .pptx. These methods allow the attackers to evade security defenses by appearing as routine user behavior.
The primary attack method is phishing, where malicious files are disguised as legitimate documents. Once executed, PowerShell scripts are used to download and run additional payloads. Dropbox is utilized for both payload distribution and data exfiltration, making detection and analysis more challenging. To maintain persistence on compromised systems, the attackers create scheduled tasks that ensure the malicious scripts run periodically. The attackers also employ code obfuscation techniques to make the malware difficult to detect and analyze.
In the first stage of the attack, the victim downloads a .zip file containing a .lnk file, which, when opened, executes a PowerShell script. This script then downloads a second-stage PowerShell script from Dropbox, continuing the infection process.
These scripts are designed to gather system information, establish persistence, and download further malicious payloads. Scheduled tasks are also used to ensure that the malicious scripts run regularly, keeping the attackers’ access to the compromised systems even after reboots.
The final payload is a .NET assembly, which is decompressed and executed in memory. This assembly likely serves as a backdoor, giving the attackers remote access to the compromised machines. The infrastructure used by the attackers is dynamic and short-lived, with Dropbox links quickly being taken down after use, suggesting the attackers are actively monitoring their campaigns to maintain operational security.
The attackers primarily target South Korean entities, tailoring phishing lures to industries such as logistics, government, and cryptocurrency. The documents used in the attack often appear legitimate, bearing names related to insurance, work logs, and cryptocurrency wallets.
Relevancy & Insights:
The threat actor behind the DEEP#DRIVE cyberattack, Kimsuky, has a well- documented history of sophisticated cyber-espionage campaigns, often targeting entities in South Korea and other regions. Historically, Kimsuky has focused on governmental, military, and research organizations, primarily aiming to steal sensitive political, defense, and strategic data. The group’s tactics have evolved over time, shifting from simple spear-phishing attacks to more complex, multi-stage intrusions involving custom malware and remote access tools. Notably, Kimsuky has also been involved in numerous cyberattacks targeting cryptocurrency exchanges and financial institutions, which aligns with its current focus on crypto- related industries in the DEEP#DRIVE campaign.
In past operations, Kimsuky has frequently relied on phishing emails with malicious attachments or links, a tactic that remains central to its recent campaigns. This mirrors earlier attacks in which the group distributed trojans like “RATs” or “DTrack” through seemingly legitimate documents, often leveraging trusted platforms like Dropbox or other cloud storage services for payload distribution and data exfiltration. This technique was notably present in its previous targeting of the South Korean government and private sector, as well as its operations involving cryptocurrency exchanges. The current DEEP#DRIVE attack is a continuation of these tactics, with Kimsuky again leveraging social engineering techniques—this time specifically targeting the growing cryptocurrency sector and key South Korean industries such as logistics and government.
ETLM Assessment:
Kimsuky, a North Korean cyber espionage group, primarily targets political, military, and economic sectors to gather intelligence for national interests. Its operations are mainly focused on East Asia, particularly South Korea, with extended attacks on the U.S. and Japan. Kimsuky targets government agencies, defense contractors, research institutions, cryptocurrency platforms, and critical infrastructure, often exploiting vulnerabilities in both human behavior (via spear- phishing) and software systems. The group uses custom malware like DTrack, PowerShell scripts, and .NET backdoors to maintain long-term access and exfiltrate data undetected. Kimsuky’s tactics have evolved to include more sophisticated tools and the exploitation of zero-day vulnerabilities, allowing it to bypass traditional defenses. With an ongoing focus on cryptocurrency exchanges, the group continues to seek avenues for illicit funding. As geopolitical tensions rise, Kimsuky is likely to expand its attacks to emerging technologies. Organizations, particularly those involved in national security and critical infrastructure, should adopt proactive cybersecurity measures like phishing defenses, system audits, and patch management to counter this growing threat.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
MITRE Framework
| Tactic | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Command and Control | T1071.001 | Application Layer Protocol: Web
Protocols |
| Command and Control | T1132 | Data Encoding |
| Defense Evasion | T1027.010 | Obfuscated Files or Information: Command Obfuscation |
| Defense Evasion | T1036.007 | Masquerading: Double File Extension |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or
Information |
| Defense Evasion | T1620 | Reflective Code Loading |
| Execution | T1059.001 | Command and Scripting Interpreter:
PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter:
Windows Command Shell |
| Execution | T1204.002 | User Execution: Malicious File |
| Command and control | T1102 | Web Service |
| Exfiltration | T1567.002 | Exfiltration Over Web Service:
Exfiltration to Cloud Storage |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Cybercrime and nation-state operations increasingly entwined
Google has released a report highlighting the national security risks posed by cybercrime, emphasizing that state-sponsored hacking cannot be viewed separately from financially motivated attacks. The report points out that state- backed groups from Russia, China, and Iran are increasingly utilizing commodity malware and other tools purchased from criminal forums. Russia, in particular, is known for employing criminal hackers to support government operations, while North Korean state-sponsored hackers often prioritize financial gains.
The researchers urge governments to treat cybercrime as a critical national security threat, calling for increased resource allocation. This includes prioritizing intelligence collection and analysis of cybercriminal organizations, strengthening law enforcement’s ability to investigate and prosecute cybercrime, and fostering international collaboration to dismantle these transnational networks.
Meanwhile, another set of researchers report that a toolset tied to Chinese espionage actors was recently used in an RA World ransomware attack against an Asian software company. In previous intrusions involving this toolset, the attacker appeared focused on traditional espionage, aiming primarily to maintain persistent access to targeted organizations through the installation of backdoors. While Chinese state-sponsored actors often share toolsets with each other, these tools aren’t usually associated with cybercrime. While in the more likely scenario, this represents a single actor, possibly an individual, who was attempting to earn extra money using their employer’s toolkit, we cannot rule out China co-opting cybercriminals for its state-run industrial espionage program, much like Russia does co-opt its own cyber criminals.
ETLM Assessment:
In the 21st century, data flows represent as much a vital lifeline to modern economies as naval shipping does and while privateering disappeared from the oceans, we increasingly see a similar concept being applied to cyber security in recent years. But these information flows on which our digitized economies are ever more dependent are being raided by criminal groups, which have received “license to hack” from their governments. Indeed, the governments of countries like Pakistan, North Korea, Iran, Russia, and China are putting these digital privateers to work on their behalf in times of increased tension in international relations. In times like these, we can expect increased institutionalization of digital privateers and their use for de facto undeclared warfare against enemies of the host government.
Russians are targeting Microsoft 365 accounts.
Recent reports warn that multiple Russian threat actors are conducting spear phishing attacks aimed at compromising Microsoft 365 accounts. These attackers are impersonating officials from the US State Department, the Ukrainian Ministry of Defence, the European Union Parliament, and leading research institutions. Volexity attributes these campaigns to at least three Russian groups, including Cozy Bear and Storm-2372.
The attacks utilize a lesser-known method called “device code phishing,” where victims are deceived into granting access through the Microsoft Device Code OAuth workflow.
Separately, researchers have identified a hacking campaign known as “BadPilot,” orchestrated by a subgroup of Sandworm, a threat actor linked to Russia’s GRU military intelligence. BadPilot is a multi-year campaign focused on exploiting vulnerable internet-facing infrastructure for initial access. While initially targeting Eastern Europe and Asia, the group has expanded its operations to the US, UK, Canada, and Australia.
Active since at least 2021, the group has used opportunistic access techniques and stealthy persistence methods to collect credentials, execute commands, and facilitate lateral movement, leading to significant regional network compromises.
Post-compromise operations have enabled Sandworm to access sensitive global targets across sectors such as energy, oil and gas, telecommunications, shipping, arms manufacturing, and international governments.
ETLM Assessment:
Both campaigns seem to be classic state-driven espionage with many similar campaigns like it probably underway at the same time. The effort, which is clearly a classic case of state-driven espionage, is likely part of a broader Russian strategy to gather intelligence on geopolitical developments and maintain influence in Europe in the face of sanctions, following its war on Ukraine.
The Qilin Ransomware Impacts HIKARI SEIKO CO. LTD
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; HARADA INDUSTRY CO., LTD.(https[:]//www[.]harada[.]com/en/), was compromised by Qilin Ransomware. HARADA INDUSTRY CO., LTD. is a Japan-based company mainly engaged in the manufacturing and sale of automotive equipment and communications equipment. Harada Industry Co Ltd manufactures and sells automotive antennas, wireless and data communications antennas, mobile device antennas, actuators, and various automotive parts, electronic devices, and components. The compromised data includes emails, contracts, 2D and 3D drawings, customer information, financial data, and supply chain details. It also involves product development documents, employee personal information, and data on employees who moved from Japan to the USA. Additionally, sensitive records such as passports, visa applications, family member information, and infant documents were exposed. The breach affected reports, audits, assembly notes, technical specifications, product roadmaps, SWOT analyses, new facility data, and documents labelled as “confidential.” Furthermore, confidential information related to leading automobile companies, including Honda, Mazda, Ford, BYD, Fujikura, Harley Davidson, Ferrari, Isuzu, Harman, Nippon, Tesla, Toyota, and other associated companies, was compromised. The total size of the compromised data is approximately 942.00 GB.
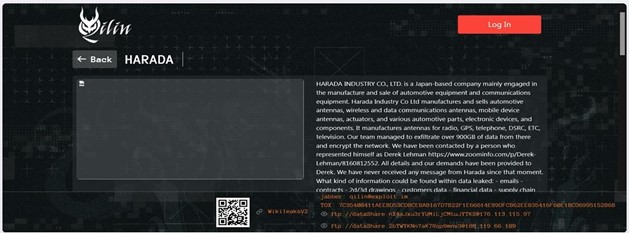
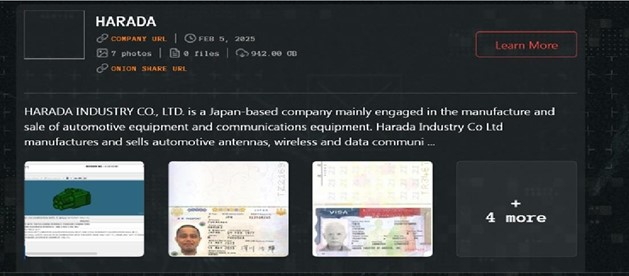
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion make it a particularly dangerous actor.
The Fog Ransomware Impacts iRidge Inc.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; iRidge Inc (https[:]//iridge[.]jp/) was compromised by Fog Ransomware. iRidge Inc. is a Japanese company that provides app development and OMO (Online Merges with Offline) solutions, aimed at seamlessly blending digital and physical experiences. It specializes in leveraging smartphones for location-based information sharing and distribution through its flagship platform. The compromised data includes confidential and sensitive information belonging to the organization. The scale of the data exposure measures approximately 7 GB.
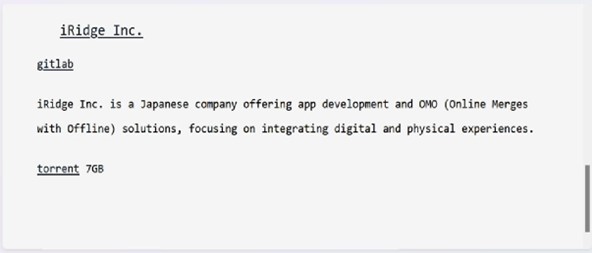
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Fog Ransomware, despite utilizing advanced techniques, presents a substantial threat due to its double extortion methods and wide- ranging targets. To effectively reduce the risk of Fog Ransomware attacks, organizations should prioritize strong security measures, including regular data backups, security awareness training, vulnerability management, and comprehensive incident response planning.
Vulnerability in FortiOS CAPWAP
Relevancy & Insights:
The vulnerability exists due to insufficient validation of quoting syntax in PostgreSQL libpq functions PQescapeLiteral(), PQescapeIdentifier(), PQescapeString(), and PQescapeStringConn() and within the command line utility programs when client_encoding is BIG5 and server_encoding is one of EUC_TW or MULE_INTERNAL. This vulnerability is being actively exploited in the wild
Impact:
A remote attacker can pass specially crafted input to the application and execute arbitrary SQL queries in the database.
Affected Products:
https://www[.]postgresql[.]org/support/security/CVE-2025-1094/
Recommendations:
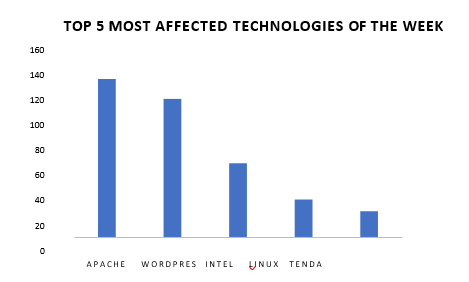
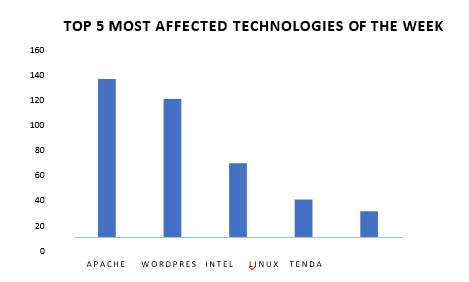
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in PostgreSQL can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of PostgreSQL is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding database management operations, including data storage, processing, and SQL compliance, across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
Killsec Ransomware attacked and published Nano Health data
Summary:
Recently, we observed that Killsec Ransomware attacked and published the data of Nano Health(https[:]//www[.]nanohealth[.]in/) on its dark web website. Nano Health, an organization based in India, focuses on managing chronic diseases such as diabetes, asthma, and hypertension within urban slums and low-income communities. It offers the most comprehensive and integrated digital health solution, aiming to improve healthcare access and outcomes for underserved populations. The data leak resulting from the ransomware attack includes patient electronic health records (EHR), IDs, bills, internal documents, and various other sensitive information. The total size of the compromised data is estimated to be around 0.5 TB.
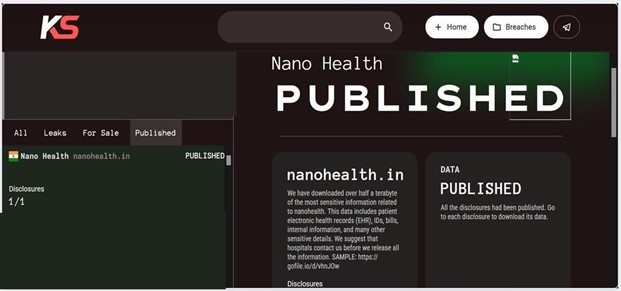
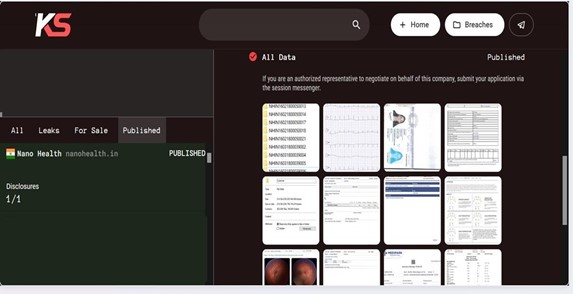
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Bank Syariah Indonesia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Bank Syariah Indonesia (https[:]//www[.]bankbsi[.]co[.]id/) in an underground forum. Bank Syariah Indonesia (BSI) is a state-owned Islamic bank in Indonesia. The compromised data includes image files containing employee profiles, deposit records, invoices, payments, product details, salaries, and other sensitive information. The breach has been attributed to a threat actor known as “CrackedGotSeized.”
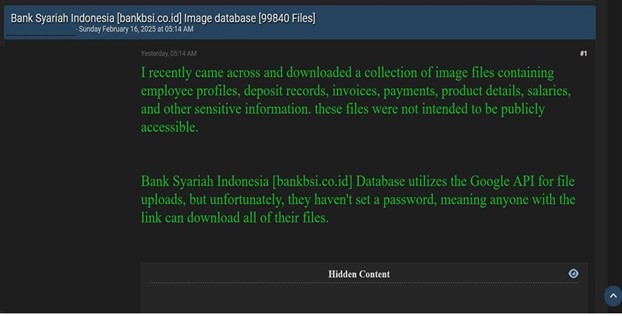
Source: Underground forums
Summary:
The CYFIRMA Research team observed a data sale related to a Thai telecommunication company in an underground forum. The company ranks among the top 10 telecom providers in Thailand, generating a revenue of 1 billion USD. It offers various services, including Internet/Fiber, landline, and mobile communications.
The compromised data includes:
Additionally, the database contains information on dealers, sales records, internal logs, employees, internal departments, SIM cards, and more. The asking price for the compromised data is $2,000. The breach has been attributed to a threat actor known as “Sorb.”
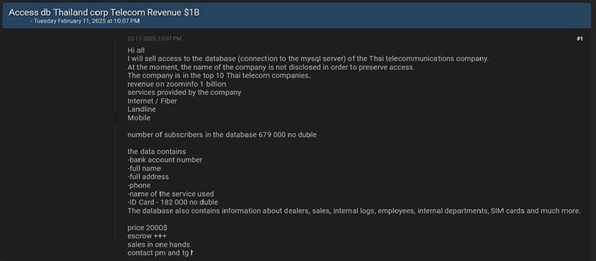
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Sorb is a threat actor engaged in selling stolen databases on cybercrime forums. This individual specializes in marketing databases that may have been acquired from various companies. The data breach poses a serious threat to the Thai telecommunications company and its stakeholders. Immediate and decisive actions are necessary to limit the damage and prevent additional losses. A comprehensive investigation, strong remediation measures, and a long-term commitment to cybersecurity best practices are vital for recovery and ensuring future protection.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a data leak related to JSEA (Jurukur Saharuddin El-Asas)(https[:]//www[.]jsea[.]com[.]my/) in an underground forum. JSEA (Jurukur Saharuddin El-Asas) is a licensed land and engineering surveying firm in Malaysia. It specializes in cadastral, strata, engineering, hydrographic, and topographic surveying services. The company operates with a focus on professionalism and integrity, serving both government and private sectors. The compromised data includes confidential and sensitive information embedded in PHP code format. The breach has been linked to a threat actor known as “BanyuwangiXploit.”
Source: Underground forums
The CYFIRMA Research team observed a data leak related to SICANTIK (Sistem Informasi Pencatatan Kehadiran dan Kinerja) (https[:]//sicantik[.]bogorkab[.]go[.]id/) in an underground forum. SICANTIK (Sistem Informasi Pencatatan Kehadiran dan Kinerja) is an attendance and performance recording system designed for government employees in Bogor Regency, Indonesia. The compromised data includes the application ID (id app), employee ID (id pegawai), and employee identification number (nip), which is specific to Indonesian civil servants. It also contains authentication tokens (token), device unique identifiers (device uuid), and the date of joining (join date). Additionally, the breach exposed device information (info device), platform details (platform) such as Android, iOS, or Web, and records of the last login (last login). Alongside these, other confidential information was also compromised. The compromised data has a total size of approximately 3.5 GB and is stored in CSV and PDF formats. The breach has been attributed to a threat actor identified as “ClaratZ.”
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
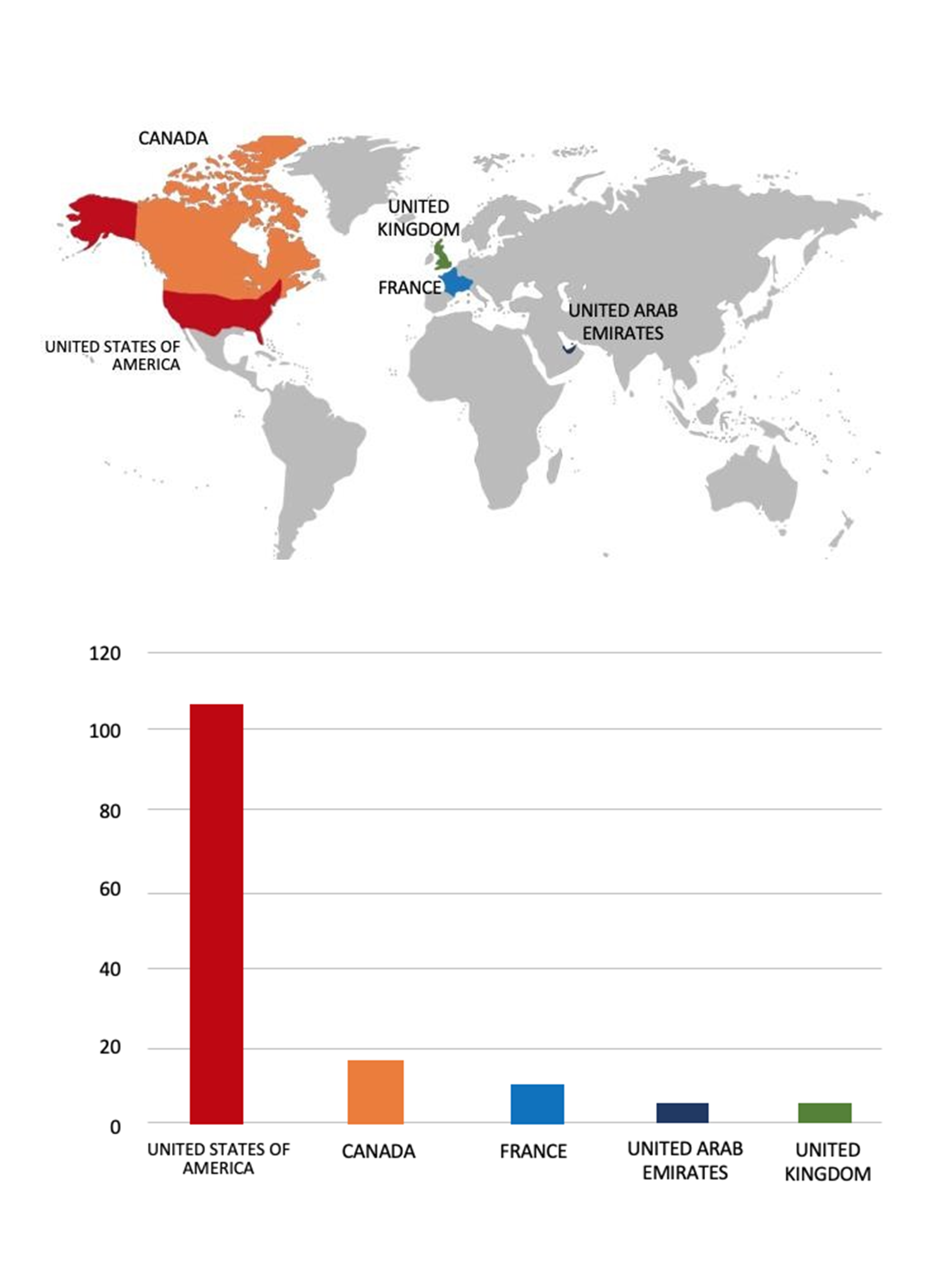
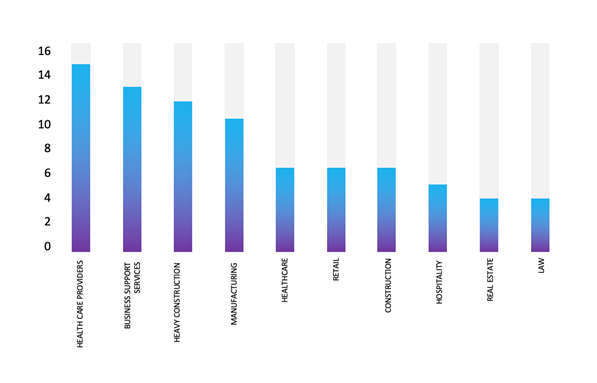
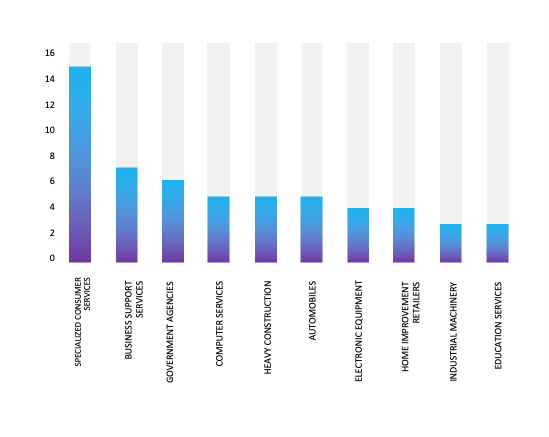
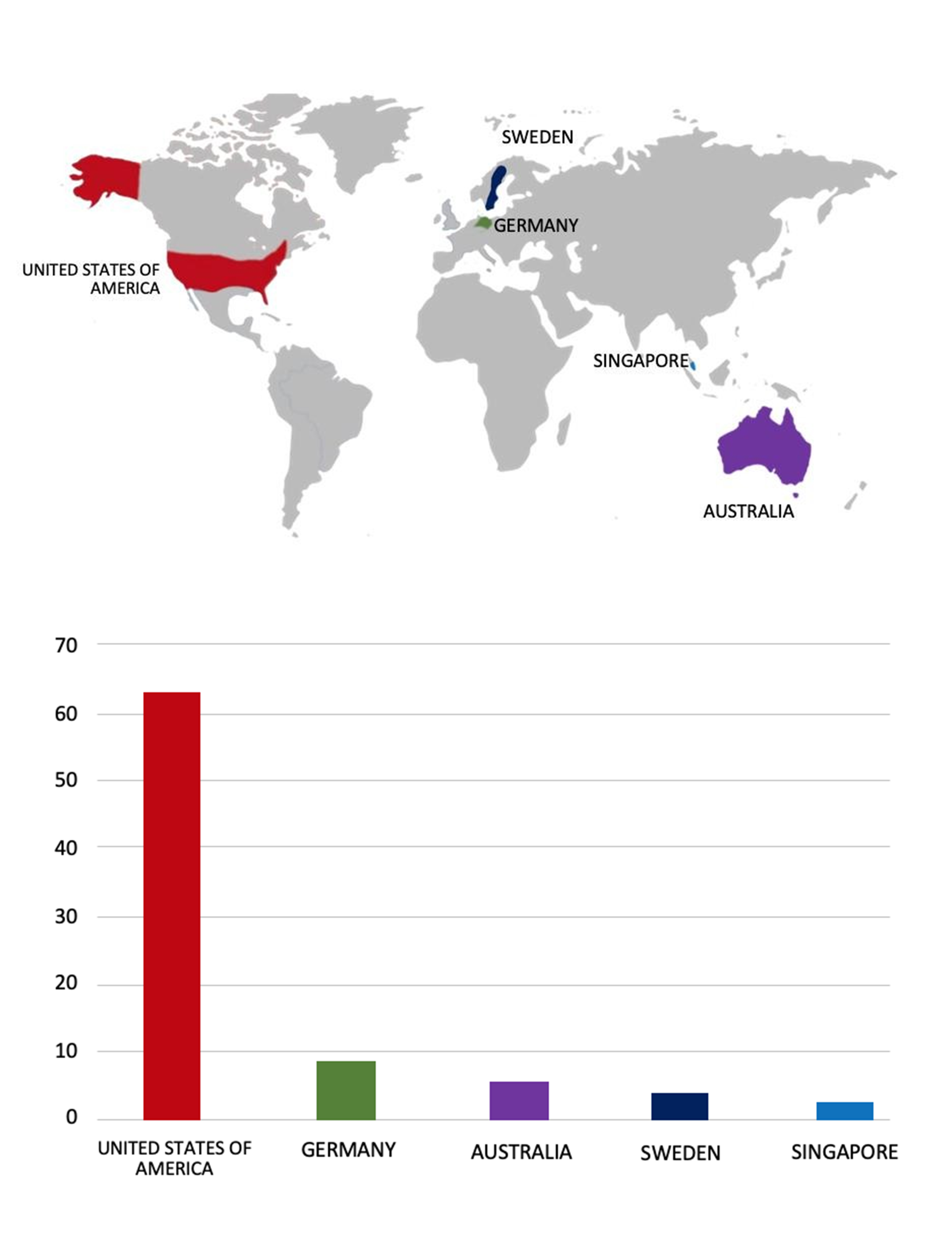
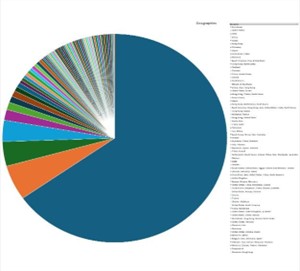
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph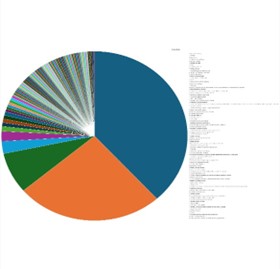
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.