



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Help_restoremydata Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Help_restoremydata Ransomware
Researchers have recently identified a new ransomware named Help_restoremydata.
The ransomware encrypts files on a victim’s system and demands payment for their decryption.
This ransomware appends the extension “.help_restoremydata” to the names of encrypted files, making them inaccessible. After completing the encryption process, it changes the desktop wallpaper and leaves a ransom note in an HTML file titled “HOW_TO_RECOVERY_FILES.html.”

Screenshot of files encrypted by this ransomware (Source: SurfaceWeb)
Help_restoremydata’s desktop wallpaper directs victims to read its accompanying ransom note, contained in the HTML file. The message informs victims that their organization has been targeted, and files have been encrypted using robust RSA-4096 and AES-256 cryptographic algorithms.
In addition to encryption, the attackers claim to have exfiltrated sensitive information, including financial records, administrative data, databases, contracts, HR records, login credentials, and other critical details. If the ransom demands are not met, the perpetrators threaten to sell the stolen data to competitors, leak it on the dark web, and notify the media of the breach.
As an assurance, the attackers offer victims the ability to test the decryption of a single file (subject to specific conditions) free of charge before paying the ransom. However, the ransom note strongly warns against tampering with encrypted files or using third-party decryption tools, as such actions could result in permanent data loss.

Appearance of Text presented in Help_restoremydata ransomware’s ransom note “HOW_TO_RECOVERY_FILES.html” (Source: Surface Web)

Screenshot of Help_restoremydata’s desktop wallpaper: (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.008 | Boot or Logon Autostart Execution: LSASS Driver |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Privilege Escalation |
T1055 | Process Injection |
| Privilege Escalation |
T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation |
T1547.008 | Boot or Logon Autostart Execution: LSASS Driver |
| Privilege Escalation |
T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Privilege Escalation |
T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Credential Access |
T1003 | OS Credential Dumping |
| Credential Access |
T1539 | Steal Web Session Cookie |
| Credential Access |
T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Command and Control |
T1071 | Application Layer Protocol |
| Command and | T1090 | Proxy: Multi-hop Proxy |
| Control | ||
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data indicates that this ransomware specifically targets enterprises, as evident from its ransom note detailing the theft of sensitive organizational data such as financial records and credentials. Future attacks are likely to grow more sophisticated, employing advanced evasion techniques, stronger encryption, and exploiting additional Windows vulnerabilities to maximize damage, disrupt operations, and compel victims to pay ransom quickly. To mitigate such threats, robust cybersecurity measures, including advanced endpoint protection, regular backups, network monitoring, and employee awareness training, are essential.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’
CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Spyware
Objective: Espionage, Data theft
Threat Actor: Gamaredon (aka Primitive Bear, Shuckworm) Target Technology: Android OS
Target Geographies: Former Soviet states (Uzbekistan, Kazakhstan, Tajikistan, and Kyrgyzstan).
Active Malware of the Week
This week “BoneSpy and PlainGnome” is trending.
Summary
Researchers have uncovered two Android surveillance malware families, BoneSpy and PlainGnome, linked to the Russian Gamaredon APT group. BoneSpy, active since 2021, and PlainGnome, emerging in January 2024, primarily target Russian-speaking individuals in former Soviet states, including Uzbekistan, Kazakhstan, Tajikistan, and Kyrgyzstan. BoneSpy operates as a standalone application, while PlainGnome functions as a dropper, embedding its payload within the app. Both remain active and continue to support Gamaredon’s espionage activities. Despite their differences, both exhibit extensive surveillance capabilities. Both malware families rely on targeted social engineering for distribution, as none of their apps have been found on Google Play, highlighting their reliance on tricking users into manual installation.
BoneSpy
BoneSpy is a sophisticated surveillance malware based on the open-source DroidWatcher app from 2013. Delivered through trojanized Telegram apps or by impersonating Samsung Knox, its early 2022 variants experimented with various lures, including battery monitoring and photo gallery apps, before shifting to fully functional Telegram “Beta” versions.

Fig: The KnoxSystemManager BoneSpy sample (left) presents an extremely basic activity with “Install” and “Exit” options; the real Samsung Knox Manage (right) presents full EMM functionality.
Early variants demonstrated significant feature experimentation, incorporating key functions such as call log collection, file system access, contact retrieval, SMS interception, and email extraction. Some versions also introduced audio recording capabilities. A couple of samples employed RTMP (Real-Time Messaging Protocol), an open-source streaming protocol, for command and control, while others tested for root access by attempting to write the string “ZZZ” to restricted file paths requiring elevated permissions.
Features of BoneSpy
BoneSpy’s surveillance features had become more consistent, with a near-exclusive reliance on trojanized Telegram samples. The observed BoneSpy variants demonstrate the following capabilities:
A key feature of BoneSpy is its ability to be remotely controlled via SMS messages, allowing it to receive a wide range of commands. By contrast, PlainGnome was developed independently and shares no significant code overlap with BoneSpy, although it offers similar surveillance capabilities.
PlainGnome
PlainGnome employs a two-stage deployment process, beginning with a lightweight first stage that drops a malicious APK as its second stage. The first stage, requiring the REQUEST_INSTALL_PACKAGES permission, contains basic emulator checks and minimal code. Victims initiate the second-stage installation by clicking the splash screen button labeled “каталог” (catalog). This lure persisted throughout PlainGnome’s 2024 deployment, maintaining its deceptive simplicity to target users effectively.

Fig: First stage app’s splash screen with the “каталог” button.
PlainGnome’s second-stage payload evolved throughout 2024, adopting Jetpack WorkManager classes for data exfiltration, enabling conditional execution, such as operating only when the device is idle to avoid detection. Unlike the minimalist first stage, the second stage manages all surveillance functions, requesting 38 permissions and supporting 19 commands, including collecting:
Upon activation, the payload prompts the user to grant specific permissions until it secures access to essential ones, including READ_SMS, READ_CALL_LOG, READ_CONTACTS, and CAMERA. Interestingly, PlainGnome offers two ambient audio recording modes: one ceases recording when the device screen is active, while the other continues regardless of screen activity. This approach is likely intended to evade detection, as newer Android versions display a microphone icon in the status bar when the microphone is in use, potentially alerting the victim to the malware’s presence.
Linking BoneSpy and PlainGnome to Gamaredon’s Expanding Espionage
Researchers have firmly linked the BoneSpy and PlainGnome malware families to the Russian Gamaredon APT group by identifying shared IP addresses and command-and-control (C2) infrastructure with Gamaredon’s desktop campaigns. Both malware families leverage dynamic DNS services, notably ddns[.]net, a tactic Gamaredon has consistently used since 2017. The C2 domains follow Gamaredon’s established naming patterns, such as wildcard DNS records and rapidly rotating IP infrastructure, with many tied to Russian ISP Global Internet Solutions LLC based in Sevastopol, Crimea.
Adding to the attribution, the infrastructure is connected to Yevgeniy Valentinovich Marinko, a Russian national who owns both Global Internet Solutions LLC and UK-based hosting provider Global Connectivity Solutions LLP. Marinko’s known history in hacker forums and stolen-credential trading since 2018 underscores the group’s operational depth. While most infrastructure is rooted in Russian- controlled providers, an unusual exception includes a C2 domain hosted on Google Cloud. These findings provide compelling evidence of Gamaredon’s expanding focus on mobile surveillance through BoneSpy and PlainGnome.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the BoneSpy and PlainGnome campaigns highlight the increasing use of advanced mobile surveillance tools, posing significant threats to organizations and employees. These tools are likely to target a broader range of individuals, leveraging mobile devices as gateways to sensitive data, which could lead to risks such as unauthorized system access, exposure of confidential conversations, and operational disruptions. As social engineering tactics continue to evolve, attackers may deploy more sophisticated malicious apps disguised as legitimate tools, creating vulnerabilities for larger cyberattacks, including corporate espionage and data breaches. The integration of malware into trusted apps may undermine confidence in popular platforms, urging businesses to prioritize mobile security in their defense strategies. As per the telemetry data, the campaign targeting former Soviet states like Uzbekistan, Kyrgyzstan, and Tajikistan, with the potential for future attacks towards Ukraine, given Gamaredon’s historical focus. The use of Telegram lures and Russian-language filenames in early BoneSpy samples suggests that Eastern Europe, where Telegram is popular, will remain a key target, with trojanized Telegram samples continuing to drive these campaigns forward.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Potential China-based Hackers Target Prominent Organizations in Southeast Asia
Summary:
Threat actors, potentially linked to China-based APT groups, have targeted multiple high-profile organizations in Southeast Asia, including government ministries, an air traffic control organization, a telecoms company, and a media outlet. These attacks, which began in October 2023, appear to be primarily focused on intelligence gathering. The attackers employed a mix of open-source and living-off-the-land tools to infiltrate networks, leveraging legitimate applications for DLL sideloading and proxy tools, including Rakshasa, which is linked to the Earth Baku (APT41) group. While precise attribution remains difficult, various tools used in the campaign have been historically associated with multiple China-based advanced persistent threat (APT) groups.
The typical attack chain starts with the execution of remote access tools, using Impacket to perform command execution via Windows Management Instrumentation (WMI). The attackers install keyloggers, password collectors, and reverse proxy tools (such as Rakshasa, Stowaway, and ReverseSSH) to maintain persistence and establish command-and-control channels. They also deploy customized Dynamic Link Libraries (DLLs) to intercept authentication mechanisms, enabling the extraction of sensitive user credentials. The attackers often exploit living-off-the-land techniques, using tools like PowerShell, reg.exe, and WMI to traverse networks, discover assets, and execute commands remotely. In some instances, tools like Dismap and Infostealer were used to identify systems of interest and harvest information.
Exfiltration activities, which were stealthily conducted over an extended period, involved compressing files into password-protected archives using WinRAR and uploading them to legitimate file-sharing platforms such as file.io. The attackers’ prolonged dwell time within targeted environments suggests a highly sophisticated and persistent operation. While various APT groups share tools and techniques, the use of proxies like Rakshasa and SharpGPOAbuse, coupled with the use of Chinese- language tools, strongly suggests the involvement of Chinese state-backed actors, possibly APT31, APT41, or similar entities. However, the variety of tools and shared tactics make precise attribution challenging.
Relevancy & Insights:
The threat actor in the current incident shares clear ties to previous attacks attributed to China-based APT groups, particularly APT41 (Earth Baku) and APT31. Historically, APT41 has been involved in campaigns focused on espionage and intellectual property theft, using a variety of tools for reconnaissance and data exfiltration. In previous attacks, APT41 has leveraged tactics such as DLL sideloading and proxy tools like Rakshasa, both of which are seen in the ongoing Southeast Asia campaign. The use of Impacket for lateral movement and WMI for command execution, as well as data exfiltration via services like File.io, mirrors tactics previously employed by APT41 in past intrusions.
Similarly, APT31, known for its use of remote access tools like PlugX and for exfiltrating sensitive data, has also relied on cloud storage for data theft, a strategy observed in the current incident. The focus on prolonged access, credential harvesting, and stealthy exfiltration techniques showcases the persistence and sophistication of these groups, with current operations aligning with their well-documented history of covert intelligence gathering and infiltration.
ETLM Assessment:
China-based APT groups, such as APT41 and APT31, have targeted Southeast Asia, including government ministries, telecoms, air traffic control, and media organizations. These attacks focus on intelligence gathering, exploiting Windows-based systems with tools like PowerShell, WMI, and DLL sideloading to gain access and move laterally within networks. Vulnerabilities targeted include misconfigurations like LocalAccountTokenFilterPolicy. Malware used includes Rakshasa (proxy tool), PlugX (RAT), Stowaway, and infostealers for data exfiltration. Previously used tools include TightVNC, WinRAR, and Impacket. These actors employ living-off-the-land techniques to evade detection, maintaining prolonged access for months, often exfiltrating data via cloud services like File.io. Looking forward, these attacks are likely to increase, targeting critical infrastructure sectors and employing more sophisticated evasion tactics. Organizations will need advanced defenses, such as endpoint detection, patch management, and monitoring to prevent lateral movement and credential theft, especially as geopolitical tensions rise in the region.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
Future Assessment:
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation |
T1055 | Process Injection |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1056 | Input Capture |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Command and Control | T1071 | Application Layer Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
The US government moves to ban China Telecom from US networks
The US Commerce Department has issued a notice to the US subsidiary of China Telecom outlining a preliminary finding that the company’s presence in American networks poses a national security risk to the United States. The move is viewed as the Biden Administration’s response to China’s alleged hacking of multiple US telecommunications networks. The US government has already reduced China Telecom’s presence in American networks over the past few years, but the company still maintains nodes that would be stripped under the Commerce Department’s order. The final decision on whether to ban China Telecom Americas will likely fall to the incoming Trump Administration
ETLM Assessment:
Recent reports indicate that Chinese state-sponsored hackers have infiltrated at least eight US telecommunications companies. These hacks are part of a broader state espionage campaign by the Chinese government and potentially also an indicator of positioning of Chinese hackers in US networks to disrupt critical infrastructure in case of a crisis, likely over Taiwan or in the South China Sea.
Iran-linked threat actor deploys new ICS malware
Researchers have discovered a new strain of IoT/OT malware “IOCONTROL” used by Iran-affiliated attackers to target devices in Israel and the US. According to the researchers, IOCONTROL has been used to attack IoT and SCADA/OT devices of various types, including IP cameras, routers, PLCs, HMIs, firewalls, and more. Some of the affected vendors include: Baicells, D-Link, Hikvision, Red Lion, Orpak, Phoenix Contact, Teltonika, Unitronics, and others.
A significant IOCONTROL attack compromised hundreds of fuel management systems in Israel and the United States. These systems included Israeli-made Orpak Systems and American-made Gasboy units. The malware, specifically designed for IoT devices, also disrupted operational technology (OT) like the fuel pumps used at gas stations.
This attack was attributed to “CyberAv3ngers,” a threat actor with suspected links to Iran’s Islamic Revolutionary Guard Corps Cyber Electronic Command.
ETLM Assessment:
The fall of the Assad regime in Syria is another nail in the coffin of Iran’s “forward defence”, forcing Tehran to rethink its security strategy. Its huge investments in Lebanon and now Syria have come to naught. The significance of the fall of the Assad regime for Iran can hardly be overstated – without Assad and with the Sunni regime in Damascus, Shiite Iran’s ability to restore Hezbollah’s power and its ability to threaten Israel from Lebanon has been dramatically weakened. To restore its strategic depth, Tehran is likely to rely more heavily on its ballistic missiles and cyber-attacks in the future and we should expect many more similar attacks.
The Killsec Ransomware Impacts JSSR Options Co., Ltd. (JSSR)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; JSSR Options Co., Ltd. (JSSR)(www[.]jssr[.]co[.]th), was compromised by Killsec Ransomware. JSSR Options Co., Ltd. operates primarily in the auction and logistics sectors, specializing in the sale of imported goods, including agricultural machinery, vehicles, and construction equipment. Key offerings include an extensive range of auction products through its JSSR auction platform, logistics services for transporting goods, and a variety of merchandise available in tax-free zones. The company also provides online bidding options, a buyer-seller regulation framework, and specialized services for both buyers and sellers. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
The INC Ransomware Impacts Haji Husein Alireza
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia; Haji Husein Alireza (www[.]hha[.]com[.]sa), was compromised by INC Ransomware. Haji Husein Alireza and Company Limited is a general trading company with diverse interests in foodstuffs, building materials, toilets, and jewellery. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Based on recent assessments by CYFIRMA, INC Ransomware represents a significant threat within the evolving landscape of ransomware attacks. Its use of strong encryption methods and double extortion tactics highlights the increasing sophistication of cybercriminal operations. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this and other ransomware variants. Continuous vigilance is essential to protect against the threats posed by emerging ransomware groups like INC Ransomware.
Vulnerability in Siemens Parasolid
Summary:
The vulnerability allows a remote attacker to compromise a vulnerable system.
Relevancy & Insights:
The vulnerability exists due to a boundary error when processing untrusted input.
Impact:
A remote attacker can create a specially crafted PAR file, trick the victim into opening it using the affected software, trigger an out-of-bounds write, and execute arbitrary code on the target system.
Affected Products: https[:]//cert-portal[.]siemens[.]com/productcert/html/ssa-979056.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
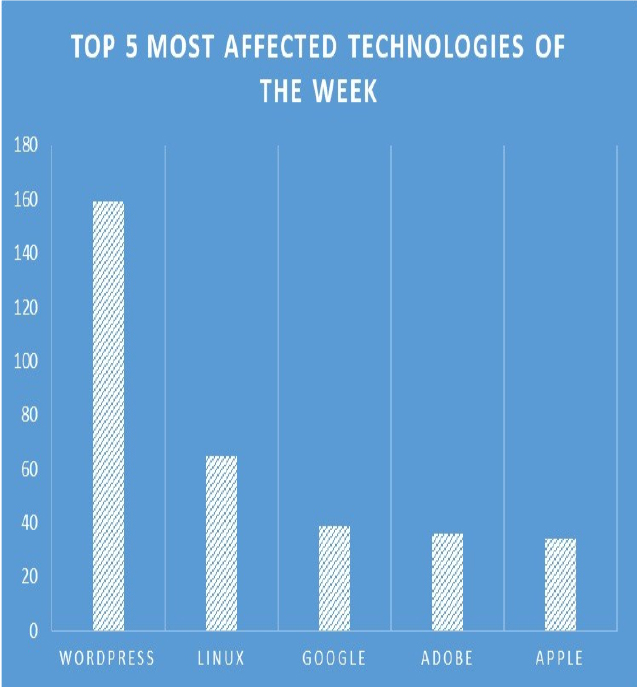
ETLM Assessment:
Vulnerability in Siemens Parasolid can pose significant threats to user privacy and security. This can impact various industries globally, including engineering, manufacturing, healthcare, and beyond. Ensuring the security of Siemens Parasolid is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding 3D geometry creation and editing processes, including the development of complex shapes and models in formats such as solids, facets, lattices, and surfaces, across different geographic regions and sectors.
Funksec Ransomware Attacked and Published the Data of the Mandiricoal
Summary:
Recently, we observed that Funksec Ransomware attacked and published the data of the Mandiricoal (https[:]//mandiricoal[.]co[.]id/) on its dark web website. Mandiricoal appears to refer to Mandiri Coal, a coal mining company operated by PT Mandiri Intiperkasa, a part of PT Prima Andalan Mandiri Tbk. Based in Indonesia, Mandiri Coal holds a concession in Nunukan, North Kalimantan, and specializes in producing coal with environmentally friendly features, such as low ash and sulfur content. Their services include coal mining, contractor services, and coal transportation. The company emphasizes sustainable practices, adhering to ISO certifications for quality, safety, and environmental management. The data leak resulting from the ransomware attack includes complete tables, payment records, signed documents, user information, timesheets, WFO data, and various other sensitive files.


Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Funksec ransomware poses a significant threat due to its aggressive tactics and politically motivated operations. Organizations are advised to implement robust cybersecurity measures to defend against such threats, including regular software updates, employee training on phishing awareness, and maintaining reliable backups. Continuous monitoring of emerging threats like Funksec is essential for effective incident response and risk mitigation strategies.
Indonesia’s Ministry of Transportation (Kementerian Perhubungan Republik Indonesia) Data Advertised on a Leak Site
Summary:
A data breach has allegedly impacted Indonesia’s Ministry of Transportation (www[.]dephub[.]go[.]id), exposing sensitive governmental documents. This incident raises significant concerns about the security of critical information and the privacy of governmental data.
The breach highlights vulnerabilities in protecting sensitive data within government systems and underscores the urgent need for enhanced cybersecurity measures. Authorities are urged to investigate the breach thoroughly and implement stronger protections to prevent future incidents. The Ministry of Transportation has not yet issued an official statement addressing the breach or its potential implications.
The leaked data includes Name, Student Identification Number (NIS), Employee Identification Number (NIP), Place & Date of Birth, Rank, and Work Unit. The data is available in PDF, PNG, and JPG formats, with a total size of 890.58 MB. The data breach has been linked to a threat actor known as “ClaratZ.”

Source: Underground Forums
Institute of CFO Vietnam Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to the Institute of CFO Vietnam in an underground forum. The Institute of CFO Vietnam is a professional organization dedicated to enhancing the skills and knowledge of Chief Financial Officers (CFOs) and finance professionals in Vietnam. The compromised database includes add-ons, applications, BBB meetings, blogs, blog categories, blog comments, categories, CI sessions, comments, contacts, coupons, courses, new courses, currency data, custom pages, enrollments, languages, lessons, logs, messages, newsletters, and other sensitive and confidential information. The breach has been linked to a threat actor identified as “LordVoldemort.”

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
“ClaratZ” is a notable threat actor within the cybersecurity landscape, engaging in defacement attacks and data breaches across various sectors. Organizations are encouraged to enhance their cybersecurity measures to defend against such threats by implementing robust security protocols and monitoring for unusual activity. Continuous vigilance is essential to mitigate risks associated with emerging cyber threats like ClaratZ.
Recommendations:
Enhance the cybersecurity posture by
The CYFIRMA Research team observed a data leak related to SHARK MARKET (www[.]sharkmarket[.]vn) in an underground forum. SHARK MARKET is a representative Korean startup in Vietnam. The company offers a wide range of products, including groceries, healthcare items, personal care products, electronics, and pet supplies. Their platform is accessible via their website and mobile applications, providing convenient home delivery services to customers. The compromised data includes Entity ID, Increment ID, Creation Date, Creation Time, Status, Customer Email, Payment Method, Ward, District, Region, Delivery Type, Completion Date, and Completion Time. The breach has been linked to a threat actor identified as “888.”

Source: Underground forums
A potential data breach at AlphaSense, a market intelligence platform, has been detected on a hacking forum. A ransom of 10 BTC has been demanded. According to the post, the threat actor known as “KryptonZambie” claims to possess the full database, full source code, and complete access to AlphaSense’s system. Multiple samples have been provided. The ransom demand to remove the data is 10 BTC.

Source: Underground forums
ETLM Assessment:
The threat actor group “888” has gained notoriety in underground forums, emerging as a significant force in cybercrime, primarily motivated by financial gains. This group has already targeted a wide range of industries, including government, industrial conglomerates, retail, staffing, business consulting, banking, e-commerce, and utilities. Their diverse targeting patterns suggest that they plan to broaden their scope and potentially expand their attacks to additional industries worldwide in the future.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.