



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found RADAR while monitoring various underground forums as part of our Threat Discovery Process.
RADAR
Researchers discovered the RADAR ransomware by late July 2024. This malicious software encrypts files and demands a ransom for their decryption.
Upon executing a sample of RADAR, the ransomware encrypted files and appended their filenames with a random character string. After completing the encryption process, RADAR changed the desktop wallpaper and generated a ransom note titled “README_FOR_DECRYPT.txt”. The message within the text file indicates that this ransomware also engages in data theft for double-extortion purposes.
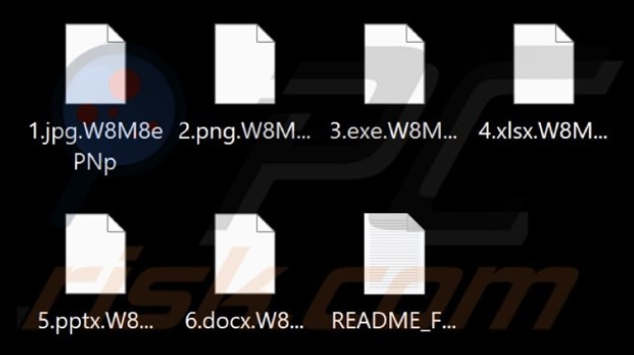
Screenshot of files encrypted by this ransomware (Source: SurfaceWeb)
RADAR’s ransom note informs victims that their files have been encrypted and their data stolen, with a threat to leak the information unless demands are met. The note details the cybercriminals’ previous attacks and corporate data leaks.
Victims can test the decryption process on 5-10 files before paying the ransom. They are cautioned against renaming, modifying, or deleting the encrypted files, as doing so will make them undecryptable.
The note warns that contacting authorities will result in the immediate publication of the exfiltrated data. Refusal to cooperate will have the same consequence. Additionally, the note advises against seeking help from third-party recovery companies, claiming this will lead to increased financial loss due to added fees.
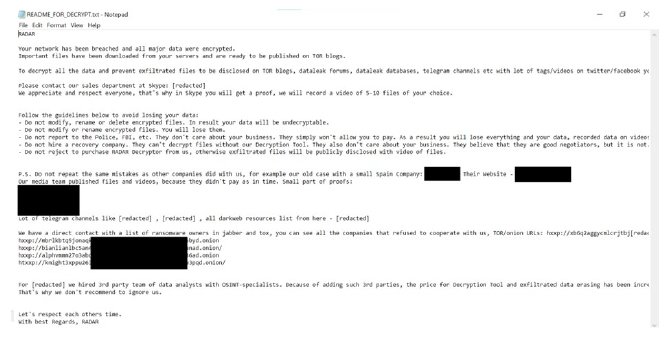
Appearance of RADAR ransomware’s text file “README_FOR_DECRYPT.txt” (Source: SurfaceWeb)
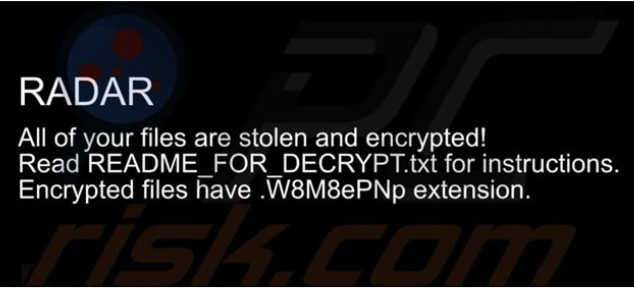
Screenshot of RADAR’s desktop wallpaper (Source: SurfaceWeb)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059.001: Command and Scripting Interpreter: PowerShell |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1202: Indirect Command Execution | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1074: Data Staged | ||
| T1114: Email Collection | ||
| T1560: Archive Collected Data | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| T1095: Non-Application Layer Protocol | ||
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1491.001: Defacement: Internal Defacement |
Relevancy and Insights:
ETLM Assessment:
Based on available data, CYFIRMA anticipates that RADAR ransomware will target industries such as banking, finance, transportation, and others to maximize ransom earnings. Their strategy of using double extortion and threatening to leak data across multiple platforms indicates an aggressive and expansive approach. Potential collaboration with other ransomware operators suggests RADAR ransomware may have already targeted regions such as the UK, US, Europe, Southeast Asia, and other economically developed nations. Additionally, references to previous corporate leaks and partnerships with other cybercriminals in their ransom notes suggest RADAR is part of a broader network, amplifying the overall threat. Vigilance and strong cybersecurity measures are essential to mitigate these threats effectively.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
SIGMA Rule:
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: SurfaceWeb)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing financial information, Data exfiltration Suspected Threat Actor: CyberCartel
Target Technologies: Windows OS, Browsers Target Geographies: Latin America
Target Industry: Financial Institutions
Active Malware of the Week
This week “Caiman” is trending.
Caiman
Researchers have recently observed a significant increase in malware campaigns involving malicious Chrome extensions, specifically targeting financial institutions in Latin America.
Two notable campaigns have been identified: one involves malicious Chrome extensions mimicking Google Drive, and the other features the Caiman malware, a banking trojan designed to steal sensitive financial information by employing deceptive Chrome extensions that capture screenshots, access clipboard data, inject malicious scripts, and redirect users to phishing sites. Caiman ensures its persistence through a flexible command and control system, often communicated via Telegram, and uses the Man in the Browser technique to illicitly gather banking data and other sensitive information. The threat is further exacerbated by the CyberCartel group, which capitalizes on established Malware- as-a-Service models rather than developing new malware, focusing on high-value targets such as government offices and financial institutions.
Attack Method
The malware employs a technique involving the installation of a malicious Chrome extension named “Chrome Notification,” which does not mimic legitimate extensions like Google Drive but rather uses a seemingly innocuous name. Once installed, this extension injects malicious scripts into web pages and redirects the victim to a phishing site that impersonates their targeted bank. This method effectively deceives users into providing sensitive financial information to the attackers. Caiman malware employs an AutoIT script to execute web injection attacks. The script monitors for user visits to the website bbvanet[.]com[.]mx/mexiconet and, upon detection, injects a JavaScript file from hxxps[:]//www[.]cssangular[.]com/jquery[.]js. This JavaScript script uses variables to encode the bank URL in base64 and denote the current date. The primary objective of this method is to harvest sensitive information, including account balances, usernames, passwords, and screenshots.
OTPBypass/Figrabber attack
Researchers have detected new activity in Colombia involving an ATS Engine injection panel designed to steal information. This technique primarily aims to bypass OTP (One- Time Password) protections, which are commonly exploited in phishing and other fraudulent activities. There are two main features of this web inject:
Communicate function
The communication function in the malware sends data to the attacker’s server by constructing a URL with various parameters and dynamically loading a script. The data sent to the Command and Control (C&C) server includes:
Deception of Victim
The attacker requests an OTP from the victim and deceives them into believing there are “technical difficulties.” During this time, the OTP is stolen and sent to the C&C server. The attacker also gathers additional information, including credit card numbers, CVV, ID, and telephone numbers.
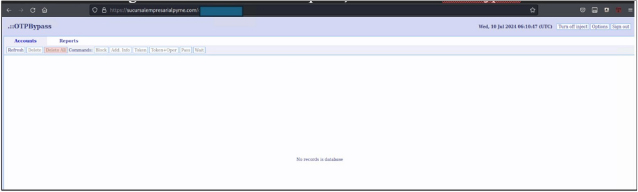
Fig: OTPBypass C&C Panel for Full Info Grabbing (Source: Surface Web)
Malicious Chrome extension Campaign
In the LATAM region, a campaign has been observed involving generic malware that utilizes a malicious Chrome extension, masquerading as Google Drive. The extension’s manifest.json file grants extensive permissions, allowing it to execute scripts, access system resources, manage other extensions, and interact with web content and user data. It injects malicious content scripts across websites, particularly targeting email platforms like Gmail, Hotmail, and Yahoo Mail, to modify email content related to banking withdrawals. Background scripts help manage tasks and maintain responsiveness. Network request rules manage traffic, and a config.js file dynamically updates the domain configuration via Telegram, making the extension adaptable. The extension injects malicious code to steal sensitive information, such as credit card details and login credentials, by fetching injection data and injecting external JavaScript when victims visit targeted URLs.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the rise in sophisticated malware campaigns like Caiman suggests that financial institutions and organizations, particularly in Latin America, will face increasingly complex cybersecurity threats. The continued use of web-injects by banking trojans poses a growing threat to financial institutions worldwide, with attacks already impacting over 40 banks across North America, South America, Europe, and Japan. This trend indicates a significant potential for similar attacks in Southeast Asia, where financial systems might also be targeted. As these techniques evolve, cybercriminals are likely to intensify their efforts to infiltrate and exploit banking systems, increasing the risk of severe data breaches and financial losses.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
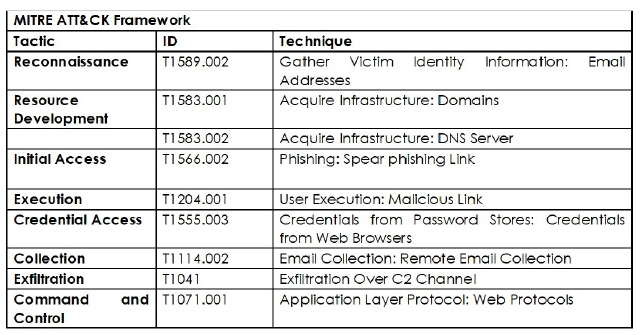
Smishing Triad Targets India Post Users: Unveiling the Latest Fraud Campaign
Summary:
Researchers have recently observed a fraud campaign targeting India Post users, attributed to a China-based threat actor known as the Smishing Triad. The current campaign focuses on India Post, which is part of the Ministry of Communications and operates one of the largest postal systems globally with over 150,000 post offices. The attackers initiate their scheme by sending smishing messages via iMessage to iPhone users, falsely claiming that a package is waiting at an India Post warehouse. These messages contain short URLs that lead to fraudulent websites designed to collect sensitive personal and financial information from the victims.
Between January and July 2024, researchers identified over 470 domain registrations mimicking India Post’s official domain. Most of these domains were registered via Chinese registrar Beijing Lanhai Jiye Technology Co., Ltd., and American registrar Namesilo, with a significant number hosted by Tencent, a Chinese hosting service provider. Domains like ‘indiapost[.]top’ are used to host cloned copies of the official India Post website, which gained a reputation over time to evade detection by antivirus engines. The fraudulent sites prompt users to provide personal information and payment details for a fake redelivery fee of INR 25.02.
The Smishing Triad’s primary motive is financial gains. By deceiving users into paying a small fee, they collect debit/credit card information and personal details such as names, addresses, email IDs, and phone numbers. This information can be leveraged in future scams, phishing attacks, spreading misinformation, or distributing malware.
The threat actors use newly registered Apple IDs or compromised accounts to send messages through iMessage, ensuring the messages appear legitimate within the recipient’s Messages app. This campaign highlights the need for heightened vigilance and robust security measures to detect and prevent such phishing attacks.
Relevancy & Insights:
The Smishing Triad, a China-based threat actor, has a history of launching smishing campaigns across various regions, including the U.S., the U.K., the EU, UAE, KSA, Pakistan, and India. In past attacks, they have targeted postal system users in India and the UAE, impersonating India Post and Emirates Post respectively, and have similarly attacked USPS in the U.S. Their current incident involves a large-scale smishing campaign against India, using deceptive iMessages that claim a package is waiting at an India Post warehouse, leading recipients to fraudulent websites. The Smishing Triad’s primary motive is financial gains and identity theft, aiming to steal personally identifiable information (PII) and payment data.
ETLM Assessment:
The Smishing Triad, a China-based threat actor, has a history of executing sophisticated smishing campaigns across the U.S., the United Kingdom, The European Union, UAE, KSA, Pakistan, and most recently, India. Their primary targets are postal services and their customers, especially iPhone users, and they have impersonated major Fortune 100 brands. Leveraging compromised Apple iMessage accounts and URL shortening services like QR codes, they exploit user trust in iMessage and postal services and target SQL injection vulnerabilities in their smishing kits. The group uses these kits to steal credit card information and has also distributed malicious code against the energy sector. The Smishing Triad’s expansive operations in India and UAE underscore a substantial threat to the global cybersecurity landscape. Future assessments suggest that their evolving tactics and adaptive strategies will continue to pose significant risks, necessitating vigilant cybersecurity practices, including regular software updates, user education on phishing threats, and robust, tailored defenses to counter advanced persistent threats.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
North Korea ramps up cyber campaigns
A newly designated North Korean threat actor known as APT45 has been observed by researchers conducting cyberespionage against the government and defense sectors since at least 2009. The group has gradually expanded into financially motivated operations, including ransomware attacks. As one of North Korea’s longest-running cyber operators, the group’s activity mirrors the regime’s geopolitical priorities even as operations have shifted from classic cyber espionage against government and defense entities to include healthcare and crop science. The threat actor has also targeted nuclear research facilities and power plants, including in India.
Meanwhile, the US State Department is offering a $10 million reward for information leading to the arrest of Rim Jong Hyok, a North Korean national accused of conducting ransomware attacks against critical infrastructure and healthcare organizations in the US. Hyok has been identified as part of a state-sponsored threat actor team that used malware to extract ransom payments from hospitals to fund malicious cyber operations targeting U.S. government entities and the U.S. or foreign defense contractors.
South Korea is investigating a leak that reportedly exposed the identities of its military intelligence agents, allegedly caused by a North Korean hack of a personal laptop belonging to South Korean intelligence personnel.
ETLM Assessment:
North Korean cyber operations have increased in sophistication over the past two years, and our researchers noted last year in a research report that Pyongyang’s threat actors seem particularly interested in stealing information related to maritime and missile technology research, given the emphasis the Kim regime puts onto developing a full nuclear triad. The interest in software is most likely related to Pyongyang’s interest in supply chain attacks. The heavily sanctioned regime in North Korea is hungry for the off-limits technologies it cannot obtain on the open market and thus uses cyber means to obtain them. Financially motivated activity occurring alongside intelligence collection has become a defining characteristic of North Korean cyber operations under which the cyber actors also fill the regime’s coffers.
Russian hackers disrupted heating services in Ukraine
Researchers have recently published their findings on “Cuckoo Spear,” a suspected Chinese cyberespionage operation targeting Japanese companies. The researchers attribute the operation to APT10, a threat actor tied to China’s Ministry of State Security. APT 10 has been active as early as 2006 and the group’s focus is to support the Chinese government by gathering intelligence against the relevant targets. APT10 often targets various critical infrastructure sectors, such as communications, manufacturing, and various public sectors, and has participated in the Chinese IP theft programme.
ETLM Assessment:
The threat actor has likely conducted cyber espionage focusing on intellectual property theft. The programme scoops data and projects what makes a particular organization competitive in its field in the Chinese state-sponsored IP theft programme, we reported on earlier. However, the APT has also targeted upstream providers and supported additional intrusions against high-profile assets. In this campaign, the cyber attack was likely a part of a state-driven espionage campaign.
The RansomEXX Ransomware impacts the LITEON Technology Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; (www[.]liteon[.]com), was compromised by the RansomEXX Ransomware. LITEON Technology Corporation, based in Taiwan, is a leading company in the electronics industry known for its diverse range of products. LITEON specializes in the development and manufacturing of optoelectronics, storage devices, and other electronic components. Its products include LED lighting solutions, semiconductors, automotive electronics, and smart healthcare devices. LITEON is recognized for its innovation and commitment to sustainability, providing high-quality technology solutions to global customers while emphasizing environmental responsibility. The breached data includes sensitive and confidential information from the organization. The total size of the leaked data is 142GB.
The following screenshot was observed published on the dark web:
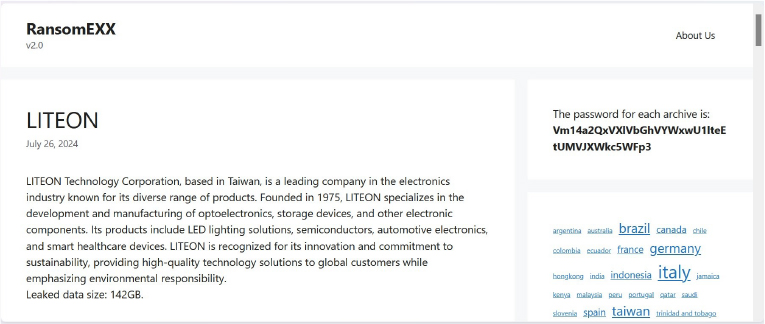
Source: Dark Web
Relevancy & Insights:
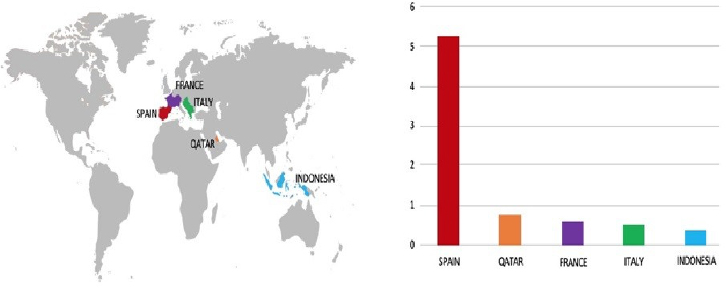
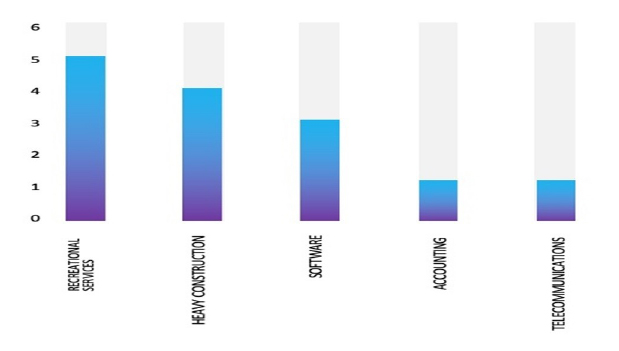
ETLM Assessment:
RansomEXX ransomware is known to target large enterprises and high-value targets. They have also been known to focus on those in the government, Informational Technology, and healthcare sectors, as well as high-value manufacturing entities. RansomEXX ransomware targets its victims through phishing and spear phishing emails. They are also known to leverage exposed and vulnerable applications and services, such as remote desktop protocol (RDP) and third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike). Based on CYFIRMA’s assessment, RansomEXX ransomware targets worldwide organizations. The attack on LITEON Technology Corporation also highlights ransomware groups’ interest in Asian organizations that are financially strong in the region with exploitable vulnerabilities.
The RansomHub Ransomware impacts Kumagai Gumi Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]kumagaigumi[.]co[.]jp), was compromised by the RansomHub Ransomware. Kumagai Gumi Co., Ltd. is a Japanese construction company known for its comprehensive building services, including infrastructure projects, such as tunnels, bridges, and dams, as well as commercial and residential buildings. The company emphasizes safety, quality, and sustainability in its operations, contributing to social development and environmental protection. They also focus on disaster preparedness and lifecycle management of their projects. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 5 TB.
The following screenshot was observed published on the dark web:
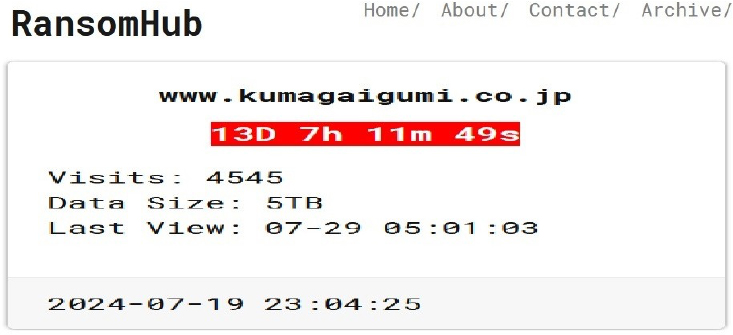
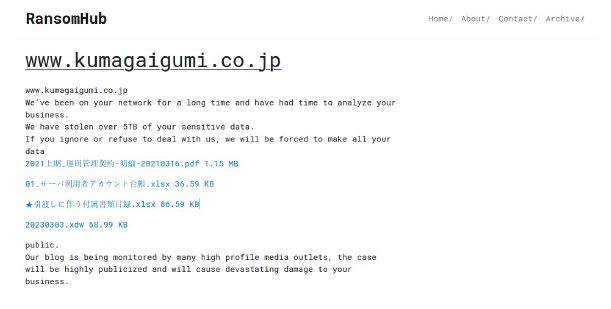
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Kumagai Gumi Co., Ltd, a leading Construction firm in Japan, highlighting RansomHub’s significant threat presence in the Asia Pacific.
Vulnerability in GStreamer ORC
Summary:
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Relevancy & Insights:
The vulnerability exists due to a boundary error when compiling orc files. A remote attacker can trick the victim into compiling a malicious source code file, trigger a stack- based buffer overflow and execute arbitrary code on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of a vulnerable system.
Affected Products:
https[:]//gstreamer[.]freedesktop[.]org/security/sa-2024-0003.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
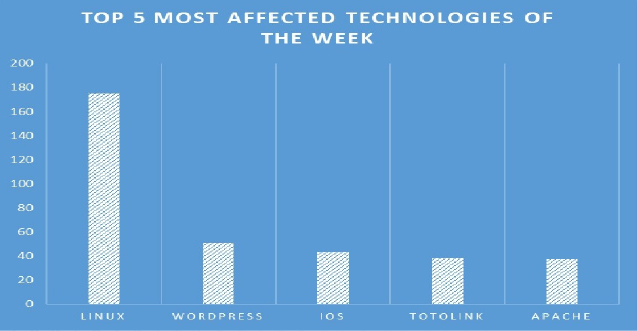
ETLM Assessment:
Vulnerability in GStreamer Orc can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Orc is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding data processing operations, especially those involving SIMD instructions across various architectures, in different geographic regions and sectors.
Raworld Ransomware attacked and Published data of Melchers Singapore
Summary:
Recently we observed that Raworld Ransomware attacked and published data of Melchers Singapore (www[.]melchers[.]com[.]sg) on its dark web website. The Melchers Group is a global service-oriented company that focuses on identifying, sourcing, and supplying quality products and services to selected market segments. The Singapore branch coordinates Melchers’ trading activities in Southeast Asia. The data leak, following the ransomware attack, includes legal documents, financial documents, business contracts, and other files containing sensitive and confidential information related to the organization. The total size of the compromised data is 15GB.
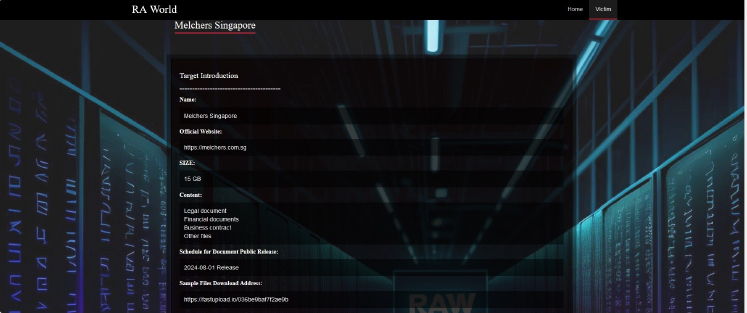
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that RA World Ransomware will persist in targeting various industries globally, particularly focusing on the United States, Europe, and Asia. The recent attack on Melchers Singapore, a prominent business services company, highlights the significant threat posed by this ransomware strain in the Southeast Asia region.
Digital Bank Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Digital Bank in an underground forum. The threat actor known as “Alcatraz666” claims to have breached sensitive personal data from a major digital bank in Indonesia. The compromised data, stored in CSV format, includes critical information, such as customer names (nasabah), ID numbers (no_nik), family card numbers (no_kk), account numbers (no_rekening), full names (nama_lengkap), genders (jenis_kelamin), dates of birth (tanggal_lahir), places of birth (tempat_lahir), home addresses (alamat_rumah), and additional valuable details.
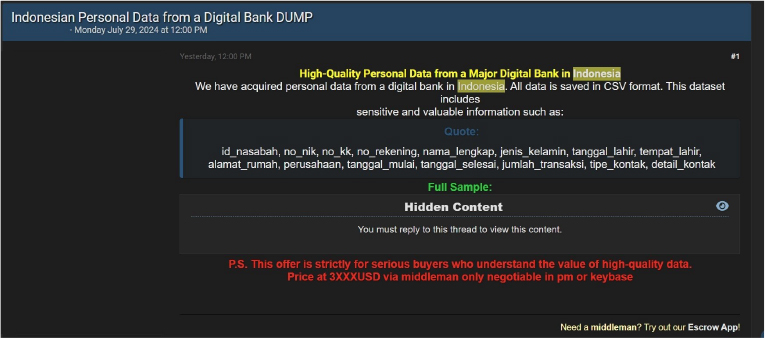
Source: Underground Forums
SIAK DUKCAPIL MINISTRY OF HOME AFFAIRS OF INDONESIA data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to the SIAK DUKCAPIL MINISTRY OF HOME AFFAIRS OF INDONESIA in an underground forum. The breached data includes NIK (ID Card No), Name, KK (Family Card No), Gender, DOB, Mother’s Maiden Name, Mother’s ID Card No, Father’s Name, Father’s ID Card No, Address, and other details in CSV format. The total size of the data is 131 GB, and it is priced at 5,000 USD.
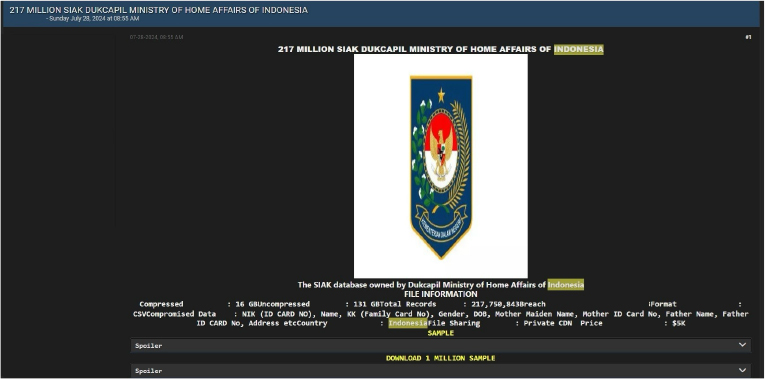
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as “Alcatraz666” poses a significant risk to organizations. This group is known for targeting various institutions and profiting from selling sensitive data on the dark web or underground forums. Organizations targeted by “Alcatraz666” typically have inadequate security measures, making them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data leak related to the Saudi Arabia Marketing Company. A threat actor published a post on a dark web forum about an alleged data leak from a Saudi company. According to the post, Saudi Marketing Company, which operates 90 branches and 17 mini markets, suffered a data breach in July 2024 through its FarmGo app. This breach allegedly led to the exposure of sensitive information belonging to 568,886 users.
The Compromised Data Includes:
The threat actor also published a sample from the alleged leak and no price information was included. The data breach is allegedly claimed by the threat actor “888”.

Source: Underground forums
The CYFIRMA Research team observed a potential data sale related to Vivamax (Philippines). According to the post, a user on a dark web forum is selling a substantial dataset from Vivamax, a service provided by VIVA COMMUNICATIONS, INC. in the Philippines.
According to the post, the data was acquired through API scraping, specifically by using authenticated access with admin privileges.
The seller describes two main categories of data available:
The Members/Subscribers Data is noted to be over 2.08 GB in size, containing more than
6.8 million lines, all formatted in JSON. This dataset purportedly includes detailed personal information, such as full names, phone numbers, email addresses, countries of registration, account creation dates, subscription IDs, subscription start and end times, subscription types (including Google, Huawei, card, Apple, and PayMaya), and parental control pins.
Additionally, the post mentions the availability of Subscribers’ Transaction Data, which is approximately 1.0 GB in size and includes multiple transaction rows per line, also formatted in JSON.
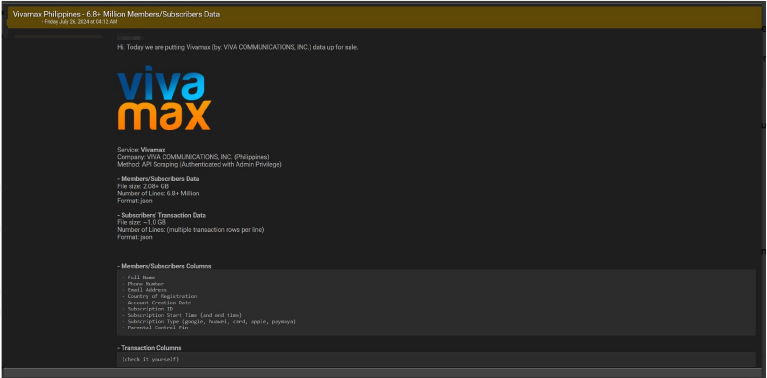
Source: Underground forums
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as “888” poses a significant risk to organizations. This group is known to target any institution and profit from selling sensitive data on the dark web or underground forums. Organizations targeted by “888” typically have inadequate security measures, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
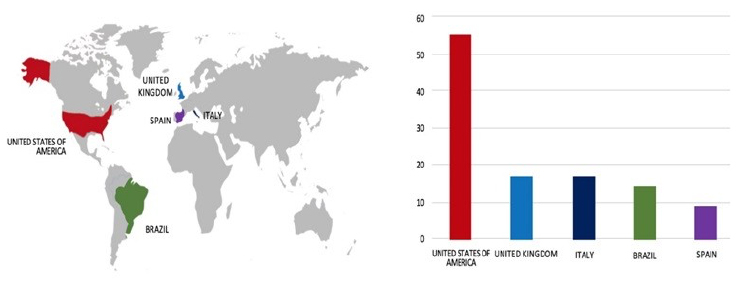
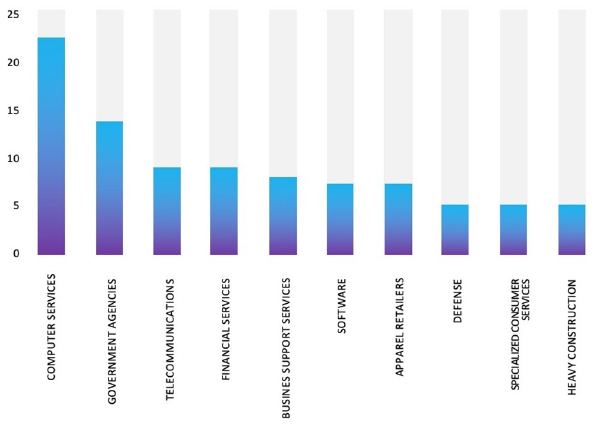
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.