



Key Intelligence Signals:
An Unknown China-based Threat Actor Observed Stealing Information from Korean Companies
Summary:
In a recent development, researchers observed a China-based unknown threat actor targeting Korea-based companies and shared very limited information about the whole incident. One company targeted was in the semiconductor industry and the other was in smart manufacturing, by utilizing artificial intelligence. Researchers also suspected that threat actors named Xiaoqiying and Dalbit could be behind this attack. The threat actor employed FRP (Fast Reverse Proxy) and deployed it on the victim’s vulnerable server. Within this server, a variety of hacking tools like CobaltStrike, VPN, and remote control reside, alongside numerous log files were uploaded. These log files are stored within directories named numerically. Among the stealer logs, one can find credentials, network details, and assumed proprietary data, belonging to various companies.
Insights:
The operation, led by the China-based unknown threat actor, focused on the outright theft of information and credentials. There is a possibility that the acquired data could be employed to aid and assist the same industries in China.
The specific vulnerability used by the threat actor to access the server remains undisclosed. However, it appears that they exploited a Remote Code Execution vulnerability for their malicious activities.
The Chinese nation-state actor known as Mustang Panda or Bronze President has been linked to the new set of sophisticated and targeted attacks, aimed at European foreign affairs institutions, since the beginning of the year. According to researchers, the APT is using a custom firmware implant, designed explicitly for TP-Link routers, which includes a custom backdoor named ‘Horse Shell’ that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks.
It is presently uncertain how exactly the altered firmware images were installed on the compromised routers, as well as how it was exploited and involved in actual assaults. Initial access is thought to have been obtained via taking advantage of well-known security holes or brute-forcing systems with pre-set or weak passwords. The malicious implant gives the attackers access to the router, allowing them to upload and download files, as well as relay communication between two clients.
According to researchers, the discovery is yet another example of a long-standing trend of Chinese threat actors to exploit internet-facing network devices and modify their underlying software or firmware for espionage purposes. Mustang Panda itself has targeted both NGOs and governmental organizations for espionage purposes before. However, it has previously focused on Asia, while the latest attack has been targeting undisclosed European countries.
Recently leaked classified U.S. intelligence files suggest that a pro-Russian hacktivist group may have breached the network of a Canadian gas pipeline company in February. The group, known as Zarya, is reported to be an offshoot of Killnet; a well-known hacktivist group that has previously targeted websites and organizations in the United States.
The briefing describes intercepted communication between Zarya and a representative of the FSB; Russia’s primary intelligence service, including the FSB representative instructing hackers on how to manipulate controls to cause an emergency pipeline shutdown. The briefing is part of a larger set of leaked documents that show how the United States gathers intelligence on its major allies, enemies, and rivals.
The FSB officer stated in his instructions that while “a successful operation would cause an explosion,” the objective was “not to cause loss of life” but rather to cause financial damage. The capacity of Zarya to create an explosion was questioned by several experts, who claimed that physical safety measures would have most certainly prevented such a result.
Researchers have reported on a supposed Islamist Sudanese hacktivist collective, dubbed Anonymous Sudan, which appears in fact to be a false-flag operation, conducted by Russian intelligence services. A recently published report concludes that the group uses a false pretext to disguise a Russian operation, directed at Sweden to interfere with Sweden’s accession to NATO, using a mix of nuisance-level distributed denial-of-service (DDoS) attacks and influence operations, directed at Sweden’s Muslim minority and Turkish public opinion.
The group has demonstrated a depth of understanding of Swedish politics and its societal and religious frictions and access to money, much beyond an average hacktivist organization, while the timing and organization of the attacks and operational similarities to other Russian psyops are just some of the reasons why researchers have concluded that Anonymous Sudan is a Russian front.
The collective on their part has tried to deflect the accusation by stating that they’re not Russian but repaying Russia for its help in the past, which is yet another implausible claim since the ongoing mass use of violence in Sudan would suggests that actual Sudanese Islamist hacktivists would have more pressing concerns in their homeland.
CYFIRMA Research team observed a potential data leak related to Liferay, (www[.]liferay[.]com). Liferay is an open-source company that provides free documentation and paid professional service to users of its software. Mainly focused on enterprise portal technology, the company has its headquarters in the United States of America. The data breach comprises of confidential and sensitive information of customers.
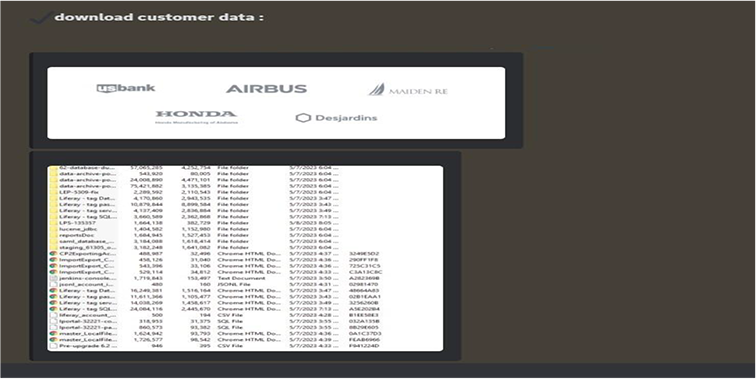
Source: Underground forums