



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
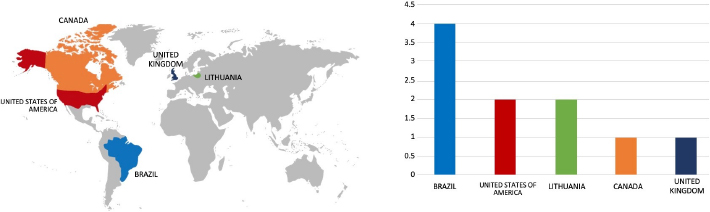
Target Countries: Australia, Canada, Colombia, Curacao, France, Germany, Ireland, Italy, Malaysia, New Zealand, Palau, Portorico, South Africa, Spain, Sweden, United Kingdom, United States.
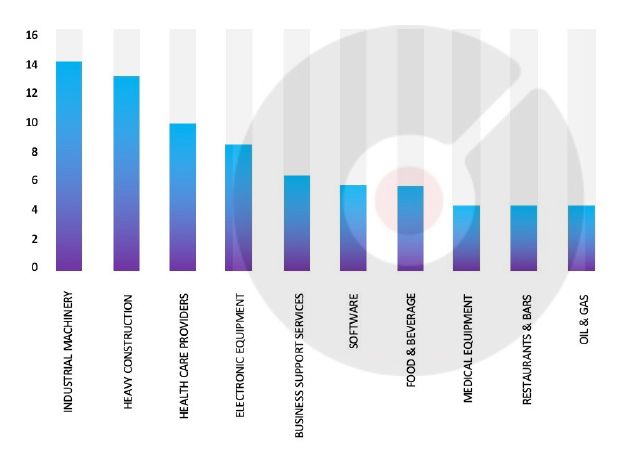
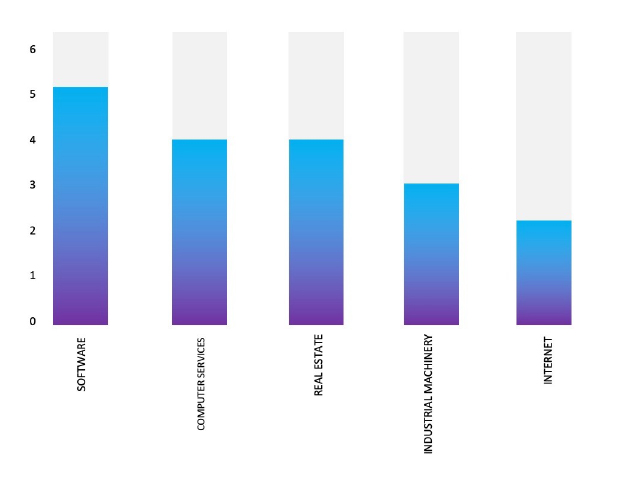
Target Industries: Accounting, Business Service, Construction, Education, Energy, Finance, Government, Healthcare, Hospitality, Law, Manufacturing, Real Estate, Retail, Software, Transportation.
Introduction
CYFIRMA Research and Advisory Team has found DragonForce while monitoring various underground forums as part of our Threat Discovery Process.
DragonForce
Researchers uncovered a new ransomware variant dubbed DragonForce in the mid of July 2024. This ransomware encrypts files, renames each encrypted file, and leaves a ransom note titled “readme.txt.” The renaming process involves replacing the original filenames with random strings and appending the “.dragonforce_encrypted” extension.
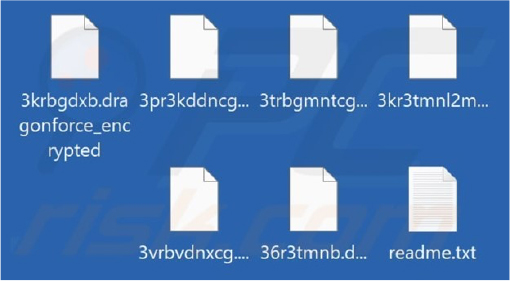
Screenshot of files encrypted by this ransomware (Source: SurfaceWeb)
The ransom note from the DragonForce ransomware states that the cybercriminals have stolen and encrypted files, demanding payment in Bitcoin for their decryption. The recovery process involves contacting the attackers, receiving a list of stolen files, verifying their decryption capabilities, agreeing on a payment amount, and then receiving a decryption tool.
The note instructs victims to contact the attackers via a Tor Browser link and a unique ID, with additional support available through Tox messenger.
It also warns against resetting or shutting down the system, renaming or moving files, and deleting the ransom note, to avoid further damage. The note threatens that if the victim does not comply by the specified time and date, the stolen files will be published, and the decryption tool will be destroyed.
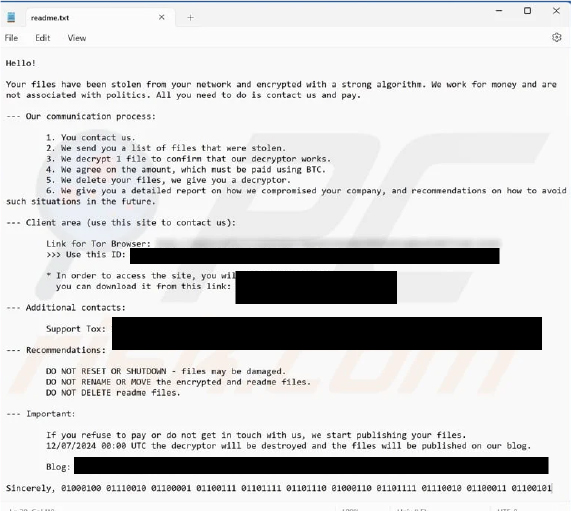
Screenshot of DragonForce’s text file (“readme.txt”) (Source: SurfaceWeb)
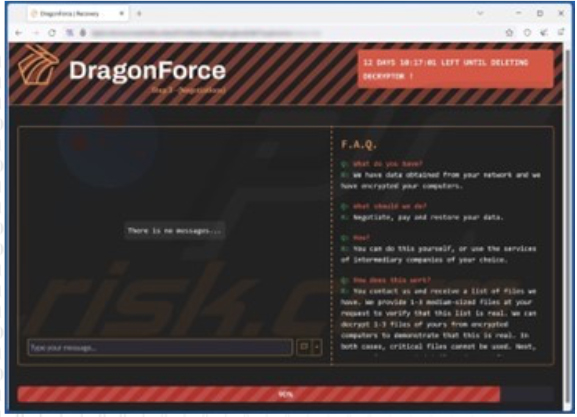
Screenshot of DragonForce’s contact website (Source: SurfaceWeb)
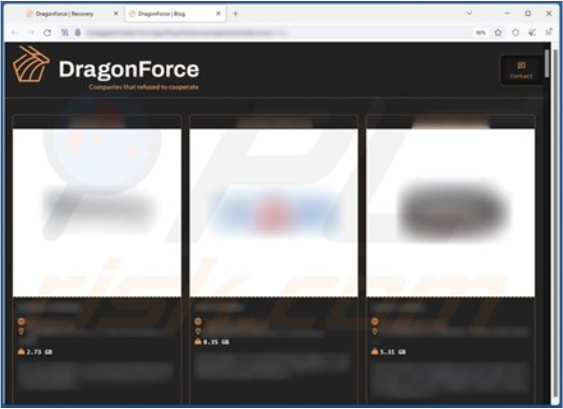
Screenshot of DragonForce’s data leaking site (Source: SurfaceWeb)
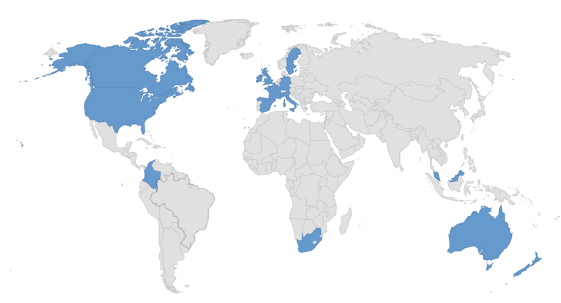
Targeted countries
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053.005: Scheduled Task/Job: Scheduled Task |
| T1129: Shared Modules | ||
| T1569.002: System Services: Service Execution | ||
| 2 | TA0003:Persistence | T1053.005: Scheduled Task/Job: ScheduledTask |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1574.002: Hijack Execution Flow: DLL Side – Loading | ||
| 3 | TA0004: Privilege Escalation | T1053.005: Scheduled Task/Job: Scheduled Task |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side – Loading | ||
| 4 | TA0005: Defense Evasion | T1027.005: Obfuscated Files or Information: Indicator Removal from Tools |
| T1036: Masquerading | ||
| T1070: Indicator Removal | ||
| T1055: Process Injection | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System |
| T1114: Email Collection | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 10 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s anticipates with available data, DragonForce ransomware could likely expand its attack footprints in other regions in Southeast Asia possibly to include nations such as Thailand, Indonesia, Singapore and others, given that its already observed presence in Malaysia. This anticipated shift could be attributed to the increasing digital transformation in these regions, presenting lucrative opportunities for cybercriminals. Technically, DragonForce may enhance its obfuscation techniques, leverage advanced persistence mechanisms, and increase the use of WMI and registry manipulation to evade detection and hinder data recovery efforts.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
SIGMA Rule:
title: Uncommon File Created In Office Startup Folder tags:
– attack.resource_development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_* falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high
(Source: SurfaceWeb)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing financial information, Data exfiltration
Target Technology: Windows OS
Target Industry: Financial Institutions, Banks
Target Geographies: Latin America (Brazil)
Active Malware of the Week
This week “Coyote” is trending.
Coyote
Coyote is a .NET banking Trojan that targets Brazilian financial institutions in the LATAM region. It is notable for its unique execution methods, which set it apart from other similar Trojans. First detected in February 2024, Coyote earned its name by leveraging Squirrel, a legitimate software tool used for managing Windows application installations and updates. During attacks, Coyote injects a compromised DLL into legitimate files like OBS and Chromium Embedded Framework, using the Nim programming language. This allows it to persistently harvest financial information from users of Brazilian banks. Coyote has also been observed targeting Binance, the world’s largest cryptocurrency exchange, by daily trading volume.
Technical Analysis
While the delivery method of the Coyote Trojan wasn’t directly observed during analysis, it is typically distributed through phishing. Users are lured into clicking malicious links rather than receiving them as email attachments, likely due to their large file size (+170 MB), which could cause emails with such attachments to be blocked by systems limiting large files. File names in Brazilian Portuguese found on systems suggest the Trojan targets exclusively Brazilian victims. Examples of filenames used during the attack include:
Upon execution of the main malicious file, such as pdfpapel327088636055.exe, the Coyote Trojan initiates a complex installation process using Squirrel for updates:
Persistence on the infected system is ensured through modifications in the Registry:
Upon launching the benign obs-browser-page.exe, the Squirrel update process loads libcef.dll, a non-malicious Google Chrome DLL vulnerable to DLL sideloading. This DLL then loads the malicious chrome_elf.dll. The final loaded DLL, chrome_elf.dll, functions as a Nim loader, facilitating the execution of the embedded Coyote banking Trojan in memory.
Nim, a modern programming language incorporating features from Python, Ada, and Modula, enables Coyote to perform advanced operations upon activation. The Trojan selectively communicates with its command-and-control (C2) servers only when the active window title matches the predefined targets list. Coyote’s capabilities encompass 24 distinct commands and functions, including capturing screenshots, displaying full-screen overlays (such as fake banking apps), modifying registries, simulating mouse movements, initiating system shutdowns, and logging keystrokes.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolution of Coyote malware suggests several implications for organizations and employees. As malware authors refine their techniques, future iterations of Coyote and similar Trojans are expected to become more sophisticated and adaptable. This could lead to faster adaptation to security measures and more complex evasion tactics, posing significant challenges for cybersecurity teams in detecting and mitigating such threats. Future variants of Coyote may increasingly focus on targeted attacks customized for specific organizations or industries. This could involve deeper reconnaissance and more precise exploitation of vulnerabilities unique to each target, potentially resulting in more damaging and costly breaches.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules import “pe”
rule coyote_nimloader { meta:
hash = “110b616bc12c29b070b0dc60c197a4d63b3e3caae6bb80a25b8864489a51da79”
hash = “1bed3755276abd9b54db13882fcf29c543ebf604be3b7fcf060cbd6d68bcd23f” strings:
$nim1 = “strformat.nim” fullword ascii
$nim2 = “fatal.nim” fullword ascii
$nim3 = “io.nim” fullword ascii
$export_name = “chrome_elf.dll” fullword ascii condition:
pe.characteristics & pe.DLL and pe.number_of_sections > 8 and $export_name and (2 of ($nim*))
}
Source: Surface web
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
MuddyWater Cyber Threat Analysis: Phishing Campaigns and Advanced Malware Tactics
Summary:
MuddyWater, a persistent and sophisticated threat group, has been conducting extensive phishing campaigns primarily targeting organizations in the Middle East, including Israel, Saudi Arabia, Turkey, India, Portugal, Azerbaijan, and Jordan. Their focus encompasses a diverse range of sectors such as municipalities, airlines, travel agencies, media outlets, and government entities, reflecting their strategic interests and objectives.
The group typically initiates their attacks by sending large volumes of spear-phishing emails from compromised accounts. These emails contain meticulously crafted lures tailored to specific industries. For example, early campaigns aimed at municipalities included lures promoting a new municipal app with a subject like “Special Offer: New App for Municipalities – Limited Time Only!” More recent campaigns have adopted more generic themes such as invitations to webinars and online courses, allowing the same lure to be reused across different targets and regions. While these campaigns initially employed the locally spoken languages of their targets, there has been an increasing use of the English language.
A significant advancement in MuddyWater’s attack methods is the deployment of the custom-made BugSleep backdoor, introduced in May 2024, which partially replaces their use of legitimate Remote Monitoring and Management (RMM) tools. BugSleep is a sophisticated malware that includes several versions with varying features and bug fixes, suggesting a trial-and-error development approach. The typical infection chain begins with the abuse of Egnyte subdomains, which are used for seemingly legitimate file-sharing. Recipients receive links that appear to come from legitimate sources, aligning with the naming conventions of the targeted country. For instance, in a link sent to a transportation company in Saudi Arabia, the displayed name was Khaled Mashal, a former prominent leader of Hamas.
BugSleep employs several evasion techniques, such as making multiple calls to the Sleep API to evade sandboxes and enabling flags to prevent other processes from injecting DLLs or generating dynamic code. The malware creates a mutex, decrypts its configuration (including the Command and Control (C&C) IP address and port), and ensures persistence by creating scheduled tasks that run the malware at regular intervals. The malware’s communication with the C&C server is encrypted, with every message following a specific format. BugSleep can perform various commands based on the data sent from the C&C, and it incorporates additional evasion methods to protect against Endpoint Detection and Response (EDR) solutions.
MuddyWater’s campaigns have been linked to over 50 spear-phishing emails targeting more than 10 sectors and hundreds of recipients since February 2024. Their operations have been consistently attributed to them due to distinct patterns of behavior and tools observed over several years. The group’s activity highlights their persistent nature and evolving tactics, posing a significant threat to a wide array of targets. Their espionage-driven campaigns aim to gather intelligence and disrupt operations in strategically important sectors, with a notable increase in activity and focus on higher volume rather than highly specific targets. The shift to simpler, more versatile phishing lures and the development of tailored malware like BugSleep underscores their adaptability and continued operational threat.
Relevancy & Insights:
MuddyWater, an Iranian threat group active since at least 2017, has targeted a diverse range of sectors including telecommunications, defense, local government, and oil and natural gas across Asia, Africa, Europe, and North America. Known for using tools developed in Python, C#, and PowerShell, they exploit vulnerabilities and utilize open- source tools for unauthorized access, espionage, intellectual property theft, and occasionally deploying ransomware. Their recent deployment of the BugSleep backdoor underscores their ongoing cyber espionage activities, aimed at stealing sensitive data and providing illicit access to Iranian government entities, often sharing these accesses with other cyber actors. The group has intensified operations in Israel since October 2023 amid geopolitical tensions, alongside targeting entities in Saudi Arabia, Turkey, Azerbaijan, India, and Portugal. Organizations in sectors of strategic importance and regions targeted by MuddyWater should prioritize robust cybersecurity measures and vigilance against evolving threats to mitigate potential impacts.
ETLM Assessment:
MuddyWater, an Iranian threat group affiliated with the Ministry of Intelligence and Security (MOIS) and active since 2017. MuddyWater conducts widespread cyber espionage globally, with recent escalations in Israel and targeting sectors such as telecommunications, defense, local government, and oil and natural gas across Asia, Africa, Europe, and North America. They exploit vulnerabilities through phishing campaigns from compromised email accounts, deploying tools like Atera Agent and Screen Connect. Known for leveraging malware variants like PowGoop, Small Sieve, Canopy (Starwhale), and most recently, the new BugSleep backdoor, MuddyWater’s tactics emphasize persistence and strategic data theft. As part of the broader state- sponsored threat landscape, their operations highlight the evolving sophistication in cyber espionage. Future assessments indicate ongoing threats, necessitating vigilant cybersecurity practices, including regular updates, user education against phishing, and robust defenses tailored to detect and counter such advanced persistent threats.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers deploy new malware
Researchers have recently published a report on “DodgeBox,” a newly discovered malware loader associated with the Chinese threat actor APT41. DodgeBox is used to install a new backdoor dubbed “MoonWalk” that uses Google Drive for command-and- control communications. According to the researchers, what sets DodgeBox apart from other malware is its unique algorithms and techniques. The telemetry suggests the malware has been used to target entities in Thailand and Taiwan, which aligns with APT41’s previous targeting.
ETLM Assessment:
The consolidation of ties among a new Russian-North Korean security partnership signed during President Vladimir Putin’s visit to Pyongyang, and comments by Xi Jinping and Putin at the Shanghai Cooperation Organization about cooperating to resist external interference and push back on American hegemony signal the intensification of efforts by the so-called axis of ill will to dominate their respective neighborhoods. The observed campaign is likely a state-sponsored effort to gain intelligence in the hotly contested region and many others similar to this one are expected to be going on at the same time.
The Hunters International Ransomware impacts the Carigali Hess Operating Company
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; (www[.]carigalihess[.]com), was compromised by the Hunters International Ransomware. Carigali Hess Operating Company (CHOC) is a joint venture between PETRONAS Carigali JDA Ltd. and Hess Oil Company of Thailand Ltd. The company operates in the Malaysia-Thailand Joint Development Area (JDA) on Block A-18, focusing on gas production. The breached data includes sensitive and confidential organizational information.
The following screenshot was observed published on the dark web:
Source: Dark Web
Relevancy & Insights:
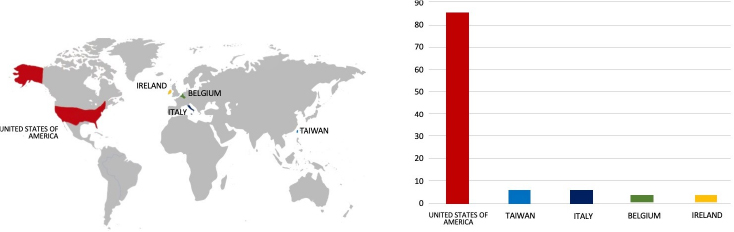
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Hunters International Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Carigali Hess Operating Company, a prominent Gas company in Malaysia, underscores the extensive threat posed by this ransomware strain in the Southeast Asia region.
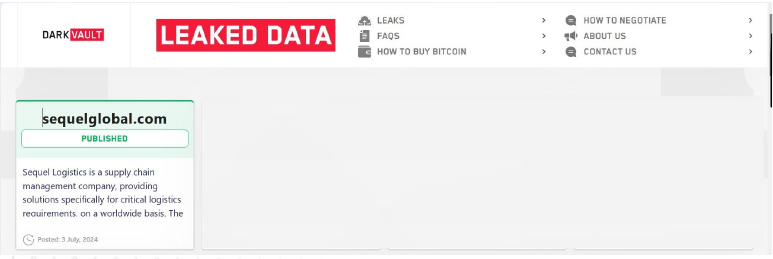
The DarkVault Ransomware impacts the Sequel Global
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; (www[.]sequelglobal[.]com), was compromised by the DarkVault Ransomware. Sequel Logistics is a supply chain management company, providing solutions specifically for critical logistics requirements, on a worldwide basis. The company was founded in 2004 in Bangalore, and over the years, has developed specialized capabilities and domain knowledge, to design, execute, and manage the supply chain and logistics of high-value and critical products for B2B & B2C business in India, the US, and Europe. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:
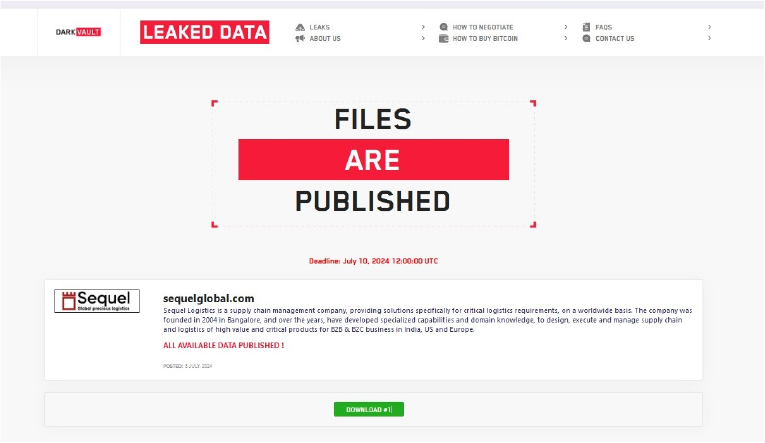
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The DarkVault ransomware group has honed its approach to deploying ransomware by leveraging a variety of sophisticated techniques. These include phishing emails, which lure victims into clicking on malicious links or attachments and exploiting vulnerabilities in unpatched software to gain initial access to systems. According to CYFIRMA’s assessment, DarkVault is likely to continue its aggressive targeting of a wide array of industries on a global scale. Their focus is particularly intense in the United States, Europe, and Asia. A recent attack on Sequel Global, a leading Logistics company based in India, highlights the broad and severe threat posed by DarkVault, especially in South Asia. This incident underscores the group’s capacity to disrupt operations and underscores the critical need for robust cybersecurity defenses across diverse regions and sectors.
Vulnerability in Apache Wicket
Summary:
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation. A remote attacker can perform XSLT injection and execute arbitrary code on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable systems.
Affected Products: https[:]//lists[.]apache[.]org/thread/lm84pzcbh34rsv9spz9cm24g4jspzbqg
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
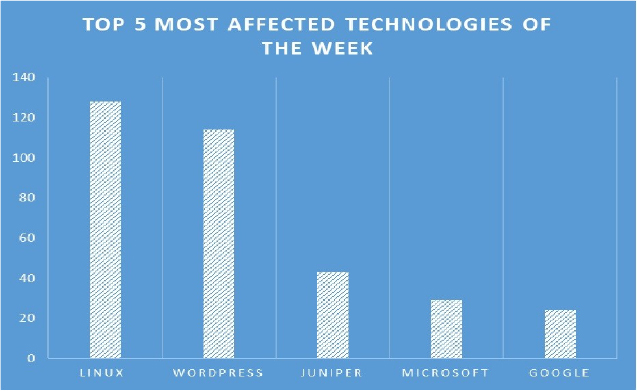
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Apache Wicket can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Apache Wicket is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding web applications built using this component-based framework across different geographic regions and sectors.
RansomHub Ransomware attacked and Published data of the Coca-Cola – Myanmar office
Summary:
Recently we observed that RansomHub Ransomware attacked and published data of the Coca-Cola – Myanmar office (www[.]coca-cola[.]com[.]mm) on its dark web website. The Coca-Cola Company is an American multinational corporation. It manufactures, sells, and markets soft drinks including Coca-Cola, other non-alcoholic beverage concentrates and syrups, and alcoholic beverages. Coca-Cola operates in Myanmar through its local subsidiary, Coca-Cola Pinya Beverages Myanmar Ltd. The Myanmar office is involved in manufacturing and distributing Coca-Cola products and has made significant investments in local production facilities. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization. The total size of the compromised is 800 GB.
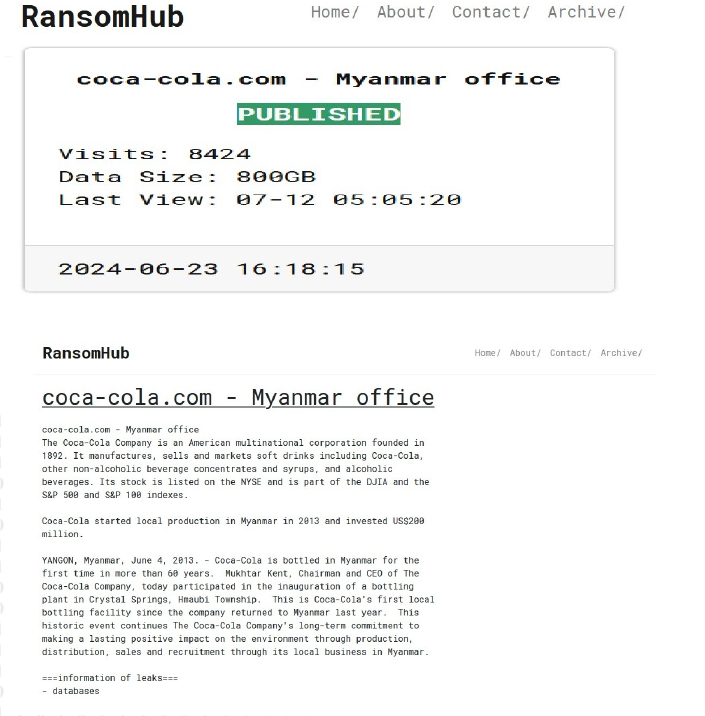
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that RansomHub Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on the Coca-Cola – Myanmar office, a prominent Food and Beverage company located in Myanmar, underscores the extensive threat posed by this particular ransomware strain in the Southeast Asia region.
Indonesian Government Employees Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Indonesian Government Employees in an underground forum. A threat actor shared an alleged data leak on a dark web forum. According to the threat actor, the alleged leak belongs to an online attendance service for government employees in Blora district, Indonesia.
The forum post also contains a data sample from the alleged leak. According to the sample, the leak contains IDs, email addresses, names, passwords, usernames, and other data points. Price information, details of the leak, and information about the time of the leak are not stated. The threat actor only says that those interested can DM for more information.
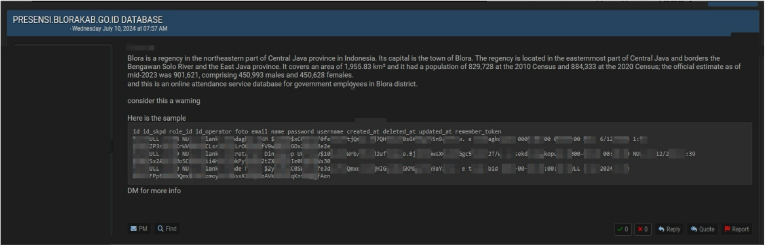
Source: Underground Forums
PT Tekno Mandiri Abadi Indonesia data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to PT. Tekno Mandiri Abadi in an underground forum. A hacker has claimed to possess and is now selling the customer data of PT. Tekno Mandiri Abadi, a distributor of Epson Indonesia. According to the hacker, the compromised data includes comprehensive personal and business information of 60,000 customers.
The data fields allegedly available in the breach are extensive, covering customer IDs, contact information, business phone numbers, mobile numbers, emails, fax numbers, websites, primary currencies, notes, billing addresses, cities, provinces, shipping addresses, accounts receivable, advance accounts, invoice totals, including tax, taxpayer identification numbers (NPWP), tax obligations, national identity numbers (NIK), VAT registration numbers (NPPKP), tax addresses, initial balances, initial balance dates, currency balances, and more.
The hacker has provided a sample of personal data from the breach to validate their claims, emphasizing the scale of the breach and the substantial amount of customer records involved. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.
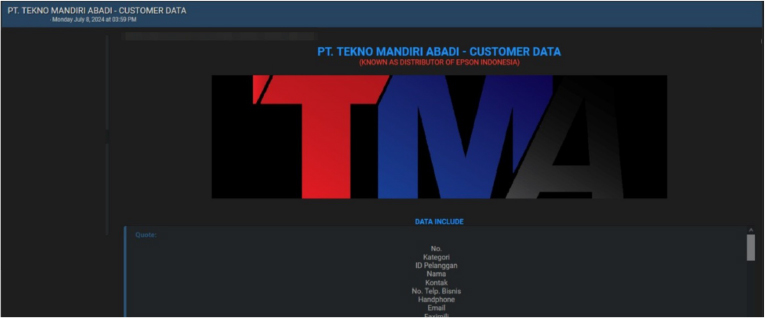
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as “Sedapmalam” poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by “Sedapmalam” typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data leak related to 1Tx(Singapore). 1TX is a tech-focused organization that offers a variety of innovation and performance-testing tools & services to assist organizations in successfully digitalizing. A threat actor claimed that 1Tx.io suffered a data breach, potentially exposing the information of up to 23,000 companies. The compromised data, formatted in a CSV file with 23,305 rows, includes various sensitive details.
The data fields allegedly include company IDs, account types, company names, emails, first and last names, roles, user IDs, and other pertinent information, such as phone numbers, skillsets, and marketing consent status. This breach could have far-reaching implications for the affected companies and individuals.
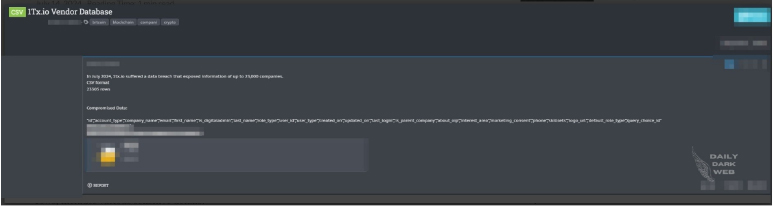
Source: Underground forums
The CYFIRMA Research team observed a potential access sale related to a Japanese electronics company. IntelBroker claims to be selling access to a Japanese electronics company. The company has a revenue of $60 billion. Access includes API (customers, inventory, orders) and any point.
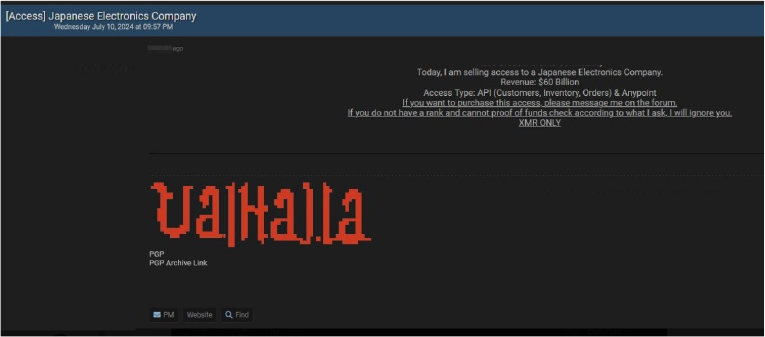
Source: Underground forums
ETLM Assessment :
Threat Actor ‘IntelBroker’ group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
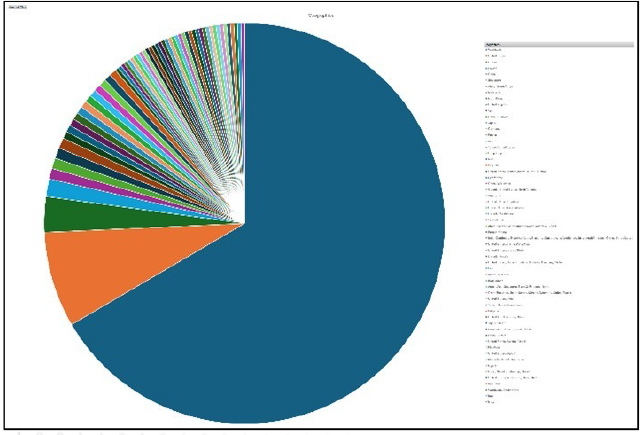
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.