



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Industries: Agriculture, Accessories, Accounting Services, Business Services, Customer Services, Construction, E-Commerce, Education, Energy, Finance, Government, Law Firms, Healthcare, Hospitality, Manufacturing, Media, Non-Profit Organizations, Retail, Software, Telecommunications, Transportation.
Target Geography: Argentina, Australia, Belgium, Brazil, Canada, Colombia, Chile, France, India, Italy, Japan, Malaysia, New Zealand, Spain, South Africa, Slovakia, Turkey, United Kingdom, United States.
Introduction
CYFIRMA Research and Advisory Team has found Medusa ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Medusa
Medusa ransomware appeared in late 2022 and became well-known in early 2023. It specifically goes after Windows systems. It’s important to note that Medusa is not the same as another ransomware called MedusaLocker, which has been around since 2019.
Medusa encrypts data, adds the “.MEDUSA” extension to encrypted filenames, and places a ransom note in a file named “!!!READ_ME_MEDUSA!!!.txt.”
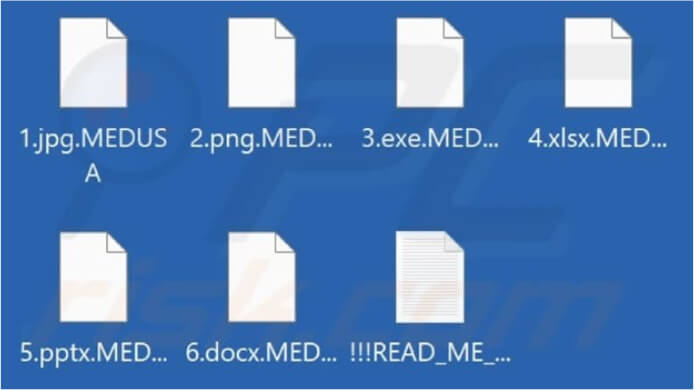
Screenshot of a Files Encrypted by Medusa Ransomware. (Source: Surface Web)
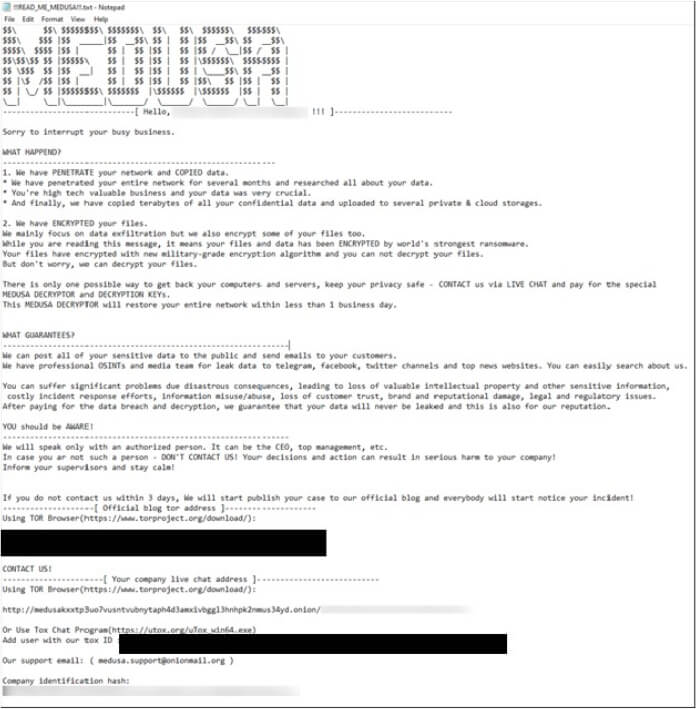
Medusa ransomware ransom note. (Source: Surface Web)
Tools and techniques used by Medusa ransomware actors that were discovered during a recent incident:
Medusa ransomware operators were seen uploading a webshell to a Microsoft Exchange Server that had been compromised.
After engaging in webshell activity, threat actors employed PowerShell to initiate a bitsadmin transfer from a file hosting site known as filemail[.]com. The downloaded file from this site was a ZIP archive named baby[.]zip. Upon decompression and execution, it installed remote monitoring and management (RMM) software called ConnectWise.
The operators of the Medusa ransomware deployed two kernel drivers, each designed to target distinct sets of security products. These kernel drivers were safeguarded using a software protector named Safengine Shielden. The Safengine Shielden protector applied code obfuscation techniques by randomizing the code through various mutations.
Additionally, it utilized an embedded virtual machine interpreter to execute the obfuscated code.
Each of the drivers was coupled with its loader. These loaders underwent packing using a tool known as ASM Guard. The packed loaders employed a deceptive UPX header, along with subsequent addresses positioned adjacent to the fabricated UPX bytes.
In the resource section, there are numerous references to ASM Guard, fake WINAPI imports, and various other junk paddings, as shown in the figure below.
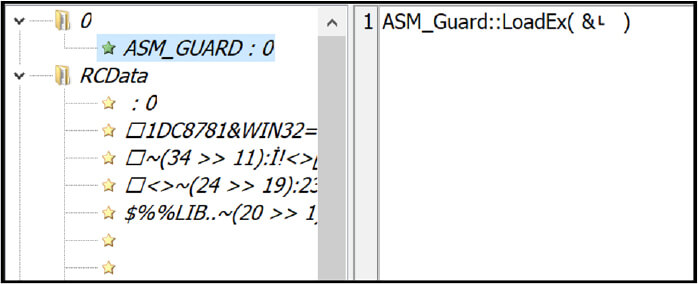
The resource section of the driver loader is packed with ASM Guard. (Source: Surface Web)
The primary objective of both drivers is to contain a list of security endpoint products to target for termination or deletion.
The comparison operation involves utilizing a fixed list of string names corresponding to security products, as depicted in the figure below. This list is then compared against the processes currently running on a system.
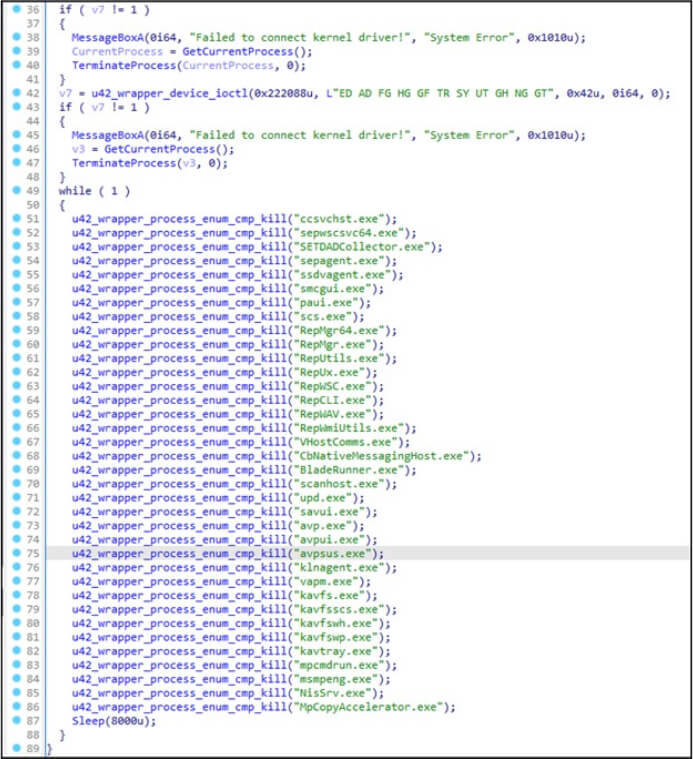
First driver targeting list of security processes for termination. (Source: Surface Web)
If the system identifies a running process with a name matching any of the predetermined security tool process names, an undisclosed IOCTL code (0x222094) is employed to terminate that process, as illustrated in the figure below. The key distinction between the two drivers lies in their utilization of file paths and the specific IOCTL (0x222184). This IOCTL, based on the provided file path, facilitates the deletion of the corresponding file.
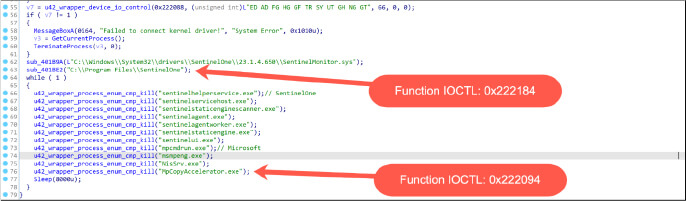
The second driver targeting file paths and list of processes. (Source: Surface Web)
The threat actors are employing a unique approach by utilizing the portable version of Netscan. They have paired it with an associated netscan.xml file, enhancing the software’s overall functionality right from the start. This enhanced functionality encompasses diverse types of remote service discovery and preconfigured mappings for actions like PsExec.
Additionally, it facilitates the deployment of the ransomware binary.
Many options are available from the custom configuration related to the following:
The capabilities of the tool VBScript and JScript.
Remote scripts utilize Cyrillic script, but they are translated into English. This translation indicates that the preferred language of the creator and users of the configuration are English speaking individuals.
After completing a network scan, the operator of the tool can right-click on a device listed in the results, revealing numerous custom point-and-click options on a remote system, as illustrated in below figure. The menu options in figure, concluding with “Gaze,” adhere to a naming convention employed by Medusa ransomware. This provides insights into a technique for deploying the Medusa ransomware, as indicated by the associated ransomware binary.
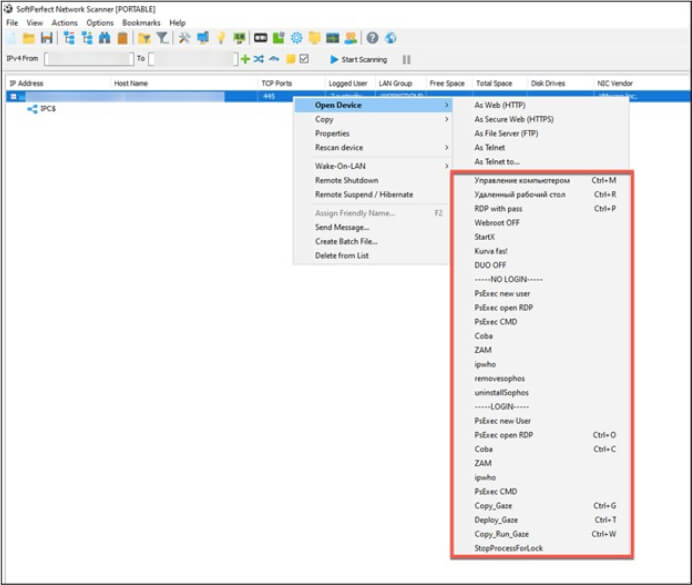
Medusa ransomware configuration. (Source: Surface Web)
A consistent theme within the Medusa ransomware binary aligns with the mythology of Medusa herself, notably the utilization and incorporation of the term “gaze” in the debug path within PEStudio. This thematic pattern extends to the binary’s name and the naming convention applied in the netscan.xml configuration file.
The Medusa ransomware can be run with 11 possible arguments, as shown below.
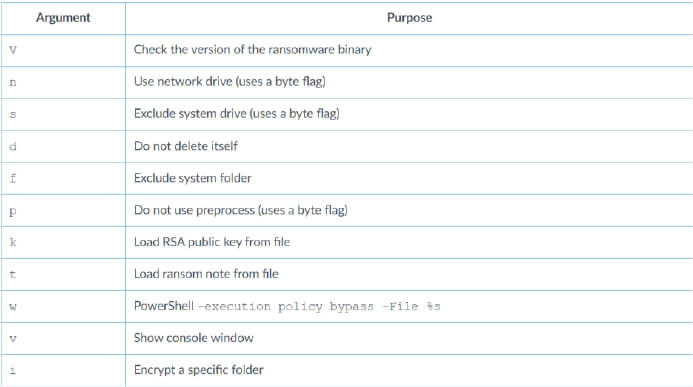
(Source: Surface Web)
Executing a recent Windows executable sample with the -V argument reveals that the sample is identified as version 1.20, as depicted in the figure below. This versioning system indicates a development cycle for the ransomware. One of the earliest publicly observed instances of the ransomware binary, uploaded in February 2023, corresponds to version 1.10, as indicated by its SHA-256.
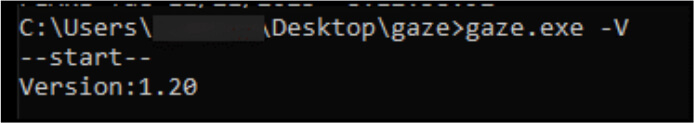
Ransomware sample version. (Source: Surface Web)
The ransomware binary employs string encryption for the following functions:
The ransomware employs RSA asymmetric encryption to safeguard the AES256 key, which, in turn, is utilized for encrypting a victim’s files. The AES256 key is established using a 32-byte key along with a 16-byte initialization vector.
While enumerating and encrypting files, the sample steers clear of files with the following extensions:
The following is the list of folder paths that the ransomware skips:
The ransomware executes various vssadmin-related operations and delete itself using the following commands to hinder recovery and forensic efforts:
Researchers observed a significant increase in ransomware activities, marked by the launch of the new Medusa Blog accessible through TOR on an .onion site in early 2023. This platform serves as a means for the perpetrators to expose sensitive data of victims who resist complying with their ransom demands.
Additionally, the group has incorporated links to Telegram and X (formerly known as Twitter) on the Medusa Blog site. The Telegram channel utilized by Medusa is named “information support” and is employed to disseminate and publish data exfiltrated by the group. Conversely, the link to X directs to a search result page for “Medusa ransomware.”
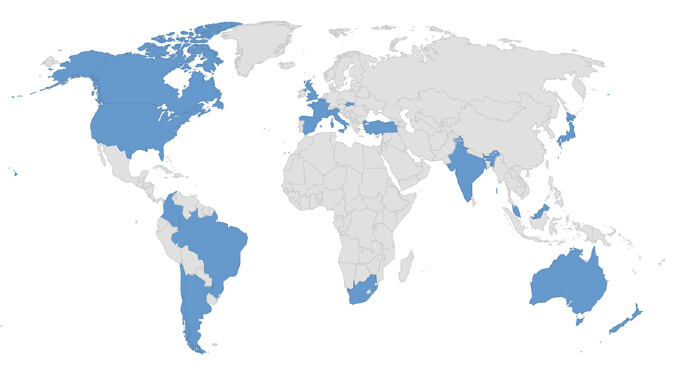
Countries targeted by Medusa. Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| 5 | TA0006: Credential Access | T1056: Input Capture |
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 7 | TA0009: Collection | T1056: Input Capture |
| T1560: Archive Collected Data | ||
| 8 | TA0011: Command and Control | T1090: Proxy |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery |
ETLM Assessment:
CYFIRMA’s assessment, relying on the available information about the Medusa ransomware, suggests that the threat is poised to evolve further in sophistication. Future iterations are likely to incorporate advanced evasion tactics, heightened focus on specific sectors and regions, and potentially more intricate methods for disseminating exfiltrated data. Moreover, the ransomware’s persistence mechanisms and anti-detection measures are anticipated to undergo further refinement, presenting continuous challenges for Organizations. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan/Hacktool
Objective: Infiltration, Credential Harvesting
Target Technology: Cloud, SaaS, Web Services & Payment Services (AWS, Office365, PayPal, Sendgrid, and Twilio)
Active Malware of the Week
This week“FBot”is trending.
FBot
Researchers have identified a new Python-based malware called FBot designed to target cloud and payment services. This sophisticated tool allows threat actors to compromise various web services, including Amazon Web Services (AWS), Office365, PayPal, Sendgrid, and Twilio. FBot stands out from other malware like AlienFox, Predator, Greenbot, and Legion as it does not utilize the Androxgh0st code.
FBot’s primary purpose is to facilitate the hijacking of cloud, SaaS, and web services, with a secondary focus on acquiring accounts for spamming attacks. The tool offers features for credential harvesting, allowing actors to gain initial access, which can be sold to other parties. Additionally, FBot includes various utilities such as an IP address generator, port scanner, and an email validator that leverages an Indonesian technology service provider.
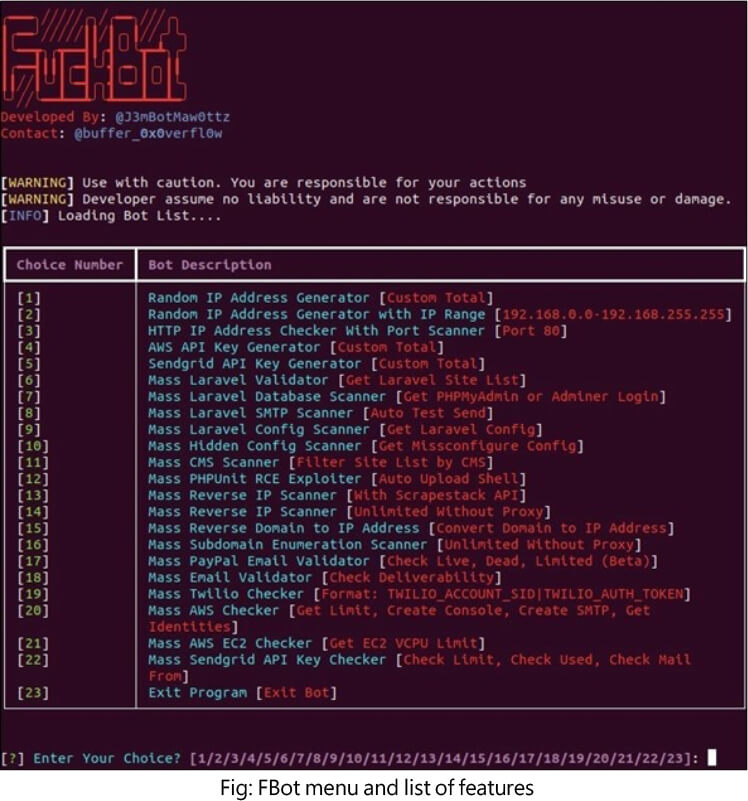
FBot’s AWS Attack Functions
FBot focuses on AWS account attacks with three dedicated functions.
The first function, aws_generator, creates a random AWS access key ID by appending 16 randomly selected alphabetic characters to the standard AKIA prefix. Subsequently, it generates a secret key using 40 randomly selected alphabetic characters. Despite not incorporating Androxgh0st modules, FBot shares a feature with the Legion stealer and an older Androxgh0st variant. This feature, identified in research, remains unchanged and is deemed unlikely to effectively brute force account credentials due to the vast number of potential combinations of access key and password.
The second AWS feature in FBot is the Mass AWS Checker, managed by the aws_checker function. This function examines AWS Simple Email Service (SES) email configuration details, including the maximum send quota and rate, as well as the number of messages sent in the past 24 hours. It also creates a new user account and associates the AdministratorAccess policy to elevate privileges for the new account, possibly for maximizing spamming efforts. Unlike other cloud attack tools, FBot does not delete the compromised account used for gaining access.
The third AWS feature is an AWS EC2 Checker, specifically focused on obtaining the EC2 VCPU Limit. The ec_checker function reads AWS identities from a text file and checks the targeted account’s EC2 service quotas. The tool provides information on the account’s EC2 configurations and capabilities, detailing the types of EC2 instances that can run. The script iterates through specified AWS regions, performs queries for each region, and logs the results to a text file.
Payment Services Exploitation: PayPal Validator
FBot includes features targeting payment services and SaaS configurations. One such feature is the PayPal Validator, managed by the paypal_validator function. This function validates PayPal account status by contacting a hardcoded URL with an email address from an input list, using the email in the customer details section to determine if it is associated with a PayPal account.
Notably, all identified FBot samples utilize the Lithuanian fashion designer’s retail sales website(hxxps[:]//www[.]robertkalinkin[.]com/index[.]php) for authenticating PayPal API requests, and several Legion Stealer samples also employ the same approach. The PayPal Validator feature crafts requests to this site, including a fake item ID and fabricated customer details, and then parses the response to determine the success status.
FBot’s SaaS Focus: Sendgrid and Twilio Exploits
FBot extends its targeting to various SaaS platforms such as Sendgrid and Twilio. For Sendgrid, there is a feature named Sendgrid API Key Generator, producing keys with a specific format. The Twilio feature involves taking the Twilio SID and Twilio Auth Token as input, separated by a pipe. This function checks the SID and auth token combination, retrieving details about the account, including balance, currency, and a list of phone numbers connected to the account.
Web Framework Features
FBot comes equipped with functionalities to verify whether URLs contain a Laravel environment file and to extract credentials from these files. The Hidden Config Scanner feature accepts a URL as input and constructs an HTTP GET request to multiple PHP, Laravel, and AWS-related URIs, where configuration values, including credentials, might be stored, including:
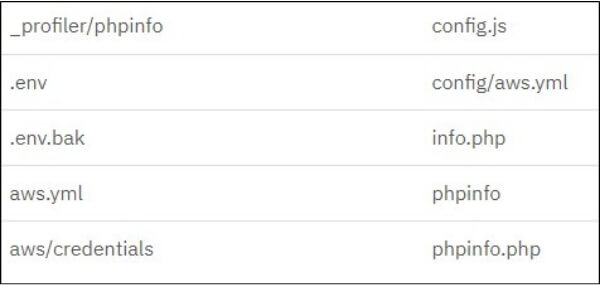
The response is analyzed for keys and secrets associated with the following services, and the outcome is recorded in a text file.
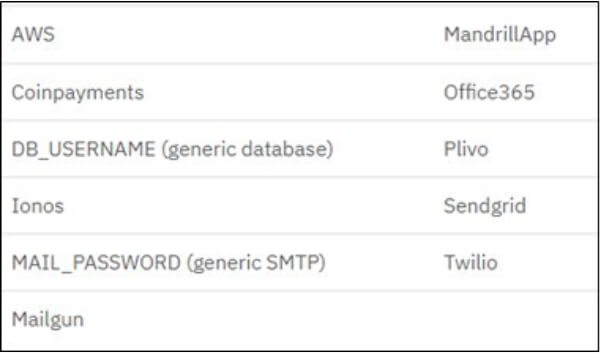
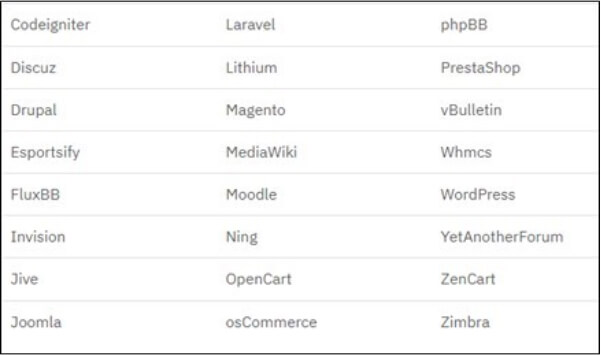
FBot extends its focus to various popular Content Management Systems (CMS). The cms_scanner function utilizes a map of CMS and web frameworks to corresponding regular expressions (regex) linked to the service. The tool generates a request to the specified URL and analyzes the response for the presence of the following technologies:
Taxonomy
FBot relies on configuration values provided through a configuration file or headers, and FBot has a version compiled as a Windows executable. The consistent use of the handle “iDevXploit” as the author is observed across all samples, with the aws_checker function leaving artifacts in targeted AWS consoles. FBot’s username and password are uniform in new AWS account creations. Unlike similar cloud hacktools, FBot lacks references to the Androxgh0st code present in tools like AlienFox, GreenBot, and Predator. While both Androxgh0st and FBot share a similar logic of parsing environment configuration files for credentials related to mail and cloud services, their implementations differ, indicating no direct code borrowing. There is notable similarity with the Legion cloud infostealer in how both tools scrape URLs for PHP configuration. However, FBot is smaller and less feature- rich than Legion, with FBot samples averaging around 200 KB, while Legion ranges from 800-1200 KB in size.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that FBot’s persistent targeting of critical infrastructures, including web servers, cloud services, and SaaS platforms, suggests a continuing threat to organizational cybersecurity. As it refines its capabilities, the potential for unauthorized access and credential exploitation may increase, posing heightened risks to the affected organizations. The adaptability demonstrated by FBot, along with its potential ties to private development, indicates an ongoing evolution that may lead to more sophisticated and targeted attacks in the future.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
related compliance issues.
Guarding Against Cyber Threats: Analysing a Surge in Android Malware Attacks
Summary:
In a recent observation, researcher have uncovered a series of malicious Android Package Kit (APK) files targeting Chinese users, orchestrating a sophisticated financial fraud scheme. The threat actors, posing as law enforcement officials, manipulate victims into downloading a deceptive app, leading to the theft of sensitive information and subsequent draining of bank accounts.
This malicious APK activity first appeared on our radar in November 2022, with a surge in delivery attempts more than 717 times in September 2023 after months of dormancy. The attackers exploit non-official third-party sources to distribute their malware, utilizing social engineering tactics observed in Chinese security advisories.
The malicious Android application, disguised as “安全防护” (Security Protection), requests permissions to control phone calls and block SMS messages. By impersonating law enforcement.
The threat actor’s financial fraud strategy involves masquerading as an official authority, providing a fake legal case number and urging victims to input sensitive information. Once trust is established, victims are directed to download a next-stage payload under the guise of investigating bank transactions. The app supports various banking institutions, enabling the theft of personal details, including payment card information.
Relevancy & Insights:
With an alarming trend, threat actors are increasingly directing their efforts towards the banking sector, aiming to generate substantial financial losses. This shift highlights a growing sophistication in cyber threats, emphasizing the need for enhanced cybersecurity measures within the financial industry. Organizations must proactively strengthen their defences to treat these targeted attacks and safeguard sensitive financial information. The evolving landscape underscores the importance of staying vigilant, investing in cutting-edge cybersecurity technologies, and fostering collaboration across the financial sector to counteract emerging threats effectively.
ETLM Assessment:
In the current cybersecurity landscape, threat groups are employing advanced tactics, as seen in recent attacks on China using malicious APKs disguised as “Security Protection.” This threat extends beyond regional boundaries, raising concerns about potential cross-border proliferation. With a focus on financial losses and data theft, these attackers may revisit with upgraded malware and new features, employing social engineering for increased impact. The evolving nature of this external threat underscores the importance of global cooperation in implementing proactive cybersecurity measures and sharing threat intelligence to effectively thwart these malicious activities.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Paraguay’s largest telecommunications company targeted by a cyber attack
Tigo; Paraguay’s largest telecommunications company, was hit by a ransomware attack early January. The attack, launched by the ransomware gang; BlackHunt, encrypted around three hundred servers maintained by the company. The attack reportedly affected several of Tigo’s customers, including several government agencies, and the Paraguayan Army’s cybersecurity team called on organizations in the country to work to harden their own networks and said that the attack was having a significant impact on the country’s economy. The director of Paraguay’s main civilian cybersecurity agency (CERT-PY) said that he hoped that Tigo was working with the FBI and U.S. National Security Agency on the hack, but that Tigo had been very secretive about its response to the incident. Tigo issued a statement denying the scope of the disruption, saying that “outside of the specific services of the corporate segment cited, no internet, phone or wallet services have been affected.”
ETLM Assessment:
At the time of writing, the most probable attacker seems to be the opportunistic financially motivated group; BlackHunt. However, Paraguay is not without some complicated relations. Hezbollah; a Lebanese political party and militant group (designated a terrorist organization by many countries), and a transnational criminal organization, has been long operating in the country, thanks to its long-standing and well-documented partnership with Latin American drug cartels. A focal point of Hezbollah operations in the Western Hemisphere is the Tri-Border Area of Argentina, Brazil, and Paraguay; a sanctuary for all sorts of organized crime. Numerous terrorism financing, money laundering, and drug trafficking operations, which include Hezbollah- aligned Lebanese nationals operate in the area, often on the Paraguay side of the border, because Paraguay has been the most reluctant to recognize and address the problem. In times of heightened tension in the Middle East, this might have attracted attention of a wide variety of actors opposing Iran, since Hezbollah is directly controlled from Tehran.
China claims it cracked Apple’s AirDrop Encryption
A Chinese cybersecurity research agency, Wangshen Dongjian, associated with the Beijing Municipal Bureau of Justice says that it managed to crack the encryption of Apple’s AirDrop file sharing function, allowing authorities to identify the phone numbers and emails associated with devices sharing content via AirDrop. AirDrop was frequently used in the 2019 pro-democracy rallies in Hong Kong and to spread photographs of a protestor in Beijing brandishing a sign labelling President Xi Jinping a “despotic dictator.” AirDrop has been an important tool for demonstrators in China and Hong Kong to share information clandestinely. It has been alleged that authorities have already made advantage of this innovation to track down and apprehend individuals who shared papers during various protests via AirDrop. Apple and the Chinese government have been at odds over AirDrop. In November 2022, Apple controversially changed the AirDrop settings for iPhones in China, limiting the duration of the “everyone” sharing option to ten minutes.
ETLM Assessment:
Within a matter of just a few years, Beijing has copied and successfully used many of Russia’s information warfare techniques, while it developed its own digital authoritarianism mechanisms, through which its cracking on even the potential of domestic dissent. But unlike Russia, the Chinese government believes it has the ability and even the mandate to turn its domestic online surveillance apparatus outward, to disrupt and, perhaps eventually, even control global narratives in real time. Developments like cracking of AirDrop’s encryption are to be absolutely expected from China on every thinkable platform in the future.
The Rhysida Ransomware impacts Lee Spring
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]leespring[.]com), was compromised by Rhysida Ransomware. Lee Spring is a global manufacturer of mechanical springs and related products. Lee Spring carries a line of 25,000+ stock springs and manufacturers custom springs made to customer specifications. The data that has been compromised has not yet surfaced on the leak site, suggesting ongoing negotiations between the affected party and the ransomware group. Within the compromised data are confidential and sensitive details pertaining to the organization. The ransom demanded for the entire dataset is set at 8 BTC.
The following screenshot was observed published on the dark web:
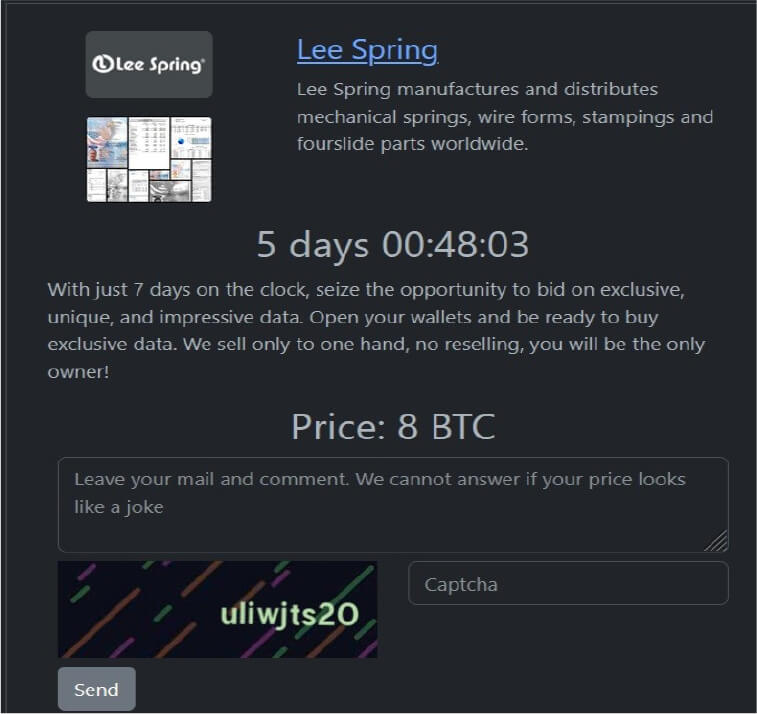
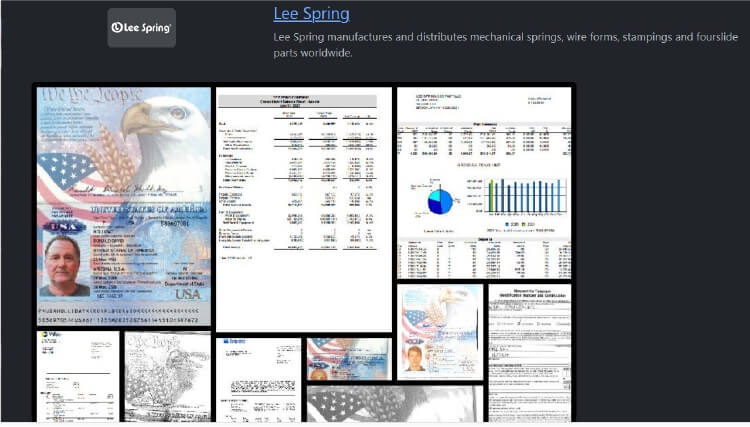
Source: Dark Web
Relevancy & Insights:
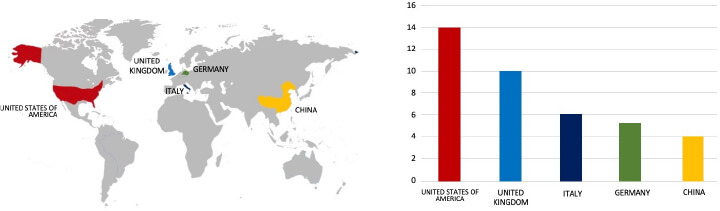
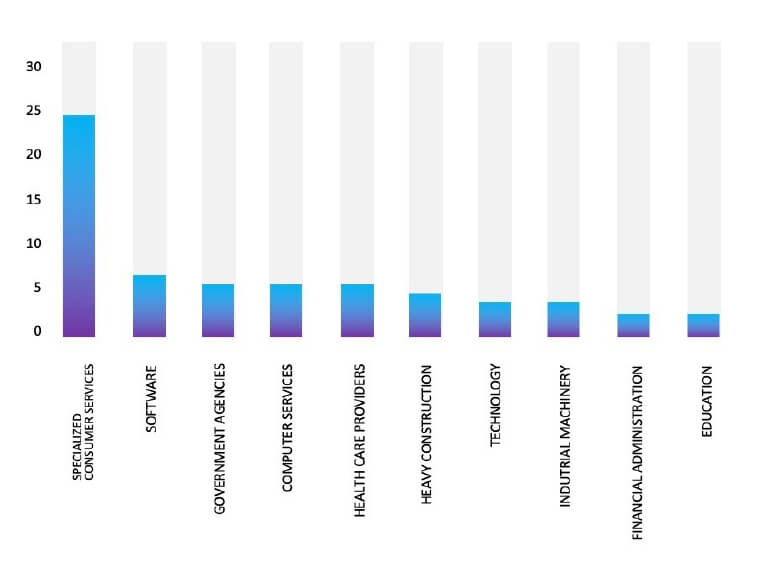
ETLM Assessment:
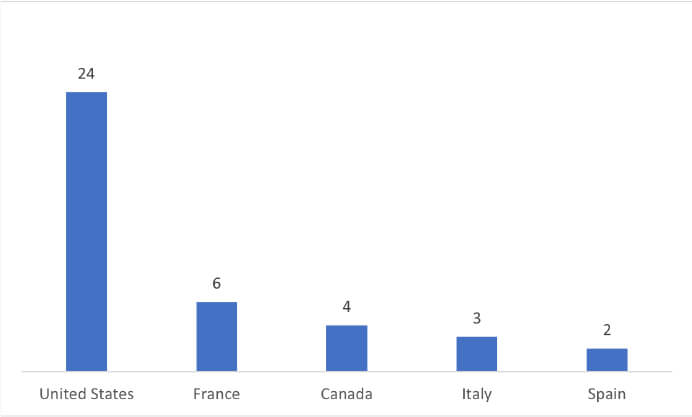
CYFIRMA’s assessment indicates a sustained focus on US-based companies by the Rhysida ransomware, as illustrated in the attached graph. Despite this, recent events, including the Lee Spring attack, underscore the potential vulnerability of other prominent manufacturing entities to similar targeting. It is evident that the threat landscape is dynamic, and organizations across various sectors should remain vigilant to mitigate risks associated with ransomware attacks.
Vulnerability in Apache Shiro
Summary:
The vulnerability allows a remote attacker to perform directory traversal attacks.
Relevancy & Insights:
The vulnerability exists due to input validation error when processing directory traversal sequences.
Impact:
A remote attacker can send a specially crafted HTTP request and read arbitrary files on the system. This can lead to authentication bypass when used together with path rewriting.
Affected Products: https[:]//seclists[.]org/oss-sec/2024/q1/19
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
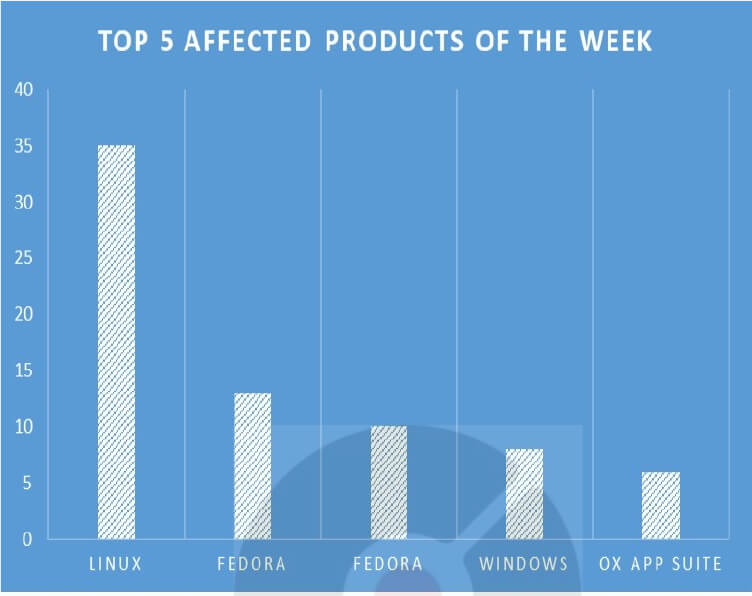
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
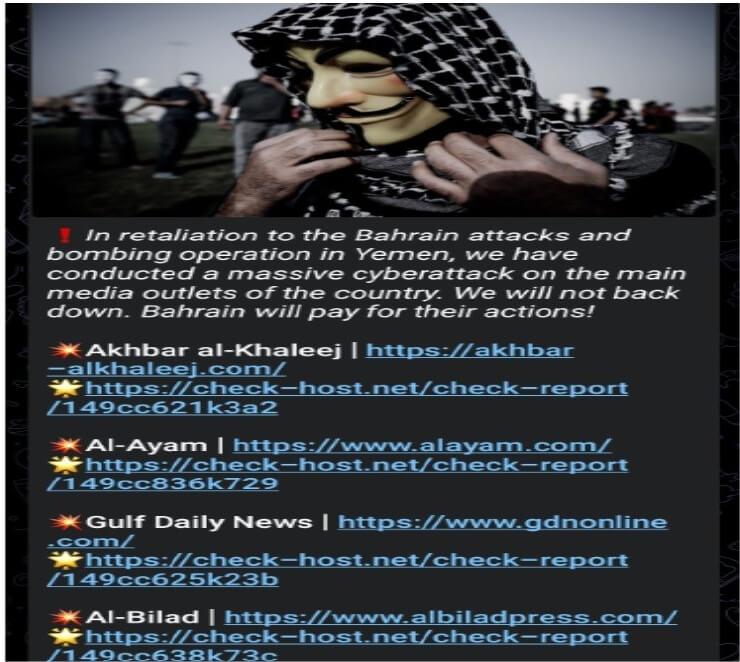
Anonymous Collective Launches Cyberattack on Bahrain
Summary:
We recently observed that the Anonymous Collective has orchestrated an alleged cyberattack on Bahrain, pointing to the country’s support for the US and UK strikes on Yemen. According to the hacker collective, the distributed denial-of-service (DDoS) attack has affected several websites, including prominent media outlets like Akhbar al- Khaleej, Al-Ayam, Gulf Daily News, and Al-Bilad. The Anonymous Collective, in a statement on its dark web channel, declared, “! In retaliation to the Bahrain attacks and bombing operations in Yemen, we have conducted a massive cyberattack on the main media outlets of the country. We will not back down. Bahrain will pay for their actions!” The listed organizations, known for their involvement in the media and news sector, have yet to issue an official statement or response regarding this cyberattack on Bahrain and the involvement of the Anonymous Collective hacker group, leaving the claims unverified.
Relevancy & Insights:
Anonymous Collective is a well-known group of hacktivists. Recently, the Anonymous Collective claimed responsibility for a cyberattack on Cosmote; Greece’s largest mobile network operator. Additionally, they orchestrated a Distributed Denial of Service (DDoS) attack on Cairo International Airport, citing motivations related to Egypt’s perceived support for Israel in the Gaza conflict.
ETLM Assessment:
The hacktivist group Anonymous Collective has reportedly targeted Bahrain by executing a distributed denial-of-service (DDoS) cyberattack. The attack is purportedly motivated by Bahrain’s alleged support for US and UK airstrikes on Yemen. According to CYFIRMA’s assessment, there is a likelihood that Anonymous Collective will persist in its campaign of DDoS attacks on Bahrain and other countries’ organizations supporting the mentioned airstrikes. The aim is to induce reputational damage and operational disruptions within these entities.
Qonstanta Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Qonstanta, {www[.]qonstanta[.]id}. Qonstanta is one of the study guidance in Indonesia, with support from a management team and tutors, who have proven experience in guiding many students to enter the FA major. The compromised data encompasses a variety of sensitive information, including names, telephone numbers, email addresses, usernames, passwords, addresses, class details, National Student Identification Numbers (NISN), bank names, genders, account numbers, department affiliations, dates, and more. The entirety of compromised data amounts to 4.17 gigabytes.

Source: Underground forums
Relevancy & Insights:
Cybercriminals with financial motivations frequently exploit exposed and vulnerable systems and applications. A significant number of these individuals engage in covert discussions within online forums dedicated to illegal activities, where they trade stolen digital assets. In contrast to certain financially driven groups such as ransomware or extortion gangs that boast about their exploits, these opportunistic attackers choose a more discreet approach. They capitalize on unpatched systems and vulnerabilities in applications to illicitly access and abscond with valuable data. Following the theft, they promote the pilfered data for sale within clandestine forums, where it may be further circulated and repurposed by other malicious actors in their nefarious endeavors.
ETLM Assessment:
MastaBeen; an emerging threat actor based in Indonesia, focuses on targeting organizations within the country. According to CYFIRMA’s assessment, organizations in Indonesia that lack adequate security measures are deemed potential targets for this particular threat actor.
CYFIRMA Research team observed a potential data leak related to McDonald’s Corporation, {www[.]mcdonalds[.]com}. McDonald’s is the world’s leading global food service retailer with over 36,000 locations in over 100 countries. More than 90% of McDonald’s restaurants worldwide are owned and operated by independent local businessmen and women. The data available for purchase comprises internal tools, names, and email addresses, along with bank logs and additional sensitive information.
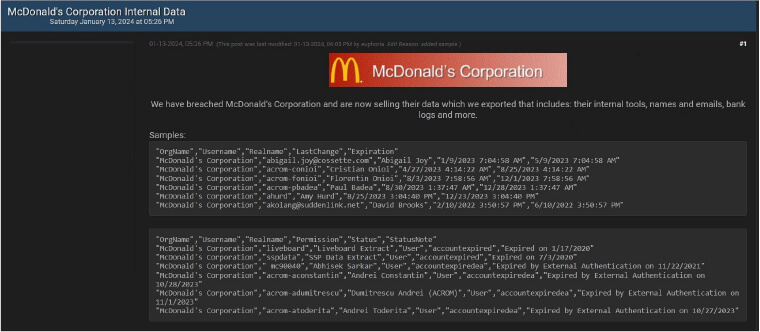
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS