



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Dzen ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Dzen ransomware
Researchers discovered Dzen, a ransomware from the Phobos family, in the wild in early April 2024. Dzen encrypts files, changes their names, and shows two ransom notes named “info.txt” and “info.hta”. It adds the victim’s ID, email address, and “.dzen” to the end of encrypted filenames.
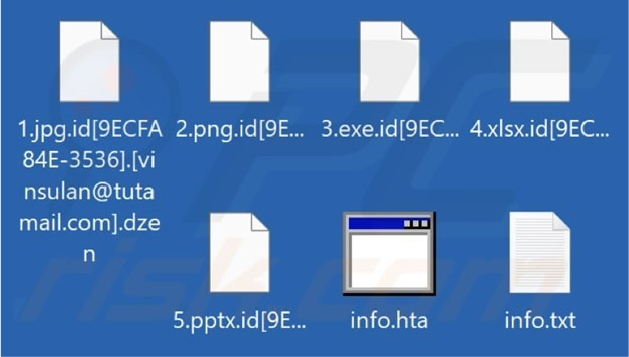
Screenshot of files encrypted by Dzen ransomware (Source: Surface Web)
The Dzen ransomware presents a complex threat by not just encrypting files but also disabling firewalls, making systems vulnerable to malicious actions. Furthermore, it actively removes Volume Shadow Copies, preventing potential file recovery.
Moreover, Dzen includes functionalities to collect location data and use persistence mechanisms, selectively avoiding specific areas in its operations.
The ransom note notifies the victim that their data has been encrypted and can only be unlocked with the perpetrators’ software. It warns against independent decryption attempts, stressing the risk of permanent data loss.
Furthermore, it advises against involving intermediary or recovery companies. The criminals promise confidentiality and pledge to delete all downloaded data after the ransom is paid. They assure not to sell or exploit the victim’s personal data for future attacks.
However, they set a two-day deadline for contact, threatening data sharing with interested parties if missed. Contact details are provided via two email addresses, with instructions to include a specific ID in the message title.
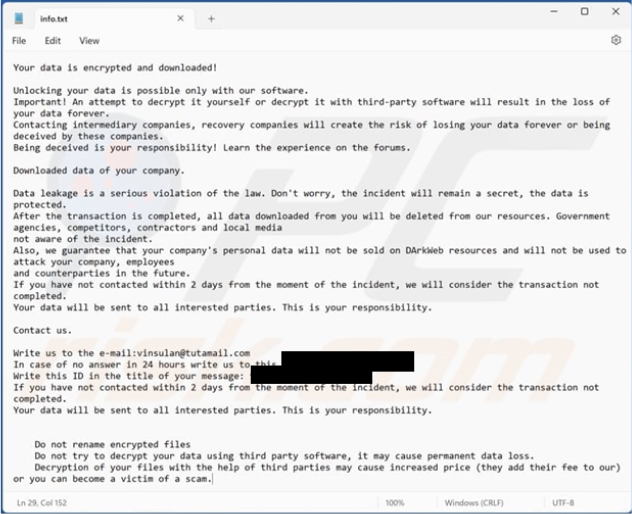
Screenshot of Dzen’s text file (“info.txt”) (Source: Surface Web)
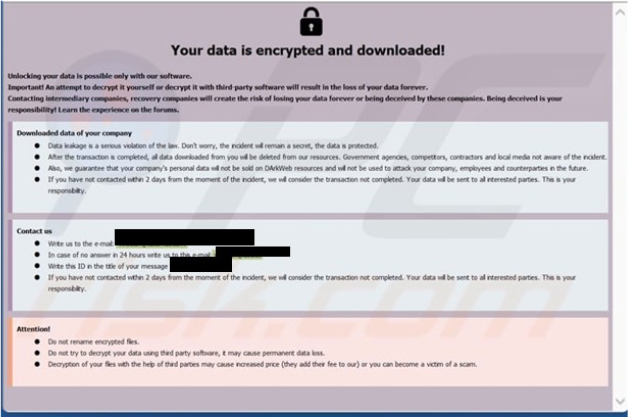
Screenshot of Dzen’s pop-up window (“info.hta”) (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job |
| T1059: Command and Scripting Interpreter | ||
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1134: Access Token Manipulation | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1134: Access Token Manipulation | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1016: System Network Configuration Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System |
| T1056: Input Capture | ||
| 9 | TA0011: Command and Control | T1105: Ingress Tool Transfer |
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Relevancy and Insights:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Paramet ers\FirewallPolicy\PublicProfile\EnableFirewall. It changes the DWORD values to 0x00000000, effectively turning off the firewall protection.
ETLM Assessment:
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Espionage, Data theft, Remote Access
Threat Actor: Virtual Invaders
Target Technology: Android Applications
Target Geographies: South Asia (India and Pakistan)
Campaign: eXotic Visit
Active Malware of the Week
This week “XploitSPY” is trending
Summary
Researchers have identified an ongoing espionage campaign named eXotic Visit targeting Android users. This campaign began in late 2021 and primarily masquerades as messaging apps, distributing these apps via dedicated websites and briefly through the Google Play store, where they had low installation numbers before being removed. The primary targets of this campaign appear to be Android users in Pakistan and India. Researchers have been unable to identify the specific threat group behind this activity, so they internally refer to them as “Virtual Invaders” for tracking purposes.
Researchers have identified that the apps in this campaign, which pose as messaging services, actually contain a customized version of the open-source Android RAT known as XploitSPY, harboring malicious code. This malware allows them to extract contact lists, files, GPS location, and file names from directories associated with the camera, downloads, and messaging apps such as Telegram and WhatsApp.
XploitSPY
XploitSPY, derived from the open-source Android RAT L3MON (which was removed from GitHub by its author), incorporates features inspired by another RAT called AhMyth, expanding its capabilities. This malware is equipped with extensive data-stealing functionalities and has been detected infiltrating devices packaged with seemingly legitimate applications. To further evade detection, XploitSPY utilizes a native library commonly employed in Android app development. Unlike its typical usage to enhance performance and system access, this library is repurposed to conceal critical information like the addresses of command-and-control (C&C) servers. This tactic aims to thwart security tools and complicates the analysis of the app. Below are the capabilities of XploitSPY:
Malicious App Campaign Timeline: eXotic Visit
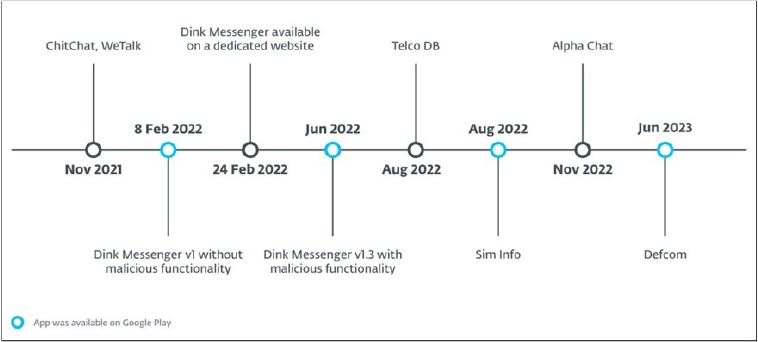
Fig: Timeline of the first appearance of XploitSPY-riddled apps that are part of the malicious campaign
Attack Method
The eXotic Visit campaign gains initial access to devices by enticing victims to install fake but functional apps. Malicious apps like ChitChat and WeTalk were distributed through dedicated websites and GitHub (https[:]//github[.]com/Sojal87/). Additionally, LearnSindhi.apk, SafeChat.apk, and wechat.apk were hosted on the same GitHub account, although their distribution methods are unknown. These apps were no longer available for download from GitHub as of July 2023. New malicious apps associated with eXotic Visit, containing variants of XploitSPY code, have since appeared on the same GitHub account. The Dink Messenger and Alpha Chat apps were hosted on letchitchat[.]info, enticing victims to download and install them. Apps like Dink Messenger, Sim Info, and Defcom were once available on Google Play but were removed by Google.
Toolset
All analyzed apps associated with the eXotic Visit campaign contain customized versions of the XploitSPY malware code sourced from GitHub. From its inception in 2021 to the latest version introduced in July 2023, ongoing development efforts by Virtual Invaders have been observed. These efforts include:
One specific analysis focused on the Defcom app, previously available on Google Play, which integrates the XploitSPY code alongside a unique chat feature likely developed by Virtual Invaders. Upon installation, Defcom prompts users to create an account while simultaneously attempting to retrieve the device’s location details via api.ipgeolocation.io. This information is then forwarded to a Firebase server, which serves as the messaging component’s server.
Defcom incorporates a native library named defcome-lib.so, typical in Android app development for optimizing performance and accessing system features. This native library, likely written in C or C++, is used to conceal sensitive information, such as Command and Control (C&C) server details, from static app analysis. The library employs methods that return base64-encoded strings, which are decoded by the malicious code during runtime. Although this technique is not highly sophisticated, it effectively prevents static analysis tools from extracting C&C server information.
Malicious Android Apps Targeting South Asian Users
Researchers have identified that the malicious apps developed by the eXotic Visit campaign were distributed through Google Play and dedicated websites, primarily targeting users in Pakistan and India. Four specific apps— Sim Info, Telco DB (com.infinitetechnology.telcodb), Shah jee Foods, and Specialist Hospital—were key targets. Sim Info and Telco DB allow users to search for SIM owner information for Pakistani mobile numbers via the dbcenteruk.com online service.
On July 8th, 2022, an app named Shah jee Foods, uploaded from Pakistan to VirusTotal, displayed a food ordering website for the Pakistan region (foodpanda.pk) upon startup. The Specialist Hospital app, found on GitHub, masquerades as an app for Specialist Hospital in India (specialisthospital.in) and requests necessary permissions before prompting users to install the legitimate app from Google Play. Although over 380 compromised accounts were identified within these apps, their geolocation remains unknown. The discovery of shared insecure code across ten apps strongly suggests they were developed by the same threat actor.
Device Control Commands
Commands for the compromised device are received from the Command and Control (C&C) server as string values. The commands include:
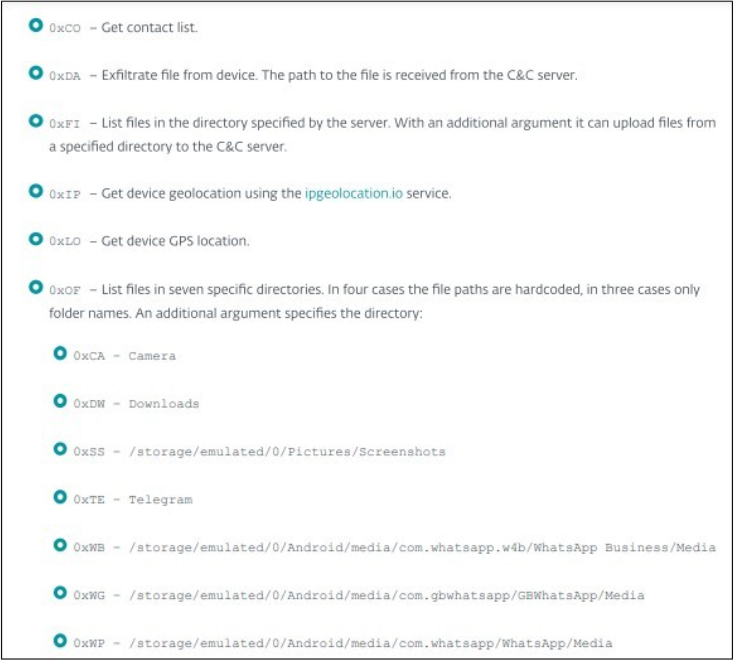
GB WhatsApp is an unofficial clone of WhatsApp that offers extra features and is widely popular. However, it’s not on Google Play and is typically found on download sites, where versions are often infected with malware. Despite these security risks, GB WhatsApp has a significant user base in countries like India.
Network Infrastructure
Virtual Invaders utilize ngrok as their Command and Control (C&C) server infrastructure. Ngrok is a cross-platform tool used by developers to expose local development servers to the internet. It creates a tunnel connecting local machines to ngrok servers, enabling users (in this case, attackers) to reserve specific IP addresses or redirect victims to the attackers’ domain on specific ports.
INSIGHTS
ETLM ASSESSMENT
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
LightSpy: A State-Sponsored Threat Resurfaces for Espionage in Southern Asia
Summary:
The sophisticated group of native Chinese speakers believed to be behind LightSpy are suspected to have ties to state-sponsored activity, potentially working for the Chinese government. This inference is supported by infrastructure and functionality overlaps observed between the LightSpy malware and that used by MISSION2025, also known as APT41, a Chinese state-sponsored threat actor. These connections raise significant concerns about the geopolitical implications and motives behind the LightSpy campaign. The primary objective of the LightSpy campaign is espionage, with a focus on exfiltrating sensitive information from high-profile targets such as politicians, CEOs, journalists, activists, and diplomats. This includes personal data, financial information, and location tracking.
LightSpy utilizes advanced mobile spyware techniques, employing a modular framework with capabilities such as file theft, audio recording, data harvesting, and system access. The attack involves a multi-stage process, likely initiated through compromised news websites. The malware primarily targets iOS devices, particularly Apple iPhones and iPads. It possesses modules designed to exfiltrate data from popular messenger applications like QQ, WeChat, and Telegram, as well as accessing device information, browser history, and media files.
The campaign primarily targets individuals in Southern Asia. Previous campaigns have been associated with escalating political tensions, such as those in Hong Kong. The targets of LightSpy are diverse, including politicians, CEOs, journalists, activists, and diplomats. This suggests that a wide range of industries and sectors are vulnerable to this espionage campaign.
The resurgence of LightSpy poses a significant threat due to its sophisticated modular capabilities and potential geopolitical implications. Victims risk exposure to personal and sensitive information, leading to potential security breaches, reputational damage, and compromise of confidential data. The ongoing nature of these attacks underscores the need for heightened cybersecurity measures and vigilance among high-profile individuals and organizations.
Relevancy & Insights:
The suspected state-sponsored activity behind LightSpy, coupled with past infrastructure and functionality overlaps with MISSION2025 aka APT41suggests potential Chinese government involvement. This threat has previously targeted IT services, telecom, and healthcare industries, with a focus on facilitating surveillance operations and cooperating in espionage campaigns, including hacker-for-hire activities. The historical impact analysis within Telecommunications & Media underscores the severity of the threat, particularly affecting Telecommunication devices and services, as well as Marketing and Advertising organizations. The cyber espionage campaign in South Asia, deploying LightSpy, posed significant risks, showcasing an agile approach to surveillance framework deployment in the region. This highlights the pressing need for heightened cybersecurity measures and international cooperation to effectively mitigate the threat.
ETLM Assessment:
The threat actor behind LightSpy, suspected to be a sophisticated group of native Chinese speakers possibly working for the Chinese government, poses a significant challenge in the external threat landscape. With reported infrastructure and functionality overlaps with the notorious APT41 group, there are concerning implications for industries targeted by both entities. While the initial focus of the LightSpy campaign has been on IT services, telecommunications, healthcare, and media, organizations must be wary of potential geographical expansions. Despite starting predominantly in Southern Asia, particularly India, the threat actor’s motives could drive them to widen their scope to other strategic targets in the region. Therefore, proactive measures and heightened cybersecurity efforts are imperative for organizations globally to mitigate the risks posed by this dynamic threat landscape.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Ukraine-linked Hackers Targeting Russian Infrastructure Company
Researchers have recently published findings on a strain of ICS malware dubbed “Fuxnet” which was reportedly deployed by Ukraine-linked hackers against a Moscow- based company that manages underground water and communications infrastructure called Moscollector. The “Blackjack” hacking group claimed responsibility for the attack and said it was able to damage 87,000 remote sensors and IoT devices used by the utility company. This claim is deemed to be exaggerated by researchers, but the malware does appear to have bricked at least 500 sensor gateways. If the gateways were indeed damaged, the repairs could be extensive given that these devices are spread out geographically across Moscow and its suburbs and must be either replaced or their firmware must be individually reflashed.
ETLM Assessment:
Russia has been attempting to destabilize Ukrainian energy infrastructure in a massive kinetic campaign for the last couple of months with the apparent aim of destroying the Ukrainian grid and power sources beyond repair. After much deliberation and over the well-publicized grumbling by the Western partners, Ukraine is now trying to retaliate in kind, targeting Russian oil refineries and export infrastructure with further cyber-attacks on critical infrastructure in Russia, trying to deter Russia from further attacks on its infrastructure by punishing retaliation. So far there are no signs that the Kremlin got the memo, and we are likely to see further escalation of cyberattacks on critical infrastructure, which may very well spread beyond the two warring nations.
Heritage Foundation Discloses Cyberattack
The Heritage Foundation, a Washinton, DC-based think tank focused on conservative policy, sustained a cyberattack according to media reports. A Heritage Foundation official told the media that a nation-state actor was likely responsible, but the nature of the attack hasn’t been disclosed. Nation-state actors frequently target think tanks for cyberespionage purposes, and the Heritage Foundation itself was hit by a separate breach in 2015.
ETLM Assessment:
Influential think tanks are attractive targets for intelligence gathering for all government-sponsored actors, as they are perceived to be close to policy-making circles and are thus in a position to influence the intelligence and policy communities. This campaign should be regarded as a classic case of state-driven espionage with many similar ones possibly underway. The Heritage Foundation is perceived by many analysts as the future policy-making center in the case Donald Trump wins the next presidential elections in the United States and gaining insights of the inner workings on the institute could put all governments but especially North Korea, Russia, and China “in the loop” of the highest decision-making circles in the US with profound impact on policymaking. Think tanks typically do not have the cyber defense resources and established best practices like government offices do and are thus the soft underbelly for counterintelligence, which is especially the case with the Heritage Foundation. The organization was singled out, but Chinese and other actors see it as the place from which the upcoming administration of President Trump would draw many loyal cadres that would implement policies envisioned by the think tank.
The DragonForce Ransomware Impacts The MajuHome Concept
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; (www[.]majuhome [.]com[.]my), was compromised by the DragonForce Ransomware. MajuHome Concept has been one of the favourite brands of Malaysian consumers when it comes to furniture solutions that are of good quality and come with the latest and trendy designs. The compromised data includes confidential and sensitive information crucial to the organization’s operations. The total size of the compromised data stands at 6.84 gigabytes.
The following screenshot was observed published on the dark web:
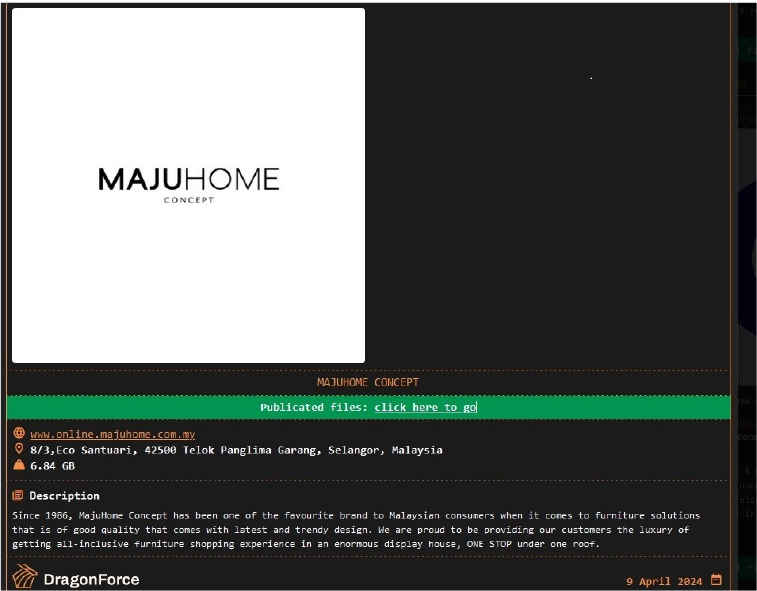
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
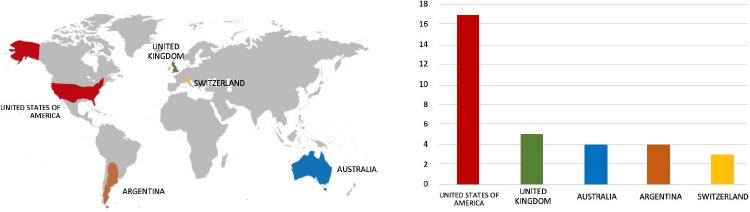
Based on the available information, CYFIRMA’s assessment indicates that DragonForce Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on MajuHome Concept, a prominent Manufacturing company located in Malaysia, underscores the extensive threat posed by this particular ransomware strain in the Southeast Asia region.
The Hunters International Ransomware impacts the Chicony Electronics
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; (www[.]chicony[.]com), was compromised by the Hunters International Ransomware. Chicony Electronics Co., Ltd. is a Taiwan-based multinational electronics manufacturer. Its product lineup includes input devices, power supplies, and digital image products. Chicony Electronics offers desktop keyboards, mobile keyboards, digital cameras, personal computer cameras, integrated webcams, and digital video cameras. It has also been a well-known manufacturer of motherboards for personal computers and notebooks. Chicony Electronics has operations in Australia, Brazil, Canada, China, the Czech Republic, Germany, Ireland, Japan, Mexico, the Philippines, Singapore, Thailand, Taiwan, the United Kingdom, and the United States. The compromised data holds confidential and sensitive information pertaining to the organization. In total, the compromised data amounts to 1.2 terabytes.
The following screenshot was observed published on the dark web:
Source: Dark Web
Relevancy & Insights:
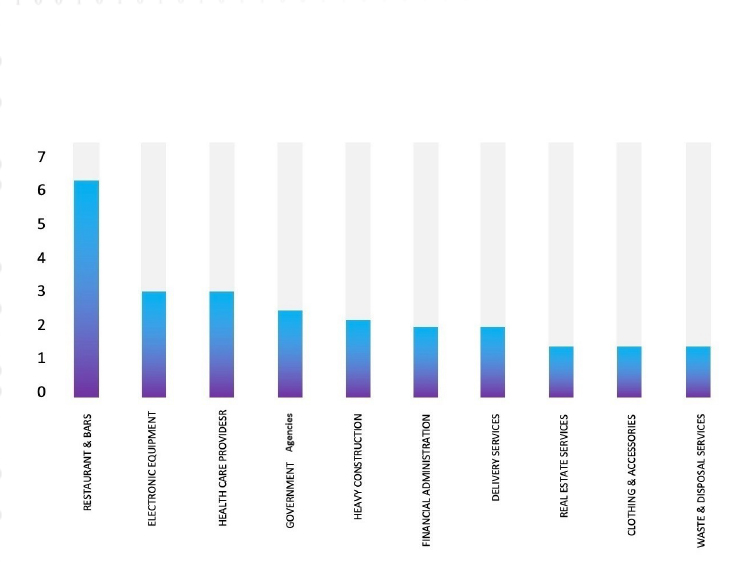
The Top 10 Industries, most affected by Hunters International Ransomware from 1 Jan 2023 to 17 April 2024 are as follows: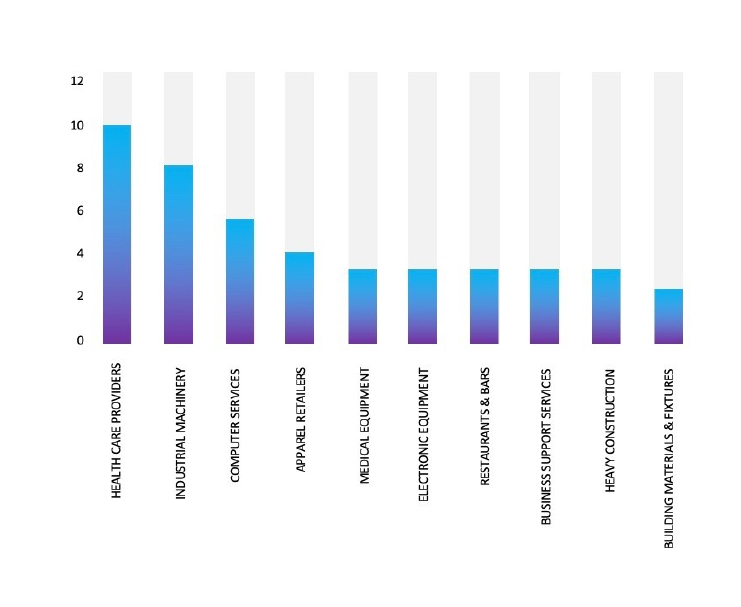
ETLM Assessment:
Based on CYFIRMA’s assessment, there is a persistent targeting of global companies by the Hunters International Ransomware, as depicted in the accompanying graph. However, recent incidents, such as the attack on Chicony Electronics, highlight the susceptibility of other prominent Manufacturing entities to similar targeting. These events emphasize the dynamic nature of the threat landscape, necessitating heightened vigilance among organizations across different sectors to mitigate the risks associated with ransomware attacks. The attack on Chicony Electronics also highlights ransomware groups’ interest in Asian organizations that are financially strong in the region with exploitable vulnerabilities.
Vulnerability in PHP
Command Summary:
The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation when processing array-ish $command parameter of proc_open. A remote attacker can pass a specially crafted input to the application and execute arbitrary OS commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products:
https[:]//www[.]php[.]net/ChangeLog-8.php
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
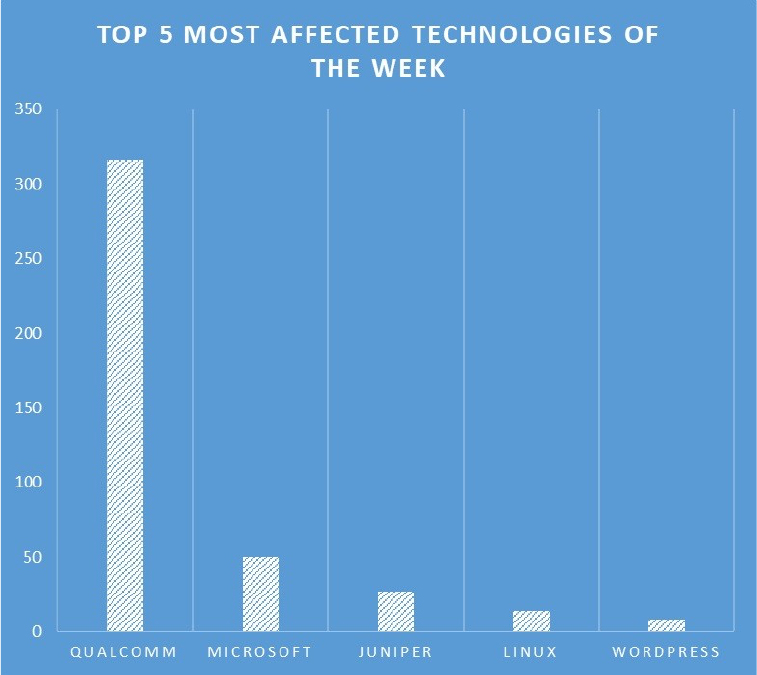
ETLM Assessment:
PHP, extensively used in web development, server-side scripting, and automation, has the potential to impact diverse industries such as technology, e-commerce, finance, healthcare, and education. Its broad application range extends beyond these sectors, potentially disrupting systems and exposing them to security threats across the globe.
8Base Ransomware attacked and Published data of Inno-soft Info Systems Pte Ltd
Summary:
Recently we observed that 8Base Ransomware attacked and Published data of Inno- soft Info Systems Pte Ltd on its dark web website. Inno-soft Info Systems Pte Ltd (www [.]inno-soft[.]com[.]sg) is a prominent technology company based in Singapore, renowned for its innovative solutions and cutting-edge services. Established with a vision to revolutionize the technological landscape, Inno-soft has been a key player in Singapore’s thriving tech industry. The breached data encompasses a broad spectrum of sensitive information, comprising invoices, receipts, accounting documents, personal data, certificates, employment contracts, a significant volume of confidential information, confidentiality agreements, personal files, and various other critical documents.
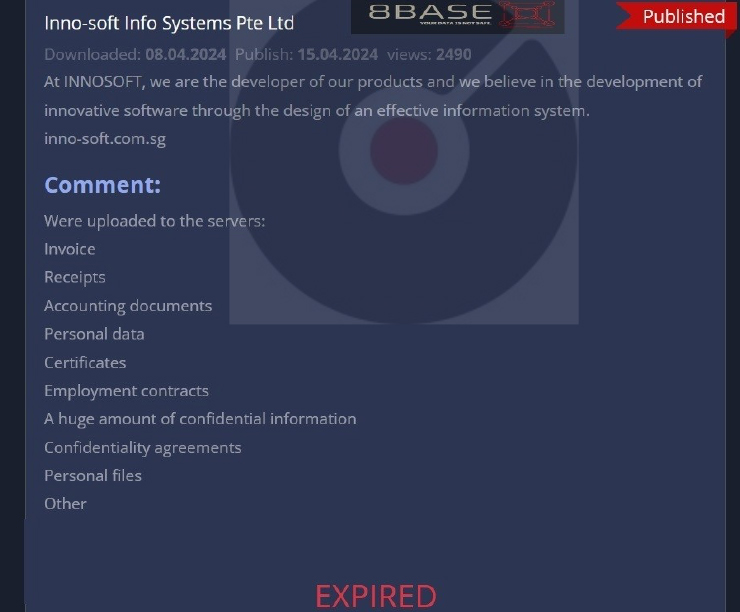
Source: Dark Web
ETLM Assessment:
The 8Base ransomware group first emerged in March 2022 and swiftly gained notoriety, exhibiting a notable surge in activity throughout 2023 and early 2024. Though their ransom demands remain undisclosed, they employ double extortion tactics, leveraging exfiltrated data for additional leverage. Operating with remarkable sophistication, 8Base employs advanced security evasion techniques and primarily targets Windows systems, with a particular focus on sectors including business services, manufacturing, finance, and information technology. Continuous assessments conducted by CYFIRMA indicate that 8Base ransomware has set its sights on Southeast Asian Nations, driven by a relentless pursuit of substantial financial gains through ransomware operations.
TELKOM data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to TELKOM,
{www[.]telkom[.]co[.]id} in an underground forum. PT Telkom Indonesia (Persero) Tbk (Telkom) is a state-owned information and communications technology enterprise and telecommunications network in Indonesia. The dataset available for sale contains personal information such as names, profile photos, status updates, comprehensive data, birthplaces, and other confidential and sensitive details. The asking price for this data is $345.
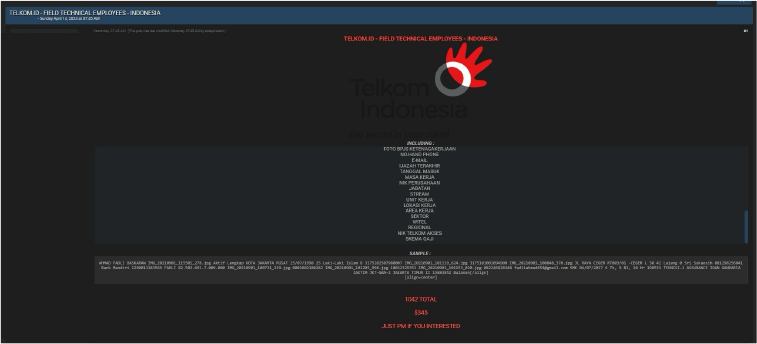
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as ‘Sedapmalam’ poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by ‘Sedapmalam’ typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
MyRepublic Indonesia data advertised on a Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to MyRepublic Indonesia, {www[.]myrepublic[.]co[.]id} in an underground forum. MyRepublic is an ISP / Mobile carrier based in Singapore. MyRepublic is one of the fastest growing telecom operators in the Asia-Pacific. MyRepublic has operations across Singapore, Indonesia, New Zealand, and Australia, and is set to expand further into the region. A threat actor has successfully breached the Indonesian subsidiary of MyRepublic, gaining unauthorized access to the entire customer database. The compromised data includes sensitive information such as names, email addresses, phone numbers, billing addresses, and NIK (National Identification Numbers), which are unique identifiers for Indonesian citizens, akin to driver’s licenses or ID numbers in the USA. This valuable trove of personal information is now being offered for sale at the price of $2,500.
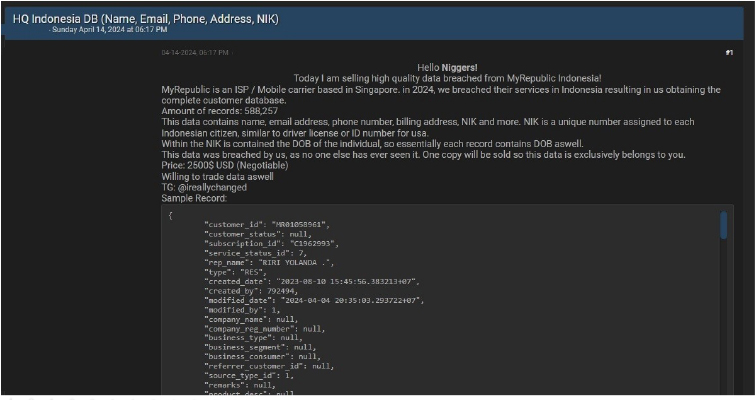
Source: Underground Forums
ETLM Assessment:
The emergence of a threat actor, identified as “abyss0,” has brought to light concerning financial motives, as evidenced by the active dissemination of data from MyRepublic Indonesia in an underground forum. This data breach includes a variety of sensitive information, such as personally identifiable information (PII), financial records, and other confidential data. This breach not only jeopardizes the security and integrity of MyRepublic Indonesia but also poses a significant risk to the affected individuals whose data has been compromised. It emphasizes the urgent need for organizations to bolster their cybersecurity defenses and implement robust measures to safeguard sensitive information against such malicious threats.
CYFIRMA Research team observed a potential data leak related to Space-Eyes, {www[.]Space-Eyes[.]com}. Space-Eyes provides on-demand tasking to a Synthetic Aperture Radar satellite. Its collections across all weather and lighting conditions are integrated with contextual data and analysed automatically for threats in the maritime domain. Space-eyes.com suffered a data breach that exposed highly confidential documents related to their services for national security within the US government.
Space-eyes customers include:
US Department of Justice
US Department of Homeland Security US Navy / Army / Air Force
Defence Science and Technology Agency US Space Force
National Geospatial-Intelligence Agency.
A threat actor group known as CyberNiggers is attributed to the data breach at Space- eyes.
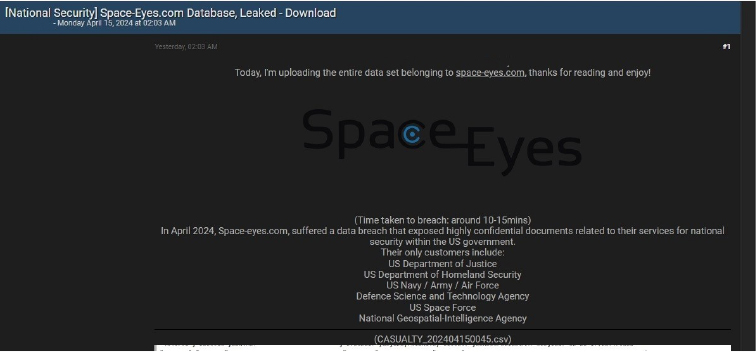
Source: Underground forums
ETLM Assessment:
CyberNiggers threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
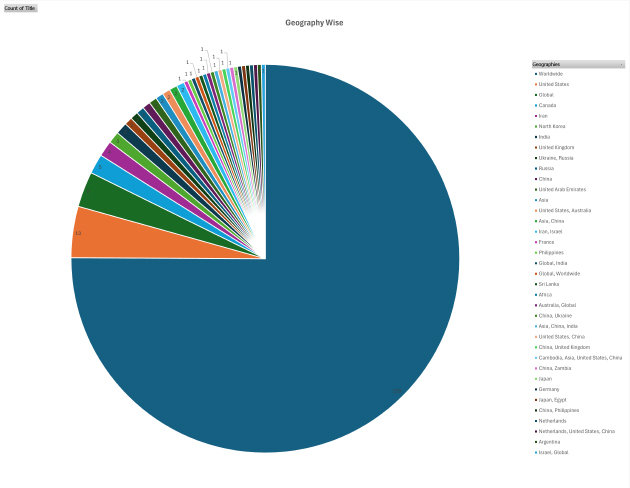
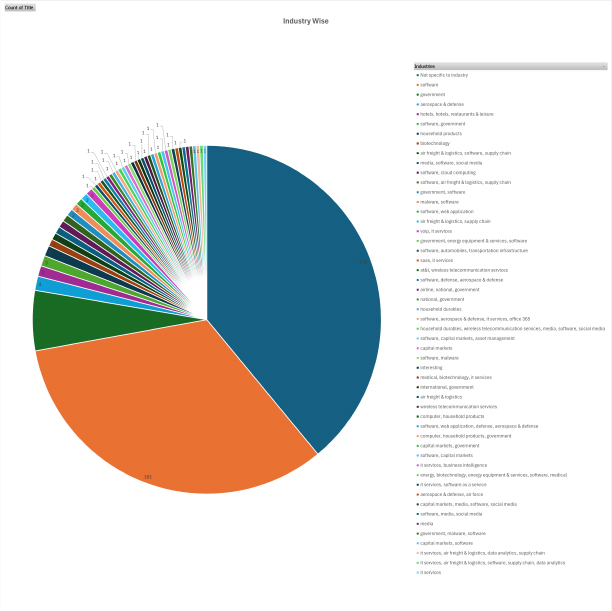
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.