



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Geography: Israel.
CYFIRMA Research and Advisory Team has found ransomware-as-a-service known as GhostLocker while monitoring various underground forums as part of our Threat Discovery Process.
A new Ransomware-as-a-Service (RaaS) program named GhostLocker has been introduced by the hacktivists known as GhostSec.
The threat actor group is promoting their Ransomware-as-a-Service (RaaS) through a Telegram channel, where they initially offer it at a price of $999. If the offer is missed, the price is incrementally raised to $4999. Currently, this Telegram channel has approximately 688 members.
The options are presented in the following manner to give a degree of customization and flexibility to the individuals or groups who are using the service to distribute ransomware:
The following options are presented as checkboxes:
Stage 1 of the GhostLocker ransomware is a compiled x64 binary created with the Python compiler Nuitka. Nuitka optimises and translates Python code into machine code, enhancing performance and making it resistant to reverse engineering. Stage 1 drops various files in a folder in the Windows temporary directory, including .pyd and .dll files, along with Stage 2, which shares the same name.
Stage 1 launches Stage 2 as a child process using the CreateProcess API, with Stage 2 also compiled using Nuitka. The Python script within Stage 2 contains functions and activities. These activities involve copying itself to the Windows startup directory, downloading a watchdog, incrementing launches, generating a symmetric encryption key with Fernet, creating a random ID, sending victim data to a specified URL, terminating services, retrieving the user’s login name, and enumerating directories to encrypt files. Encrypted files receive a “.ghost” extension.
The ransomware utilizes 128-bit AES-CBC encryption implemented through Fernet. It begins by generating a key using Fernet.generatekey(), which is then sent to the hacker via sendDB(). This key is employed to encrypt the data, producing cipher text. The resulting encrypted data, known as a Fernet token, is URL-safe and base64-encoded.
Ransom notes are deposited in all the folders that have been targeted, with the file name “readme.html”.
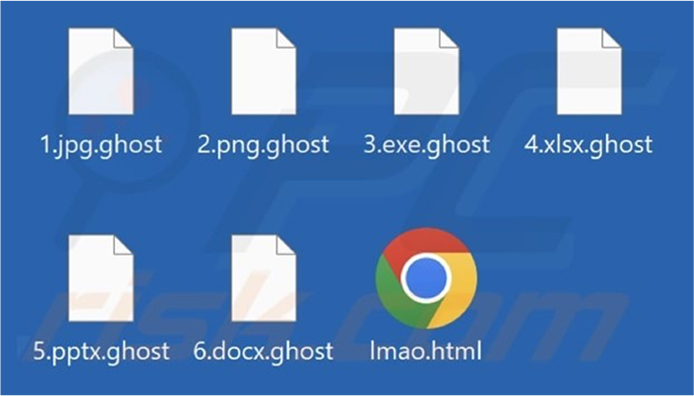
Screenshot of the files encrypted by GhostLocker ransomware (Source: Surface web)
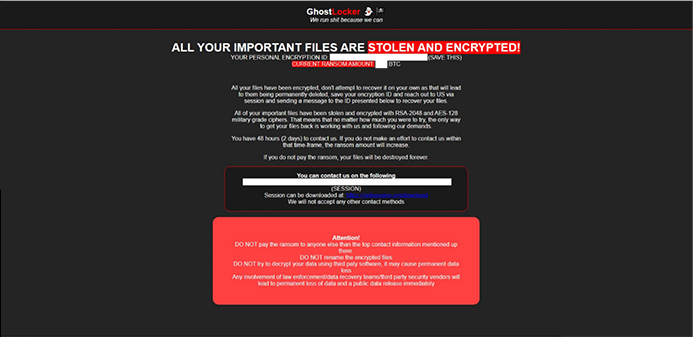
Ransom note by GhostLocker ransomware (Source: Surface web)
About the Threat Actor:
GhostSec originated as a hacktivist group branching from Anonymous. Initially focused on counterterrorism, they rose to prominence after the 2015 Charlie Hebdo shooting and the emergence of ISIS. Unlike Anonymous, GhostSec claims to collaborate closely with law enforcement and intelligence agencies, emphasizing their dedication to tracking and disrupting ISIS-related online propaganda.
GhostSec made headlines with its cyber activities. Very recent activities include: In April 2023, it targeted the water pump industry; May saw a data leak from unauthorized access to PLC devices. October brought an assault on water pumps coupled with the GhostLocker ransomware. November witnessed a sustained cyber offensive on Israel, purportedly in response to alleged war crimes.
Some of the countries targeted by these hacking groups are as follows,
| Russia | Columbia | Israel |
| Iran | Nigeria | South Africa |
| Pakistan | United Arab Emirates | Iraq |
| Lebanon | Brazil | France |
| Sudan | Nicaraqua | Myanmar |
| Philippines | Turkic | Canada |
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.006: Indicator Removal: Timestomp | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0007: Discovery | T1046: Network Service Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497.001: Virtualization / Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 6 | TA0009: Collection | T1005: Data from Local System |
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 8 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1496: Resource Hijacking |
Cyfirma Assessment, based on the available information, indicates that GhostLocker ransomware primarily targets the widely used Windows operating system across diverse sectors. The ransomware deploys robust 128-bit AES-CBC encryption via Fernet, rendering file decryption highly challenging for victims. The secure key exchange process, encompassing Fernet.generatekey() and sendDB(), heightens the confidentiality of the encryption key. It is expected that GhostLocker will maintain its technical sophistication and adaptability. Its developers may continue refining evasion techniques and encryption methods, extending the threat beyond Windows to other platforms. Consequently, organizations should bolster their cybersecurity defenses and remain vigilant to effectively counter this evolving menace.
Kindly refer to the IOCs section to exercise controls on your security systems.
title: Stop Windows Service Via Sc.EXE tags:
– attack.impact
– attack.t1489 logsource:
category: process_creation product: windows
detection: selection_img:
– OriginalFileName: ‘sc.exe’
– Image|endswith: ‘\sc.exe’ selection_cli:
CommandLine|contains: ‘ stop ‘ filter_kaspersky:
CommandLine:
– ‘sc stop KSCWebConsoleMessageQueue’ # kaspersky Security Center Web Console double space between sc and stop
– ‘sc stop LGHUBUpdaterService’ # Logitech LGHUB Updater Service User|contains: # covers many language settings
– ‘AUTHORI’
– ‘AUTORI’
condition: all of selection_* and not 1 of filter_*
falsepositives:
– There are many legitimate reasons to stop a service. This rule isn’t looking for any suspicious behaviour in particular. Filter legitimate activity accordingly
level: low
(Source: Surface web)
Type: Information Stealer
Objective: Data exfiltration
Target Technology: Browsers, Windows OS
Target Sectors: Education and Health
Active Malware of the Week
This week “Jupyter” is trending.
In the ever-evolving landscape of cyber threats, the notorious Jupyter Infostealer has resurfaced with persistence. Targeting crucial sectors like Education and Health, this malware is proving to be a formidable adversary. The latest variants employ sophisticated techniques, including PowerShell command modifications and private key signatures, allowing them to masquerade as legitimate files. Over the last two weeks, the number of Jupyter Infostealer infections that researchers have observed has steadily risen, now totalling 26 infections.
Jupyter
Infostealer, (aka Yellow Cockatoo, Solarmarker, or Polazert) emerged in late 2020 and has since undergone continuous evolution to avoid detection. Primarily targeting Chrome, Edge, and Firefox browsers, it employs SEO poisoning and search engine redirects to lure users into downloading malicious files as the initial step in its attack strategy. This malware showcases capabilities such as credential harvesting and encrypted command-and-control communication, enabling the theft of sensitive data.
In the most recent attacks, the threat actor behind Jupyter employed the tactic of signing files with valid certificates, significantly enhancing their ability to avoid detection. The use of multiple certificates in this process instills trust in the malicious files, facilitating initial access to the victim’s machine. Noteworthy recent signers include:

Threat actors actively seek to acquire such certificates, taking advantage of the trust they inspire. Even experienced security analysts may unknowingly place trust in software with these certificates, influenced by their deceptive appearance of authenticity.
Jupyter Infostealer employs different delivery methods typical of many malware strains. It can infiltrate systems through malicious websites, drive-by downloads, or phishing emails. Users might accidentally download Jupyter Infostealer when navigating compromised websites or clicking on deceptive ads. The malware predominantly targets popular web browsers like Firefox, Chrome, and Edge. Once downloaded, the executable is triggered by the user’s browser, initiating the malicious actions of the Infostealer.
Researchers observed that the initial files use different names, crafted to trick users into opening them. Examples include:
The mentioned executables serve as instances of installation files generated by InnoSetup; an open-source compiler employed for crafting installation packages in the Windows operating system. In these recent infections, the common presence of the installer- bundle.exe file is notable, maintaining a consistent hash despite variations in their file names.
While delving into the details, an incident involving a signed Autodesk Create Installer emerged. This installer, deployed by installer-bundle.exe, exploited Autodesk, a software often targeted in cyber-attacks, as a Remote Desktop application on the victims’ devices. Subsequently, a file named No-Hoa-Letter-Mortgage.tmp executed powershell.exe, establishing a connection to a C2 server in the Netherlands. Multiple files, including a .dat file, were created and granted write privileges in the %Temp% directory.
The malware dropped a decoy PDF file into %Temp%, serving as a diversion for the victim. Shortly after the initial infection, the created files were deleted. Upon gaining a foothold, PowerShell initiated multiple network connections to the C2 server, executing a command to decrypt the .DAT file with a custom XOR key. The decoded PowerShell script revealed its use to decrypt the Infostealer payload and load the DLL payload in-memory through the Reflection.Assembly::load method.
From the ETLM perspective, CYFIRMA anticipates that Jupyter Infostealer continues to demonstrate adaptability and sophistication, the future threat landscape appears increasingly challenging for organizations. The integration of advanced features, such as the ability to execute PowerShell scripts, showcases a resilient and evolving threat. Typically, the impact on organizations is poised to intensify, with the potential for more widespread and targeted attacks. The multifaceted nature of Jupyter Infostealer, coupled with its persistence, suggests a continuous evolution that demands proactive cybersecurity measures. Organizations should anticipate a rise in both the frequency and complexity of Jupyter-related incidents, necessitating enhanced defense strategies to safeguard sensitive data and maintain the resilience of their networks against this persistent threat.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
Unknown Threat Actor Targets Gilgit-Baltistan Region Using Android Malware
Summary:
In a recent observation, researchers uncovered an unknown threat actor delivering Android malware via a Hunza news website in the Gilgit-Baltistan region; a disputed region governed by Pakistan. The attack involves a spyware-infected Android app named Kamran, discovered on the website’s Urdu mobile version(urdu[.]hunzanews[.]net), posing as a legitimate news app. This malicious Android application specifically targets Urdu-speaking users in Gilgit-Baltistan. The espionage capabilities of Kamran are alarming, compromising at least 20 mobile devices, and gathering extensive personal data upon user permission. The app requests access to contacts, call logs, location info, SMS, images, and more, exploiting the user’s trust. It’s noteworthy that the app is not available on the Google Play store, requiring users to enable installations from unknown sources. The deployment of Kamran coincided with civil unrest in Gilgit-Baltistan over land rights, power outages, and other grievances. The region’s strategic significance, hosting significant mountain ranges and the Karakoram Highway, connecting China and Pakistan, adds weight to the attack’s implications. This attack marks a concerning trend where malicious software leverages trusted platforms to exploit sensitive data, highlighting the importance of vigilance in downloading apps from secure sources.
Relevancy & Insights:
The attribution of the malware targeting Urdu-speaking users in Gilgit-Baltistan remains uncertain regarding the responsible APT (Advanced Persistent Threat) or nation-based threat actor. While speculation exists about the involvement of an Indian-based threat actor seeking intelligence from residents, it’s equally crucial not to dismiss the potential involvement of Chinese threat actors. The region’s significance in the context of the CPEC (China-Pakistan Economic Corridor) project amplifies its importance to Chinese interests, raising the possibility of Chinese authorities monitoring the region by gathering data from local sources. The complexity of geopolitical interests surrounding Gilgit-Baltistan underscores the challenge of pinpointing the specific actor behind such malicious activities, leaving room for various potential motivations and actors involved in this cyber threat landscape.
ETLM Assessment:
Cyber-attacks involving malware in this particular region are rare occurrences. However, this attack stands out due to its meticulous planning, utilizing a delivery sub- domain of the official domain of Hunza News, indicating a high level of sophistication. The deliberate focus on targeting solely Urdu-speaking users hints at a clear objective of cyber espionage. Witnessing further attacks of this nature would indeed be surprising, considering the difficulty and lengthy process of hijacking a sub-domain and then deploying malware. Our analysis suggests that attacks utilizing these specific tactics may occur, but we don’t anticipate similar tactics will be employed frequently.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Australian Ports hit by a Cyberattack
Australia’s National Cyber Security Coordinator announced that the government was
investigating a cyberattack that disrupted several Australian ports. Australia’s leading container terminal and supply chain operator; DP World Australia, has announced it has restricted access to its Australian port operations in Sydney, Melbourne, Brisbane and Fremantle. The operator manages the flow of nearly 40% of the country’s goods and is owned by Dubai-based logistics giant; DP World. This interruption has continued for a number of days and had an impact on the movement of goods into and out of the country, leading to a huge backup of cargo. The cyber incident has not yet been further specified or attributed but the operator noted that it has not received a ransom demand, while the government called it “a nationally significant cyber incident.” According to media reports, the shutdown at the ports was preventive after “unauthorized activity” had been detected in DP World Australia’s systems.
ETLM Assessment:
In a recent report, CYFRIMA analysts have warned about similar attacks on infrastructure in Europe, following Russia’s campaign which aims at disrupting Ukraine’s agricultural exports (parts of which were replaced by Australian exports) and replacing Ukrainian grain with Russian products on the world market. However, Russia is not the only country that would be motivated to perform such an attack.
Since 2020, China has been trying to coerce Australia into subduing to its political demands and a full blown trade war between the two countries had commenced in 2020. In 2022, the Indo-Pacific Economic Framework (IPEF) was formed, including Australia, Brunei, Fiji, India, Indonesia, Japan, Malaysia, New Zealand, the Philippines, Singapore, South Korea, Thailand and Vietnam in response to the security deal between China and the Solomon Islands, which was signed earlier that year. Chinese Foreign Minister; Wang Yi, heavily criticized the new alliance and leading up to the 2022 Australian federal election, China was trying to interfere with the election with the goal of promoting Australian parties more favourable to Chinese demands. With world distracted by the wars in Gaza and Ukraine, China continues to stir trouble in the South China Sea and its surroundings, and this attack could be a part of the campaign. China is even willing to use cyber tools against its allies, as recently reported, two major Chinese APTs engaged in cyberespionage against Cambodia in a campaign targeting at least twenty government and industry organizations in a long-term collection effort.
Cambodia and China enjoy generally good diplomatic and economic relations, but that’s irrelevant to China’s choice of targets. Beijing’s long-range goal is an enhanced naval presence in the waters off Southeast Asia, and the intelligence being gathered is designed to support that end.
There are, however, further possibilities for the perpetrators of the Australia attack. The company operating the ports is incorporated in Dubai, UAE and the attack could have been part of an intricate web of rivalries and shadow cyber wars currently taking place in the Middle East, or the work of some opportunistic criminals.
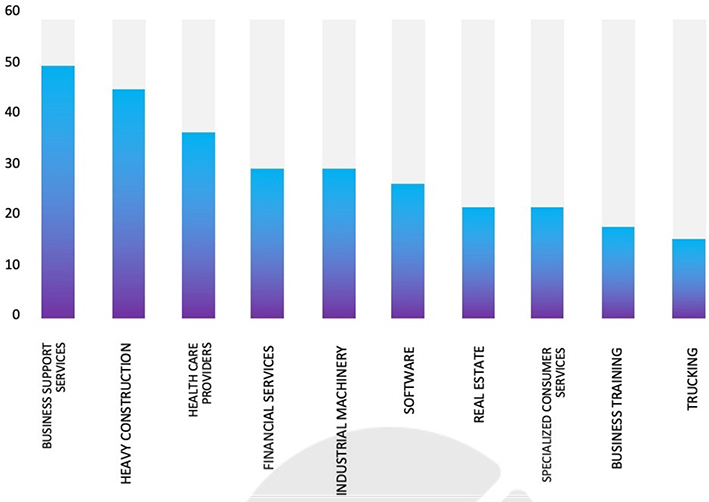
As we have reported here, the logistics industry, being a critical part of infrastructure, confronts substantial risks from advanced threat actors. Data we have recently published on the industry reveals a consistent pattern of attacks, with a clear emphasis on developed economies and major global logistics hubs. Although true that the detection of APT campaigns has declined, a correlation between the current geopolitical landscape and the most targeted countries remains evident. Moreover, Russia seems to be increasingly employing privateering actors, motivated by financial gains to put distance between Moscow and the global food insecurity. Such a trend is expected to continue as privateers are offered ever more leniency: in the eyes of the Kremlin, the more global instability, the better the attention is deflected from its persecution of Ukraine, with fewer resources available to oppose it. The attack on Australian ports should serve as a reminder of the serious risk that cyber-attacks pose to any country, and to vital infrastructure we all rely on.
Iranian APTs targeting Israel
Researchers have recently described a series of cyberattacks that targeted Israeli organizations as well as other Middle Eastern nations in the transportation, logistics, and technology sectors in October 2023. The campaign has been attributed to the Iranian APT known as IMPERIAL KITTEN, which is widely suspected to be an arm of Iran’s Islamic Revolutionary Guard Corps (IRGC) and which likely fulfils Iranian strategic intelligence requirements, based on the directions from the intelligence wing of IRGC. In this case, the threat actor used spearphishing emails to deliver several strains of malware via malicious Excel documents, including IMAPLoader and Standard Keyboard. While there is a strategic cooperation between Hamas and Iran (directed by IRGC), this attack seems to be an opportunistic cyber espionage action and more likely than a part of an integrated campaign developed in cooperation with Hamas.
So far there are no direct indications that would suggest Iran was involved in planning the operations on October 7, in which Hamas massacred over 1200 Israelis, most of them civilians. Iran cyber operators have been largely reactive in the cyber domain, since the current war in Gaza began, exploiting opportunities to try and take advantage of events on the ground as they unfold. According to the researchers it took more than a week from the start of the ground conflict before Iran entered the war in the cyber domain. So far researchers see Iranian APTs continuing to employ their tried-and-true tactics, notably exaggerating the success of their computer network attacks, and amplifying those claims and activities via a well-integrated deployment of information operations.
Besides the aforementioned spearphising attacks, Imperial Kitten has been observed using watering hole attacks and exploitation of one-day exploits, stolen credentials and even targeting upstream IT service providers for initial access. Another Iranian nation- state actor known as MuddyWater has been observed using a previously undocumented command-and-control (C2) framework called MuddyC2Go as part of attacks targeting Israel while Hamas-affiliated threat actor named Arid Viper has targeted Arabic speakers with an Android spyware known as SpyC23 through weaponized apps masquerading as Skipped and Telegram.
ETLM Assessment:
As we have warned in our assessment last week, we are likely to see a spike in the activity of Iranian APTs attacking Israel and other countries that support Israel. These attacks are likely just the beginning with many more to be revealed in due time. So far Israel seems to have been largely successful in blunting state-directed attacks, since it employs a proactive cyber defensive approach adopted by the Israeli National Cyber Directorate (INCD) as well as the mobilization of the country’s cyber security ecosystem due to the high-tech nature of the Israeli economy. However, the same cannot be said of every country supporting Israel and the risk of potential spill out is imminent.
The conflict in Gaza has revealed the complex and contradictory forces that shape Iran’s behaviour and interests in the Middle East, which are driven by both ideology and pragmatism. Iran’s proxies in the region, namely Lebanese Hezbollah, Iraqi Popular Mobilization Forces and Yemeni Houthis have all joined the struggle and started a low intensity war against Israel and the U.S., mostly by way of rocket and drone attacks. Hezbollah alone has lost over 50 fighters but the recent speech by its leader Hassan Nasrallah and Iranian supreme leader Ali Khamenei suggest that these attacks are likely meant to show Iran’s strength and deterrence capabilities to Israel and the United States, but also that Iran and its proxies are walking a thin line trying to avoid a direct clash that could harm Iran’s interests and security. Iranian officials have been walking a tightrope between their ideological commitment to the Palestinian cause and their pragmatic calculations of regional interests and risks. Their statements expose the dilemmas and difficulties that Iran confronts in dealing with its friends and foes. But they also reflect their domestic concerns and calculations. This, however, does not apply to the fifth domain, where the risk of high scale physical retaliation seems low. Israel’s National Cyber Directorate confirms this observation and states that the prospect of an intensified Iranian cyber campaign is deeply worrying, since Iran “knows that they can act there [in cyberspace] more freely than in physical space”.
Pricesmart is Impacted by BlackCat Ransomware
Summary:
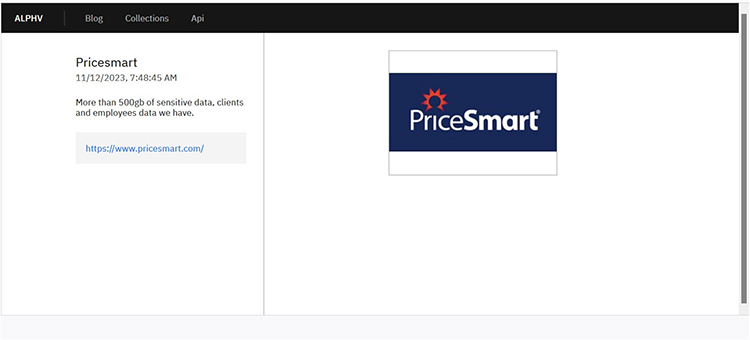
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from The United States of America, (www[.]pricesmart[.]com), was compromised by BlackCat Ransomware. PriceSmart, Inc. is only operator of membership warehouse clubs in Central America, the Caribbean, and Colombia, serving over 3 million cardholders. The compromised information comprises over 500 gigabytes of sensitive data, including details related to clients and employees.
The following screenshot was observed published on the dark web:
Source: Dark Web
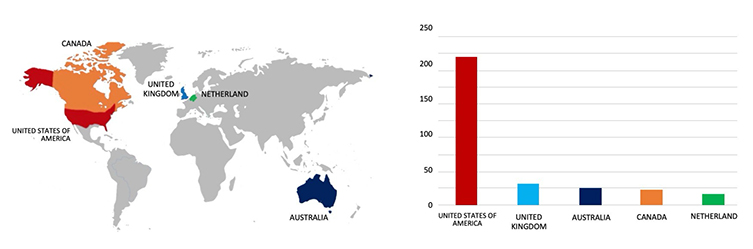
Relevancy & Insights:
ETLM Assessment:
CYFIRMA assesses BlackCat Ransomware to maintain a focus on American businesses and related entities that hold significant amounts of Personally Identifiable Information (PII). Nonetheless, the recent attack on Pricesmart underscores the global threat posed by the BlackCat Ransomware.
Vulnerability in Discourse
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied input within the Onebox favicon URL.
Impact:
A remote attacker can pass specially crafted input to the application and perform a denial of service (DoS) attack.
Affected Products: https[:]//github[.]com/discourse/discourse/security/advisories/GHSA- 77cw-xhj8-hfp3
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 3 most affected products.

DDoS Cyberattack Hits Cairo International Airport
Summary:
Anonymous Collective hacker group has claimed Cairo International Airport cyberattack in their latest campaign. The Cairo International Airport allegedly grapples with a relentless Distributed Denial of Service (DDoS) attack orchestrated by the infamous threat actor. This incident, spanned over 25 hours, marks the most extensive cyber assault on any Egyptian airport to date. The airport’s digital infrastructure, including its website and mobile application, remains allegedly crippled, with losses amounting to millions of dollars. Anonymous Collective, in a bold statement, asserts that the Cairo International Airport DDoS attack is a response to Egypt’s perceived support for Israel in the Gaza conflict. The Anonymous Collective’s message, delivered through their Telegram channel, highlights the gravity of the situation. Notably, the email system has also fallen victim to the attack, exacerbating the overall impact on the airport’s operations. In a public declaration, the threat actor emphasized that the attack is complete, having achieved its objectives.
Relevancy & Insights:
Anonymous Collective claims that the DDoS attack on Cairo International Airport is a response to Egypt’s perceived support for Israel in the Gaza conflict. The bold statement delivered through their Telegram channel indicates that the threat actor sees the cyber-attack as a form of protest or retaliation against the country’s political stance.
ETLM Assessment:
CYFIRMA assesses that the DDoS attack on Cairo International Airport is a response to Egypt’s perceived support for Israel in the Gaza conflict. The perpetrators might persist in executing DDoS attacks with the intention of harming the reputation of targeted organizations
Ringcentral Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Ringcentral, {www[.]ringcentral[.]com}. RingCentral, Inc. offers comprehensive global enterprise solutions for cloud-based communications and collaboration. The company integrates voice, video, team messaging, conferencing, online meetings, and contact center solutions into a unified platform. The breached data includes unique identifiers, names, email addresses, last-seen timestamps, country codes, regions, cities, carrier information, time zones, and other sensitive details.
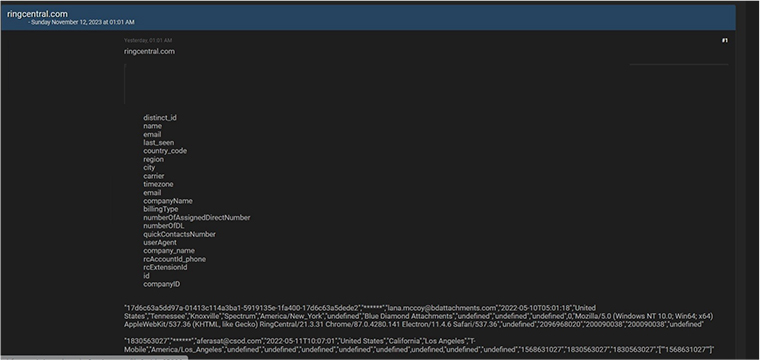
Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial motives are consistently searching for exposed and vulnerable systems and applications. Most of these attackers participate in clandestine forums, where they discuss related matters and trade stolen digital goods. In contrast to other financially motivated groups, like ransomware or extortion collectives that frequently publicize their attacks, these cybercriminals prefer to keep a low profile. They secure unauthorized access and pilfer valuable data by exploiting unpatched systems or vulnerabilities in applications and systems. The purloined data is subsequently promoted for sale in underground forums, where it is resold and repurposed by other attackers for their own malicious activities.
ETLM Assessment:
The United States of America remains a prominent target for cybercriminals globally. As per CYFIRMA’s assessment, U.S. institutions without robust security measures and infrastructure are expected to face an elevated risk of potential cyberattacks.
CYFIRMA Research team observed a potential data leak related to the Farmaciavernile, {www[.]farmaciavernile[.]it}. Farmaciavernile offers a wide assortment of pharmaceutical, parapharmaceutical, homeopathic, herbal, and veterinary products. The pharmacy also has a modern galenic laboratory for the preparation of master medicines and cosmetic preparations with a vast assortment of raw materials. The compromised data comprises of usernames, email addresses, passwords, and other confidential details.
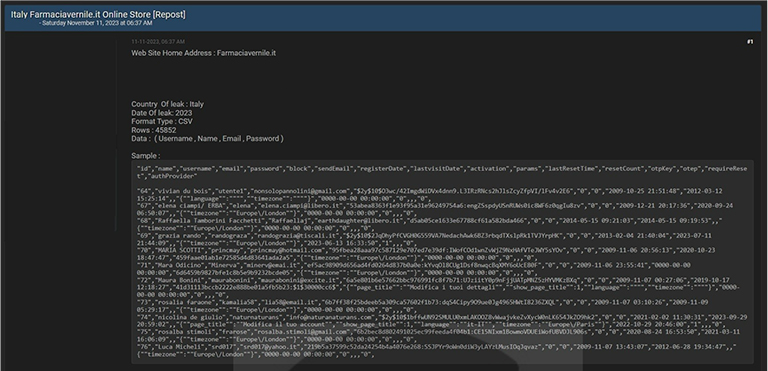
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS