



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found EnigmaWave ransomware while monitoring various underground forums as part of our Threat Discovery Process.
EnigmaWave ransomware
Researchers uncovered EnigmaWave ransomware at the beginning of May 2024, the ransomware program encrypts data to make it inaccessible and demands payment for its decryption.
The ransomware appends encrypted file names with the attackers’ email address, a unique victim ID, and the “.EnigmaWave” extension. Additionally, EnigmaWave creates a ransom- demanding message titled “Readme.txt”.
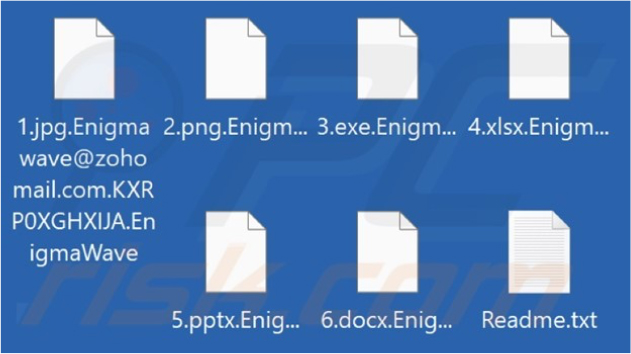
Screenshot of files encrypted by ransomware (Source: Surface Web)
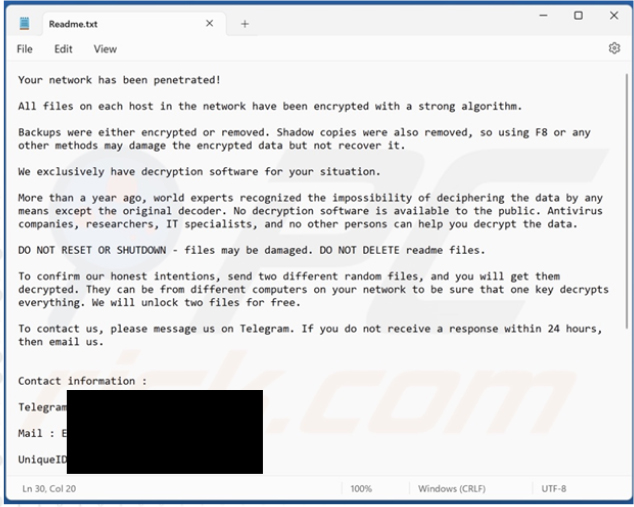
Screenshot of EnigmaWave ransomware’s text file (“Readme.txt”): (Source: Surface Web)
EnigmaWave’s ransom note notifies victims of their network’s infection and the encryption of their files, accompanied by the removal of backups and Volume Shadow Copies. The attackers claim exclusive ability to restore the locked files, suggesting ransom payment in Bitcoin cryptocurrency. Victims are offered a test decryption on two random files before committing to payment. Additionally, the note cautions against file deletion, system shutdown, or reset, as these actions may jeopardize data decryption.
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0003: Persistence | T1176: Browser Extensions |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 2 | TA0004: Privilege Escalation | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 3 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1112: Modify Registry | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 4 | TA0007: Discovery | T1012: Query Registry |
| T1018: Remote System Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 5 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 6 | TA0009: Collection | T1185: Browser Session Hijacking |
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| T1102: Web Service | ||
| T1573: Encrypted Channel | ||
| 8 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that EnigmaWave ransomware will persist in targeting various industries worldwide, exploiting vulnerabilities in Windows Operating Systems. Future versions may intensify evasion strategies, utilizing registry manipulation for persistence and evading detection through sophisticated anti-debugging methods. Global industries must fortify cybersecurity measures to counter potential threats.
Sigma Rule
title: Suspicious Run Key from Download tags:
– attack.persistence
– attack.t1547.001 logsource:
category: registry_event product: windows
detection: selection:
Image|contains:
– ‘\Downloads\’
– ‘\Temporary Internet Files\Content.Outlook\’
– ‘\Local Settings\Temporary Internet Files\’
TargetObject|contains: ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\’ condition: selection
falsepositives:
– Software installers downloaded and used by users level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Information Stealer
Objective: Data theft
Target Industry: Gaming
Target Technology: Windows OS, Browsers, Cryptocurrencies, Software (Steam, osu!, Roblox, Growtopia, and Discord)
Active Malware of the Week
This week “zEus Stealer” is trending.
zEus Stealer
The zEus malware is a type of malicious software categorized as a stealer, designed specifically to extract sensitive information from devices. This includes logging credentials for various accounts. Researchers discovered the zEus stealer malware within a source pack shared on YouTube and embedded in a Minecraft source pack, disguised as a WinRAR self-extract file. This file masquerades as a Windows screensaver file and initiates the stealer while displaying an image with the label “zEus,” which is also referenced in the Discord webhook profile used for receiving stolen data.

Fig: The string on the icon of the inserted file
Attack Method
The zEus stealer, once executed by a victim, first checks for any analysis tools to evade detection. If undetected, it proceeds to gather sensitive information and deploys script files to enhance its attack capabilities. The malware creates folders within C:\ProgramData to store both stolen data and its own malicious scripts.
Anti-analysis
zEus conducts checks to determine if it is under analysis by comparing the computer’s name and active processes against predefined blacklists.
Computer name blacklist:
WDAGUtilityAccount, Abby, Peter, Wilson, hmarc, patex, JOHN-PC, RDhJ0CNFevzX, kEecfMwgj, Frank, 8Nl0ColNQ5bq, Lisa, John, george, PxmdUOpVyx, 8VizSM, w0fjuOVmCcP5A, lmVwjj9b, PqONjHVwexsS, 3u2v9m8, Julia, HEUeRzl, BEE7370C- 8C0C-4, DESKTOP-NAKFFMT, WIN-5E07COS9ALR, B30F0242-1C6A-4, DESKTOP- VRSQLAG, Q9IATRKPRH, XC64ZB, DESKTOP-D019GDM, DESKTOP-WI8CLET, SERVER1, LISA-PC, JOHN-PC, DESKTOP-B0T93D6, DESKTOP-1PYKP29, DESKTOP-1Y2433R, WILEYPC, WORK, 6C4E733F-C2D9-4, RALPHS-PC, DESKTOP-WG3MYJS, DESKTOP-7XC6GEZ, DESKTOP-5OV9S0O, QarZhrdBpj, ORELEEPC, ARCHIBALDPC, JULIA-PC, d1bnJkfVlH, QDAVNJRH
Program blacklist:
httpdebuggerui, wireshark, fiddler, vboxservice, df5serv, processhacker, vboxtray, vmtoolsd, vmwaretray, ida64, ollydbg, pestudio, vmwareuser, vgauthservice, vmacthlp, x96dbg, vmsrvc, x32dbg, vmusrvc, prl_cc, prl_tools, xenservice, qemu-ga, joeboxcontrol, ksdumperclient, ksdumper, joeboxserver
Information Stealing
The zEus stealer collects a diverse array of information, saving each piece into separate text files within specific folders located at C:\ProgramData\STEALER. These folders include PCINFO, IPINFO, HARDWARE, BROWSERS, STEAL, LDB, and SESSION, organizing the
stolen data accordingly.
PCINFO
In a specified folder, zEus maintains two subfolders: IPINFO and HARDWARE. To obtain the victim’s IP address and related details, zEus utilizes online services like My External IP, ipapi, and ip-api, storing outcomes as text files in the IPINFO directory. Using this IP address, zEus requests more information from these tools, including the internet service provider, city, longitude, latitude, and postal code. Furthermore, zEus captures whether the victim employs a proxy server or a mobile network. Additionally, using command-line utilities and PowerShell, zEus collects hardware data, including active processes, OS version, product key, hardware ID, system configuration, installed programs, and WIFI passwords, saving this information in the HARDWARE folder.
BROWSERS
zEus retrieves login data and user preferences from specific browsers, including Chrome, Opera, Brave, Vivaldi, Edge, and Firefox. It copies files related to login data and encryption keys for a password (if needed) from the browser’s profile directories and stores them in designated folders. The stolen information includes cookies, browsing history, shortcuts, and bookmarks from these targeted browsers.
STEAL
In this folder, zEus stores login data obtained from software including Steam, osu!, Roblox, Growtopia, and Discord. This data is typically copied from each software’s data path.
Additionally, zEus searches for a file named discord_backup_codes.txt in the Downloads folder. This file contains backup codes used for multi-factor authentication (MFA) on Discord, which zEus attempts to retrieve from the default download location.
LDB
The “LDB” folder exclusively contains .ldb files copied from %appdata%\discord\Local Storage\leveldb. These files enable the attacker to extract Discord tokens containing account and password details, which can be used to log into the victim’s Discord account.
SESSION
zEus copies diverse data to the SESSION folder from specific paths, gathering credentials and victim information. It retrieves logs folders from the parent directory of EpicGamesLauncher, containing debug logs. It also copies parent folders related to game companies like Battle.net and Electronic Arts. This data helps the attacker learn about the victim’s gaming preferences and provides insights for disguising future malware attacks.
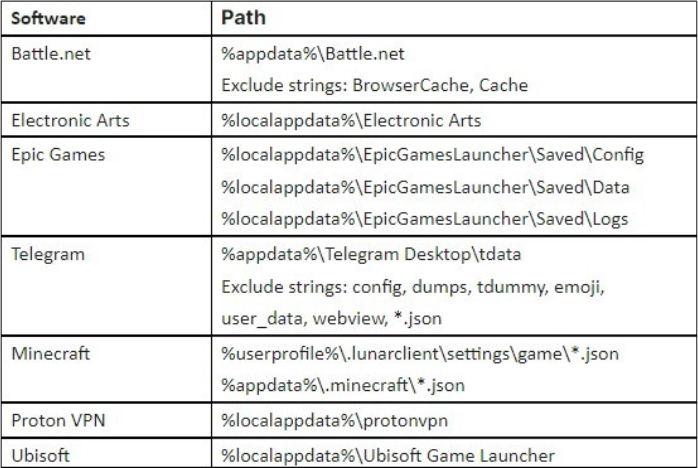
After collecting data, the zEus stealer drops two files, KEYWORDSEARCHER.bat and Keyword.txt, into the STEALER folder. KEYWORDSEARCHER.bat is a batch file that assists users in searching for specific keywords within a folder, while Keyword.txt serves as its README file. Subsequently, the STEALER folder is compressed into a zip file named STEALER.zip and then deleted. However, it’s important to note that the KEYWORDSEARCHER.bat and Keyword.txt files are not utilized by the zEus stealer itself.
zEus organizes the stolen data and sends it as an attachment named STEALER.zip. This report confirms whether the expected items were successfully stolen and includes the following details:
The zEus stealer checks if the victim uses specific cryptocurrencies, including Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, AtomicWallet, Guarda, and Coinomi.
Additionally, zEus searches the Downloads folder for files containing specific keywords related to login mechanisms and sensitive information. These keywords include terms like 2fa, mdp, motdepasse, mot_de_passe, login, seed, key, data, db, password, secret account, acount, paypal, banque, metamask, wallet, code, exodus, memo, compte, token, backup, and recovery. These keywords cover aspects of two-factor authentication (2FA), password recovery, and various terms related to banking and account security, including French language equivalents.
Features in Dropped Files
In addition to stealing information, the script files dropped to C:\ProgramData\{ComputerName} perform the following features:
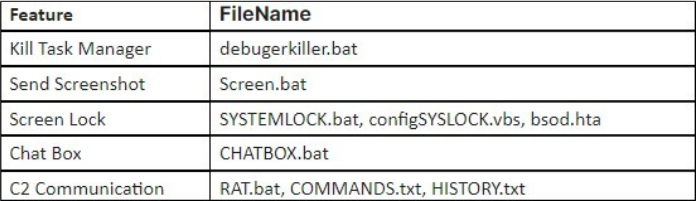
Three script files, debugerkiller.bat, Screen.bat, and RAT.bat, are executed immediately upon dropping and ensure persistence by registering their paths under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. They use the names of Windows system files and folders as value names to evade suspicion. zEus stealer includes various functionalities through dropped script files:
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the growing trend of using game add-ons and source packs to enhance gaming experiences presents an ongoing challenge for users and organizations alike. As more individuals engage in gaming and game development activities, the risk of encountering malware like zEus continues to rise. Future iterations of zEus could introduce new features and methodologies, making detection and mitigation more challenging for cybersecurity professionals. This continuous evolution of zEus malware may expand its scope and effectiveness, potentially infiltrating systems more deeply and evading traditional security measures. Additionally, the data collected by zEus poses a persistent risk, as it could be leveraged for secondary infections or targeted attacks. Organizations must anticipate these potential developments and enhance their cybersecurity posture with proactive monitoring, threat intelligence, and response strategies.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Persistent Cyber Intrusions: APT28’s Operations Against Global Institutions
Summary:
A sophisticated cyber-espionage campaign, attributed to APT28 and linked to the Russian GRU, has been actively targeting Polish government institutions. Techniques employed include DLL side-loading and executing scripts that further download and execute additional payloads.
Their operations exhibit a high level of technical proficiency and employ a diverse range of techniques and objectives. One key indicator of their activity is the use of spear-phishing emails, meticulously crafted to appear legitimate and personalized to their targets within government agencies. These emails often contain malicious links that lead to websites like run[.]mocky[.]io and webhook[.]site, which serve as initial entry points for malware delivery.
Once victims click on the links, they unwittingly initiate the download of a ZIP archive containing malware disguised as image files. This archive typically includes a Windows Calculator binary, masquerading as a JPG image file, alongside hidden batch script and DLL files. A notable aspect of APT28’s operations is their use of DLL side-loading, a technique that allows them to load a malicious DLL file while executing a legitimate application, thereby evading detection by security software. This enables APT28 to execute its malicious code surreptitiously, ultimately compromising the victim’s system. Furthermore, APT28 demonstrates a keen understanding of network evasion tactics, leveraging widely used services like run.mocky.io and webhook[.]site to obscure their malicious activities. By exploiting the trust associated with these legitimate platforms, APT28 reduces the likelihood of their malicious links being detected or blocked by security controls. Additionally, the group employs a multi-stage attack approach, incorporating social engineering tactics to maintain the illusion of legitimacy and deceive victims.
Relevancy & Insights:
Forest Blizzard, a threat group aligned with Russian foreign policy goals, has been actively engaged in espionage activities targeting government, energy, transportation, and non-governmental organizations across the United States, Europe, and the Middle East. Additionally, it has shown interest in media, IT, sports, and educational institutions globally. APT28, commonly associated with Russian interests, employs similar tactics, focusing on espionage and utilizing customized malware like GooseEgg and XAgent to infiltrate networks and gather sensitive information. Understanding the tactics and motives of APT28 is crucial for organizations globally to bolster their cybersecurity defences against such sophisticated threats.
ETLM Assessment:
APT28, a Russia-linked nation-state actor, has conducted a large-scale malware campaign targeting Polish government institutions, following accusations from NATO countries of its involvement in a long-term cyber espionage campaign against political entities and critical infrastructure. Known for using tailored malware, such as XAgent, which targets political and government entities in Western Europe, APT28 has a history of focusing on intelligence gathering to support Russian foreign policy goals. With past activities targeting a wide range of industries globally, including government, energy, transportation, media, IT, sports, and education, APT28’s sophisticated tactics and tailored malware pose a continued and evolving threat to organizations worldwide.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
The LockBit3 Ransomware impacts the Grand Indonesia
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]grand- indonesia[.]com), was compromised by the LockBit3 Ransomware. Grand Indonesia is an integrated multipurpose complex at Thamrin Road in Central Jakarta, Indonesia. The 640,000 m² complex consists of a huge shopping mall, office tower Menara BCA, high-end serviced residential tower Kempinski Residences, and the five-star all-suite Hotel Indonesia Kempinski. It is located near the Selamat Datang Monument. The data that has been compromised has not yet surfaced on the leak site, suggesting ongoing negotiations between the affected party and the ransomware group. The compromised data encompasses sensitive and confidential information pertinent to the organization.
The following screenshot was observed published on the dark web:
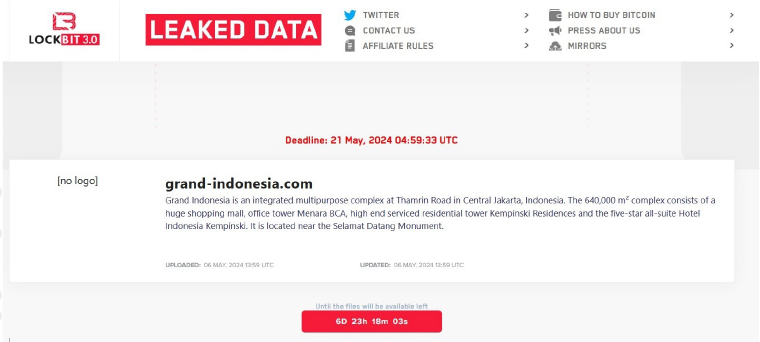
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
CYFIRMA’s assessment underscores the persistent and widespread threat posed by LockBit 3.0 Ransomware to companies worldwide. Our observations reveal an escalating pattern, wherein LockBit 3.0 Ransomware exploits vulnerabilities in diverse products to infiltrate systems, facilitating lateral movement within organizational networks. Based on the available information, CYFIRMA’s assessment indicates that LockBit 3.0 Ransomware will continue to target various industries globally, with a significant emphasis on the United States, Europe, and Asian regions. The recent breach targeting Grand Indonesia, a leading hospitality firm based in Indonesia, serves as a potential indicator of LockBit 3.0 ransomware’s inclination towards targeting organizations across Southeast Asia.
The RansomHub Ransomware impacts the LPDB KUMKM LPDB.ID/LPDB.GO.ID
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]lpdb[.]go[.]id), was compromised by the RansomHub Ransomware. LPDB KUMKM Kementerian Koperasi is an Indonesian government institution responsible for managing revolving funds for cooperatives and small and medium enterprises (SMEs). The main goal of LPDB KUMKM is to provide financial support and assistance to cooperatives and SMEs to help them grow and develop. This includes providing loans, grants, and other financial services to eligible organizations. The data that has been compromised has not yet surfaced on the leak site, suggesting ongoing negotiations between the affected party and the ransomware group. The compromised data includes more than 15TB of the organization’s private documents, backups, and NAS backups that were encrypted.
The following screenshot was observed published on the dark web:
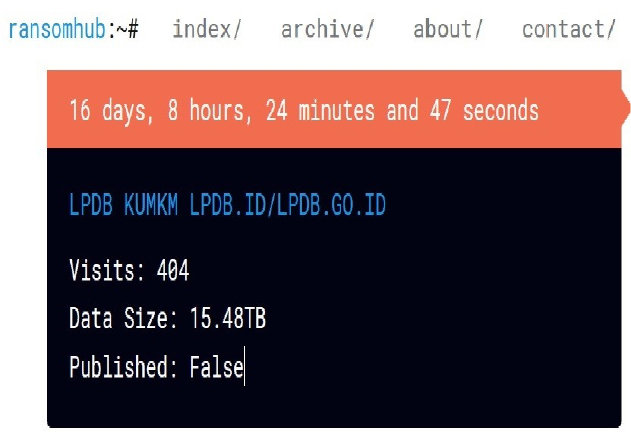
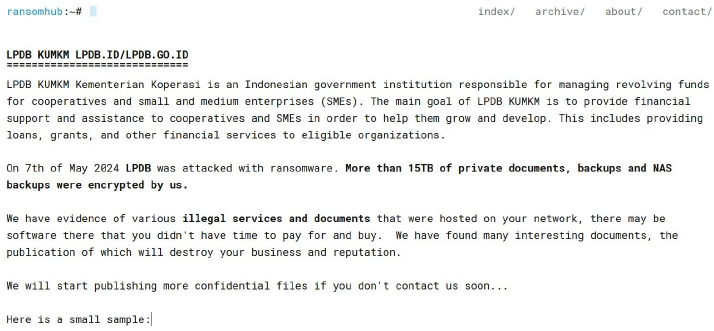

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The RansomHub group seems to be a recently emerged ransomware group, likely with roots in Russia. Due to the benefit it offers its affiliates and the strict controls it enforces, they could be vying for the leadership position amidst pressure from security forces to major players like LockBit and ALPHV. However, their ransomware strains appear to be just a revised version of an old sample for now. An interesting part is that this strain is also written in the Golang language. Based on CYFIRMA’s assessment, RansomHub Ransomware targets worldwide organizations. The attack on LPDB KUMKM LPDB.ID/LPDB.GO.ID also highlights ransomware groups’ interest in Southeast Asian organizations financially strong in the region with exploitable vulnerabilities.
Vulnerability in PowerDNS DNSdist
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insights:
The vulnerability exists due to a reachable assertion when incoming DNS over HTTPS support is enabled using the nghttp2 provider, and queries are routed to a tcp-only or DNS over TLS backend.
Impact:
A remote attacker can send a specially crafted request for a zone transfer (AXFR or IXFR) over DNS over HTTPS and perform a denial of service (DoS) attack.
Affected Products: https[:]//dnsdist[.]org/security-advisories/powerdns-advisory-for-dnsdist- 2024-03.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
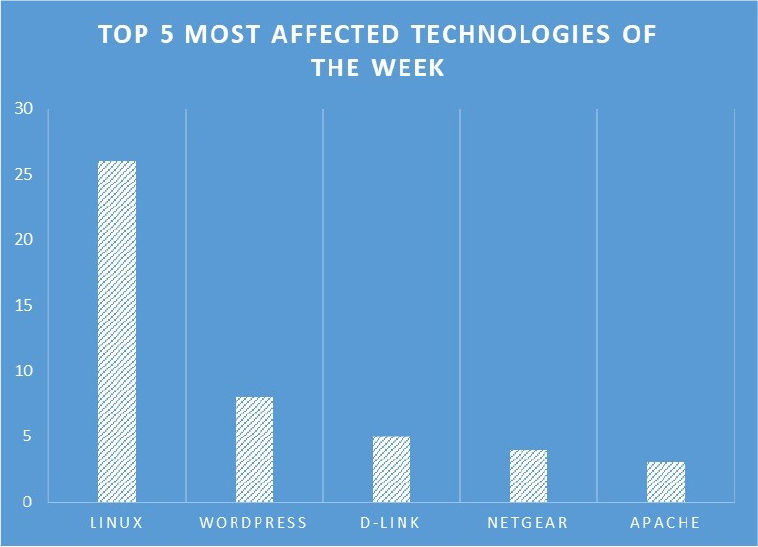
ETLM Assessment:
Vulnerabilities in DNSdist, a UNIX daemon for DNS proxy and load balancing, could disrupt services and compromise network integrity across industries like technology, finance, and healthcare worldwide, necessitating robust security measures and continuous monitoring. Its adaptability ensures efficient and resilient DNS services, catering to diverse geographic regions’ needs.
underground Ransomware attacked and Published data from Synology
Summary:
Recently we observed that underground Ransomware attacked and Published data of Synology on its darkweb website. Synology Inc(www[.]synology[.]com). is a prominent technology company known for its expertise in network-attached storage (NAS) solutions. Founded in 2000 and headquartered in Taipei, Taiwan, Synology has a global presence with offices in Germany, the United States, the UK, France, Japan, and China. The company provides a range of products designed to help businesses and individuals manage, secure, and protect their data effectively. Synology’s product lineup includes high-performance NAS systems, storage solutions for virtualization environments, and comprehensive data management and protection tools. Their DiskStation Manager (DSM) is a widely acclaimed operating system that powers their NAS devices, offering features like multimedia management, file synchronization, data backup, and virtualization support. DSM is known for its user-friendly interface and robust security measures, making it suitable for both home users and enterprises. The data leak, following the ransomware attack, encompasses a broad spectrum of sensitive and confidential information pertinent to the organization. The data leak is approximately 51 GB in total size.
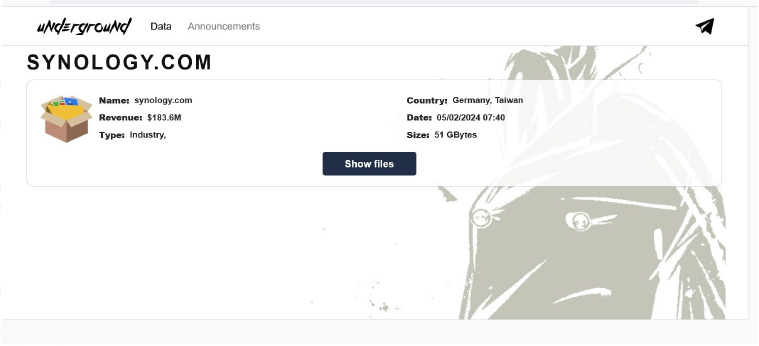
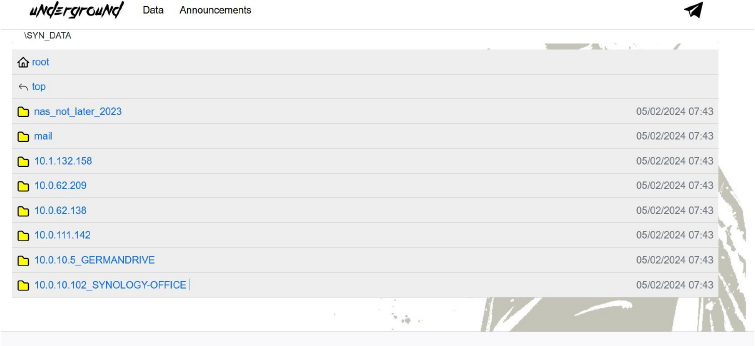
Source: Dark Web
Relevancy & Insights:
The Underground ransomware gang announced a massive operation recently. The hackers listed 11 victims on their leak website, along with a short summary of each. The amount of data leaked varies between 35 GB and 1.6 TB. We observed that the Underground Ransomware group uses the double-extortion practice to force the victims into paying the ransom. They always leave a ransom note behind, containing information about the type of data they stole and where they’ve exfiltrated it.
ETLM Assessment:
There are some conflicting reports and theories at play regarding Underground’s actual identity. One such theory claims that the gang is the successor of the infamous Industrial Spy ransomware that was active in 2022. This hasn’t been confirmed yet. Based on the available information, CYFIRMA’s assessment indicates that Underground ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent breach targeting Synology, a leading informational technology firm based in Taiwan, serves as a potential indicator of Underground ransomware’s inclination towards targeting organizations across the East Asia region.
Hunters Bali data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Hunters Bali,
{www[.]huntersbali[.]com } in an underground forum. Hunters Bali is a premium meat supplier in Bali offering high-quality, nutrient-dense animal products. animal products include grass-fed beef, free-range poultry, wild-caught seafood, and other premium meats sourced locally and from neighboring regions. The compromised data includes customer information such as name, username, last active date, sign-up date, email, orders, total spend, average order value (AOV), country, city, region, postal code, and other sensitive and confidential details. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.
Source: Underground Forums

PT Kreasi Putra Hotama Indonesia data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to PT Kreasi Putra Hotama Indonesia, {www[.]hotama[.]co[.]id } in an underground forum. PT Kreasi Putra Hotama Indonesia is a reputable software development and IT consulting company with over 10 years of experience. The compromised data includes email address, phone number, first name, last name, country, and zip code.
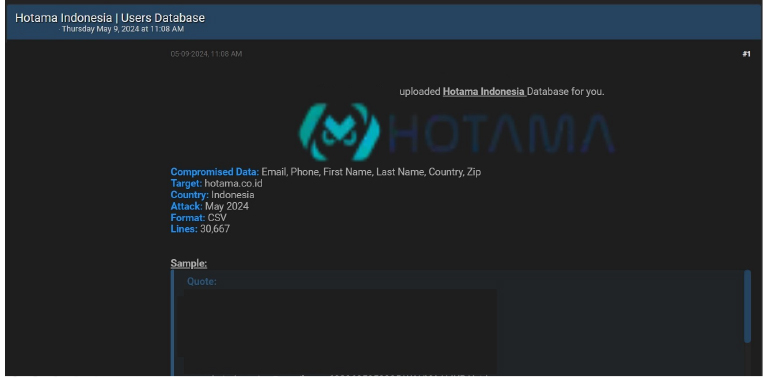
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as ‘Sedapmalam’ poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by ‘Sedapmalam’ typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data leak related to Localplace l(www[.]localplace[.]jp). The local place is the Japanese Online Reservation Agency. The compromised data includes client ID, company form, company name, full company information, phone number, full name, family name, email address, billing information, and other sensitive and confidential details.

Source: Underground forums
ETLM Assessment:
Satanic threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
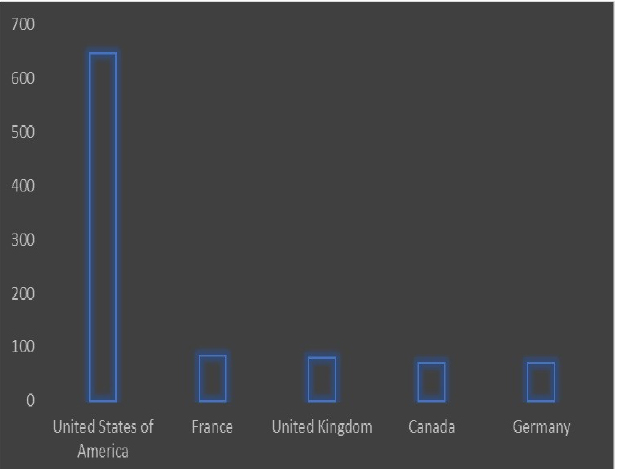
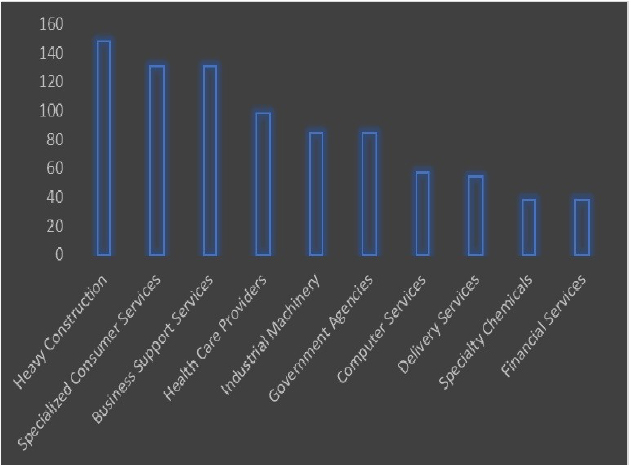
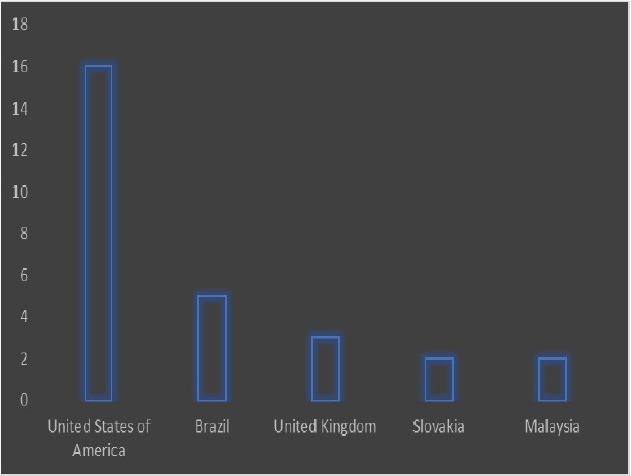
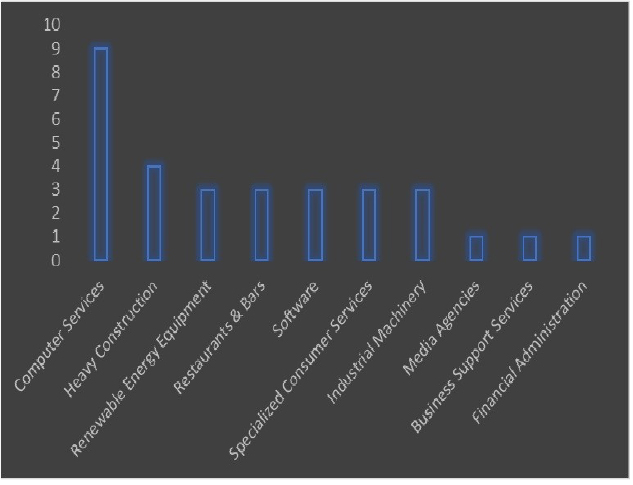
Please find the Geography – Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
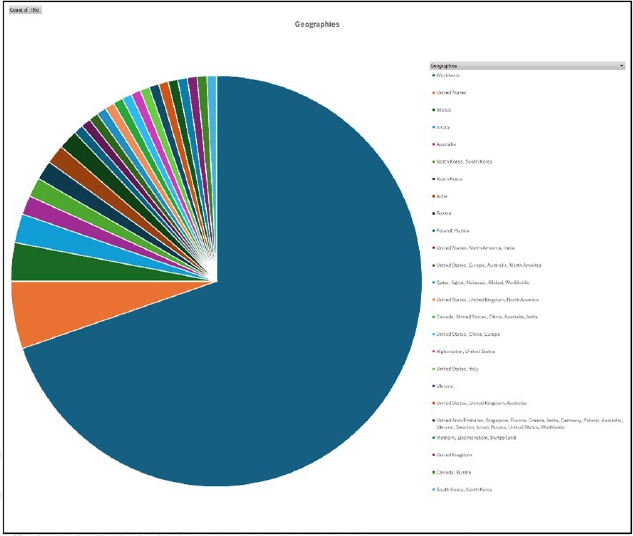
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.