



Key Intelligence Signals:
China-Based APT SharpPanda Continues Targeting Southeast Asian Region
Summary:
Sharp Panda is a China-based advanced persistent threat group, they have been active from the year 2018 targeting government entities of the Southeast Asian region. The group has been conducting strikes through spear phishing attacks on government entities, in a previous campaign the actor used a custom-made backdoor named VictoryDLL and RoyalRoad Kit. In a recent campaign, a new version of the SoulSearcher loader has been used by the threat actor. Previously it was observed that the soul malware framework was used in targeting Information and Communications Technology, Healthcare, and Defence sector industries in Southeast Asian countries. In the current campaign, the initial attack vector remained the same, the threat actor used RTF and word documents to deliver the final payload. Few changes were observed in the technicality of the malware used in the campaign, such as the threat actor making the malware geo-fenced, and the C&C server being different from what was used in their previous campaigns.
Insights:
Sharp Panda supports the interest of Chinese requirements. APT targets Southeast Asian countries, particularly those with similar territorial claims or strategic infrastructure projects.
It is interesting to know that the C&C servers did not return payloads during the time of Chinese Spring Festivals, however, it was active throughout the time from Monday to Friday.
Researchers have been tracking a campaign from suspected North Korean espionage group UNC2970, which has been observed targeting media and technology companies in the West. The researchers suspect the threat actors to have ties to Pyongyang and consider it to be an offshoot of a group also known as Temp. Hermit, a known ATP which has been observed for at least 10 years. Temp. Hermit was seen targeting primarily South Korean companies, with a small part of the attacks targeting organizations across the globe, whereas the reported campaign by UNC2970 has been primarily targeting entities in the West.
The attacks begin on LinkedIn, with the threat actors posing as recruiters and reaching out to targets. Researchers have identified files and suspicious drivers within compromised hosts. The malicious LIGHTSHOW payload, once delivered, then performs arbitrary read and write operations to kernel memory. The payload relies on trusted yet vulnerable drivers to function and is thus not a state-of-the-art attack.
Researchers have recently publicly discussed a campaign by Pakistan-based threat actor Transparent Tribe, which appears to be targeting Indian and other military and government officials with romance scams. The victims are persuaded to install hacked versions of secure messaging apps on their Android smartphones. These applications will set up the information stealing CapraRAT backdoor. Experts think the attackers first get in touch with their victims via phone or email before luring them into a romantic scam—a ruse Transparent Tribe has previously employed. The attackers continue to communicate with the victims via the Trojanized chat app once they have downloaded it, all the while stealing information in the background. The researchers were able to identify over 150 victims in India, Pakistan, Russia, Oman, and Egypt thanks to the malicious programs’ lax operational security.
The President’s Budget for Fiscal Year 2024 has been published, and it addresses cybersecurity across the spectrum of the US Federal Government’s operations. The Budget contains large spending requests in accordance with the US National Cybersecurity Strategy with a large part of the funding being intended for countering cyber operations by adversaries originating from China and Russia, but also for more enforcement actions against cybercrime, to the countering of “malign influence,” and to “bolstering Federal cybersecurity.” The US Cybersecurity and Infrastructure Security Agency (CISA) would receive, under the plan, a budget of $3.1 billion, an increase of $145 million over current funding.
The US Director of National Intelligence, Avril Haines, has recently predicted to the US Senate Intelligence Committee that Russia could be expected to turn to alternative forms of military power as its conventional forces continue to fail on the battlefield. According to Mr. Haines, Russia will become even more reliant on asymmetric options such as cyber operations and increased cooperation with China.
Operations in the cyber realm however are not without challenges for Russia. Russian cyberattacks against Ukraine and its allies have not been very effective so far. While some of this is attributable to deterrence, especially in countries with superb capabilities, the Ukrainian defenses and Western assistance effectiveness are mostly to blame for the failure. It has also turned out to be harder than expected for Russian intelligence to maintain cohesion among top criminal gangs they use as auxiliary forces. Several of them including Conti broke up due to the conflict but others are trying to acquire new capabilities and take up the space on the privateering market.
The Team also observed a potential data leak related to www[.]venova[.]ch. A Switzerland-based e-commerce platform that deals with household, electronics, sports or leisure items, or garden accessories has been breached by an unknown threat actor, and data leaked in an underground forum. This data leak contains the user id, email, and other confidential information of the customers.
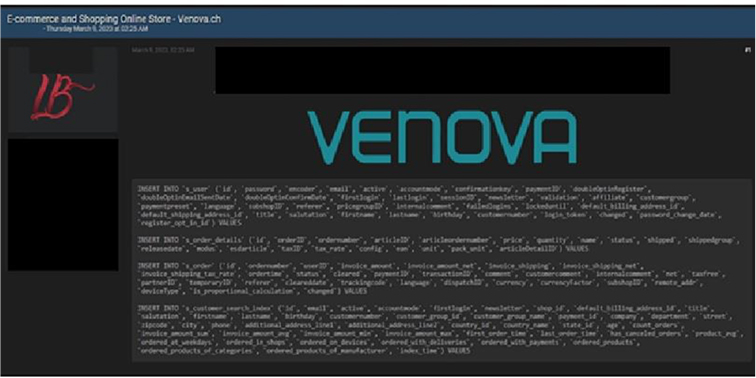
Source: Underground Forums