


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
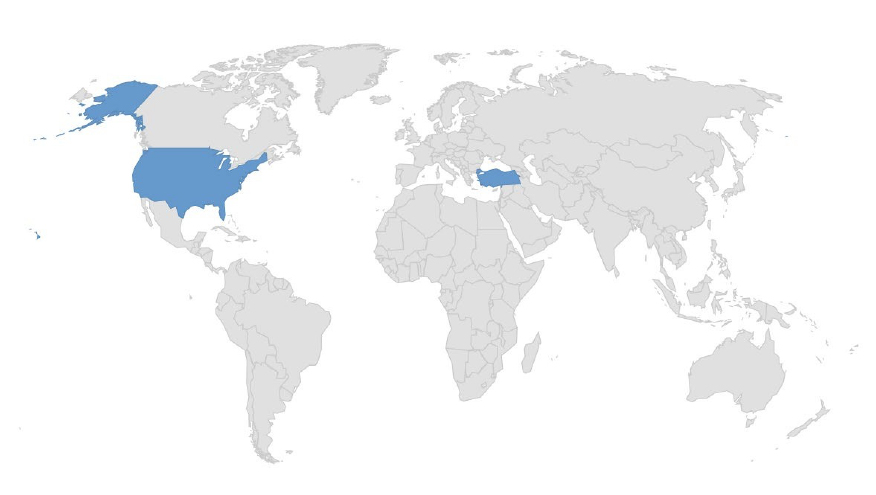
Target Geography: Turkey, USA
Target Industry: Business Services, Hospital, Software.
Introduction
CYFIRMA Research and Advisory Team has found Bert Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Bert Ransomware
Bert is a ransomware variant that encrypts victims’ files and appends the extension “.encryptedbybert” to affected filenames. In addition to modifying filenames, Bert drops a ransom note titled “.note.txt” in directories containing encrypted files.

The ransom note informs victims that their network has been compromised and that files have been encrypted. It further claims that sensitive data has been exfiltrated from the compromised environment. Victims are instructed to reach out to the attackers using the Session messaging app via the provided Session ID.


Following are the TTPs based on the MITRE Attack Framework
| Tactic | Techniqu e ID | Technique Name |
| Execution | T1106 | Native API |
| Persistence | T1547.00 1 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547.00 1 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.00 6 | Indicator Removal: Timestomp |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1562.00 1 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.00 1 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.00 1 | Software Discovery: Security Software Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment with available data suggests that Bert ransomware may evolve into a broader threat targeting global industries, including finance, manufacturing, and healthcare. Its use of stealth techniques and persistence via registry manipulation indicates increasing sophistication. Given its focus on data exfiltration and evasion of debugging environments, Bert is likely to adapt and scale operations beyond Turkey and the USA. Organisations worldwide should remain vigilant as this ransomware could expand its reach across critical business sectors.
Sigma rule:
title: Suspicious desktop.ini Action tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Stealing sensitive information, Espionage, Data exfiltration | Threat Actor: COLDRIVER (aka UNC4057, Star Blizzard, Callisto) | Target Technology: Windows OS | Target Sectors: NATO Governments, Non-Governmental Organizations (NGOs), Former Intelligence and Diplomatic Personnel.
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “LOSTKEYS” is trending.
LOSTKEYS
Researchers have discovered a new malware strain known as LOSTKEYS, linked to the Russian state-sponsored threat group COLDRIVER (also known as UNC4057, Star Blizzard, Callisto). This group, known for credential phishing against high-profile entities such as NATO governments, non-governmental organizations (NGOs), and former intelligence and diplomatic personnel, appears to be expanding its tactics beyond traditional phishing campaigns. LOSTKEYS is designed to silently steal sensitive files from specific directories and extensions while also collecting system details and information about running processes. Spotted in several campaigns throughout early 2025, the emergence of this malware marks a notable shift in COLDRIVER’s strategy, indicating a move toward more intrusive and versatile cyber operations.
COLDRIVER
COLDRIVER is a Russian state-linked threat group that primarily targets high-profile individuals through personal and NGO-associated email addresses. The group is known for stealing credentials and, once inside a compromised account, exfiltrating emails and contact lists. In some cases, they escalate their operations by delivering malware to victims’ devices and attempting to access stored files. Their recent campaigns have focused on current and former advisors to Western governments and militaries, as well as journalists, think tanks, and NGOs. COLDRIVER has also maintained consistent targeting of individuals connected to Ukraine. Their activities suggest a clear objective: gathering intelligence that aligns with Russia’s strategic interests. In a few instances, the group has been tied to hack-and-leak operations aimed at officials and organizations in the UK.
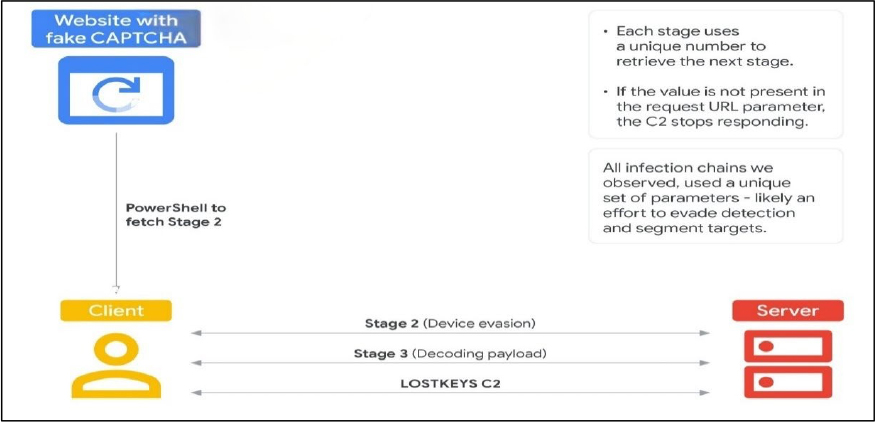
Attack Method
LOSTKEYS is delivered through a multi-step social engineering attack that begins with a lure website posing as a legitimate page. The site displays a fake CAPTCHA, tricking the user into thinking they must complete a verification step. Once the CAPTCHA is “solved,” the site silently copies a PowerShell command to the user’s clipboard and prompts them to run it via the Windows “Run” dialog. This command initiates the first stage of the attack, which then fetches and executes a second-stage payload— observed in some cases to be retrieved from a specific IP address. This approach falls under a broader social engineering tactic known as “ClickFix,” where users are tricked into copying and running malicious code themselves. While COLDRIVER has adopted this method, it’s not unique to them; several other threat actors, including advanced persistent threats and financially motivated groups, have also been seen using similar techniques.
The second stage of the infection includes a simple evasion check, where it calculates a hash based on the device’s screen resolution. If the result matches one of three specific values, the process stops—likely an attempt to avoid running in virtual environments used for analysis. If the check passes, the malware proceeds to download the next stage. Notably, each infection chain uses unique identifiers that must be included to successfully retrieve the third stage, which has consistently been hosted on the same server as the earlier stages.
In the final stages of the infection chain, the malware delivers a Base64-encoded file that decodes into additional PowerShell code. This code is responsible for retrieving the actual payload by downloading two more files from the same server used in earlier steps—each linked to unique identifiers specific to that attack instance. The first file is a Visual Basic Script (VBS), acting as a “decoder,” while the second contains the encrypted payload. Both files rely on two unique keys to unlock the final stage using a basic substitution method—one key stored in the decoder and the other embedded in the previous stage.
Once decoded, the final payload is revealed: a VBS-based malware known as LOSTKEYS. This tool is capable of stealing files from targeted folders and file types, while also collecting system information and details on running processes. While COLDRIVER is primarily known for credential theft and email exfiltration, it occasionally deploys malware like SPICA to access files directly from a target’s device. LOSTKEYS appears to serve a similar purpose and is reserved for carefully chosen, high-value targets.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that LOSTKEYS signals a move towards more silent and focused cyberattacks, where attackers aim to stay hidden while collecting valuable information over time. Instead of causing immediate disruption, future operations may quietly gather sensitive files, monitor internal activity, or gain insights into private decision-making. While the current focus has been on carefully selected individuals, this approach could expand to affect a broader range of organizations and regions as the techniques become more refined. As a result, the impact of such campaigns may grow, changing how trust, privacy, and information security are managed in the long term.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule LOSTKEYS Strings { meta:
description = “wscript that steals documents and becaons system information out to a hardcoded address”
hash = “28a0596b9c62b7b7aca9cac2a07b067109f27d327581a60e8cb4fab92f8f4fa9” strings:
$rep0 = “my_str = replace(my_str,a1,\”!\” )”
$rep1 = “my_str = replace(my_str,b1 ,a1 )”
$rep2 = “my_str = replace(my_str,\”!\” ,b1 )”
$mid0 = “a1 = Mid(ch_a,ina+1,1)”
$mid1 = “b1 = Mid(ch_b,ina+1,1)”
$req0 = “ReqStr = base64encode( z & \”;\” & ws.ExpandEnvironmentStrings(\”%COMPUTERNAME%\”) & \”;\” & ws.ExpandEnvironmentStrings(\”%USERNAME%\”) & \”;\” & fso.GetDrive(\”C:\\\”).SerialNumber)”
$req1 = “ReqStr = Chain(ReqStr,\”=+/\”,\”,-_\”)”
$cap0 = “CapIN \”systeminfo > \”\”\” & TmpF & \”\”\”\”, 1, True”
$cap1 = “CapIN \”ipconfig /all >> \”\”\” & TmpF & \”\”\”\”, 1, True”
$cap2 = “CapIN \”net view >> \”\”\” & TmpF & \”\”\”\”, 1, True”
$cap3 = “CapIN \”tasklist >> \”\”\” & TmpF & \”\”\”\”, 1, True” condition:
all of ($rep*) or all of ($mid*) or all of ($req*) or all of ($cap*)
}
(Source: Surface Web)
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
From Access to Exfiltration: Marbled Dust’s Full-Spectrum Exploitation of Output Messenger
Summary
Relevancy & Insights:
ETLM Assessment:
Strategic Recommendations:
Tactical Recommendations
Operational Recommendations
| MITRE FRAME WORK | ||
| Tactic | ID | Technique |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1078 | Valid Accounts |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Credential Access | T1557 | Adversary-in-the-Middle |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
North Korean hackers targeting South Korea and Ukraine for intelligence
A North Korean hacking outfit, APT37, also known as ScarCruft, has launched a new espionage campaign targeting South Korean organizations involved in national security, according to findings from South Korean cybersecurity researchers. The group impersonated a North Korea-focused expert and a think tank to craft phishing emails aimed at luring recipients into opening malicious links. One email purported to contain information about North Korean troops deployed to Russia, while another posed as an invitation to a national security conference. Both messages included compromised Dropbox links, a method APT37 frequently uses to mask malicious activity.
Believed to operate under North Korea’s Ministry of State Security, APT37 is considered a state-sponsored threat actor with a track record of targeting high- profile individuals and institutions in South Korea. The group is known for its use of social engineering to deliver malware through seemingly legitimate files and platforms. APT37 has consistently used mainstream cloud services—such as Dropbox, Yandex, OneDrive, and Google Drive—to distribute malicious payloads. In the latest campaign, the attackers embedded code that executed PowerShell commands to deploy RoKRAT, a remote access trojan capable of harvesting system information, capturing screenshots, and storing them for later retrieval.
In a related development, another North Korean threat actor, TA406, was recently reported to have targeted Ukrainian government entities using similar phishing techniques.
ETLM Assessment:
Both campaigns are likely intended to support strategic intelligence efforts on behalf of North Korean regime stakeholders. TA406’s operation appears focused on collecting political intelligence to assess Ukraine’s determination in the ongoing conflict—potentially aiding North Korean decision-makers in evaluating whether Moscow might request further troop support.
Chinese hackers targeting drone supply chains in Taiwan
A newly released report reveals that a cyber espionage group, believed to have ties to the Chinese government, has conducted a series of supply chain attacks targeting software service providers and military-related firms in Taiwan and South Korea. The group, known as Earth Ammit, carried out two waves of attacks between 2023 and 2024, impacting sectors such as defense, satellite communications, heavy industry, media, technology, software services, and healthcare.
According to the researchers, Earth Ammit aimed to breach trusted networks through supply chain compromises, thereby gaining access to high-value targets and broadening its operational reach. Victims of these attacks face significant risks of data theft, including the exfiltration of credentials and screen captures. The first wave focused on infiltrating drone supply chains by compromising trusted vendors. The second wave targeted Taiwan’s satellite and defense industries using customized espionage backdoors.
ETLM Assessment:
In a related development, researchers also reported that multiple Chinese-linked state actors exploited a critical vulnerability in SAP NetWeaver to infiltrate critical infrastructure networks. Victims included natural gas distributors, water and waste management utilities in the UK, U.S.-based oil and gas firms, medical device manufacturers, and government ministries in Saudi Arabia responsible for investment and financial oversight. The campaign bears all the hallmarks of a high- level state-driven campaign, which is supposed to enable Chinese cyber forces to play a major role in a potential military conflict over Taiwan.
The Qilin Ransomware Impacts NSS Nagasaki Sempaku Sobi Co., LTD.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; NSS Nagasaki Sempaku Sobi Co., LTD. (https[:]//www[.]nssjpn[.]co[.]jp/), was compromised by Qilin Ransomware. NSS Nagasaki Sempaku Sobi Co., Ltd. is a well-established Japanese company specializing in ship interior outfitting and land-based construction projects. The compromised data consists of confidential and sensitive information related to the organization.

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
The Brain Cipher Ransomware Impacts D’Decor
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India, D’Decor (https[:]//www[.]ddecor[.]com/), was compromised by Brain Cipher Ransomware. D’Decor is one of the world’s leading manufacturers and exporters of home furnishing fabrics and products. Headquartered in India, the company has a strong global presence, supplying more than 65 countries worldwide. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 350 GB.

Relevancy & Insights:
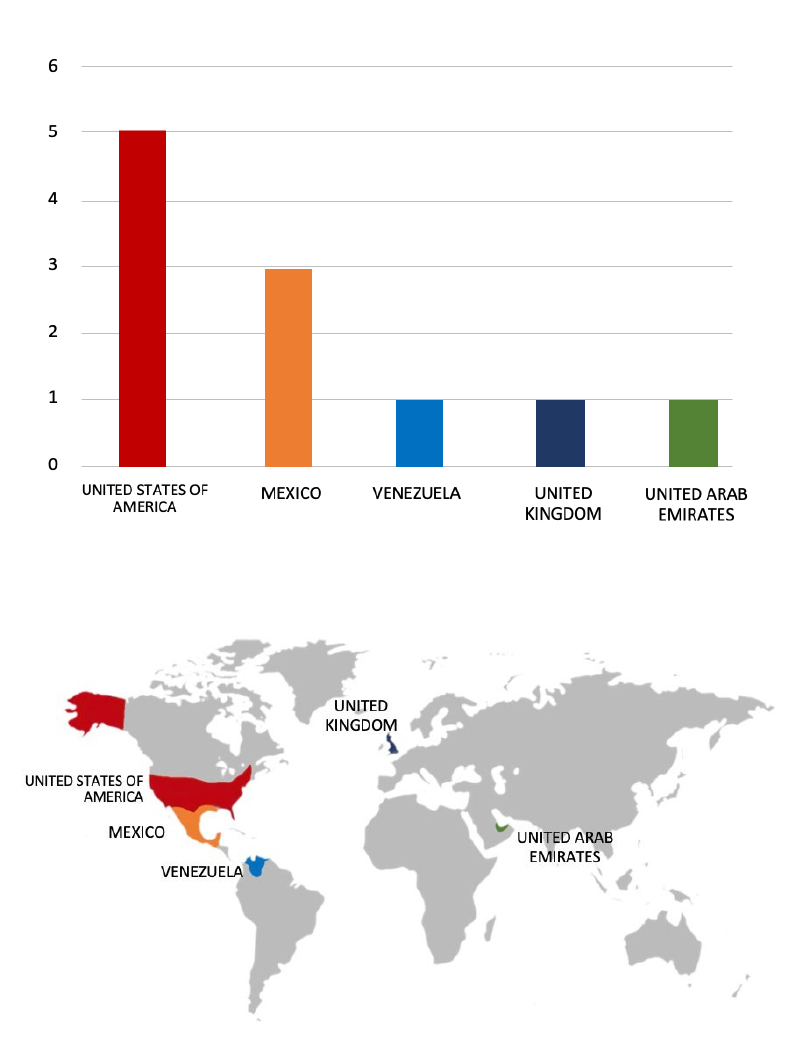
ETLM Assessment:
According to CYFIRMA’s assessment, Brain Cipher Ransomware represents a growing threat in the cybersecurity landscape, particularly due to its focus on critical infrastructure and government entities. Organizations must enhance their cybersecurity measures, including robust incident response plans and employee training on recognizing phishing attempts, to mitigate risks associated with this evolving threat.
Continuous monitoring and updating of security protocols are essential to defend against such sophisticated attacks.
Vulnerability in Ivanti Neurons for ITSM
Relevancy & Insights:
The vulnerability exists due to an error when processing authentication requests.
Impact:
A remote attacker can bypass the authentication process and gain unauthorized access to the application.
Affected Products:
https[:]//forums[.]Ivanti[.]com/s/article/Security-Advisory-Ivanti- Neurons-for-ITSM-on-premises-only-CVE-2025-22462?language=en_US
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
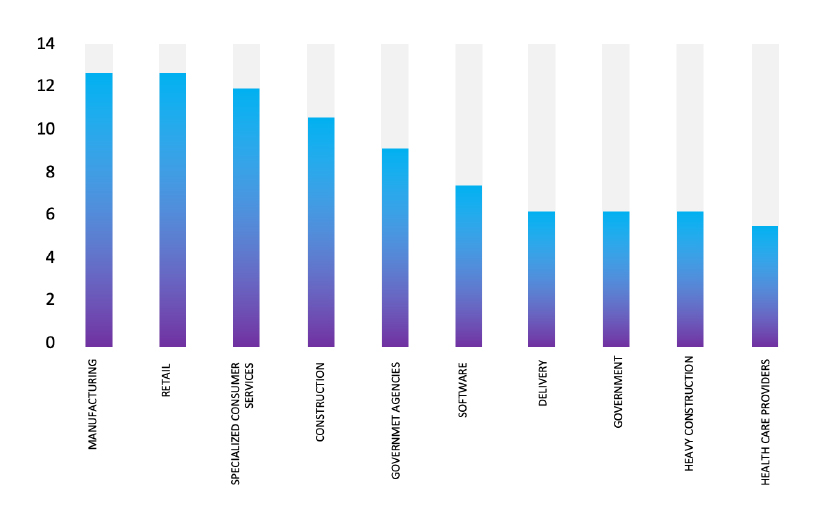
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
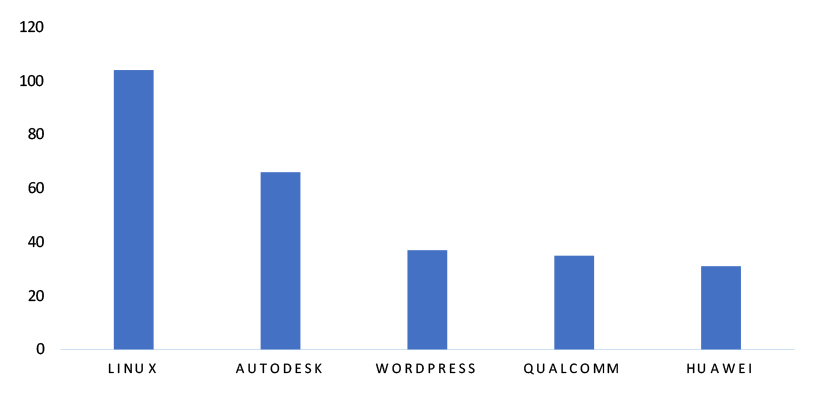
ETLM Assessment
Vulnerability in Ivanti can pose significant threats to user privacy and security. This can impact various industries globally, including government, healthcare, finance, and enterprise IT. Ensuring the security of Ivanti’s solutions is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding IT asset management, endpoint security, patch management, and service delivery operations across different geographic regions and sectors.
Everest Ransomware attacked and published the data of Jamjoom Pharma
Summary:
Recently, we observed that Everest Ransomware attacked and published the data of Jamjoom Pharma(https[:]//www[.]jamjoompharma[.]com/) on its dark web website. Jamjoom Pharma is a leading pharmaceutical manufacturing company headquartered in Saudi Arabia. It has quickly emerged as one of the largest and most prominent pharmaceutical players in the Middle East and Africa (MEA) region, with a direct and indirect presence in 36 countries, including key markets such as Saudi Arabia, the UAE, Egypt, and Iraq. The ransomware attack resulted in a data breach that exposed employees’ personal and confidential information. A total of 1,445 personal records were compromised. The leaked data includes details such as Employee ID, First Name, Joining Date, Job Grade, Mobile Number, Cluster, Department, Section, Job Title, Promotion Date, Email, Date of Birth, Appraisal Type, Employment Category, Employee Category, Location, Business Unit, Nationality, and Saudi/Non-Saudi classification. The total size of the compromised data is approximately 4.8 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest Ransomware remains a persistent and evolving threat in 2025. Despite the takedown of its leak site, the group continues to target new sectors, expand its operations as an initial access broker, and leverage data leak extortion as its primary tactic. Organizations should remain vigilant, strengthen access controls, monitor for lateral movement and Cobalt Strike activity, and ensure robust incident response capabilities to defend against Everest’s ongoing campaigns
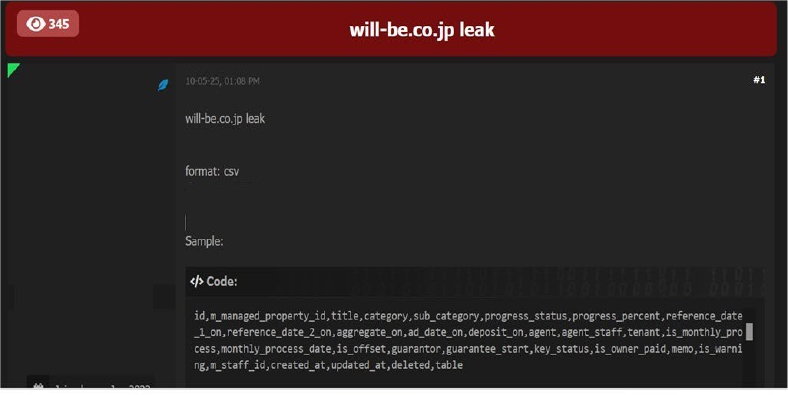
Will-Be Co., Ltd Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Will-Be Co., Ltd. (https[:]//will-be[.]co[.]jp/) in an underground forum. Will-Be Co., Ltd. is a Japan- based real estate company specializing in property leasing, sales, and management. Committed to a customer-first approach, the company focuses on building long-term relationships and offers professional support to both Japanese and international clients. The leaked data includes ID, managed property ID, title, category, subcategory, progress status, progress percentage, reference date, along with other sensitive and confidential information.
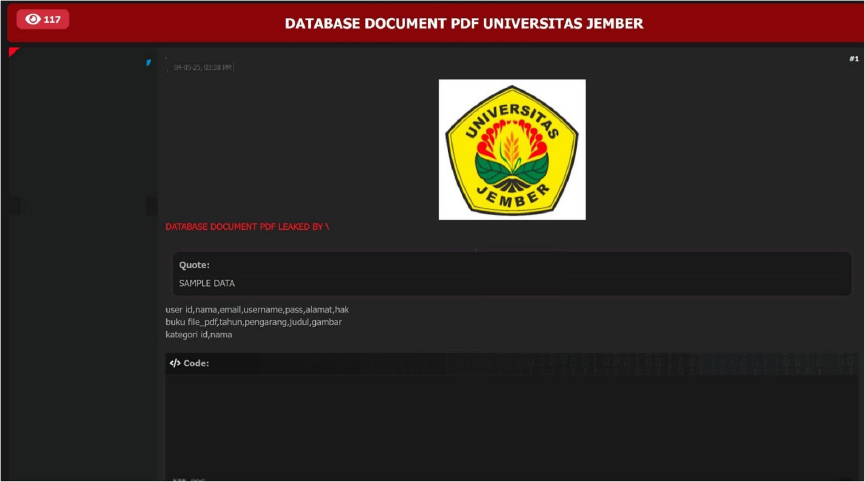
Indonesia’s Universitas Jember Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Universitas Jember (https[:]//www[.]psn[.]co[.]id/) in an underground forum. Universitas Jember (UNEJ) is a public university in Indonesia that has evolved into a leading institution recognized for its strong commitment to education, research, and community engagement. The threat actor claims to have leaked sensitive user and publication data from Universitas Jember on a dark web forum. The leak includes alleged admin credentials and academic documents. The breach has been linked to a threat actor identified as “VirXploit24.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “VirXploit24” has recently emerged as a highly active entity specializing in data leaks. Credible reporting links this group to multiple data breaches involving unauthorized access and the attempted sale of stolen data on dark web forums. Although “VirXploit24” is not yet widely documented in major threat intelligence roundups, its operational pattern aligns with current trends in cybercrime, where actors exploit vulnerabilities to exfiltrate sensitive information and monetize it through underground markets. Given this threat landscape, it is critical for organizations to maintain a robust cybersecurity posture. This includes continuous monitoring for suspicious activity, integrating timely threat intelligence, and implementing proactive defense strategies to protect critical data assets from emerging actors like “VirXploit24.”
Recommendations: Enhance the cybersecurity posture by:
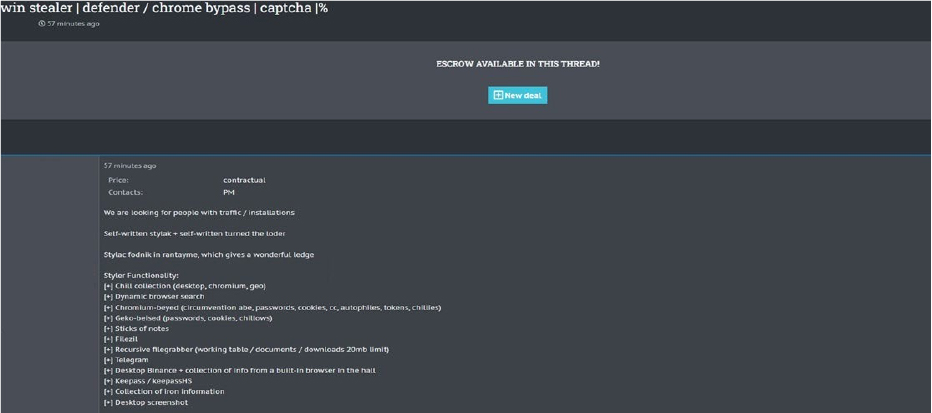
The CYFIRMA Research team observed an Alleged Sale of “Win Stealer,” a sophisticated malware that bypasses Windows Defender and Chrome security to steal passwords, cookies, credit card details, and authentication tokens from Chromium/Gecko browsers.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
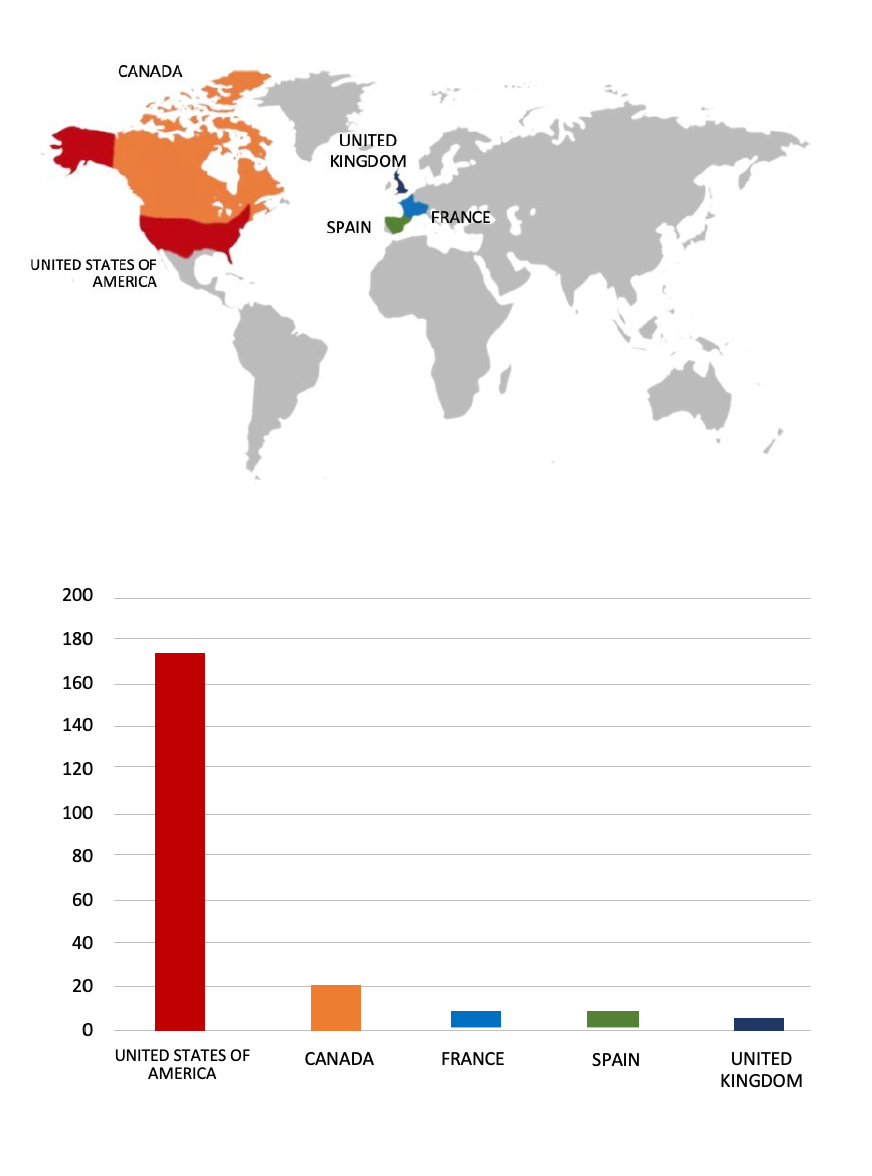
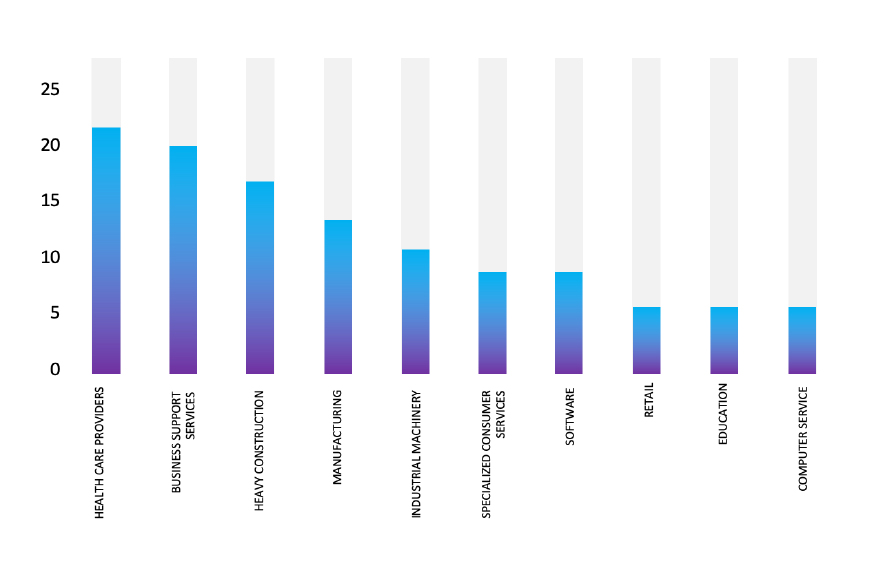
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.