


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows OS
Target Geography: North America, Europe, Asia-Pacific
Target Industry: BFSI, professional services, manufacturing, healthcare,
Introduction:
CYFIRMA Research and Advisory Team has found Karma (MedusaLocker) ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Karma (MedusaLocker) ransomware
Researchers have discovered a new ransomware strain called Karma (MedusaLocker) ransomware. Karma (MedusaLocker) ransomware is a financially motivated, enterprise- focused ransomware variant belonging to the MedusaLocker family that encrypts victim files using a hybrid RSA and AES cryptographic scheme and appends the “.KARMA” extension to affected data. After gaining access, typically through phishing, malicious attachments, or compromised network entry points, it conducts network-wide file encryption, changes the desktop wallpaper, and drops a ransom note (“HOW_TO_RECOVER_DATA.html”) claiming both data encryption and data exfiltration. The attackers threaten to leak or sell stolen sensitive information if payment is not made, offering limited free decryption as proof and increasing ransom demands after a fixed deadline. The operation is designed to pressure organizations into negotiated ransom payments, with no publicly available decryption tool and no guarantee of data recovery even if the ransom is paid.

Screenshot: File encrypted by ransomware (Source: Surface Web)
CYFIRMA’s assessment identifies Karma as a ransomware variant associated with the MedusaLocker family that encrypts victim files and appends the “.KARMA” extension to affected data, after which it deploys an HTML-based ransom note titled “HOW_TO_RECOVER_DATA.html” and modifies the desktop wallpaper to reinforce extortion messaging. The ransom note asserts that the victim’s corporate network has been penetrated and claims that files were encrypted using a hybrid RSA and AES cryptographic scheme, while explicitly warning victims not to rename encrypted files or attempt recovery using third-party tools, stating that such actions could result in permanent data corruption. The note further alleges that highly sensitive and confidential data has been exfiltrated and stored on a private server, threatening public disclosure or resale of the information in the event of non-payment, while claiming the data will be destroyed upon successful ransom payment. To intensify pressure, the operators impose a 72-hour deadline, after which the ransom amount is stated to increase, and they offer free decryption of 2–3 non-essential files as proof of their ability to restore access to encrypted data.
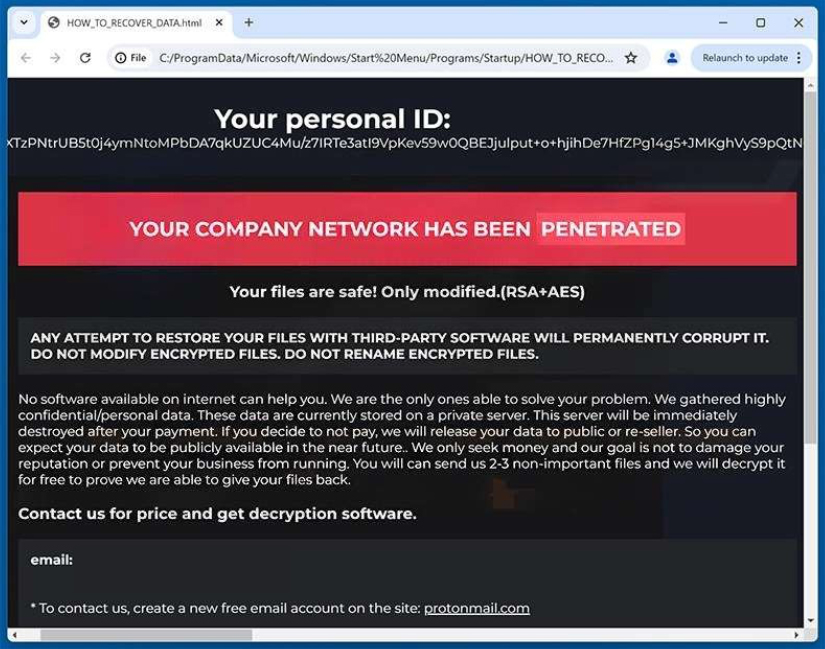
Screenshot: The appearance of Karma (MedusaLocker) ransomware‘s ransom note “HOW_TO_RECOVER_DATA.html “) (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID |
Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1614 | System Location Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment suggests that Karma (MedusaLocker) ransomware is likely to continue evolving as a data-extortion–centric ransomware operation, maintaining and potentially refining its dual-pressure model that combines file encryption with credible data-leak threats. The consistent use of hybrid cryptography, anonymized communication channels, proof-of-decryption offers, and strict time-bound ransom escalation indicates a mature and repeatable extortion framework designed to maximize victim compliance. Going forward, these operational characteristics position the group to sustain activity across enterprise environments, particularly where incident response maturity and backup hygiene are weak. The continued absence of a publicly available decryptor and reliance on backup-based recovery further enhance the group’s leverage, suggesting that Karma (MedusaLocker) will remain an effective and persistent threat within the broader ransomware ecosystem, with potential expansion in victim scale and extortion pressure rather than a shift in core tactics.
Sigma rule:
title: New RUN Key Pointing to Suspicious Folder detection:
selection_target: TargetObject|contains:
– ‘\Software\Microsoft\Windows\CurrentVersion\Run’
– ‘\Software\WOW6432Node\Microsoft\Windows\CurrentVersion\Run’
– ‘\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run’ selection_suspicious_paths_1:
Details|contains:
– ‘:\Perflogs’
– :\ProgramData’
– ‘:\Windows\Temp’
– ‘:\Temp’
– ‘\AppData\Local\Temp’
– ‘\AppData\Roaming’
– ‘:\$Recycle.bin’
– ‘:\Users\Default’
– ‘:\Users\public’
– ‘%temp%’
– ‘%tmp%’
– ‘%Public%’
– ‘%AppData%’ selection_suspicious_paths_user_1:
Details|contains: ‘:\Users\’ selection_suspicious_paths_user_2:
Details|contains:
– ‘\Favorites’
– ‘\Favourites’
– ‘\Contacts’
– ‘\Music’
– ‘\Pictures’
– ‘\Documents’
– ‘\Photos’ filter_main_windows_update:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\’ Image|startswith: ‘C:\Windows\SoftwareDistribution\Download\’ Details|contains|all:
– ‘rundll32.exe ‘
– ‘C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32’ Details|contains:
– ‘\AppData\Local\Temp\’
– ‘C:\Windows\Temp\’ filter_optional_spotify:
Image|endswith:
– ‘C:\Program Files\Spotify\Spotify.exe’
– ‘C:\Program Files (x86)\Spotify\Spotify.exe’
– ‘\AppData\Roaming\Spotify\Spotify.exe’ TargetObject|endswith:
‘SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Spotify’ Details|endswith: ‘Spotify.exe –autostart –minimized’
condition: selection_target and (selection_suspicious_paths_1 or (all of selection_suspicious_paths_user_* )) and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Software using weird folders for updates level: high
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Astaroth
Objectives: Messaging on WhatsApp
Target Technology: Android/
Windows OS
Target Geography: Brazil.
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Astaroth” is trending.
Overview of Operation Astaroth
Astaroth, a well-established Brazilian banking malware, has re-emerged in a recently identified campaign that introduces a significant change in its distribution approach. The threat actors have adopted WhatsApp Web as a propagation channel, reaffirming the malware’s strong focus on Brazilian users using widely trusted communication platforms and region-specific social engineering techniques.
In this campaign, victims are lured into opening malicious files delivered via WhatsApp messages. Once executed, the malware leverages the compromised WhatsApp environment to disseminate additional malicious files to the victim’s contacts, enabling rapid and self-sustaining spread while minimizing reliance on conventional phishing methods.
In parallel with its propagation activity, the malware conducts financially motivated operations by targeting users during online banking sessions. This dual capability highlights Astaroth’s continued evolution, combining efficient distribution mechanisms with persistent banking fraud objectives within a geographically focused threat landscape.
Attack Method
The campaign employs a multi-stage infection chain initiated by a heavily obfuscated Visual Basic Script embedded within a compressed archive distributed via WhatsApp. This downloader functions as the primary execution trigger, resolving obfuscation at runtime before retrieving multiple secondary components from remote infrastructure. Upon execution, it deploys both the core banking malware and an auxiliary propagation module, ensuring that credential theft and lateral spread capabilities are established early in the compromise lifecycle.
A distinctive feature of this operation is the integration of a Python-based propagation mechanism, deployed alongside a locally installed Python runtime. This module interfaces with the victim’s WhatsApp Web session to enumerate stored contacts and automate message delivery. The attacker-crafted logic generates context-aware messages that closely resemble legitimate user interactions, dynamically adjusting greetings based on local time to improve engagement and attachment execution rates.
Beyond propagation, the malware implements internal telemetry to monitor campaign effectiveness. The propagation module records delivery success rates, failure counts, and message throughput, periodically generating runtime statistics to track spread efficiency. In parallel, harvested contact data is transmitted to external command-and-control infrastructure, enabling attackers to maintain visibility into infection scale and refine targeting within the affected regional ecosystem.
The following are the TTPs based on the MITRE Attack Framework
| Tactic (ID) | Technique ID | Technique Name |
| Initial Access | T1204.002 | User Execution: Malicious File |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Persistence | T1543 | Create or Modify System Process |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1082 | System Information Discovery |
| Collection | T1005 | Data from Local System |
| Command and control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
ETLM ASSESSMENT
From an ETLM perspective, this activity signals a future environment in which trusted communication platforms increasingly serve as indirect conduits for threat exposure rather than overt attack surfaces. As employees rely more heavily on consumer messaging tools for routine coordination, organizations may experience heightened residual risk originating outside formal enterprise controls. Over time, this dynamic is likely to blur the separation between personal and professional digital spaces, expanding the scope of organizational risk while increasing the potential for employee-driven propagation, reputational impact, and operational disruption without clear indicators of compromise.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Astaroth_WhatsApp_Campaign_StringBased
{
meta:
description = “Detects Astaroth campaign artifacts using SHA256 hashes treated as strings and known domains”
campaign = “WhatsApp-based propagation”
strings:
/* Astaroth MSI Installer Hashes */
$h1 = “098630efe3374ca9ec4dc5dd358554e69cb4734a0aa456d7e850f873408a3553”
$h2 = “073d3c77c86b627a742601b28e2a88d1a3ae54e255f0f69d7a1fb05cc1a8b1e4”
$h3 = “bb0f0be3a690b61297984fc01befb8417f72e74b7026c69ef262d82956df471e”
/* WhatsApp Spreader (Python) Hashes */
$h4 = “c185a36317300a67dc998629da41b1db2946ff35dba314db1a580c8a25c83ea4”
$h5 = “5d929876190a0bab69aea3f87988b9d73713960969b193386ff50c1b5ffeadd6”
$h6 = “9081b50af5430c1bf5e84049709840c40fc5fdd4bb3e21eca433739c26018b2e”
$h7 = “3b9397493d76998d7c34cb6ae23e3243c75011514b1391d1c303529326cde6d5”
$h8 = “1e101fbc3f679d9d6bef887e1fc75f5810cf414f17e8ad553dc653eb052e1761”
$h9 = “01d1ca91d1fec05528c4e3902cc9468ba44fc3f9b0a4538080455d7b5407adcd”
$h10 = “025dccd4701275d99ab78d7c7fbd31042abbed9d44109b31e3fd29b32642e202”
$h11 = “19ff02105bbe1f7cede7c92ade9cb264339a454ca5de14b53942fa8fbe429464”
$h12 = “1fc9dc27a7a6da52b64592e3ef6f8135ef986fc829d647ee9c12f7cea8e84645”
$h13 = “3bd6a6b24b41ba7f58938e6eb48345119bbaf38cd89123906869fab179f27433”
$h14 = “4a6db7ffbc67c307bc36c4ade4fd244802cc9d6a9d335d98657f9663ebab900f”
$h15 = “4b20b8a87a0cceac3173f2adbf186c2670f43ce68a57372a10ae8876bb230832”
$h16 = “4bc87764729cbc82701e0ed0276cdb43f0864bfaf86a2a2f0dc799ec0d55ef37”
$h17 = “6168d63fad22a4e5e45547ca6116ef68bb5173e17e25fd1714f7cc1e4f7b41e1”
$h18 = “7c54d4ef6e4fe1c5446414eb209843c082eab8188cf7bdc14d9955bdd2b5496d”
$h19 = “a48ce2407164c5c0312623c1cde73f9f5518b620b79f24e7285d8744936afb84”
$h20 = “f262434276f3fa09915479277f696585d0b0e4e72e72cbc924c658d7bb07a3ff”
/* Contacted Domains */
$d1 = “centrogauchodabahia123.com”
$d2 = “coffe-estilo.com”
$d3 = “empautlipa.com”
$d4 = “miportuarios.com”
$d5 = “varegjopeaks.com”
condition:
any of ($h*) or any of ($d*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Fancy Bear (APT28) Phishing Campaign Exploiting Enterprise Authentication Portals
About the Threat Actor
FANCY BEAR is a well-documented Russian state-sponsored threat actor that has been active since at least 2007 and is widely assessed to operate in close coordination with Russian intelligence services. Security researchers have attributed multiple high-profile cyber operations to the group, including election interference activities in several countries, aimed at influencing political outcomes in favor of the Russian government.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023-38831 | WinRAR | 7.8 | Link |
| CVE-2021-4034 | pkexec application | 7.8 | Link 1, Link 2 |
| CVE-2016-5195 | Linux kernel | 7.0 | Link1, Link2, Link3, Link4, Link5, and Link6 |
| CVE-2020-0688 | Microsoft Exchange | 8.8 | Link 1 and Link 2 |
| CVE-2015-2545 | Microsoft Office | 7.8 | – |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1598.003 | Phishing for Information: Spearphishing Link |
| Reconnaissance | T1598 | Phishing for Information |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.008 | Compromise Infrastructure: Network Devices |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1091 | Replication Through Removable Media |
| Initial Access | T1199 | Trusted Relationship |
| Initial Access | T1078 | Valid Accounts |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Persistence | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Persistence | T1133 | External Remote Services |
| Persistence | T1137.002 | Office Application Startup: Office Test |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1078.004 | Valid Accounts: Cloud Accounts |
| Privilege Escalation | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Privilege Escalation | T1098.002 | Account Manipulation: Additional Email Delegate Permissions |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1037.001 | Boot or Logon Initialization Scripts: Logon Script (Windows) |
| Privilege Escalation | T1546.015 | Event Triggered Execution: Component Object Model Hijacking |
| Privilege Escalation | T1078.004 | Valid Accounts: Cloud Accounts |
| Defense Evasion | T1134.001 | Access Token Manipulation: Token Impersonation/Theft |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1221 | Template Injection |
| Defense Evasion | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.004 | Valid Accounts: Cloud Accounts |
| Credential Access | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1110.001 | Brute Force: Password Guessing |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1003.002 | OS Credential Dumping: Security Account Manager |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1528 | Steal Application Access Token |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Lateral Movement | T1091 | Replication Through Removable Media |
| Lateral Movement | T1550.001 | Use Alternate Authentication Material: Application Access Token |
| Lateral Movement | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Collection | T1557.004 | Adversary-in-the-Middle: Evil Twin |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1119 | Automated Collection |
| Collection | T1213 | Data from Information Repositories |
| Collection | T1213.002 | Data from Information Repositories: Sharepoint |
| Collection | T1005 | Data from Local System |
| Collection | T1039 | Data from Network Shared Drive |
| Collection | T1025 | Data from Removable Media |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1074.002 | Data Staged: Remote Data Staging |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1113 | Screen Capture |
| Command and Control | T1001.001 | Data Obfuscation: Junk Data |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1092 | Communication Through Removable Media |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1030 | Data Transfer Size Limits |
| Exfiltration | T1048.002 | Exfiltration Over Alternative Protocol: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol |
| Impact | T1498 | Network Denial of Service |
Latest Developments Observed
The threat actor is assessed to be deploying new credential-harvesting campaigns leveraging spoofed Microsoft Outlook Web Access (OWA), Google, and Sophos VPN login portals. Targeting is believed to be primarily focused on Türkiye and broader European regions, with sustained interest in organizations linked to energy research, defense collaboration, and government communication networks. The observed activity suggests an intelligence-gathering objective, likely aligned with Russian state intelligence requirements.
ETLM Insights
APT28 is a highly capable, state-aligned cyber espionage actor assessed to operate in support of Russian military and intelligence objectives. Unlike financially motivated groups, APT28’s operations are mission-driven, disciplined, and tightly aligned to geopolitical priorities. Their campaigns consistently focus on intelligence collection, influence positioning, and operational readiness, rather than immediate disruption.
From an ETLM perspective, APT28 represents a persistent external pressure actor— one that adapts quickly to defensive changes, shifts infrastructure rapidly, and deliberately operates within the gray zone between espionage and influence operations.
Going forward the approach ETLM indicators suggest APT28 will:
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule FancyBear_IOCs_Match
{
meta:
author = “CYFIRMA”
description = “Detects IOC artifacts associated with Fancy Bear” date = “2026-01-13”
threat_actor = “FANCY BEAR / APT28” strings:
// CVEs as text (if present in code, comments, exploit kits, etc.)
$cve1 = “CVE-2017-11882”
$cve2 = “CVE-2021-4034”
$cve3 = “CVE-2016-5195”
$cve4 = “CVE-2020-0688”
$cve5 = “CVE-2023-32315”
$cve6 = “CVE-2021-44228”
$cve7 = “CVE-2018-13379”
$cve8 = “CVE-2023-23397”
$cve9 = “CVE-2020-1472”
$cve10 = “CVE-2023-38831”
$cve11 = “CVE-2018-8174”
$cve12 = “CVE-2020-2021”
$cve13 = “CVE-2020-5902”
$cve14 = “CVE-2014-4114”
$cve15 = “CVE-2020-15505”
$cve16 = “CVE-2019-19781”
$cve17 = “CVE-2022-30190”
$cve18 = “CVE-2022-38028”
$cve19 = “CVE-2024-21412”
$cve20 = “CVE-2022-21587”
$cve21 = “CVE-2021-1675”
$cve22 = “CVE-2020-1380”
$cve23 = “CVE-2023-27350”
$cve24 = “CVE-2012-0158”
$cve25 = “CVE-2009-3129”
$cve26 = “CVE-2021-22555”
$cve27 = “CVE-2023-36025”
$cve28 = “CVE-2023-27351”
$cve29 = “CVE-2023-27992”
$cve30 = “CVE-2015-2545”
$cve31 = “CVE-2023-32231”
$cve32 = “CVE-2019-11510”
$cve33 = “CVE-2014-1761”
// IPs
$ip1 = “208.91.197.27”
$ip2 = “127.0.0.1”
$ip3 = “198.49.23.177”
$ip4 = “50.7.210.226”
$ip5 = “185.220.101.143”
$ip6 = “142.250.31.102”
// Domains
$domain1 = “jinjinpig.co.kr”
$domain2 = “cloud-mail.ink”
$domain3 = “background-services.net”
$domain4 = “futuresfurnitures.com”
// Suspicious Files
$file1 = “win32 exe”
$file2 = “hrm3jvh9v.dll”
$file3 = “ruodjxk.exe” condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($file*)
}
Recommendations Strategic
Management
Tactical
Chinese attacks on Taiwan’s energy infrastructure on the rise
According to a report from Taiwan’s National Security Bureau, cyberattacks originating from China against Taiwan’s energy sector surged by 900% in 2025 compared to the previous year. Many of these attacks took place during software update windows, when Chinese hackers exploited the upgrade process to inject malware into the systems. The malware was intended to provide continuous monitoring of Taiwan’s energy sector, including operational planning and mechanisms, material procurement processes, and the establishment of backup systems.
ETLM Assessment:
Taiwan is a hot spot for increased Sino-American rivalry. China wants to reunite with Taiwan because it sees it as a colony gone wild. These days, there is some degree of relationship between the two regions, and they also depend on each other economically. However, Beijing regularly threatens Taipei with heightened military drills in the Taiwan Strait in recent years. When Beijing feels that the “one China” principle has been violated, as it did in 2022 when Nancy Pelosi, the then-U.S. Speaker of the House of Representatives, became the first senior official to visit Taiwan in 25 years. The Chinese capital usually reacts with a show of force. Preparations for debilitating cyber-attacks in case of invasion are increasingly becoming part of the measures China regularly uses to intimidate Taiwan into submission.
Cambodia extradites alleged cybercriminal boss to China
Cambodia has extradited to China a billionaire businessman accused of leading a major fraud syndicate that operated forced-labor scam compounds in the country. The 38-year-old, Chen Zhi, is a Chinese national who acquired Cambodian citizenship in 2014, though his Cambodian citizenship has since been revoked. Last year, the US Justice Department indicted Chen and seized $15 billion worth of his bitcoin. His company, Prince Group, was also sanctioned by the US and the UK. The extradition appears to signal that Cambodia is starting to respond to international pressure, particularly from China, to tackle the country’s massive cyberscam industry. US authorities have alleged that Chen had connections to Chinese state officials, which may have prompted Beijing to push Cambodia to act. However, a wider crackdown on the Cambodian cyberscam sector remains unlikely, given that the industry has grown into a significant pillar of the national economy.
ETLM Assessment:
The situation in Cambodia shares notable parallels with recent raids on similar scam operations in Myanmar, though the scale and governmental responses differ significantly. In both countries, these cyberscam industries—often involving human trafficking, forced labor, and pig-butchering frauds—have flourished as economic mainstays in border regions, drawing international scrutiny from the US and China due to their ties to organized crime and state-linked figures.
However, while Cambodia’s action appears limited to high-profile extraditions like Chen’s, prompted by pressure from Beijing and Washington but unlikely to escalate into a broader crackdown given the sector’s economic importance, Myanmar’s military junta has pursued more aggressive, publicized raids throughout 2025. For instance, in November 2025, the junta raided scam hubs along the Thai border, arresting over 1,600 people in one operation alone and deporting thousands more, including many Chinese nationals, as part of a declared “zero tolerance” policy. By December, demolitions targeted notorious compounds like KK Park, freeing thousands of trapped workers amid calls for foreign governments to repatriate their citizens.
Qilin Ransomware Impacts Sugawara Laboratories
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Sugawara Laboratories (https[:]//www[.]sugawara-labs[.]co[.]jp/), was compromised by Qilin Ransomware. Sugawara Laboratories Inc. is an industrial measuring equipment manufacturer based in Japan, producing and selling high- precision measurement systems and testing instruments such as stroboscopes, dynamometers, and vibration testers. The compromised data contains confidential and sensitive information belonging to the organization.
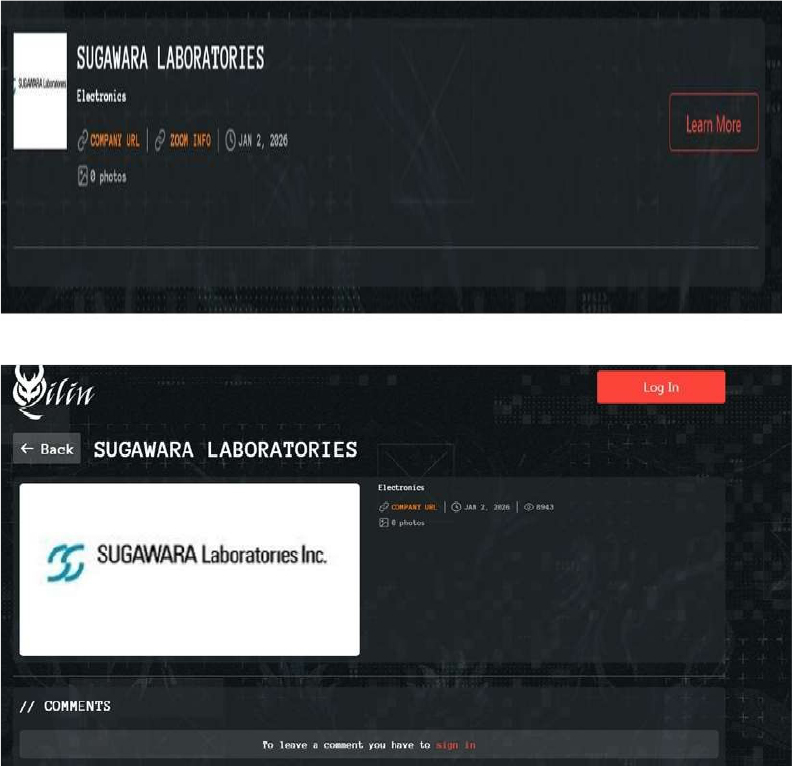
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Everest Ransomware Impacts Nissan Motor Corporation
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: Japan
Ransomware: Everest Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Nissan Motor Corporation (https[:]//www[.]nissan-global[.]com/), was compromised by Everest Ransomware. Nissan Motor Corporation is a multinational automobile manufacturer headquartered in Yokohama, Japan. The company, founded in 1933, produces a comprehensive range of vehicles, from luxury cars to commercial trucks. Nissan is known for its innovation in electric and autonomous driving technology. It includes brands like Infiniti and Datsun. It also has partnerships with Renault and Mitsubishi. The compromised data includes internal documents such as blueprints, financial records, and other sensitive materials, totaling 900 gigabytes of files.
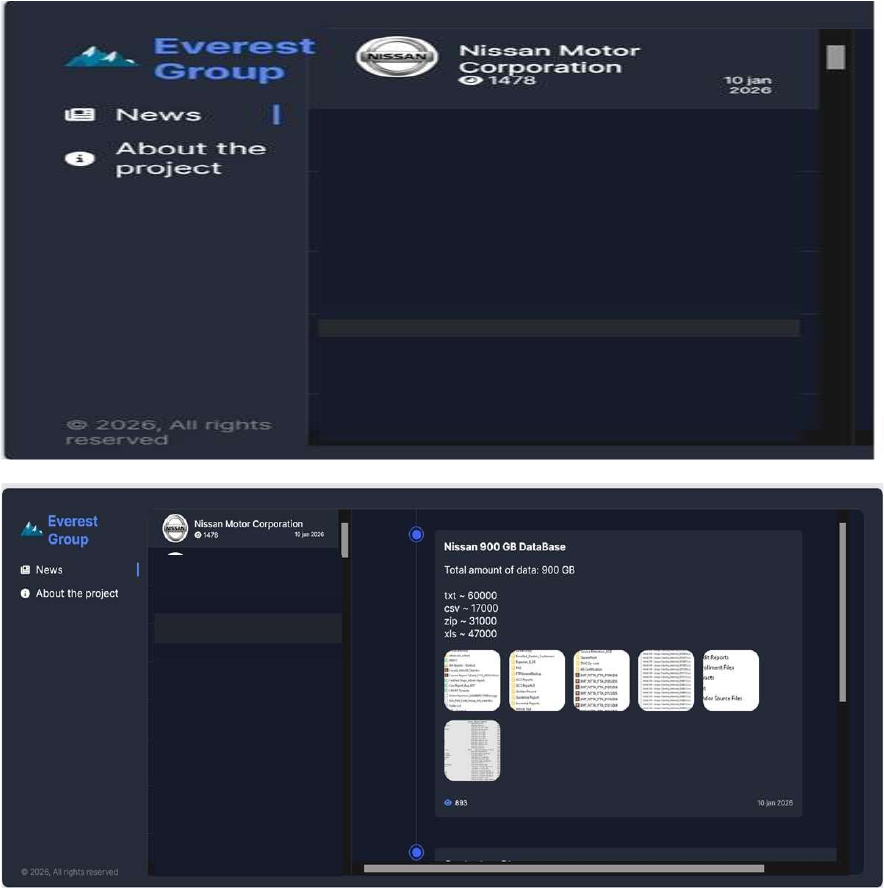
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest ransomware continues to pose a persistent and evolving cyber threat. The group is actively broadening its targeting across new sectors, expanding its role as an initial access broker, and increasingly relying on data-leak extortion as its core operational tactic. Organizations are advised to remain vigilant by strengthening access controls, closely monitoring for lateral movement and Cobalt Strike–related activity, and maintaining robust incident response and detection capabilities to mitigate the risks posed by Everest’s ongoing campaigns.
Vulnerability in Langflow
Attack Type: Vulnerabilities & Exploits
Target Technology: AI Agent Tool
Vulnerability: CVE-2026-21445
CVSS Base Score: 8.8 Source
Vulnerability Type: Missing Authentication for Critical Function
Summary:
The vulnerability allows a remote attacker to compromise the target system.
Relevancy & Insights:
The vulnerability exists due to missing authentication for a critical function in critical API endpoints.
Impact:
A remote attacker can gain access to sensitive user conversation data and perform destructive operations.
Affected Products:
https[:]//github[.]com/langflow- ai/langflow/security/advisories/GHSA-c5cp-vx83-jhqx
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behaviour that might indicate an attempted exploitation of this vulnerability.
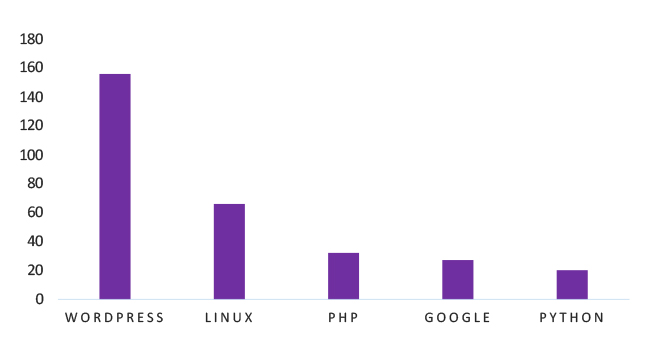
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Langflow can pose significant threats to application security and system integrity. This can impact various industries globally, including organizations leveraging AI-driven workflows, automation platforms, and language model orchestration frameworks. Ensuring the security of Langflow is crucial for maintaining the integrity and protection of application logic, data flows, and access controls across environments. Therefore, addressing these vulnerabilities is essential to safeguarding AI workflow management, operational reliability, and secure application deployment across different geographic regions and sectors.
Dire Wolf Ransomware attacked and published the data of Bina Darulaman Berhad Threat Actor: Dire Wolf Ransomware
Attack Type: Ransomware
Objective: Data Leak, Financial Gains
Target Technology: Web Applications
Target Industry: Civil Engineering Construction
Target Geography: Malaysia
Business Impact:
Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that Dire Wolf Ransomware attacked and published the data of Bina Darulaman Berhad (https [:]//www[.]bdb[.]com[.]my) on its dark web website. Bina Darulaman Berhad (BDB) is a Malaysian investment holding company listed on Bursa Malaysia (KLSE: BDB) focused on property development, construction, leisure, and sustainability initiatives. The ransomware incident resulted in the compromise of approximately 500 GB of data, encompassing Internal Documents, Insurance Policy Documents, Financial Documents, Email Backups, Legal Documents, Design Drawings, Confidential Documents, Supplier Documents, Employee Records, Audit Documents, Internal Agreements, Customer Data, Tax Filing Documents, Financial Records, and Personal Information.
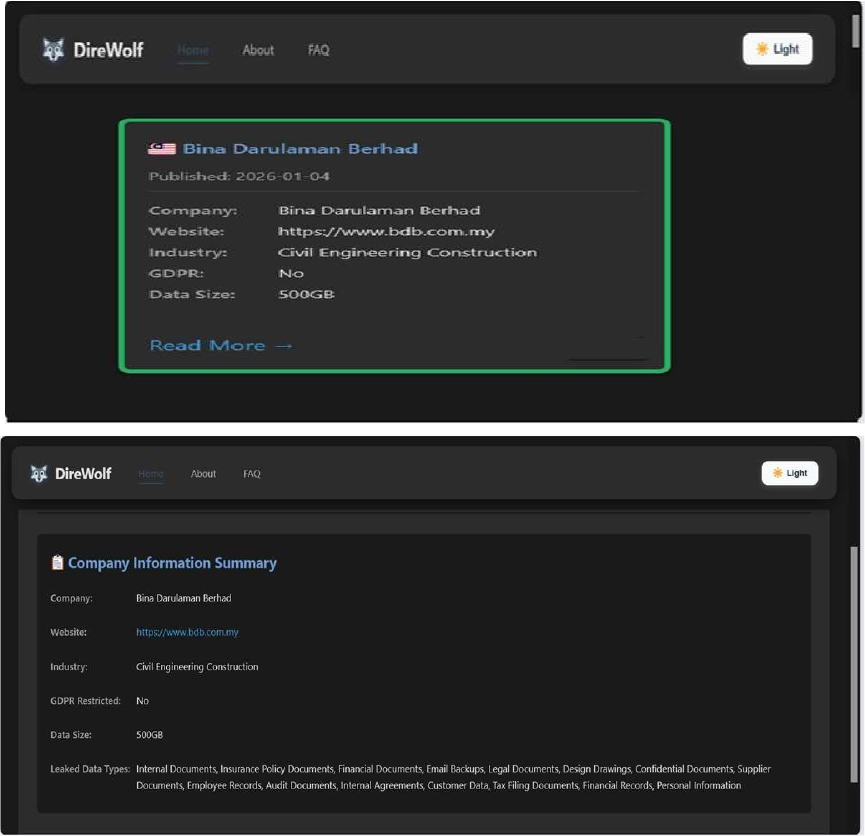
Source: Dark Web
Relevancy & Insights:
Dire Wolf is a newly emerged ransomware group that surfaced in May 2025. It operates an onion-based data leak site (DLS) where it posts information about its victims, including file trees, sample files, and descriptions of stolen data.
The Dire Wolf Ransomware group primarily targets industries, including Manufacturing, Industrial Machinery, Information Technology, Business Support Services, and Heavy Construction.
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
EMACHI Data Advertised on a Leak Site Attack Type: Data leak
Target Industry: Internet Media/Online Advertising
Target Geography: Japan
Objective: Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA research team has identified claims made by a threat actor operating under the alias “Solonik,” who alleges responsibility for a security breach involving e-machitown Co., Ltd. (emachi[.]co[.]jp). e-machitown Co., Ltd. operates a regional information portal in Japan that provides listings and information on local businesses, events, and town guides. According to the actor, the breach resulted in the exfiltration of a large database containing detailed information on local shop owners and their businesses, reportedly affecting more than 680,000 verified businesses.
The threat actor claims the compromised dataset contains extensive business and owner information related to Japanese local enterprises.
The allegedly exposed data includes:
The actor states the dataset:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.Top of FormBottom of Form
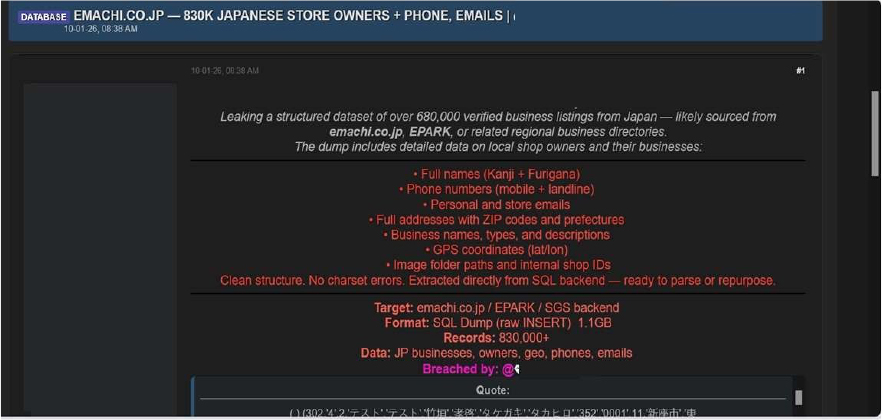
Source: Underground Forums
FUSE Group Data Advertised on a Leak Site
Summary
The CYFIRMA Research team has observed claims made by a threat actor using the alias “Solonik,” who alleges responsibility for a security breach involving the FUSE Group. FUSE Group (micro[.]fuse[.]co[.]id) is a prominent InsurTech provider in Southeast Asia, operating since 2017 with a presence across Indonesia, Malaysia, and Vietnam. According to the actor, the breach resulted in the exfiltration of sensitive data from the Simas Insurtech backend, including insurance policy applications, API activity logs, loan information, customer identification records, and direct links to policy documents in PDF format.
The allegedly compromised dataset is said to contain extensive customer personally identifiable information (PII), insurance loan records, and full credit policy metadata. The data reportedly includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
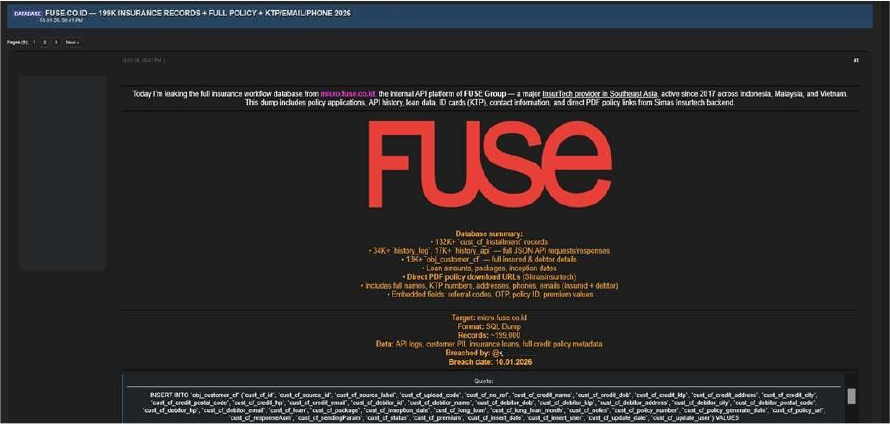
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor operating under the alias “Solonik” is assessed to be a newly emerged yet highly active and capable group, primarily focused on data-leak operations. Multiple credible sources have linked Solonik to a series of security incidents involving unauthorized access to organisational systems. The actor’s activities reflect the persistent and rapidly evolving cyber-threat landscape fueled by underground criminal ecosystems and underscore the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, enhanced threat-intelligence capabilities, and proactive defensive measures to safeguard sensitive data and critical infrastructure.
Recommendations:
Enhance the cybersecurity posture by:
Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
Ensure proper database configuration to mitigate the risk of database-related attacks.
Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
The CYFIRMA Research team observed that Rmoney India, an Indian fintech platform, has allegedly been compromised in a significant data security incident. On January 8, 2026, the organization was listed on a dark web forum by a threat actor who claims to have exfiltrated the company’s full production database. The breach reportedly involves a 1.5GB SQL dump encompassing multiple schemas, including insurance data, online KYC records, and WhatsApp bridge integrations.
According to the actor, the leaked database contains sensitive Personally Identifiable Information (PII) and internal records. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
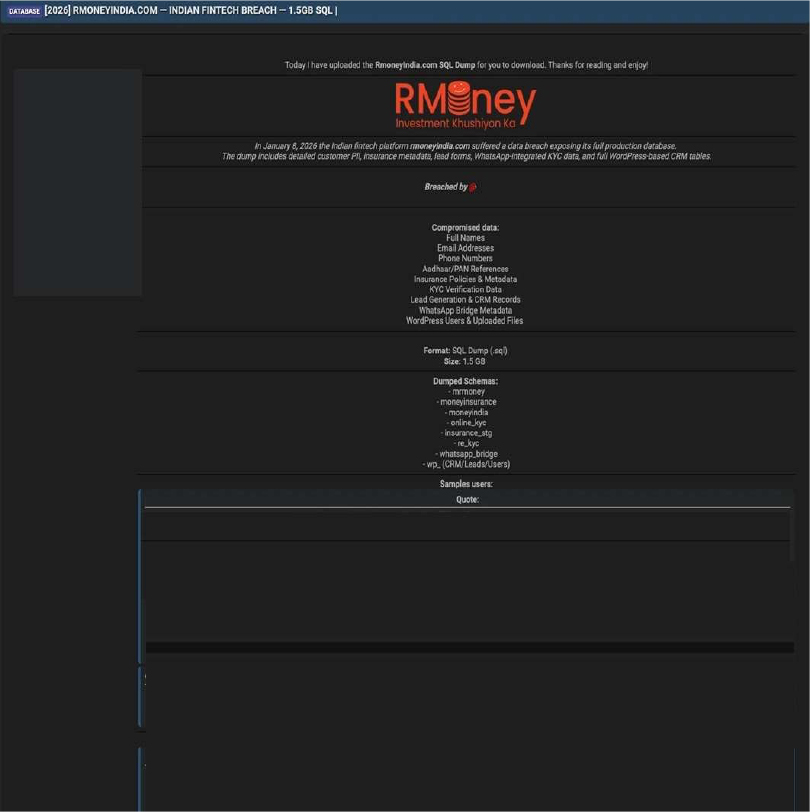
Source: Underground Forums
The CYFIRMA Research team has identified that ASML, a Dutch multinational corporation and the world’s leading supplier of photolithography systems and critical equipment for the semiconductor industry, has allegedly been the target of a significant data leak. A threat actor on a cybercrime forum claims to have published approximately 154 databases belonging to the technology giant. The leaked files, which are reportedly in SQL format, were posted for download with instructions on how to convert them for viewing.
According to the actor, the allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
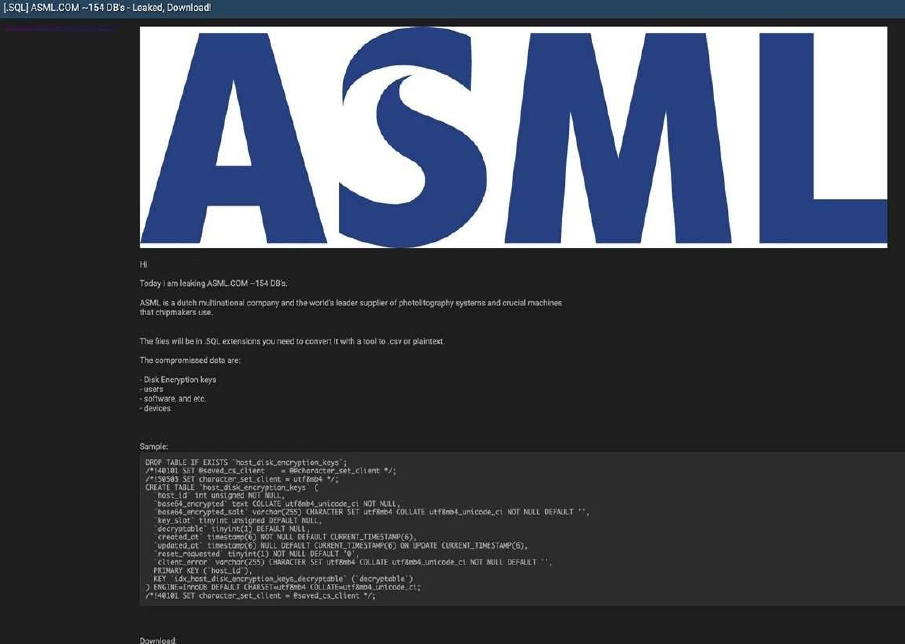
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
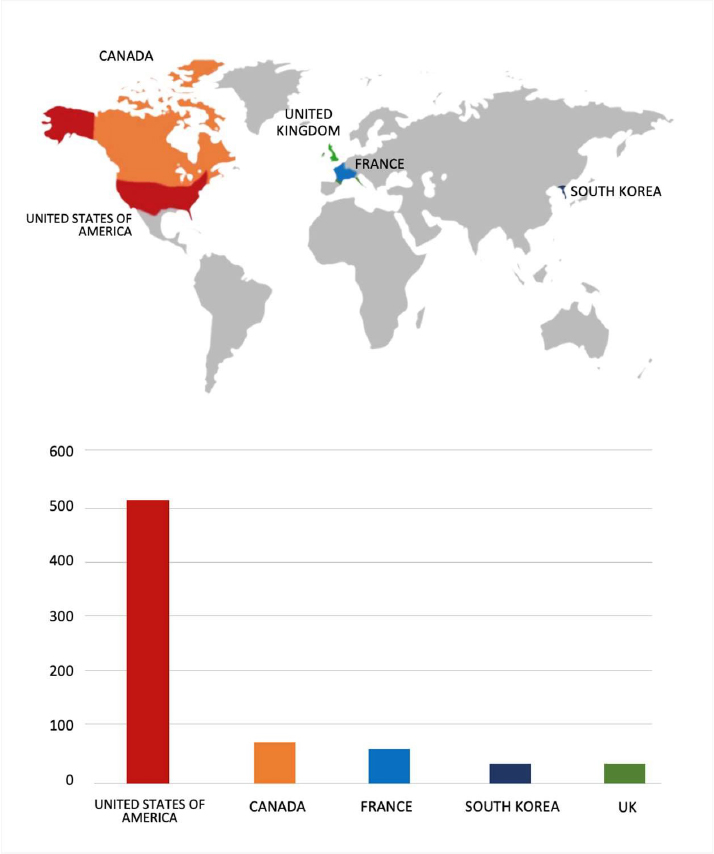
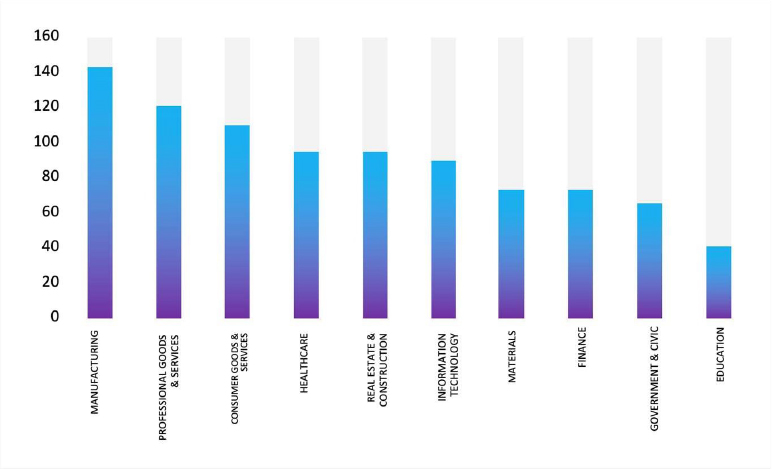
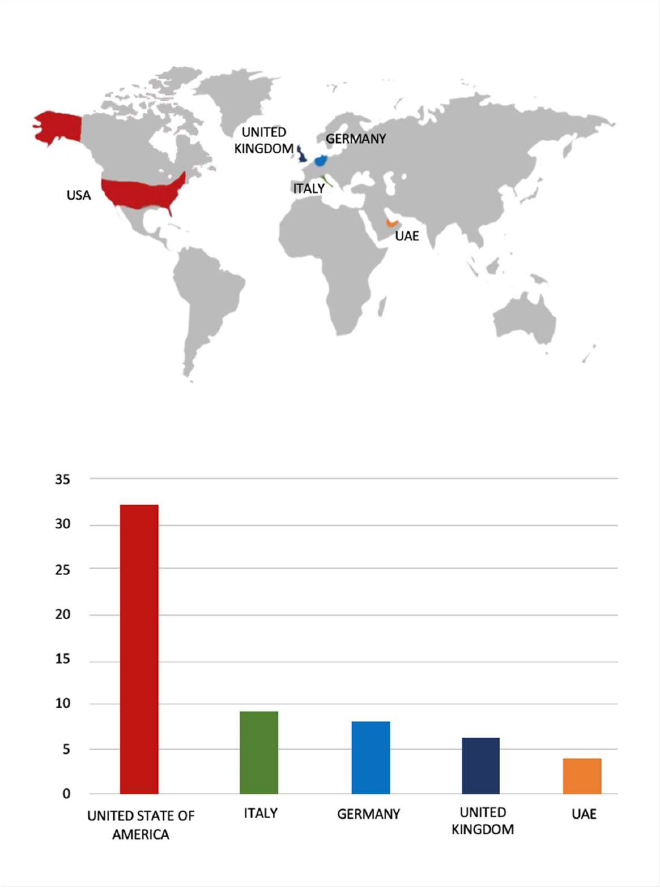
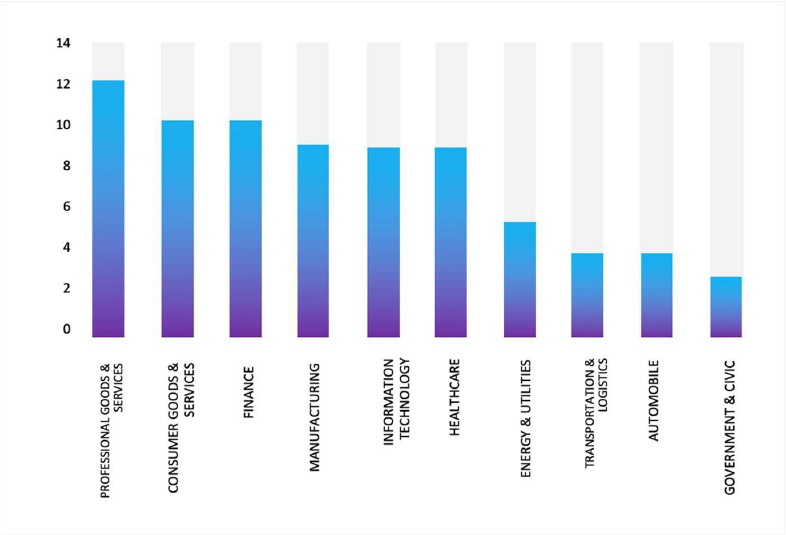
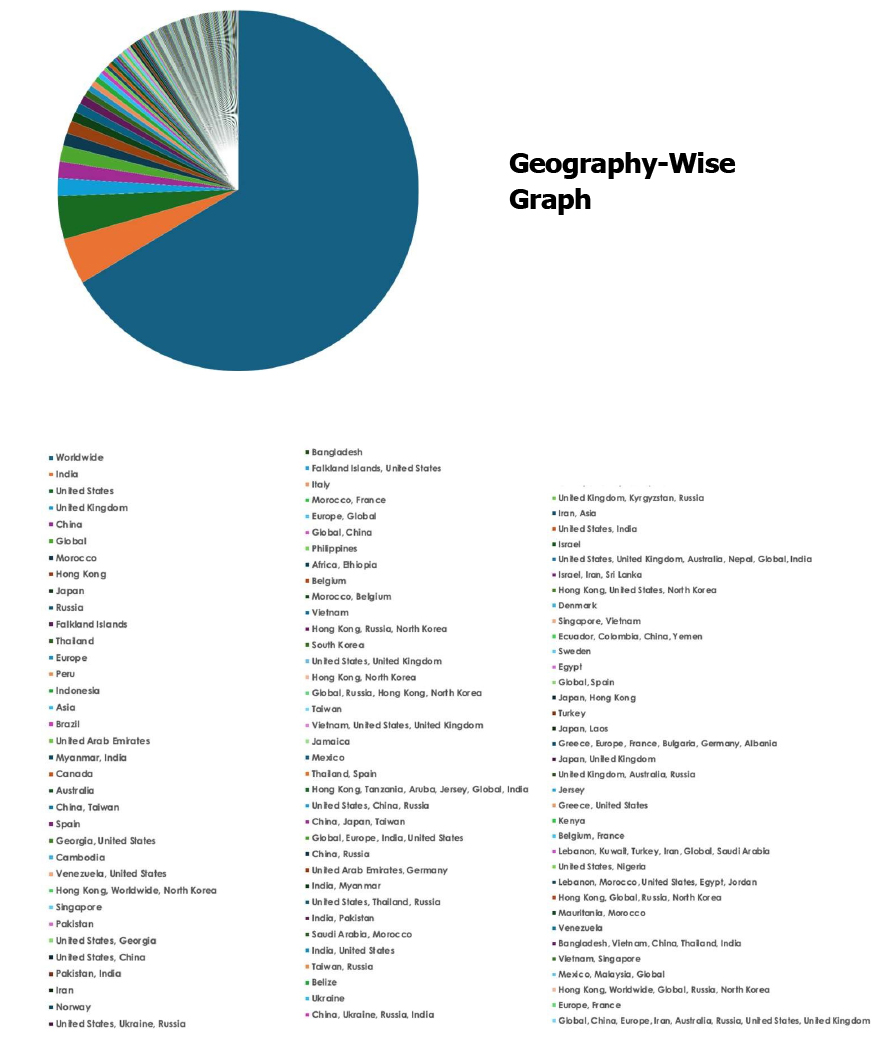
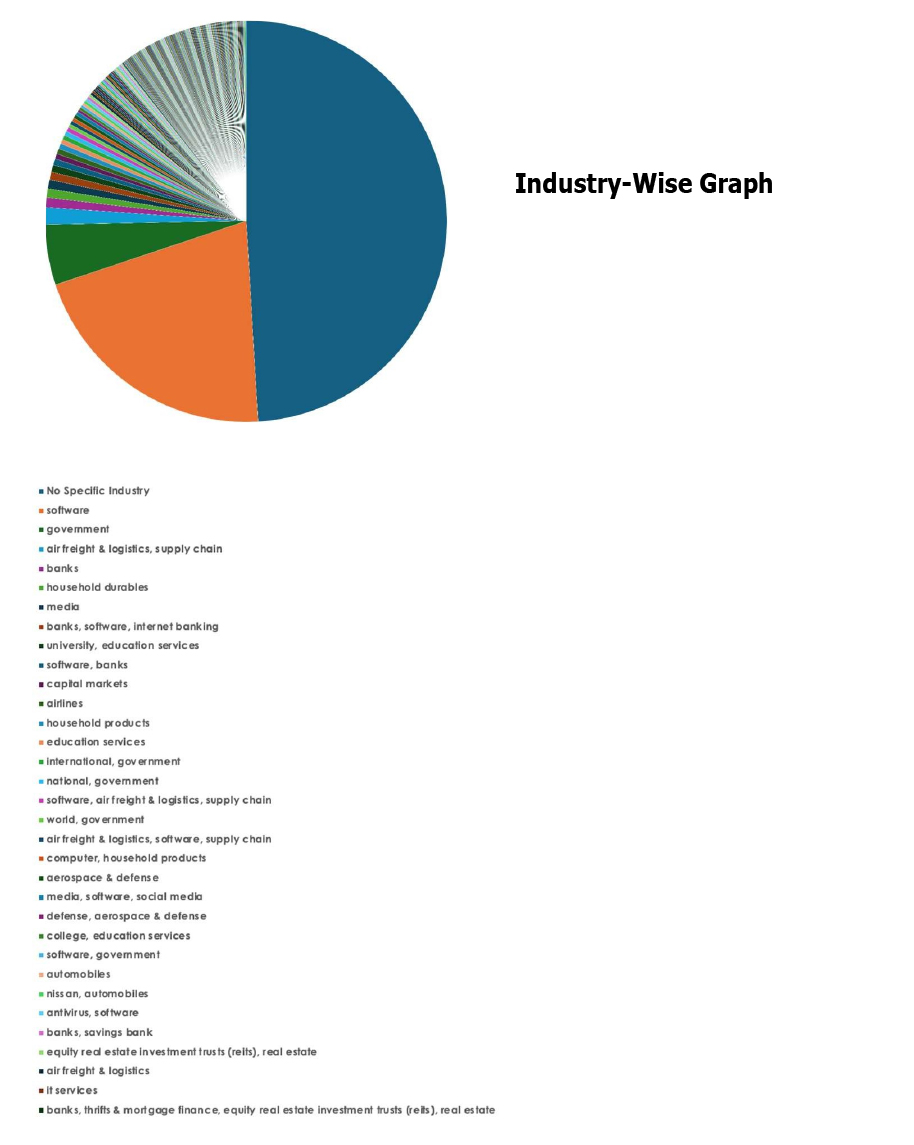
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.