



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Albabat ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Albabat Ransomware
Albabat, also recognized as White Bat is a financially motivated ransomware variant coded in Rust. It made its debut in November 2023 with the initial variant, Version 0.1.0. Subsequently, Version 0.3.0 was introduced in late December, followed by Version 0.3.3 in mid-January 2024.
The ransomware appears to be distributed as rogue software, like a fake Windows 10 activation tool or a cheat program for the game Counter-Strike 2.
The ransomware samples were submitted to a publicly available file scanning service, and it appears to be primarily targeting companies and individuals in Argentina, Brazil, the Czech Republic, Germany, Hungary, Kazakhstan, Russia, and the United States. However, since it masquerades as fake software, the ransomware has the potential to impact anyone.
Once the ransomware is executed, it looks for files to encrypt. It avoids encrypting the following file types:
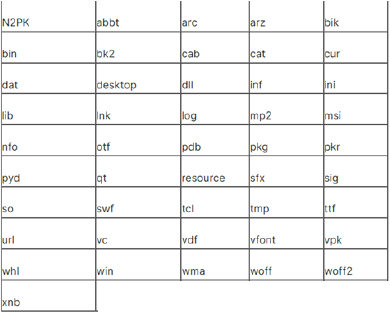
(Source: Surface web)
In versions 0.3.0 and 0.3.3, specific file types listed below are exempted from encryption:
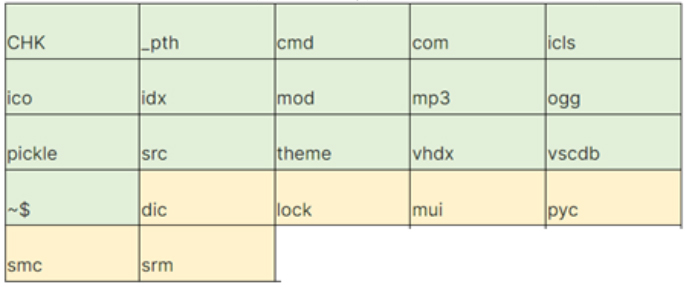
Note that the file types highlighted in light green are excluded in version 0.3.0. The file types highlighted in light yellow are additional files excluded in version 0.3.3.(Source: Surface web)
The Albabat ransomware appends a “.abbt” file extension to the files it encrypts. Additionally, the ransomware swaps out the desktop wallpaper with its own and creates the “README.html” file (a ransom note).
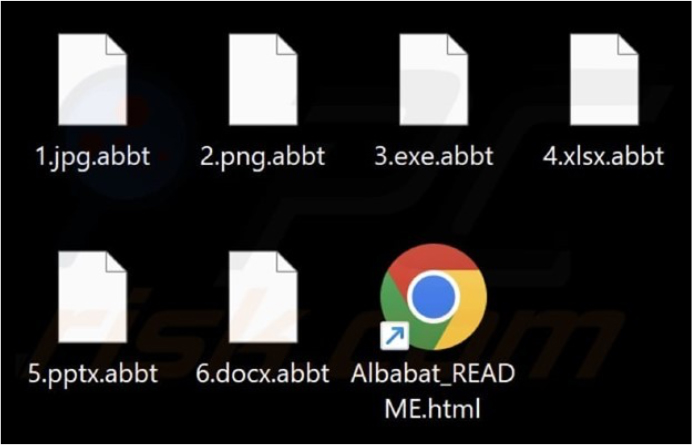
Screenshot of files encrypted by Albabat ransomware (Source: Surface Web)
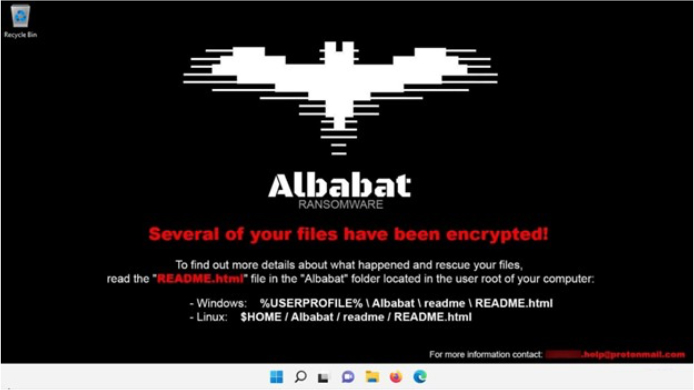
Desktop wallpaper replaced by the Albabat ransomware version 0.3.0 (Source: Surface Web).
The wallpaper displayed by the Albabat ransomware asserts compatibility with both Windows and Linux platforms. However, researchers haven’t found any Linux samples yet. Considering that the ransomware is coded in the Rust language, which allows for cross- compilation across different operating systems, there is a possibility that a Linux version might be released in the future.
In Version 0.1.0, the ransomware attempts to terminate Chrome.exe. Starting from Version 0.3.0 onwards, it also makes efforts to terminate the following additional processes:
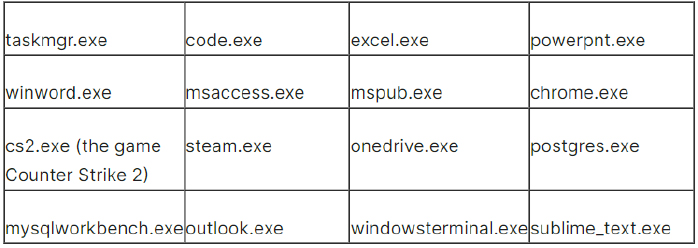
(Source: Surface web)
Version 0.3.0 and later also stops the following services:
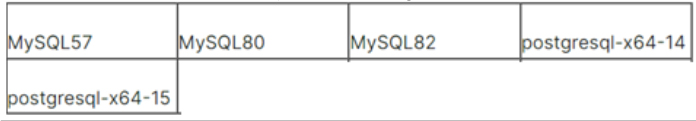
(Source: Surface web)
Beginning with version 0.3.0, the ransomware might engage in theft from or alteration of the following files:
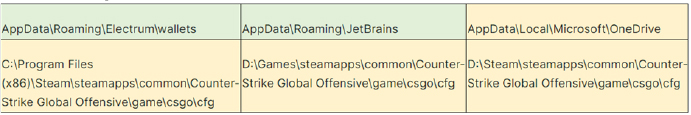
(Source: Surface web)
After completing the encryption process, the ransomware deposits the following files:
Version 0.1.0
Version 0.3.0
Version 0.3.3
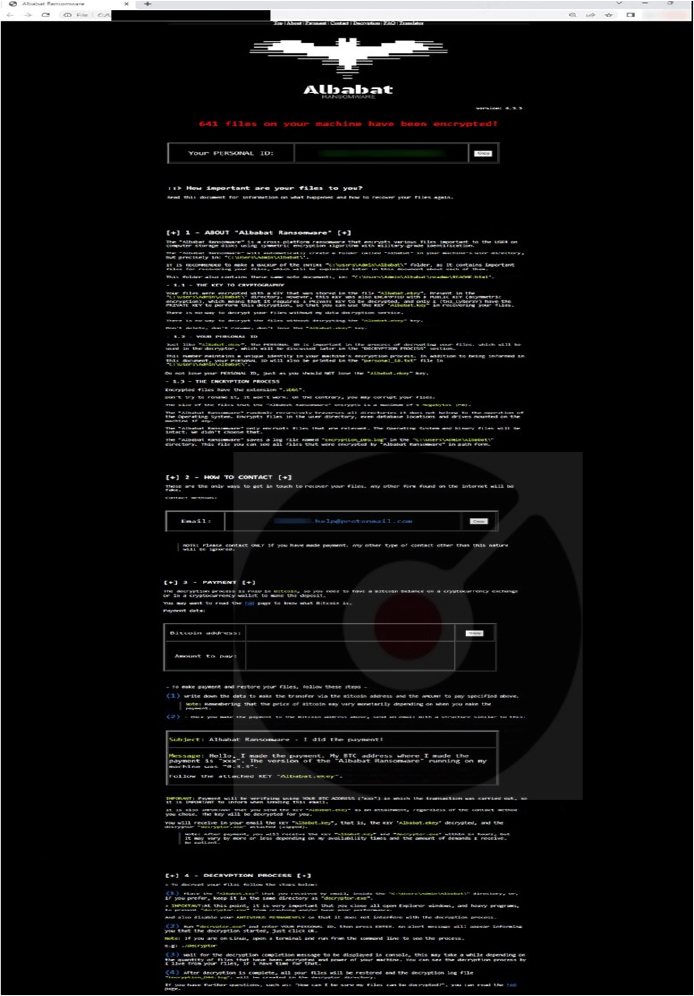
Recent Ransom note (Source: Surface web)
The ransom note features a translation option utilizing the Google Translate service, facilitating translation into over 100 languages. When opting for translation, Portuguese is automatically chosen, suggesting that this may be the primary language of the ransomware developer.
Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1106: Native API | ||
| T1569.002: System Services: Service Execution | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| 3 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| 4 | TA0005: Defense Evasion | T1006: Direct Volume Access |
| T1027: Obfuscated Files or Information | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 6 | TA0007: Discovery | T1012: Query Registry |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1119: Automated Collection | ||
| T1560: Archive Collected Data | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1490: Inhibit System Recovery | ||
| T1491: Defacement |
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that Albabat ransomware is likely to evolve further, with potential releases targeting additional countries. As the ransomware is written in Rust and capable of cross-compilation, the threat to Linux systems may increase. Continuous improvements in evasion techniques and enhanced functionalities are expected. Organizations should prioritize robust cybersecurity measures and regular threat intelligence updates to mitigate the risk of falling victim to such attacks.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Espionage, Data theft
Threat Actor: Roaming Mantis (aka Shaoye)
Target Technology: Android OS
Target Geographies: Japan, South Korea, France, Germany, India
Active Malware of the Week
This week “MoqHao (aka Wroba, XLoader)” is trending.
Summary
The MoqHao malware family, which has existing for several years, continues to evolve with increasingly sophisticated tactics to elude detection and target users. Notably, there is a surge in the number of C2 commands compared to previous versions, along with the utilization of legitimate platforms like Pinterest for storing and updating phishing data. The code exhibits potential targeting of Asian countries such as Japan and South Korea, as well as countries like France, Germany, and India. The latest variant is anticipated to have a significant impact as it infects devices upon installation without requiring user execution.
MoqHao
MoqHao, also known as Wroba and XLoader (not to be confused with the Windows and macOS malware of the same name), is an Android-based mobile threat associated with the financially motivated Chinese cluster known as Roaming Mantis (aka Shaoye). Initially detected in 2015, MoqHao has a history of targeting Asian countries, specifically Korea and Japan. Researchers have identified a new version of the MoqHao Android malware linked to the Roaming Mantis threat actor group. Traditionally, users were required to install and launch the malicious app to initiate its activities. However, this new variant employs a dangerous technique where malicious activity starts automatically upon installation, without the need for user execution. The distribution method remains consistent, involving sending a link via SMS to download the malicious app. Notably, this technique, previously introduced, is now being exploited by other active malware campaigns, expanding the threat beyond MoqHao.
Attack Method
MoqHao is distributed through phishing SMS messages, commonly referred to as Smishing. When a user receives a message containing a malicious link and clicks on it, the device downloads the malicious application.

Fig: Smishing message impersonating a notification from a courier service.
A notable change in their approach is the use of URL shortener services. Unlike using their own domain, which can be easily blocked, employing legitimate URL shorteners poses a challenge, as blocking the short domain may impact all URLs associated with that service. When a user clicks on the link in the message, the URL shortener service redirects them to the actual malicious site.
This variant of MoqHao differs from previous versions in its behavior. While typical MoqHao requires manual launch by the user after installation, this variant automatically initiates upon installation without requiring user interaction.
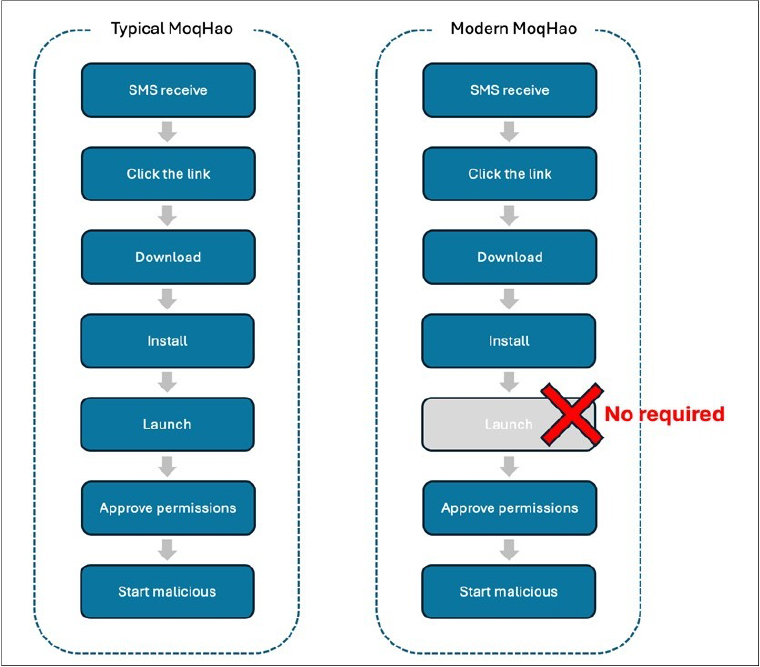
Fig: Differences between typical MoqHao and Modern MoqHao
Android is structured to check for the uniqueness of a specific value used by an app upon installation. MoqHao, a highly active Trojan family, exploits this feature to auto-execute itself without requiring user interaction. This recent variant of MoqHao involves distribution, installation, and auto-execution.
This recent MoqHao variant employs a new approach in using Unicode strings in app names, resulting in certain characters appearing bold and visually resembling “Chrome.” This technique poses a challenge to app name-based detection methods that rely on comparing app names (such as “Chrome”) with package names (like com.android.chrome).
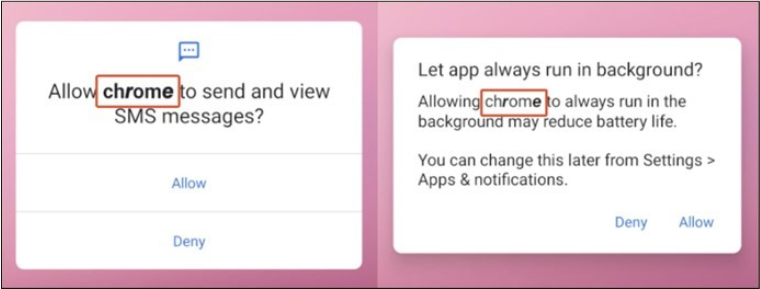
Fig: App name using Unicode strings.
Furthermore, the attackers employ social engineering techniques to designate malicious apps as the default SMS app. Prior to the appearance of the settings window, a deceptive message prompts users to set up the app under the guise of preventing spam, even though the message is fraudulent.
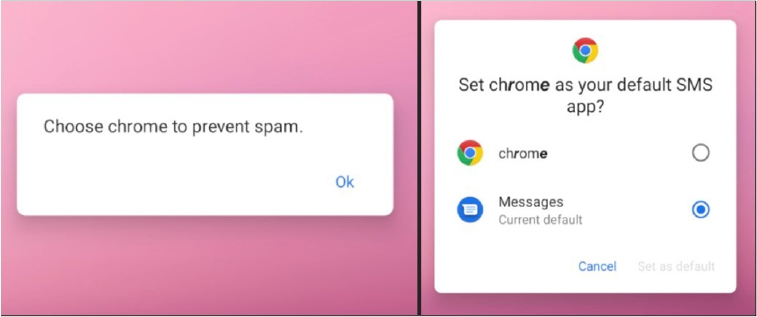
Fig: Fake message using social engineering techniques.
The varied languages used in the text related to this behavior indicate that, apart from Japan, the attackers are also targeting South Korea, France, Germany, and India.
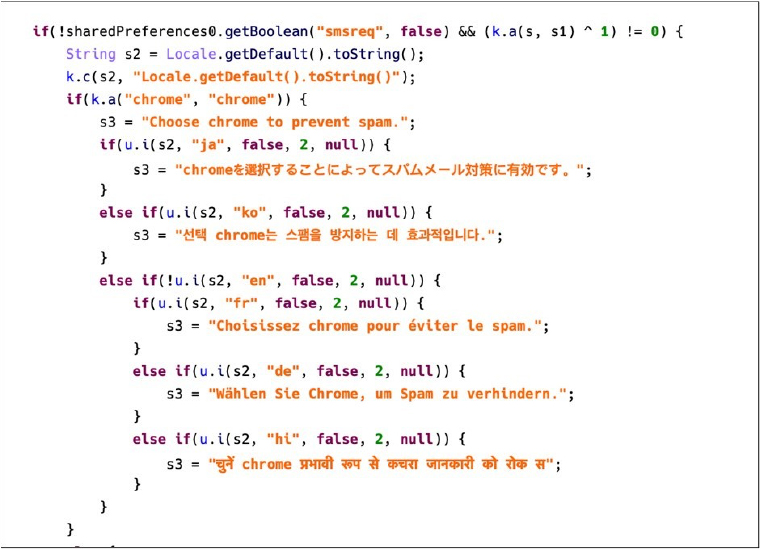
Fig: Fake messages designed to target different countries.
Once the malware initialization process is finished, it establishes a notification channel for the purpose of displaying phishing messages.
Fig: Create a notification channel for the next phishing attack.
The malware assesses the device’s carrier and utilizes notifications tailored to send phishing messages, deceiving users into clicking on them. MoqHao retrieves both the phishing message and URL from Pinterest profiles.
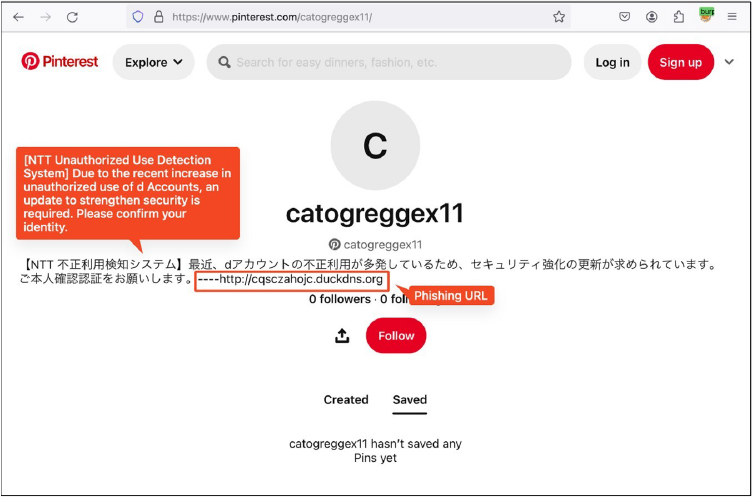
Fig: Phishing message and URL in Pinterest profile
In cases where the phishing string is empty, MoqHao resorts to using the phishing message present in the code.
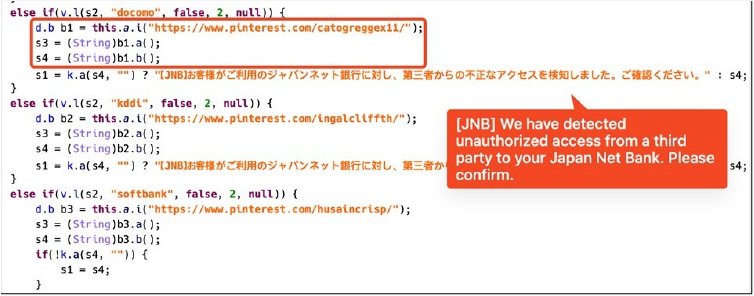
Fig: Phishing notification code for each carrier
This variant of the malware establishes a connection to the C2 server through WebSocket. It has been verified that, along with the commands from previous versions, several additional commands have been incorporated.
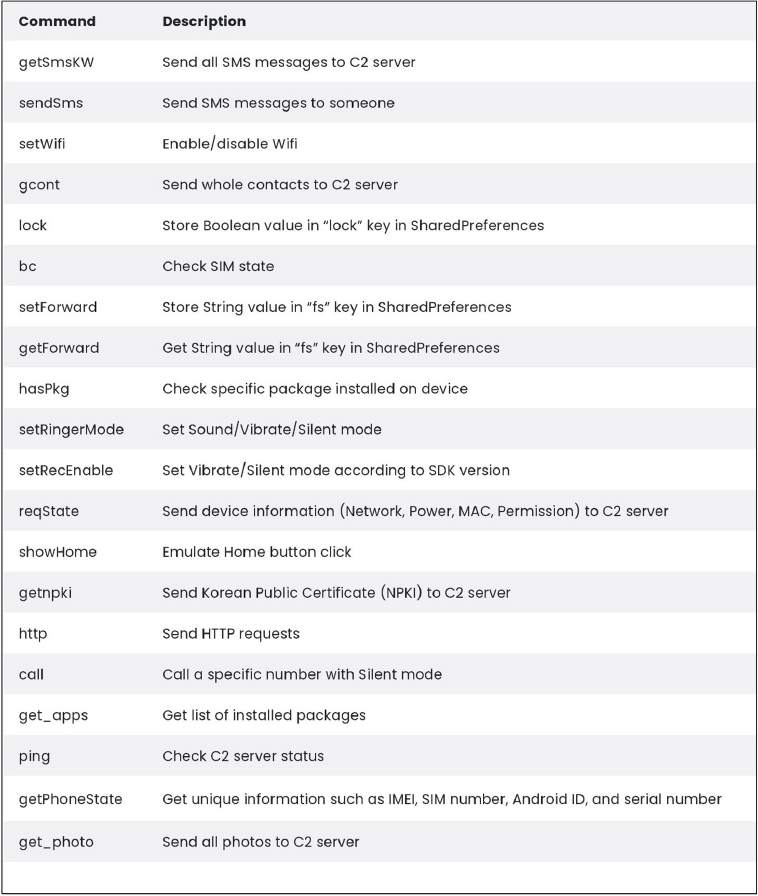
Fig: Updated Commands list
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that in today’s interconnected digital landscape, the threat of cyber smishing and scams has become a significant concern. This diversity in target regions underscores the malware’s global impact and its capability to adjust its focus based on geopolitical considerations. However, there is a potential for malware, including sophisticated campaigns like MoqHao and Roaming Mantis, to introduce new features in the future, expanding their target base beyond current limits. The risk of similar attacks to the ones implemented by MoqHao and Roaming Mantis is likely to increase, emphasizing the importance of proactive cybersecurity measures.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
Security Awareness training should be mandated for all company employees. The training should ensure that employees:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Unraveling the Complex Tactics of a Cyber-Espionage Campaign: The Intricacies of the Zardoor Malware
Summary:
A sophisticated cyber-espionage campaign has been targeting an Islamic charitable organization in Saudi Arabia, utilizing a newly discovered backdoor malware called Zardoor. The attackers, deemed advanced by researchers, have been active since at least May 2023 demonstrating expertise in creating new malware, customizing open- source tools, and employing living-off-the-land techniques to evade detection.
The primary motive behind the campaign appears to be intelligence gathering, as evidenced by the periodic exfiltration of data from the targeted Islamic charitable non- profit organization. The primary target of the espionage campaign is an unnamed Islamic charitable non-profit organization based in Saudi Arabia. This indicates a focus on entities operating within the Middle East region, particularly those associated with Islamic causes or humanitarian efforts. The targeted industry encompasses charitable and non-profit organizations.
The cyber-espionage campaign initiated through an undisclosed method, with the threat actor leveraging the Zardoor backdoor malware to establish persistent access within the targeted organization’s network. To orchestrate their command-and-control framework, they adeptly repurposed open-source reverse proxy tools like Fast Reverse Proxy (FRP), sSocks, and Venom. Their customization efforts, particularly with sSocks, involved eliminating dependencies on Visual C Runtime libraries, ensuring smooth execution without encountering runtime errors. Utilizing Windows Management Instrumentation (WMI) for lateral movement and remote command execution, the threat actor deployed backdoors such as zar32.dll and zor32.dll is the main backdoor component that communicates with the attacker’s C2 and sustaining access.
Additionally, they utilized various tactics, including system service manipulation and scheduled task creation, to ensure prolonged persistence. Notably, they manipulated scheduled tasks to register their reverse proxies, enabling communication with their command and control (C2) servers every 20 minutes. This included replacing existing tasks named “KasperskySecurity” or “Microsoft Security Essentialss” with a new task named “msbuildss.exe” for the proxy. Furthermore, researchers observed the threat actor storing the remote server’s public key, facilitating access to SSH servers for remote port forwarding. This enhancement allowed external servers and devices to access resources within the private network, significantly bolstering the threat actor’s remote access capabilities.
Relevancy & Insights:
The emergence of an unknown threat actor utilizing open-source tools and developing new malware underscores the evolving landscape of cybersecurity threats. With low confidence in attributing their actions to existing groups, the utilization of common tools highlights the challenge of distinguishing between different threat actors. Moreover, their development of new malware highlights the continuous arms race between attackers and defenders, emphasizing the need for vigilant cybersecurity measures to detect and mitigate emerging threats effectively.
ETLM Assessment:
An unknown threat actor is carrying out a sustained cyber espionage campaign targeting an Islamic organization, notably focusing on a non-profit entity in Saudi Arabia. The motivation behind this targeting could be linked to geopolitical interests, potentially aimed at disrupting religious beliefs and sowing chaos. The operation includes the deployment of undisclosed malware backdoors, leading to significant compromises and data breaches. Enforcing strict policies on resource usage is vital to effectively mitigate these threats. Moreover, it is imperative to emphasize the importance of vigilant management of the external threat landscape to defend against evolving cyber threats and potential collaboration among sophisticated adversaries.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Five Eyes publish report on Volt Typhoon
The US Cybersecurity and Infrastructure Security Agency (CISA), NSA, FBI, and the
cybersecurity directorates of Australia, Canada, New Zealand, and the UK have published a joint advisory outlining the Chinese state-sponsored threat actor Volt Typhoon’s operations against US critical infrastructure.
According to the advisory, the U.S. authoring agencies have confirmed that Volt Typhoon has compromised the IT environments of multiple critical infrastructure organizations – primarily in Communications, Energy, Transportation Systems, and Water and Wastewater Systems Sectors – in the continental and non-continental United States and its territories, including Guam. Volt Typhoon’s choice of targets and pattern of behaviour is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions. The U.S. authoring agencies are concerned about the potential for these actors to use their network access for disruptive effects in the event of potential geopolitical tensions and/or military conflicts. The US agencies note that the threat actor has been “maintaining access and footholds within some victim IT environments for at least five years.”
The Canadian Centre for Cyber Security assesses that the direct threat to Canada’s critical infrastructure from PRC state-sponsored actors is likely lower than that to U.S. infrastructure, but should U.S. infrastructure be disrupted, Canada would likely be affected as well, due to cross-border integration. ASD’s ACSC and NCSC-NZ assess Australian and New Zealand critical infrastructure, respectively, could be vulnerable to similar activity from PRC state-sponsored actors.
ETLM Assessment:
Last year, Volt Typhoon and other APTs like Mustang Panda have been focused on countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has allegedly been targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command, 20 times in a single year, while many other incursions have probably never been found. As we have warned in an earlier report, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way it could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting of critical infrastructure in Guam could affect U.S. military operations in significant way.
Iran refines cyber operations against Israel, US sanctions Iranian cyber officials
According to researchers, Iran has accelerated its cyber operations against Israel over the course of the Israel-Hamas war. In the immediate aftermath of the October 7 Hamas attack on Israel and the subsequent war, most of Iran’s immediate operations were hasty and chaotic. However, Iran has achieved growing success. Despite early Iranian claims, many ‘attacks’ in the early days of the war were either ‘leaking’ old material, using pre-existing access to networks or were false. However, Iran’s activity quickly grew from 9 groups, monitored by researchers and active in Israel during the first week of the war to 14, just weeks into the war. Cyber-enabled influence operations went from roughly one operation every other month in 2021 to 11 in October 2023 alone. The cyber campaign entails an almost 50% increase in traffic, in the first week of the war, to news sites run by or affiliated to the Iranian state.
ETLM Assessment:
As the war progresses, Iranian actors are expanding their geographic scope to include attacks on Albania, Bahrain and the USA. They also increased their collaboration, enabling greater specialization and effectiveness. In response, the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) recently announced sanctions against six Iranian officials from the Islamic Revolutionary Guard Corps Cyber- Electronic Command (IRGC-CEC) for their role in cyber-attacks on U.S. soil. The officials, members of the hacker group Cyber Av3ngers, disabled Unitronics programmable logic controllers (PLC) at a booster station operated by the Municipal Water Authority of Aliquippa, Pennsylvania in the attack. PLCs control pumps and valves in U.S. water and wastewater infrastructure and have been exploited in past destructive cyberattacks. The hackers appear to have targeted the PLCs because Unitronics is an Israeli company. The group also targeted ten water treatment stations in Israel around the time of its attack on Aliquippa. The new sanctions will prohibit companies that want to operate in the United States from conducting business with the six named Iranian officials.
The BianLian Ransomware impacts the J.P. Original
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]jpo[.]com), was compromised by the BianLian Ransomware. J.P. Original; makers of the popular labels Bamboo, Anne Michelle, Sunny Feet, Society 86, and Dollhouse, is one of the leading shoe manufacturers in the marketplace since 1986. The compromised data includes financial data, HR data, clients’ and partners’ data, business data, design images, mailboxes, internal and external email correspondence, and other confidential information. The total size of the compromised data is approximately 1.2 terabytes (TB).
The following screenshot was observed published on the dark web:
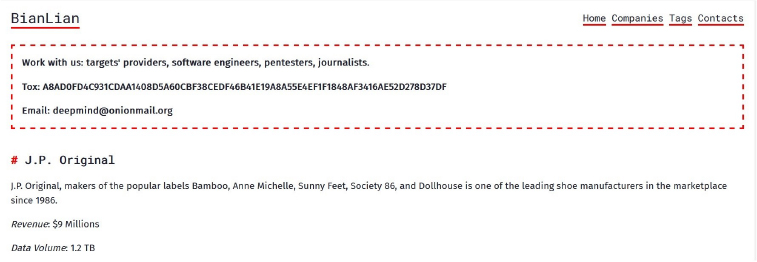

Source: Dark Web
Relevancy & Insights:
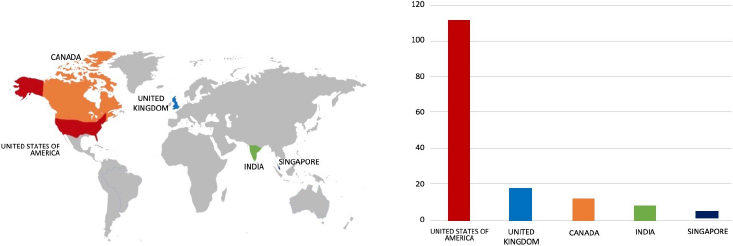
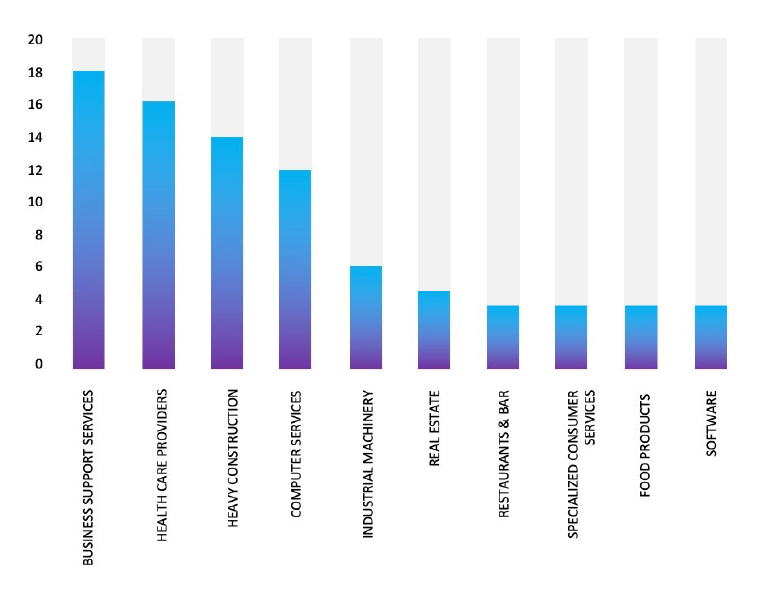
ETLM Assessment:
BianLian; a ransomware strain developed in GoLang, persistently infiltrates various industries, demanding substantial ransom payments. Employing the double extortion strategy, threat actors pilfer an organization’s files and threaten to leak them online if the ransom is not promptly paid. BianLian gains entry to victim systems through valid Remote Desktop Protocol (RDP) credentials, utilizing open-source tools and command-line scripting for discovery and credential harvesting. The exfiltration of victim data is executed via File Transfer Protocol (FTP), Rclone, or Mega. CYFIRMA’s assessment indicates that BianLian Ransomware will continue its focus on global businesses and related entities, holding significant amounts of Personally Identifiable Information (PII), financial data, or other sensitive information. Nevertheless, the recent attack on J.P. Original underscores the substantial risks posed by BianLian Ransomware to companies in advanced economies.
Vulnerability in Liferay Portal and Liferay DXP
Summary:
The vulnerability allows a remote attacker to gain unauthorized access to otherwise restricted functionality.
Relevancy & Insights:
The vulnerability exists due to improper access restrictions in the “doAsUserId” URL parameter.
Impact :
A remote user can impersonate a user after accessing the linked content. Affected Products: https[:]//liferay[.]dev/portal/security/known-vulnerabilities/-/asset_publisher/jekt/content/cve-2024-25148
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
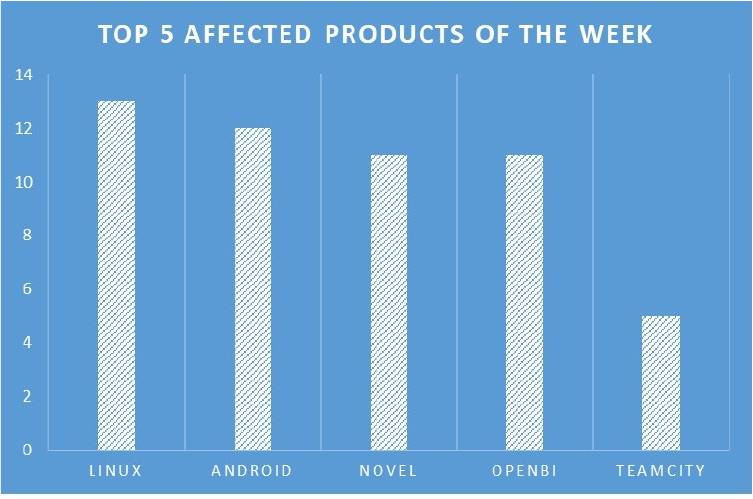
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
Black Basta claims ransomware attack on Hyundai Motor Europe
Summary:
Black Basta ransomware gang claims the hack of the car maker; Hyundai Motor Europe, and the theft of three terabytes of their data. In January the company experienced IT issues, the ransomware attack likely caused the outage, The crooks provided evidence of the data breach, it seems that the gang stole data from various departments, including legal, sales, and human resources. The carmaker launched an investigation into the incident with the help of external cybersecurity and legal experts.
Relevancy & Insights:
Since April 2022, the Black Basta ransomware group has remained active, employing a double-extortion attack model common to other ransomware operations. This malicious entity utilizes various deployment methods, including the use of Cobalt Strike or similar frameworks, as well as leveraging email phishing techniques. Notably, Black Basta is frequently introduced as a secondary infection, with instances observed following a Qakbot infection, underscoring the sophistication and adaptability of its attack vectors.
ETLM Assessment:
Black Basta; a ransomware group that operates primarily in the Russian-speaking domain, has gained notoriety for its attacks on various industries. This malicious group, known for deploying the Black Basta ransomware, has demonstrated a propensity to target a diverse array of sectors, including healthcare, government, financial services, education, and media. According to assessments by CYFIRMA, there is a significant likelihood that Black Basta will persist in its efforts to compromise companies on a global scale, aiming to secure substantial financial gains through their ransomware activities.
OpenSea Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to OpenSea, {www[.]opensea[.]io}. OpenSea is the first peer-to-peer marketplace for blockchain- based assets, which include collectibles, gaming items, digital art, domain names, event tickets, and physical assets backed by a blockchain. The data available for purchase includes email addresses, subscriber registration dates, and various other confidential details. The asking price for this dataset is 2,000 USD.
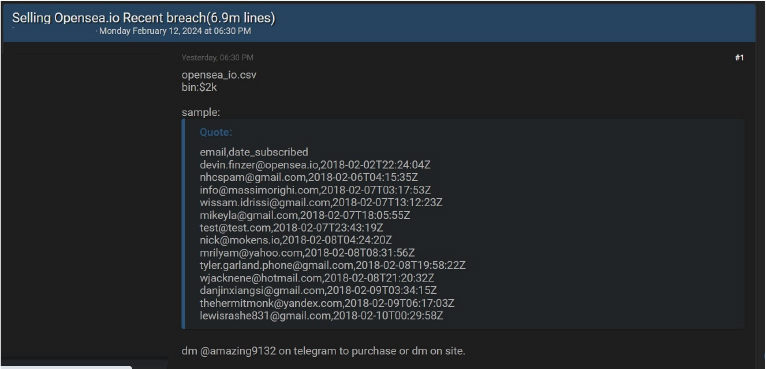
Source: Underground forums
Relevancy & Insights:
Financially motivated cybercriminals systematically monitor unprotected and vulnerable systems and applications, enticed by the prospect of monetary rewards. Many of these perpetrators actively engage in clandestine online forums, participating in discussions and transactions centred around pilfered digital assets. What sets these cybercriminals apart from other groups motivated by financial gains, such as ransomware or extortion groups, is their preference for operating discreetly. They leverage vulnerabilities in systems or applications to access valuable data, which is later advertised for sale on underground forums. Consequently, this unlawfully obtained data is repurposed by other attackers for their campaigns.
ETLM Assessment:
Bossmoves90004 is an emerging threat actor motivated primarily by financial gains, and they are presently involved in actively trading Open Sea data within illicit online forums. According to CYFIRMA’s assessment, U.S. institutions lacking robust security measures and infrastructure are likely to encounter an increased risk of potential cyberattacks from this threat actor.
CYFIRMA Research team observed a potential data leak related to “Primo Taglio”, {www[.]primotaglio[.]it}. “Primo Taglio” is a renowned Italian online marketplace dedicated to offering a wide selection of premium, Made in Italy food products. The compromised data includes sensitive details such as ID numbers, first and last names, email addresses, passwords, account activation status, birth dates, genders, newsletter subscription status, company affiliations, VAT numbers, timestamps, and anticipatory identification numbers.
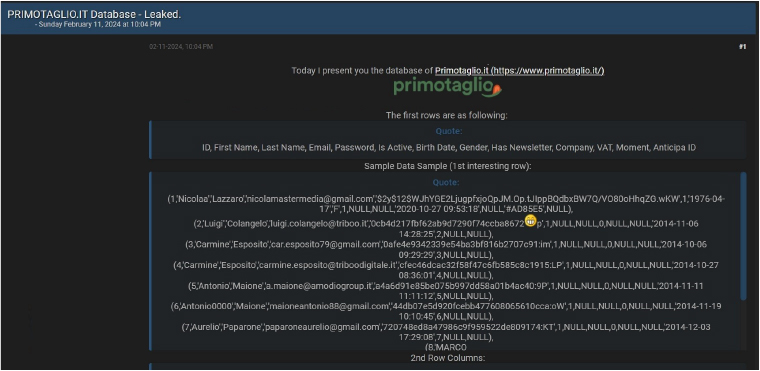
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS