



Key Intelligence Signals:
Summary:
MuddyWater is Iran’s state-sponsored cyber espionage group which has been conducting cyber operations since the year 2017. The group has penetrated several private organizations, government, defense, telecommunication, and oil-natural gas organizations, in the Middle East, Asia, Africa, Europe, and North America. In recent attacks, the group targeted Egyptian Hosting companies and Israeli Insurance organizations through spear phishing attacks. An HTML attachment was sent in phishing mail. The attachment is not an archive or an executable which does not raise end-user suspicion because HTML is mostly overlooked in phishing awareness training and simulations. The embedded link in the HTML file leads to OneDrive, which hosted a Syncro MSI installer. The activity of Muddywater revealed the campaign started back in starting of October. This campaign was backed by the new remote administration tool named Syncro. Syncro is a web-based platform for Managed Service Providers (MSPs) to run their business. Syncro provides a carrier for MSPs to control any device that has Syncro installed in it.
Insight:
It seems like Syncro is working well to fulfill the interest of threat actors and that is the reason the same RAT was found in other campaigns by other threat actors.
Syncro provides 21 days of free trial service. The trial version provides features that allow threat actors to gain control over the victim’s machine.
National Security Agency (NSA) has recently released a memo that warns of activity by APT5, a threat actor known for extensively focusing on telecommunication and technology companies. While NSA does not explicitly attribute this threat actor to Beijing, researchers have long been strongly convinced that APT5 is a Chinese intelligence threat group.
The threat actor is mostly focused on Southeast Asia and has been active since at least 2007. It also appears to consist of several subgroups, often with distinct tactics and infrastructure, creating a larger organization together. In the past, the primary focus was satellite communications and related telecommunications both in the civilian and military spheres. The NSA’s advisory offers guidance on file integrity and behavioral checks, as well as YARA rules useful for detection.
A new data wiper dubbed “Fantasy” has been recently observed to be utilized by Iran-linked Agrius APT, targeting supply chains in IT, business consultancies, and diamond-related industries in South Africa, Israel, and Hong Kong.
Another Iranian threat actor APT42 aka Charming Kitten has been observed expanding outside of its standard set of targets in academia, government, and media to include targets in healthcare, real estate, and other assorted industries. Researchers speculate that the
Islamic Revolutionary Guard Corps (IRGC) refocused the group to target new sets of individuals based on the recent outbreak of unrest in the country, which seems to be confirmed by apparent attempts to lure targeted individuals into kidnapping traps.
The recent focus of the Russian military targeting Ukraine’s power grid and the experience of Russian hackers attacking the grids in the past have prompted the authorities in the European Union into a cybersecurity audit of the European power grid.
CYFIRMA has repeatedly warned in the past that the energy industry and critical infrastructure are going to be prime targets in the coming months and years, especially during winter. The Ukrainian grid has been disconnected from the Russian one, which raises the risk considerably, given the apparent lack of restraint on part of Russia in its attacks on purely civilian infrastructure. The Ukrainian government has expressed concerns about a shortage of qualified cybersecurity operators who could be employed in safeguarding its grid.
The State Service for Special Communications and Information Protection of Ukraine warned citizens to be alert about a phishing campaign, where the attackers disguise themselves as the State Emergency Service of Ukraine in an email that supposedly contains warning information on Russian kamikaze drones. The targeted organizations are mostly government agencies and rail transportation with victimology and other circumstantial evidence pointing to the origin of the campaign in Russia.
The email contains a malicious payload called DolphinCape, whose main function “is to collect information about the computer…launch EXE/DLL files, display a list of files and download them, as well as create and exfiltrate snapshots screen,” the warning explains. This campaign follows several similar campaigns from earlier this fall when the attackers disguised themselves as the press service of the General Staff of the Armed Forces of Ukraine or even CERT-UA.
UNA Seguros, SA Portugal Insurance Company Impacted by PLAY Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective CYFIRMA observed UNA Seguros, SA – a Life and Non-Life insurance provider – being impacted by the PLAY ransomware group. The ransomware group claimed UNA Seguros, SA (www[.]unaseguros[.]pt) as one of their victims by disclosing the update on their dedicated leak site. It is suspected that a large amount of clients’ information, passports, IDs, finance, agreements, and many other business-critical and sensitive data has been exfiltrated. At the time of CTI’s observation, the ransomware group provided a deadline of 20 December 2022 to make the ransom payment.
Insights:
PLAY Ransomware has been active since at least mid-June 2022. The ransomware encrypts files using the standard RSA-AES hybrid cryptosystem. Additionally, the ransomware executable has been heavily obscured using a variety of anti-analysis techniques that are uncommon in malware families. PLAY Ransomware uses double extortion against its victims.
To gain initial access to a company’s network, the PLAY Ransomware group makes use of a known valid account, exposed RDP servers, and unpatched Fortinet SSL VPN vulnerabilities. This group employs living-off-the-land binaries (LOLBins) as part of its attacks, like the majority of contemporary ransomware. It employs Task Manager for Local Security Authority Server Service (LSASS) process dumping and credential cracking, as well as the remote tool WinSCP for data exfiltration.
Based on the victims’ list PLAY ransomware is targeting government and critical infrastructure organizations in Europe followed by America and Asia.
Well-known activist Kim Dotcom posted a document on Twitter stating that the New Zealand Department of Internal Affairs has access to Facebook [backdoor] to censor content.
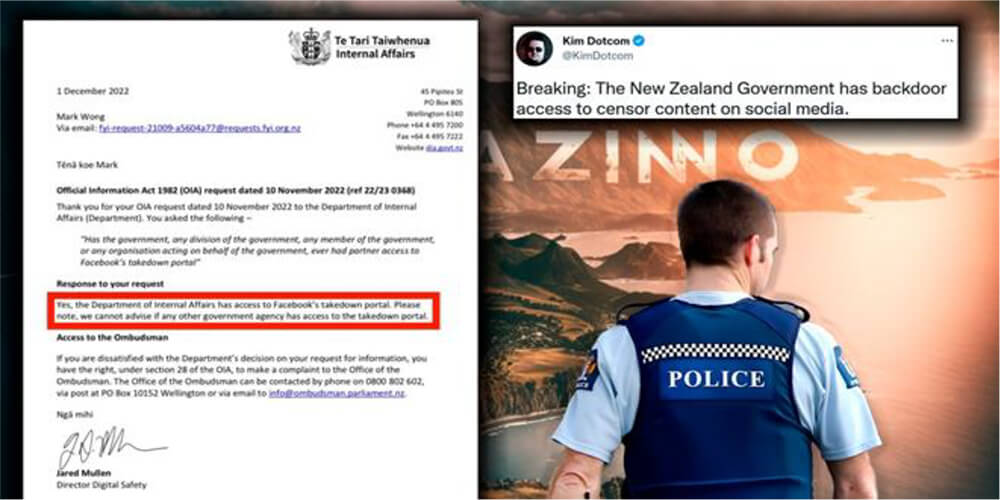
Source: Telegram
In Russia, cryptocurrency will become a recognized currency in 2023. However, according to Anatoly Aksakov, Head of the State Duma committee on the financial market, it will be possible to use it as a form of payment for domestic settlements.
“I can assure everyone that crypto as a legal product will definitely appear in our country next year, there will definitely be legislation, and I hope that the deputies will support it, it is necessary that the deputies vote, then the president sign. I hope that this will happen because the conciliation procedures, as I said, have been adjusted. Next year, the crypto will be in the legal field, I can only say unequivocally that it cannot be used in the Russian Federation as a means of payment for internal settlements,” – Anatoly Aksakov, Head of the State Duma committee on the financial market.
This can possibly make cyber criminals like ransomware groups easier to spend their cryptocurrencies as well as easier money laundering.
Pro-Russian hacktivist group KillNet’s sub-group Zarya launched their website to operate independently joining the ranks of pro-Russian groups.

Source: Underground Forums
Possibly Doha, Qatar bank network access for sale in the telegram channel.
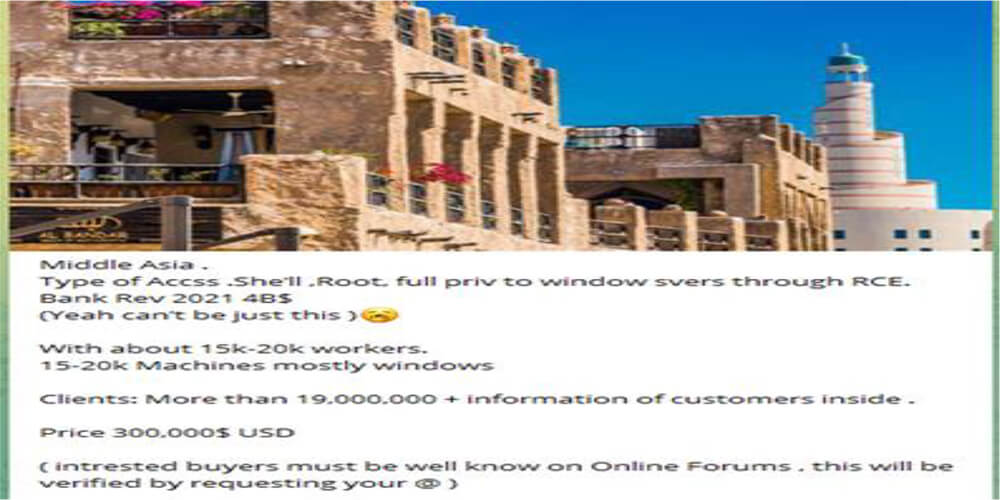
Source: Telegram