



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found OceanSpy ransomware while monitoring various underground forums as part of our Threat Discovery Process.
OceanSpy
Researchers uncovered a new ransomware dubbed OceanSpy, a ransomware variant based on the Chaos, designed to encrypt files and append a four-character random extension to their filenames. Additionally, OceanSpy modifies the desktop wallpaper and generates a ransom note titled “OceanCorp.txt.”
The threat actors behind OceanSpy ransomware identify themselves as OceanCorp, and have been active since at least April 2024, initially focusing on data dumps and demanding payment along with advisories to victim companies. However, possibly finding this approach unprofitable, they appear to have shifted to ransomware.
Monitoring by CYFIRMA researchers of the Telegram channel provided in the ransom note indicates that OceanCorp has now announced its entry into the ransomware landscape with the launch of OceanSpy ransomware.
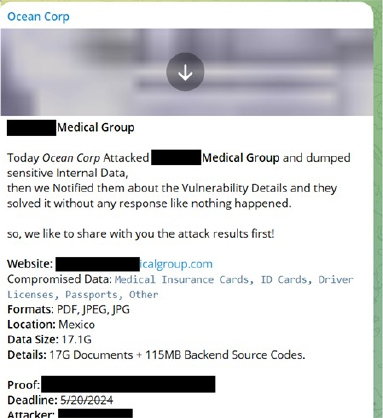

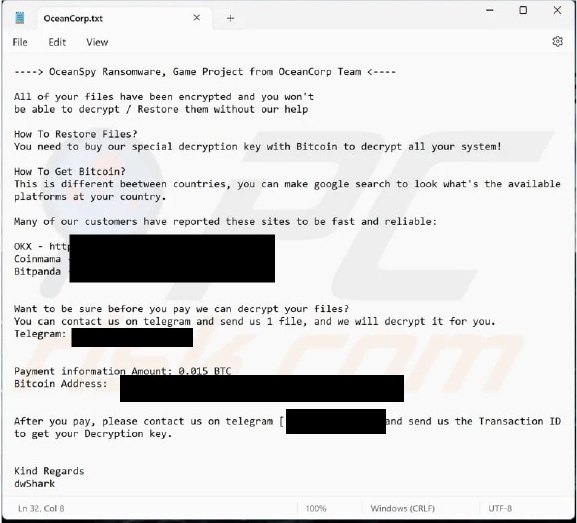
The ransom note informs victims that their files have been encrypted and cannot be restored without the attackers’ assistance. It instructs victims to purchase a decryption key for 0.015 BTC using the provided cryptocurrency wallet. After making the payment, victims are required to contact the attackers via Telegram and provide the transaction ID to receive the decryption key. The note also offers victims the option to send one file for free decryption before payment, demonstrating the attackers’ ability to decrypt the files.

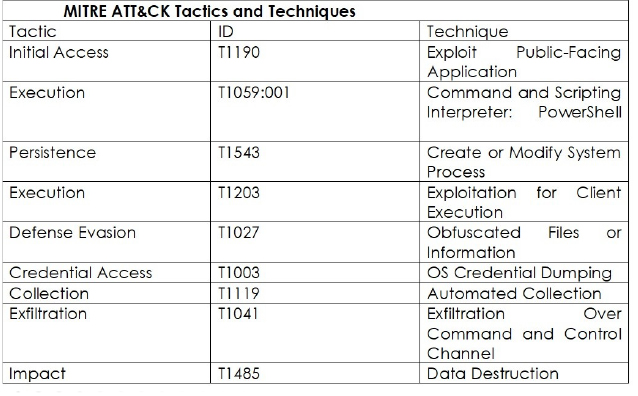
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job |
| T1059: Command and Scripting Interpreter | ||
| T1106: Native API | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| T1555.003: Credentials from Password Stores: Credentials from Web Browsers | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1114: Email Collection | ||
| T1115: Clipboard Data | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Based on the available data, CYFIRMA assesses that OceanSpy ransomware is likely to target a broad spectrum of industries, including healthcare, business services, construction, telecommunications, finance, banking, and manufacturing, to maximize ransom revenue. The threat actors have previously targeted various regions and sectors without using ransomware, indicating a strong possibility they may now expand their tactics to include ransomware attacks. OceanSpy ransomware is expected to target regions such as the US, Russia, Southeast Asia, Mexico and other economically developed nations, aiming to exploit these markets for financial gain.
SIGMA Rule:
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Spyware
Objective: Data theft, Data exfiltration Target Technology: Android OS Target Geography: Russia
Active Malware of the Week This week “LianSpy” is trending.
LianSpy
Researchers have uncovered a previously unknown Android spyware named LianSpy, which has been active since July 2021 and primarily targets individuals in Russia. This malware is designed to capture screen recordings, extract user files, and collect call logs and app lists. The attackers behind LianSpy use various evasive techniques to avoid detection, including utilizing Yandex Disk, a Russian cloud service, for command-and- control communications. They also avoid maintaining dedicated infrastructure and implement additional stealth features. The evidence suggests that LianSpy may be distributed via an unidentified vulnerability or through direct physical access to the victim’s phone.
Technical Analysis
LianSpy starts by checking if it operates as a system app, which gives it automatic permissions. If it is not a system app, it requests various permissions, including for screen overlays, notifications, background activity, contacts, and call logs. After getting these permissions, it makes sure it’s not running in a debugging environment. If the environment is clean, LianSpy sets itself up with default values. It saves this setup locally using SharedPreferences, which keeps the configuration intact even after the device reboots. The spyware uses integer keys in SharedPreferences to link with specific settings.
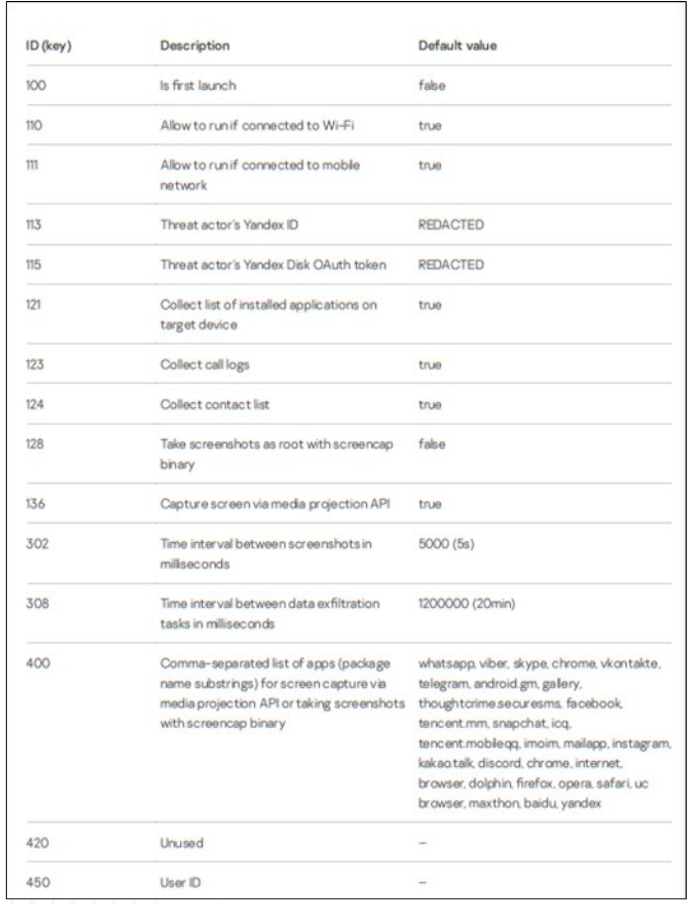
After activation, the spyware hides its icon and sets up a broadcast receiver to receive system intents. This receiver initiates malicious activities, including screen capturing through the media projection API, taking screenshots as root, exfiltrating data, and updating its configuration. LianSpy updates its configuration by checking every 30 seconds for a file on a threat actor’s Yandex Disk that matches the pattern “^frame_.+\\.png$”. If found, the file is downloaded and decrypted using a hardcoded AES key. The decrypted data contains configuration updates for LianSpy. Victim data, stored encrypted in the SQL table Con001, includes device information, contact lists, and call logs, each with a SHA-256 hash. The data is encrypted using an AES key generated by a secure pseudorandom number generator to prevent timing-based attacks. This AES key is then encrypted with a hardcoded public RSA key embedded in the spyware. Only the threat actor with the corresponding private RSA key can decrypt the stolen data.
Stealth features
LianSpy employs unconventional sophisticated evasion techniques to remain undetected.
Infrastructure
LianSpy operates without private infrastructure, using Yandex Disk for both data exfiltration and configuration storage. Victim data is uploaded to a dedicated Yandex Disk folder.
Communication with its command-and-control (C2) server is unidirectional, with no incoming commands; LianSpy autonomously handles updates and data exfiltration. Yandex Disk credentials can be updated via a hardcoded pastebin URL, which may differ among malware variants.
INSIGHTS
LianSpy demonstrates advanced capabilities beyond typical espionage activities, such as collecting call logs and app lists. It employs root privileges for stealthy screen recording and sophisticated evasion techniques. The use of a renamed su binary implies that LianSpy may be a secondary infection after an initial breach. Unlike financially driven spyware, LianSpy’s emphasis on capturing instant message content indicates a highly targeted data-gathering effort.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as smartphones become nearly ubiquitous worldwide, including in rapidly digitizing regions like Asia, the potential for sophisticated Android malware like LianSpy to target a broad geographic range grows. Android is the leading mobile operating system globally, and its usage continues to rise year-over-year. LianSpy’s advanced evasion techniques, which currently focus on specific areas, could soon reach a global audience, impacting organizations and employees across various regions. This shift highlights the urgent need for enhanced cybersecurity measures and employee training to counteract the evolving threat and safeguard sensitive information in an increasingly interconnected world.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Exploring Earth Baku’s Latest Cyber Campaign
Summary:
Earth Baku, a sophisticated threat actor linked to APT41, has recently broadened its operations from its traditional Indo-Pacific base to target countries across Europe, the Middle East, and Africa. This expansion includes high-profile targets such as Italy, Germany, the UAE, and Qatar, with potential activities also noted in Georgia and Romania. The group leverages vulnerabilities in public-facing applications, like IIS servers, to gain initial access, deploying a range of advanced malware tools in the process. Their arsenal includes the Godzilla webshell and custom-developed tools, such as StealthVector and StealthReacher, which are designed to deploy backdoor components, while using AES encryption and code obfuscation to remain undetected. Their newest backdoor, SneakCross, is particularly notable for its use of Google services for command and control, allowing for modular updates and enhanced stealth. Once inside a network, Earth Baku maintains a foothold with tools like a customized iox tool, Rakshasa, and Tailscale, while utilizing MEGAcmd for data exfiltration. This evolving and global reach underscores the increasing sophistication and impact of their cyber operations, highlighting the need for enhanced security measures and vigilance.
Relevancy & Insights:
Earth Baku, an advanced persistent threat (APT) group, focuses on targeting organizations in Southeast Asia. They employ sophisticated tactics, such as spear- phishing emails with malicious attachments or links, to infiltrate high-value targets, including government agencies, and critical infrastructure. In the observed campaign, Earth Baku exploited IIS server vulnerability in public-facing applications. Once inside a network, Earth Baku deploys custom-built malware, such as remote access trojans (RATs), to maintain long-term access, escalate privileges, and move laterally across systems. Their primary objective is to exfiltrate sensitive data, which they do through encrypted channels to avoid detection.
ETLM Assessment:
Earth Baku’s latest campaign reveals several critical aspects for evaluation. The group’s shift to targeting a broader range of regions, including Europe, the Middle East, and Africa, indicates a strategic escalation and diversification of their threat landscape. The advanced tools and techniques used, such as StealthVector, StealthReacher, and SneakCross, highlight the sophistication and adaptability of their malware, emphasizing the need for advanced detection and response capabilities. The use of AES encryption, code obfuscation, and legitimate services for command-and-control communications complicates traditional threat detection methods, suggesting a need for more nuanced and adaptive security measures. Additionally, their persistence mechanisms and data exfiltration tactics underline the importance of continuous monitoring and adaptive security practices.
Recommendations:
To effectively defend against cyberespionage and minimize the risk of compromise, individuals and organizations should follow these best practices:
By implementing these practices, you can strengthen your defenses against cyber threats and better protect your valuable data.
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Iran interfering in US elections
Researchers have recently published a report on Iranian cyber operations focused on the US 2024 elections. According to the report, Mint Sandstorm, a threat actor attributed to the Islamic Revolutionary Guard Corps (IRGC) sent a spear-phishing email to a high-ranking official of a presidential campaign from a compromised email account of a former senior advisor. The same group also unsuccessfully attempted to log in to an account belonging to a former presidential candidate. Additionally, Peach Sandstorm, another group tied to the IRGC, compromised a low-level user account at a county government in a swing state.
The Revolutionary Guards are also running an influence operation comprising of four websites masquerading as news outlets, actively engaging US voter groups on opposing ends of the political spectrum with polarizing messaging on issues such as the US presidential candidates, LGBTQ rights, and the Israel-Hamas conflict. The threat actor uses generative AI tools to assist in this operation.
Meanwhile, the Trump campaign disclosed that some of its internal communications had been hacked by “foreign sources hostile to the United States”, and the said internal data were shared with the center-left news website POLITICO, which says it received the hacked information from an anonymous AOL email address. In the past, old anonymous AOL addresses were mostly used by Russian actors.
ETLM Assessment:
In 2018, during his previous term in office, Trump unilaterally abandoned the 2015 nuclear accord that Tehran had signed with world powers and imposed waves of sanctions on the Islamic Republic, putting its economy under severe pressure. Iran’s long-term strategy is trying to manouvere the US out of the Middle East, where Tehran intends to play the role of a dominant power. Looking forward, we can thus expect Iranian actors to employ all forms of statecraft, including cyberattacks against American institutions, while simultaneously intensifying their efforts to sow internal divisions on the US soil, driving the attention of both electorate and politicians inward. These campaigns are likely going to be centered around amplifying existing divisive issues within the US, like racial tensions, economic disparities, and gender-related issues.
North Korean hackers targeting universities in South Korea
Researchers have recently issued a warning about the North Korean threat actor Kimsuky, which is conducting phishing attacks against South Korean universities. The group is targeting university staff, researchers, and professors by creating fake university login pages to steal credentials. Additionally, Kimsuky uses a specialized tool to send spear phishing emails from compromised accounts. The likely objective of these attacks is cyber espionage.
ETLM Assessment:
North Korean cyber operations have increased in sophistication over the past two years, and our researchers noted last year in a research report that Pyongyang’s threat actors seem particularly interested in stealing information related to maritime and missile technology research, given the emphasis the Kim regime puts onto developing a full nuclear triad. The interest in software is most likely related to Pyongyang’s interest in supply chain attacks. The heavily sanctioned regime in North Korea is hungry for the off-limits technologies it cannot obtain on the open market and thus uses cyber means to obtain them.
The Everest Ransomware impacts the NIDEC CORPORATION
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; NIDEC CORPORATION (www[.]nidec[.]com), was compromised by the Everest International Ransomware. Nidec Corporation is a prominent global manufacturer specializing in electric motors and related components. Nidec has grown to become the world’s leading comprehensive motor manufacturer, providing motors for a wide range of applications, including automotive, industrial, and consumer products. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes a vast collection of sensitive and confidential records, extracted from the organization’s database.
The following screenshot was observed published on the dark web:

Relevancy & Insights:
The Top 10 Industries, most affected by Everest International Ransomware from 1 Jan 2023 to 13 August 2024 are as follows: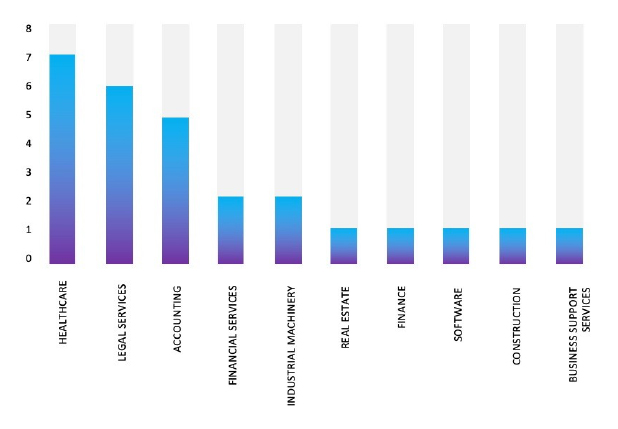
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Everest Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on NIDEC CORPORATION, a prominent Manufacturing company in Japan, highlights the extensive threat posed by this ransomware strain in the Asia Pacific region.
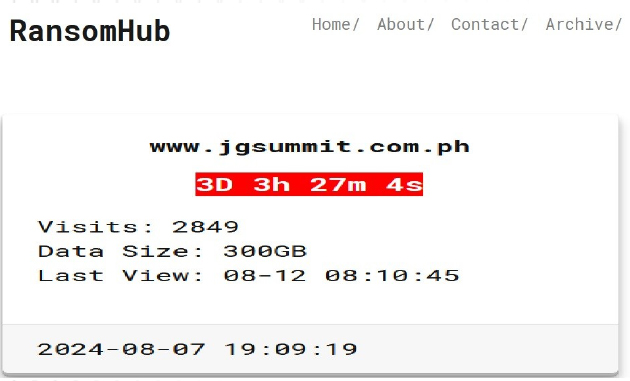
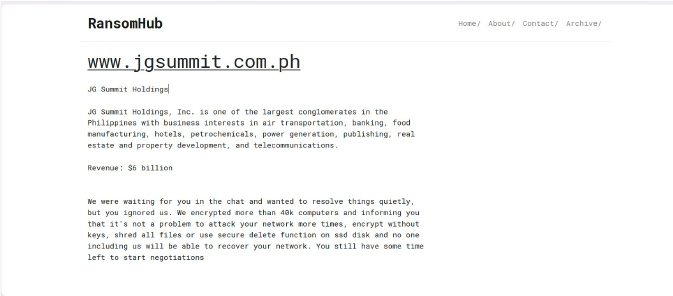
The RansomHub Ransomware impacts JG Summit Holdings
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the Philippines; JG Summit Holdings (www[.]jgsummit[.]com[.]ph), was compromised by the RansomHub Ransomware. JG Summit Holdings, Inc. is one of the largest conglomerates in the Philippines with business interests in air transportation, banking, food manufacturing, hotels, petrochemicals, power generation, publishing, real estate and property development, and telecommunications. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 300GB.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
The Top 10 Industries, most affected by the RansomHub Ransomware from 1st Jan 2023 to 13 August 2024 are as follows: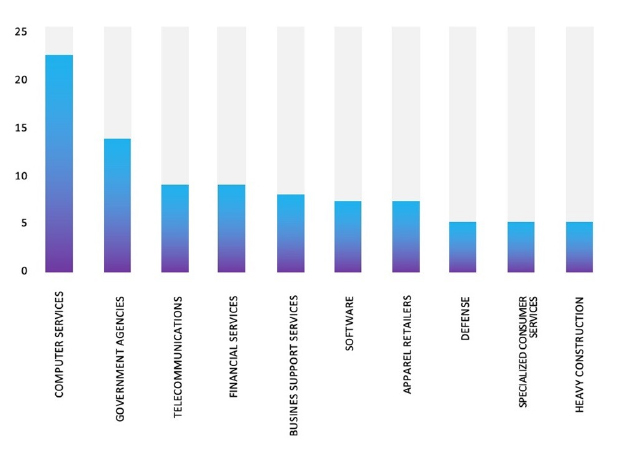
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on JG Summit Holdings, from the Philippines, highlighting RansomHub’s significant threat presence in the Southeast Asia region.
Vulnerability in PostgreSQL
Summary:
The vulnerability allows a remote user to escalate privileges within the database.
Relevancy & Insights:
The vulnerability exists due to a race condition when executing concurrent pg_dump sessions.
Impact:
A remote user with privileges to create and drop non-temporary objects can execute arbitrary SQL commands with the privileges of the role running pg_dump (which is often a superuser).
Affected Products: https[:]//www[.]postgresql[.]org/support/security/CVE-2024-7348/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
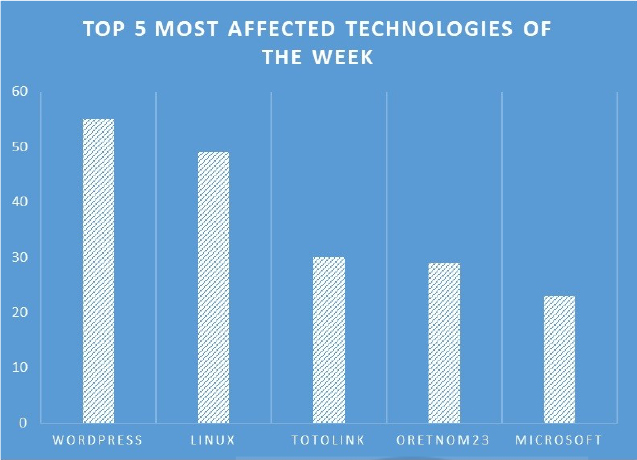
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in PostgreSQL can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of PostgreSQL is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguard relational database management activities, emphasizing extensibility and SQL compliance, across different geographic regions and sectors.
RansomEXX Ransomware attacked and Published data of Brontoo Technology Solutions
Summary:
Recently we observed that RansomEXX Ransomware attacked and published data of Brontoo Technology Solutions (www[.]brontoo[.]com) on its dark web website. OstaApp, developed by Brontoo Technology Solutions India Private Limited, is a digital payment platform that offers a secure, fast, and convenient way to make transactions without relying on traditional cards, wallets, or point-of-sale (POS) systems. The platform generates a unique, one-time-use digital number or QR code, which users can utilize for payments at registered merchants, partner ATMs, and more. The ransomware attack resulted in a data leak that exposed a database containing information on 146,123 users.
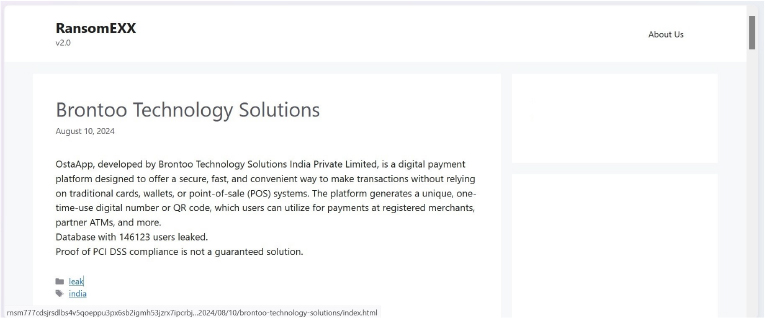
Relevancy & Insights:
ETLM Assessment:
RansomEXX ransomware is known to target large enterprises and high-value targets. They have also been known to focus on those in the government, Informational Technology, and healthcare sectors, as well as high-value manufacturing entities. RansomEXX ransomware targets its victims through phishing and spear phishing emails. They are also known to leverage exposed and vulnerable applications and services, such as remote desktop protocol (RDP) and third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike). Based on CYFIRMA’s assessment, RansomEXX ransomware targets worldwide organizations. The attack on Brontoo Technology Solutions also highlights ransomware groups’ interest in Asian organizations that are financially strong in the region with exploitable vulnerabilities.
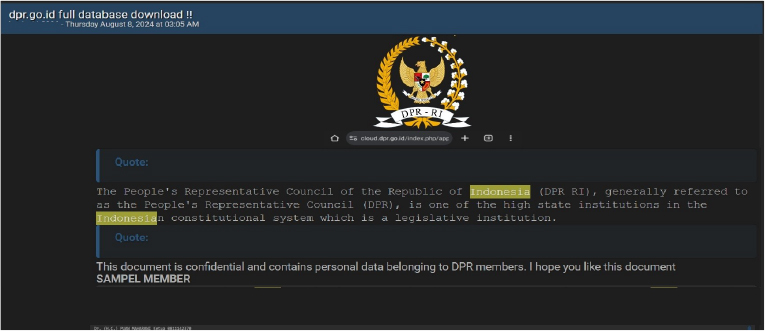
People’s Representative Council of the Republic of Indonesia (DPR RI) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to the People’s Representative Council of the Republic of Indonesia (DPR RI) in an underground forum. The People’s Representative Council of the Republic of Indonesia (DPR RI), generally referred to as the People’s Representative Council (DPR), is one of the high state institutions in the Indonesian constitutional system, which is a legislative institution. The compromised document is confidential and includes the personal information of DPR members.
CV. TWIN GROUP data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to CV. TWIN GROUP(www[.]twincom[.]co[.]id) in an underground forum. CV. TWIN GROUP(Twincom) is based in Indonesia, specializing in the sale and servicing of computer hardware and accessories. They operate five branches across the region, including locations in Banjarmasin and Banjarbaru. Twincom offers a wide range of products, such as laptops, motherboards, RAM, and printers, along with repair services. The compromised data contains Customer ID, Name, Contact Information, Business Phone Number, Mobile Number, Email, Fax, Website, Primary Currency Notes, Billing Address, Shipping Address, City, Province, Country, Postal Code, Branch Used, Pricing and Discount Categories, Payment Terms, Consignment, Accounts Receivable, Down Payment Account, Default Invoice Status (Tax Included), Taxpayer ID (NPWP),Personal ID (NIK), Transaction and Document Types. The data breach has been attributed to a threat actor identified as “Sedapmalam”.
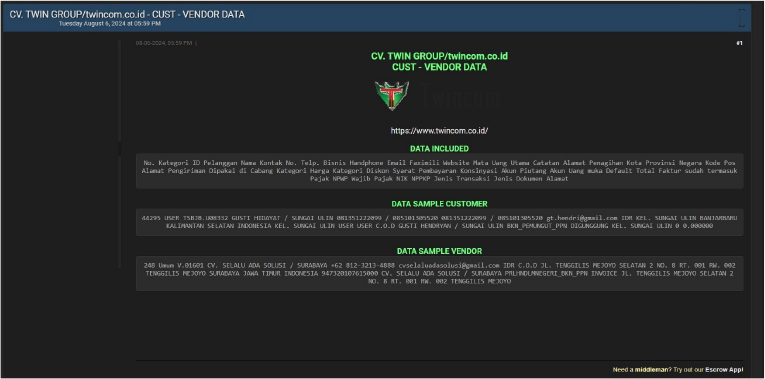
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as “Sedapmalam” poses a significant risk to organizations, as it is known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by “Sedapmalam” typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data leak related to the Manila Health Department, Philippines. A threat actor claims to have leaked a database from the Manila Health Department, containing sensitive patient and employee records. The compromised data reportedly includes usernames, names, dates of birth, appointment details, and 19,000 unique email addresses.
According to the threat actor, the breach occurred in July 2024 and was initially brought to attention by a group called “The Nexus Squad.” The stolen data was subsequently listed for sale on a prominent hacking forum. In addition to the personal information, the breach also exposed passwords in MD5 hash format, further heightening security concerns.
The exposed database includes detailed patient records with fields such as ID, username, password, role, first and last names, health center affiliations, email addresses, dates of birth, and more. The breach represents a significant compromise of the Manila Health Department’s services, raising serious concerns about the protection of sensitive health information in the region.
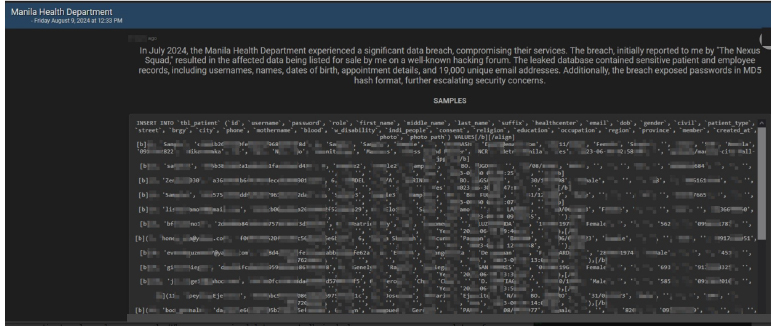
Source: Underground forums
The CYFIRMA Research team observed a potential data leak related to a Mykukun. A threat actor known as “IntelBroker” has claimed responsibility for a significant data breach involving Mykukun, a company that collaborates with major banks and financial institutions, such as NYK, SOFI, and USBank. The breach, reportedly executed in August 2024, predominantly affects USBank members
The compromised data includes User IDs, usernames, source User IDs, user emails, first and last names, screen names, addresses, zip codes, profile images, avatars, phone numbers (including mobile), additional information, activation keys, user status, phone validation status, registration and verification dates, application details, account activity status, and metadata related to the creation and updates. Approximately 2.7 million lines of user data were exposed.
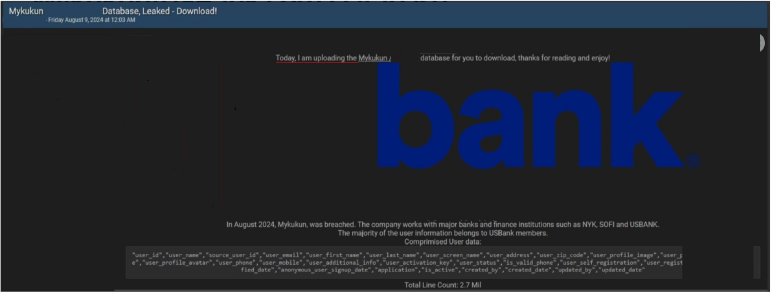
Source: Underground forums
ETLM Assessment:
The “IntelBroker” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
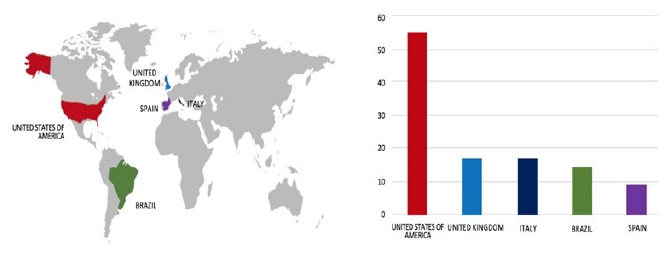
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.