



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Weaxor ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Weaxor ransomware
Researchers identified a new strain of ransomware named Weaxor.
Weaxor is a ransomware strain that encrypts files, compelling victims to pay for decryption. It appends the “.rox” extension to affected filenames and leaves a ransom note titled “RECOVERY INFO.txt” with instructions for recovery.

Screenshot of files encrypted by ransomware (Source: Surface Web)
Weaxor’s ransom note informs victims that their data has been encrypted and requires a decryption tool for recovery. Victims are instructed to download the TOR browser and use a provided link to contact the attackers. The note includes two contact emails and offers free decryption of up to three files (5 MB each), excluding databases or backups.

Screenshot of Weaxor’s text file (“RECOVERY INFO.txt”):(Source: Surface Web)

Screenshot of Weaxor’s chat website: (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1542.003: Pre-OS Boot: Bootkit |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1134: Access Token Manipulation | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1542.003: Pre-OS Boot: Bootkit | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0007: Discovery | T1012: Query Registry |
| T1016: System Network Configuration Discovery | ||
| T1018: Remote System Discovery | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 6 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 7 | TA0009: Collection | T1560: Archive Collected Data |
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| T1095: Non-Application Layer Protocol | ||
| T1105: Ingress Tool Transfer | ||
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment based on available info suggests that Weaxor ransomware could continue to evolve in stealth and evasion techniques, targeting Windows systems across diverse sectors. Likely to focus on developed nations and high-value industries like manufacturing, healthcare, finance, and FMCG, Weaxor’s prolonged inactivity tactic makes detection challenging, maximizing impact. Proactive monitoring and defense strategies are essential against this threat.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and
“shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*)
fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high (Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information stealer | Objectives: Data theft | Target Technology: Windows OS | Target Industries: Entertainment, Media, and Technology, Software Sector | Target Geographies: United States, Europe, East Asia, and South America | Campaign: CopyRh(ight)adamantys
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “Rhadamanthys” is trending.
Rhadamanthys
Researchers have been tracking a large-scale phishing campaign, dubbed CopyRh(ight)adamantys, which deploys the new version of the Rhadamanthys stealer (version 0.7) across regions including the United States, Europe, East Asia, and South America. This sophisticated campaign impersonates various companies, primarily in the Entertainment, Media, and Technology sectors, and falsely claims that victims have committed copyright infringement on their Facebook pages. Phishing emails, often sent from different Gmail accounts, encourage recipients to download an archive file that triggers DLL side-loading, leading to the installation of the Rhadamanthys stealer. While the latest version of the stealer allegedly includes an AI-powered OCR module, researchers have found that it instead uses older machine learning techniques typical of traditional OCR software. The campaign’s scale, automation, and potential use of AI tools indicate a highly organized operation, adopted by both cybercriminals and state- sponsored actors, with ongoing efforts to understand its tactics and improve detection.
Attack method
Check Point Software Technologies reported receiving phishing lures that mimic its own branded emails, which ultimately lead to the deployment of the Rhadamanthys stealer. This campaign begins with spear-phishing emails from Gmail accounts impersonating well-known companies and alleging copyright violations on the recipient’s social media pages. The emails, crafted to appear as communications from the companies’ legal representatives, accuse targets of brand misuse and demand the removal of specific images or videos. To support these claims, attackers provide a download link hosted on appspot.com, which redirects recipients to Dropbox or Discord to access a password- protected archive file (with the password included in the email). This file, once downloaded, initiates the infection process by deploying Rhadamanthys, illustrating both the adaptability and the broad scope of this phishing operation.

Fig: Phishing email impersonating Check Point
Infection Chain
The infection process starts with a spear-phishing email containing a link to download a password-protected archive, which holds three files: a legitimate executable, a malicious DLL with the packed Rhadamanthys, and a decoy Adobe or PDF file. When the executable runs, it uses DLL sideloading to load the malicious DLL, which then unpacks and activates the Rhadamanthys stealer.

Fig: Infection chain
When executed, the malware uses DLL sideloading to load the malicious DLL, triggering the stealer’s deployment. Rhadamanthys then injects itself into common processes like `credwiz.exe`, `dllhost.exe`, or `rundll32.exe` to evade detection and establish persistence. The malware’s modular structure enables multi-stage deployment: in Stage 2, it connects to a Command-and-Control (C2) server, while Stage 3 loads an OCR module embedded in a WAV file, enabling text extraction from images.
Targets and Attribution
The campaign’s targets span the US, Europe, the Middle East, East Asia, and South America, with an emphasis on entertainment, media, and tech sectors due to their frequent copyright-related communications. Despite previous links to state-sponsored groups, this campaign’s indiscriminate targeting pattern and automation suggest a financially driven cybercrime group.
Rhadamanthys 0.7 and OCR Module
The latest Rhadamanthys version, 0.7, introduces an OCR module, albeit not a modern AI-based tool. The module scans images in popular formats (e.g., BMP, JPEG) for specific phrases associated with Bitcoin wallets, indicating a financial motive. Using machine-learning techniques, it searches files for wallet-related phrases from the Bitcoin Improvement Proposal 39 (BIP39) wordlist. The OCR module’s limited capabilities (e.g., font restrictions, inability to read handwritten text) reflect its narrow focus, making it useful in attacks aimed at cryptocurrency assets.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the Rhadamanthys stealer campaign is likely to expand its reach, posing escalating threats to organizations and employees. As phishing tactics grow more sophisticated, particularly with automated, targeted lures, businesses may face increased risks from email-based attacks, especially in sectors like media, technology, and finance. The malware’s OCR capabilities suggest that attackers will focus on extracting sensitive financial and personal data from images and documents, amplifying the risks of fraud and intellectual property theft. As more organizations adopt image-heavy communication and digital assets, this threat could widen, requiring businesses to rethink their data protection strategies. Additionally, the social engineering tactics used, such as leveraging copyright infringement claims, may prompt organizations to enhance phishing detection and awareness, especially within legal and PR teams, to avoid compliance-driven compromises. With phishing campaigns becoming more sophisticated, businesses will need to invest in dynamic cybersecurity training and more adaptive defenses to mitigate these evolving risks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Analyzing Earth Estries’ Persistent Tactics, Techniques, and Procedures in Sustained Cyber Operations
SUMMARY
Earth Estries, an advanced threat actor active since 2020, employs two distinct attack chains to exploit vulnerabilities in systems like Microsoft Exchange servers and QConvergeConsole. In the first infection chain, the group uses CAB files to deliver tools such as Cobalt Strike, Crowdoor, and Trillclient, which enable lateral movement, credential theft, and persistence. PsExec and WMIC facilitate the spread of backdoors, while Trillclient collects credentials from browser caches. The second chain targets Exchange servers, deploying web shells (like ChinaChopper) to introduce backdoors, including Zingdoor and SnappyBee, with components delivered through cURL downloads. Earth Estries’ tactics also include credential theft and data exfiltration via anonymized file-sharing services.
Persistence is maintained through frequent updates to installed tools, while internal proxies help hide backdoor traffic. Notably, the group demonstrates a strategic, adaptive approach, often cleaning up older tools as new backdoors are installed, and employs a variety of credential dumping and data collection methods. Earth Estries’ diverse and evolving toolkit, featuring techniques like DLL sideloading and multi- layered attack strategies, poses significant challenges to detection and remediation efforts.
Relevancy & Insights:
In past campaigns, Earth Estries demonstrated a strong focus on exploiting vulnerable and exposed systems within high-profile Asian organizations, with particular emphasis on Microsoft Exchange servers and network management tools. Previously, they relied heavily on Cobalt Strike and Hemigate as primary backdoors, deployed through CAB files, while employing tools like PsExec and WMIC for lateral movement. Their past operations also included the use of credential-stealing tools and anonymous exfiltration channels, illustrating a layered attack approach designed to secure persistent access and evade detection.
The current incident mirrors these tactics but with evolved methods. Earth Estries now incorporates additional backdoors like Crowdoor, Zingdoor, and SnappyBee, expanding their toolkit for maintaining control and stealthily moving within networks. For instance, instead of solely using PsExec, they now deploy WMIC and cURL to spread and download malware, showing an adaptation toward bypassing modern defenses. Their emphasis on using QConvergeConsole for entry, along with scheduled tasks and internal proxies for persistence, reflects a consistent yet refined methodology from past campaigns. This alignment of old and new techniques highlights Earth Estries’ strategic approach and adaptability, suggesting that their evolving tactics will continue to challenge traditional security measures.
ETLM Assessment:
Earth Estries is a sophisticated threat actor active since 2020, known for targeting high- value entities in Asia, focusing primarily on sectors like finance, telecommunications, and government. Their operations exploit vulnerabilities in widely-used technologies, such as Microsoft Exchange servers, QConvergeConsole, and network management tools, taking advantage of flaws in Apache Tomcat and Exchange’s web-facing components to gain initial access. This group deploys a blend of custom and well- known malware, including recent tools like Zingdoor, SnappyBee, and Crowdoor, as well as older tools like Cobalt Strike and Hemigate, delivered through CAB files or cURL downloads for seamless infiltration and lateral movement.
Earth Estries exhibits high adaptability, frequently updating malware installations and leveraging internal proxies to evade detection. They often use multi-layered backdoor strategies, credential-stealing tools like Trillclient, and anonymized channels for data exfiltration. This adaptability and deep knowledge of targeted environments suggest a persistent threat landscape for organizations using vulnerable or exposed systems, as Earth Estries is expected to continue refining its methods to bypass defenses.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique / Sub technique |
| Execution | T1129 | Shared Modules |
| Defense Evasion | T1027.001 | Obfuscated Files or Information: Binary Padding |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1027.004 | Obfuscated Files or Information: Compile After Delivery |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| CredentialAccess | T1056 | Input Capture |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497.002 | Virtualization/Sandbox Evasion: User Activity Based Checks |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1056 | Input Capture |
| Command and Control | T1071 | Application Layer Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
3. Major Geo political Developments in Cyber security
Chinese Hackers Target EU Diplomats
The China-aligned threat actor known as MirrorFace has been observed targeting a diplomatic organization in the European Union, marking the first time the hacking crew has targeted an entity in the region. According to researchers during this attack, the threat actor used the upcoming World Expo which will be held in 2025 in Osaka, Japan as a lure. MirrorFace has been repeatedly targeting Japan and is now again observed using events related to it as well.
ETLM Assessment
MirrorFace, also identified as Earth Kasha, is believed to be part of the larger APT10 group, which includes other clusters like Earth Tengshe and Bronze Starlight. This group has been targeting Japanese organizations since at least 2019, but a new campaign observed in early 2023 shows an expansion in their activities to now include Taiwan and India. The campaign seems to be a classic state-driven espionage with many similar campaigns like it probably underway at the same time.
The DarkVault Ransomware impacts NEJOUM ALJAZEERA
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates; NEJOUM ALJAZEERAI (www[.]naj[.]ae), was compromised by DarkVault Ransomware. Nejoum Al Jazeera, is a UAE-based company specializing in car logistics and auto shipping services, especially for vehicles imported from the U.S. and Canada. The company has expanded its global presence with branches in the UAE, USA, Oman, Iraq, and Cambodia. Nejoum Al Jazeera offers services that include car shipping, customs clearance, and tracking for customers in the Middle East and beyond. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database.

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Based on recent assessments by CYFIRMA, DarkVault Ransomware represents an evolving threat in the ransomware landscape with its diversified criminal activities and aggressive tactics. Organizations are advised to enhance their cybersecurity measures to protect against such threats, including implementing robust incident response plans and employee training on recognizing phishing attempts and other attack vectors. As the situation develops, continued monitoring of DarkVault’s activities will be essential for understanding its impact on global cybersecurity.
The RansomHub Ransomware Impacts the Melange Systems
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; Melange Systems (www[.]melangesystems[.]com) was compromised by RansomHub Ransomware. Melange Systems is a wireless networking company with an emphasis on the Internet of Things (IoT). The company offers low-cost, low-power wireless networking modules, and complementary solutions for the next generation smart grid networks, smart cities, and connected infrastructure. The compromised data contains Personal Documents, Legal Documents, Source Codes for Company Apps/Programs, Credentials of all employees, and many more things. The total size of the compromised data is approximately 1.2 TB.

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Melange Systems, a prominent Technology company from India, highlighting RansomHub’s significant threat presence in the South Asian region.
Vulnerability in XStream
Relevancy & Insights:
The vulnerability exists due to a boundary error when processing untrusted input. A remote attacker can pass a specially crafted stream to the application, trigger a stack overflow, and perform a denial of service (DoS) attack.
Impact:
Successful exploitation of this vulnerability requires that XStream is configured to use the BinaryStreamDriver.
Affected Products:
https[:]//github[.]com/x-stream/xstream/security/advisories/GHSA- hfq9-hggm-c56q
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment
Vulnerability in XStream can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of XStream is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding object serialization and deserialization activities, specifically when converting objects to XML, across different geographic regions and sectors.
APT73 Ransomware attacked and published the data of PT. Sokka Kreatif Teknologi
Summary
Recently, we observed that APT73 Ransomware attacked and published the data of PT. Sokka Kreatif Teknologi (www[.]sokkakreatif[.]com) on its dark web website. PT. Sokka Kreatif Teknologi is a subsidiary of PT. Persada Inti Utama based in Indonesia. This company focuses on Information and Communication Technology (ICT) services, specializing in software engineering and providing IT solutions for businesses. Their offerings include custom ERP (Enterprise Resource Planning) solutions for efficient data management across operations, hospital management systems like Solvus, which handles patient records and financial processes, and MyKlinik, a management tool for clinics and pharmacies. Sokka Kreatif Teknologi also develops solutions tailored to Human Resources with ARYS HRMS, helping companies streamline HR operations, and Hepidesk, a helpdesk system for ISPs to monitor and manage customer interactions. Their mission is to deliver professional services, comprehensive IT products, and innovative solutions that support business growth and operational efficiency. The ransomware attack resulted in a data leak affecting CRM systems, export files, backups, and personal information, with an estimated exposure size of around 10 GB.

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
APT73 Ransomware represents a significant addition to the roster of active ransomware groups, leveraging tactics reminiscent of more established players like LockBit while targeting business services across multiple countries. Organizations are advised to implement robust cybersecurity measures, including regular updates and employee training on recognizing phishing attempts, to mitigate risks associated with this emerging threat actor.
National Electricity Company PLN (Perusahaan Listrik Negara) Data Advertised on a Leak Site
Summary
An extensive dataset from Indonesia’s National Electricity Company, PLN, has reportedly been leaked, encompassing over 44 million records. The exposed data includes sensitive information, such as user IDs, meter numbers, aliases, national ID numbers (KTP), email addresses, phone numbers, taxpayer numbers (NPWP), unit types, energy consumption types, meter kWh numbers, and various location details, such as province codes, district names, and GPS coordinates. This breach has raised significant privacy concerns, particularly regarding the potential misuse of personal and location data of PLN customers. The data breach has been attributed to a threat actor identified as “Cedar”.
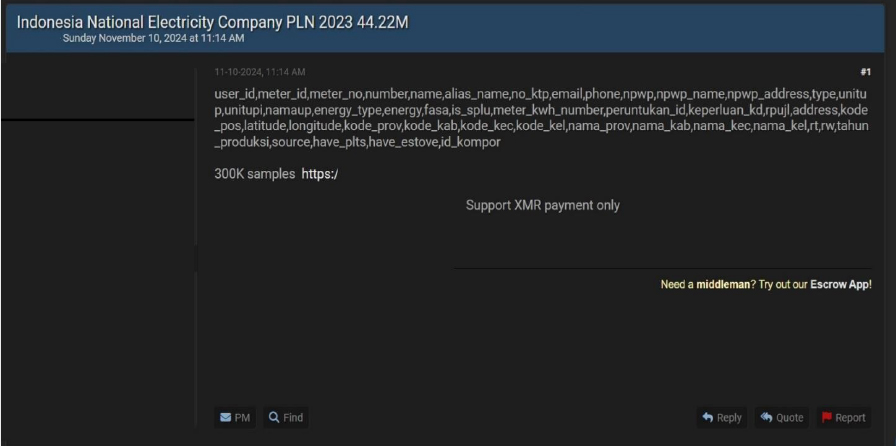
Source: Underground forums
Dept of Occupational Safety & Health Malaysia (DOSH) Access Advertised on a Leak Site
Summary:
The unauthorized access to the Department of Occupational Safety and Health (DOSH) portal in Malaysia, overseen by the Ministry of Human Resources, is allegedly being offered for sale. This access reportedly includes administrator-level permissions, potentially allowing control over sensitive functions, such as user management, data viewing, and regulatory updates. The DOSH portal plays a critical role in monitoring chemical safety and hazardous materials compliance across Malaysian workplaces, making this breach particularly concerning.
The incident underscores the importance of securing governmental systems that manage essential regulatory functions. Authorities are urged to investigate the breach and enhance cybersecurity measures to prevent unauthorized access. The Ministry of Human Resources has not yet issued an official response to address the alleged incident. The Access Sale has been attributed to a threat actor identified as “Sentap”.

Source: Underground forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Sentap” has recently surfaced in the cybercrime landscape, attracting significant attention due to its activities. CYFIRMA’s assessment underscores growing concerns about this actor, identifying it as a potential cybersecurity risk. Organizations are advised to enhance their defenses to guard against such emerging threats.
Recommendations: Enhance the cybersecurity posture by:
An alleged breach of Bahrain Medical Society’s website (http[:]//bhmedsoc[.]com) has been reported, with the attackers claiming access to 21 databases containing sensitive information. The compromised data includes usernames, passwords, IP addresses, payment IDs, and doctors’ information. The breach actor stated that the attack targeted Bahrain Medical Society due to their perceived support of Israel. This incident raises serious concerns about the security of sensitive medical and personal information held by professional organizations.

Source: Underground forums
A recent post claims to have access to a vast database containing information on 100 million users of Zalo (http[:]//Zalo[.]vn), a popular Vietnamese social media platform. The hacker has shared a demo sample and mentioned that they are in the process of updating additional data columns to complete the database. The data breach has been attributed to a threat actor identified as “Binanhang123”.

Source: Underground forums
ETLM Assessment
Threat actor “Binanhang123” represents a significant threat in the cybersecurity landscape due to its sophisticated techniques and focus on critical infrastructure sectors. Organizations are urged to implement robust cybersecurity measures, including regular updates to systems, employee training on phishing awareness, and comprehensive incident response plans to mitigate risks associated with this threat actor group.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.