



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industries: Automobile, Business Services, Electronic Equipment, Financial Services, Health Care, Manufacturing, Software and Transportation.
Target Geography: China, France, Germany, India, Taiwan, the United Kingdom and the United States.
CYFIRMA Research and Advisory Team has found RA World ransomware while monitoring various underground forums as part of our Threat Discovery Process.
The RA World ransomware, formerly known as the RA Group, has demonstrated a concerning capability to infiltrate organizations on a global scale since its initial emergence in April 2023.
RA World encrypted files and appended their filenames with a “.RAWLD” extension. After the encryption is completed, a ransom-demanding message titled “Data breach warning.txt” will be created.
Researchers have recently uncovered an RA World cyber attack specifically targeting multiple healthcare organizations in the Latin American region. This sophisticated incursion incorporates multi-stage components meticulously designed to achieve maximum impact and operational success for the group.
The multi-stage attack by RA World.
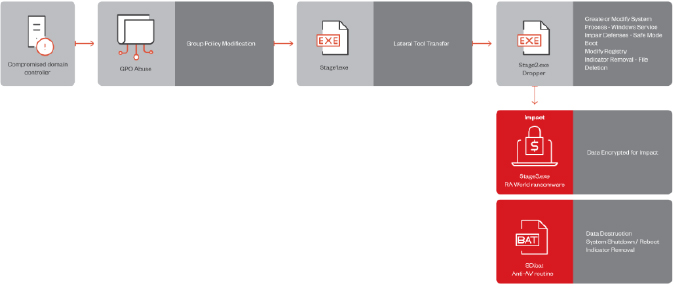
The RA World attack chain (Source: Surface Web)
The operators of RA World establish their initial entry point by exploiting compromised domain controllers, through which they deploy their components to the SYSVOL share path for a machine Group Policy Object (GPO).
Researchers have observed the execution of Stage1.exe within the network environment, indicating the utilization of PowerShell. This suggests potential modifications to Group Policy settings to enable PowerShell script execution.
In the initial phase, Stage1.exe systematically compiles a list of all domain controllers affiliated with the present domain. Subsequently, it validates the current domain name and systematically traverses each domain controller, ceasing its operations under specific predefined conditions.
These conditions involve scrutinizing the initial segment of the domain controller’s name to verify its alignment with the local machine’s hostname. Additionally, Stage1.exe undertakes an examination for the presence of Finish.exe and Exclude.exe within the
%WINDIR%\Help Directory. The existence of Finish.exe implies a potential previous compromise, while the presence of Exclude.exe indicates a potential exclusion of the respective machine.
Following the initial verification process, the ransomware conducts an assessment to determine the presence of Stage2.exe within the local machine’s %WINDIR%\Help directory. If Stage2.exe is not detected, the ransomware proceeds to copy both pay.txt and Stage2.exe from the pre-defined SYSVOL Path to the local machine. Subsequently, the execution of Stage2.exe is initiated.
The analysis underscores the nature of a targeted attack, evident in the presence of a hardcoded company domain name and SYSVOL path within the binary. Furthermore, it implies a strategic approach wherein the payloads are initially situated within the compromised machine and subsequently deployed to other local systems through the manipulation of Group Policies. This signifies a sophisticated and multi-stage attack methodology designed to compromise systems strategically within the target network.
Stage2.exe is tasked with delivering the ransomware payload and, akin to stage1.exe, it incorporates embedded strings that include the domain name of the targeted company.
The program begins by assessing whether the machine is operating in safe mode. If not, it conducts a similar verification for the presence of Exclude.exe and Finish.exe. Subsequently, the program proceeds to create a new service named MSOfficeRunOncelsls, wherein Stage2.exe is configured as a service set to run in Safe Mode with Networking.
Moreover, it configures the Boot Configuration Data (BCD) to enable Safe Mode with Networking and proceeds to initiate the machine startup in this mode.
If the machine is already in Safe Mode, Stage2.exe similarly confirms the non-existence of Exclude.exe and Finish.exe on the system. Following this, it decrypts the contents of pay.txt using Base64 and AES encryption, transferring the decrypted information to Stage3.exe, which functions as the ransomware payload.
Upon executing the ransomware payload, the program engages in cleanup activities, effectively removing residual malware elements and establishing necessary registry keys.
Ultimately, the RA World ransomware payload, denoted as Stage3.exe and leveraging the leaked Babuk source code, is executed. This ransomware variant deposits the text file Finish.exe, containing the singular string “Hello, World.” Additionally, it establishes a mutex named “For whom the bell tolls, it tolls for thee,” previously utilized in earlier versions alongside the Babuk ransomware.
The accompanying ransom note incorporates a list of recent victims who have not met the ransom fee, employing this information as part of extortion tactics to exert pressure on other potential victims to comply with the group’s demands.
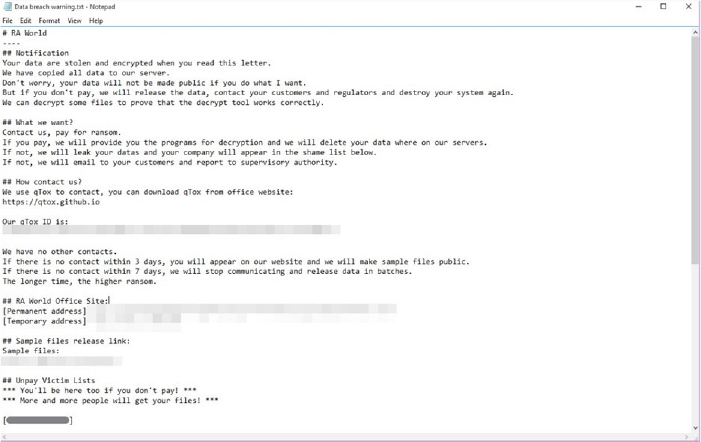
The RA World ransom note (Source: Surface Web)
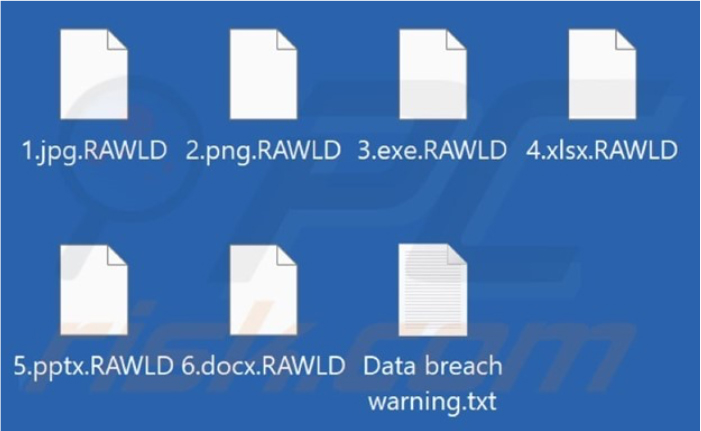
Screenshot of files encrypted by RA World ransomware (Source: Surface Web)
The RA World operators also utilize SD.bat, a script intended to eradicate the security software folder. Moreover, it leverages the WMI command-line (WMIC) utility to gather disk information and generates a log stored at C:\DISKLOG.TXT.
Following the removal of the security software folder, the ransomware proceeds to eliminate the Safe Mode with Networking option that was previously added to the default boot configuration in the Windows operating system. Ultimately, it initiates an immediate and forceful reboot of the computer system.
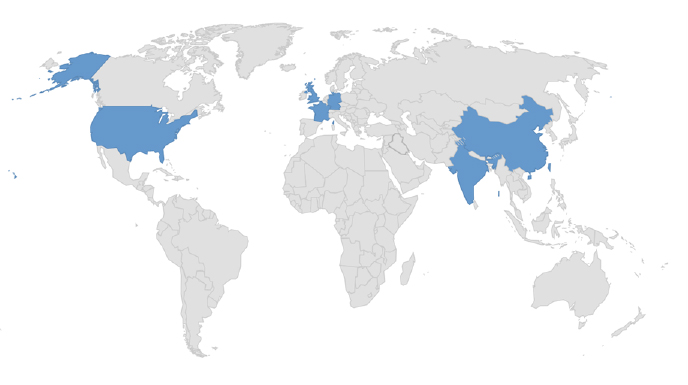
Countries targeted by RA World (Formerly known as the RA Group)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 6 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 7 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1005: Data from Local System |
| 10 | TA0011: Command and Control | T1090: Proxy |
| 11 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery |
Based on CYFIRMA’s analysis of the RA World ransomware, there has been a concerning trend of global infiltration since its emergence. The recent attack on healthcare organizations in Latin America reveals a sophisticated multi-stage strategy, demonstrating the group’s adaptability. Predictions suggest that RA World may continue evolving its tactics, targeting sectors with high stakes, employing advanced methods, and leveraging extortion tactics for increased impact and financial gain. Organizations should enhance cybersecurity measures accordingly.
title: Suspicious Volume Shadow Copy VSS_PS.dll Load tags:
– attack.defense_evasion
– attack.impact
– attack.t1490 logsource:
category: image_load product: windows
detection: selection:
ImageLoaded|endswith: ‘\vss_ps.dll’ filter_legit:
Image|startswith: ‘C:\Windows\’ Image|endswith:
– ‘\clussvc.exe’
– ‘\dismhost.exe’
– ‘\dllhost.exe’
– ‘\inetsrv\appcmd.exe’
– ‘\inetsrv\iissetup.exe’
– ‘\msiexec.exe’
– ‘\rundll32.exe’
– ‘\searchindexer.exe’
– ‘\srtasks.exe’
– ‘\svchost.exe’
– ‘\taskhostw.exe’
– ‘\thor.exe’
– ‘\thor64.exe’
– ‘\tiworker.exe’
– ‘\vssvc.exe’
– ‘\WmiPrvSE.exe’
– ‘\System32\SystemPropertiesAdvanced.exe’ filter_programfiles:
# When using this rule in your environment replace the “Program Files” folder by the exact applications you know use this. Examples would be software such as backup solutions
Image|startswith:
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_update:
CommandLine|startswith: ‘C:\$WinREAgent\Scratch\’ CommandLine|contains: ‘\dismhost.exe {‘
filter_image_null:
Image: null
condition: selection and not 1 of filter_* falsepositives:
– Unknown level: high
(Source: Surface Web)
Type: Information Stealer
Objective: Credential Stealing, Financial theft
Target Technology: Browser Extension (Edge Browser)
Target Industries: Banks
Target Geographies: Latin America (LATAM), Europe and North America
Attack Methods: Man-in-the-Browser (MitB), Web-injection attacks.
Active Malware of the Week
This week “Fakext” is trending.
In November 2023, researchers discovered the Fakext malware, employing a malicious Edge extension for widespread man-in-the-browser and web-injection attacks, notably targeting users in Latin America. The campaign has affected 35,000 sessions, primarily in Latin America, with a smaller impact in Europe and North America. The success of the campaign is evident in its extensive reach. Researchers also noted that Fakext displays injected content in Spanish, including error messages and user forms. The malware specifically targets 14 banks operating in Latin America, particularly in Mexico.
Script Injection and Deceptive Tactics
The extension’s primary function is to consistently inject scripts into the victim’s HTML page. The script, obtained from one of several command-and-control servers maintained by the threat actor, operates within the current page context. Fakext utilizes Telegram’s API as an additional communication channel for sending information, including the current injection state and screenshots, to the C2 servers. The malware downloads the fingerprintJS library from its official CDN to generate the victim’s user ID, adding it as an HTML document attribute named “fkr-client-uid,” which signals that the extension is installed and running. The script checks for this ID and the current page URL, determining whether it corresponds to one of the targeted banks and fetching additional modules accordingly.
Fakext operates on targeted sites through two primary modules:
The malware employs deceptive tactics by disguising its network traffic with domain names that closely resemble legitimate CDNs and frameworks, including examples like:
The threat actor employs Cloudflare’s workers to disseminate web injections. The extension, currently boasting over 10,000 users, masquerades as a tool to assist in utilizing Mexico’s SAT portal, a government tax agency website.
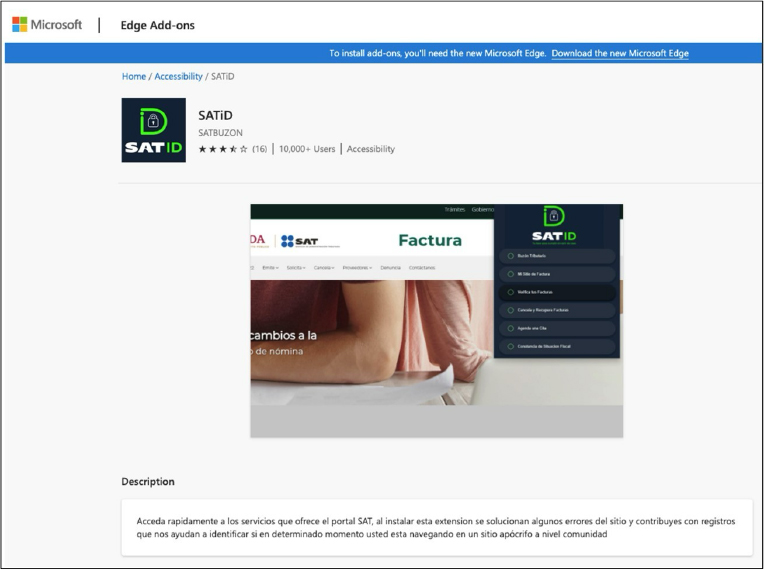
Fig: SATiD extension page from the Edge store
Fakext also employs well-known anti-debugging techniques, including code obfuscation, native function overrides, and intentionally crafted code sections designed to disrupt development tools. These measures collectively enhance the difficulty of detecting and analyzing the code.
Fakext operates a generic form grabber on the current page, capturing all input fields and sending the entire input element, including style, ID, type, and value, to the C2 server upon a keypress event. The malware also transmits the current page URL, providing the fraudster with precise information about the stolen credentials. For specific targets with known HTML structures and element IDs, only relevant inputs are intercepted, indicated by specific IDs hardcoded in the script, suggesting tailored injections for selected targets.
For certain targets, Fakext employs an alternate attack method, introducing an overlay that mimics the current page styling, obstructing the user’s typical actions. Disguised as the bank’s IT support, the popup coerces the user into downloading a seemingly legitimate remote access tool (RAT) and discloses the tool’s credentials to the fraudster. The rest of the page is dimmed and unresponsive, and the prompt can’t be removed.
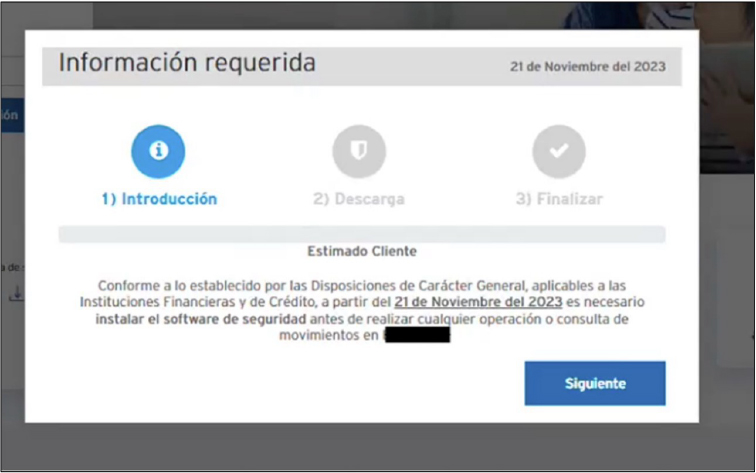
Fig: Prompt to install “security software” before continuing with bank operations.
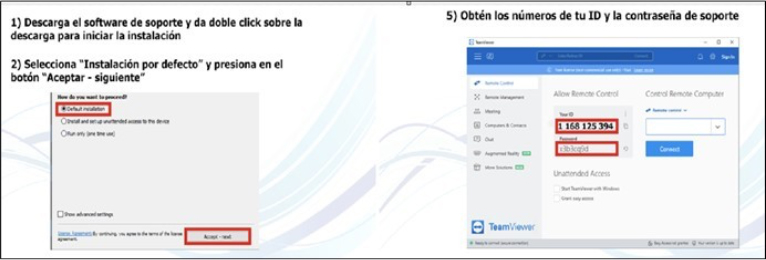
Fig: Instructions provide guidance on downloading and installing TeamViewer while also acknowledging the credentials required from the victim.
The injection consistently reports the overlay’s status to C2 servers, including details about the user’s popup and banking page, along with the type of remote access tool (RAT) installed. Armed with RAT credentials, user information, and the capability to inject pages onto the victim’s screen (such as a fake one-time password (OTP) page), the fraudster can conduct transactions and engage in various financial fraud activities.
Native security measures like content security policy (CSP), SSL certificates, and CORS limitations are ineffective against this threat, as the browser extension overrides them. The injected external content remains undetected by the victim, creating the illusion of a legitimate security procedure. Furthermore, the overlay may also present an optional credit card information form, contributing to additional data theft.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Fakext, a significant piece of malware targeting browser extensions, poses concerns regarding its potential future impact on organizations and employees. Employees who are heavily dependent on browser extensions for productivity and personalization may become more vulnerable to sophisticated attacks leveraging Fakext-like malware. The malware’s demonstrated versatility in targeting specific regions suggests a potential expansion of its geographical reach, broadening the threat landscape. Considering its current sophistication, it is plausible that Fakext may evolve to incorporate even more advanced techniques, challenging detection, and mitigation efforts.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
Intelligence Signals:
Unveiling ‘Magnet Goblin’: A Financially Motivated Threat Actor
Summary:
Researchers have uncovered a new threat actor dubbed “Magnet Goblin” operating with a clear financial motivation. This actor has been observed exploiting 1-day vulnerabilities for initial access, with recent attention drawn to vulnerabilities in Ivanti Connect Secure VPN (CVE-2023-46805 and CVE-2023-21887), swiftly adopted by multiple threat actors.
Additionally, Magnet Goblin has targeted platforms such as Magento, Qlik Sense, and potentially Apache ActiveMQ to deploy its custom malware, particularly on Linux systems. Additionally, Remote Monitoring and Management software like ConnectWise’s ScreenConnect has been utilized in their operations. While some of these activities were previously reported, they were not attributed to a specific actor until now.
Upon successful exploitation, Magnet Goblin deploys malware from the Nerbian family, notably NerbianRAT; a cross-platform Remote Access Trojan (RAT) with variants for both Windows and Linux, and MiniNerbian; a compact Linux backdoor. Notably, the threat actor has demonstrated adaptability, extending their activities beyond Linux environments to target Windows systems using tools like ScreenConnect and AnyDesk.
Following the establishment of command and control (C2), NerbianRAT facilitates various malicious activities on compromised systems. These actions include executing Linux commands immediately or in a new thread, altering connection interval and work time settings, updating configuration variables, and delivering command results. The emergence of Magnet Goblin underscores the ever-evolving landscape of cyber threats, highlighting the importance of proactive security measures and prompt patching of vulnerabilities.
Relevancy & Insights:
Researchers have pinpointed a fresh menace in the cyber landscape dubbed the Magnet Goblin. Operating primarily for financial gains, this threat actor leverages various publicly disclosed one-day vulnerabilities to gain initial access. Subsequently, they deploy custom malware for nefarious activities such as data exfiltration. The geographic targets of the threat actor remain unknown, as does their affiliation or location. This revelation underscores the ongoing evolution of cyber threats and emphasizes the critical need for robust cybersecurity measures.
ETLM Assessment:
A new threat actor known as the Magnet Goblin has emerged, driven by financial motives. This actor exploits publicly disclosed one-day vulnerabilities, such as the Ivanti VPN Vulnerabilities, to gain initial access and deploy custom malware. It is crucial to note that while the Magnet Goblin is known to use these vulnerabilities, other threat actors may also be leveraging similar tactics, potentially without detection. Understanding and monitoring the use of one-day vulnerabilities across the threat landscape is essential for effective external threat landscape management. Staying informed about emerging threats like the Magnet Goblin and their tactics is crucial for organizations to bolster their defences and mitigate risks effectively.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers using data stolen from Microsoft
According to a statement from Microsoft, the Russian state-sponsored threat actor Midnight Blizzard is exploiting information stolen from the company earlier this year. Midnight Blizzard has recently been using information initially exfiltrated from Microsoft corporate email systems to gain or attempt to gain unauthorized access. This has included access to some of the company’s source code repositories and internal systems. The company adds, “It is apparent that Midnight Blizzard is attempting to use secrets of different types it has found. Some of these secrets were shared between customers and Microsoft in email, and as we discover them in our exfiltrated email, we have been and are reaching out to these customers to assist them in taking mitigating measures. Midnight Blizzard has increased the volume of some aspects of the attack, such as password sprays, by as much as 10-fold in February, compared to the already large volume we saw in January 2024.”
ETLM Assessment:
By keeping footholds for extended periods of time without drawing notice, the larger cyber espionage mission this campaign was part of aims to obtain sensitive information of strategic relevance to Russia. Researchers are warning that many more organizations that revealed have probably been targeted in this campaign. This threat actor is known to primarily target governments, diplomatic entities, non-governmental organizations (NGOs) and IT service providers, primarily in the U.S. and Europe, a targeting mostly consistent with countries opposing the Russian war against Ukraine. The same set of targets are likely being targeted in this campaign and any gains in sensitive information would certainly be weaponized further by the Russian state to gain access to intelligence and map out strategic infrastructure Russian hackers could embed themselves in.
The BianLian Ransomware impacts the Palmer Construction
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]palmerconstruction[.]net), was compromised by the BianLian Ransomware. Palmer Construction is a design-build, general contractor with a 100% commitment to quality and reliability. The compromised data includes personal information, accounting records, budget details, financial data, contract information including Non-Disclosure Agreements (NDAs), employee profiles, project information, drawings, and other sensitive and confidential data. The total size of the compromised data amounts to 475 gigabytes.
The following screenshot was observed published on the dark web:
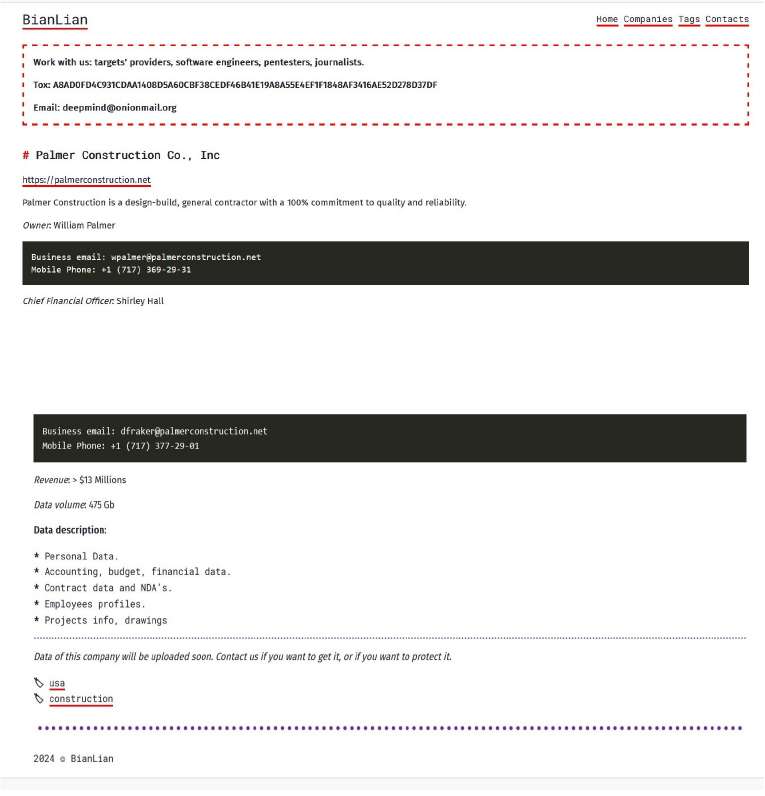
Source: Dark Web
Relevancy & Insights:
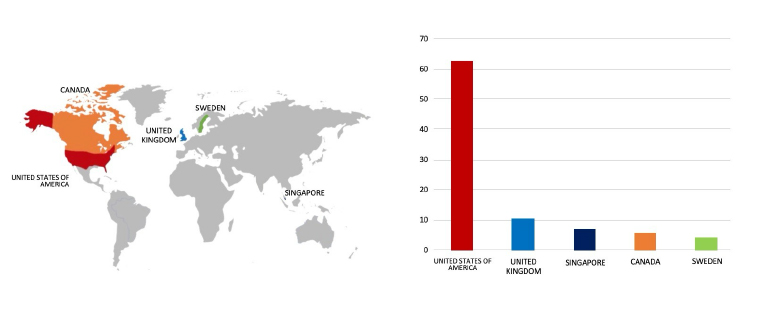
ETLM Assessment:
BianLian; a ransomware strain developed in GoLang, persistently infiltrates various industries, demanding substantial ransom payments. Employing the double extortion strategy, threat actors pilfer an organization’s files and threaten to leak them online if the ransom is not promptly paid. BianLian gains entry to victim systems through valid Remote Desktop Protocol (RDP) credentials, utilizing open-source tools and command-line scripting for discovery and credential harvesting. The exfiltration of victim data is executed via File Transfer Protocol (FTP), Rclone, or Mega. CYFIRMA’s assessment indicates that BianLian Ransomware will continue its focus on global businesses and related entities, holding significant amounts of Personally Identifiable
Information (PII), financial data, or other sensitive information. Nevertheless, the recent attack on Palmer Construction underscores the substantial risks posed by BianLian Ransomware to companies in advanced economies.
Vulnerability in Apache Doris
Summary:
The vulnerability allows a remote attacker to gain access to sensitive information.
Relevancy & Insights:
The vulnerability exists due to observable discrepancy in the authentication process.
Impact:
A remote attacker can perform a timing attack and gain access to sensitive information. Affected Products: https[:]//seclists[.]org/oss-sec/2024/q1/204
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
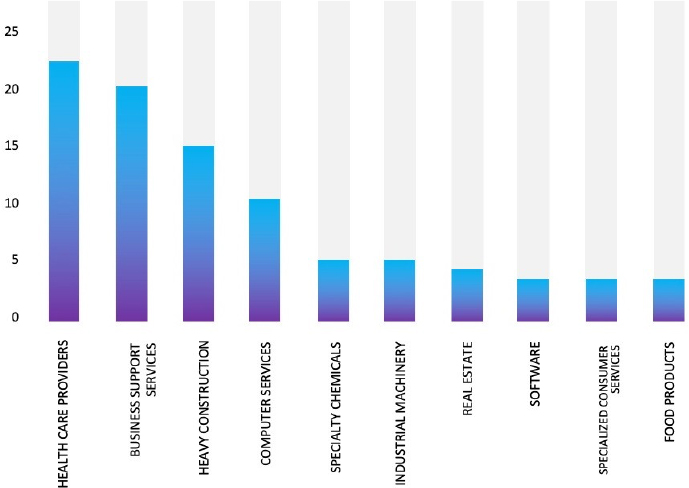
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
Multiple French government agencies hit by significant DDoS attacks
●
Summary:
The French government seems to have experienced a notable Distributed Denial of Service (DDoS) attack, leading to the disruption of numerous websites across various departments, rendering them temporarily inaccessible. In a statement issued on Monday (11 Mach 2024), Prime Minister Gabriel Attal’s office confirmed that a series of DDoS attacks started on Sunday (10 March 2024) night, hitting multiple government ministry websites. Anonymous Sudan has claimed the severe distributed denial of service (DDoS) attacks that disrupted several French government services on Monday (11 Mach 2024).
Anonymous Sudan in an official Telegram channel run by the group posted “We have conducted a massive cyberattack on the infrastructure of the French Interministerial Directorate of Digital Affairs (DINUM),” In addition to the DINUM, the group confirmed in the post that the attacks also impacted other French ministries and government organizations including the Directorate General of Civil Aviation, Ministry of Health and Social Affairs, National Geographic Institute, Ministry of Economy, Finance and Industrial and Digital Sovereignty, and Ministry of Ecological Transition and Territorial Cohesion.
Although neither the hacktivist group nor the French government have issued any statement on the motive of these attacks, experts have been linking the attack to France’s pro-Ukraine position on the Ukraine-Russia conflict. At a recent meeting convening several European leaders, French President Emmanuel Macron suggested a united European effort to resist Russia’s illegal military advances within Ukraine, which did not rule out sending troops to fight alongside the Ukrainian military.
Relevancy & Insights:
Anonymous Sudan is a hacking collective known for its DDoS attacks. Earlier this year, in February 2024, the University of Cambridge reported suffering a widespread distributed denial of service (DDoS) attack that was also causing disruptions across various other higher education institutions in the UK. Before that, in June 2023, Microsoft’s cloud services were also the target of Anonymous Sudan, with the group succeeding in temporarily bringing down OneDrive for some users. The attack against Cambridge was due to the UK’s “unconditional support for Israel and complicity in the ongoing genocide in Gaza, as well as bombing campaigns on Yemen.
ETLM Assessment:
Anonymous Sudan is a hacktivist group renowned for its involvement in cyber-attacks, notably distributed denial-of-service (DDoS) attacks, often motivated by religious and political causes. CYFIRMA’s assessment of the ongoing campaign indicates that pro- Russian threat actors are expected to continue targeting France and other NATO member nations, aiming to tarnish their reputation and cause extensive disruptions.
Mitsukoshishop data advertised on the Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to Mitsukoshishop, {www[.]mitsukoshishop[.]ph}. Mitsukoshi Motors Philippines Incorporated (MMPI) is the exclusive importer, assembler, and distributor of SYM, Euro Motors, and Euro Keeway Motors in the Philippines. The data for sale comprises a database containing records of 2.1 million customers and employees. The total size of the dataset being offered is 2.1 gigabytes. The listed price for this dataset is $500.
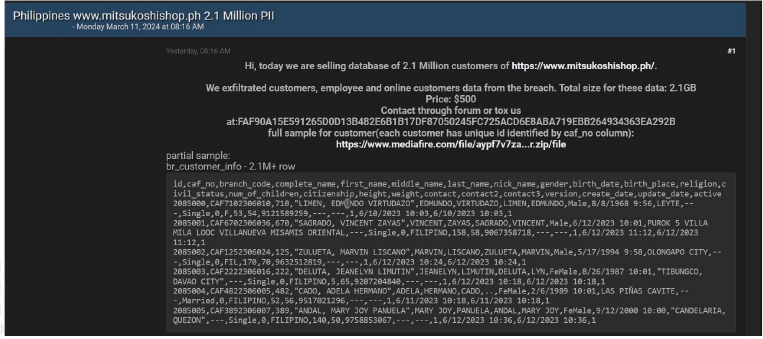
Source: Underground forums
Relevancy & Insights:
Financially motivated opportunistic cybercriminals are perpetually scouring for exposed
and vulnerable systems and applications. Predominantly congregating in underground forums, these attackers participate in discussions centered around buying and selling stolen digital assets. Differing from other financially motivated groups such as ransomware or extortion entities, they prefer to operate discreetly. Their modus operandi involves exploiting unpatched systems or vulnerabilities within applications to infiltrate and pilfer valuable data. Subsequently, this stolen data is advertised for sale within clandestine online communities, where it may be further redistributed and repurposed by fellow attackers in subsequent assaults.
ETLM Assessment:
The threat actor “haxormy1337” is a recently emerged entity primarily driven by financial incentives. Presently, they are actively involved in the illicit trade of sensitive data, encompassing personally identifiable information (PII), financial records, and other confidential data sourced from Mitsukoshishop. CYFIRMA’s assessment highlights that institutions in the Philippines lacking robust security measures and infrastructure are particularly vulnerable to potential cyberattacks orchestrated by this threat actor.
CYFIRMA Research team observed a potential data sale related to Atlas Scientific, {www[.]atlas-scientific[.]com}. Atlas Scientific is on a mission to convert devices that were originally designed to be used by humans into devices that are specifically designed to be used by robots. The data for sale contains ID, user login, user pass, user nickname, user email, user URL, user activation key, user status, display name, and other confidential
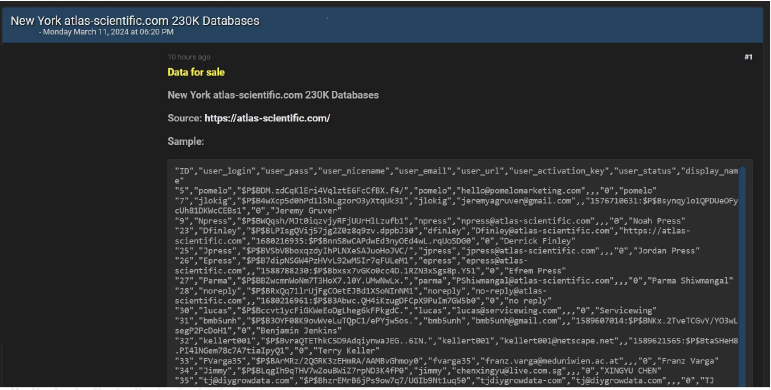
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS