



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows, Linux, VMware ESXi servers.
Targeted Geography: Argentina, Austria, Belgium, Canada, China, Netherlands, Serbia, South Korea, Thailand, United Kingdom, United States.
Targeted Industries: Apparel and accessories, Business Services, Education, Finance, Health Care, Hotels, Industrial Machinery, IT, Law Firms & Legal Services, Manufacturing, Real Estate, Retail.
Introduction
CYFIRMA Research and Advisory Team has found a new ransomware variant of Qilin while monitoring various underground forums as part of our Threat Discovery Process.
Qilin/Agenda
The Qilin/Agenda ransomware was initially observed on a widespread scale in August 2022. The ransomware, originally developed in the Go language, had been recognized for targeting the healthcare and education sectors in the initial days. Researchers later found a new variant of Qilin that is coded in the Rust language and identified as Ransom.Win32.AGENDA.THIAFBB.
The Ransomware encrypts files, appends a string of random characters as a file extension, and drops the “[random_string]-RECOVER-README.txt” file (with the same random string in its filename as encrypted files have).
The Rust variant of ransomware has also been observed employing intermittent encryption, to facilitate faster encryption and evade detection.
Upon execution, the Rust binary triggers an error that necessitates the provision of a password as an argument. This command-line functionality mirrors the behavior observed in the Agenda ransomware binaries developed in Golang.
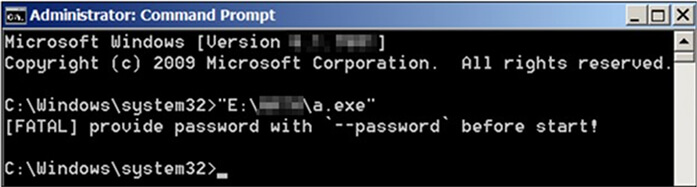
Error prompt when the sample was executed (Source: Surfaceweb)
In contrast to the Golang variant of Agenda, which accepts 10 arguments, the Rust variant only accommodates three arguments.
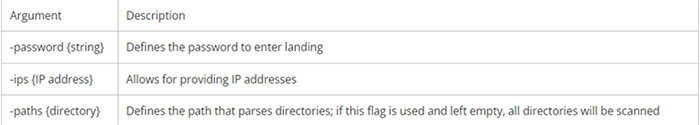
Arguments Accepted by Rust Variant. (Source: Surfaceweb)
Arguments Accepted by Golang variant. (Source: Surfaceweb)
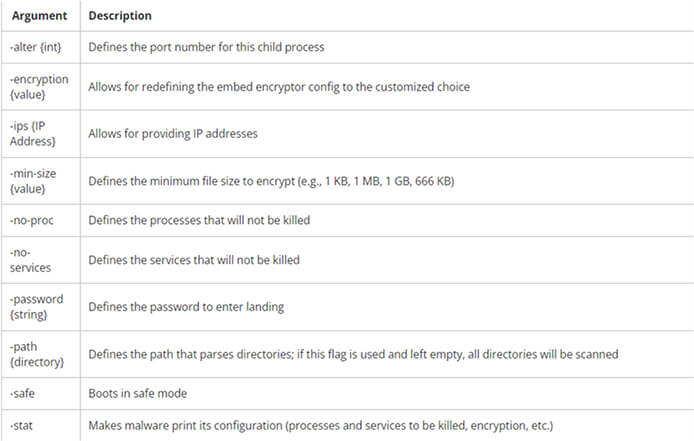
Encryption in both Golang and Rust Variants.
Golang based Variant:
Agenda/Qilin written in Golang employs AES-256 for file encryption and RSA-2048 for encrypting the generated key. To achieve this, it initially generates the key and initialization vector (IV) through the “generateKey” function, utilizing the API “rand_read()”.
Using this randomly generated key, Agenda proceeds to encrypt the target files using AES- 256. Subsequently, it encrypts the key using RSA-2048 with the embedded public key obtained from the runtime configuration.
Rust Based Variant
In its configurations of Rust-based, Qilin introduced additional flags -n, -p, fast, skip, and step, which are absent in the Golang variant configuration and are exclusively utilized through command-line arguments. Upon closer examination, it was discovered that these flags serve the purpose of intermittent encryption. This strategy allows the ransomware to expedite the file encryption process by partially encrypting files based on the values assigned to these flags. The adoption of this tactic is popular among ransomware actors as it enables faster encryption and helps evade detection mechanisms that heavily depend on monitoring read/write file operations.
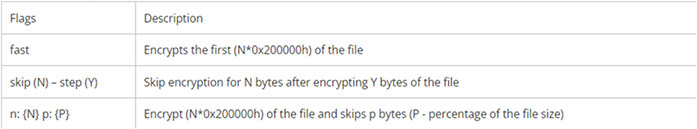
Flags used for intermittent encryption. (Source: Surfaceweb)
In addition to the extra flags employed for distinct encryption modes, the Rust variant has expanded its list of services to terminate by incorporating AppInfo. This inclusion involves the disabling of User Account Control (UAC), a Windows feature designed to prevent malware from running with administrative privileges. This action ultimately hinders the execution of other applications with administrative rights.
Recent Development in Qilin Ransomware
Researchers have found a new variant of Qilin that can be used on Linux, FreeBSD, and VMware ESXi servers, it heavily focuses on encrypting virtual machines and deleting their snapshots.
The encryptor developed by Qilin incorporates an embedded configuration that defines parameters such as the file extension for encrypted files, the processes to terminate, and specifications for files and folders to encrypt or exclude.
Moreover, the encryptor offers a wide range of command-line arguments, providing extensive customization capabilities for configuring how files are encrypted on a server. These command-line options encompass features such as enabling a debug mode, executing a dry run without encrypting any files, and tailoring the encryption process for virtual machines and their snapshots.
The full list of command line options are listed below:
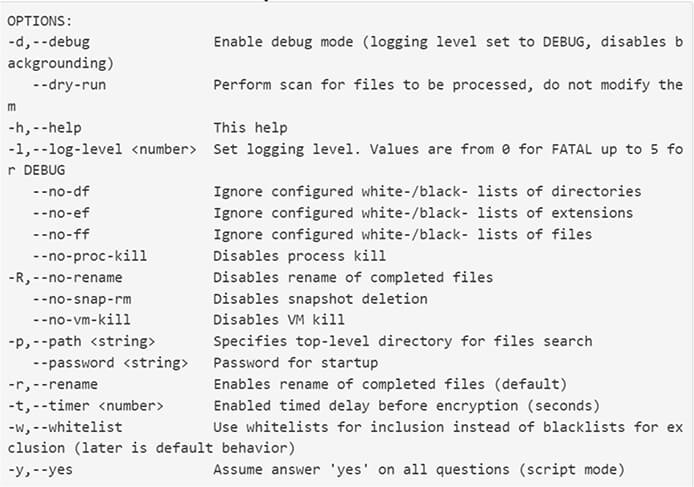
The encryptor is configured by default with the following exclusions and targeting criteria:
Processes to exclude from termination.
“kvm”, “qemu”, “xen”
Directories to exclude from encryption:
“/boot/”, “/proc/”, “/sys/”, “/run/”, “/dev/”, “/lib/”, “/etc/”, “/bin/”, “/mbr/”, “/lib64/”, “/vmware/lifecycle/”, “/vdtc/”, “/healthd/”
Files to exclude from encryption:
“initrd”, “vmlinuz”, “basemisc.tgz”, “boot.cfg”, “bootpart.gz”, “features.gz”, “imgdb.tgz”, “jumpstrt.gz”, “onetime.tgz”, “state.tgz”, “useropts.gz”
File extensions to exclude from encryption:
“v00”, “v01”, “v02”, “v03”, “v04”, “v05”, “v06”, “v07”, “v08”, “v09”, “b00”, “b01”, “b02”, “b03”, “b04”, “b05”, “b06”, “b07”, “b08”, “b09”, “t00”, “t01”, “t02”, “t03”, “t04”, “t05”, “t06”, “t07”, “t08”, “t09”
Directories to target for encryption:
“/home”, “/usr/home”, “/tmp”, “/var/www”, “/usr/local/www”, “/mnt”, “/wp-content/uploads”, “/srv”, “/data”, “/backup”, “/var/lib/mysql”, “/var/mail”, “/var/spool/mail”, “/var/vm”, “/var/lib/vmware”, “/opt/virtualbox”, “/var/lib/xen”, “/var/opt/xen”, “/kvm”, “/var/lib/docker”, “/var/lib/libvirt”, “/var/run/sr-mount”, “/var/lib/postgresql”, “/var/lib/redis”, “/var/lib/mongodb”, “/var/lib/couchdb”, “/var/lib/neo4j”, “/var/lib/cassandra”, “/var/lib/riak”, “/var/lib/influxdb”, “/var/lib/elasticsearch”
Files to target for encryption:
“3ds”, “3g2”, “3gp”, “7z”, “aac”, “abw”, “ac3”, “accdb”, “ai”, “aif”, “aiff”, “amr”, “apk”, “app”, “asf”, “asx”, “atom”, “avi”, “bak”, “bat”, “bmp”, “bup”, “bz2”, “cab”, “cbr”, “cbz”, “cda”, “cdr”, “chm”, “class”, “cmd”, “conf”, “cow”, “cpp”, “cr2”, “crdownload”, “cs”, “csv”, “cue”, “cur”, “dat”, “db”, “dbf”, “dds”, “deb”, “der”, “desktop”, “dmg”, “dng”, “doc”, “docm”, “dot”, “dotm”, “dotx”, “dpx”, “drv”, “dtd”, “dvi”, “dwg”, “dxf”, “eml”, “eps”, “epub”, “f4v”, “fnt”, “fon”, “gam”, “ged”, “gif”, “gpx”, “gz”, “h264”, “hdr”, “hpp”, “hqx”, “htm”, “html”, “ibooks”, “ico”, “ics”, “iff”, “image”, “img”, “indd”, “iso”, “jar”, “java”, “jfif”, “jpe”, “jpeg”, “jpf”, “jpg”, “js”, “json”, “jsp”, “key”, “kml”, “kmz”, “log”, “m4a”, “m4b”, “m4p”, “m4v”, “mcd”, “mdbx”, “mht”, “mid”, “mkv”, “ml”, “mobi”, “mov”, “mp3”, “mp4”, “mpa”, “mpeg”, “mpg”, “msg”, “nes”, “numbers”, “odp”, “ods”, “odt”, “ogg”, “ogv”, “otf”, “ova”, “ovf”, “pages”, “parallels”, “pcast”, “pct”, “pdb”, “pdf”, “pds”, “pef”, “php”, “pkg”, “pl”, “plist”, “png”, “pptm”, “prproj”, “ps”, “psd”, “ptx”, “py”, “qcow”, “qcow2”, “qed”, “qt”, “r3d”, “ra”, “rar”, “rm”, “rmvb”, “rtf”, “rv”, “rw2”, “sh”, “shtml”, “sit”, “sitx”, “sketch”, “spx”, “sql”, “srt”, “svg”, “swf”, “tar”, “tga”, “tgz”, “thmx”, “tif”, “tiff”, “torrent”, “ttf”, “txt”, “url”, “vdi”, “vhd”, “vhdx”, “vmdk”, “vmem”, “vob”, “vswp”, “vvfat”, “wav”, “wbmp”, “webm”, “webp”, “wm”, “wma”, “wmv”, “wpd”, “wps”, “xhtml”, “xlsm”, “xml”, “xspf”, “xvid”, “yaml”, “yml”, “zip”, “zipx”
It is also feasible to configure a list of virtual machines that should not undergo encryption.
Upon execution of the encryptor, the threat actor is required to specify the starting directory for encryption and a specific password associated with the encryptor.
During execution, the ransomware assesses whether it is operating on a Linux, FreeBSD, or VMware ESXi server.
If it identifies VMware ESXi, the ransomware proceeds to execute certain commands, namely esxcli and esxcfg-advcfg. Notably, these commands have not been observed in previous ESXi encryptors.
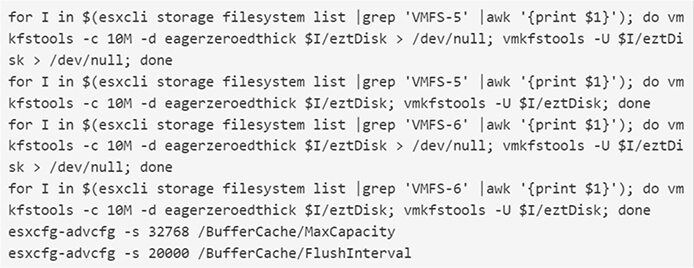
Before encrypting any detected virtual machines, the ransomware will first terminate all VMs and delete their snapshots using the following commands:
esxcli vm process list
vim-cmd vmsvc/getallvms
esxcli vm process kill -t force -w %llu
vim-cmd vmsvc/snapshot.removeall %llu > /dev/null 2>&1
All targeted files will then be encrypted and have the configured extension appended to the file name.
Within each folder, a ransom note titled [extension]_RECOVER.txt is generated. This note includes links to the ransomware gang’s Tor negotiation site and the login credentials necessary to access the victim’s chat page.
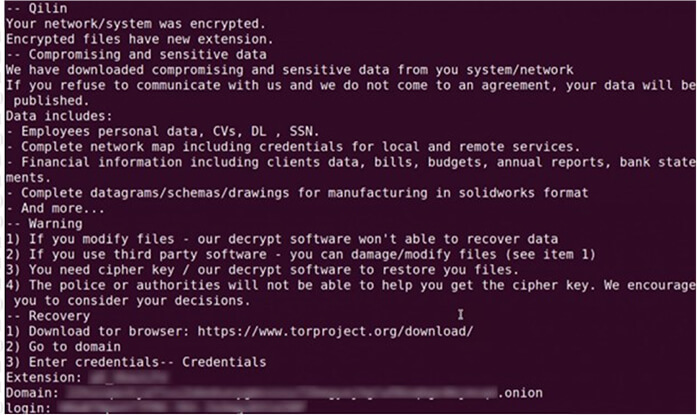
Qilin ransom note (Source: Surfaceweb)
Researchers have noticed that the ransom demanded by Qilin ranges from $25,000 to millions of dollars.
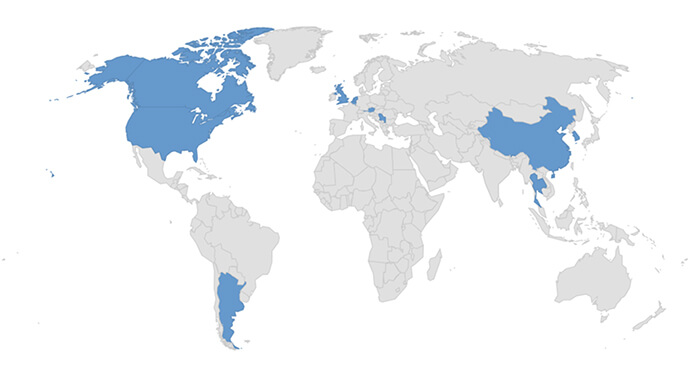
Countries Targeted by Qilin Ransomware
Following are the TTPs based on the MITRE Attack Framework.
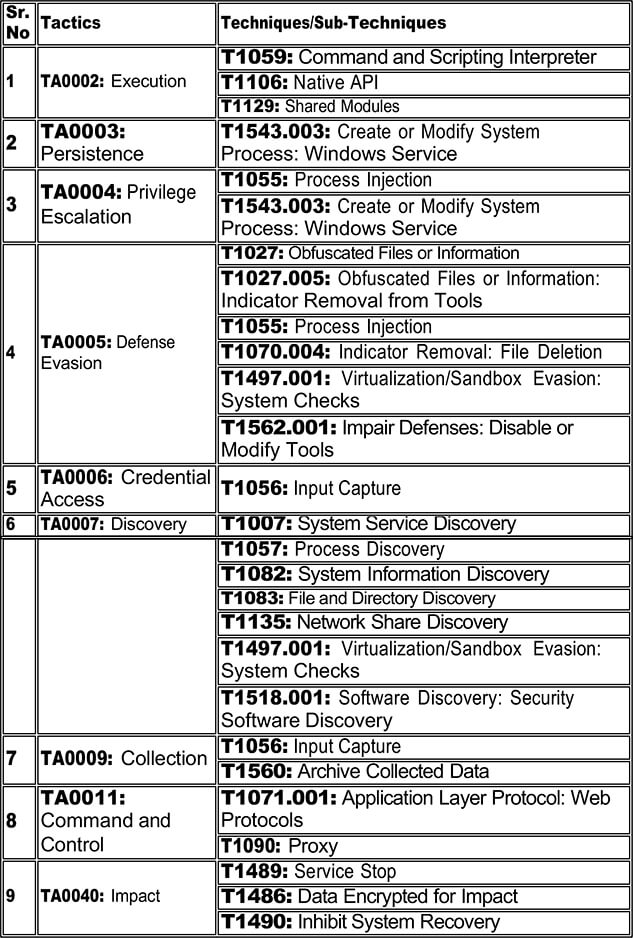
Relevancy and Insights:
ETLM Assessment:
Cyfirma’s assessment, based on available information about the Qilin ransomware, suggests that it is likely to evolve by incorporating advanced evasion techniques and expanding to target more platforms. Future variants may enhance encryption speed and evade detection more effectively. Expect increased customization options for attackers, possibly enabling more precise targeting and higher ransom demands. The ransomware may adopt new strategies to exploit vulnerabilities and target critical infrastructure. As cybersecurity measures improve, Qilin could respond with enhanced obfuscation methods and diversification of attack vectors. Staying vigilant against evolving tactics is crucial, emphasizing the need for robust backup solutions, regular software updates, and user education to mitigate potential impacts.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule:
title: Process Creation Using Sysnative Folder
tags:
– attack.t1055
logsource:
category: process_creation
product: windows
detection:
sysnative:
CommandLine|startswith: ‘C:\Windows\Sysnative\’
condition: sysnative
fields:
– CommandLine
– ParentCommandLine
falsepositives:
– Unknown level: medium
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Remote Access, Espionage
Target Industries: Telecommunications
Target Technology: Linux
Target Geography: Thailand
Active Malware of the Week
This week “Krasue” is trending.
Krasue
Recently, researchers identified a Linux Remote Access Trojan named Krasue, which remained undetected for a considerable period. This malware, initially identified on Virustotal in 2021, has primarily targeted organizations in Thailand, particularly in the telecommunications sector. However, there is a strong possibility that this malware has also been utilized in assaults against organizations in different industry sectors.
Attack Method
Researchers are currently unable to determine the initial infection vector and the extent of Krasue’s usage. Possible entry points for Krasue into a system could be vulnerability exploitation, credential brute force attacks, and less commonly, being unintentionally downloaded from an untrustworthy third-party source in a deceptive package (i.e. a file masquerading as a product update). It has been confirmed that Krasue was employed in targeting telecommunications companies in Thailand, suggesting its likely use in the later stages of an attack after a cybercriminal has already breached the target network.
Krasue’s Covert Networking Tactics Unveiled
Krasue initiates a child process and sets up a UDP socket server on port 52699 to await commands from a Command and Control (C2) server. The communication with the C2 server involves AES-CBC encryption, utilizing a static key, with the author employing the tiny-AES library. The Trojan interprets and responds to C2 commands as outlined below:
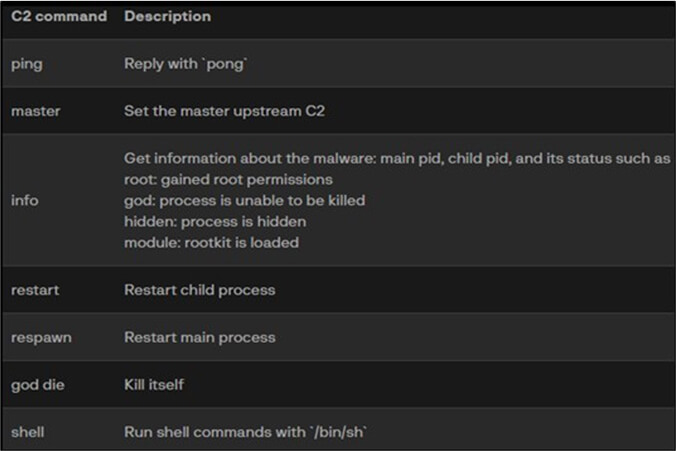
Krasue designates a master Command and Control (C2) by continually sending an alive ping, `DESCRIBE rtsp://server/media[.]mp4 RTSP/1.0\r\nCSeq: 2\r\n\r\n` and receiving a blank space character `\x20` in return. This method utilizes the Real Time Streaming Protocol (RTSP), commonly used for real-time media streams in applications like video streaming.
There are 9 hardcoded IP addresses for its master C2, with Krasue attempting to connect to internal addresses initially. After multiple non-replies, it connects to 128[.]199[.]226[.]11 at port 554, an unusual choice for RTSP. This suggests an attempt to camouflage network communication, a rare tactic in malware. The presence of 8 internal IP addresses may be an effort to mislead sandbox analyses, delaying connection to external IPs. Alternatively, it implies cybercriminals accessed Krasue from within the victim’s infrastructure, possibly using tunnels created during an earlier attack stage. This indicates Krasue is deployed in later attack stages for sustained remote access.
Decoding Krasue: The Art of Evasion
Krasue has managed to go unnoticed for several reasons. Firstly, older Linux servers often lack effective Endpoint Detection & Response (EDR) coverage. Additionally, the malware employs UPX packing, making it more challenging for security solutions to detect. Furthermore, Krasue enhances its evasion tactics by daemonizing itself, running in the background, and ignoring SIGINT signals, ensuring its resilience against interruption signals, such as those triggered by the user terminating the process with Ctrl-C. If the program has root privileges, it can proceed to install a rootkit.
Analysis of Krasue.Rootkit
The Krasue rootkit, functioning as a Linux Kernel Module (LKM), specifically targets Linux Kernel versions 2.6x/3.10.x. LKMs are dynamic object files loaded into the Linux kernel at runtime, extending kernel functionality without requiring full recompilation. Masquerading as a VMware driver and lacking a valid digital signature, the rootkit supports various Linux kernel versions by embedding 7 compiled versions. Upon determining the kernel version from `/proc/version`, the RAT attempts to install the rootkit using the `init_module` function, loading the ELF image into kernel space. As these modules don’t persist after system reboot, it suggests that cybercriminals leveraging Krasue likely establish persistence earlier in the attack chain within the targeted network.
The code seems to be based on 3 different open-source LKM rootkits:
The 7 embedded rootkits are compiled from identical source code, sharing the same functionalities. Notably, all these rootkits feature identical fake metadata, specifically labelled as “VMware User Mode Helper.”
Rootkit Stealth Tactics Unveiled The rootkit uses following methods:
In its initialization phase, the rootkit hides its presence and proceeds to hook critical functions such as `kill()`, network-related functions, and file listing operations. This manipulation conceals its activities and aids in avoiding detection. Specifically, files and directories starting with “auwd” and “vmware_helper” are concealed from directory listings. Additionally, the rootkit enhances stealth by hiding ports 52695 to 52699.
Communication with the rootkit
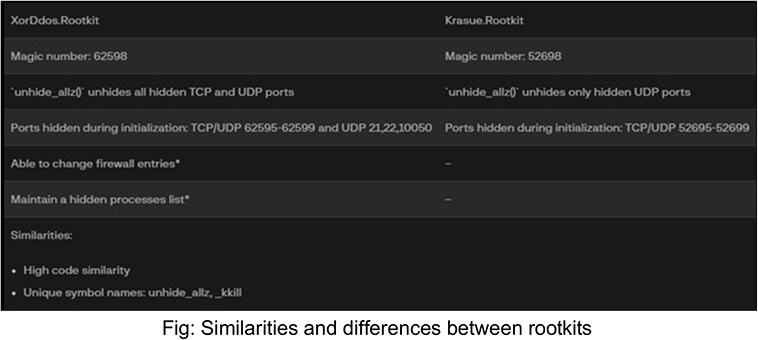
The rootkit component of Krasue exhibits a distinctive overlap with the rootkit of XorDdos, another Linux malware. Notably, the Krasue kernel rootkit encompasses the following functions:
Comparative Analysis with XorDdos
Krasue and XorDdos, both Linux malware, share multiple rootkit similarities. However, Krasue differs by employing signals, not `ioctl()`, for rootkit communication. The rootkit conveniently ignores kill signals by intercepting the `kill()` syscall. Commands are issued to the rootkit via terminal commands like `kill(arg1,signal)` or `kill -signal arg1`. Unaffected signals pass through the regular `kill()` system call. Notably, the author used specific magic numbers such as 52698 and 758.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Krasue’s demonstrated ability to establish covert communication, employ advanced encryption, and use concealment techniques underscores the potential for significant harm. The innovative use of Real- Time Streaming Protocol (RTSP) messages as an ‘alive ping’ introduces a novel challenge for conventional security measures. As technology advances and cyber threats evolve, the impact of sophisticated threats like Krasue is expected to intensify in the future. The cybersecurity landscape will witness an escalation of such intricately designed malware, necessitating the continuous adaptation of defense mechanisms to stay ahead of malicious actors. Collaborative efforts within the cybersecurity community will become increasingly crucial for sharing threat intelligence and developing agile countermeasures to effectively mitigate the evolving impact of threats like Krasue on organizations.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule linux_trojan_unpacked_krasue {
meta:
description = “Detects unpacked linux trojan krasue”
sample =
“902013bc59be545fb70407e8883717453fb423a7a7209e119f112ff6771e44cc”
strings:
$s1 = “DESCRIBE rtsp://server/media.mp4 RTSP/1.0”
$s2 = “%s: main/child pid: %d/%d root/god/hidden/module”
$s3 = “god die”
$s4 = “set master done”
condition:
2 of ($s*)
}
rule linux_rootkit_krasue {
meta:
description = “Detects krasue kernel rootkit, overlaps with xorddos rootkit”
sample =
“3e37c7b65c1e46b2eb132f98f65c711b4169c6caeeaecc799abbda122c0c4a59”
strings:
$s1 = “unhide_allz”
$s2 = “kkill”
$s3 = “is_invisible”
$s4 = “give_root”
$s5 = “hide_tcp4_port”
condition:
4 of them
}
(Source: Surface Web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Operation Blacksmith: Lazarus Group’s APT Campaign Unveiled, Exploiting Log4Shell and deploying malware written in DLang
Summary:
In a recent cybersecurity revelation, the Lazarus Group; a sophisticated hacking collective linked to North Korea, has unleashed a highly advanced operation dubbed “Operation Blacksmith.” In this operation, they employ three new DLang-based malware families, two of which are remote access trojans (RATs). One of these RATs is the Telegram-based “NineRAT,” and the other is a non-Telegram-based RAT named “DLRAT.” Additionally, they utilize a Dlang-based downloader known as “BottomLoader.”
This targeted assault specifically focused on European manufacturing entities in September 2023, South American agricultural organizations, and an American subsidiary of a South Korean physical security firm as early as May 2023.
Operation Blacksmith comprises two main phases, with the Lazarus group exploiting CVE-2021-44228 (Log4Shell) in Phase 1 to gain initial access to publicly facing VMWare Horizon servers. Following the successful exploitation, the Lazarus group initiates preliminary reconnaissance. After the initial reconnaissance of the compromised system, a proxy tool is installed to enable direct access to the infected system. The BottomLoader downloader, is then employed to avoid detection. It is specifically designed for downloading and executing the next stage payload from the remote host, such as HazyLoa.
HazyLoa dynamically switches to a new remote IP address, allowing the threat actors to maintain access as their infrastructure evolves. Additionally, the threat actors create a local account with a name matching a legitimate Windows account and proceed to perform credential dumping using tools like ProcDump and Mimikatz.
Moving on to Phase 2, following the successful completion of credential dumping, Lazarus has introduced a new Remote Access Trojan (RAT) named “NineRAT” and DLRAT. DLRAT incorporates innovative tactics, making it challenging to detect, and its communication with the Command and Control (C2) server has been enhanced, drawing inspiration from the techniques employed by MagicRAT. In DLRAT, session information is hardcoded into the malware as a base64-encoded string.
Once active, NineRAT engages in Telegram-based communication, receiving initial commands to re-fingerprint infected systems. This implies that data collected by Lazarus through NineRAT may be shared among different APT groups, suggesting a separation of data collected during the initial access and implant deployment phase from the data collected through NineRAT.
Relevancy & Insights:
“Operation Blacksmith” by the Lazarus Group reveals a dynamic and sophisticated APT campaign, marked by the adoption of diverse programming languages, including DLang. The use of innovative tactics, such as leveraging Telegram for C2 communication in the NineRAT malware, demonstrates a strategic shift. The existence of sub-groups within Lazarus, like Andariel, highlights collaboration and specialization. Opportunistic targeting of critical sectors and the exploitation of vulnerabilities like Log4j underscore the global impact. The group’s commitment to persistence, redundancy in backdoor entries, and hands-on keyboard activities showcase a multifaceted and adaptive threat landscape, emphasizing the ongoing evolution of APT strategies. Cybersecurity defences must continually adapt to counter these dynamic and sophisticated threats.
ETLM Assessment:
CYFIRMA’s team assessment suggests that the heightened risk of sophisticated cyber threats, as exemplified by the Lazarus Group’s Operation Blacksmith, is likely to persist due to several factors. The use of innovative tactics, diverse programming languages, and collaboration within sub-groups of Advanced Persistent Threats (APTs) indicate a continued evolution in cyber strategies. The increasing interconnectedness of global industries and the opportunistic targeting of critical sectors amplify the potential impact of such campaigns. Moreover, the persistent exploitation of vulnerabilities like Log4Shell underscores the challenge in mitigating risks associated with widely used software. CYFIRMA may emphasize the need for organizations to maintain vigilance, adapt security measures in response to emerging threats, and collaborate within the cybersecurity community to collectively address the evolving and multifaceted nature of cyber risks.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Non-kinetic effects will likely decide the next war according to US Navy
According to a new U.S. Navy cyber strategy, non-kinetic effects rather than missiles, fighter jets and torpedoes are likely to decide the next war on the high seas. The document reflects the central idea that the next fight against a major adversary will be like no other and that the use of non-kinetic effects and defense against those effects prior to and during kinetic exchanges will likely be the deciding factor in who prevails. But the navy sees it as imperative that cyber warfare is far more than networks and cybersecurity. Cyber warfare is presented as a warfighting discipline that should be considered a core competency that is going to play a key role in modern warfare.
ETLM Assessment:
The US Navy highlights the pivotal role of non-kinetic effects and defense against such effects in future conflicts. The potential for massive cyberattacks by advanced state actors like China looms large, threatening to disrupt critical infrastructure and the internet-powered amenities that underpin modern life. The Navy emphasizes that cyber warfare extends far beyond networks and cybersecurity issues, yet neither governments nor businesses are adequately prepared to confront this emerging threat. Asia, once perceived as a region of relative peace, now stands at the precipice of conflict. The international community must urgently address the growing tensions in Asia and establish clear norms of behavior in cyberspace to prevent a catastrophic conflict. Failure to act could lead to a devastating clash with far-reaching consequences.
Chinese hackers targeting critical infrastructure
In what appears to be a staging and battlespace preparation effort, China’s People’s Liberation Army cyber operators have intruded into infrastructure in several countries, with special attention to the United States. According to US officials, the network intrusions are part of a broader effort to develop ways to sow panic and chaos or snarl logistics in the event of a U.S.-China conflict in the Pacific. The staging forms part of the ongoing Volt Typhoon campaign; the latest US disclosures build on February’s annual assessment by the Office of the Director of National Intelligence. Cybersecurity and Infrastructure Security Agency (CISA) has stated on the matter that It is very clear that Chinese attempts to compromise critical infrastructure are in part to pre-position themselves to be able to disrupt or destroy that critical infrastructure in the event of a conflict, to either prevent the United States from being able to project power into Asia or to cause societal chaos inside the United States — to affect the decision-making in the U.S. government in case of a crisis. That is a significant change from Chinese cyber activity from seven to 10 years ago which was focused primarily on political and economic espionage.
ETLM Assessment:
This year, Mustang Panda and other APTs have been focused on countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has allegedly been targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. As we have warned earlier, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way it could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters.
Burton Wire & Cable is Impacted by the Play Ransomware
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: The United States of America
Ransomware: Play Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from The United States of America, (www[.]burtonwire[.]com), was compromised by Play Ransomware. Burton Wire & Cable is a leading manufacturer of quality wire and cable. They manufacture a wide variety of products, which include Communications wire, Fire Alarm, Thermostat, Low Voltage Landscape, Irrigation, Hidden Fence, High Strand Audio, Lamp Cord, Twisted Alarm, Phone, Mining and Blasting Wire. The compromised data comprises private and confidential personal information, client documents, budget details, identification records, scans, financial information, and more.
The following screenshot was observed published on the dark web:
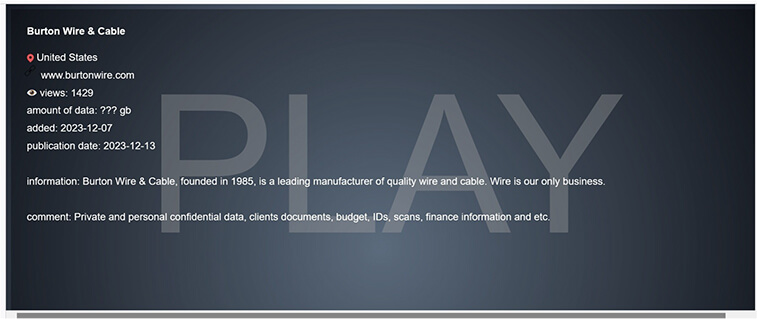
Source: Dark Web
Relevancy & Insights:
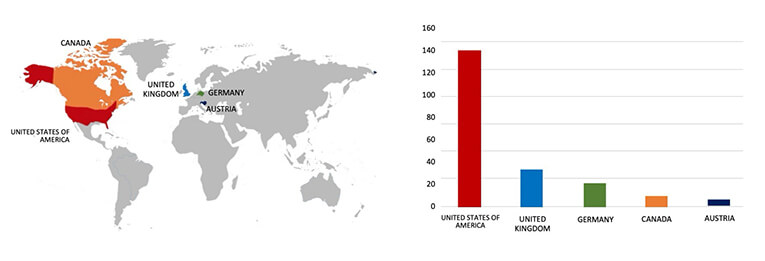
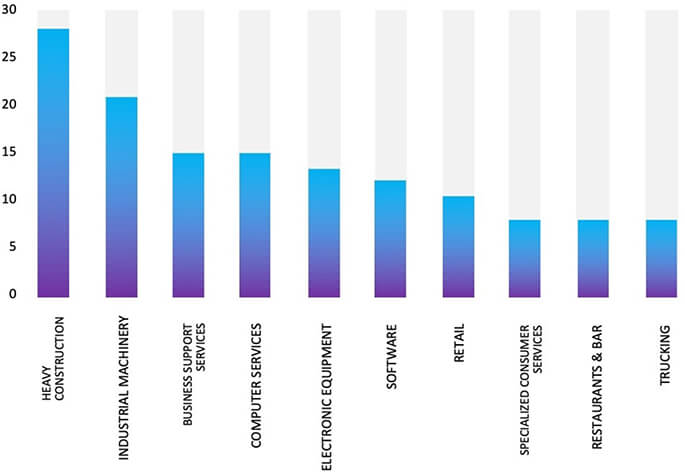
ETLM Assessment:
Our observation indicates that Play Ransomware is now being offered as a service to cybercriminals. CYFIRMA’s assessment remains unchanged: we predict ongoing targeting of US-based companies by the Play ransomware, as depicted in the accompanying graph. However, recent incidents such as the Burton Wire & Cable attack highlight that even other prominent manufacturing corporations are not exempt from potential targeting.
Attack Type: Vulnerabilities & Eploits
Target Technology: Hardware solutions / Firmware
Vulnerability: CVE-2023-23372 (CVSS Base Score 6.1)
Vulnerability Type: Cross-site scripting
Summary:
The disclosed vulnerability allows a remote attacker to perform cross-site scripting (XSS) attacks.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data. A remote user can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in user’s browser in context of vulnerable website.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change appearance of the web page, perform phishing and drive-by-download attacks.
Affected Products:
https[:]//www[.]qnap[.]com/en/security-advisory/qsa-23-40
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
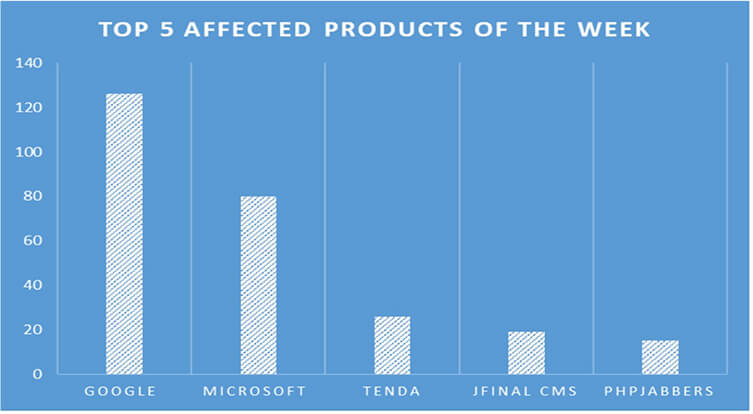
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Ukraine’s biggest mobile operator suffers massive cyber attack.
Summary:
Ukraine’s leading telecommunications operator; Kyivstar, experienced a significant cyberattack, resulting in widespread disruption to cell service and internet connectivity for millions of users. Reports of network and internet outages prompted the company to confirm the incident on Facebook, describing it as a “powerful” cyberattack leading to a “large-scale technical failure.” Fortunately, the company reassured its customers that their data remained uncompromised.
The Ukrainian computer emergency response team (CERT-UA) is actively investigating the cyberattack. Kyivstar’s core network, a pivotal component of the operator’s telecommunications infrastructure, serves as the central hub connecting various regions and countries, facilitating the flow of traffic to external networks like the internet and cloud services. This attack on Kyivstar had a cascading effect on the operations of PrivatBank, Ukraine’s largest state-owned bank. PrivatBank reported disruptions to certain banks, ATMs, and point-of-sale (POS) terminals, attributing the issues to their reliance on Kyivstar SIM cards.
Furthermore, the consequences of the Kyivstar hack extended to critical systems, impacting the air raid alert systems that notify residents of potential missile strikes in the region. The outage had repercussions for 75 small towns and settlements in the Kyiv region. While the identity of the hacking group remains unknown, suspicions point towards Russia. Ukraine’s security service (SBU) has expressed its belief that Russian intelligence services may be involved in the cyberattack.
Relevancy & Insights:
Ukraine’s largest mobile network operator, Kyivstar, reported a significant hacker attack, leading to a temporary disruption of cellular and internet services. The disruption highlights the vulnerability of critical sectors, such as telecommunications, to cyber threats.
ETLM Assessment:
The aftermath of the Kyivstar cyberattack is likely to prompt intensified cybersecurity measures across Ukraine’s critical infrastructure sectors. Authorities need to prioritize bolstering the resilience of telecommunications networks, financial institutions, and emergency alert systems to mitigate the potential impact of future cyber threats. The incident underscores the vulnerability of interconnected systems, necessitating collaborative efforts between government agencies, private enterprises, and cybersecurity experts to enhance threat detection and response capabilities.
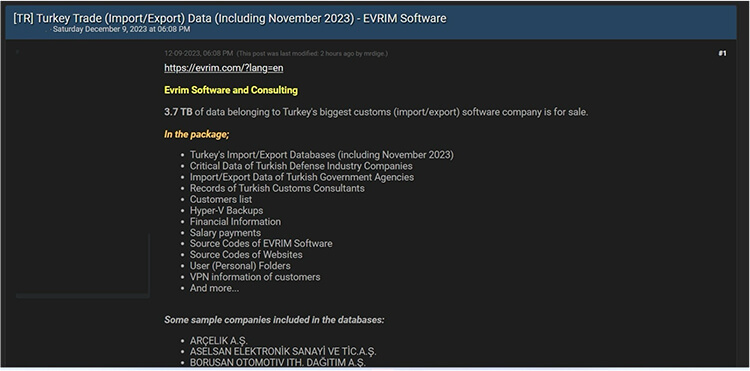
Turkey Trade (Import/Export)- EVRIM Software Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Turkey Trade (Import/Export)- EVRIM Software{www[.]evrim[.]com}. Evrim Software and Consulting is a company that operates in the International Trade and Development industry. The breached information encompasses databases related to Turkey’s imports and exports, sensitive data from Turkish defense industry firms, import/export records of government agencies in Turkey, customer lists of Turkish Customs Consultants, Hyper-V backups, financial details including salary payments, source codes for EVRIM Software and websites, personal user folders, VPN information of customers, and additional data.

Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial incentives are consistently searching for susceptible systems and applications. Most of these perpetrators conduct their activities in clandestine online forums, participating in discussions related to their illicit endeavors and engaging in the trade of pilfered digital assets. In contrast to other financially motivated groups, such as ransomware or extortion collectives, who often publicize their exploits, these individuals prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. The purloined data is subsequently advertised for sale within underground forums, where it may be acquired, repurposed, and utilized by other malicious actors in their attacks.
ETLM Assessment:
According to CYFIRMA’s assessment, organizations in Turkey lacking adequate security measures are likely to be targeted by the threat actor; Mrdige, who predominately focuses on Turkey as a target.
CYFIRMA Research team observed a potential data leak related to Zivame, {www[.]Zivame[.]com} Zivame was founded in 2011 with the vision to facilitate women to shop uninhibitedly for intimate wear and to make lingerie shopping personalized and convenient. Zivame is now the No. 1 online lingerie company in India with 30+ retail stores. The compromised information encompasses details such as the first name, last name, address, city, postal code, country, phone number, email address, monthly user count of 1.1 million, and other confidential data.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS