



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
CYFIRMA Research and Advisory Team has found ransomware known as Xollam while monitoring various underground forums as part of our Threat Discovery Process.
Xollam, a .NET executable, represents a modified iteration of the TargetCompany ransomware strain.
It encrypts files, appends the “.xollam” extension to filenames, and creates the “FILE RECOVERY.txt” text file containing a ransom note.
The TargetCompany ransomware, which first appeared in June 2021, has undergone multiple name changes, reflecting significant updates like encryption algorithm modifications and different decryption characteristics. Initially, it appended “.tohnichi” extensions, reflecting targeted attacks on specific victim companies. Subsequently, the group used victim organization names as extensions. Security experts later dubbed it “TargetCompany.”
Variants like Tohnichi (2021), Mallox, and Fargo (2022) exploit Microsoft SQL Server vulnerabilities to breach enterprise defences.
Researchers found that Xollam employed a technique resembling phishing attacks by utilizing Microsoft OneNote files to infiltrate enterprises and disseminate malware. This new variant of TargetCompany ransomware spreads through spam emails that carry malicious OneNote attachment files.
It is found that Xollam employs a fileless technique akin to using PowerShell for reflective loading, enabling the downloading of malicious files.
The Xollam strains were also found on the SQL server which is hosted in Azure. TargetCompany ransomware group employs multiple tools for evading and disabling antivirus software, like GMER and Advanced Process Termination. Additionally, the presence of YDArk.exe (PCHunter64) is seen as potentially used for rootkit functionalities.
The ransomware group also attempts to deploy a program called KILLAV to halt security software processes and services. Furthermore, it installs a batch file named “killer.bat” to terminate various services and applications, including those related to GPS, and gathers system information, including computer details and related data.
This ransomware employs encryption techniques, including ChaCha20, Curve25519 (an ECC algorithm), and AES-128, to encrypt the victim’s files.
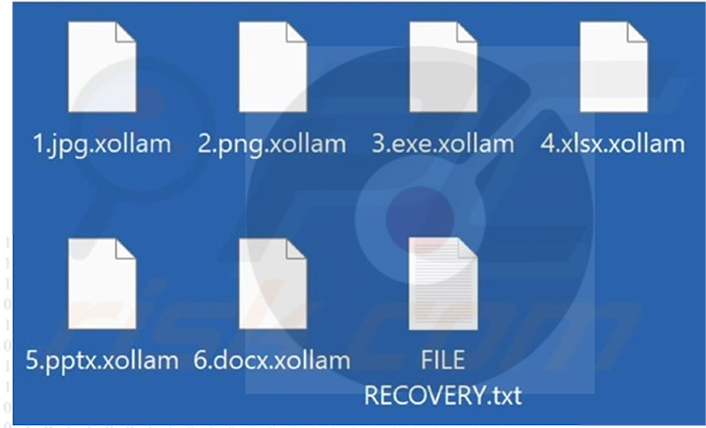
Screenshot of a Files Encrypted by Xollam Ransomware. (Source: Surface Web)
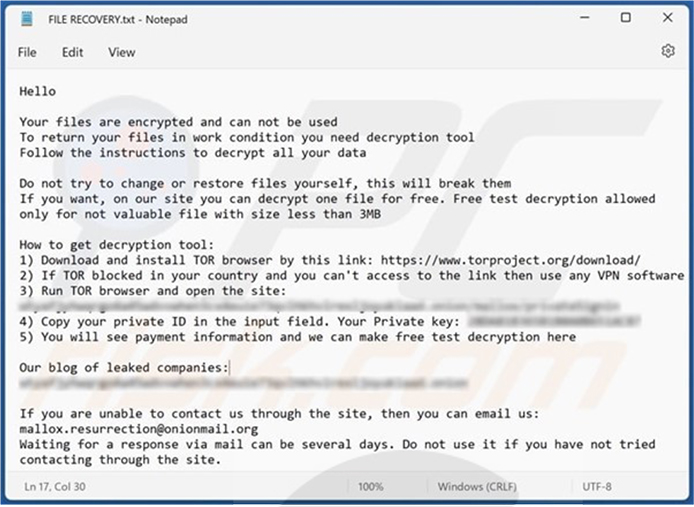
Screenshot of a ransom note by Xollam Ransomware. (Source: Surface Web)
CYFIRMA’s Assessment based on available information states that, the TargetCompany ransomware group, including its variants like Xollam, has demonstrated an evolving and sophisticated threat landscape. These attackers continuously adapt their tactics, techniques, and procedures, making it challenging to predict specific future targets. However, organizations across various industries, especially those with vulnerable Microsoft SQL Server deployments, should remain vigilant. Additionally, businesses relying heavily on Microsoft technologies may face increased risk. We will continue to monitor and provide a more comprehensive assessment when further information becomes available.
Following are the TTPs based on MITRE Attack Framework.
| Sr.No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001:Initial Access | T1566: Phishing |
| 2 | TA0002:Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1569.002: System Services: Service Execution | ||
| 3 | TA0003:Persistence | T1543.003: Create or Modify System Process: Windows Service |
| 4 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| 5 | TA0005: Defense Evasion | T1036: Masquerading |
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 6 | TA0007:Discovery | T1010: Application Window Discovery |
| T1016: System Network Configuration Discovery | ||
| T1018: Remote System Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 8 | TA0040:Impact | T1486: Data Encrypted for Impact |
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli: CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
Type: Information Stealer
Objective: Data theft
Target Technology: MacOS
Active Malware of the Week
This week “MetaStealer” is trending.
Researchers have identified a new malware called MetaStealer, which is targeting Apple macOS. This malware is the latest addition to a growing list of information-stealing malware families that specifically target the macOS platform. MetaStealer stands out from recent information-stealing malware due to its unique characteristics and shows interesting similarities with other malicious software. This highlights the proactive tactics of threat actors who are targeting macOS businesses by pretending to be fake clients and manipulating victims into activating harmful payloads.
Researchers have observed the samples of MetaStealer are distributed in malicious application bundles contained in disk image format (.dmg) with names indicating that the targets were business users of Mac devices. MetaStealer disk images contain names such as,
The disk image droppers often feature names like “Official Brief Description,” for instance, “(Cover references, tasks, logos, brief) \ YoungSUG_Official_Brief_Description_LucasProd.dmg.” These names imply that they were used as bait to target macOS business users. In a specific incident, a malicious variant of MetaStealer was uploaded to VirusTotal under the name “Contract for payment & confidentiality agreement Lucasprod.dmg,” with a comment from the victim explaining how they were enticed into downloading it.
In addition, various versions of MetaStealer have employed names that impersonate Adobe files or software, like “AdobeOfficialBriefDescription.dmg” and “Adobe Photoshop 2023 (with AI) installer.dmg.” This targeted approach toward business users is somewhat atypical for macOS malware, as it typically spreads through torrent sites or suspicious third- party software sources, where cracked versions of popular business and productivity software are more commonly found.
The MetaStealer disk images contain macOS bundles that include the essential components for validity: an Info.plist file, a Resources folder with an icon image, and a MacOS folder containing the malicious executable. While some versions featured an embedded Apple Developer ID string (Bourigaultn Nathan (U5F3ZXR58U)) within the executable, none of the observed samples had a code signature or utilized ad hoc signing. Consequently, to execute these files, the threat actor would likely need to convince or guide the victim to bypass security measures like Gatekeeper and OCSP. Interestingly, all collected samples are exclusively Intel x86_64 binaries, which means they cannot run on Apple’s M1 and M2 machines without Rosetta’s assistance.
The primary executable within MetaStealer bundles is an Intel x86 Mach-O file containing compiled and heavily obfuscated Go source code. This code has had its Go Build ID removed, and function names have been obfuscated. The obfuscation technique used resembles that seen in obfuscated Sliver and Poseidon malware binaries, possibly attributed to the garble obfuscator or similar tools. Despite the obfuscation, some discernible traces of the binary’s functionality remain, including functions for extracting data from the keychain, retrieving stored passwords, and collecting files. Some versions of MetaStealer also appear to target Telegram and Meta services. Additionally, there have been instances of MetaStealer attempting to establish outgoing TCP connections to specific hosts and ports (13[.]125[.]88[.]10 or 13[.]114[.]196[.]60 on port 3000).
CYFIRMA Observed the continuous improvement and evolution of this by its operators suggest a challenging future for macOS users. As macOS remains the choice of many high-profile individuals, the persistent targeting of this operating system is expected to continue. Various malware families are already focusing on infiltrating macOS, and MetaStealer’s presence adds to this concern. In the coming years, CYFIRMA believes there will be an elevated risk as malware similar to MetaStealer becomes more sophisticated and finds new ways to infiltrate systems, posing a heightened risk to users. The stolen data could be employed for espionage or financial gain, and although macOS malware isn’t widespread, its potential impact on victims could be devastating, making robust cybersecurity practices and vigilance crucial for mitigating future threats.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
New Cyber Espionage Group Redfly Targets Critical Infrastructure
Summary:
In a recent observation, researchers detected a new China-based cyber-espionage group known as ‘Redfly’. The APT group successfully infiltrated a prominent Asian national electricity grid organization, maintaining unauthorized access to its network for a six-month period. Researchers also uncovered the use of ShadowPad malware activities within the organization’s infrastructure from February 28 to August 3, 2023.
ShadowPad is a remote access Trojan (RAT), that was modified as a successor to the Korplug/PlugX Trojan. It was, for a time, available for purchase in underground forums. Additionally, the presence of keyloggers and specialized file launchers was detected, underscoring the extent of the intrusion. Although ShadowPad is a widely available trojan employed by various APT groups, the investigation highlights Redfly’s unique concentration on critical national infrastructure. The ShadowPad variant utilized in these attacks camouflages its components as VMware files for stealthy behavior.
Moreover, it ensures persistence by creating services named after VMware, scheduled to initiate the malicious executable and DLL during system startup. ShadowPad, renowned for its versatility as a modular RAT, supports functions like data exfiltration to the Command-and-Control server, keystroke recording, file searching and manipulation, and remote command execution. The group utilized Packerloader to load and execute shellcodes wrapped within AES-encrypted files, effectively evading antivirus detection. This tool was employed to execute code modifications in driver files, enabling the creation of credential dumps in the Windows registry for future use while simultaneously erasing Windows security event logs.
Relevancy & Insights:
Experiencing such severe attacks is undoubtedly an unfortunate situation for any nation. Nevertheless, there is a silver lining in the whole incident, the attack was successfully identified and thwarted. Detecting and preventing persistent access to critical infrastructure is crucial, as such access could potentially be exploited for strategic offensives in times of conflict or during periods of geopolitical instability. However, following our recommendation section can help such critical industries avoid the attack in the very initial stage.
ETLM Assessment:
Attacks on critical infrastructure by nation-based threat actors like Redfly can leave substantial threats in the future. These attacks not only disrupt essential services, cause economic losses, or could be leveraged during the ongoing war. The interconnected nature of critical infrastructure can lead to negative effects, affecting multiple sectors. Additionally, such attacks may involve data breaches, and theft, posing multifaceted challenges for defense. As attackers continually refine their methods, it is imperative for governments, organizations, and infrastructure operators to prioritize cybersecurity.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
India G20 Cyber Threat
ETLM Assessment:
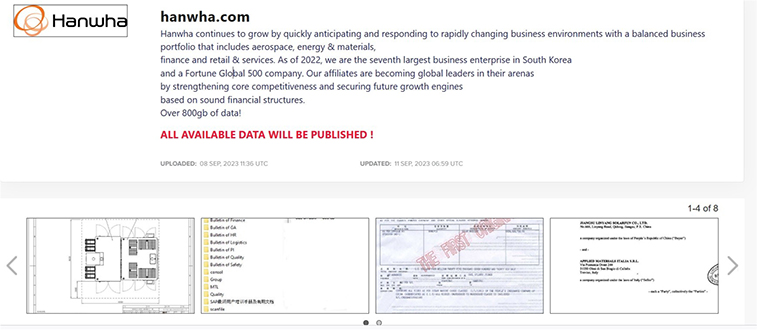
Hanwha Group is Impacted by LockBit 3.0 Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from South Korea, (www[.]hanwha[.]com), was compromised by LockBit 3.0 Ransomware. Hanwha group is a global leader with a diversified business portfolio, covering green energy, materials, aerospace, ocean & mechatronics, finance, and retail and services, Hanwha group delivers future-ready solutions and impactful innovations that power industries and enrich communities. The data that has been compromised remains unreleased on the leak site, suggesting the possibility of ongoing negotiations between the victim and the ransomware group. It is conceivable that the compromised data includes sensitive and confidential information.
The following screenshot was observed published on the dark web:
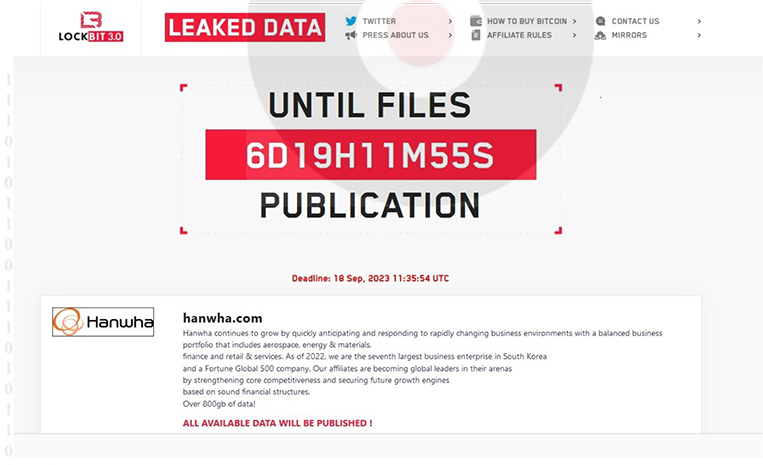
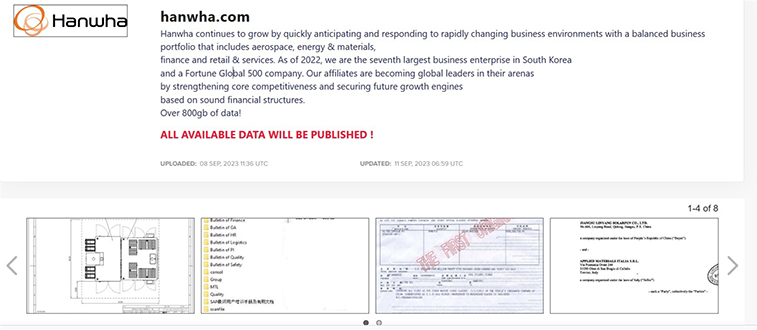
Source: Dark Web
Relevancy & Insights:
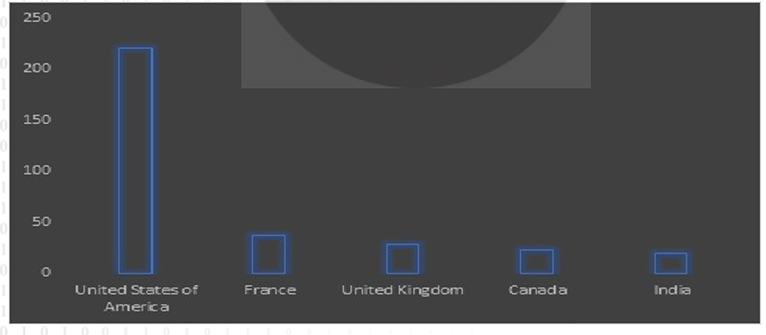
ETLM Assessment:
Summary:
The vulnerability allows a local user to escalate privileges on the system.
Relevancy & Insights:
The vulnerability exists due to usage of an untrusted search path.
Impact:
A local user can place a malicious binary into a specific location on the system and execute arbitrary code with escalated privileges.
Affected Products: https[:]//explore[.]zoom[.]us/en/trust/security/security-bulletin/#ZSB- 23045
Recommendations:
Summary:
The hacker group Anonymous Sudan has launched a distributed denial-of-service (DDoS) attack against Telegram in retaliation to the messaging platform’s decision to suspend their primary account. Purporting to be a hacktivist collective, driven by political and religious motivations, Anonymous Sudan has conducted distributed denial-of-service (DDoS) assaults on entities across Australia, Denmark, France, Germany, India, Israel, Sweden, and the United Kingdom. Since the start of the year, this group has been in operation and set up its Telegram channel on January 18, where they declared their intention to conduct cyberattacks against any entity that opposes Sudan. Their initial activities involved targeting numerous websites in Sweden. Nonetheless, Anonymous Sudan gained widespread attention in June when they initiated a string of disruptive distributed denial-of-service (DDoS) attacks aimed at Microsoft 365, resulting in disruptions to Outlook, Microsoft Teams, OneDrive for Business, and SharePoint Online. Microsoft’s Azure cloud computing platform was also impacted by these attacks. Anonymous Sudan proudly claimed responsibility for the assault on its Telegram channel, and Microsoft, tracking the group under the codename Storm-1359, verified that DDoS attacks were indeed the source of the disruptions. Towards the end of August, the group directed their efforts at X (formerly Twitter), launching a disruptive distributed denial-of-service (DDoS) attack with the aim of pressuring Elon Musk to introduce the Starlink service in Sudan. The assault on Telegram, in contrast to the group’s usual objectives, had a distinct motive, yet it failed to accomplish its goal. Consequently, the hacktivists have temporarily relocated their primary Telegram channel.
Relevancy & Insights:
The observed campaigns have no link to political issues related to Sudan, the group does not seek the support of pro-Islamic groups and only interacts with Russian hackers, and mainly posts in English and Russian, instead of Arabic.
ETLM Assessment:
While the DDoS attack on Telegram is not the normal modus operandi for Anonymous Sudan, and the groups motivations are unclear, it could be that their main account was banned by Telegram. We have seen, they have also previously attacked X (formally Twitter), but their motivations were clearer and this related to the Star link service. We therefore assess that further DDoS attacks against Telegram and its associated platforms are possible if their new account is also banned.
THAIRUNG GROUP’s Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Thairung Group, {www[.]thairunggroup[.]co[.]th}. Thairung is a leading group of companies in the automobile business with more than 40 years of experience, that is now expanding into the property sector. The compromised data consists of customer IDs, first names, last names, districts, provinces, postcodes, phone numbers, fax numbers, mobile numbers, emails, and other confidential information stored in SQL format. The total size of the compromised data is 8 gigabytes.

Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial incentives are perpetually searching for opportunities involving unprotected and susceptible computer systems and software applications. Most of these malicious actors conduct their activities within covert online communities where they engage in discussions related to their illicit pursuits, including the trade of stolen digital assets. In contrast to other financially motivated threat actors, such as ransomware or extortion groups, who often publicize their attacks, these individuals prefer to remain discreet. Their modus operandi involves infiltrating and pilfering valuable information through the exploitation of unpatched systems or vulnerabilities in software or hardware. Subsequently, they promote the stolen data for sale in clandestine online forums, where it may be acquired, resold, and repurposed by other cybercriminals for their own nefarious activities.
CYFIRMA Research team observed a potential data leak related to the Dergi Platform, {www[.]dergiplatformu[.]com}. Dergi Platform is used for academic journals published anywhere in the world, in Turkey, or in electronic media, hosting and management services, offering editorial process. The compromised data includes email addresses, passwords, phone numbers, and various confidential details formatted in SQL.
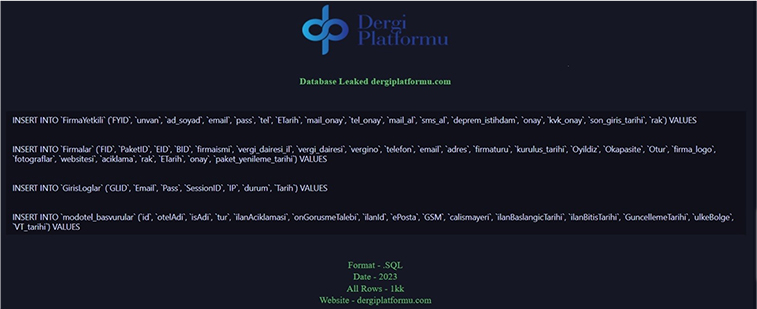
Source: Underground forums