


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technology: Windows OS
Introduction
CYFIRMA Research and Advisory Team has found BAGAJAI Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
BAGAJAI Ransomware:
Researchers have discovered a new ransomware strain called BAGAJAI. This ransomware encrypts victims’ files, renaming them and appending a random extension to filenames (e.g., .BAGAJAI) and creating a ransom note (“read_to_decrypt_files.html “)

Screenshot of files encrypted by ransomware (Source: Surface Web)
CYFIRMA’s assessment indicates that the BAGAJAI ransomware group is demonstrating a steady transition from a traditional file-encryption model to a mature, data-extortion-driven operation. The group employs strong hybrid encryption (RSA-4096 and AES-256), threatens the publication of exfiltrated data, and leverages time-bound ransom escalation alongside anonymous negotiation channels, such as Tor and qTox. Its tactics, offering free file decryption to build trust, emphasizing confidentiality in communication, and using psychological pressure through data-leak threats reflect an increasingly professional and structured operational model. Based on these established behaviors, CYFIRMA assesses that BAGAJAI is likely to expand its double-extortion practices, refine leak-site infrastructure for public exposure, and develop more automated negotiation and payment workflows to scale operations. Over time, the group could evolve into a sustained, service-oriented ransomware entity, aligning with broader trends observed among organized cyber-extortion collectives.
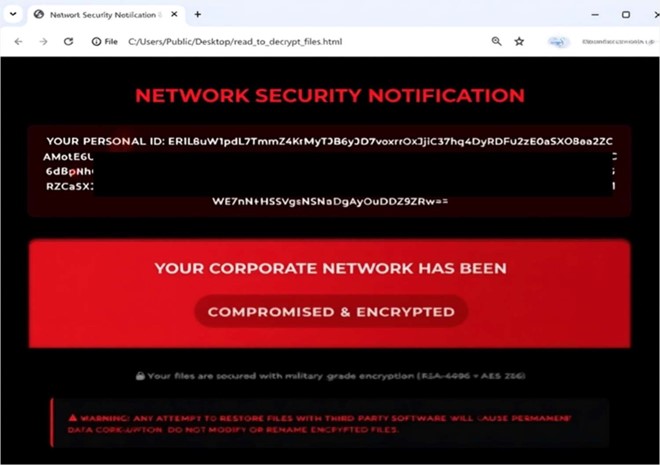
Screenshot: The appearance of BAGAJAI ‘s ransom note (“read_to_decrypt_files.html”) (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1614 | System Location Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that the BAGAJAI ransomware group, based on the material provided and its stated cryptographic choices (AES-256-CTR and RSA- 4096), claims of exfiltrating large volumes of sensitive data, use of timed price/pressure demands (72 hours; 7–14 days), offers of limited free decryptions to build trust, and reliance on anonymous communications (Tor/qTox/email). It is likely to pursue several concrete operational steps: continue and scale combined encryption-plus-data-theft campaigns to increase leverage for extortion; professionalize negotiation and payment workflows (more automated Tor portals, standardized ransom communications and price-adjustment mechanics); broaden and formalize proof-of-theft tactics (expanded sample disclosures and routine test decryptions to accelerate trust and payments); maintain strong anti-forensics and anti-recovery guidance to deter third-party remediation efforts; operate or expand a persistent leak publication capability to maximize reputational pressure; diversify and harden contact/payment channels to retain anonymity and operational resilience; and, over time, explore revenue-scaling arrangements, such as affiliate or partnership models, that would allow third parties to deploy their encryptor under a shared brand—each inference drawn solely from the behaviors and capabilities documented in the material you supplied.
Sigma rule:
title: New RUN Key Pointing to Suspicious Folder tags:
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: selection_target:
TargetObject|contains:
Details|contains:
– ‘%tmp%’
selection_suspicious_paths_user_1: Details|contains: ‘:\Users\’
selection_suspicious_paths_user_2: Details|contains:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\’ Image|startswith: ‘C:\Windows\SoftwareDistribution\Download\’ Details|contains|all:
Image|endswith:
‘SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Spotify’
Details|endswith: ‘Spotify.exe –autostart –minimized’
condition: selection_target and (selection_suspicious_paths_1 or (all of selection_suspicious_paths_user_* )) and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Software using weird folders for updates level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan | Objectives: Credential Theft & Data Exfiltration | Target Technology: Windows OS | Target Industry: Health & Tourism sector| Target Geography: Global
CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “PureRAT” is trending.
Overview of PureRAT Malware
Researchers have recently identified an extensive phishing campaign targeting customers across the global hospitality industry. The operation employed deceptive communication methods, including messages distributed via compromised hotel Booking.com accounts and the WhatsApp platform. Active since April 2025, the campaign distinguished itself through its persistence and authenticity, as threat actors utilized legitimate customer and reservation details to enhance the credibility of their messages. The intrusion process often began with emails designed to resemble genuine customer inquiries, incorporating Booking.com’s visual identity to reinforce legitimacy. Victims were deceived by clicking on malicious links through a method known as the ClickFix social engineering tactic, which enabled attackers to compromise hotel accounts.
Once obtained, these accounts were either sold on illicit platforms or repurposed to disseminate fraudulent messages to guests, primarily to extract financial or personal data. The attackers further employed a sophisticated remote access tool, PureRAT, capable of covertly controlling infected systems and exfiltrating sensitive information. This campaign exemplifies the growing trend of cybercriminals exploiting trusted digital services and psychological manipulation techniques to undermine user confidence, emphasizing the critical need for enhanced cybersecurity awareness and protective measures within the hospitality sector.
Attack Method
The attackers initiated their campaign by exploiting compromised corporate email accounts to deliver malicious messages to hotels across multiple countries. These emails, often impersonating Booking.com, contained legitimate-looking booking references or customer messages to appear trustworthy. Embedded within the emails were URLs that triggered the ClickFix social engineering tactic, a technique designed to deceive victims through a multilayered redirection chain. Once the recipient clicked the malicious link, they were redirected through several domains before arriving at a counterfeit Booking.com extranet page. This fake page instructed users to copy and execute a PowerShell command, masquerading as a routine verification step. By leveraging familiarity with Booking.com’s interface and branding, the attackers successfully exploited human trust to initiate the infection.
Malware Delivery Process
When the PowerShell command was executed, it initiated a sequence of downloads from an attacker-controlled infrastructure. The script first collected system details such as the hostname, OS version, and antivirus information before retrieving a compressed archive containing an executable and multiple DLL files. These files were extracted into the user’s AppData directory, where persistence was established through Windows registry modifications and startup shortcuts. The executable then performed DLL side- loading, activating a loader component that downloaded additional payloads and ensured that the malware could restart automatically after system reboots. Throughout this process, the infected system communicated with the attacker’s command-and- control (C2) server to report progress and confirm successful installation.
PureRAT Malware Execution
The final payload in this chain was the PureRAT remote access trojan (RAT), a powerful malware tool sold as Malware-as-a-Service (MaaS) by the developer “PureCoder.” Once deployed, PureRAT provided full remote control over the compromised system, allowing attackers to perform actions such as screen capture, keylogging, file transfer, webcam and microphone access, and command execution. The malware’s modular design enabled it to dynamically load plugins based on the operator’s objectives, extending its capabilities for data theft or further exploitation. To evade analysis, PureRAT used .NET Reactor obfuscation, encrypted communications over TLS, and fileless execution through AddInProcess32.exe, ensuring its presence remained concealed from most antivirus solutions.
The following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
|
Initial Access |
T1566.002 |
Phishing: Spear phishing Link |
| Initial Access |
T1566.003 |
Phishing: Spear phishing via Service |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
|
Persistence |
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1055 | Process Injection |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Collection | T1113 | Screen Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that in the coming years, tactics exemplified by the ClickFix technique and tools like PureRAT are likely to evolve into even more seamless and adaptive threats. ClickFix-style social engineering—built around trusted digital workflows—may become harder to distinguish from legitimate verification or update processes, allowing attackers to compromise systems through routine user actions. Meanwhile, remote-access tools such as PureRAT are expected to grow more modular and covert, integrating easily with everyday business software and cloud environments. This combination of subtle psychological manipulation and silent technical control could blur the line between compromise and normal activity, making detection increasingly challenging. For both organizations and employees, the lasting consequence may be a gradual erosion of digital trust, where even verified platforms or familiar interfaces could conceal sophisticated intrusions.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule indicators_all
{
meta:
author = “Cyfirma”
description = “Detects supplied malicious URLs, domains, hashes and C2 IP:port indicators”
strings:
/* Explicit URLs */
$u1 = “https://headkickscountry.com/lz1y”
$u2 = “https://activatecapagm.com/j8r3”
$u3 = “https://homelycareinc.com/po7r”
$u4 = “https://byliljedahl.com/8anf”
$u5 = “https://jamerimprovementsllc.com/ao9o”
$u6 = “https://seedsuccesspath.com/6m8a”
$u7 = “https://zenavuurwerkofficial.com/62is”
$u8 = “https://brownsugarcheesecakebar.com/ajm4”
$u9 = “https://hareandhosta.com/95xh”
$u10 = “https://customvanityco.com/izsb”
$u11 = “https://byliljedahl.com/lv6q”
$u12 = “https://ctrlcapaserc.com/loggqibkng”
$u13 = “https://bqknsieasrs.com/loggqibkng”
$u14 = “https://confirmation887-booking.com/17149438”
$u15 = “https://verifyguest02667-booking.com/17149438”
$u16 = “https://guest03442-booking.com/17149438”
$u17 = “https://confirmation8324-booking.com/17149438”
$u18 = “https://cardverify0006-booking.com/37858999”
$u19 = “https://verifycard45625-expedia.com/67764524”
$u20 = “https://ctrlcapaserc.com/bomla”
$u21 = “https://bknqsercise.com/bomla”
$u22 = “https://bkngssercise.com/bomla”
$u23 = “https://bkngpropadm.com/bomla”
$u24 = “https://cquopymaiqna.com/bomla”
$u25 = “https://emprotel.net.bo/updserc.zip”
$u26 = “https://cabinetifc.com/upseisser.zip”
/* Explicit domains */
$d1 = “whooamisercisea.com”
$d2 = “sqwqwasresbkng.com”
$d3 = “whooamisercise.com”
$d4 = “aidaqosmaioa.com”
$d5 = “bqknsieasrs.com”
$d6 = “update-infos616.com”
$d7 = “mccplogma.com”
$d8 = “mccp-logistics.com”
$d9 = “cquopymaiqna.com”
$d10 = “contmasqueis.com”
$d11 = “update-info1676.com”
$d12 = “admin-extranet-reservationsinfos.com”
$d13 = “eiscoaqscm.com”
$d14 = “comsquery.com”
$d15 = “caspqisoals.com”
$d16 = “ctrlcapaserc.com”
$d17 = “admin-extranet-reservationsexp.com”
$d18 = “admin-extranetmngrxz-captcha.com”
$d19 = “admin-extranetrservq-cstmrq.com”
$d20 = “admin-extranetadmns-captcha.com”
$d21 = “extranet-admin-reservationssept.com”
$d22 = “bkngssercise.com”
$d23 = “admin-extranetmnxz-captcha.com”
$d24 = “bknqsercise.com”
$d25 = “admin-extranetadm-captcha.com”
$d26 = “bookreservfadrwer-customer.com”
$d27 = “bookingadmin-updateofmay2705.com”
$d28 = “breserve-custommessagehelp.com”
$d29 = “confvisitor-doc.com”
$d30 = “confirminfo-hotel20may05.com”
$d31 = “guestinfo-aboutstay1205.com”
$d32 = “confsvisitor-missing-items.com”
$d33 = “guesting-servicesid91202.com”
$d34 = “booking-agreementstatementapril0429.com”
$d35 = “booking-agreementaprilreviews042025.com”
$d36 = “booking-viewdocdetails-0975031.com”
$d37 = “booking-agreementstatementapril0225.com”
$d38 = “api-notification-centeriones.com”
$d39 = “booking-visitorviewdetails-64464043.com”
$d40 = “booking-reservationsdetail-id0025911.com”
$d41 = “booking-refguestitem-09064111.com”
$d42 = “reserv-captchaapril04152025.com”
$d43 = “booking-reviewsguestpriv-10101960546.com”
$d44 = “booking-aprilreviewstir-9650233.com”
$d45 = “booking-confviewdocum-0079495902.com”
$d46 = “booking-confview-doc-00097503843.com”
$d47 = “booking-reservationinfosid0251358.com”
/* SHA256 hashes provided */
$hash1 = “703355e8e93f30df19f7f7b8800bd623f1aee1f020c43a4a1e11e121c53b5dd1”
$hash2 = “5301f5a3fb8649edb0a5768661d197f872d40cfe7b8252d482827ea27077c1ec”
$hash3 = “64838e0a3e2711b62c4f0d2db5a26396ac7964e31500dbb8e8b1049495b5d1f3”
/* IP:port combos */
$ip1 = “85.208.84.94:56001”
$ip2 = “77.83.207.106:56001”
condition:
any of ($u*) or any of ($d*) or any of ($hash*) or any of ($ip*)
}
STRATEGIC RECOMMENDATIONS:
MANAGEMENT RECOMMENDATIONS:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT37: North Korea’s Shift Toward Mobile Espionage
About the Threat Actor
Reaper (APT37) is a suspected North Korean cyber espionage group active since 2012, known for its advanced malware development and sophisticated tactics, techniques, and procedures (TTPs). Initially targeting South Korea, Reaper has expanded its operations to Japan, Vietnam, and the Middle East. Their notable campaigns include Operation Daybreak, Erebus, Golden Time, FreeMilk, Are You Happy?, and Evil New Year.
Additionally, malware families and tools such as Konni, Nokki, DogCall, and CarrotBat have been associated with the group’s operations, further demonstrating its technical capability and adaptability. The group has been linked to attacks on academic and strategic institutions, including a Japanese entity associated with a UN human rights project. Reaper’s activities align closely with North Korean state objectives, making it a persistent and evolving threat.
Details on Exploited Vulnerabilities
|
CVE ID |
Affected Products |
CVSS Score |
Exploit Links |
|
CVE-2018-4878 |
Adobe Flash Player |
9.8 |
link |
|
CVE-2022-41128 |
Windows Scripting Languages |
8.8 |
– |
|
CVE-2024-38178 |
Scripting Engine Memory |
7.5 |
– |
|
CVE-2020-1380 |
Internet Explorer |
8.8 |
Link |
|
CVE-2017-8291 |
Artifex Ghostscript |
7.8 |
link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
|
Execution |
T1059 |
Command and Scripting Interpreter |
|
Execution |
T1059.003 |
Command and Scripting Interpreter: Windows Command Shell |
|
Execution |
T1059.005 |
Command and Scripting Interpreter: Visual Basic |
|
Execution |
T1059.006 |
Command and Scripting Interpreter: Python |
|
Execution |
T1203 |
Exploitation for Client Execution |
|
Execution |
T1559.002 |
Inter-Process Communication: Dynamic Data Exchange |
|
Execution |
T1106 |
Native API |
|
Execution |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
Execution |
T1204.002 |
User Execution: Malicious File |
|
Persistence |
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
|
Persistence |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
Privilege Escalation |
T1053.005 |
Scheduled Task/Job: Scheduled Task |
|
Privilege Escalation |
T1548.002 |
Abuse Elevation Control Mechanism: Bypass User Account Control |
|
Privilege Escalation |
T1547.001 |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
|
Privilege Escalation |
T1055 |
Process Injection |
|
Defense Evasion |
T1548.002 |
Abuse Elevation Control Mechanism: Bypass User Account Control |
|
Defense Evasion |
T1036.001 |
Masquerading: Invalid Code Signature |
|
Defense Evasion |
T1027 |
Obfuscated Files or Information |
|
Defense Evasion |
T1027.003 |
Obfuscated Files or Information: Steganography |
|
Defense Evasion |
T1055 |
Process Injection |
|
Credential Access |
T1555.003 |
Credentials from Password Stores: Credentials from Web Browsers |
|
Discovery |
T1120 |
Peripheral Device Discovery |
|
Discovery |
T1057 |
Process Discovery |
|
Discovery |
T1082 |
System Information Discovery |
|
Discovery |
T1033 |
System Owner/User Discovery |
|
Collection |
T1123 |
Audio Capture |
| Collection |
T1005 |
Data from Local System |
|
Command and Control |
T1105 |
Ingress Tool Transfer |
|
Command and Control |
T1071.001 |
Application Layer Protocol: Web Protocols |
|
Command and Control |
T1102.002 |
Web Service: Bidirectional Communication |
|
Impact |
T1561.002 |
Disk Wipe: Disk Structure Wipe |
|
Impact |
T1529 |
System Shutdown/Reboot
|
Latest Developments Observed
The threat actor is suspected of exploiting Google’s Find My Device (Find Hub) functionality to track the GPS locations of targeted individuals and remotely perform factory resets on Android devices. The group has been observed targeting South Korean users via the KakaoTalk messenger platform, with the primary objective appearing to be the exfiltration of sensitive personal and device data.
ETLM Insights
APT37’s evolution reflects a deliberate alignment between its cyber operations and North Korea’s broader intelligence and geopolitical objectives. The group effectively blends espionage with hybrid disruption, with an increasing emphasis on mobile and identity exploitation. Its targeting of NATO-aligned nations and Western- affiliated states underscores the expanding risk landscape associated with North Korea–linked cyber activity.
APT37 operates with a high degree of adaptability and operational tempo, leveraging both custom-developed malware and open-source tools to sustain persistent access and evade detection. The group’s digital footprint has extended beyond its traditional areas of focus, now encompassing a wider range of technologies and infrastructures—including Windows, Android, web browsers, and cloud environments—to support long-term intelligence collection and strategic espionage objectives.
Recent campaigns highlight increasingly sophisticated tactics, techniques, and procedures (TTPs), such as targeted spear-phishing, exploitation of software vulnerabilities, and deployment of advanced modular malware frameworks.
APT37’s evolving capabilities indicate a clear pivot toward mobile platform exploitation and abuse of legitimate services to enable surveillance, data exfiltration, and remote device control.
Looking ahead, the group is expected to integrate cross-platform malware, AI- enabled social engineering, and strategic supply-chain compromises to enhance persistence and extend its intelligence-gathering reach across both state and private-sector targets.
IOCs
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule APT37_Indicators
{
meta:
description = “Detects indicators related to APT37 (ScarCruft) including CVEs, IPs, and domains”
author = “CYFIRMA” date = “2025-11-11”
threat_actor = “APT37 / ScarCruft”
strings:
// Known CVE strings often referenced in attack artifacts or logs
$cve1 = “CVE-2018-4878”
$cve2 = “CVE-2022-41128”
$cve3 = “CVE-2024-38178”
$cve4 = “CVE-2020-1380”
$cve5 = “CVE-2017-8291”
// Domains linked to APT37 infrastructure
$domain1 = “st0746.net”
$domain2 = “crowdon.info”
$domain3 = “joinupvts.org”
$domain4 = “seoulhobi.biz”
$domain5 = “pcpaathshala.com”
// IP addresses associated with malicious activity
$ip1 = “127.0.0.1”
$ip2 = “209.85.147.147”
$ip3 = “209.85.147.106”
$ip4 = “74.125.195.147”
$ip5 = “173.194.67.106”
$ip6 = “173.194.78.99”
condition:
any of ($cve*) or any of ($domain*) or any of ($ip*)
}
Strategic Recommendations:
Management Recommendations:
Tactical Recommendations
Russia’s attacks against Ukraine’s grain sector
Researchers have found that Sandworm, a threat actor linked to Russia’s military intelligence, is deploying wipers against Ukrainian entities in the government, energy, logistics, and grain sectors, trying to undermine the Ukrainian economy. The grain sector is a notable addition to Sandworm’s targeting, as grain exports are one of Ukraine’s primary sources of hard currency revenue.
The researchers add that these attacks are a reminder that wipers very much remain a frequent tool of Russia-aligned threat actors in Ukraine. Although there have been reports suggesting an apparent refocusing on espionage activities by such groups in late 2024, we have seen Sandworm conducting wiper attacks against Ukrainian entities on a regular basis since the start of 2025.
ETLM Assessment:
Sandworm, aka APT44, operates under Russia’s Main Intelligence Directorate (GRU), specifically Military Unit 74455 (Main Center for Special Technologies). The group has been active since at least 2009 and is known for blending espionage, sabotage, and destructive attacks, often in support of Russian geopolitical objectives. Sandworm’s operations have caused billions in global damages and targeted critical infrastructure worldwide, with a primary focus on Ukraine amid Russia’s ongoing invasion. The recent attack shows Russia’s disregard for the global availability of foodstuffs – as we have reported previously – in which Ukraine’s grain plays a large role, as some Middle Eastern and African nations depend on affordable Ukrainian grain. The war will keep affecting Ukraine’s grain exports, and some of the largest importers in the most vulnerable countries will be forced to spend extra on the very basic foodstuffs their populations depend on.
China to execute 5 Myanmar scam bosses
A Chinese court in Shenzhen, Guangdong Province, sentenced five members of a Myanmar-based crime syndicate to death for operating massive scamming compounds near the China-Myanmar border. The court announced the death penalties for syndicate leader Bai Suocheng, his son Bai Yingcang, and other high-profile associates. Five others received life sentences, nine were given prison terms ranging from three to 20 years, and two were handed two-year suspended death sentences, meaning execution could follow further crimes.
Bai Suocheng and Bai Yingcang, former heads of the Kokang Border Guard Force— a militia tied to Myanmar’s military junta—profited from illegal activities, including large-scale scams targeting Chinese citizens. In response, China launched a 2023 cross-border crackdown, arresting tens of thousands, including Kokang crime family leaders. In September, 11 members of the Ming crime family were also sentenced to death for similar scam operations.
Xinhua reported that the Bai syndicate built 41 industrial parks, engaging in telecom and online fraud, casino operations, murder, assault, kidnapping, extortion, forced prostitution, and illegal border crossings. The court alleged they defrauded victims of over 29 billion yuan (approximately $4 billion) and caused at least six Chinese deaths.
ETLM Assessment:
Myanmar remains a hub for the global scamming industry, driving billions in losses through schemes like pig butchering. Recently, Myanmar’s junta claimed to have raided and destroyed parts of the notorious KK Park scam compound near Thailand. Thai authorities detained over 1,600 people fleeing these centers while attempting to cross the border.
Warlock Ransomware Impacts TEIN, INC.
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: Japan
Ransomware: Warlock Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, TEIN, INC., (https[:]//www[.]tein[.]co[.]jp/), was compromised by Warlock Ransomware. TEIN, Inc. is a Japanese company specializing in the design, development, manufacturing, and sales of automotive suspension systems and related parts. The company serves both passenger vehicles and motorsports markets, offering a wide range of products, including lowering springs, OE- shaped shock absorbers, coilovers, and motorsport gear. TEIN operates globally with manufacturing and sales facilities in Japan, the United States, and the United Kingdom. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data contains confidential and sensitive information belonging to the organization.
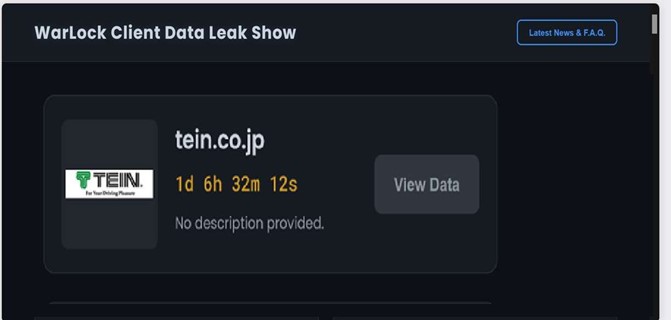
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Warlock ransomware represents a rapidly evolving and high-impact threat in the global cybersecurity landscape in 2025. Warlock operators have demonstrated advanced technical capabilities in gaining initial access, escalating privileges, moving laterally, and deploying ransomware with data exfiltration. Their use of DLL sideloading, legitimate administrative tools for lateral movement, and the “double extortion” tactic of encrypting files while threatening to release stolen data makes this ransomware particularly disruptive.
Qilin Ransomware Impacts Tass Meister Patent Firm
Summary
CYFIRMA observed in an underground forum that a company from Japan, Tass Meister Patent Firm (https[:]//tassmeister[.]com/), was compromised by Qilin Ransomware. Tass Meister Patent Firm is an intellectual-property law firm based in Japan, offering global IP filing, licensing, and enforcement services. The compromised data includes sensitive personally identifiable information (PII), financial records, and other confidential organizational information. The total size of the leaked data is estimated to be approximately 210 gigabytes.
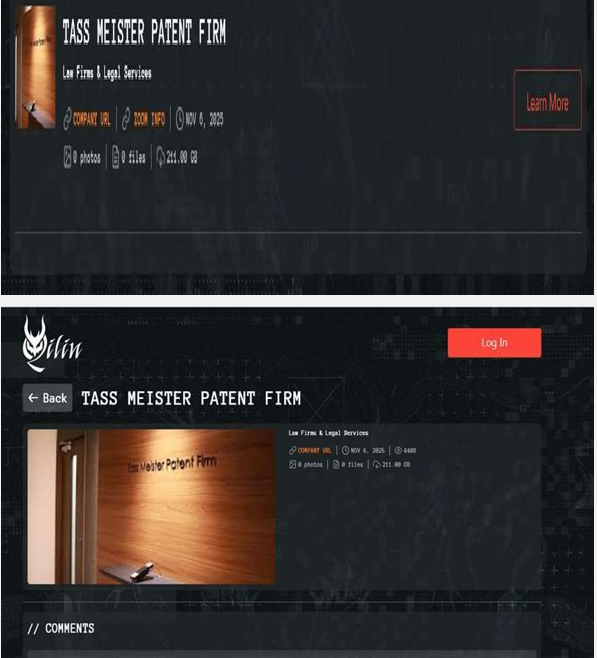

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in the expr-eval JavaScript library
Relevancy & Insights: The vulnerability exists because the application uses the unsafe evaluate() method on untrusted input.
Impact: A remote attacker can pass specially crafted data to the application and execute arbitrary JavaScript code.
Affected Products: https[:]//github[.]com/advisories/GHSA-jc85-fpwf-qm7x
Recommendations:
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
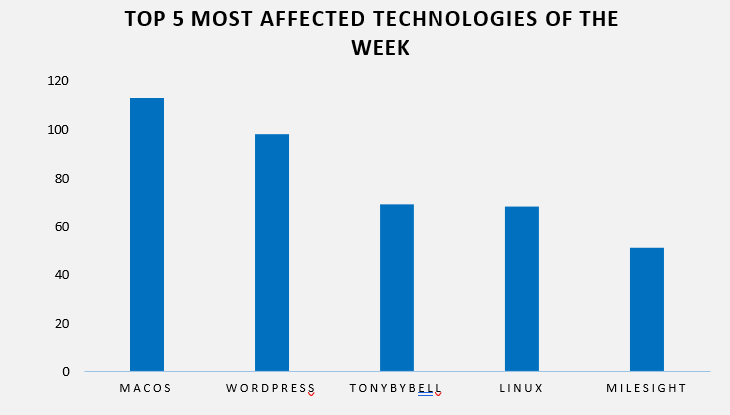
ETLM Assessment
Vulnerability in the expr-eval JavaScript library can pose significant threats to user privacy and application security. This can impact various industries globally, including technology, finance, healthcare, and education. Ensuring the security of expr-eval is crucial for maintaining the integrity and protection of applications that rely on dynamic expression parsing and evaluation.
NightSpire Ransomware attacked and published the data of KONCISE COMPANY LIMITED
Summary:
Recently, we observed that NightSpire Ransomware attacked and published the data of the KONCISE COMPANY LIMITED (https[:]//koncise01[.]com/) on its dark web website. KONCISE COMPANY LIMITED is a company primarily operating in Thailand, specializing in design, construction, and project development services for hotels, resorts, hospitals, and large-scale commercial buildings. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The total size of the data compromised is approximately 2 GB.
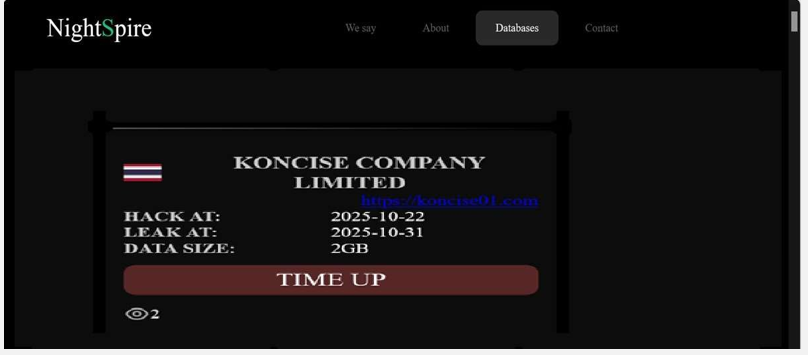
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
Pruksa Holding Data Advertised on a Leak Site
Summary: |
The CYFIRMA Research team observed that a threat actor “AgSlowly” claims to have breached Pruksa Holding Public Company Limited (PSH), one of Thailand’s largest real estate developers. The actor is advertising a database for sale that allegedly originates from the company’s website, pruksa[.]com.
The data dump, totaling 476 MB, reportedly contains a table
named exp_pruksa_member with hundreds of thousands of user records.
According to the actor, the compromised data includes a significant amount of personally identifiable information (PII). The main table alone allegedly contains 463,577 names.
The exposed data fields include:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
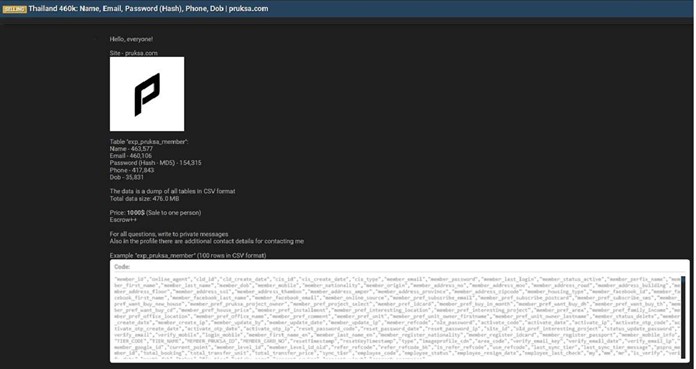 Source: Underground Forums
Source: Underground Forums
Internet Initiative Japan (IIJ) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a hacking group called “KaruHunters” claims the exfiltration and leak of the proprietary source code of Internet Initiative Japan (IIJ), a leading Japanese internet service provider and telecommunications company. This data breach is significant, spotlighting critical cybersecurity challenges faced by major infrastructure and telecom providers.
The dark web post offers downloads of stolen IIJ source code, allegedly obtained through unauthorized access to internal development environments or source code repositories. Source code represents the core intellectual property for IIJ’s network services and cloud infrastructure. The breach indicates a severe compromise either from phishing, vulnerability exploitation, insider threats, or an advanced persistent threat (APT) actor leveraging stealthy tactics.
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
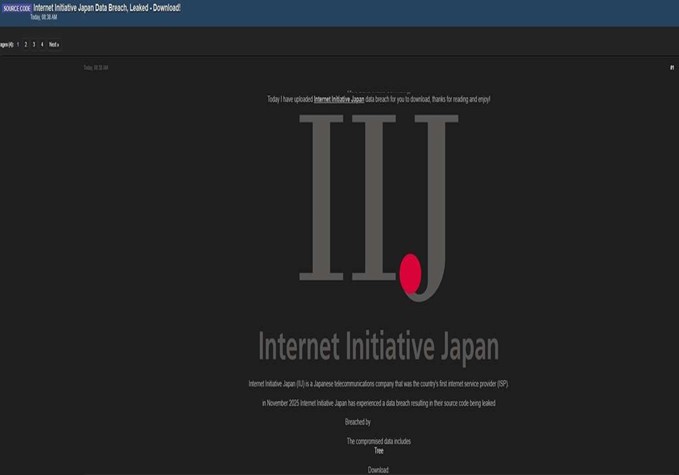
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “KaruHunters” is a highly active and sophisticated group specializing in data leaks. Numerous credible sources attribute multiple security breaches to this group, involving unauthorized access to systems and the illicit sale of stolen data on dark web marketplaces. KaruHunters’ operations highlight the persistent and evolving nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to enhance their cybersecurity posture through continuous monitoring, leveraging advanced threat intelligence, and adopting proactive defense strategies to protect sensitive data and vital infrastructure.
Recommendations:
Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor claims to have breached the National Informatics Centre (NIC), India’s government technology agency. The breach specifically targets the Kavach Authentication App, a two-factor authentication (2FA) tool developed by the NIC for securing access to government email services (like NIC/GOV) and other IT systems. The actor claims to have stolen 1.7 million records.
According to the threat actor, the compromised data from the Kavach app includes:
The actor also claims to be selling further access, including:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
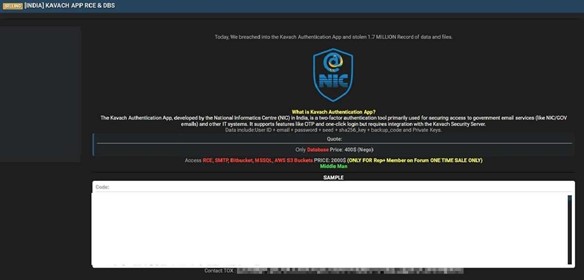
Source: Underground Forums
The CYFIRMA Research team observed that a threat actor claims to have breached and stolen data from Envía, a major Colombian logistics company operated by Colvanes SAS. Envía is a prominent logistics and courier service specialising in freight transport and e-commerce solutions, with operations across more than 1,400 destinations.
The threat actor is offering a large database for sale, allegedly exfiltrated from the company’s systems. The proof provided includes screenshots of internal databases and application backends, suggesting access to sensitive operational and customer information.
According to the actor, the breach involves over 500GB of data, totalling more than 140 million data points. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
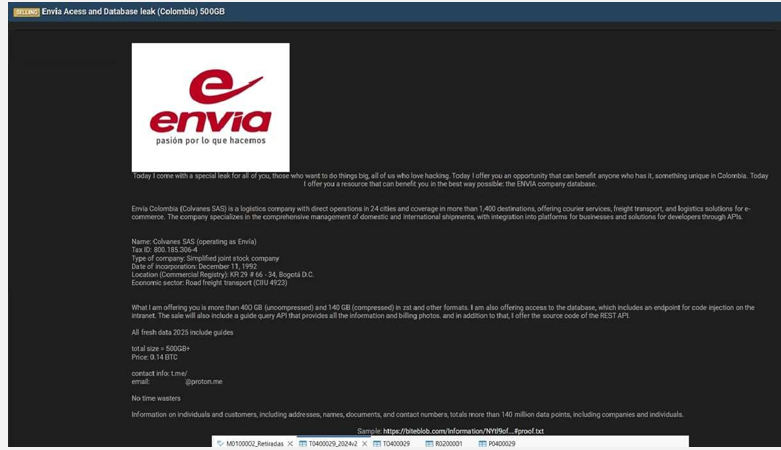
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Situational Awareness – Cyber News
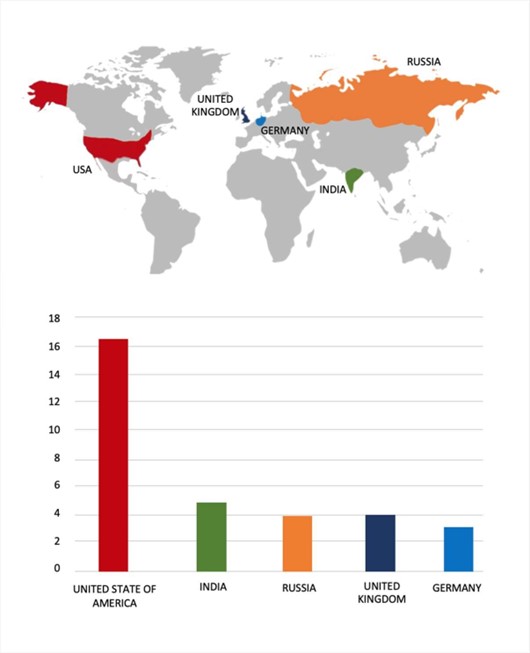
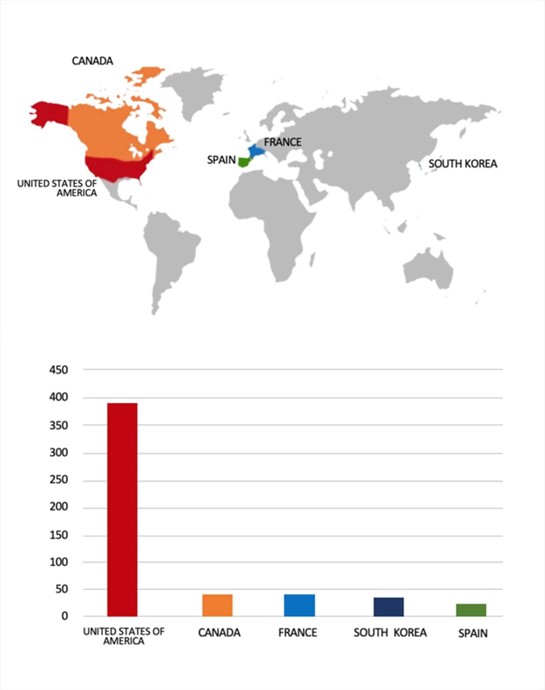
Geography-Wise Graph
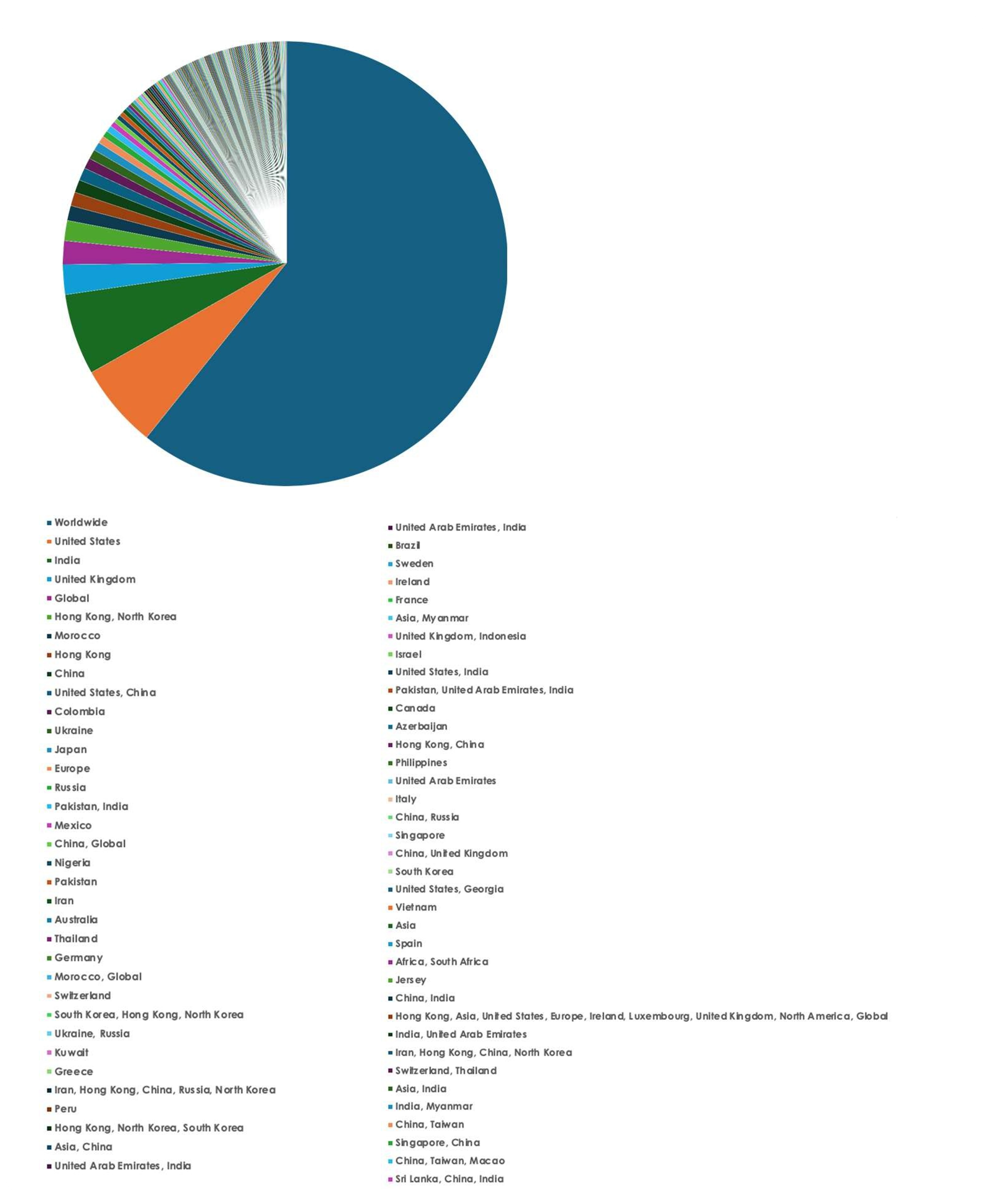
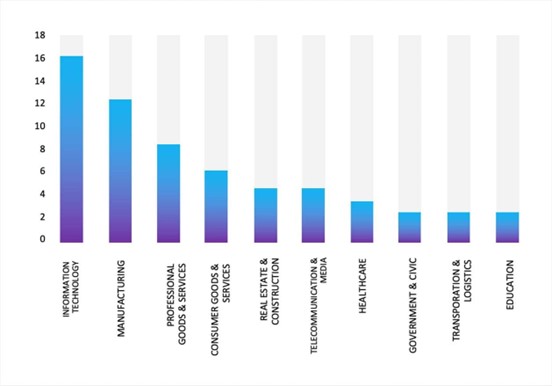
Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.