



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: Windows OS, Linux OS, and macOS.
Target Geography: Australia, Guatemala and the United States.
Target Industry: Consumer Services, Healthcare, Government.
CYFIRMA Research and Advisory Team has found new ransomware known as Cyclops while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy: From the onset of its operation, the ransomware has targeted various industries, recent victims include:
This ransomware targets the widely used Windows Operating System, Linux OS, and macOS, which is prevalent across numerous industries and organizations.
Researchers have recently come across a change in the modulus operandi of an emerging ransomware-as-a-service (RaaS) provider. In addition to providing ransomware services, Cyclops ransomware operators have introduced a separate binary specifically designed for data theft.
The ransomware operators are found to actively advertise their services on various forums, explicitly requesting a portion of the profits generated by individuals leveraging their malware for malicious purposes.
To streamline the distribution process, the RaaS operators offer a dedicated panel that enables easy dissemination of their ransomware across all three major operating systems.
Researchers found some similarities between Cyclops with Babuk and Lockbit ransomware, the similarities are.
Upon extracting the downloaded archive file obtained from the RaaS panel, researchers discovered two key components: the builder binary and a readme.txt file. Notably, the threat actor has privately shared a unique builder ID, which enables the creation of a ransom payload referred to as locker.exe.
In addition to stealer and Ransomware capabilities, the payload is specifically designed with worm-like capabilities that enable it to spread through the network. The accompanying text file contains payload execution instructions with and without command line arguments.
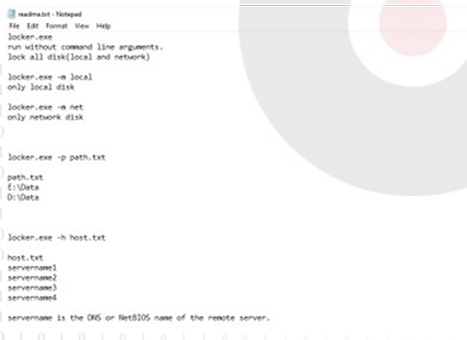
Ransom payload execution command line (Source: Surface web)
The ransomware payload is a compiled executable binary tailored for x64-bit architecture, developed using the VC++ compiler.
The payload performs a comprehensive scan of running processes on the victims’ machines, swiftly terminating any identified process that may impede the encryption of targeted files, ensuring smooth execution of the ransomware’s file encryption process.
Such processes include:
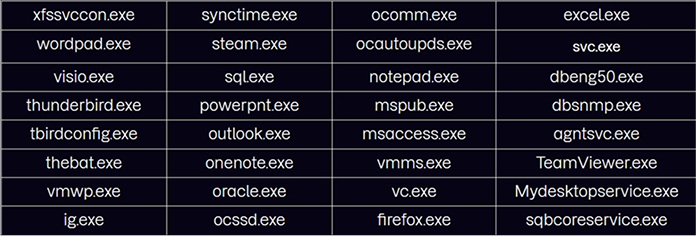
The payload leverages the GetLogicalDriveStrings API to gather crucial information about the logical drives present within the system, enabling it to identify and access the appropriate storage locations for encryption during its operation.
Following the acquisition of drive letters, the payload proceeds to enumerate folders and deposit a ransom note file named “How To Restore Your Files.txt” on the disk. Before encrypting each file, the payload verifies whether its file extension matches the predefined encryption blacklist. If the file extension does not match the specified criteria, the payload initiates encryption and appends a “.CYCLOPS” extension to the encrypted file.
An attacker obtains shadow copy details from a victim system and initiates deletion of a specific shadow copy identified by its ID; it does so by executing the Windows Management Instrumentation command-line (WMIC) utility via a command prompt.

Windows Ransom Note of Cyclops (Source: Surface Web)
The Linux binary of the ransomware is compiled using Golang, with the intentional removal of function names to impede reverse engineering efforts. It utilizes CGO, meaning the source code is written in C and then built using Golang, adding an additional layer of complexity to the analysis process.
When running the sample, it offers the choice to encrypt files within a designated directory, encrypt virtual machines, or enable detailed output.
The encryption process does not apply to files located in the /proc and /boot directories.
Instead, it focuses on encrypting specific file types such as .vmcx, .vmdk, .vmem, .vmrs, .vmsd, .vmsn, .txt, .csv, .lock, .pdb, .csv, and various others.
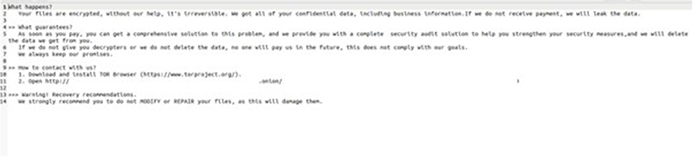
Linux Ransom note of Cyclops. (Source: Surface Web)
Upon completing the encryption process, a comprehensive report is generated, containing statistics regarding the discovered files, encrypted files, encrypted error files, as well as information on the elapsed time and other relevant details.
The ransomware utilizes the CryptAcquireContext function in Windows or the crypto_rand_batched library in Linux to obtain a random 32-byte private key. This private key is used in the ECDH algorithm on Curve25519 to generate a corresponding public key. A shared/session key is derived using the attacker’s hardcoded public and private keys.
The shared key’s SHA512 hash is calculated and used for symmetric encryption, with constants hardcoded in the ransomware. The CRC32 of the SHA512 hash is computed and appended to the encrypted file. Windows employs the HC-256 stream cipher with the SHA512 hash for symmetric encryption, while Linux uses ChaCha. A file marker is added to identify if the file has already been encrypted. The Linux file marker is 00ABCDEF, while in Windows, it is 000000000000000000000000.
The file is compiled in Golang, similar to the Linux variant, and is in the format of a mach-O binary.
On executing the sample, it will provide options to encrypt files in a specific path, or virtual machines, or enable verbose output.
By selecting the ransom execution option, the encrypted files are moved to a specified folder, accompanied by a ransom note named “How to Restore Your Files.txt.”
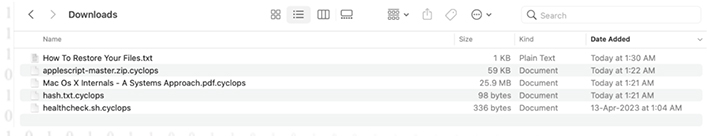
Ransom encrypted folder (Source: Surface web)
Windows stealer:
The master Cyclops panel provides the means to download the stealer. Once the archive file is extracted, two important files become available: “stealer.exe” and “config.json”.
The stealer is designed as an executable binary specifically for x64 systems. Its purpose is to extract valuable system information from targeted machines. This information encompasses details such as the operating system specifics, computer name, number of processes, and logon server.
Afterwards, the stealer proceeds to read the “config.json” file, which is located in the same directory as the stealer’s execution. This configuration file holds a collection of filenames accompanied by their corresponding extensions and sizes.
Next, the stealer scrutinizes the \system32 directory for the existence of unidentified files, (characterized by randomly generated and excessively long filenames).
Next, the stealer scans directories for targeted files and specific extensions. Matches are used to create a password-protected zip file (zip file name-n.zip) containing the identified files and their folder structure. The stolen data is then sent to the attacker’s server for exfiltration.
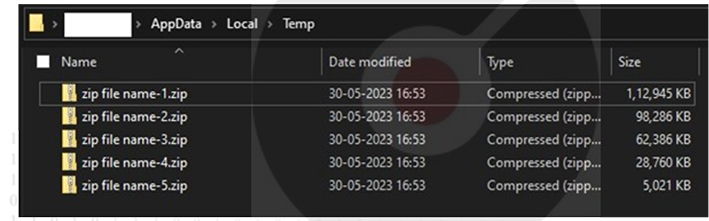
Collected victim files in the temp folder.
The ” zip file name-n.zip” contains files illicitly obtained from the victims’ machines.
Linux stealer:
Similarly, the Linux stealer can also be acquired from the master Cyclops panel. Upon extracting the obtained archive file, researchers come across two files: “stealer.linux” and “config.json”. The functionality of this stealer, which is Golang-compiled, resembles that of the Windows stealer. It begins by reading the “config.json” file situated in the same directory as its execution. This file includes a list of filenames along with their corresponding extensions and sizes.
After enumerating directories, the stealer verifies the existence of targeted files and specific file extensions specified in the JSON file. If any matches are discovered, it generates a new password-protected zip file (named “zip file name-n.zip”) within the /tmp directory. This zip file includes an exact copy of the identified file, preserving its corresponding folder tree structure.
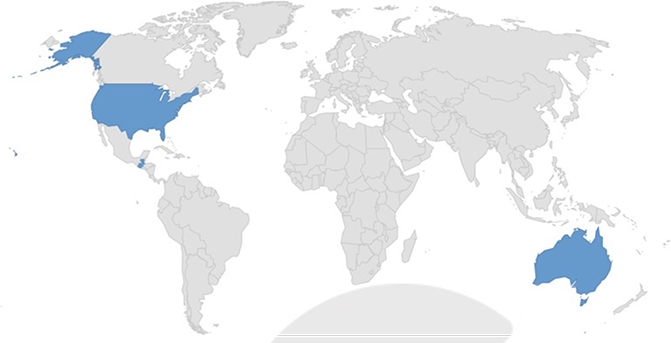
Countries targeted by Cyclops Ransomware.
Following are the TTPs based on MITRE Attack Framework.
| Sr.No | Tactics | Techniques / Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1070.006: Indicator Removal: Timestomp | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| 3 | TA0007: Discovery | T1016: System Network Configuration Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 4 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| 5 | TA0040: Impact | T1486: Data Encrypted for Impact |
Type: Spyware
Objective: Information Stealing & Banking Fraud
Target Technology: Android
Target Geography: South Korea
Target Industry: Banks
Active Malware of the Week
This week “LetsCall” is trending.
Researchers have discovered a new and advanced form of voice phishing (vishing) Malware called “Letscall” that is specifically targeting individuals in South Korea. The criminals behind Letscall employ a multi-step attack strategy, deceiving victims into downloading harmful applications from a fake Google Play Store website. The threat actor group responsible for these campaigns refers to their toolset as Letscall. However, there is the possibility that they could expand their attacks to European Union countries. This framework is readily available and contains all the necessary instructions and tools for operating affected devices and communicating with victims, making it accessible for any threat actor to use.
The attack consists of three stages: The victim visits a specially crafted phishing web page that looks like Google Play Store. From that page, the victim downloads the first stage of the malicious applications chain.
The method by which attackers convince victims to visit the decoy web page containing the Downloader remains unknown, but it could involve Black SEO techniques or social engineering through spam. These deceptive pages imitate the Google Play store and are optimized for mobile screens. It is worth noting that the pages are predominantly in the Korean language, suggesting a focus on targeting individuals in South Korea. Downloaders primary objectives are to download and execute the second stage application, with the payload URL hardcoded into the application, and to open a web view displaying a phishing window, also hardcoded into the application.
The phishing pages employed vary depending on the ongoing distribution campaign. At least three pages have been observed mimicking Banksalad (a loan comparison aggregator), Finda (a loan comparison aggregator), and KICS (Korea Information System of Criminal-Justice Services). Each page tricks victims into entering sensitive information, including their resident registration number (or ID), phone number, home address, salary size, and employer name. This input data is then automatically sent to the attackers. It is highly likely that the same data is intended to be entered into the legitimate web page of the loan aggregator. Attackers may use the exfiltrated data to fill out a similar form on the genuine website to request a loan. Alternatively, the phishing page may act as a proxy between the victim and the loan aggregator page.
The second stage of the attack exploits the legitimate service called ZEGOCLOUD as a provider for Voice over IP (VoIP) communication and messaging. To handle these communications, the attackers utilize relay servers. They make use of both publicly available STUN/TURN servers, including servers from Google, as well as self-configured servers. Unfortunately, the credentials for these servers were leaked within the application code.
This functionality is necessary to establish peer-to-peer (P2P) voice and video connections between the call-center operator and the victim. The same channel is also used for command and control (C2) communication, with various commands being sent.
Additionally, the malware supports communication through web sockets. There may be some overlap between commands received through P2P service and web socket communication.
The “zego” command, depending on its arguments, allows the operator of “Letscall” to start or stop video streaming. This enables the operator to communicate with the victim using the device’s video camera and microphone. There are also 32 other commands that pertain to device fingerprinting, victim location tracking, data exfiltration, and cleaning infection traces.
To exfiltrate data and modify configuration settings, the malware employs traditional HTTP communication. The attacker can configure a whitelist for redirected phone numbers and a blacklist for numbers that should bypass redirection.
Another interesting observation is the use of nanoHTTPD, an application that creates a local HTTP server and then opens the Chrome browser to access it. By exploiting accessibility services, the malware inserts the necessary interface elements within Chrome and delivers the third-stage malware to the victim. This more sophisticated method aims to deceive victims more effectively and convince them that nothing suspicious is occurring.
In the third stage of the attack, the installed APK file bears similarities to the second stage APK. It employs similar evasion techniques and contains XOR-encrypted DEX files in its root folder. This application also possesses a substantial code base. Of particular interest in the third stage is a package called “phonecallapp.” This package contains code responsible for executing a phone call manipulation attack. It intercepts incoming and outgoing calls and redirects them according to the attacker’s preferences.
Within the assets of the third stage APK, there are pre-prepared MP3 voice messages that are played to the victim during outgoing calls to banks. One of these MP3 files, translated from Korean to English,
The purpose of these prerecorded messages is to mimic the experience a customer would have when calling their bank. Additionally, there are other MP3 files that imitate DTMF dialing codes, reproducing the sounds made by pushing numbers on a dialing pad. The third stage also introduces its own set of commands, including those for web socket communication. Some of these commands involve manipulating the address book by creating or removing contacts, while others deal with creating, modifying, and removing call filters.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
TA453 aka Charming Kitten Targets a US-based Think Tank by using LNK and macOS Malware
Summary:
In a recent observation, an Iran-based advanced persistent threat group was observed targeting nuclear security experts associated with a US-based Think Tank. The name of the threat actor is TA453, also known by the names APT35 and Charming Kitten. The threat group is affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), that has been active since at least 2011. Researchers discovered a new development in TA453’s tactics. They have upgraded their Powershell implant called CharmPower (also called GhostEcho or POWERSTAR). In a targeted attack in mid-May 2023, TA453 utilized phishing emails to target a nuclear security expert at a US-based think tank, specializing in foreign affairs. The emails contained a malicious link to a Google Script macro that redirected the victim to a Dropbox URL, hosting a RAR archive.
Within the RAR archive, an LNK dropper was found. It initiated a multi-stage process that culminated in the deployment of GorjolEcho. While presenting a decoy PDF document to deceive the target, GorjolEcho secretly awaited instructions from a remote server. Upon realizing that the target was using an Apple computer, TA453 modified its approach. They sent a second email with a ZIP archive containing a Mach-O binary, disguised as a VPN application. In reality, the binary was an AppleScript that connected to a remote server to download a Bash script-based backdoor called NokNok. Once installed, NokNok retrieved four modules capable of collecting information about running processes, installed applications, system metadata, and established persistence using LaunchAgents. These modules share significant functionality with CharmPower, and there are code similarities between NokNok and macOS malware, previously attributed to TA453 in 2017. Additionally, TA453 employed a fraudulent file-sharing website, likely used for visitor fingerprinting and tracking successful victims.
Insights:
The recent campaign clearly demonstrates Charming Kitten’s remarkable adaptability, as it can effectively target macOS systems when required. This emphasizes the increasing danger posed by advanced malware campaigns to users of macOS.
Chinese hackers targeting the US government with a Microsoft cloud exploit
Researchers have described recent activity by the Chinese state-sponsored APT known as Storm-0558, in which the hackers gained access to email accounts affecting over 25 government agencies and other organizations in the USA as well as private email boxes, likely belonging to individuals associated with these organizations. Researchers took notice of anomalous mail activity mid-June 16th but the inquiry into the problem found that the cyber espionage campaign began a month earlier. The attackers gained access by using forged authentication tokens to access user email, using an acquired Microsoft account (MSA) consumer signing key. Microsoft has completed mitigating the impacts of the activity for all impacted customers since becoming aware of the hack, while the US government is still evaluating the breadth of the Chinese operation and determining the potential harm stemming from the hack.
Storm-0558 has been previously observed attacking governmental agencies in Western Europe and is considered to be a sophisticated threat actor.
Cyberattacks targeting the NATO summit in Lithuania
Researchers have uncovered a new campaign by RomCom, a threat actor that has previously been observed targeting politicians in Ukraine or healthcare services in the US. In its recent campaign, it has been observed using malicious documents to spread its remote access Trojan. The intended victims were representatives of Ukraine and foreign organizations, who were connected to the ongoing NATO Summit in Vilnius on July 11-12. The attackers were sending lure documents using spear-phishing techniques, engaging the targets to click on a specially crafted website. Ukraine’s potential future participation in the defense organization is one of the subjects on the agenda and the threat actor has produced and disseminated a malicious document, posing as the Ukrainian World Congress group, to target Ukraine supporters by exploiting this occasion and the country’s bid to join NATO.
NATO considers Article 5 in cyberspace
The aforementioned Vilnius summit affords an opportunity for NATO to overview its collective cyber defenses. The NATO Cooperative Cyber Defence Centre of Excellence in Tallinn, Estonia has proven its value, and, as cyberspace has become a generally recognized operational domain (called the fifth domain in military jargon), the Alliance may consider ways of enhancing security in the ever-more important fifth domain. One of the considerations that will need to be discussed is the ways in which cyberattacks might trigger the collective defense provisions of Article 5.
Christian-Marc Lifländer, the head of NATO’s cyber and hybrid policy section has recently noted that cyber operations tend to blur lines, which complicates coordination of reaction to them. According to Mr. Lifländer, cyber operations don’t respect organizational boundaries, which means the technical, operational, and political layers must coordinate, to produce a timely and effective response. Better coordination in the fifth domain is one of the goals for the technical staff at the summit. Appropriate Alliance response to threats in the cyber domain, whether they amount to political pressure, disruption, or direct attack against infrastructure is a hot topic and the organization will continue to consider proper institutionalization of coordinated response to cyberattacks in the provisions of Article 5.
CLS Group is Impacted by LockBit 3.0 Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United Kingdom; (www[.]cls- group[.]com), was compromised by LockBit 3.0 Ransomware. CLS Group is a financial services company that assists clients in foreign exchange markets with settlements, processing, and data reports. As of now, the compromised data has not been released on the leak site, suggesting that there may be ongoing negotiations between the victim and the ransomware group. It is possible that the compromised data includes sensitive and confidential information.
The following screenshot was observed published on the dark web:
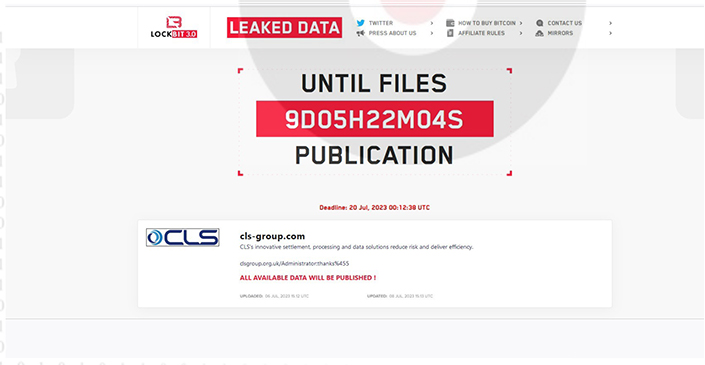
Source: Dark Web
Insights:
Lockbit ransomware threat actors have recently introduced a new variant of Lockbit 3.0 called LockBit GREEN. As per public reports, the LockBit GREEN variant’s source code bears significant resemblances to the Conti ransomware, which was disclosed in March 2022.
LockBit 3.0 ransomware has become a global threat in 2023, infiltrating both private and government organizations worldwide. Notably, the United States of America has borne the brunt, with approximately 70% of victim organizations being based in the country.
Vulnerability in Sensormatic Electronics iSTAR
Summary:
Sensormatic Electronics iSTAR could allow a remote attacker to bypass security restrictions, caused by improper authentication.
Insights:
By sending a specially crafted request, an attacker could exploit this vulnerability to login with administrator rights.
Impact:
An unauthenticated user could log into iSTAR Ultra, iSTAR Ultra LT, iSTAR Ultra G2, and iSTAR Edge G2 with administrator rights.
Affected Products: https[:]//www[.]johnsoncontrols[.]com/-/media/jci/cyber- solutions/product-security-advisories/2023/jci-psa-2023-05[.]pdf
Archive of Our Own (AO3) Suffered Massive DDoS Attack by Anonymous Sudan
Summary:
In a recent observation, Anonymous Sudan conducted a cyber strike, by launching a DDoS attack on Archive of Our Own (AO3). Anonymous Sudan claims themselves to be a hacktivist group and targets anyone with Anti-Sudan and Anti-Russia stance. The popular fanfiction platform Archive of Our Own (AO3) is currently grappling with a wave of distributed denial-of-service attacks (DDoS attacks). Since early Monday morning, the AO3 website has been experiencing intermittent periods of going offline and coming back online, leaving users frustrated. On its Telegram channel, Anonymous Sudan claimed responsibility for launching an attack on AO3 due to certain reasons it is “against all forms of degeneracy, and the site is full of disgusting smuts and other LGBTQ+ and NSFW things”.
Insights:
It is suspected that Anonymous Sudan, who exhibit Islamist motivations, are possibly state-sponsored Russian actors disguising themselves as Sudanese individuals. They employ this facade to camouflage their activities by targeting Western or Western- aligned entities. Furthermore, Anonymous Sudan allied itself with two groups that support Russia, namely Killnet and REvil.
ModuleWorks Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Moduelworks, {www[.]moduleworks[.]com}. ModuleWorks is widely acknowledged as the premier provider of software components for the CAD/CAM industry. Its exceptional proficiency in toolpath creation and simulation has gained industry-wide recognition, making its software components highly esteemed. The leaked data comprises of all project attachments, including HTML-formatted data with screenshots, admin panels, FTP access, server log files, and other sensitive information. The total size of the data is 700MB.
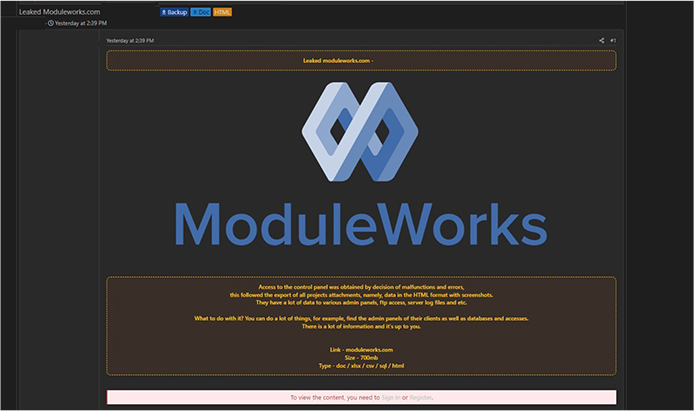
Source: Underground forums
Insights:
Financially motivated cybercriminals are constantly searching for vulnerable systems and applications, employing opportunistic strategies. Many of these attackers participate in underground forums, where they discuss and conduct illegal transactions involving stolen digital assets. Unlike ransomware or extortion groups, who often publicize their attacks, these individuals prefer to maintain a low profile. They exploit unpatched systems and application vulnerabilities to gain unauthorized access and steal valuable data. This stolen data is later advertised, sold, and repurposed by other attackers for their own malicious activities.
CYFIRMA Research team observed a potential data leak related to Parkbench, (www[.]parkbench[.]com). Parkbench is a prospecting tool for real estate agents and mortgage brokers. At the most basic level, Parkbench produces a neighborhood- focused website that provides local information, serving much the same function as the small-town newspaper used to. The publicly exposed data consists of a wide range of sensitive and confidential information, presented in the SQL format, with a total size of 3.5 GB.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS