



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Core Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Core Ransomware
Researchers recently discovered Core ransomware, a new variant within the Makop ransomware family, which is designed to encrypt files and demand a ransom for decryption. Once executed, Core ransomware encrypts data and modifies filenames by appending a unique victim ID, the attackers’ email address, and the “.core” extension. After completing the encryption process, it changes the desktop wallpaper and generates a ransom note in a text file named “+README-WARNING+.txt”, instructing victims on how to recover their files.
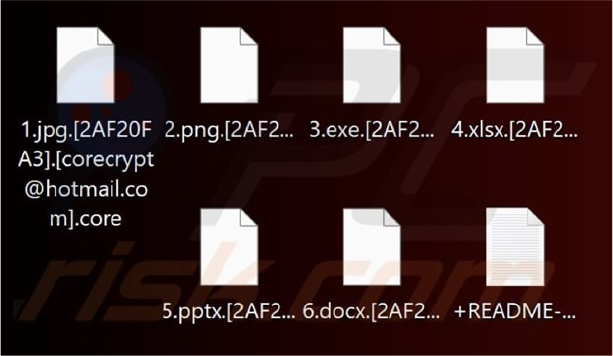
Screenshot of files encrypted by this ransomware (Source: Surface Web)
The ransom note from Core ransomware informs the victim that their files have been both encrypted and stolen. It warns that any attempt to decrypt the files without the attackers’ assistance could make them permanently inaccessible, leading to irreversible data loss.
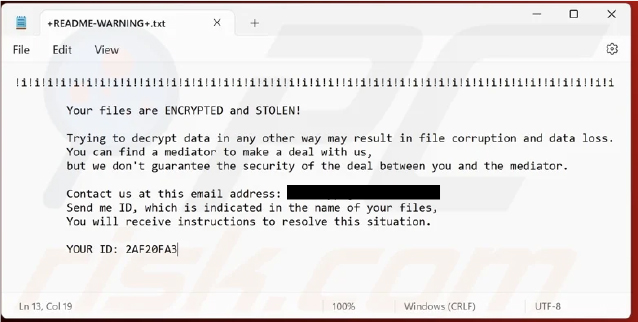
Screenshot of Core ransomware’s text file (“+README-WARNING+.txt”) (Source: Surface Web)
Screenshot of Core’s desktop wallpaper: (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | ID | Technique |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion |
T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion |
T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion |
T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion |
T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Collection | T1115 | Clipboard Data |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
According to an assessment by CYFIRMA, Makop ransomware has been targeting industries such as software, IT, finance, and others on a global scale. This new variant is expected to continue focusing on these sectors due to their high financial value.
Cybercriminals are likely to exploit vulnerabilities within these industries to disrupt operations, steal sensitive data, and demand significant ransoms. This underscores the urgent need for strengthened defense mechanisms to safeguard these high-priority sectors from potential ransomware attacks.
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Web Traffic Manipulation, Unauthorized Redirection Suspected Threat Actor: DragonRank
Target Industries: Government, Universities, Technology, Telecommunications
Target Geographies: India, Thailand, Vietnam, the Philippines, Singapore, Taiwan, South Korea, Japan, Brazil, and Bangladesh
Target Technology: IIS servers
Active Malware of the Week
This week “BadIIS” is trending.
BadIIS
Researchers observed threat actors targeting IIS servers in Asia to deploy BadIIS malware as part of an SEO manipulation campaign. This malware enables attackers to inject malicious content, display unauthorized ads, distribute malware, and conduct watering hole attacks. The campaign appears financially motivated, as infected servers redirect users to illegal gambling sites. Researchers suspect that a Chinese-speaking threat group, known as DragonRank, is behind this activity. Through analysis of extracted domains and strings written in simplified Chinese found in malware samples, researchers believe these variants were likely created and deployed by Chinese-speaking groups. The attack has impacted multiple countries, including India, Thailand, Vietnam, the Philippines, Singapore, Taiwan, South Korea, Japan, and Brazil, with Bangladesh also identified as a potential target.
Researchers also found that victims were not always in the same region as the infected servers. Some users were affected when they visited compromised servers in different locations. The compromised servers belong to government agencies, universities, tech firms, and telecommunications companies, highlighting the widespread risk posed by this campaign.
Attack method
While the initial access method remains unclear, attackers may have exploited vulnerabilities or used zero-day flaws to compromise IIS servers. Once inside, attackers deployed batch files to install BadIIS modules, embedding the malware within the system. These scripts automated the deployment, ensuring persistent access and control over the infected servers.
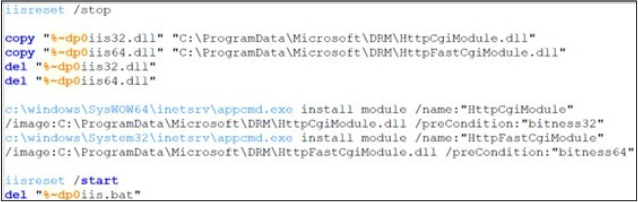
Fig: One of the scripts used for IIS module installation
SEO Manipulation mode
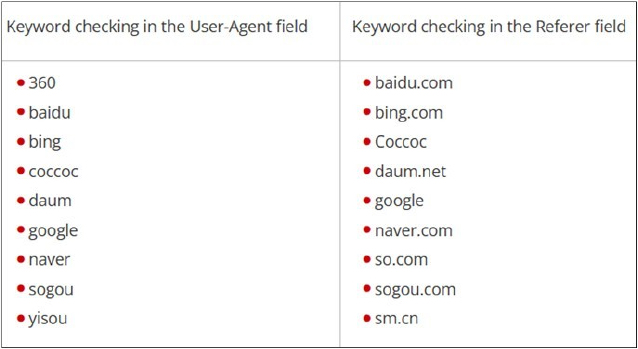
BadIIS operates in multiple modes, one of which focuses on manipulating search engine traffic. Once installed, BadIIS manipulates web traffic by modifying HTTP response headers. It examines incoming requests, specifically looking at the User-Agent and Referer fields. If these fields contain certain search engine sites or keywords, the malware redirects users to illegal gambling pages instead of the intended website. This technique allows attackers to manipulate search results and divert traffic for financial gain.
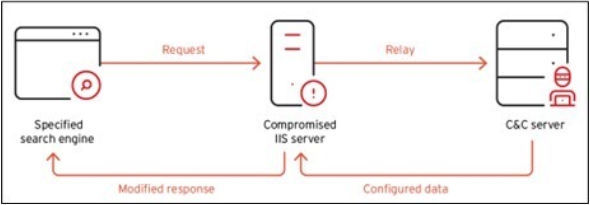
Fig: Workflow of SEO Manipulation mode
Injector mode
Another method used by BadIIS is injector mode, where the malware injects suspicious JavaScript into responses for legitimate visitors, causing them to be redirected to malicious websites. The malware also encrypts its command-and-control (C&C) URL using a simple XOR key, which is decrypted during execution to evade detection.
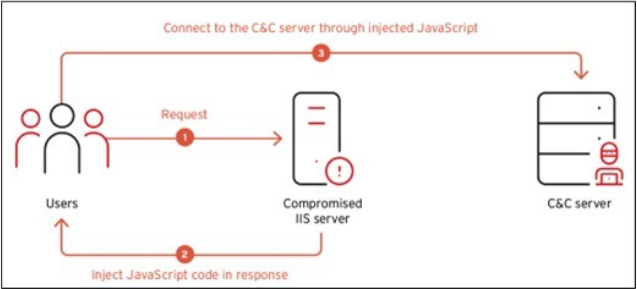
Fig: Workflow of injector mode
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as cybercriminals refine their techniques, future variants of BadIIS or similar malware could evolve beyond SEO manipulation and website redirection. Organizations that rely on web infrastructure for operations, customer engagement, or internal systems may face persistent risks, where their own servers unknowingly become tools for cybercrime. Future versions of BadIIS-like threats might inject malicious scripts that harvest login credentials or manipulate web content to distribute malware. Employees accessing company resources through infected servers may inadvertently expose sensitive data, leading to widespread security breaches, financial losses, and reputational damage. As these threats evolve, they may expand across regions and industries, creating new challenges for businesses as attackers refine their monetization and exploitation tactics.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Analysis of HWP malware incidents attributed to the ‘APT37’ group, delivered via K Messenger
Summary:
The APT37 group, also referred to as the “RoKRAT” group, utilizes a fileless attack strategy, employing a shellcode structure with a hidden 32-bit EXE executable module targeting South Korea. The executable is triggered via XOR logic, allowing it to be activated through PowerShell and shellcode, enabling the malware to execute directly in memory, without leaving any traces on disk. This approach, often referred to as “in- memory execution,” makes detection more difficult by bypassing traditional file-based security measures. Once activated, the RoKRAT module collects sensitive data from the infected machine, including login credentials, email accounts, and online messenger data. This information is then exfiltrated through the pCloud API Token key, a cloud-based storage service, further complicating detection efforts. Additionally, the attackers can install remote control add-ons, providing them with the ability to carry out further exploitation depending on their objectives.
The attack exploits the fact that many users store multiple passwords and remain logged into various services on their personal devices. If the victim leaves their computer unattended or moves around while it’s still on, the attacker can remotely access messenger services or other applications without permission. This allows the attacker to spread malicious files or further compromise the system. The report emphasizes the importance of not leaving computers on in work environments to mitigate such risks.
The attack typically starts with a spear-phishing attempt, wherein the attacker targets the victim with malicious files, often embedded in seemingly legitimate documents.
These files collect information about the victim’s system and can then be used to distribute additional malicious payloads, especially through messaging platforms. The report also highlights the growing sophistication of APT37’s tactics, such as using group chat rooms in messenger applications to further their attacks. Even files sent from trusted contacts can be weaponized to steal identities and carry out further attacks
Relevancy & Insights:
APT37, also known as the RoKRAT group, has been consistently targeting organizations, primarily in South Korea, with sophisticated cyberattacks. Their past operations have heavily relied on spear-phishing techniques, exploiting vulnerabilities in common applications like Microsoft Office. APT37’s use of malicious OLE objects in documents has been a hallmark of their attacks, allowing them to execute code without detection. They have also relied on fileless methods, such as embedding shellcode within documents or leveraging PowerShell, making it harder for traditional security systems to detect their activity. In earlier campaigns, they used trusted contacts and messaging platforms to spread malware and gain access to sensitive systems. The current RoKRAT attack follows a similar pattern but has evolved further. The group now uses cloud-based storage for exfiltrating stolen data and installs remote control modules, demonstrating an increasing sophistication in their tactics to maintain persistence and evade detection while further compromising targeted systems.
ETLM Assessment:
APT37 primarily targets organizations in South Korea, though their reach extends to other regions in Asia and beyond. Their focus includes industries such as government, defense, technology, and telecommunications. APT37 is known for exploiting vulnerabilities in widely used technologies, particularly Microsoft Office, through spear-phishing emails and malicious documents, such as those containing OLE objects.
Earlier, they relied heavily on file-based malware, including remote access tools, while current operations emphasize fileless techniques using PowerShell, shellcode, and cloud-based exfiltration (e.g., pCloud). The group has historically used variants of malware like Emmental, and their attacks often include remote control implants and keyloggers. The threat landscape shows APT37’s continued evolution in evading detection, utilizing social engineering, and deploying sophisticated exfiltration methods. Looking ahead, their tactics are likely to become even more advanced, utilizing zero- day vulnerabilities and more aggressive use of cloud services for persistence and data theft.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
MITRE ATT&CK Tactics and Techniques
| Tactics | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1106 | Native API |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1221 | Template Injection |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Thailand cuts power to Myanmar to disrupt scam hubs
The Thai government cut off power to five towns in Myanmar along the border of northern Thailand in an effort to disrupt online scam compounds. Prime Minister Paetongtarn Shinawatra told the press: “We must take care of our people first. The impact on Thai people and our country’s image has been enormous. It’s time to take decisive action.”
After Myanmar’s 2021 coup, organized criminal gangs established compounds in the area, using them as hubs to orchestrate scams targeting victims worldwide. Many workers in these compounds are effectively enslaved, having been deceived into taking jobs under false pretenses. The majority of these gangs are operated by Chinese nationals.
ETLM Assessment:
Special Economic Zones (SEZs) in northern Laos have effectively become Chinese enclaves, with the most infamous being the Golden Triangle SEZ in Bokeo province. Situated along the Mekong River at the intersection of Thailand and Myanmar, the zone is controlled by the Chinese-owned Kings Romans Group under a 99-year land lease. Reports have repeatedly exposed widespread criminal activity in the SEZ, including money laundering, illegal wildlife trade, and online scam centers, which have proliferated in high-rise buildings within the zone. While Chinese authorities conducted joint raids in some of the zones last year, the problem these scammers are causing over all of Southeast Asia does not seem to be a priority for the Chinese government, let alone the crumbling Myanmar junta.
The Qilin Ransomware Impacts HIKARI SEIKO CO. LTD
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; HIKARI SEIKO CO. LTD. (https[:]//www[.]hikari-seiko[.]co[.]jp), was compromised by Qilin Ransomware. HIKARI SEIKO CO. LTD is a Japan-based top manufacturer of universal joints and precision automotive parts, such as universal joints and oil jets. The compromised data includes emails, reports, maintenance records, restricted-access drawings, production enhancements, cost reduction strategies, labor expenses, pricing matrices, packaging details, quality control records, employee information, an employee database backup, and customer details. The affected companies include Aisin, BYD, ZEEKR, FORD, HONDA, and others. The total size of the compromised data is approximately 502.50 GB.
The following screenshot was observed published on the dark web:
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion make it a particularly dangerous actor.
The Hunters International Ransomware Impacts Sakai Souken Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Sakai Souken Co., Ltd (www[.]sakai[.]co[.]jp) was compromised by Hunters International Ransomware. Sakai Souken Co., Ltd is a Japanese company in the manufacturing and construction industry. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The scale of the data exposure measures approximately 604.4 GB, comprising a total of 2,52,669 discrete files.
The following screenshot was observed published on the dark web:
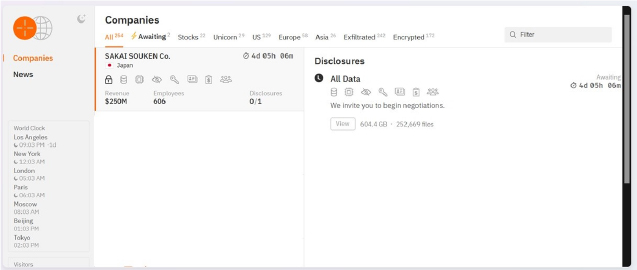
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Hunters International ransomware represents a significant threat within the ransomware landscape due to its sophisticated tactics and focus on double extortion strategies. Organizations are advised to enhance their cybersecurity measures by implementing robust backup solutions, conducting regular employee training on phishing awareness.
Vulnerability in FortiOS CAPWAP
Relevancy & Insights:
The vulnerability exists due to a boundary error in FortiOS CAPWAP control. A remote unauthenticated attacker can send specially crafted UDP packets to the affected service, trigger a stack-based buffer overflow, and execute arbitrary code on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of the vulnerable system.
Affected Products:
https[:]//www[.]fortiguard[.]com/psirt/FG-IR-24-160
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
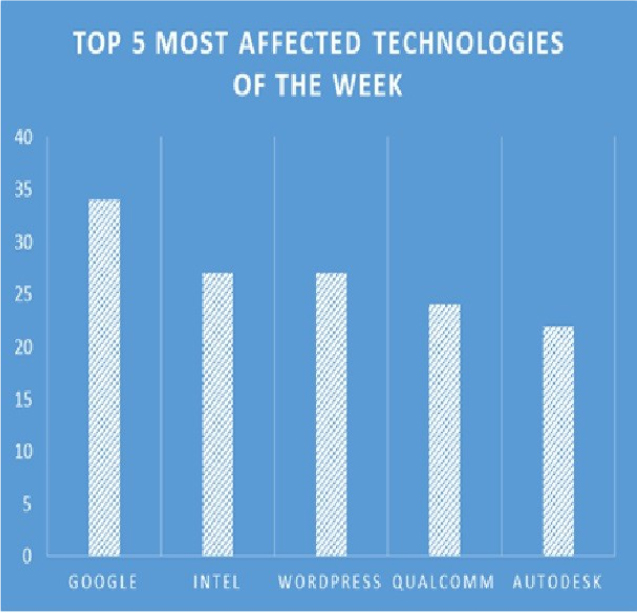
ETLM Assessment:
Vulnerability in FortiOS CAPWAP control can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of FortiOS CAPWAP control is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding wireless network communications, centralized access point management, and secure data transmission across different geographic regions and sectors.
RansomHub Ransomware attacked and published the data of Supreme Group
Summary:
Recently, we observed that RansomHub Ransomware attacked and published the data of Supreme Group(https[:]//supremegroup[.]co[.]in/) on its dark web website. Supreme Group is an India-based conglomerate with a multitude of business interests across various sectors such as commodities, IT, leisure and hospitality, real estate, investments, and luxury. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The total size of the compromised data is approximately 102 GB.
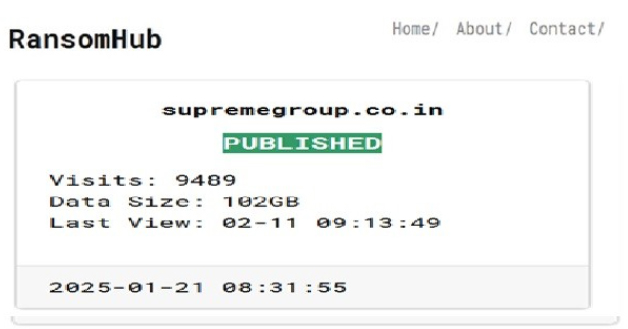
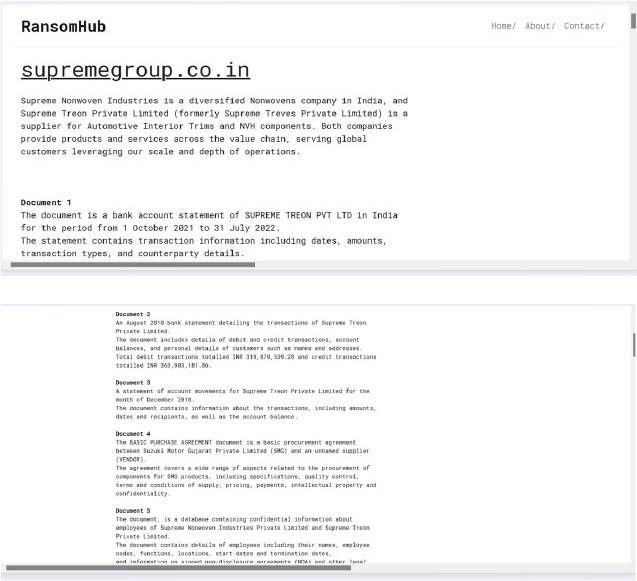
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to recent assessments by CYFIRMA, RansomHub has quickly emerged as a major threat in the ransomware landscape, utilizing aggressive tactics and a strong affiliate model. Organizations are urged to strengthen their cybersecurity defenses and stay alert to potential attacks as the group continues to evolve and expand its operations.
Indonesian government Kota Mojokerto Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to the Indonesian government Kota Mojokerto(https[:]//mojokertokota[.]go[.]id/) in an underground forum. The Government of Kota Mojokerto, Indonesia, is responsible for managing the city’s administration, public services, and regional development. The government operates through various departments and agencies that oversee different sectors, including infrastructure, economy, social welfare, and public safety. The leaked data consists of SQL database files and a portion of Indonesian identity card (KTP) information. The total size of the compromised data is approximately 6 GB. The breach has been linked to a threat actor identified as “KryptonSec My.”
Source: Underground Forums
The Body Shop Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to The Body Shop(https[:]//thebodyshop[.]co[.]th/) in an underground forum. The Body Shop is a revolutionary cosmetics supermarket in Thailand. The compromised data includes customers’ email addresses, names, gender, dates of birth, and address details (both billing and shipping, including country, state, and zip code), as well as billing amounts and billing addresses. The breach has been attributed to a threat actor known as “CanyonGod.”
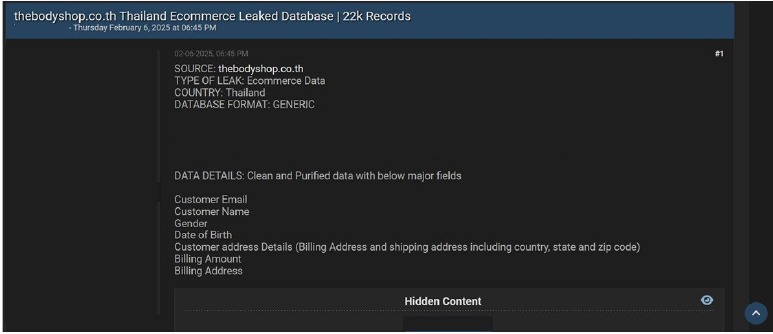
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
A new threat actor, “CanyonGod,” has emerged, and their motives remain unclear, though financial gain, reputational damage, or a combination of both are possible. This actor is responsible for a significant data leak impacting The Body Shop Thailand and its customers. The compromised data includes personally identifiable information (PII), creating substantial risks such as identity theft, phishing attacks, and targeted marketing campaigns. This assessment analyzes the threat landscape, and attack lifecycle, and recommends mitigation strategies to address this incident.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a data leak related to SkidBin in an underground forum. SkidBin was a website designed for users to share text-based content, such as code snippets or written information. It offered features like paste management, editing, and deletion for registered users. The compromised data includes ID, username, hashed passwords, creation date, rank, bio, profile pictures, account status, name, color(s), and login tokens. The total dataset consists of 2,423 rows and is in SQL format. The breach has been attributed to a threat actor known as “Jayze.”

Source: Underground forums
The CYFIRMA Research team observed a data leak related to VideoToolbox (https[:]//www[.]videotoolbox[.]com/) in an underground forum. VideoToolbox is a free online video editor that enables users to convert, crop, merge, and record videos with ease. The leaked data includes ID, profile ID, activation ID, email, status, password, payment status, conversion mode, registration date, newsletter subscription details, as well as sensitive and confidential information. The breach has been attributed to a threat actor identified as “Zix.”
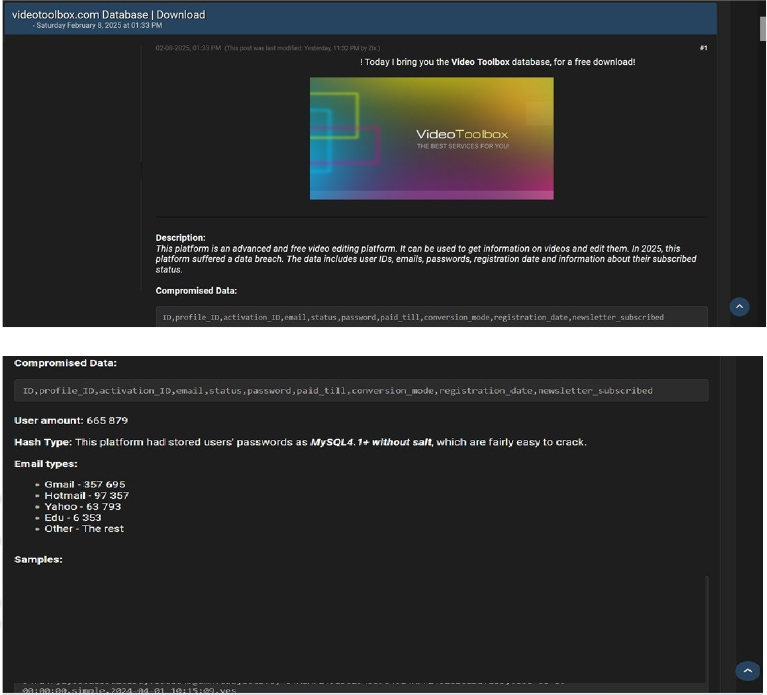
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
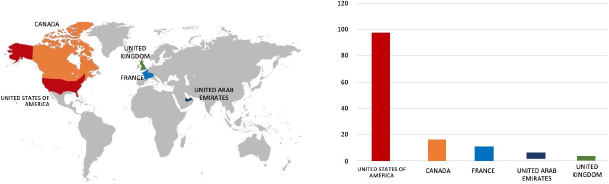
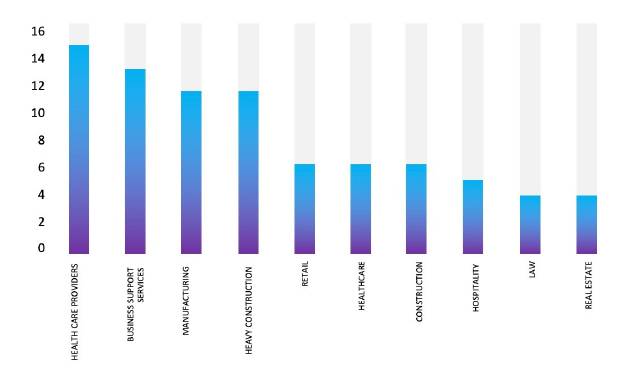
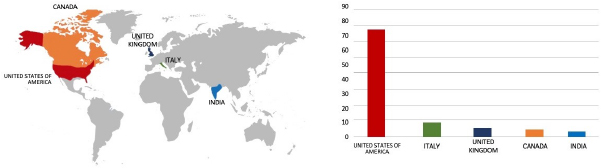
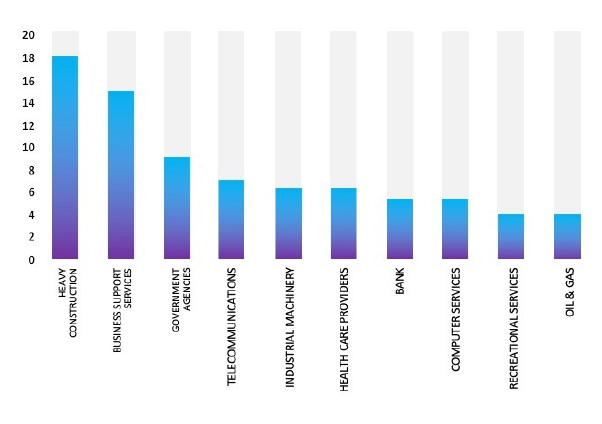
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
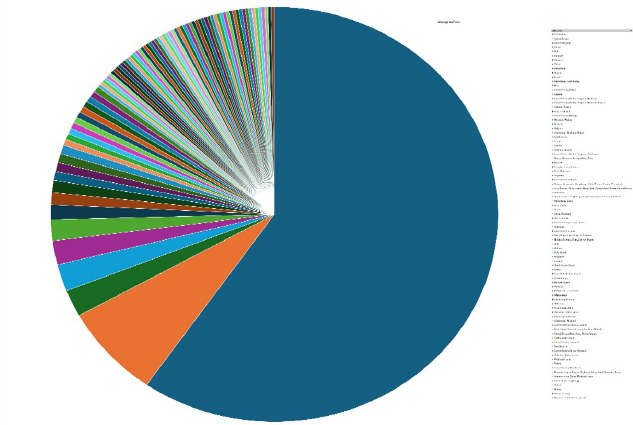
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.