Published On : 2023-10-13
Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Industries: Education, Government entities, Health Care.
Introduction
The CYFIRMA Research and Advisory Team has identified a Megazord ransomware while monitoring various underground forums as part of the Threat Discovery Process.
Megazord Ransomware
Megazord Ransomware made its debut at the end of August 2023. This ransomware, created using the Rust programming language, integrates numerous allusions to the renowned Power Rangers franchise. It encrypts files and appends the ‘powerranges’ extension and delivers the ransom note as ‘powerranges.txt.’
Remarkably, Megazord characteristics align closely with those of the Akira ransomware. There exist multiple static similarities and code resemblances between Megazord and Akira ransomware.
Consequently, it is reasonable to infer that Megazord represents an evolutionary or closely related branch of the Akira ransomware lineage.
The initial access methods employed by the Megazord operators exhibits variability. These methods encompass the use of spear phishing emails and the targeting of vulnerable services. Whenever feasible, Megazord operators make use of LOLBINS and heavily rely on the existing infrastructure of the target to prolong their presence within the network. For lateral movement, the operators leverage Remote Desktop Protocol (RDP) in conjunction with tools such as Advanced IP Scanner and NET.EXE (also known as NET USE).
Upon activation, Megazord initiates attempts to terminate numerous processes and services. The functionality for both process termination and exclusion features bear notable similarity to those observed in the Akira ransomware.
Megazord ransomware takes steps to terminate a significant number of processes and services that could potentially disrupt the encryption process. These actions are executed through distinct CMD.EXE instances, and the following commands are issued by the ransomware:
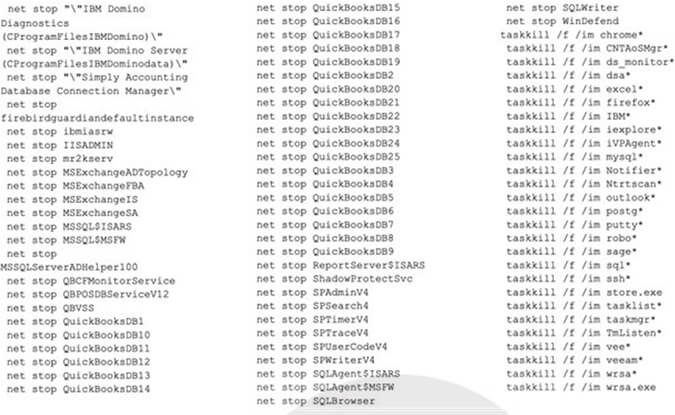
In ransomware payloads, there is an attempt to locate and forcefully terminate local virtual machines using the following command powershell “-command ” “\”Get-VM | Stop-VM -Force\”
This command is designed for interaction with Hyper-V Virtual Machines. If the ransomware identifies any locally hosted VMs, it proceeds to execute the “Stop-VM -Force” command, which results in the termination of the running VM(s), regardless of their current state or workload.
If the threat actor chooses not to use command-line arguments, the payload will straightforwardly attempt to encrypt the local device, encompassing all accessible volumes and files.
Screenshot of files Encrypted by Megazord (Source: Surface web)
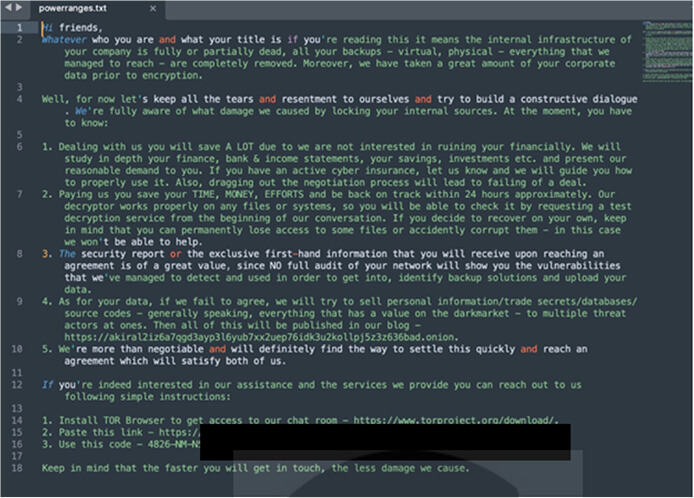
Screenshot of Ransom Note of Megazord (Source: Surface web)
Relevancy and Insights:
- This ransomware targets the Windows Operating system commonly used by many organizations of various industries.
- The use of idle periods may indicate that the ransomware is designed to operate more stealthily, waiting for the computer to be idle before encrypting files or performing other malicious activities.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. Ransomware that can detect debug environments may have implemented techniques to evade or disable debugging tools.
- Advanced VM Termination Capability: Megazord’s ability to forcefully terminate local virtual machines, especially those using Hyper-V, showcases an advanced technique for disrupting victim environments, emphasizing the malware’s sophistication and impact potential.
ETLM assessment
- Based on the information available, CYFIRMA’s assessment suggests that Megazord ransomware is likely to continue targeting Windows Operating Systems across diverse industries. Its capacity to detect and evade debugging environments, coupled with the capability to forcefully terminate virtual machines, points to an ongoing evolution aimed at amplifying its influence. Organizations worldwide, especially those reliant on Windows OS, should remain vigilant and enhance their cybersecurity defenses to effectively counter the evolving threat posed by Megazord ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No |
Tactics |
Techniques/Sub-Techniques |
| 1 |
TA0002: Execution |
T1059: Command and Scripting Interpreter |
| T1129: Shared Modules |
| 2 |
TA0005: Defense Evasion |
T1027: Obfuscated Files or Information |
| T1562.001: Impair Defenses: Disable or Modify Tools |
| 3 |
TA0007: Discovery |
T1082: System Information Discovery |
| T1083: File and Directory Discovery |
| 4 |
TA0011: Command and Control |
T1090: Proxy |
| 5 |
TA0040: Impact |
T1486: Data Encrypted for Impact |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Update all applications/software regularly with the latest versions and security patches alike.
Trending Malware of the Week
Type: Trojan
Objective: Steal Banking Credentials, Remote Access
Target Technology: Android OS
Target Industries: Financial Sector, Banks, and Government
Target Geographies: Asia pacific (Vietnam)
Active Malware of the Week
This week “GoldDigger” is trending.
GoldDigger
Researchers have discovered a new Android Trojan named GoldDigger, actively targeting financial organizations in Vietnam since June 2023. The malware disguises itself as a fake Android app, posing as both a Vietnamese government portal and a local energy company. GoldDigger’s primary objective is to steal banking credentials by exploiting Accessibility Service to extract personal information, intercept SMS messages, and execute user actions. Additionally, the Trojan possesses remote access capabilities, making it a significant threat to the security of financial organizations in the region.
GoldDigger employs an advanced protection mechanism, utilizing the legitimate software Virbox Protector consistently across all identified samples. This strategy adds complexity to both static and dynamic malware analysis, making it difficult to detect and initiate malicious activity within sandboxes or emulators.
Attack Method
GoldDigger spreads through fake websites that pose as Google Play pages and counterfeit corporate websites in Vietnam. The Trojan is likely distributed via smishing or traditional phishing methods, with the malicious links leading to downloads of harmful Android applications.
Fig: Fake website distributing GoldDigger
The default setting on all Android devices is to have “Install from Unknown Sources” disabled as a security measure, preventing installations from third-party sources. Enabling this setting allows the installation of APKs from sources other than the Google Play Store. GoldDigger requires the “Install from Unknown Sources” function to be enabled on a victim’s device in order to be downloaded and installed.
The GoldDigger Trojan, upon launch, prompts users to enable Accessibility Service on Android. While Accessibility Services are designed to assist users with disabilities, these services offer capabilities such as screen reading, magnification, gesture-based controls, speech-to-text, haptic feedback, and others. Regrettably, certain banking Trojans, such as Gustuff and Gigabud, are exploiting this feature.
Granting Accessibility Service permissions to GoldDigger gives it comprehensive access to user actions and the ability to interact with the user interface. This includes observing the victim’s balance, capturing the second credential from two-factor authentication, and implementing keylogging for credential theft. GoldDigger monitors 51 financial apps, e- wallets, and crypto apps in Vietnam, with exfiltrated data sent to command-and-control servers. The abuse of Accessibility Service provides intrusive capabilities, potentially allowing remote device access and creating a backdoor into the user’s system.
Researchers have observed a code snippet in GoldDigger’s gestures dispatcher, which is responsible for device screen unlock. Additionally, this code enables authentication bypass, including second-factor bypass, allowing GoldDigger to perform payment creation from a legitimate device.
INSIGHTS
- GoldDigger stands out as a significant cyber threat in the Asia Pacific region, emphasizing the constant evolution of cybersecurity challenges. The Trojan utilizes “Virbox Protector,” a legitimate software, making its detection and analysis notably challenging. With granted Accessibility Service permissions, GoldDigger gains complete visibility into user actions, enabling it to access sensitive information. This underscores the need for heightened cybersecurity measures to counter evolving threats like GoldDigger.
- GoldDigger actively monitors 51 financial apps, e-wallets, and crypto applications in Vietnam, extracting and sending the obtained data to command-and-control (C&C) servers. The primary goal of banking Trojans is to infect as many devices as possible and gain access to user accounts. Cybersecurity experts and researchers are always working together to catch these digital tricksters and keep your devices safe.
- As digital banking, e-wallets, and cryptocurrency platforms become integral to modern finance, offering convenience and global reach, they have also become a target for cybercriminals. The ease of access to these platforms has drawn the attention of threat actors who exploit vulnerabilities in this expanding digital domain. Threats like GoldDigger underscore the challenges and risks associated with the increasing digitization of financial services.
ETLM ASSESSMENT
- From the ETLM perspective, CYFIRMA observed that GoldDigger malware, initially focused on financial organizations in Vietnam. Its ability to continuously evolve, as evident in its recent language adaptation with translations in Spanish and traditional Chinese, signals a potential future expansion beyond its current focus on Vietnam. This indicates that GoldDigger might extend its reach to Spanish-speaking nations and other countries in the APAC region. As it adapts to new languages and potentially broadens its targets, organizations need to proactively enhance their cybersecurity measures to mitigate the evolving risks posed by GoldDigger, safeguarding against potential future threats to sensitive financial information and user accounts.
- The observed Tactics, Techniques, and Procedures (TTPs) of GoldDigger are:
| Reconnaissance |
- Gather Balance SMS InterceptionVia
- Malware
|
| Resource |
- Hosting Service
|
| Development |
- Malware
- Phishing Resource
|
| Trust Abuse |
- Branded Resource
- Enabling Accessibility Service for Malware
|
| End-User Interaction |
- Phishing
- Smishing
|
| Credential access |
- 2nd factor Capture
- Credentials Capture
- Keylogger
|
| Account Access |
- Access from Fraudster Device
- Device Remote Access
|
| Defence evasion |
- 2nd factor Bypass- Accessibility Service
- Authentication Bypass – Android Accessibility Service
- Payment from Legitimate Device
|
| Perform fraud |
- Payment to Mule Account
|
| Monetization |
- Cashout
|
| Laundering |
- Compromised Accounts
- Crypto currency exchanges
- crypto currency mixer
- E-wallets
- Fake facilitator
- illigal merchant
- Mule accounts
- Scam Hotel Reservation
- Virtual cards
|
Target Applications of GoldDigger:
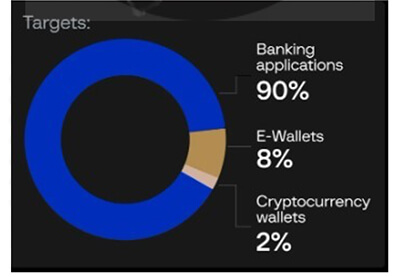
Fig: Target Applications of GoldDigger
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Implement Mobile Device Management (MDM) policy to enhance corporate data security by monitoring, managing, and securing mobile devices such as laptops, smartphones, and tablets that are used in enterprises.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATIONS
- Regularly reinforce awareness related to different cyberattacks using impersonated domains/spoofed webpages with end-users across the environment and emphasize the human weakness in mandatory information security training sessions.
- Provide your staff with basic cybersecurity hygiene training since many targeted attacks start with phishing or other social engineering techniques.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
- Enable network protection to prevent applications or users from accessing malicious domains and other malicious content on the internet.
- Enforce policies to validate third-party software before installation.
Weekly Intelligence Trends/Advisory
Weekly Attack Type and Trends
Key Intelligence Signals:
- Attack Type: Malware Implants, Spear Phishing, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gain, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware –LockBit 3.0 Ransomware | Malware – GoldDigger
- LockBit 3.0 Ransomware– One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Malware – BunnyLoader
- Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus

Cyber Attack in East Asia’s Semiconductor Sector Linked to Chinese State Sponsorship
- Threat Actors: Unknown
- Attack Type: Spear Phishing
- Objective: Espionage
- Target Technology: Windows
- Target Geographies: Eastern Asia
- Target Industries: Semiconductor
- Business Impact: Operational Disruption
Summary:
- In a recent observation, researchers have uncovered a cyber espionage campaign targeting the semiconductor industry in Mandarin/Chinese-speaking East Asian regions, including Taiwan, Hong Kong, and Singapore. The threat actors employed a variant of the HyperBro loader, using a lure related to Taiwan Semiconductor Manufacturing. Their employed TTPs show significant overlap with activities previously attributed to a cyber espionage group associated with the People’s Republic of China, however, researchers cannot confirm the specific APT behind the attack.
- The HyperBro loader variant takes advantage of a digitally signed CyberArk binary for DLL-Side loading, ultimately resulting in the execution of a Cobalt Strike beacon in the system’s memory. Further investigation revealed the presence of an undocumented malware downloader, which utilizes the BitsTransfer module in PowerShell to fetch malicious binaries from a likely compromised Cobra DocGuard server. It is interesting to note that the malware downloader employs a DLL Side-Loading technique by using a signed McAfee binary called mcods.exe to run the Cobalt Strike shellcode. Analysts also observed that the shellcode linked back to the same Cobalt Strike C2 server associated with the HyperBro loader variant.
- The compromised Cobra DocGuard web server was found to host a GO-based backdoor known as ChargeWeapon. It is highly likely that this backdoor was uploaded by the same threat actor. ChargeWeapon is specifically designed to provide remote access, enabling the attacker to gather device and network information from infected hosts and transmit it to a C2 server under their control. Probably the campaign was to fetch information from the threat actor as part of their initial reconnaissance efforts to pinpoint high-value targets among the infected hosts.
Relevancy & Insights:
- Historically, researchers have noted the presence of the HyperBro malware strain in cyberattacks dating back to 2018. APT27 threat actors have utilized this malware to attain complete control over their intended systems. The HyperBro malware family is frequently deployed through a method called DLL side-loading. However, in this latest campaign, analysts have not detected any notable connections with APT27 or any known Chinese APT.
ETLM Assessment:
- Semiconductors are like the brains of most of our gadgets, and the industry that makes them is super important. They help create the stuff we use every day, like phones and computers, and even things like big infrastructure projects. This industry keeps things moving and helps us come up with new ideas, grow our economy, and make progress. Chinese APTs have targeted this industry in the past too and tried to steal Intellectual Property (IP) from it before. It’s because getting inside information about semiconductors can be like a goldmine for state-sponsored APT groups. The semiconductor industry in Taiwan will persistently face threats, with frequent cyberattacks, primarily driven by Chinese APTs. These attacks are often motivated by geopolitical factors and the desire to extract valuable insider information.
Recommendations:
- Continuously monitor your network for signs of DLL side-loading activities, especially under the C:\ProgramData file path.
- Implement application whitelisting to restrict the execution of unsigned executables (EXE) on Windows endpoints. This can help prevent unauthorized software from running.
- Given the increasing use of PowerShell in cyberattacks, consider limiting its usage to regular Windows users. If needed, enable the PowerShell module and script logging via Windows Group Policy and use PowerShell Constrained Language Mode to reduce the attack surface.
- Engage with threat intelligence-sharing communities and organizations to stay updated on emerging threats and tactics. Collaborative efforts can help enhance your security posture.
- Use advanced endpoint protection solutions that can detect and respond to unusual or suspicious activities on your network.
Indicators of Compromise
- Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Major Geopolitical Developments in Cybersecurity
Potential Russia–DPRK cooperation in cyberspace
Russia’s immediate interest in cultivating its relationship with North Korea is the prospect of Pyongyang supplying Russia’s army with artillery ammunition, as expenditures have far exceeded Russian production capacity. There are, however, other potential areas of cooperation, notably in cyberspace. As a recent Cyfirma report notes, both North Korea and Russia are highly capable cyberwar and cyber intelligence nations, who can disrupt or break key infrastructure and steal sensitive government information. Their recently announced intensified security cooperation wouldn’t necessarily require much coordination as most of North Korea’s offensive cyber operations are already directed against countries whose relations with Russia are at least cool, if not downright adversarial.
ETLM Assessment:
- North Korean cyber operations have increased in sophistication over the past year, and our researchers note that Pyongyang’s threat actors seem particularly interested in stealing information related to maritime technology research, given the emphasis the Kim regime puts onto developing a full nuclear triad.
Palestinian hackers send fake rocket alerts as they are joined by foreign supporters
- A wave of hacking attacks on Israeli targets has added a cyber dimension to the conflict with Hamas that began with the Palestinian organization breaking out of the Gaza strip and launching a surprise attack on Israeli civilians and military personnel on October 7, slaughtering hundreds in ISIS-style executions and abducting many more to the Gaza strip, where they are now held hostage.
- The most significant measures by the Palestinians may prove to be preparation early in the year, when a Gaza Strip group known as Storm-1133 went after energy, defense and telecommunications companies inside Israel. According to a recent report, the group used fake LinkedIn profiles and posed as software developers or project managers to send malware to employees at those targets and install back doors for later use. Other hacks, mainly by self-proclaimed hacktivist allies of the Palestinians, were aimed at sowing confusion or alarm. Various groups launched dozens of denial- of-service attacks at government and private websites, knocking them offline but causing no lasting damage.
- One of the most effective was against the website of the Jerusalem Post, a major source of reporting on the fast-changing conflict. This particular denial-of-service was claimed by Anonymous Sudan.
- Pro-Palestinian hackers: AnonGhost, said it was behind an attack on an Israeli app that warns residents of incoming rocket strikes, with the group claiming it sent fake rocket alerts to Israeli civilians to help sow chaos in the country.
ETLM Assessment:
- Israel will seek to eliminate the threat posed by the Palestinian militant group for good, but that will require extensive bombing followed by boots-on-the-ground fighting in the Palestinian territory itself. This will cause very high collateral damage and civilian casualties in the Gaza strip, which could draw in other adversaries, including Hezbollah, al-Qaeda or even Iran. The cyberspace part of the conflict is likely just in its beginning and we are likely to see a spike in the activity of Iranian APTs attacking countries that support Israel. Russia might throw its weight behind some of the activity as well as intensification of the conflict suits its interest, driving attention from its war in Ukraine and consuming resources, that could otherwise help its western neighbor.
Increased sophistication of North Korean cyber espionage
- North Korea has recently been active against blockchain and decentralized finance (“DeFi”) targets, with Mixin Network (a facilitator of blockchains transactions) alone disclosing losses amounting almost to $150 million in a recent attack, attributed to DPRK by US deputy national security adviser for cyber and emerging technology Anne Neuberger.
- Another group of researchers published an assessment of the current organization and conduct of North Korean offensive cyber operations, where there has been an observation of an evolution in both complexity and sophistication, as Pyongyang continues to run both espionage and financial crime campaigns with the goals of financing its weapons programmes and other black government expenditure and advancing its backward and heavily sanctioned technological sector. North Korean groups are also increasingly cooperating among themselves, sharing tools and targets and collaborating on developing their targets. Some of the groups seem to be isolated from the central authority and are self-funding through financial crime, even as they remain aligned with North Korean goals. The attack techniques are more adaptable than they’ve been in the past and many more capable groups beyond just the infamous “Lazarus” are appearing on the scene.
ETLM Assessment:
- Pyongyang is working to develop a robust nuclear triad: land-launched stationary and mobile missiles, submarine-launched missiles, and aircraft-launched missiles, although all vectors remain underdeveloped because of lack of resources available to the North Korean regime. Since development is very difficult without external expertise and the country is under sanctions with little access to external help, the regime is increasingly turning to cyber espionage in order to gain access to dual use and military technologies, especially in maritime and aerospace domain. This activity on the part of North Korean hackers has been on the rise and similar incidents are to be expected in the future.
Rise in Malware/Ransomware and Phishing
Tata Tele Business Services (TTBS) is Impacted by LockBit 3.0 Ransomware
- Attack Type: Ransomware
- Target Industry: Telecommunication
- Target Geography: India
- Ransomware: LockBit 3.0 Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from India, (www[.]tatatelebusiness[.]com), was compromised by LockBit 3.0 Ransomware. Tata Tele Business Services (TTBS), part of the prestigious Tata group of companies, is the country’s leading provider of business connectivity and communication solutions. The data that has been compromised remains unreleased on the leak site, suggesting the possibility of ongoing negotiations between the victim and the ransomware group. It is conceivable that the compromised data includes sensitive and confidential information.
The following screenshot was observed published on the dark web:
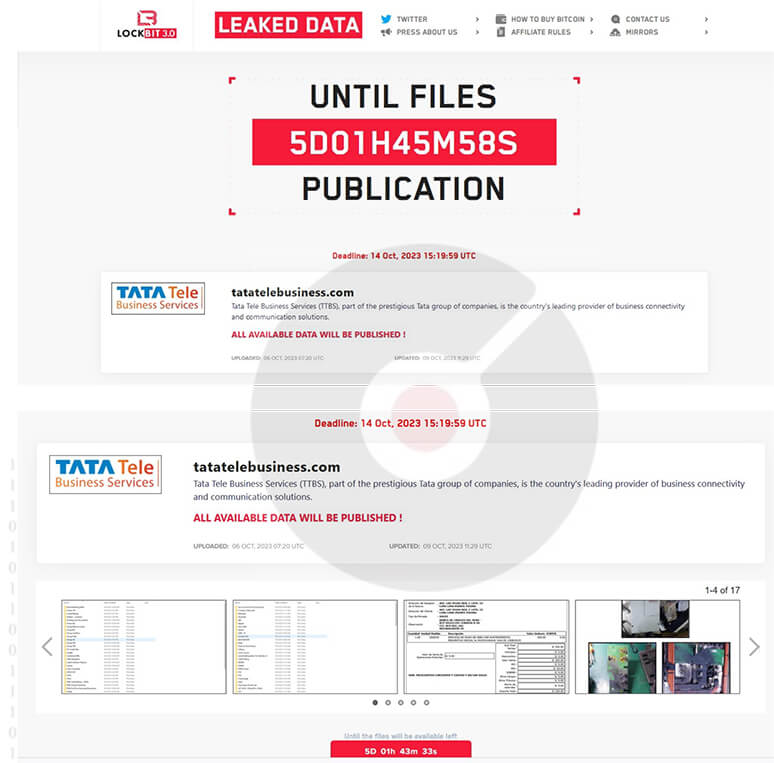
Source: Dark Web
Relevancy & Insights:
During 2023, the LockBit 3.0 ransomware has evolved into a worldwide menace, penetrating numerous public and private organizations across the globe. Notably, the United States has borne the brunt of this threat, with around 30% of the nation’s institutions being targeted and subsequently victimized by this ransomware.
Based on the LockBit 3.0 ransomware victims list in 2023, the top 5 Target countries are as follows:
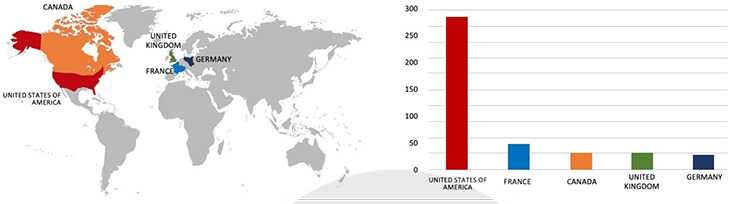
Ranking the Top 10 Industries, most affected by LockBit 3.0 ransomware
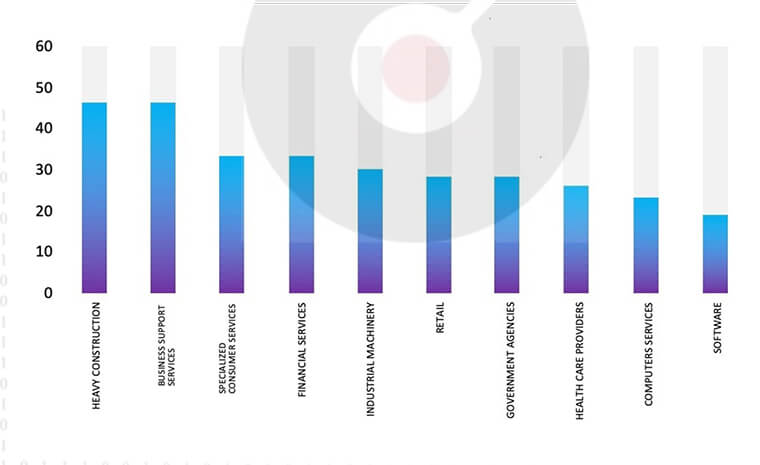
ETLM Assessment:
CYFIRMA’s evaluation remains consistent: our expectation is that LockBit 3.0 Ransomware will persist in its concentration on American businesses and their subsidiaries that store substantial volumes of Personally Identifiable Information (PII). Nevertheless, recent incidents, such as the attack on Tata Tele Business Services (TTBS), underscore the vulnerability of even renowned telecommunication companies to potential targeting.
Vulnerabilities and Exploits
Vulnerability in Atlassian Confluence Data Center and Server
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Server Applications
- Vulnerability: CVE-2023-22515 (CVSS Base Score 9.8 )
- Vulnerability Type: Improper Authentication
Summary:
Atlassian Confluence Data Center and Server could allow a remote attacker to gain elevated privileges on the system, caused by an error related to the /setup/* endpoints on Confluence instances.
Relevancy & Insights:
An attacker could exploit this vulnerability to create administrator accounts that can be used to access Confluence instances.
Impact:
A remote non-authenticated attacker can send specially crafted requests to the server to create an administrative account and gain unauthorized access to the system.
Affected Products:
https://confluence[.]atlassian[.]com/kb/faq-for-cve-2023-22515- 1295682188.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
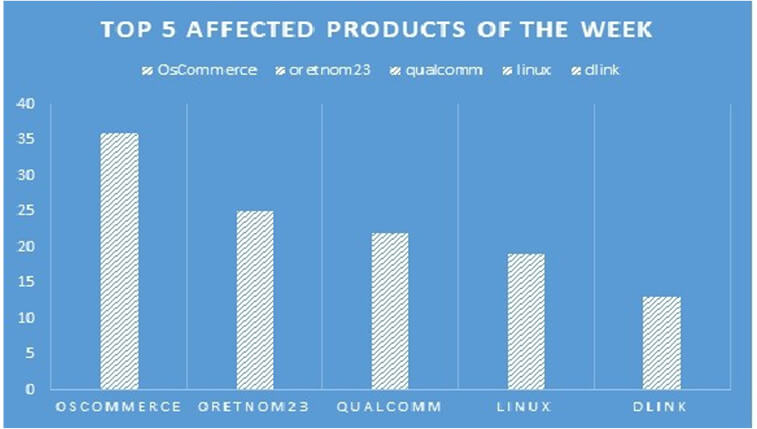
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Latest Cyber-Attacks, Incidents, and Breaches
Spain experienced DDoS attacks during the EU summit.
- Threat Actors: NoName057(16)
- Attack Type: DDoS
- Objective: Operational Disruption
- Target Technology: Web Application
- Target Geographies: Spain
- Business Impact: Operational Disruption
Summary:
During the ongoing European Union summit, Spain encountered a surge of distributed denial-of-service attacks affecting many private and public websites. These attacks were attributed to the pro-Russian hacktivist group NoName. Among the impacted websites were those associated with the city of Granada, where the summit was taking place. This included the city’s metro, bus service, and tourism portal. NoName, the hacktivist group behind the attacks, mentioned the talks between Spanish Acting Prime Minister Pedro Sanchez and Ukrainian President Volodymyr Zelenskiy in their Telegram post. These discussions involved an offer of six HAWK air defense systems to Ukraine. “It seems that the Spanish segment of the Internet has been waiting for our visit, so we are in a hurry to attack it with long-range DDoS missiles!” said NoName. All of the services affected by the DDoS attacks have already been restored, said the Spanish government, which noted that stronger security measures have also been implemented following the intrusions.
Relevancy & Insights:
Spain experienced a significant wave of distributed denial-of-service (DDoS) attacks during an ongoing European Union summit. Notable targets of the attacks included both private and public websites, particularly those associated with the city of Granada, where the summit was taking place. This encompassed the city’s metro, bus service, and tourism portal.
ETLM Assessment:
According to CYFIRMA’s analysis, there is a growing concern that Spain faces an ongoing threat of DDoS attacks, with the potential for these attacks to become more severe. This heightened level of attacks could lead to substantial disruptions in operations, causing significant harm to Spain’s reputation. The combination of Spain’s ongoing support for Ukraine and the media attention on these DDoS attacks may embolden threat actors to persist in their assault.
Data Leaks
Wobi INSURANCE AGENCY Data Advertised in Leak Site
- Attack Type: Data Leaks
- Target Industry: Business Services
- Target Geography: Israel
- Target Technology: SQL Database
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to Wobi INSURANCE AGENCY, {www[.]wobi[.]co[.]il}. Wobi is the leading online insurance price comparison engine & online broker in Israel. It allows users to compare and purchase auto, travel, home, and mortgage insurance policies offered by leading major insurance companies in Israel. The compromised dataset includes information such as Names, Emails, Hashes, Addresses, Gender, Phone Numbers, Date of Birth, and other sensitive data formatted in SQL. The total size of the compromised dataset is 8.88 gigabytes.

Source: Underground forums
Relevancy & Insights:
Cybercriminals motivated by financial gains are continually on the lookout for unprotected and poorly defended systems and software applications. The majority of these malicious individuals are active in covert online communities, engaging in discussions related to cybercrime and trading stolen digital assets. Unlike other financially motivated groups, such as ransomware or extortion gangs, who often publicize their attacks, these cybercriminals prefer to maintain a low profile. They gain unauthorized access and abscond with valuable information by exploiting unpatched systems or vulnerabilities in software and hardware. Subsequently, they market the pilfered data on underground forums, where it is either resold or repurposed by other malevolent actors for their own illicit purposes.
ETLM Assessment:
Israel consistently maintains its position as one of the primary targets for cybercriminals on a global scale. CYFIRMA’s analysis suggests that Israel’s organizations with inadequate security measures and infrastructure remain exposed to an elevated risk of potential cyberattacks.
Other Observations
CYFIRMA Research team observed a potential data leak related to the Boston College, {www[.]bc[.]edu}. Boston College (BC) is a private Jesuit research university in the USA. It still uses the word college in its name to reflect its historical position as a small liberal arts. The university offers bachelor’s degrees, master’s degrees, and doctoral degrees through its eight colleges and schools. The compromised data includes students’ and staff members’ phone numbers, physical addresses, email addresses, departments, majors, first names, last names, middle names, and other sensitive personal information.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and, are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.















