


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
The CYFIRMA Research and Advisory Team has found SafeLocker Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
SafeLocker Ransomware
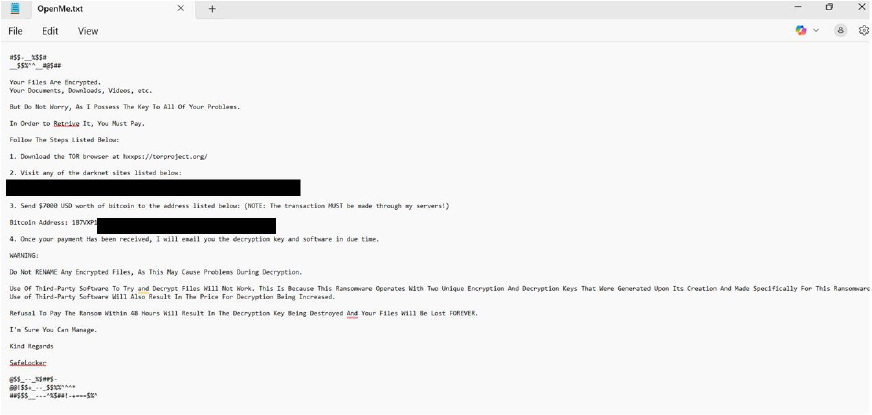
SafeLocker is a newly identified ransomware strain that, once executed, encrypts a victim’s files and appends the extension “.8xUsq62” to each one. Alongside the encryption, it drops a ransom note named “OpenMe.txt”.

The ransom note notifies the victim that their files—including documents, videos, and downloads—have been encrypted. It promises that the decryption key will be provided in return for payment. Victims are instructed to download the TOR browser, navigate to a specified darknet site, and pay $7,000 USD in Bitcoin to the listed wallet address to retrieve the decryption key.
The note also includes several warnings. It advises against renaming any encrypted files, stating this could disrupt the decryption process. It further claims that using third- party recovery tools will be ineffective. Finally, it threatens that if payment is not made within 48 hours, the decryption key will be destroyed, resulting in permanent loss of the encrypted files.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot:Bootkit |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hide Artifacts:Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1012 | Query Registry |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment with available data suggests that this ransomware will be a threat to multiple industries, particularly those reliant on the Windows ecosystem. SafeLocker’s ransom demand of $7,000 in Bitcoin indicates a clear targeting of enterprises that are financially capable of paying. Its use of stealth techniques— such as extended sleep intervals, anti-debugging checks, and registry-based persistence—demonstrates a strategic effort to bypass security controls and ensure successful encryption. Given its impact tactics, including data encryption and system recovery inhibition, SafeLocker is likely to evolve with increased sophistication. Organizations should anticipate continued targeting across sectors such as finance, healthcare, and manufacturing.
Sigma rule:
title: Delete shadow copy via WMIC id: 200076
threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer| Objectives: Data Theft, Data Exfiltration | Target Technologies: Windows OS, Browsers| Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Myth Stealer” is trending.
Myth Stealer
Researchers recently uncovered a new piece of rust-based infostealer called Myth Stealer, which had previously managed to fly under the radar. Initially released for free as a trial on Telegram in late December 2024, the malware later adopted a subscription- based model. It spreads mainly through fraudulent gaming websites, where unsuspecting users might download it thinking it’s something harmless. Once installed, the malware cleverly disguises itself by displaying a fake window to make it appear legitimate. Behind the scenes, however, it secretly runs code that steals sensitive information from web browsers, such as passwords, cookies, and autofill details. It even tries to avoid detection by using tricks like hiding its true purpose and checking the system for signs of analysis.
Furthermore, the creators of Myth Stealer regularly update the malware to stay ahead of security measures. Recent updates have added features such as screen capture capabilities and clipboard hijacking, increasing the threat it poses to users.
Myth Stealer: The Telegram Connection
In late December 2024, researchers noticed promotional posts in active Telegram groups aimed at attracting buyers for Myth Stealer. These posts appeared in dedicated Telegram channels, which were used to share updates and news about the malware.
Activity in the channel suggested that an organized team was behind its development and upkeep. Although Telegram shut down the original channel, the operators quickly set up a new group to continue promoting the malware. They frequently announce new versions in this group, often highlighting how the malware remains undetected by antivirus programs. Users are required to rebuild their malware packages regularly to incorporate the latest updates. The malware is sold through weekly and monthly subscriptions, with payments accepted in cryptocurrency and Razer Gold. The operators also ran a separate Telegram channel, called ‘Myth Vouches & Marketplace,’ where users shared testimonials and advertised stolen accounts. Telegram has since taken this channel down as well.
Attack Method
The malware is distributed by posing as game-related software on fraudulent gaming websites. The files from such websites are served in one of the following forms:
This tactic helps attackers trick users into installing the malware, believing it’s a genuine game software or related tools.
In another instance, an online forum post linked to a malicious RAR file disguised as a cheat tool. To build trust within the forum community, the poster shared telemetry data indicating the file was clean at the time, tricking users into believing it was safe to download.
Capabilities of Myth Stealer
The malware has undergone significant evolution over time. Initially, it was distributed for free and focused mainly on stealing data from applications. When it moved to a paid subscription model, additional features were added, including fake windows, screenshots, and clipboard hijacking. The team behind the malware regularly updates and refines it to remain undetected by security measures. These updates often involve changing the libraries used for fake windows and updating how it communicates with its command server. Currently, the malware is a 64-bit program written in Rust that uses a loader to decrypt and run its data-stealing components.
Loader with a fake window
After the malware is downloaded and run on a victim’s machine, it displays a fake window to make it look like a real application is being used. Meanwhile, the malware decrypts its core component — a data-stealing module — using different encryption methods. In newer versions, a custom algorithm handles this decryption. Once decrypted, the stealer module is a 64-bit file that runs directly in the system’s memory, making it harder to detect. This component includes functions that allow it to integrate seamlessly with the system and carry out its data-stealing activities.
Anti-analysis techniques
The malware employs anti-analysis techniques to make it harder for security researchers to understand its code. One way it does this is by hiding its text strings using an obfuscation method. Instead of showing readable text, the malware converts strings into hexadecimal values and uses complicated mathematical operations to hide their true meaning.
Sandbox evasion via username and filenames checks
Before stealing any data, the malware checks the computer on to see if it might be in a test environment. It does this by looking for certain usernames and files that typically belong to security researchers. If it finds any, the malware immediately stops running to avoid getting caught.
Process Termination
To avoid detection and make its data theft more effective, the malware forcibly stops popular web browsers and related processes if they are running. This includes common browsers like Chrome, Firefox, Edge, and others, as well as processes related to crash reporting. By shutting down these programs, the malware can operate without interference.
Stealing data from applications
The malware steals sensitive information from applications like Discord and Chrome, including stored passwords, cookies, autofill data, and saved credit card details. This data can be used by attackers to gain access to victims’ accounts or commit fraud.
Cookies extraction from Chromium-based browsers
The malware uses a technique called remote debugging to extract cookies from Chromium-based browsers. It does this by launching the browser in a special mode that lets it access stored cookies. For Microsoft Edge, an extra setting is added to bypass compatibility checks. In its newer versions, the malware tries to get administrative access on the victim’s computer using a Windows feature. Once it has these higher permissions, it can steal cookies more effectively using similar methods.
Clipboard hijacking
The malware monitors the clipboard for any cryptocurrency transaction details. When a victim tries to send funds, the malware swaps the intended wallet address with the
attacker’s own, effectively hijacking the transaction.
Exfiltrating data from the system
Once the malware collects the stolen information, it sends it to a remote server controlled by the attacker. In older versions, the server’s address was different, but it now uses a specific IP and port. The malware adds a special key to each request so the server can identify incoming data. The stolen data, which includes things like tokens and cookies, is bundled into a zip file before being sent. Sometimes it’s encoded or reversed to make detection harder. The malware also creates a summary file listing the stolen details, though newer versions have stopped sending this file. In some cases, instead of sending the data to its main server, the malware directly uploads it to a Discord webhook, giving the attacker quick access.
Taking screenshots
The malware starts by contacting a website to find the victim’s IP address, helping attackers identify the target. It then quickly takes a screenshot of the infected computer and sends it to a remote server, giving the attacker a snapshot of the victim’s screen.
Persistence mechanism
The malware makes sure it stays on the victim’s computer by saving a copy of itself in the system’s roaming folder and adding a shortcut to the startup menu. This way, every time the computer restarts, the malware automatically runs again.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as Myth Stealer evolves, its social engineering tactics are likely to become even more sophisticated, making it harder for users to distinguish between legitimate downloads and malicious ones. This means users could inadvertently install the malware on work devices, exposing not only their own credentials but also potentially giving attackers a foothold into broader organizational networks. With its ability to harvest credentials, cookies, and other sensitive information, organizations may face increased risks of data breaches and identity theft in the future. As the developers refine Myth Stealer’s capabilities, its potential to bypass security controls could further undermine corporate data protection efforts, making it harder to secure customer and employee information. As more threat actors adopt this malware-as-a-service model, organizations may see a surge in cyberattacks that are not just opportunistic but also well-coordinated, stretching security teams thin and forcing a rethink on how to detect and respond to advanced threats in an increasingly complex cyber landscape.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Social Engineering’s Silent Weapon: The High Cost of Voice Phishing
Summary:
Researchers uncovered a financially motivated threat actor, UNC6040, specializing in voice phishing (vishing) campaigns targeting Salesforce instances for large-scale data theft and extortion. The group compromises organizations by impersonating IT support personnel in convincing phone-based social engineering attacks, primarily targeting English-speaking employees at multinational corporations. UNC6040 manipulates victims into granting access rather than exploiting Salesforce vulnerabilities.
A key tactic involves deceiving users into authorizing a malicious connected app (often a modified version of Salesforce Data Loader) within their Salesforce portal. During vishing calls, victims are guided to approve a spoofed Data Loader app, granting UNC6040 extensive access to query and exfiltrate sensitive data. In some cases, extortion occurs months later, suggesting collaboration with a second-threatening actor. UNC6040 has falsely claimed affiliation with ShinyHunters to pressure victims.
After initial access, UNC6040 exfiltrates Salesforce data using Data Loader, then moves laterally via harvested credentials to other cloud services like Okta and Microsoft 365. The group uses phishing panels hosted on shared infrastructure to steal credentials and MFA codes. Attackers primarily connect via Mullvad VPN IPs to evade detection.
Modified Data Loader variants were observed, with exfiltration techniques varying some used small data chunks initially before scaling up, while others disguised the tool as “My Ticket Portal” to align with the vishing pretext.
This campaign highlights the growing trend of vishing-based initial access targeting IT support roles, emphasizing the continued effectiveness of social engineering in enterprise breaches. Extortion may follow months after compromise, indicating potential future attacks on additional victims.
Relevancy & Insights:
The threat actor UNC6040 has demonstrated significant evolution in its attack capabilities, transitioning from traditional credential phishing to sophisticated, cloud- focused social engineering campaigns. In previous operations, the group relied on basic phishing kits targeting Microsoft 365 and Okta credentials, showing limited technical sophistication beyond conventional credential harvesting. Their current Salesforce-focused campaigns reveal advanced capabilities in social engineering, OAuth abuse, and cloud application exploitation. By weaponizing Salesforce Data Loader through malicious connected apps, they now execute precise data exfiltration while evading detection via commercial VPN services. This progression from broad credential theft to targeted SaaS platform exploitation reflects both increased technical proficiency and strategic adaptation to high-value corporate data. The maintained focus on IT support impersonation connects their past and present operations, though the current attacks demonstrate a deeper understanding of cloud architectures and business processes. Notably, the shift from immediate credential monetization to delayed extortion suggests collaboration with more sophisticated financial actors. These developments mirror the broader threat landscape’s pivot toward cloud application attacks, making UNC6040’s evolution particularly relevant for organizations transitioning to SaaS environments. Their trajectory underscores how threat actors are refining social engineering tactics to exploit cloud migration trends.
ETLM Assessment:
UNC6040 is a financially motivated threat actor specializing in voice phishing (vishing) attacks targeting multinational corporations, primarily focusing on English- speaking employees across global enterprises. The group predominantly attacks organizations using Salesforce, with secondary targeting of Okta and Microsoft 365 integrations. Their operations exploit human vulnerabilities through IT support impersonation rather than technical flaws in Salesforce itself. Currently, UNC6040 employs weaponized versions of Salesforce Data Loader and OAuth-connected apps, while historically using credential-harvesting phishing panels. Their motivation centers on data theft for extortion, sometimes claiming affiliation with ShinyHunters to intimidate victims.
Future assessments indicate UNC6040 may expand to other SaaS platforms like ServiceNow or Workday, refine their social engineering tactics, and develop more sophisticated data exfiltration methods. The group is likely to continue leveraging VPN services like Mullvad for anonymity and may incorporate ransomware in later attack stages.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAME WORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.004 | Phishing: Spear phishing Voice |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1556.006 | Modify Authentication Process: Multi-Factor Authentication |
| Privilege Escalation | T1098 | Account Manipulation |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1578 | Modify Cloud Compute Infrastructure Injection |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1020 | Automated Exfiltration |
| Exfiltration | T1030 | Data Transfer Size Limits |
| Exfiltration | T1020 | Automated Exfiltration |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1657 | Financial Theft |
Ukrainian spies claim to have hacked a Russian defense contractor
Ukraine’s military hackers under the Main Intelligence Directorate (HUR) claim to have hacked Russia’s state-owned aerospace and defense contractor Tupolev, which manufactures Russia’s strategic bombers. The hackers allegedly stole 4.4 gigabytes of classified data, which included personal information of Tupolev staff, internal communications—such as messages between company executives—procurement records, resumes of engineers and designers, and minutes from confidential meetings.
HUR officials have been quoted in the media saying: “The value of the data obtained is hard to overstate. There is now virtually nothing secret left in Tupolev’s operations as far as Ukrainian intelligence is concerned. We now have comprehensive information on individuals directly involved in maintaining Russia’s strategic aviation.” Tupolev hasn’t commented on the claims, but the company’s website was defaced to show an image associated with HUR’s cyber operations.
ETLM Assessment:
The news of the hack came just days after Operation Spider’s Web, in which Ukraine demonstrated tactical ingenuity and highlighted transformative shifts in warfare when it was able to use off-the-shelf technology to attack Russia’s strategic air force. As CYFIRMA analysts note in a recent article on the topic, the proliferation of affordable, adaptable technologies—FPV drones, open-source software, and AI—is accelerating. Originally designed for civilian use, these tools are now weaponized with devastating effects. Their accessibility to state and non-state actors requires urgent efforts to anticipate, regulate, and counter their use in conflicts and domestic settings.
Secondly, autonomy is advancing rapidly. Current drones rely on semi-autonomous functions for navigation and targeting, but future systems will likely integrate these into fully autonomous platforms capable of independent missions over vast distances. This evolution will challenge existing doctrines, ethical frameworks, and oversight mechanisms, necessitating proactive adaptation.
Thirdly, the growing drone threat exposes vulnerabilities in military and civilian infrastructure. Conventional air defenses are often inadequate against small, precise drones. Militaries must invest in early detection, electronic warfare, and layered physical defenses to protect critical assets.
These trends highlight that technological agility, not just industrial scale, will define future strategic advantage: militaries that invest in resilience, countermeasures, and adaptive doctrines will be best equipped to navigate this evolving battlefield in response to Operation Spider’s Web’s wake- up call. The cyber warfare component of this operation then supplements future threats to Russian strategic aviation but should also lead global powers to rethink defense in an era where cheap, innovative systems can upend traditional military dominance.
Iranian hackers target Iraqi and Kurdish officials
Researchers have recently published about a cyberespionage campaign attributed to the Iranian threat actor known as “BladedFeline.” The operation targets Kurdish and Iraqi officials using multiple strains of custom malware. According to the report, the researchers uncovered two reverse tunnels, various auxiliary tools, and notably two backdoors: one dubbed “Whisper” and the other “PrimeCache,” a malicious IIS module. Whisper functions by accessing a compromised webmail account on a Microsoft Exchange server and communicates with the attackers through email attachments.
PrimeCache also acts as a backdoor.
The report highlights that PrimeCache bears similarities to the RDAT backdoor previously linked to OilRig, a threat group affiliated with Iran’s Ministry of Intelligence and Security. The researchers assess that BladedFeline is likely a subgroup of OilRig.
ETLM Assessment:
We can safely anticipate continued targeting of organizations in Iraq and the Kurdistan Regional Government (KRG) as the relations between the federal and local government sours and the regional geopolitical tensions keep rising. The KRG’s diplomatic ties with Western nations and Israel and its significant oil reserves make it an attractive target for Iran-aligned threat actors seeking to conduct espionage or influence regional affairs.
Many similar campaigns are likely underway in all other regional oil-producing nations, the host of them run by Iran, which is currently facing a fork in the road in its talks with the Trump administration regarding the future of its nuclear programme.
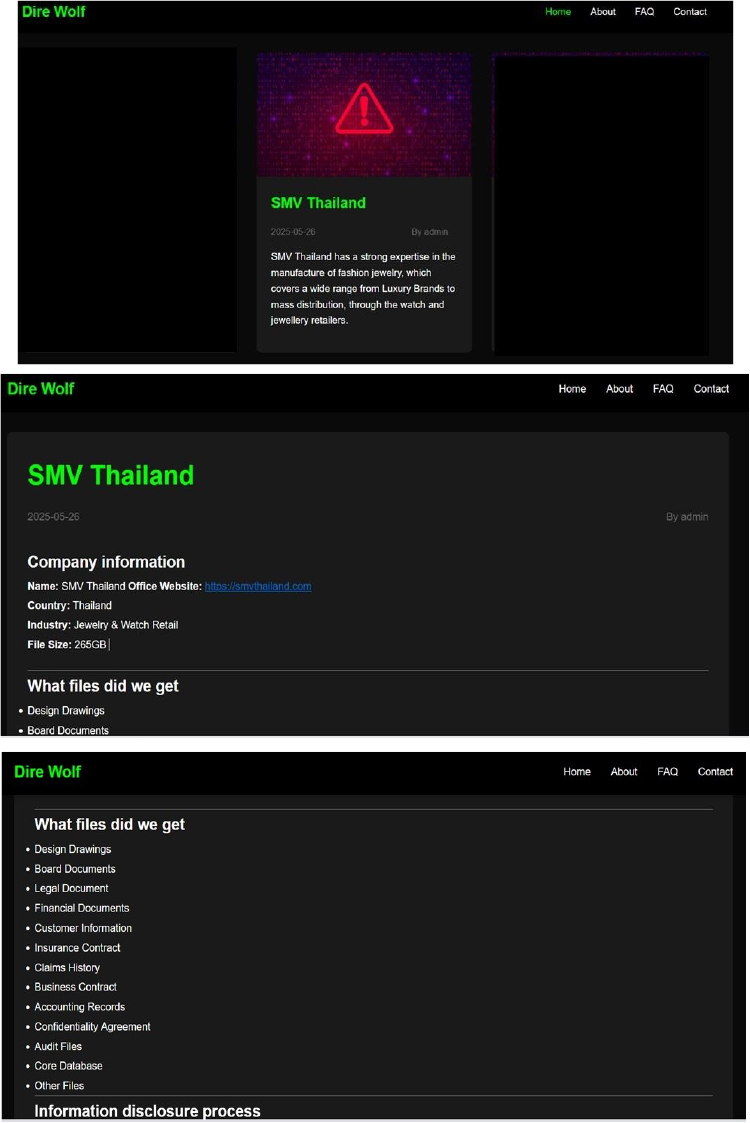
The Dire Wolf Ransomware Impacts SMV Thailand
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, SMV Thailand (https[:]//smvthailand[.]com/), was compromised by Dire Wolf Ransomware. SMV Thailand is a highly experienced manufacturer and supplier of high-quality costume and fashion jewelry, specializing in the lost wax casting technique. The company operates as a subsidiary of Renaissance Luxury Group, a leading French supplier of fashion jewelry. The compromised data includes design drawings, board documents, legal and financial records, customer information, insurance contracts, claims history, business agreements, accounting records, confidentiality agreements, audit files, the core database, and various other sensitive files. The total size of the compromised data is approximately 265 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics—combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gain, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
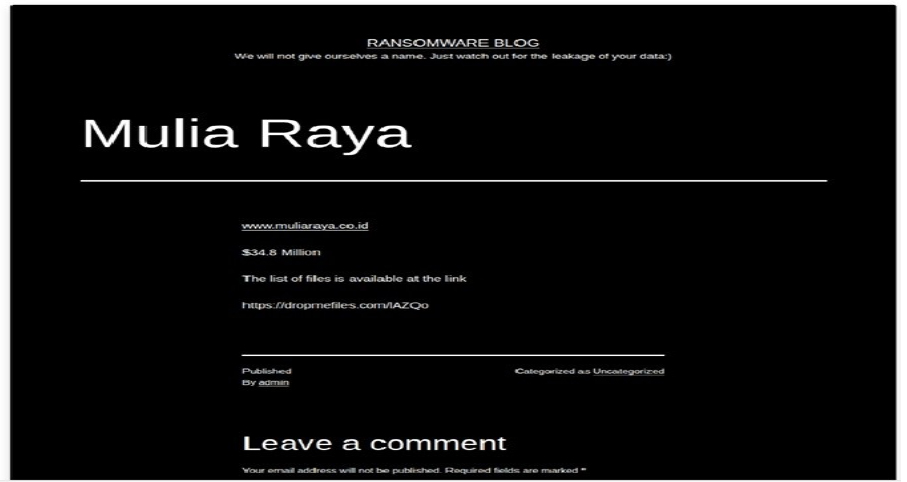
The MedusaLocker Ransomware Impacts Mulia Raya
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; Mulia Raya (https[:]//www[.]muliaraya[.]co[.]id/), was compromised by MedusaLocker Ransomware. Mulia Raya is one of Indonesia’s major importers, distributors, and producers of fresh fruits, vegetables, meat, and dairy products. The compromised data consists of confidential and sensitive information related to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, MedusaLocker ransomware represents a highly organized and financially motivated threat actor leveraging a combination of sophisticated technical methods, social engineering, and public shaming tactics to maximize extortion outcomes. Its affiliate-based RaaS model, combined with aggressive double extortion and a public-facing communication strategy, makes it a significant cybersecurity risk in 2025. Organizations are advised to adopt robust patch management, multi-factor authentication, network segmentation, and employee training to mitigate the risk posed by MedusaLocker attacks.
Vulnerability in Autodesk Installer
Relevancy & Insights: The vulnerability exists due to the usage of an untrusted search path.
Impact:
A local user can place a malicious binary into a specific location on the system and execute arbitrary code with escalated privileges.
Affected Products:
https[:]//www[.]autodesk[.]com/trust/security-advisories/adsk- sa-2025-0010
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
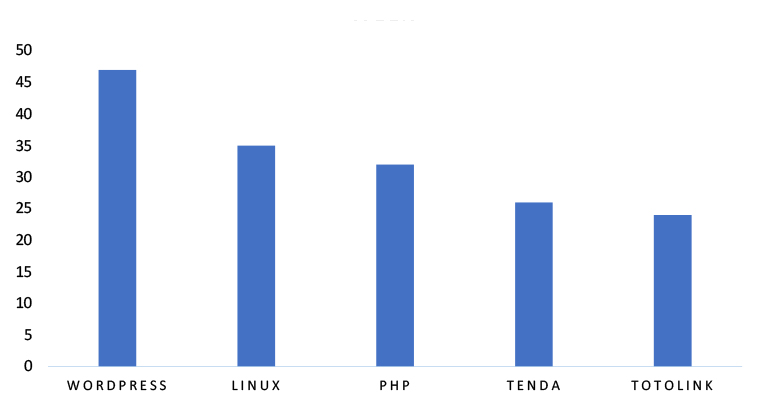
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in the Autodesk Installer can pose significant threats to user privacy and security. This can impact various industries globally, including architecture, engineering, manufacturing, and construction. Ensuring the security of the Autodesk Installer is crucial for maintaining the integrity and protection of users’ systems and data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding software installation processes, preventing unauthorized code execution or system compromise, and ensuring secure deployment of Autodesk products across different geographic regions and sectors.
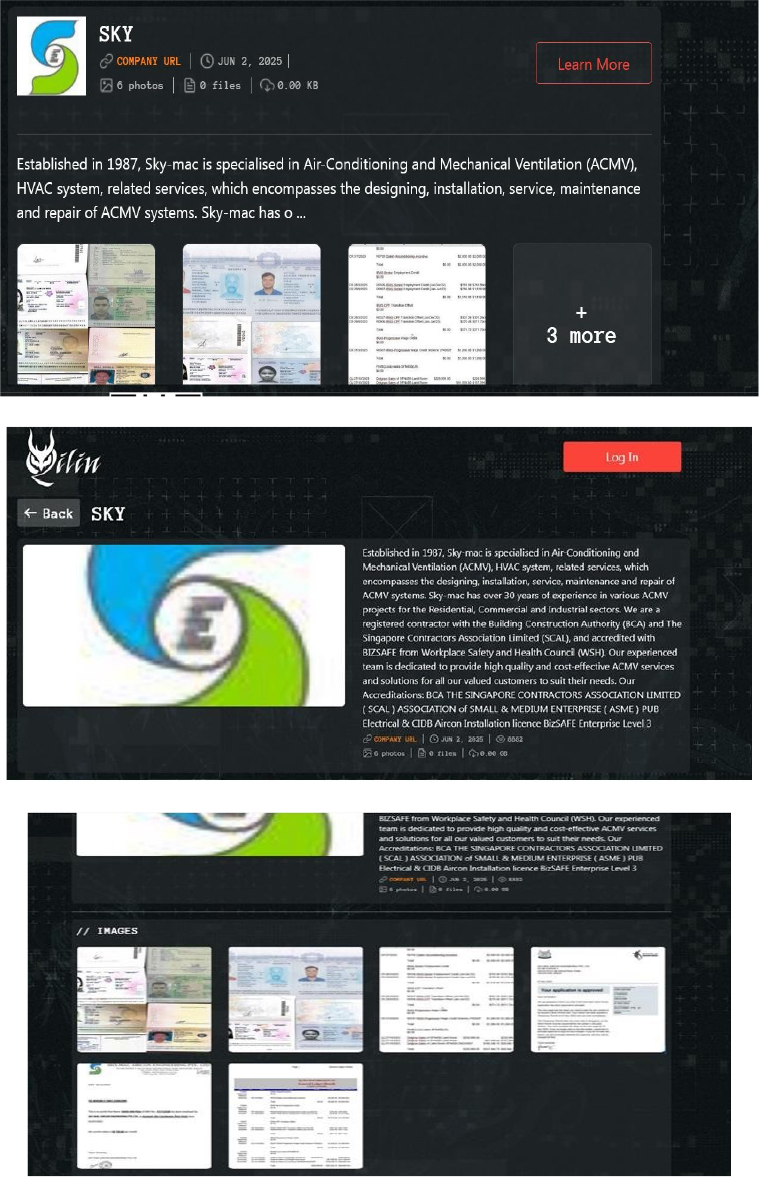
Qilin Ransomware attacked and published the data of the Sky-Mac Aircon Engineering Pte Ltd
Summary:
Recently, we observed that Qilin Ransomware attacked and published the data of the Sky-Mac Aircon Engineering Pte Ltd(https[:]//skymac[.]sg/) on its dark web website. Sky-Mac Aircon Engineering Pte Ltd, accessible via skymac.sg, is a Singapore-based company specializing in Air-Conditioning and Mechanical Ventilation (ACMV) and HVAC systems. Established in 1987, it offers services including the design, installation, maintenance, and repair of ACMV systems across residential, commercial, and industrial sectors. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
PT Wadma Berkah Sedaya Data Advertised on a Leak Site
Summary: The CYFIRMA Research team observed a data leak related to the PT Wadma Berkah Sedaya(https[:]//wadmanet[.]co[.]id/) in an underground forum. PT Wadma Berkah Sedaya, also known as Wadma Network or WadmaNet, is an Indonesian company operating primarily in the telecommunications and data connectivity sector. The company provides various services including data service connectivity solutions, reliable voice communication, devices, and management services tailored for businesses in Indonesia. The company’s role as a telecommunications provider makes this alleged breach particularly sensitive, as it could potentially expose customer and internal company data.
The origin of the breach appears to be a threat actor who posted the data on a hacking forum. The leaked data, as displayed in the forum post, allegedly contains sensitive financial and administrative information. The actor shared a sample of the data, which includes a table labeled “m_bank,” suggesting the exposure of banking details. This incident raises concerns about the security posture of the ISP and the potential for misuse of the stolen information. The breach and resulting data exposure have been attributed to a threat actor operating under the alias “LyxSec.”
The allegedly leaked data includes the following types of information:

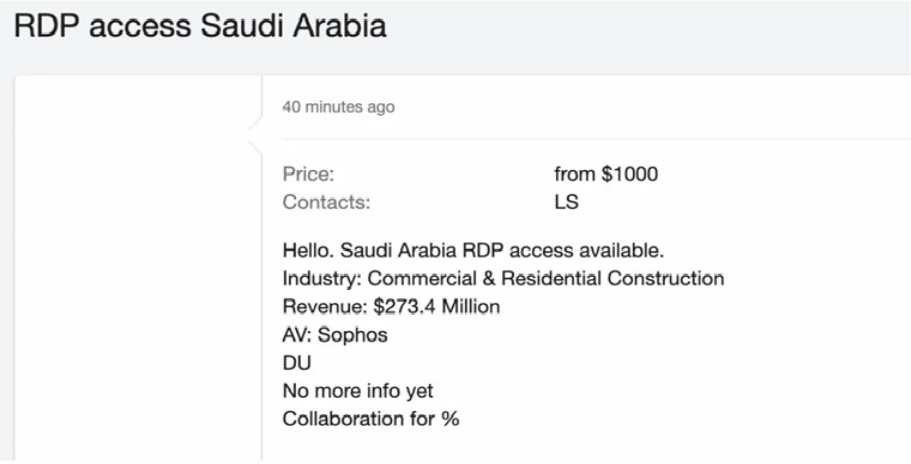
A Saudi Construction Firm’s Access Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor is allegedly selling Remote Desktop Protocol (RDP) access to a construction company based in Saudi Arabia. In a post on a specialized forum, the seller-provided details about the target, identifying it as a firm within the Commercial & Residential Construction industry with a stated revenue of $273.4 million. The sale of direct network credentials presents a serious risk to the targeted organization.
The RDP access is being offered for a starting price of $1,000. RDP allows a user to control a computer or server remotely, meaning a malicious actor could gain a direct foothold inside the company’s network. This could be used to execute further attacks, such as deploying ransomware or stealing sensitive corporate data. The post also notes the company uses Sophos antivirus and that the seller is open to a “collaboration for %,” indicating a potential partnership to exploit the alleged access for a share of the profits.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “LyxSec” has recently surfaced as a highly active group focused on data leaks. Verified reports associate the group with numerous breaches involving unauthorized system access and efforts to sell stolen data on dark web marketplaces.
LyxSec’s continued operations reflect the persistent and adaptive nature of cyber threats emerging from the dark web. These incidents emphasize the pressing need for organizations to enhance their cybersecurity defenses through continuous monitoring, strategic use of threat intelligence, and proactive security measures to safeguard critical information assets.
Recommendations: Enhance the cybersecurity posture by:
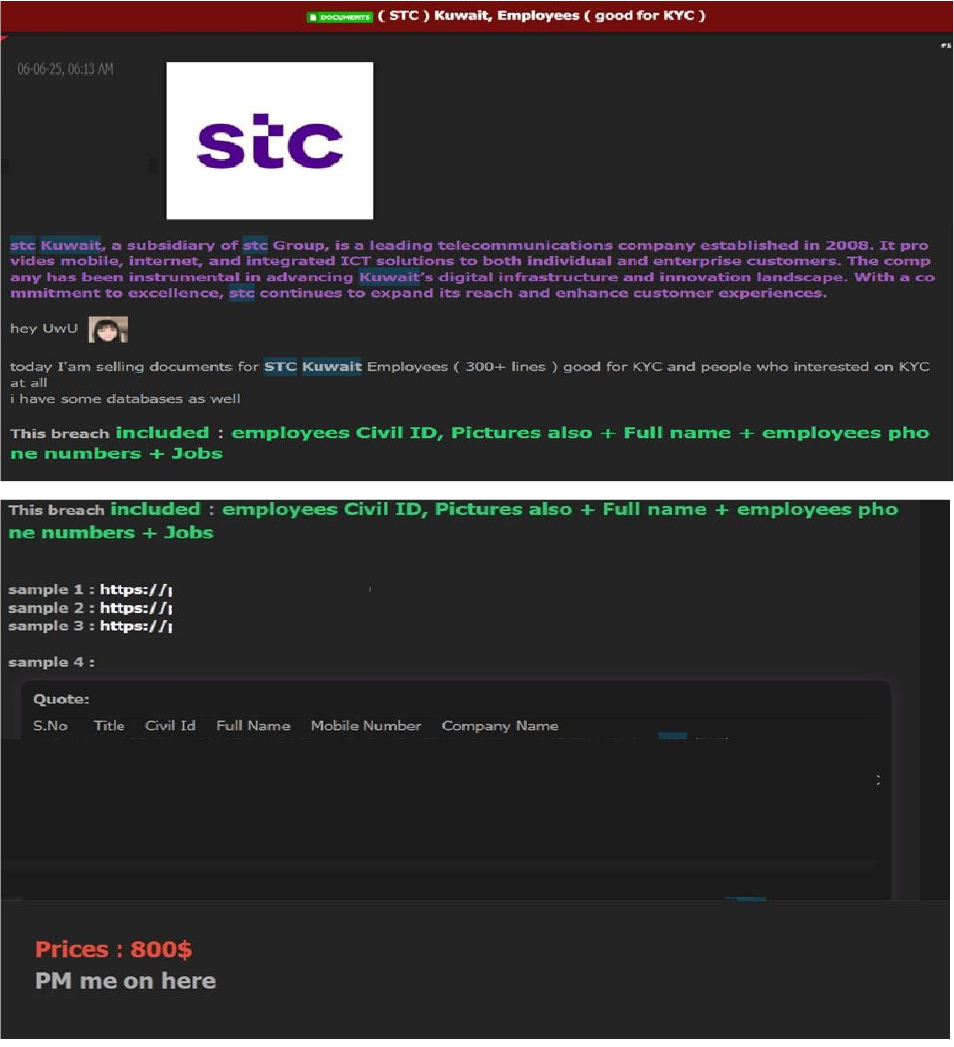
The CYFIRMA Research team observed that STC Kuwait, a major telecommunications provider in the country, has allegedly suffered a significant data breach. A threat actor has posted on a dark web forum claiming to be in possession of sensitive personal information belonging to over 300 employees of the company. STC Kuwait, a subsidiary of the stc Group, is a key player in the nation’s digital infrastructure, providing mobile, internet, and integrated ICT solutions to a wide range of customers since its establishment in 2008.
The seller on the forum claims the stolen database is particularly useful for “Know Your Customer” (KYC) verification processes, suggesting the data could be exploited for identity theft and other fraudulent activities. To substantiate their claims, the individual posted several samples of the compromised information, including screenshots of internal documents and a partial list of the affected employees. The leak allegedly exposes highly sensitive and personal employee records.
The compromised data allegedly includes the following:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
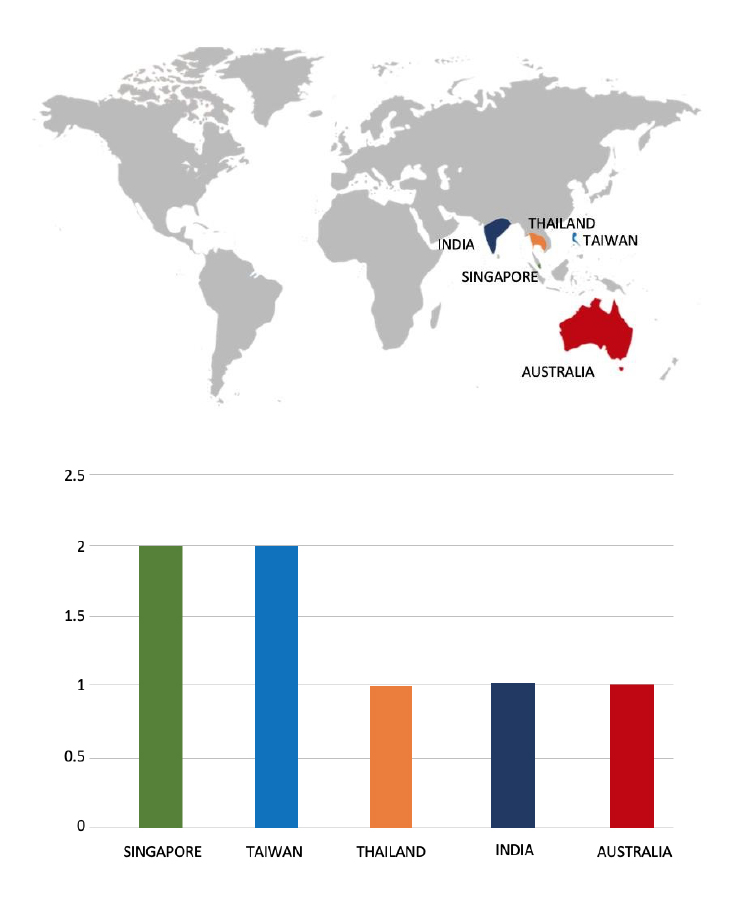
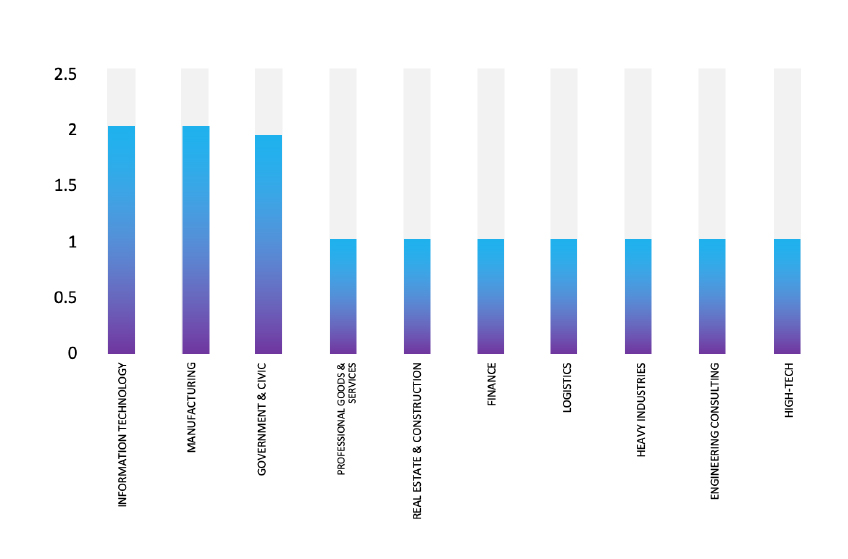
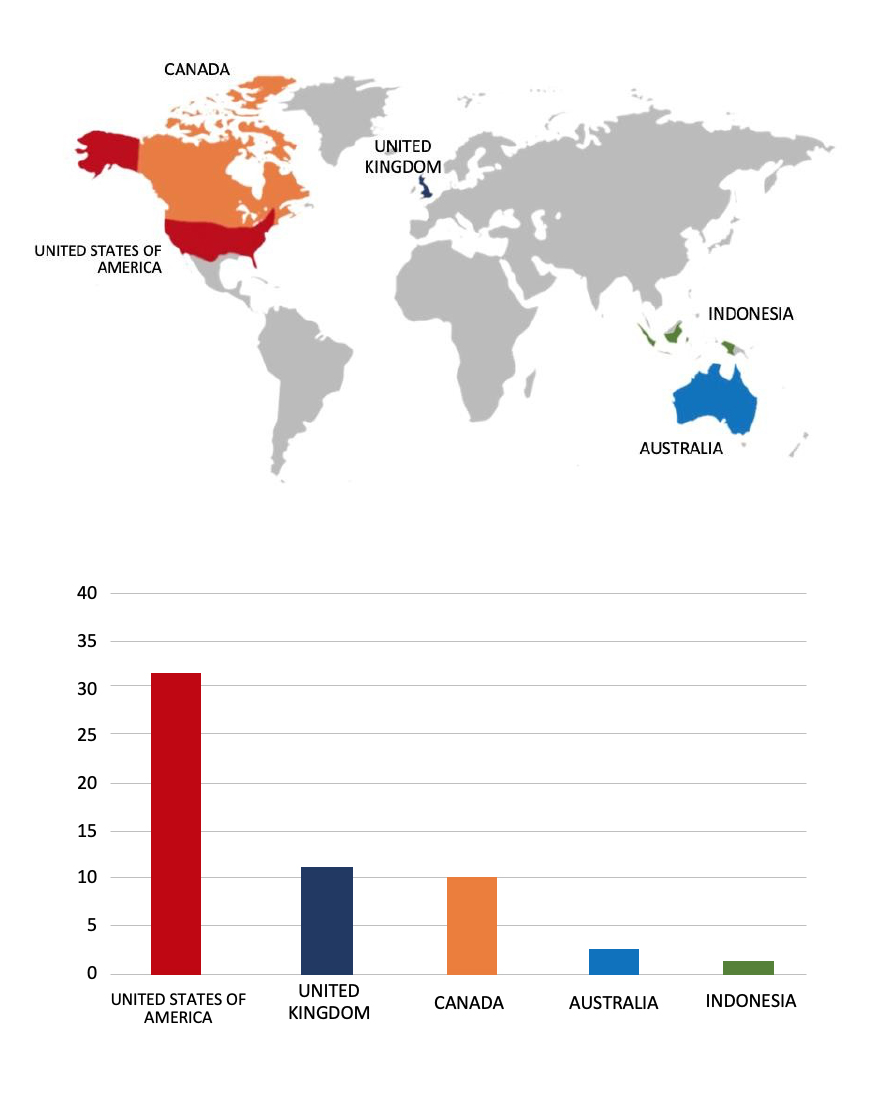
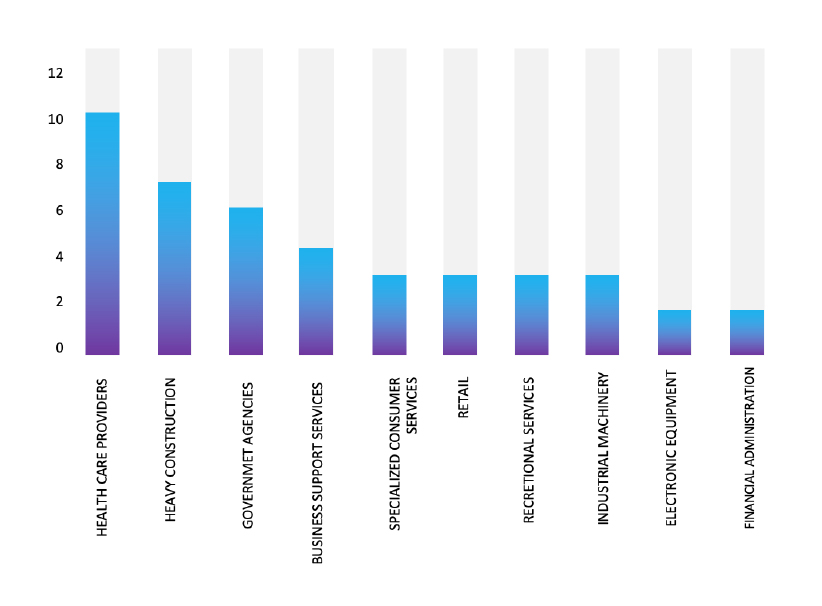
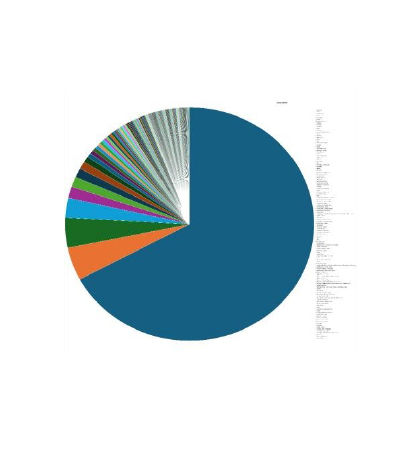
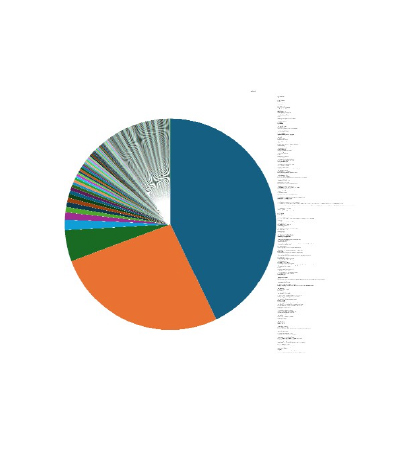
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.