



Key Intelligence Signals:
Ecuador-Based Organizations Targeted by Blind Eagle
Summary:
Blind Eagle aka APT-C-36 is a cyber espionage group, active since 2018, based in South America. They are known for targeting Columbian government cyber assets, and financial institutions and have targeted the petroleum industry. In recent attacks, Blind Eagle targeted Spanish-speaking targets in Colombia and Ecuador. In the attack, phishing emails acting to be a Colombian Ministry of Foreign Affairs, threatened the recipient with issues related to leaving the country without settling bureaucratic matters. The phishing mail drops the payload belonging to Quasar RAT; however, it is also wrapped up with a more complex infection chain that exploits the legitimate mshta.exe binary to execute VBScript embedded in an HTML file, to ultimately download two Python scripts, which adds a new stage in the infection chain. The threat actor weaponized a geo-filter feature in one of the campaigns, that redirected requests made from outside of Ecuador and Colombia to the website of the Ecuadorian Internal Revenue Service, revealing the APT’s focus.
Insights:
APT-C-36 usually targets a single country, however, in this attack the threat actor has extended his targeting region and launched campaigns against Ecuador, hinting to be more aggressive in near future.
While the Russian hacktivists, like Killnet, have served as auxiliaries in Russia’s hybrid war and have filled the media with headlines, far less has been published on the efforts of hacktivists, working on behalf of the cause of Ukraine. Ukraine has many foreign backers, while Russia enjoys good relations and support for its war effort only from a handful of countries, the most prominent of them being Iran. Tehran has been supplying the Russian military with armed drones, which Russia is using to devastate civilian infrastructure in Ukraine, which made Iran a target for Ukrainian hacktivists recently. The Cyber Sec group has claimed responsibility for a series of recent distributed denial-of-service (DDoS) attacks, which have affected several Iranian websites, including but not limited to sites belonging to the National Iranian Oil Company and Iran’s supreme leader Ali Khamenei. The group stated that their operations are a reprisal, specifically for the supply of Iranian-made Shahed kamikaze drones, used by Russia in attacks against Ukrainian civilian infrastructure. The group has also claimed, the attacks were just a showcase and threatened to attack industrial control systems in Iran if Tehran doesn’t stop the weapons flow.
Moldova is one of the countries, whose stability has been shaken by the Russian invasion of neighbouring Ukraine. The situation in Moldova shares numerous similarities to the situation of Ukraine before the war; Moldova has its own Russia-sponsored breakaway region, with a sizable Russian minority, and tries to balance its act between Russia and the West. Moldova, like Ukraine, has also been targeted by Russian cyberattacks. Recently, Moldova’s government institutions have been flooded by phishing emails, containing malicious links. The impersonation campaigns have been led by threat actors, that faked the identities of senior Moldovan officials, to lure government employees to click on malicious links. Local authorities discovered over 1300 malicious emails, sent to the email addresses of government and public institutions. Authorities have not published more details or named the attackers, but in line with recent events, researchers expect the motivation of the attacker to be lateral movement into the organizations and data espionage and their origin to be in Russia. Last year, the government of Moldova suffered from several cyberattacks. In one of them, Russian hackers targeted 80 information systems, platforms, and public portals in the country. In another, an unknown threat actor set up a website called Moldova Leaks and published damaging private exchanges of several senior politicians, which resulted in a major political scandal.
According to researchers, a little-known Russian group known as Cold River has been conducting a cyberespionage campaign against nuclear labs in the United States. More specifically, the campaign entailed the possibly FSB-linked (Russian intelligence) threat actor attempted social engineering of US employees working in nuclear research at the US Department of Energy and Lawrence Livermore National Laboratories. The campaign culminated in the late summer of the past year, during a time of heightened risk of the Russian conflict in Ukraine getting into a nuclear stage. Threats by Russian officials of potential nuclear use reached their peak during the campaign. It has not yet been made public, whether the campaign led to any results for the hackers; the US Department of Energy and the FSB declined to comment on the matt.
CYFIRMA Research team observed New Dark Pink APT group targets govt and military with custom malware.
Attacks targeting government agencies and military bodies in multiple countries in the APAC region have been attributed to what appears to be a new advanced threat actor that leverages custom malware to steal confidential information.
Security researchers refer to this group as Dark Pink, noting that it employs uncommon tactics, techniques, and procedures (TTPs).
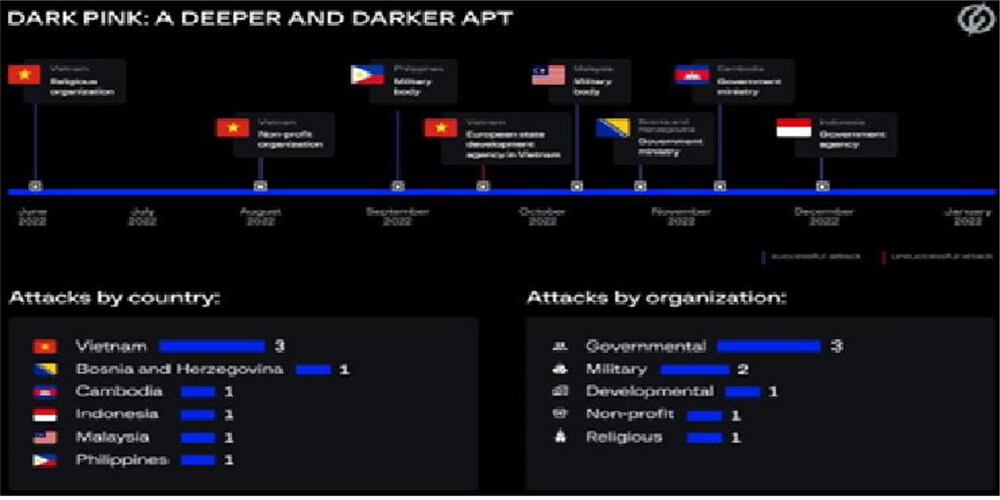
Source: Telegram
Observed a potential data leak related to www[.]epson[.]co[.]id – Digital label printers are one of the companies in Indonesia. This data leak contains the customer’s names, email addresses, and phone numbers of file size 4 GB.
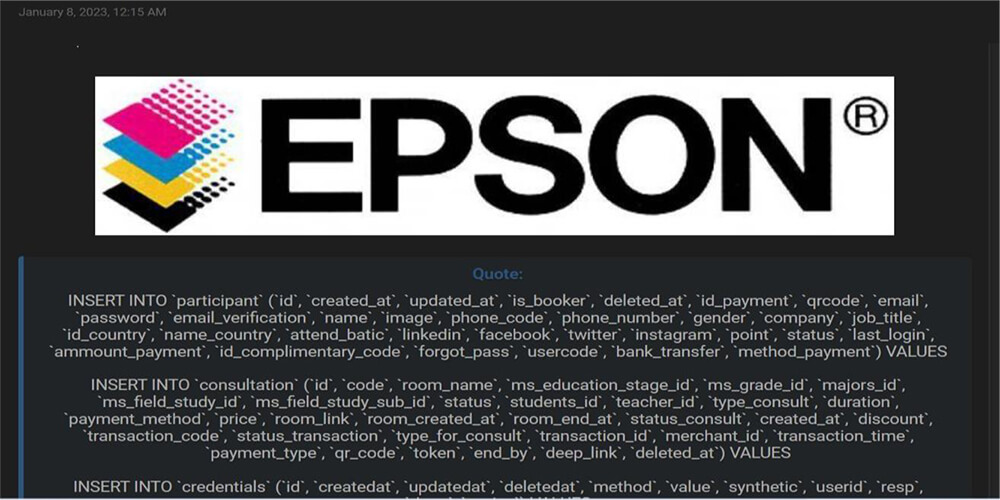
Source: Underground Forums