


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows OS
Introduction:
CYFIRMA Research and Advisory Team has found Ransoomed Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Ransoomed Ransomware
Ransoomed ransomware has been identified as an emerging extortion-focused malware strain that has been active since late 2025 and is designed to deny victims access to their data by encrypting files and appending the “.ransoomed” extension. Once executed, the malware encrypts a broad range of local files and delivers ransom instructions demanding payment in cryptocurrency in return for a purported decryption solution, while cautioning victims against altering encrypted files or attempting self-recovery and enforcing tight payment deadlines. The actors behind Ransoomed portray the operation as a ransomware-as-a-service offering, assert sole possession of the decryption capability, and deploy a ransom note in the form of “!!!READ_ME!!!.txt.” Currently, no free or verified decryption tool is available; there is no confirmed evidence that paying the ransom leads to data restoration, and payment does not reliably reduce the risk of irreversible data loss or continued exploitation of affected systems.

Screenshot: File encrypted by the ransomware (Source: Surface Web)
The Ransoomed ransomware ransom note informs victims that their files have been encrypted and renamed with the .ransoomed extension. It states that the data is protected using AES-256 and RSA-2048 encryption, and that the corresponding private decryption key is held exclusively by the attackers. It demands a payment of 2.5 Bitcoin to a specified wallet and instructs the victim to email proof of payment to an OnionMail address to receive a supposed decryption tool. The note applies psychological pressure by imposing a 72-hour deadline, threatening permanent key destruction after seven days, and warning victims not to modify files or attempt recovery using other tools. Overall, the message follows standard ransomware coercion tactics designed to induce urgency and discourage independent recovery, while offering no verifiable guarantee that file access will be restored after payment.
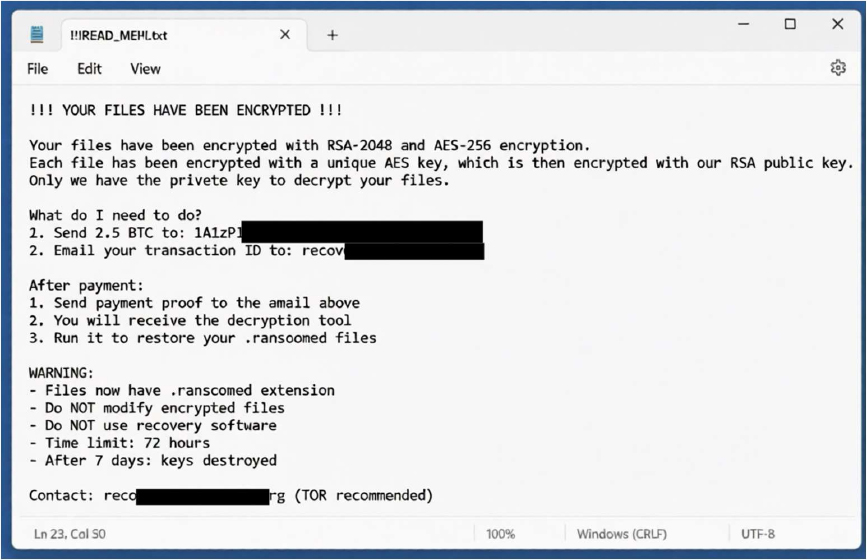
Screenshot: The appearance of the Ransoomed Ransom Note (Source: Dark Web)
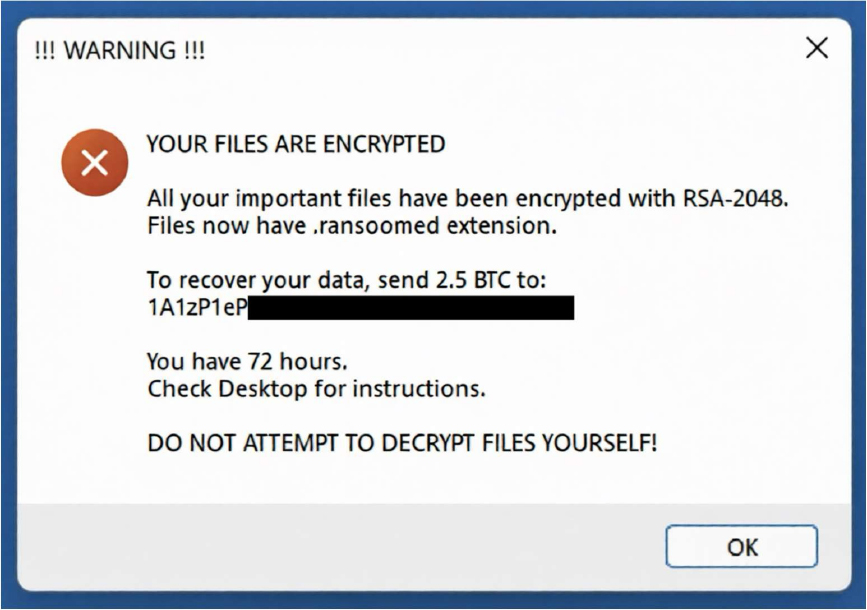
Screenshot: The appearance of Ransoomed Ransomware’s Second Ransom Note (Source: Dark Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Ransoomed ransomware is likely to persist as an extortion-centric operation with limited but functional capabilities, focusing on incremental refinement of its current execution flow rather than introducing materially new tactics or techniques. The malware already demonstrates core ransomware behaviours, file encryption, coercive ransom messaging, and recovery-hindering warnings, suggesting an intent to pressure victims primarily through data inaccessibility rather than through a mature, multi-stage extortion infrastructure. If activity continues, the operators may attempt to formalize elements of their claimed ransomware-as-a-service model, improve the reliability and presentation of their tooling, and standardize victim communications to project greater credibility. However, ongoing inconsistencies in public claims, lack of verified decryption outcomes, and indicators of early-stage development strongly suggest that any evolution will be limited to superficial or incremental improvements. As a result, Ransoomed’s future activity is expected to remain opportunistic, unevenly executed, and constrained by its evident lack of technical depth, operational discipline, and established criminal reputation.
Sigma rule:
title: Disable Windows Defender AV Security Monitoring tags:
– attack.defense-evasion
– attack.t1562.001 logsource:
category: process_creation product: windows
detection: selection_pwsh_binary:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’ selection_pwsh_cli:
CommandLine|contains:
– ‘-DisableBehaviorMonitoring $true’
– ‘-DisableRuntimeMonitoring $true’ selection_sc_binary:
– Image|endswith: ‘\sc.exe’
– OriginalFileName: ‘sc.exe’ selection_sc_tamper_cmd_stop:
CommandLine|contains|all:
– ‘stop’
– ‘WinDefend’ selection_sc_tamper_cmd_delete:
CommandLine|contains|all:
– ‘delete’
– ‘WinDefend’ selection_sc_tamper_cmd_disabled:
CommandLine|contains|all:
– ‘config’
– ‘WinDefend’
– ‘start=disabled’
condition: all of selection_pwsh_* or (selection_sc_binary and 1 of selection_sc_tamper_*)
falsepositives:
– ‘Minimal, for some older versions of dev tools, such as pycharm, developers were known to sometimes disable Windows Defender to improve performance, but this generally is not considered a good security practice.’
level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information stealer| Objectives: Data Exfiltration | Threat Actor: Unknown| Target Technology: Windows OS | Target Geography: Global (India, the United States, Brazil, the Russian Federation, and Turkey)
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “RedEngine Loader” is trending.
Overview of Operation RedEngine Loader
The cybersecurity community has discovered an ongoing malware operation that is spread through pirated video games. The campaign, which has been running since at least early 2025, makes use of customized game installers that look to be legitimate and work properly. By hiding the virus behind cracked versions of popular games, the attackers take advantage of players’ trust and interest, allowing the infection to spread extensively without raising instant suspicion. This has allowed the campaign to continue for a long time without being identified.
The intimate integration of malware and genuine applications makes this approach particularly effective. The malicious code is disguised within game launchers based on a well-known and trusted game engine. In many circumstances, the game runs normally, persuading users that nothing is amiss, while hidden programs operate quietly in the background. Because everything looks to be normal, neither users nor security tools are likely to discover the attack early.
The infection spreads gradually. After the game’s initial release, additional malicious components are slowly introduced, allowing the attackers to maintain access and expand their control over time. The main goal is to collect sensitive information, including saved browser passwords, session data, cryptocurrency details, and other personal information, and send it to attacker-controlled servers.
Overall, this campaign exemplifies the deliberate and covert nature of modern malware attacks. Rather than employing obvious or aggressive methods, the attackers rely on trusted software, established platforms, and discreet background activity. It emphasizes the dangers of downloading unlicensed software and the significance of exercising caution while installing programs from unknown sources.
Attack Method
The attack begins when users download pirated game installers or modified add-ons from popular crack and mod-sharing sites. These files are presented as fully functional, pre-activated versions of well-known games, taking advantage of piracy communities’ confidence rather than exploiting software weaknesses. When consumers install and start the game, it operates exactly as expected, which helps to conceal malicious activities during the initial phases of infection.
When the game is launched, a covert loader begins running in the background. This loader is intended to remain undetected and first determines if it is executing on a legitimate user’s system or in a security testing environment. It examines fundamental system details and signals of typical user activity before proceeding if the system appears safe to analyse. This enables malware to elude early detection by security technologies.
Following these checks, other harmful components are inserted gradually. The malware conducts its operations through trusted system processes, allowing it to grow its capabilities while remaining silent. This slow technique allows the attackers to maintain long-term access to the system rather than causing rapid or visible damage.
In the final stage, the malware installs a data-stealing component that gathers sensitive information such as saved passwords, browsing data, and cryptocurrency information. This information is discreetly transmitted to servers controlled by the attackers. Overall, the attack demonstrates how cybercriminals can exploit trusted software and user behavior to remain hidden for extended periods of time, making the danger more difficult to detect and respond to.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic (ID) | Technique ID | Technique Name |
| Execution | T1204.002 | User Execution: Malicious File |
| T1129 | Shared Modules | |
| T1059.006 | Command and Scripting Interpreter: Python | |
| Defense Evasion | T1027 | Obfuscated/Compressed Files & Information |
| T1497 | Virtualization/Sandbox Evasion | |
| T1140 | Deobfuscate/Decode Files or Information | |
| T1055 | Process Injection | |
| T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control | |
| T1562 | Impair Defenses | |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1574 | Hijack Execution Flow | |
| Discovery | T1082 | System Information Discovery |
| T1012 | Query Registry | |
| T1057 | Process Discovery | |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Collection | T1115 | Clipboard Data |
| Command and control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
INSIGHTS
ETLM Perspective
RedEngine is a multi-stage loader and information-stealing virus found in recent cybercrime campaigns. It primarily serves as an initial access enabler, gaining a footing on the victim system before releasing additional payloads. This access can enable downstream attacks, such as Business Email Compromise (BEC), financial fraud, and ransomware deployment. The threat is especially severe since it relies on user involvement and social engineering, limiting the effectiveness of traditional perimeter-based protection measures. Immediate actions organizations should undertake include:
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems. (Source: Surface Web)
YARA Rules
rule RenEngine_Loader_String_IOCs
{
meta:
description = “Detects RenEngine Loader activity” author = “CYFIRMA”
reference = “RenEngine Loader Campaign” date = “2026-02-09”
confidence = “Medium”
strings:
/* Malware Sample Hashes */
$hash_1 = “645d7c74823d39394c46c942955960dd”
$hash_2 = “1001e0a83d0a622828613a4a66735ce0”
$hash_3 = “17de79f44b8af959b3ae9e486ade55b2”
/* Infrastructure Domain & C2 Server IP */
$domain = “dodi-repacks.site”
$ip = “78.40.193.126”
condition:
any of ($hash_*) or any of ($domain, $ip)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Key Intelligence Signals:
Chinese Threat Actor Lotus Blossom: Intelligence-Gathering Operations Assessment
About the Threat Actor
Lotus Blossom is a long-standing and persistent cyber espionage threat actor that has been active since 2009. The group has conducted sustained, targeted espionage campaigns primarily affecting organizations across Southeast Asia, with more recent operations observed in Central America. Its activities predominantly focus on high-value sectors, including government, telecommunications, aviation, critical infrastructure, and media organizations, underscoring its enduring role as an established espionage threat.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2019-0708 | Microsoft Remote Desktop Services | 9.8 | Link1, Link2, Link3, Link4, Link5 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| ResourceDevelopment | T1588.002 | Obtain Capabilities: Tool |
| Execution | T1047 | Windows Management Instrumentation |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1112 | Modify Registry |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| DefenseEvasion | T1134 | Access Token Manipulation |
| DefenseEvasion | T1112 | Modify Registry |
| CredentialAccess | T1539 | Steal Web Session Cookie |
| Discovery | T1087.001 | Account Discovery: Local Account |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1482 | Domain Trust Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1016.001 | System Network Configuration Discovery: Internet Connection Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
Latest Developments Observed
The threat actor is suspected of deploying the Chrysalis backdoor and the Warbird loader to compromise infrastructure hosting Notepad++. The activity appears intended to facilitate the exfiltration of sensitive information.
ETLM Insights
Lotus Blossom is assessed as a long-standing and persistent cyber espionage group, where strategic intelligence collection and geopolitical objectives consistently outweigh financial motivation. The threat actor maintains a sustained focus on acquiring sensitive governmental, diplomatic, and technological intelligence, leveraging prolonged access and operational patience to support broader state- aligned strategic interests. Its campaign history reflects deliberate targeting aimed at long-term visibility into political decision-making, regional security dynamics, and critical service environments rather than short-term disruption.
Operationally, Lotus Blossom emphasizes stealth, persistence, and low-noise intrusion techniques to maintain durable access within high-value networks. Looking ahead, Lotus Blossom is expected to refine persistence mechanisms and expand identity- centric attack techniques such as credential abuse, cloud account compromise, and trusted relationship exploitation. This trajectory reinforces the group’s role as an enduring espionage threat capable of maintaining covert presence across strategically significant sectors, posing sustained intelligence and resilience risks to targeted organizations.
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule CVE_2019_0708_BlueKeep_IOC_Detection
{
meta:
description = “Detects potential CVE-2019-0708 (BlueKeep) exploitation artifacts based on known IOCs”
author = “CYFIRMA” reference = “CVE-2019-0708” confidence = “IOC-based” date = “2026-02-10”
strings:
/* File indicators */
$hash1 = “44812b44591121f3e711223db099043d4d72288e4f436dba2fb935b6d888d40” ascii
$file1 = “swprve.dll” ascii
$path1 = “save_malware_samples_to_disk” ascii
$path2 = “\\windows\\syswow64\\” ascii
/* Domain indicators */
$dom1 = “remotewd.com” ascii
$dom2 = “hack4gov.ph” ascii
$dom3 = “data.data” ascii
$dom4 = “mcast.net” ascii
$dom5 = “mmscloudteam.com” ascii
/* IP indicators */
$ip1 = “13.225.38.97” ascii
$ip2 = “13.225.38.70” ascii
$ip3 = “13.225.38.19” ascii
$ip4 = “13.225.30.214” ascii
$ip5 = “13.225.30.180” ascii
condition: (
any of ($hash*) or
any of ($file*, $path*) or any of ($dom*) or
any of ($ip*)
)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Singapore’s telecom penetrated by China-Linked UNC3886
Singapore’s Cyber Security Agency (CSA) has revealed that a China-linked cyber espionage group, known as UNC3886, carried out a deliberate, targeted, and well- planned campaign against all four of the country’s major telecommunications operators. The affected providers are: Singtel, M1, StarHub, and Simba Telecom.
The telcos and government worked together to contain the threat, remove the attackers’ access (which involved rootkits, zero-day exploits, and advanced persistence techniques), and strengthen defenses. Minister for Digital Development and Information Josephine Teo emphasized that while no sensitive data was compromised and services remained uninterrupted, the incident underscores the ongoing and evolving cyber threats to critical infrastructure.
ETLM Assessment:
Chinese state-linked advanced persistent threat (APT) groups, such as Salt Typhoon (also tracked as RedMike, GhostEmperor, UNC5807, and others) and UNC3886, have systematically embedded themselves in telecommunications infrastructure worldwide over recent years. These actors exploit vulnerabilities in network edge devices (routers, firewalls, VPN gateways from vendors like Cisco, Juniper, Ivanti, and Palo Alto), deploy custom rootkits and backdoors, and modify router configurations to achieve long- term, stealthy persistence. Notable examples include the Salt Typhoon campaign, which, since at least 2019, has compromised hundreds of organizations across more than 80 countries — including major U.S. providers (AT&T, Verizon, T-Mobile, Lumen), Canadian telecom firms, Australian critical networks, and Singapore’s four main operators in 2025.
The primary motivation is strategic espionage and intelligence dominance. By compromising telecom backbone networks and internet service providers (ISPs), Chinese intelligence services — primarily the Ministry of State Security (MSS) — gain a powerful, global vantage point to identify, track, and surveil high-value targets (government officials, diplomats, military personnel, dissidents, corporate executives, and researchers) across borders. Access to telecom infrastructure enables the collection of vast communication metadata, location data from mobile networks, and insights into movements and relationships — all without needing to breach individual devices or services directly. This capability supports broader foreign intelligence objectives, counters perceived threats, protects overseas interests, and prepares potential future disruptive options in crisis scenarios, while remaining below the threshold of overt conflict.
Cyberweapons assisted US strikes on the Iranian nuclear programme
The U.S. Cyber Command played a decisive role in last year’s strikes on Iran’s nuclear facilities by using offensive cyber operations to neutralize key elements of Iran’s integrated air and missile defense network. According to an anonymous source with direct knowledge of the operation, U.S. cyber operators – working in close coordination with the National Security Agency (NSA) – identified and exploited a critical vulnerability described as an “Achilles heel” in Iran’s surface-to-air missile (SAM) systems, media reports. This cyber intrusion prevented Iranian forces from effectively tracking, targeting, or launching missiles against the American strike aircraft conducting Operation Midnight Hammer. The source explained: “Military systems often rely on a complex series of components, all working correctly. A vulnerability or weakness at any point can be used to disrupt the entire system.”
By introducing targeted disruption—likely through exploitation of command-and- control links, radar processing, or missile guidance networks—the U.S. ensured that Iran’s air defenses remained blind or unresponsive during the critical window of the bombing campaign. Technical specifics of the cyber payload, the exact systems compromised, or the method of delivery (e.g., zero-day exploits, supply-chain compromise, or pre-positioned implants) have not been revealed.
ETLM Assessment:
The disclosure underscores the growing centrality of cyber effects in modern joint military operations, particularly in the suppression of enemy air defenses (SEAD) mission set, and highlights Cyber Command’s role in enabling kinetic strikes against heavily defended targets. However, if remnants of the U.S. cyber payload – such as modified firmware, rootkits, or command logs – are captured from compromised Iranian systems during post-strike forensics, security researchers could reverse-engineer its code, exploits, and techniques to attribute it to American operators, much like how Stuxnet’s zero-day vulnerabilities and centrifuge-specific sabotage were dissected in 2010 to reveal its origins as a joint U.S.-Israeli operation.
Former Google engineer stole AI IP for China
A federal jury in San Francisco has found former Google software engineer guilty of stealing highly sensitive AI trade secrets on behalf of the Chinese government. According to the U.S. Justice Department, the stolen information included detailed technical specifications about Google’s custom Tensor Processing Unit (TPU) chips and systems, its Graphics Processing Unit (GPU) infrastructure, the software enabling communication and task execution between these chips, and the orchestration software that links thousands of chips into a supercomputer capable of training and running state-of-the-art AI models. The purloined material also covered Google’s proprietary SmartNIC, a specialized network interface card critical for ultra-fast data transfer within the company’s AI supercomputers and cloud networking products.
ETLM Assessment:
As previously noted in this CYFIRMA report, the loss of intellectual property (IP) through cyber espionage and cybercrime constitutes the greatest transfer of wealth in history.
U.S. companies alone lose around a quarter to half a trillion dollars annually through intellectual property theft, with over a hundred billion lost due to cybercrime – a number that can be tripled when the costs of downtime are taken into account. There are many challenges in the field of IP protection, however, the chief among them is China and its national program of integrating IP theft into Chinese industry via cyber espionage, as its ambitions are curtailed by export restrictions. Some of the most vulnerable industries to this campaign are those in information technology, advanced manufacturing (especially in semiconductors), aerospace, maritime, rail, high-tech shipping equipment, new-energy vehicles, biotech, and pharmaceutical products.
Qilin Ransomware Impacts Kouei Co., Ltd Attack Type: Ransomware
Target Industry: Industrial Manufacturing Target Geography: Japan Ransomware: Qilin Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Kouei Co., Ltd (https[:]//www[.]kabkouei[.]co[.]jp/), was compromised by Qilin Ransomware. Kouei Co., Ltd. is a Japan-based industrial manufacturer and materials supplier specializing in nickel alloys and related processing for high-tech and heavy industry applications. The leaked data shown in the images appears to contain a mix of highly sensitive personal information and confidential corporate records. The exposure includes government-issued identity documents, such as Japanese passports, revealing full names, photographs, dates of birth, passport numbers, nationality details, and issue/expiry dates, which constitute critical personally identifiable information (PII). In addition, the images show confidential business documents, including non-disclosure agreements (NDAs), legal contracts, and internal company records in both English and Japanese, indicating the compromise of restricted corporate and legal information.
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
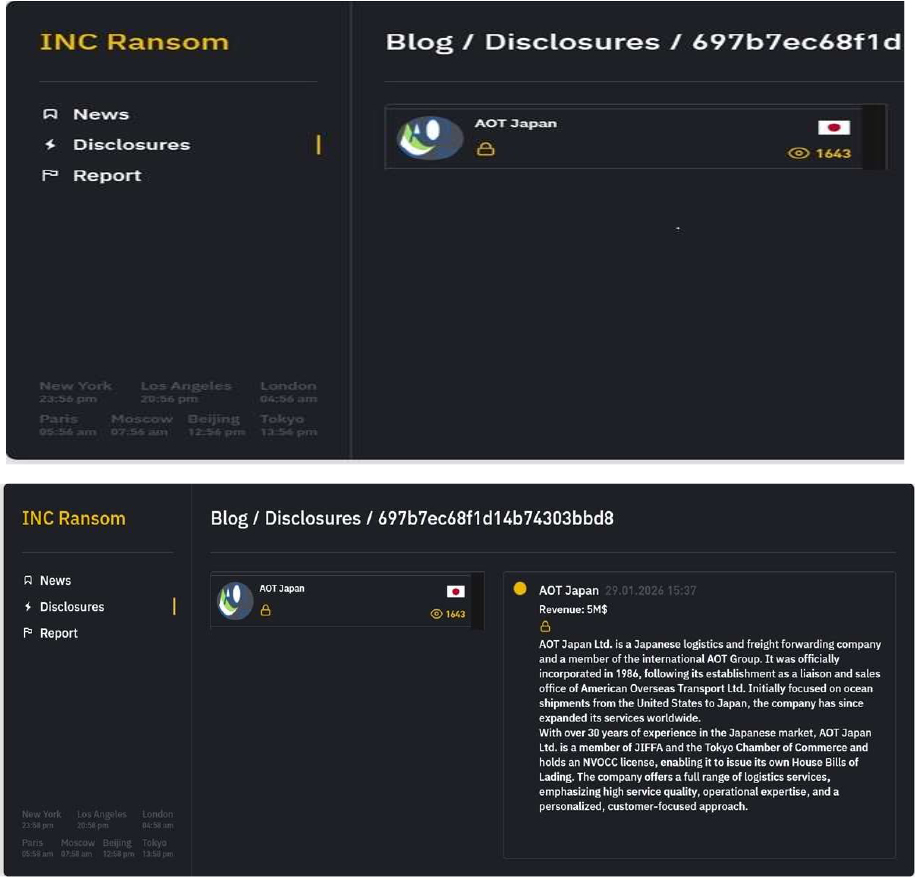
INC Ransomware Impacts AOT Japan Ltd
Attack Type: Ransomware
Target Industry: Logistics and Transportation
Target Geography: Japan
Ransomware: INC Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, AOT Japan Ltd(https[:]//www[.]aotjapan[.]com/), was compromised by INC Ransomware. AOT Japan Ltd. is a Japanese logistics and freight forwarding company and a member of the international AOT Group. It was officially incorporated in 1986, following its establishment as a liaison and sales office of American Overseas Transport Ltd. Initially focused on ocean shipments from the United States to Japan, the company has since expanded its services worldwide. With over 30 years of experience in the Japanese market, AOT Japan Ltd. is a member of JIFFA and the Tokyo Chamber of Commerce and holds an NVOCC license. The company offers a full range of logistics services, emphasizing high service quality, operational expertise, and a personalised, customer-focused approach. The compromised data includes confidential and sensitive information belonging to the organization.
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, INC Ransomware represents a significant threat within the evolving landscape of ransomware attacks. Its use of strong encryption methods and double extortion tactics highlights the increasing sophistication of cybercriminal operations. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this and other ransomware variants. Continuous vigilance is essential to protect against the threats posed by emerging ransomware groups like INC Ransomware.
Vulnerability in NanoMQ
Relevancy & Insights:
The vulnerability exists due to a NULL pointer dereference error when handling shared subscriptions.
Impact:
A remote attacker can pass specially crafted data to the application and perform a denial of service (DoS) attack.
Affected Products:
https[:]//github[.]com/nanomq/nanomq/security/advisories/GHSA-qv5f-c6v2-2f8h
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
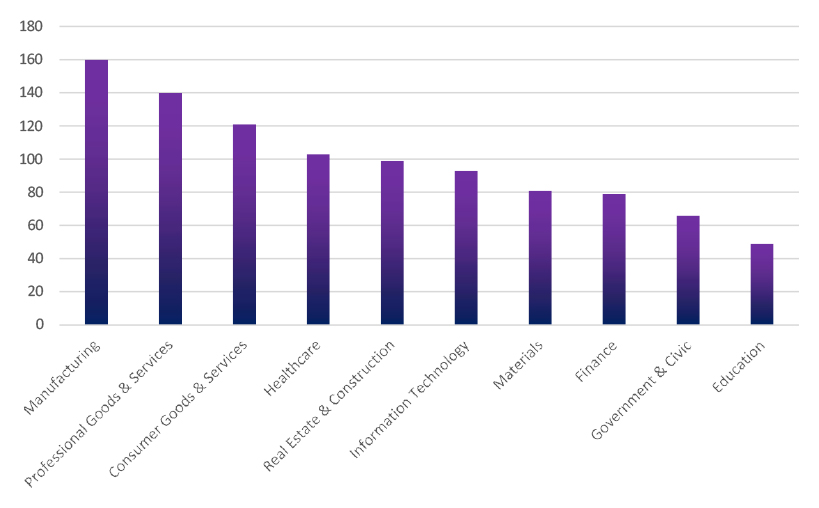
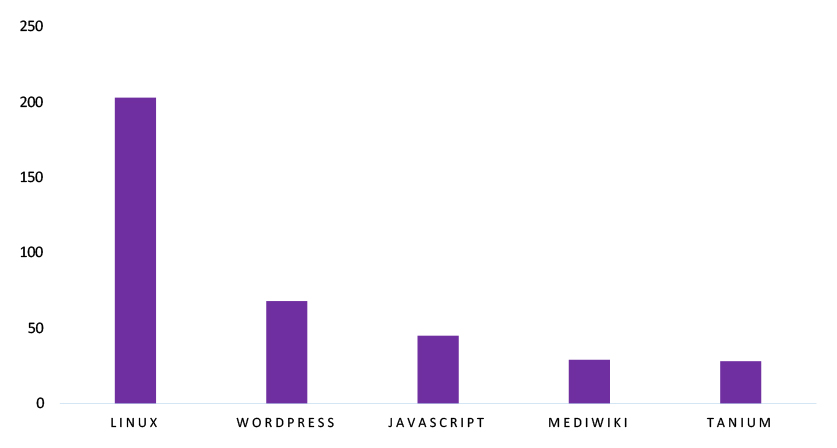
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in NanoMQ can pose significant threats to messaging reliability and lightweight communication infrastructures. This can impact industries relying on NanoMQ for IoT device communication, real-time data delivery, message brokering, and distributed event-driven workloads. Ensuring the security of NanoMQ is crucial for maintaining continuous data flow, stable message processing, and the availability of interconnected systems. Therefore, addressing this vulnerability is essential to safeguarding message routing operations, preventing service interruptions, and ensuring consistent operation of IoT networks and broker-based architectures across different geographic regions and industry sectors.
Everest Ransomware attacked and published the data of Shinwa Co., Ltd
Threat Actor: Everest Ransomware
Attack Type: Ransomware
Objective: Data Leak, Financial Gains
Target Technology: Web Applications
Target Industry: Construction Equipment & Materials Manufacturing
Target Geography: Japan
Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that Everest Ransomware attacked and published the data of Shinwa Co., Ltd(https[:]//www[.]shinwa-jp[.]com/) on its dark web website. Shinwa Co., Ltd is a Japan-based company primarily engaged in the civil engineering and construction business. The company’s operations include disaster recovery work, civil engineering, and building construction. Its construction business involves the building of private homes, condominiums, and commercial facilities. Shinwa also partakes in real estate buying, selling, and rental activities. The ransomware incident resulted in the exposure of approximately 42 GB of data, including a database and internal company documents that contained personal records and sensitive client information.
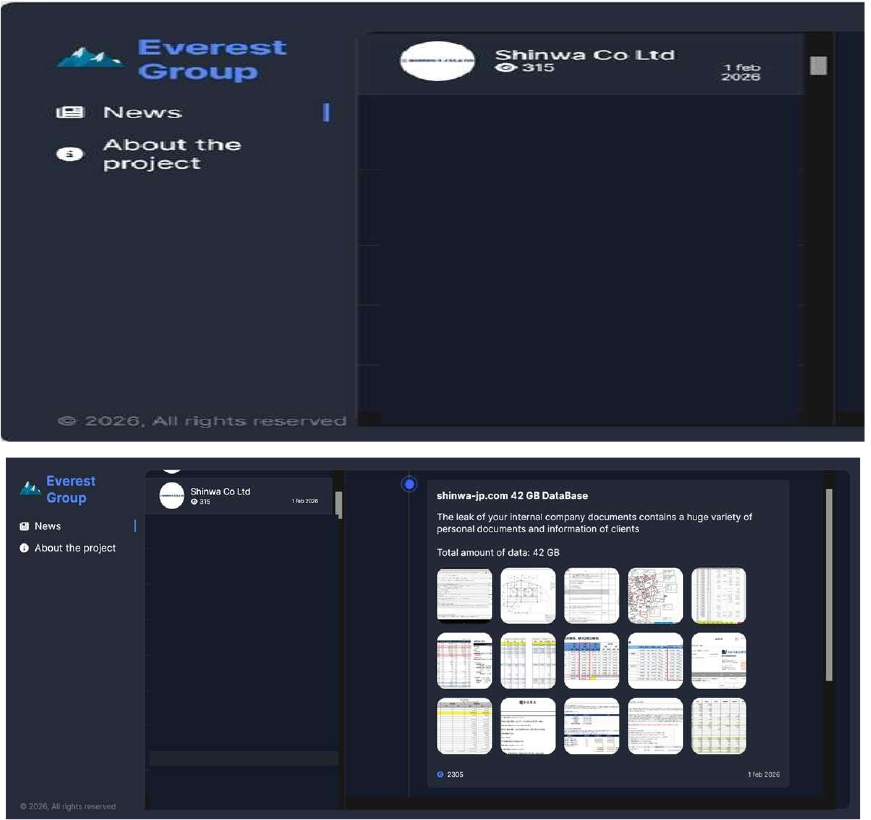
Source: Dark Web
Relevancy & Insights:
Everest is a “double-extortion” ransomware gang: attackers first exfiltrate data, then encrypt systems, and finally threaten to leak or sell the stolen information unless a ransom is paid.
ETLM Assessment:
According to CYFIRMA’s assessment, Everest ransomware continues to pose a persistent and evolving cyber threat. The group is actively broadening its targeting across new sectors, expanding its role as an initial access broker, and increasingly relying on data-leak extortion as its core operational tactic. Organizations are advised to remain vigilant by strengthening access controls, closely monitoring for lateral movement and Cobalt Strike–related activity, and maintaining robust incident response and detection capabilities to mitigate the risks posed by Everest’s ongoing campaigns.
Indonesian Government Land Authority Advertised on a Leak Site
Attack Type: Access sale
Target Industry: Government
Target Geography: Indonesia
Objective: Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary: The CYFIRMA research team has identified a dark web forum post advertising alleged unauthorized access to network infrastructure associated with the Indonesian Government Land Authority. The listing claims the sale of privileged administrative access to a firewall device, potentially exposing critical government systems to compromise.
Top of FormBottom of Form The observed forum post was published on February 4, 2026, by a user operating under the alias “miyako”, identified as an Initial Access Broker (IAB). The actor is offering access to what is described as a Linux-based firewall system belonging to the Indonesian Government Land Authority. The seller claims that the access includes root-level remote code execution (RCE), shell access, and full network administrator panel control.
The access is advertised for $300, with the seller stating that the price is non-negotiable and restricted to serious buyers. The post includes standard underground marketplace disclaimers, such as claims of no affiliation with organized cybercriminal groups.
Technical Details (As Advertised)
The authenticity of this Access sale is unverified at the time of reporting, as the claim originates solely from the threat actor.
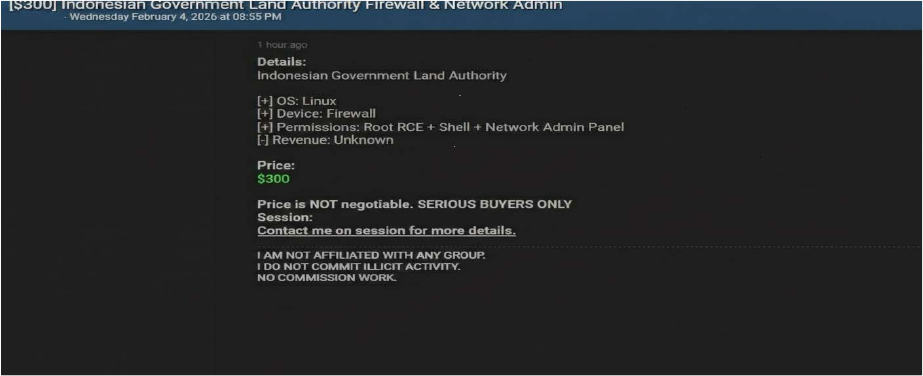
Source: Underground Forums
Leora Infotech Data Advertised on a Leak Site
Attack Type: Data leak
Target Industry: Information Technology
Target Geography: India
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary: The CYFIRMA research team identified an alleged cyber intrusion involving Leora Infotech Private Limited, an India-based IT services and consulting firm. The company, which provides software solutions, automation, ERP, and HR services, reportedly had its data advertised for sale on a dark web forum on February 6, 2026. The listing was posted by the threat actor “KaruHunters,” who is offering the compromised database for $200.
According to the actors, the breach affects approximately 35,000 records. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
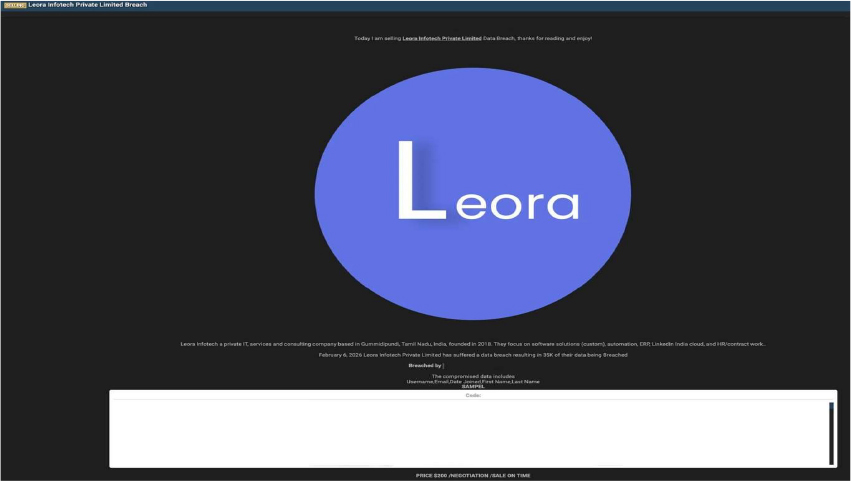
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “KaruHunters” is a highly active and sophisticated group specializing in data leaks. Numerous credible sources attribute multiple security breaches to this group, involving unauthorized access to systems and the illicit sale of stolen data on dark web marketplaces. KaruHunters’ operations highlight the persistent and evolving nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to enhance their cybersecurity posture through continuous monitoring, leveraging advanced threat intelligence, and adopting proactive defense strategies to protect sensitive data and vital infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that EgyptAir, the state-owned flag carrier of Egypt, has allegedly been compromised by an unauthorized party selling internal databases on a cybercrime forum. The leak, which purportedly contains over 104,000 records, includes sensitive human resources data and operational documents. The dataset is currently being offered for sale with a starting price of $300 USD in Monero (XMR).
According to the actor, the compromised files include CSV exports from the airline’s HR and user management systems (e.g., Egyptair_HROLC_Personal_Data2020.csv and Egyptair_HROLC_Users_Account s.csv). The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
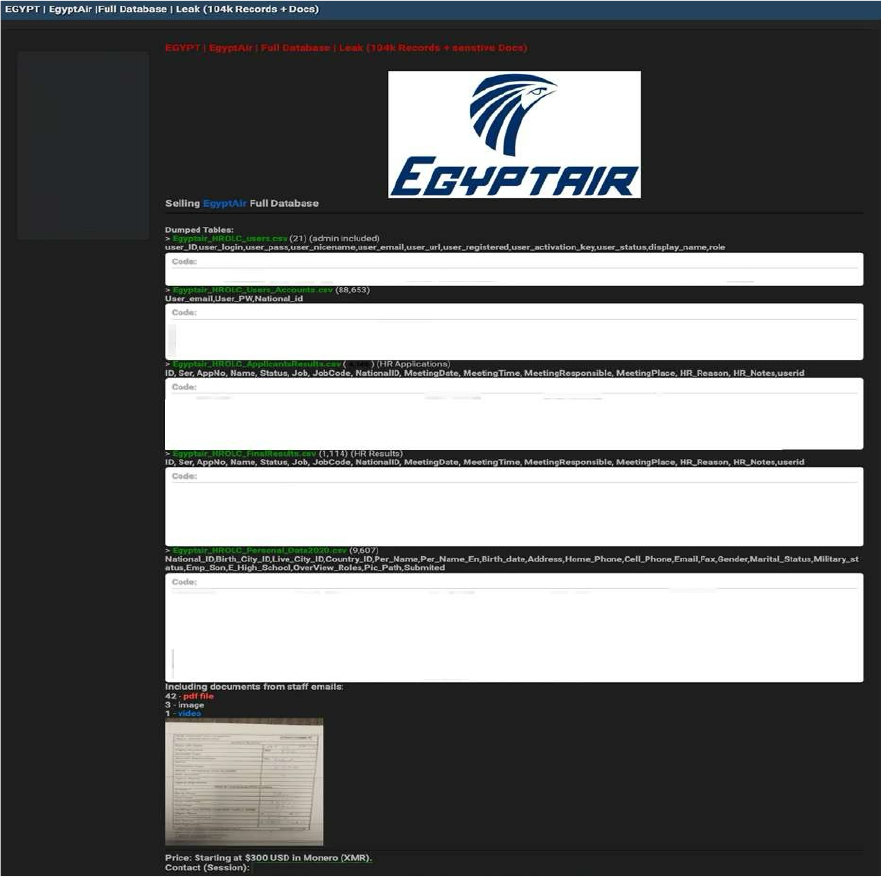
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
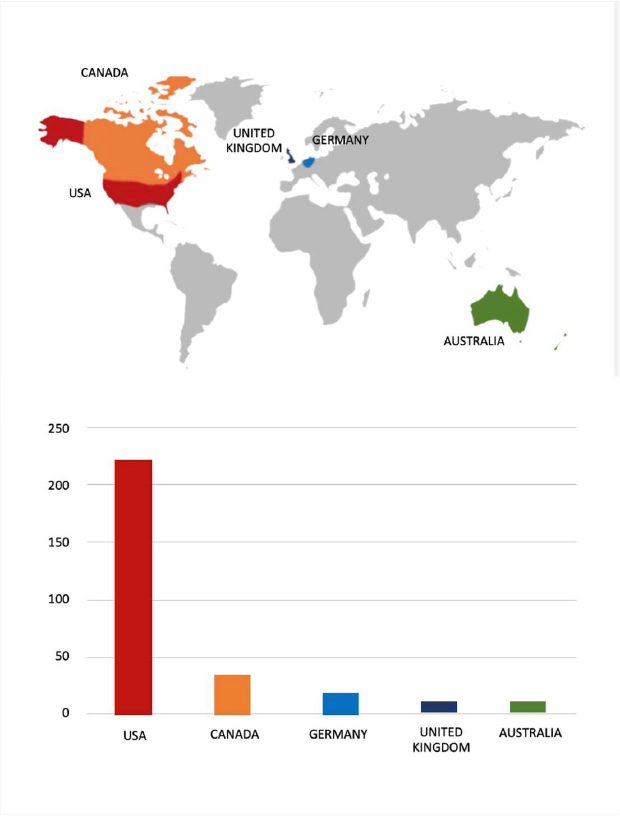
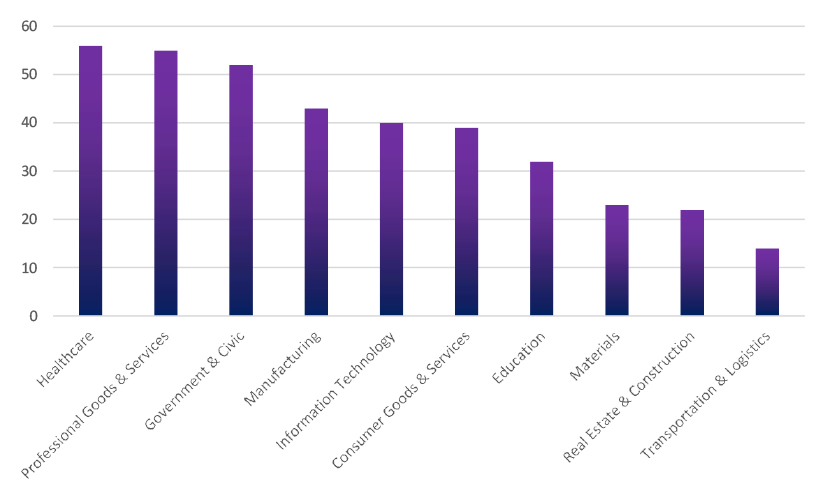
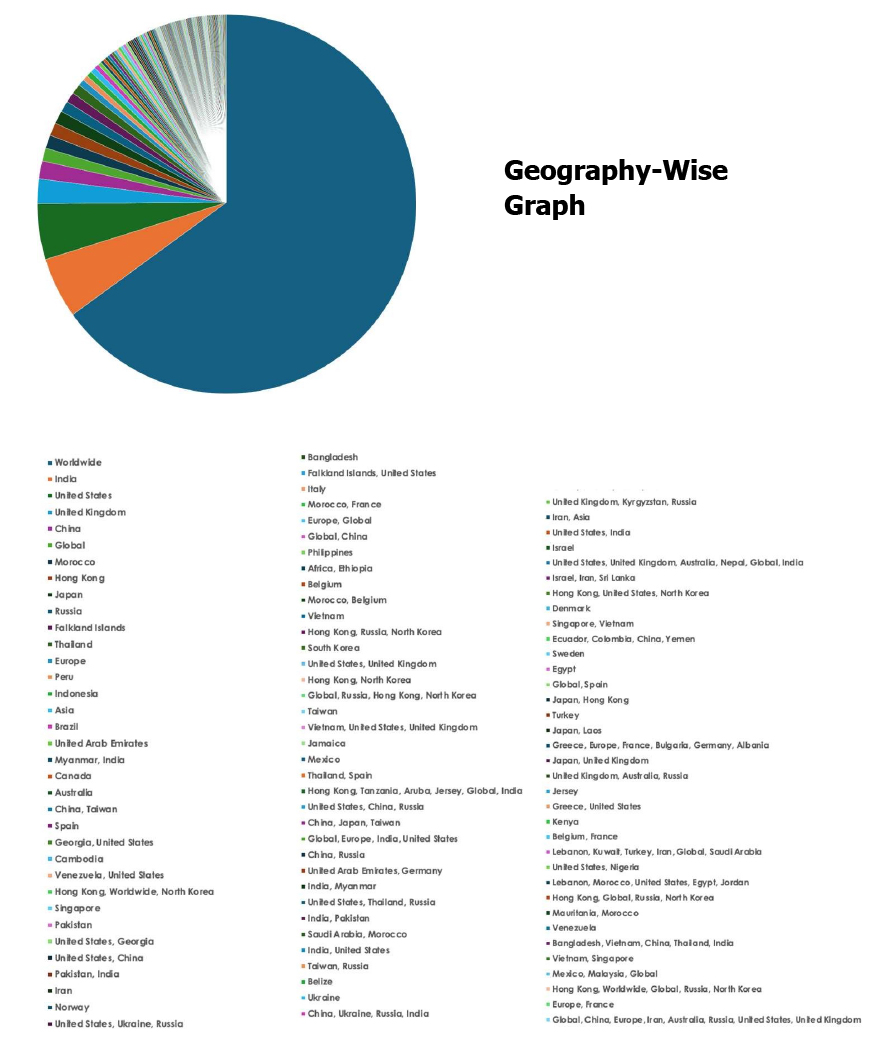
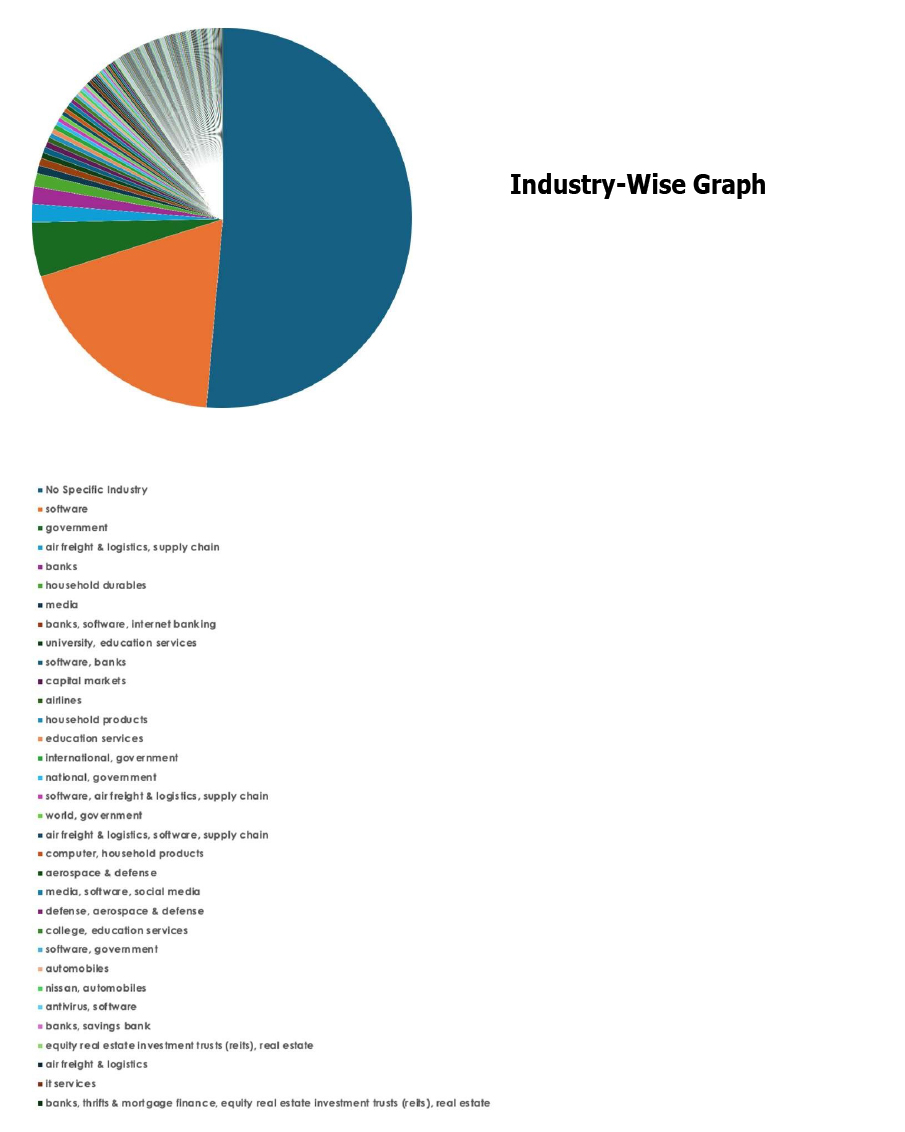
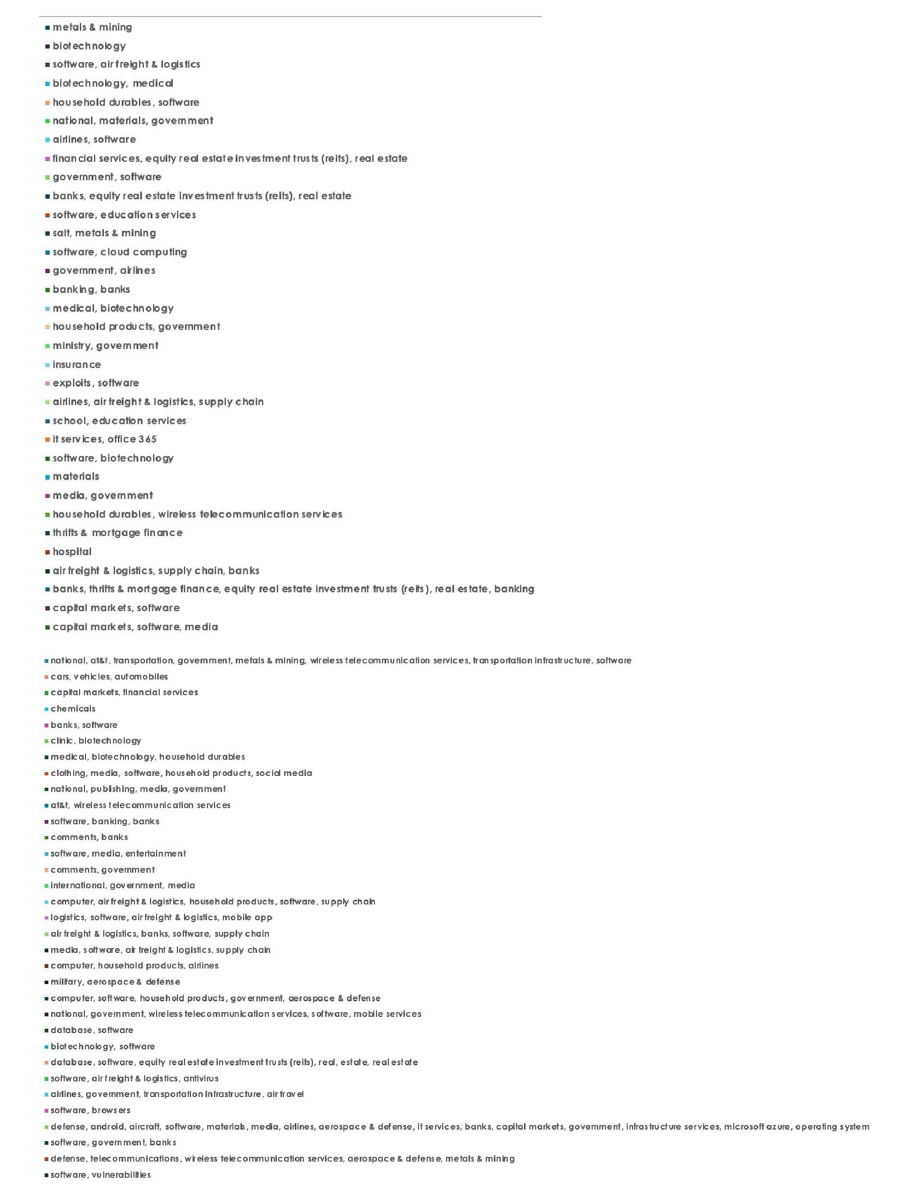
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.