



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found AllCiphered Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
AllCiphered Ransomware
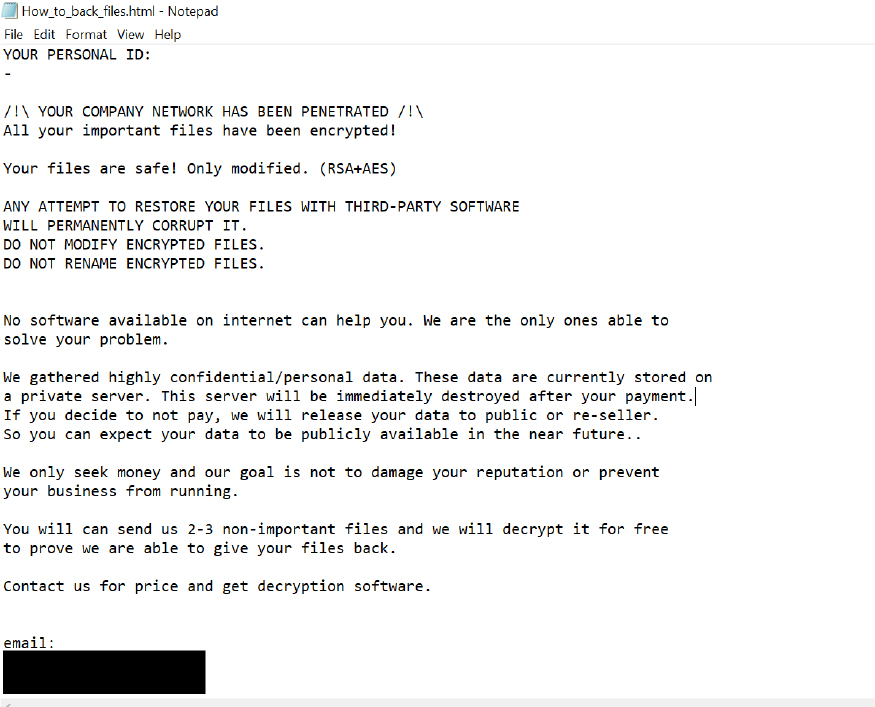
Researchers have recently identified a new variant of the MedusaLocker ransomware family, named AllCiphered. This ransomware encrypts files and appends the “.allciphered70” extension to the encrypted file names, with the number in the extension potentially varying depending on the specific variant.
After completing the encryption process, AllCiphered creates a ransom note in the form of an HTML file titled “How_to_back_files.html,” demanding payment for file decryption.

The ransom note informs the victim that their company’s network has been compromised, and that the encrypted files were secured using RSA and AES cryptographic algorithms. It warns that any attempts to rename, modify, or decrypt the files using third-party tools will render them irreversibly corrupted.
In addition to file encryption, the attackers have exfiltrated confidential and personal data from the network. The note states that the victim will receive decryption software upon payment of the ransom, but if they refuse, the stolen data will be leaked or sold. Victims are given the opportunity to test the decryption process by sending several files to the attackers. If the ransom is not paid within 72 hours, the demand will increase.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Execution | T1569.002 | System Services: Service Execution |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| PrivilegeEscalation | T1543.003 | Create or Modify System Process: Windows Service |
| PrivilegeEscalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| PrivilegeEscalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| DefenseEvasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| CredentialAccess | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1614 | System Location Discovery |
| LateralMovement | T1091 | Replication Through Removable Media |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data indicates that MedusaLocker ransomware has been actively targeting a wide range of sectors, including Manufacturing, Healthcare, Finance, IT services, and much more, since 2019. Projections suggest that AllCiphered, a more advanced variant of MedusaLocker, will likely use enhanced evasion techniques to broaden its impact, targeting both individuals and businesses. It is expected to continue affecting major industries worldwide.
Therefore, maintaining vigilance and implementing robust cybersecurity measures are crucial to mitigating these evolving threats effectively.
Sigma Rule
title: Boot Configuration Tampering Via Bcdedit.EXE
tags:
– attack.impact
– attack.t1490 logsource:
category: process_creation product: windows
detection:
selection_img:
– Image|endswith: ‘\bcdedit.exe’
– OriginalFileName: ‘bcdedit.exe’ selection_set:
CommandLine|contains: ‘set’ selection_cli:
– CommandLine|contains|all:
– ‘bootstatuspolicy’
– ‘ignoreallfailures’
– CommandLine|contains|all:
– ‘recoveryenabled’
– ‘no’
condition: all of selection_*
fields:
– ComputerName
– User
– CommandLine falsepositives:
– Unlikely level: high
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer| Objectives: Data theft, Data Exfiltration | Target Technology: Windows OS
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “RedLine Stealer Hidden in Modified HPDxLIB Activators” is trending.
RedLine Stealer Hidden in Modified HPDxLIB Activators
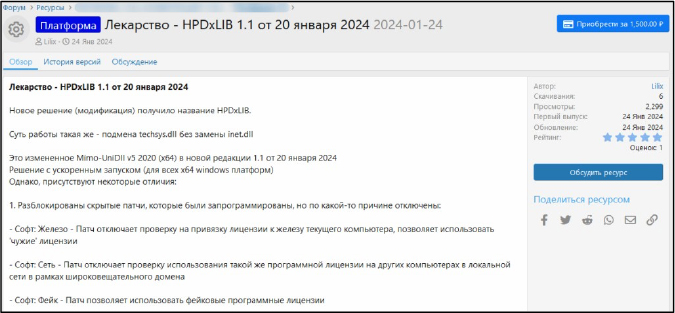
Researchers identified that attackers distributed malicious activators, targeting users of unlicensed corporate software used for automating business processes. These activators, found to be modified versions of the well-known HPDxLIB activator, contained the RedLine stealer. The malicious code was concealed using a highly sophisticated method: the activator library was obfuscated with .NET Reactor, and the malicious code was compressed and encrypted in multiple layers. This campaign, which began in January 2024, remains active and continues to pose a threat to users of unlicensed software.
Malicious Activator Distribution
The attackers target entrepreneurs using software for automating business processes by distributing a malicious version of the HPDxLIB activator. This version, disguised as an update, is developed using .NET and includes a new self-signed certificate, in contrast to the “clean” version, which is written in C++ and signed with a valid certificate. After modifying the activator, attackers distribute it via business and accounting forums, promoting the software’s ability to bypass license checks and highlight updates while omitting mention of the malicious payload.
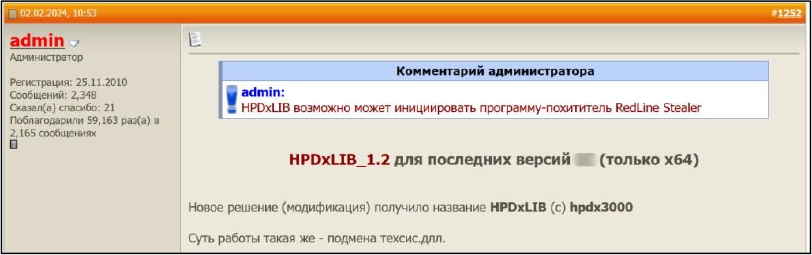
As the malware was detected by security solutions, some forums began warning users about the RedLine stealer, but the instructions still advised disabling security protections and adding the malicious files to exceptions, ensuring the activators would function.
Technical Analysis
The malicious HPDxLIB activator instructs users to replace the legitimate techsys.dll file with a version from the activator. While this method is also used by the “clean” versions, the attackers’ version leads the legitimate process (1cv8.exe) to load the malicious library, which then activates the RedLine stealer. The attackers exploit the victim’s trust rather than software vulnerabilities. Inside the malicious techsys.dll is another DLL (loader.hpdx.dll), which is heavily obfuscated and contains an encrypted RedLine payload. The payload is encrypted in multiple layers, starting with XOR encryption, followed by Base85 encoding, and further encrypted using AES-256-CBC. The RedLine stealer is unpacked using Assembly.Load().
RedLine is a malware distributed through a Malware-as-a-Service model, allowing attackers to either purchase a one-time build or subscribe for ongoing use. It specializes in exfiltrating sensitive data like browser information, instant messages, and system details. The malware communicates with a command server at 213.21.220[.]222:8080, with evidence suggesting the server is rented by different attackers, indicating the version used in this attack may have been obtained through a subscription service.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the use of malicious activators to distribute RedLine stealer suggests a growing trend in exploiting users’ trust in familiar software. As cybercriminals refine their techniques, there could be a sharp rise in attacks targeting businesses that rely on unlicensed software, with attackers increasingly using trusted forums and platforms to distribute malicious tools. This could lead to more widespread data theft, with attackers exfiltrating sensitive business information for resale or exploitation. As these threats evolve, the impact on organizations may intensify, especially if sensitive data is stolen and sold to malicious actors. The consequences could include significant reputational damage, financial losses, and even regulatory scrutiny, as companies may struggle to defend against such sophisticated, multi-layered threats. Additionally, with the use of malware-as-a- service, these attacks may become more accessible to a wider range of cybercriminals, expanding their reach and potentially increasing the frequency of incidents.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Blue Alpha Exploits Cloudflare Tunnels for GammaDrop Malware Deployment
SUMMARY
A cyber-espionage campaign has been observed targeting Ukrainian entities, employing advanced evasion techniques and sophisticated malware. BLUE ALPHA, a state-sponsored threat group, associated with Russian intelligence, has been observed utilizing spear phishing campaigns to distribute malicious HTML attachments designed for data exfiltration, credential theft, and persistent network access.
Key tactics involve HTML smuggling, where JavaScript embedded in email attachments decodes and downloads compressed files containing malicious shortcuts (.lnk). These shortcuts execute a payload using mshta.exe to deploy a malware variant named GammaDrop. GammaDrop acts as a loader, embedding and executing GammaLoad, a custom backdoor. The malware establishes persistence by modifying registry keys and monitors for security processes to evade detection. GammaDrop also stages additional malware and opens decoy documents to mimic legitimate activity.
GammaLoad, delivered via VBScript, continuously communicates with command- and-control (C2) servers. It uses DNS and DNS-over-HTTPS (DoH) for C2 resolution, enhancing its resilience against blocking techniques. Fast-flux DNS is employed to dynamically update C2 IP addresses, ensuring operational continuity.
Communication includes device-specific metadata, such as hostnames and hardware details. The group has demonstrated operational security lapses by exposing unprotected IP addresses during malware staging.
A novel aspect of this campaign is the abuse of legitimate tunneling services to obscure staging infrastructure. By leveraging free tools, the attackers create subdomains that route traffic through encrypted tunnels, bypassing traditional network security measures. These techniques hinder detection and allow the deployment of malicious payloads while concealing their infrastructure.
Relevancy & Insights:
The threat actor has a history of targeting the Ukrainian government and military entities, consistently employing spear phishing and custom malware for espionage and persistent access. Previous campaigns used tools like Pterodo and GammaSteel, with traditional C2 infrastructure and basic obfuscation techniques.
In the current incident, the group has evolved its methods by using HTML smuggling for malware delivery and abusing legitimate tunneling services to evade detection. This shift complicates attribution and mitigation. They continue to use fast-flux DNS for resilient C2 operations, now enhanced with DNS-over-HTTPS (DoH) to bypass monitoring.
Despite operational advancements, occasional security lapses, such as exposed IPs, provide insights into their infrastructure. This attack demonstrates a continuation and refinement of their techniques, maintaining a consistent focus on high-value Ukrainian targets.
ETLM Assessment:
The threat actor, linked to Russian intelligence, targets the Ukrainian government, military, and critical infrastructure. It exploits email systems via spear phishing with HTML smuggling and abuses legitimate services like Cloudflare Tunnels for malware staging. Current tools include GammaDrop, an HTA loader, and GammaLoad, a backdoor supporting command-and-control operations. Earlier campaigns featured Pterodo and GammaSteel.
The group employs advanced evasion tactics, such as DNS-over-HTTPS and fast-flux DNS, complicating detection and blocking. They continue to evolve their techniques, focusing on stealth and resilience.
Future campaigns are likely to refine these methods, extending threats to other regions or sectors of strategic interest. Enhanced email security, endpoint monitoring, and DNS traffic analysis are critical to countering this evolving threat.
Strategic Recommendations:
Tactical Recommendations:
Email Security Enhancements:
Endpoint and Network Monitoring:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547.001 | Boot or Logon Auto start Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1027.006 | Obfuscated Files or Information: HTML Smuggling |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1568.001 | Dynamic Resolution: Fast Flux DNS |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US organizations breached by Chinese hackers
Researchers say a “large US organization with a significant presence in China” sustained a four-month-long intrusion between April and August 2024. Researchers note that the available evidence suggests that the organization was breached by a China-based actor. Aside from the fact that DLL sideloading is a widely favoured tactic among Chinese groups, the same organization was targeted in 2023 by an attacker with tentative links to the China-based Daggerfly group.
The attackers moved laterally across the organization’s network, compromising multiple computers. Some of the machines targeted were Exchange Servers, suggesting the attackers were gathering intelligence by harvesting emails. Exfiltration tools were also deployed, suggesting that targeted data was taken from the organizations.
Meanwhile, US Deputy National Security Adviser for Cyber and Emerging Technologies, Anne Neuberger, revealed in a press call that China’s Salt Typhoon hacking campaign breached at least eight US telecoms as well as telecommunications companies in dozens of other countries.
ETLM Assessment:
CYFIRMA concludes the hacking campaigns in question are intended as a Chinese espionage program focused, again, on key government officials, and key corporate IP, so that will determine which telecoms were often targeted, and how many were compromised as well. The communications of US government officials rely on these private sector systems, which is why the Chinese were able to access the communications of some senior US government and political officials. Officials from the US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI said that China’s Salt Typhoon hackers likely still have access to critical telecommunications systems in the US and that companies should focus on updating and patching all systems to minimize risk.
Big tech urges Donald Trump to ‘push harder’ against Russia and China hacks
In our recent blog concerning the return of Donald Trump to the office of the president of the United States, we note the urges of Microsoft and other big tech companies that are trying to get the president-elect to push back strongly against Russian and Chinese hacking campaigns. Trump will reportedly have the backing of businesses on the issue of cyber-criminality, with Microsoft’s president calling for a harder push against cyber-attacks from Russia, China, and Iran amid a wave of state-sponsored hacks – a sentiment echoed by many other big tech businesses that constitute key drivers of the US economy. While Trump is not known for listening to the whims of big tech, should there be stock market ramifications following a cyber- incident, the administration is very likely to react strongly.
ETLM Assessment:
A second Trump presidency would likely bring heightened focus on cybersecurity, with particular emphasis on countering threats from China. Building on the bipartisan recognition of cybersecurity’s importance, Trump’s administration could implement policies to strengthen critical infrastructure defenses, encourage private-sector collaboration, and amplify responses to state-sponsored cyberattacks. Likely prioritization of trade protectionism and economic decoupling from China would also increase the urgency of safeguarding intellectual property and critical networks, making cybersecurity a cornerstone of both national security and economic policy.
This approach could face challenges, however, including the potential for an increased number of cyber-attacks from key adversaries like China, Iran, and North Korea. While businesses may benefit from incentives to bolster defenses, they will also bear increased expectations to protect against relentless cyber threats, and, as
cyber espionage grows in scope and sophistication, the Trump administration’s handling of these threats will play a pivotal role in shaping U.S. resilience in an increasingly contested digital landscape.
The Play Ransomware Impacts ITO EN, Ltd
Summary
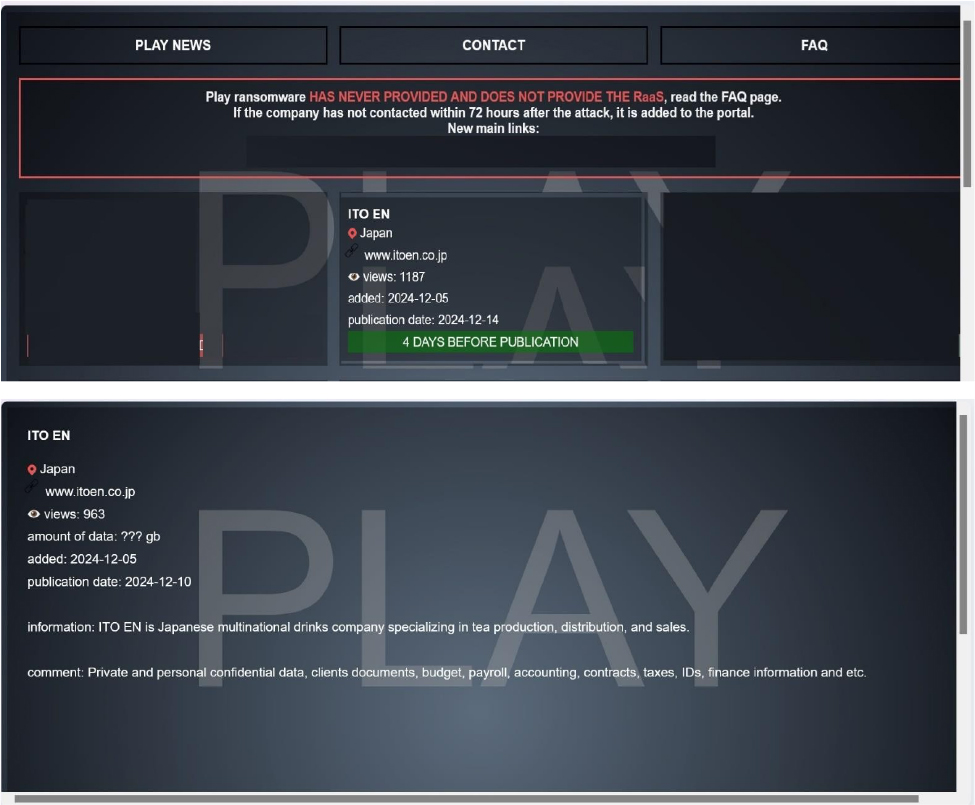
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; ITO EN, Ltd (www[.]itoen[.]co[.]jp), was compromised by Play Ransomware. ITO EN, Ltd. is a leading Japanese beverage company known for its tea-based products, including the popular “Oi Ocha” brand. The company operates from its headquarters in Tokyo and manages various domestic and international production facilities. Its product lineup includes green tea, black tea, herbal infusions, coffee, mineral water, and health-focused beverages. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data contains Private and personal confidential data, clients’ documents, budget, payroll, accounting, contracts, taxes, IDs, finance information, etc.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Play Ransomware continues to evolve as a significant threat within the cybersecurity landscape, marked by its innovative tactics and recent collaborations with other threat actors. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this evolving threat actor. Continuous vigilance is essential as ransomware groups adapt their strategies and expand their operations.
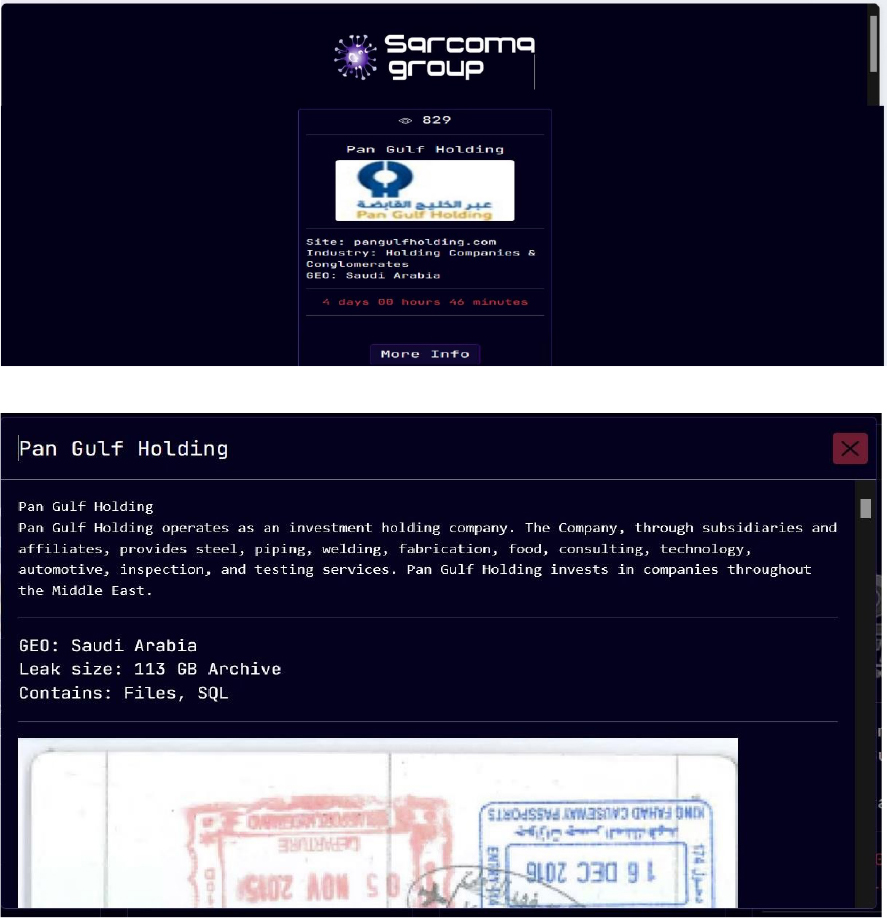
The Sarcoma Ransomware Impacts Pan Gulf Holding
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia; Pan Gulf Holding (www[.]pangulfholding[.]com), was compromised by Sarcoma Ransomware. Pan Gulf Holding is a diversified conglomerate based in Saudi Arabia, with business operations spanning multiple sectors, including Industrial Manufacturing, Steel Fabrication, Valves Manufacturing, Oil & Gas Services, Food Processing, and Investment Services. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data consists of confidential and sensitive information related to the organization, stored in SQL format, with a total size of approximately 113 GB.
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Sarcoma ransomware is rapidly becoming a significant threat due to its aggressive tactics and increasing victim count. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate risks associated with this evolving threat landscape.
Vulnerability in Python
Relevancy & Insights: The vulnerability exists because the application does not properly control the consumption of internal resources in asyncio. SelectorSocketTransport.writelines().
Impact: A remote attacker can trigger resource exhaustion and perform a denial of service (DoS) attack.
Affected Products: https[:]//www[.]openwall[.]com/lists/oss-security/2024/12/06/1
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
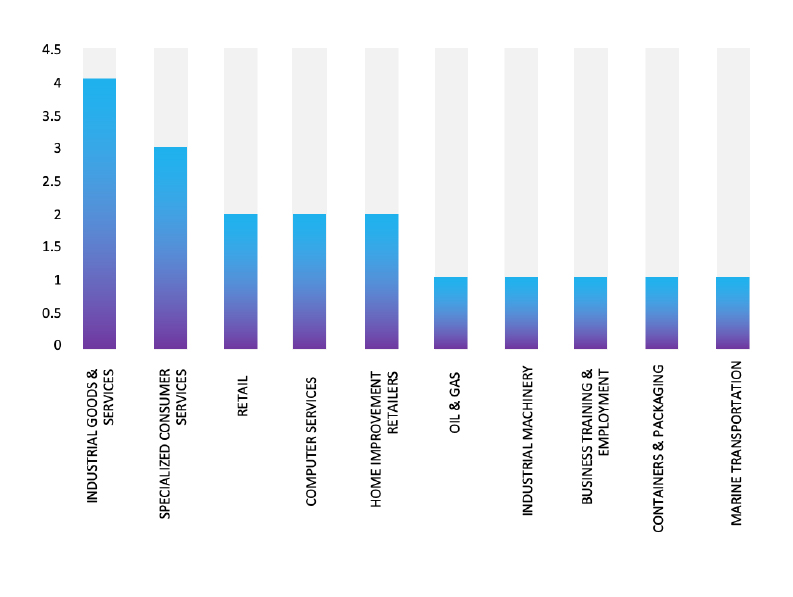
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
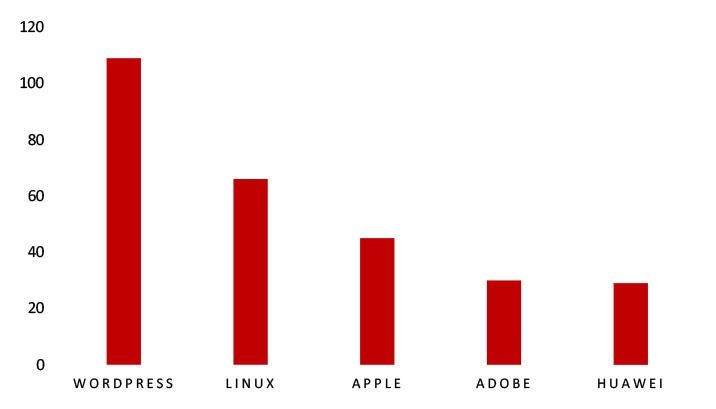
ETLM Assessment
Vulnerability in Python can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Python is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding software development and application functionality across different geographic regions and sectors, while leveraging its code readability and versatile programming capabilities.
Killsec Ransomware Attacked and Published the Data of Delux Holdings (M) Sdn. Bhd.
Summary
Recently, we observed that Killsec Ransomware attacked and published the data Delux Holdings (M) Sdn. (www[.]mydelux[.]com[.]my) on its dark web website. Delux Holdings (M) Sdn. Bhd. is a premier manufacturer and distributor of high-quality auto gates, security doors, and digital locks throughout Malaysia. The company is renowned for its innovative products, including the first fully aluminium trackless folding auto gate and advanced security doors featuring 14 locks and a fast-lock system. Delux has expanded its business internationally to countries such as Singapore, Brunei, India, Indonesia, and Thailand. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database.

Relevancy & Insights:
ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
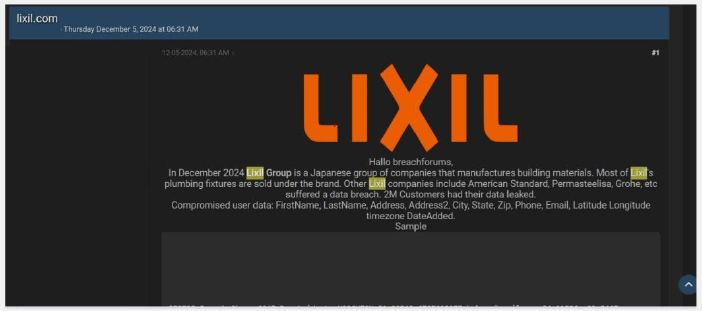
LIXIL Data Advertised on a Leak Site
Summary:
LIXIL, a leading Japanese company specializing in manufacturing housing and building materials, has experienced a data breach. The incident is said to have resulted in the exposure of sensitive customer information, including names, contact details, and other personal identifiers. This breach raises significant concerns about user privacy and security practices within the building and construction industry.
The incident highlights the importance of implementing robust cybersecurity measures to protect customer data from unauthorized access. Affected individuals are advised to monitor their accounts for suspicious activity and be cautious of potential phishing attempts. LIXIL has not yet issued an official statement addressing the breach or the steps being taken to enhance data security. The data breach has been linked to a threat actor known as “Metadata.”
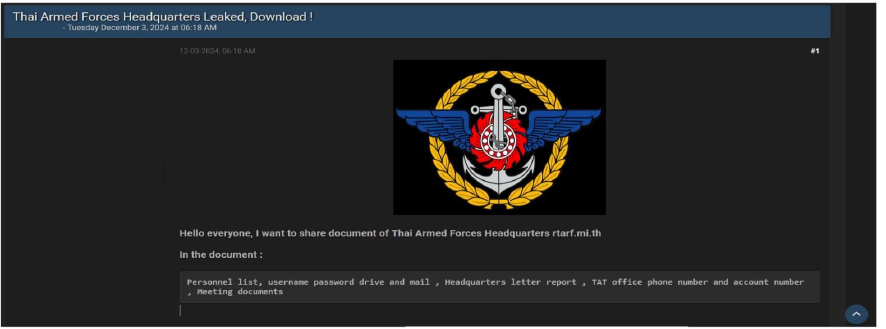
Thai Armed Forces Data Advertised on a Leak Site
Summary:
A major security breach involving the Thai Armed Forces Headquarters has surfaced on a dark web forum. The reported leak includes highly sensitive documents, such as internal communications, strategic plans, and personnel records. This incident poses significant risks to Thailand’s national security and raises serious concerns about the protection of confidential military operations. The data breach has been linked to a threat actor known as “Saltedegg.”
Relevancy & Insights:
ETLM Assessment:
The threat actor “SaltedEgg” poses a serious risk within the cybercrime landscape due to its 888advanced tactics. Organizations should strengthen their cybersecurity defenses by implementing robust anti-phishing measures, keeping security protocols up to date, and actively monitoring network activity for suspicious behavior. Gaining insight into the tactics used by SaltedEgg and similar adversaries is essential for reducing risks and enhancing overall cybersecurity resilience.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed a data leak related to SalonBiz in an underground forum. SalonBiz is technology-driven salon management software that increases productivity, automates operations and creates a personalized guest experience. The data breach affected 23,867 customers, resulting in the exposure of sensitive personal information, including First Name, Last Name, Email Address, and Phone Number. The breach has been linked to a threat actor identified as “888.”

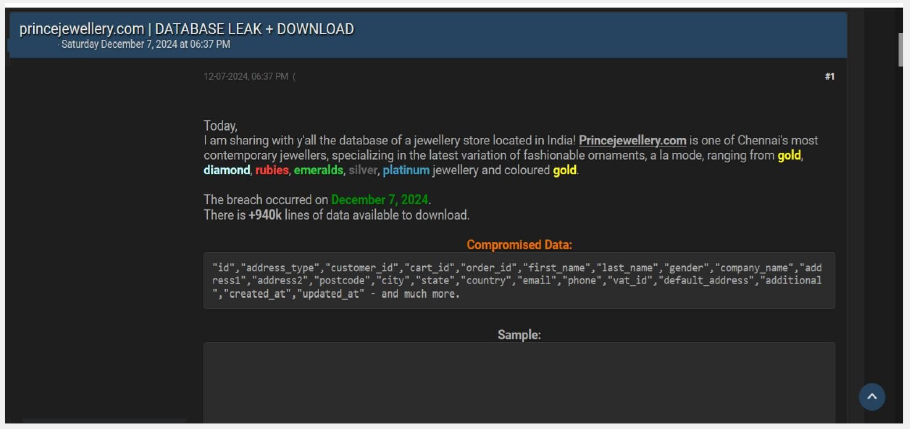
The CYFIRMA Research team observed a data leak related to Prince jewellery (www[.]princejewellery[.]com) in an underground forum. Prince jewellery store located in India is one of Chennai’s most contemporary jewellers, specializing in the latest variation of fashionable ornaments, a la mode, ranging from gold, diamond, rubies, emeralds, silver, platinum jewellery, and coloured gold. The leaked data includes ID, customer ID, cart ID, order ID, first name, last name, gender, company name, address, postcode, city, state, country, email, phone number, VAT ID, and additional sensitive information. The breach is attributed to a threat actor identified as “Gwap.”
ETLM Assessment
The threat actor group “888” has gained notoriety in underground forums, emerging as a significant force in cybercrime, primarily motivated by financial gains. This group has already targeted a wide range of industries, including government, industrial conglomerates, retail, staffing, business consulting, banking, e-commerce, and utilities. Their diverse targeting patterns suggest that they plan to broaden their scope and potentially expand their attacks to additional industries worldwide in the future.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
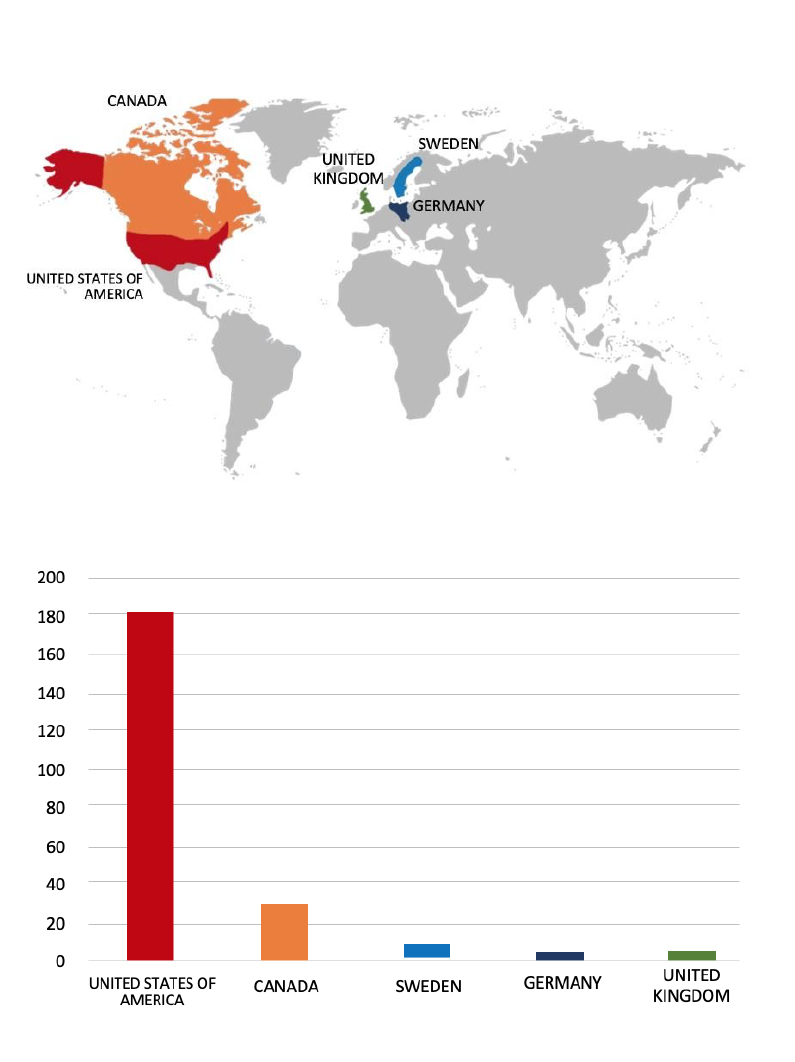
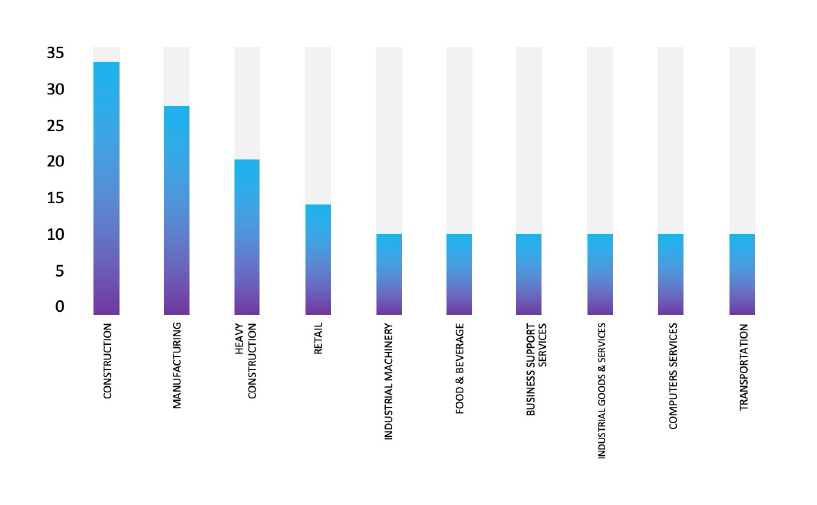
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.