



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
Target Industries: Accounting Services, Advertising & Marketing, Automotive, Business Services, Construction, Education, Energy, E-Commerce, Finance, FMCG, Furniture, Food and beverages, Healthcare, Hospitality, Insurance, Industrial Machinery & Equipment, Law Firms & Legal Services, Real Estate, Retail, Manufacturing, Telecommunication and Transportation.
Target Geography: Australia, Belgium, Canada, China, France, Germany, India, Indonesia, Italy, Luxembourg, Mexico, Netherlands, Peru, Poland, Philippines, Spain, Switzerland, the United Kingdom, United Arab Emirates, and the United States of America.
Introduction
CYFIRMA Research and Advisory Team has found 8base ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
8base:
The 8Base ransomware group has been active since 2022, but it experienced a notable surge in its activity in June 2023.
The group describe themselves as “simple pen testers”. Also, they established a leak site where they disclose victim details.
In the initial variant of 8base, after encryption, the ransomware appends the victim’s ID, [email protected] email address, and the “.8base” extension to filenames.

Screenshot of a Files Encrypted by 8Base Ransomware. (Source: Surface Web)
Recent Observations of 8Base Ransomware.
Researchers found that 8base ransomware is distributed by SmokeLoader variants. The ransomware may also rely on other distribution methods.
After execution, the ransomware scans for files to encrypt, excluding those whose filenames contain specific strings.
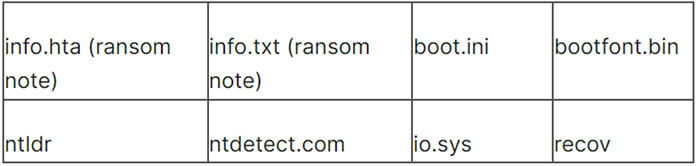
Ransomware skips the following folders:
Ransomware tries to kill the following processes before encrypting files:
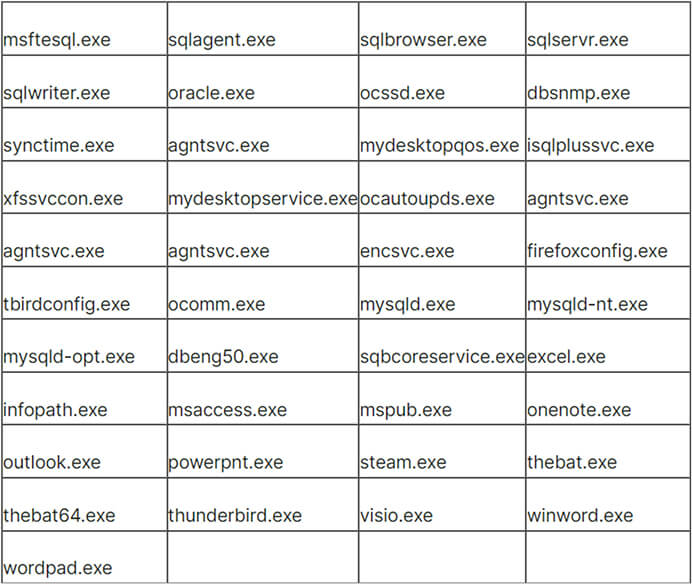
Terminating these processes guarantees the closure of any files open within them, including MS Office files, enabling the ransomware to proceed with encryption.
The 8base ransomware employs a file size threshold of 1.5MB, fully encrypting files below this size and partially encrypting larger files, likely to speedup the encryption process.
Competition among ransomware developers often centers around encryption speed to compromise as many files as possible before detection. Ransomware achieves this by injecting blocks of null bytes and encrypting specific portions of the file, strategically leaving some sections unencrypted.
The early variants of 8base were written in .NET while in recent observation researchers found the variants written in C.
The latest variant of 8base ransomware follows a similar pattern of excluding specific files and folders from encryption. However, notable differences include an extended ransom note, featuring a contact email address and a TOR data leak site address that was not present in previous versions. Additionally, a new file extension is appended to the encrypted files, that include “.id[unique ID].[recovery8files@(removed).org].8base.”
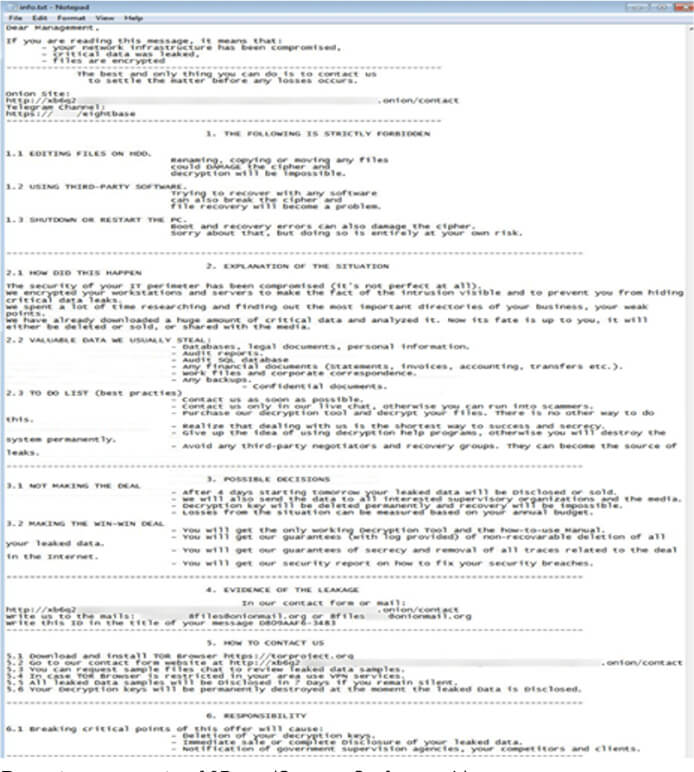
Recent ransom note of 8Base (Source: Surface web)
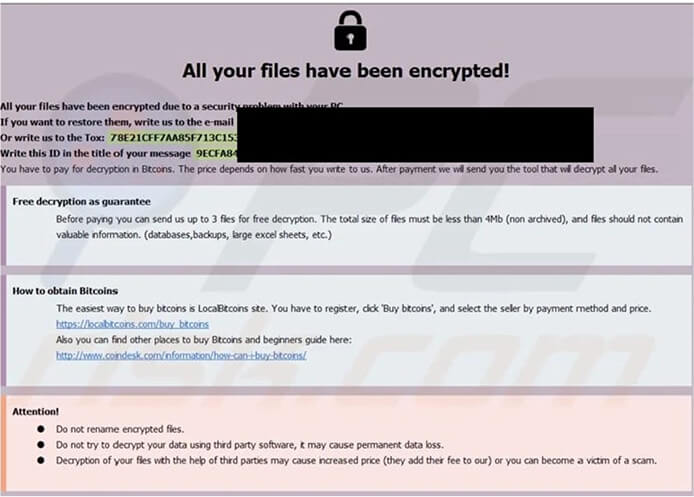
Initial Ransomnote of 8Base (Source: Surface web)
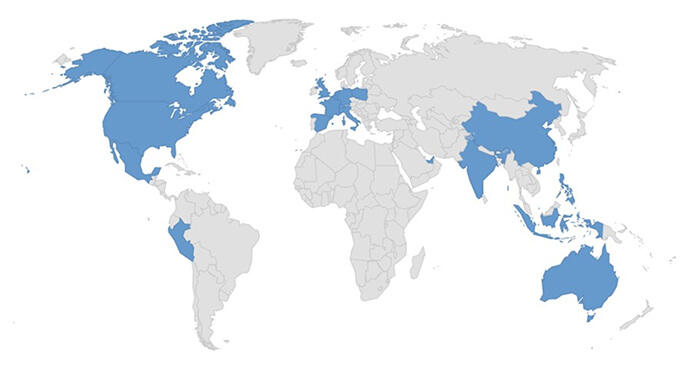
Countries Targeted by 8Base.
Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job |
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1055: Process Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.002: Obfuscated Files or Information: Software Packing | ||
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1056: Input Capture |
| T1005: Data from Local System | ||
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
ETLM Assessment:
Based on CYFIRMA’s assessment, the 8Base ransomware is likely to continue evolving. Future variants may employ more sophisticated encryption techniques, expand target industries globally, and enhance evasion strategies. Anticipate increased focus on high- profile targets, with refined persistence mechanisms. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
Sigma Rule
title: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: RAT (Remote Access Trojan)
Objective: Espionage, Remote Access
Threat Actor: UAC-0050
Target Technology: Windows OS
Target Geography: Ukraine Target Sector: Government
Active Malware of the Week
This week “RemcosRAT” is trending.
Summary
The UAC-0050 threat group, known for persistent cyber-attacks on Ukrainian targets, has employed a new advanced strategy. Researchers found that this approach enables a covert data transfer channel, effectively bypassing detection measures used by Endpoint Detection and Response (EDR) and antivirus systems. The UAC-0050 group employs RemcosRAT, a well-known remote surveillance and control malware, as its primary tool. In a recent development, they have advanced their tactics by integrating a pipe method for interprocess communication within the Windows operating system.
UAC-0050
Since 2020, the UAC-0050 group has been active, employing social engineering campaigns to target Ukrainian and Polish entities. These campaigns involve impersonating legitimate organizations to deceive recipients into opening malicious attachments. The group’s recent focus on targeting the Ukrainian government indicates a politically motivated campaign with potential geopolitical implications. Their use of RemcosRAT and innovative pipe methods for data movement underscores their emphasis on stealth and intelligence gathering. Although the speculation of state sponsorship exists, the group’s activities pose a clear risk, particularly to government sectors heavily dependent on Windows systems.
RemcosRAT
RemcosRAT is a remote access Trojan designed for unauthorized control and surveillance of compromised systems. It infiltrates computers, takes control, and extracts sensitive data. Introduced in 2016 by BreakingSecurity, a European company, it was initially marketed as a legitimate remote-control tool. Despite claims of restricted access for lawful purposes, RemcosRAT has since been widely utilized in malicious campaigns by threat actors, spreading through attachments, drive-by downloads, or social engineering tactics.
Attack Method
In December 2023, researchers discovered a .lnk file exposing UAC-0050’s use of RemcosRAT in a targeted cyber intelligence operation against Ukrainian government agencies. The initial attack vector remains unidentified, but evidence suggests phishing or spam emails posing as job offers, specifically targeting Ukrainian military personnel for consultancy positions with the Israel Defense Forces (IDF).
The LNK file initiates the download of an HTA file, containing a VBS script that activates a PowerShell script. The PowerShell script aims to download a malicious payload (word_update.exe) from a server. Upon execution, word_update.exe runs cmd.exe and shares malicious data through a pipe, ultimately leading to the launch of explorer.exe with the RemcosRAT residing in its memory.
Technical Analysis
Researchers initiated their analysis with a .lnk file, a Windows shortcut commonly exploited by cybercriminals to execute malicious software. The malicious .lnk file in question collects information about installed antivirus products on the target computer, specifically checking for the display name ‘Windows Defender’. If a match is found, the file replaces the term with an empty string, causing the condition within the ‘if’ statement to be false. This prevents the execution of the ‘exit’ statement, allowing the script to seamlessly proceed with any subsequent code. At the end of the .lnk file, the threat actor obfuscated the URL string, which, upon deobfuscation, is executed using MSHTA with the following code:
Researchers analyzed the retrieved 6.hta file, finding it contains a VBScript with fully obfuscated script content. After successfully deobfuscating the VBScript, a PowerShell script was obtained. The following PowerShell script represents the deobfuscated sequence:
The result of the deobfuscation ($hQkGkZK) produced an additional PowerShell script containing encoded data.
Researchers captured suspicious PowerShell activities, providing de-obfuscated content. The payloads, word_update.exe and ofer.docx, are downloaded from the domain new-tech- savvy[.]com. These payload files (Doc,exe) are then deposited in the root of the roaming folder (%appdata%).
Payloads
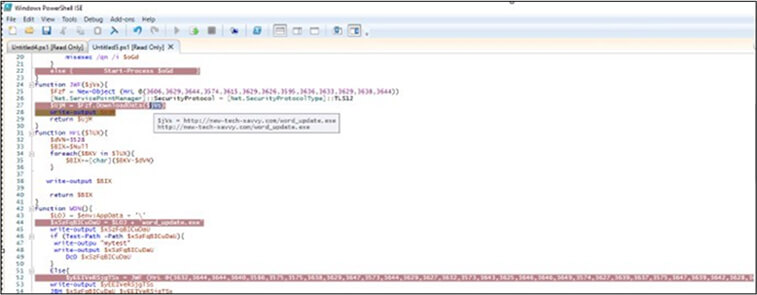
Fig: Downloading executable payload
The process begins with a request to download word_update.exe. Upon execution, word_update.exe creates a self-copy file named fmTask_dbg.exe in a new folder within the roaming directory (%appdata%). To establish persistence, an LNK file is generated in the startup folder, ensuring the execution of fmTask_dbg.exe during each boot. The file fmTask_dbg.exe contains unusual resource data, undergoes decryption through XOR operations, and transfers content to memory. Following this, the WriteFile API function is invoked, pointing to an unnamed file (\filesystem\npfs) for the first level of decryption.
To evade detection by EDR/AV systems, the attackers leverage pipes instead of conventional techniques like process injection. The malicious actor spawns a legitimate child process, cmd.exe, and cleverly transfers decrypted data from word_update.exe to cmd.exe using the WriteFile API and an unnamed pipe handle. The data in cmd.exe’s memory is decrypted during runtime, triggering the execution of the RemcosRAT. Subsequently, the process launches Explorer, moving the malicious data into its memory.
Remcos Binary
The analysis reveals the extraction of the RemcosRAT payload from cmd.exe memory. The payload’s Resource section includes an encrypted RCDATA, decrypted using CyberChef, unveiling the RemcosRAT configuration file.
Configuration:
The identified version is Remcos 4.9.2 Pro, collecting victim information like computer name and username. RemcosRAT takes preventive measures by removing cookies and login data from Internet Explorer, Firefox, and Chrome, hindering the recording of malware entries on victim machines. The RAT configures registry values related to the executable path, license, and thread time.
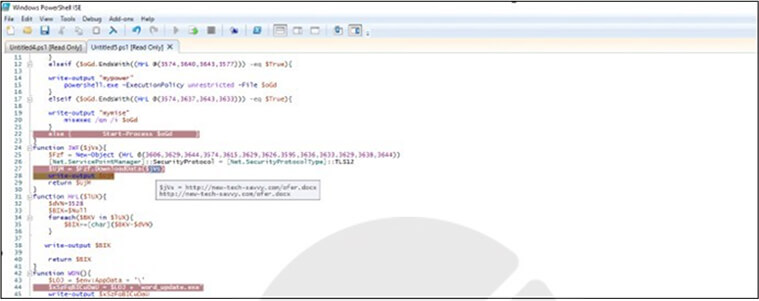
Fig: Downloading document payload
A request for downloading ofer.docx is made, and upon completion, it is executed using winword.exe. This file lacks macros but displays a defensive message from a consultant to the Israel Defense Forces (IDF). Initially, no instances of word_update.exe were detected by VirusTotal.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that organizations heavily reliant on Windows operating systems, especially government sectors with geopolitical significance, should be particularly vigilant in the face of emerging cyber threats exemplified by UAC-0050’s use of RemcosRAT. As threat actors continually refine their tactics, these entities become prime targets for espionage and data exfiltration. Additionally, businesses across various sectors should anticipate an increased risk of sophisticated attacks, necessitating investments in advanced threat detection and employee training to fortify their cybersecurity posture.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Sea Turtle Resurfaces: Cyber Espionage Campaigns Targeting the Netherlands and Kurdish Entities
Summary:
In a recent cybersecurity disclosure, it has come to light that a cyberespionage group, suspected to have affiliations with the Turkish government and increasingly involved in politically motivated cyber operations, has been conducting campaigns targeting both the Netherlands and Kurdish entities. Identified as Sea Turtle, this Turkey-based Advanced Persistent Threat (APT) group has engaged in espionage, focusing on information theft and targeting both public and private entities. Notably recognized for DNS hijacking from 2017 to 2019, Sea Turtle has adapted its capabilities to evade detection. The group’s activities have been revealed to align with strategic Turkish interests, as disclosed by Microsoft and the Greek National CERT.
Sea Turtle focuses on European and Middle Eastern organizations, with a primary emphasis on governmental bodies, Kurdish political groups like the PKK, NGOs, telecommunication entities, ISPs, IT service providers, and Media and entertainment organizations. Their targets include repositories holding valuable and sensitive data, particularly in the telecommunications sector where customer information is stored. The group’s method of working involves intercepting internet traffic directed at victimized websites and providing unauthorized access to government networks and organizational systems.
In recent campaigns, initial access is achieved by using compromised cPanel accounts to SSH onto the target infrastructure. Sea Turtle infiltrated an organization’s cPanel Web hosting environment through a VPN connection, deploying an information- gathering Linux reverse shell known as “SnappyTCP.” The tool remains active on the system to function as a persistent backdoor even when the threat actors have logged out, utilizing the POSIX command and preventing its termination. The group adeptly utilized this tool, featuring code tailored for unauthorized remote access to Linux or Unix systems. This access facilitated the execution of commands, data exfiltration, and the compromise of system security. Sea Turtle established a command-and-control (C&C) channel over TCP using HTTP, associated with the domain forward.boord[.]info and port 443. Subsequently, the group utilized a database management tool within the cPanel environment to compromise accounts and exfiltrate an email archive.
Relevancy & Insights:
Sea Turtle employs sophisticated tactics, such as a reverse shell mechanism, to streamline their data collection and extraction efforts for surveillance and intelligence activities. Their strategic use of supply chain infiltration involves targeting initial victims with the ultimate aim of accessing more high-profile or secure entities. This aligns with the 2020 Turkish-affiliated hacker groups focusing on identities and locations in geopolitically significant countries. Sea Turtle’s utilization of defensive evasion techniques, interception of internet traffic, and unauthorized access to government networks indicate an intensified pursuit of objectives, particularly within the Netherlands. Their focus spans telecommunications, media, ISPs, and IT services organizations, with a notable emphasis on targeting Kurdish websites, including those affiliated with The Kurdistan Workers’ Party (PKK).
ETLM Assessment:
CYFIRMA’s team assessment attributes Sea Turtle’s success in espionage campaigns to its advanced tactics, utilizing tools like the SnappyTCP reverse shell mechanism and employing strategic supply chain infiltration. By targeting various sectors, including telecommunications, media, ISPs, and IT services, the group secures access to valuable data. Geopolitically, Sea Turtle’s focus on telecom companies and Kurdish websites in the Netherlands aligns with Turkey’s interests. The group’s covert capabilities are evident in their use of defensive evasion techniques, interception of internet traffic, and unauthorized access to government networks. Despite takedown efforts, Sea Turtle displays adaptability and persistence in maintaining its espionage operations.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers were in Kyivstar’s networks for months
Ukraine’s SBU cybersecurity department, has told media that the Sandworm element of Russia’s GRU had gained access to telecom provider Kyivstar’s networks at least as long ago as May of 2023. It’s likely that Sandworm started attempting to penetrate Kyivstar as early as March of that year. Its objective was data collection, mostly on specific Kyivstar service users. Data destruction and service interruption were implemented in the latter phases of the operation. Although Solntsepyok; a purported hacktivist group, took credit for the attack, it is quite likely that Solntsepyok is a GRU front.
The effects of the attack on Kyivstar were severe and widespread, but mostly affected civilian users as opposed to military operations – the Ukrainian military doesn’t make much tactical use of civilian telecoms. However individual soldiers did use the network which might have been a great source for intelligence collection. According to the SBU, this attack is a big message and a big warning not only to Ukraine, but for the whole Western world to understand that no one is actually untouchable. Kyivstar is a large, wealthy, private company, a subsidiary of the Netherlands multinational VEON, and it was by no means a soft target. Kyivstar was known for its extensive investment in cybersecurity, but it was successfully attacked nonetheless.
ETLM Assessment:
Kyivstar network destruction is a tactical success but a strategic failure for Russia. To have such access and incredible collection opportunity for months and then destroy it all one day for no tangible gain but bragging rights is a show of myopia, where the intelligence agencies were probably under pressure to present “results”, which shows a large degree of political meddling in intelligence work, a recurring theme in the Russian war against Ukraine.
The Office of the Director of National Intelligence report on election interference
The Office of the Director of National Intelligence declassified a report regarding attempted foreign meddling in the US midterm elections of 2022. The report’s main conclusions were that Iran and Russia intended to sow widespread mistrust in U.S. electoral processes, that China tacitly approved of interference in a small number of races involving both Democrats and Republicans with positions hostile to China, and that U.S. intelligence agencies had not detected any attempts to gain access to or tamper with voting infrastructure at the federal, state, or local levels. The study is released at a time when there are many factors posing a threat to the 2024 global election cycle, which will be the biggest until 2048. These factors include the possibility of new, potent generative AI tools being used in disinformation campaigns, as well as the distraction of major tech companies from growing revenues and the U.S. election cycle.
ETLM Assessment:
Russia has inherited the rich Soviet legacy of information operations and put it to early use by pioneering instrumentalization of social media for large-scale high-efficiency influence operations around the globe. Other authoritarian regimes like China and Iran are quickly catching up on the game as they simultaneously turn the screws on domestic digital repression. Russia and China are also exporting digital authoritarianism packages to the third world, while getting increasingly sophisticated in sowing discontent in other countries through the use of generative AI in information operations. Cyfirma will release a full report on the topic this Friday.
Iranian Hackers Targeting Albania
The recent wave of cyber-attacks targeting Albanian organizations involved the use of a wiper called No-Justice. According to researchers, this malware crashes the operating system in such a way that it cannot be rebooted. An Iranian group known as Homeland Justice, which has been active since July 2022, has claimed responsibility for the attacks. The group has resurfaced after a hiatus, referencing the Albanian city of Durrës, which currently hosts Iranian dissident group; People’s Mojahedin Organization of Iran (MEK). The attacks included targeting of telecom operators like ONE Albania, Eagle Mobile Albania, Air Albania and the Albanian parliament.
Two of the primary tools deployed during the campaign include an executable wiper and a PowerShell script that’s designed to propagate the former to other machines in the target network after enabling Windows Remote Management (WinRM).
ETLM Assessment:
Albania, a member of NATO, was a victim of malign cyber activity at first in July 2022. The attackers were the same group; “HomeLand Justice”, most probably sponsored and / or directed from Iran, were probably reacting to a planned and later cancelled conference held in Tirana – the capital of Albania. The conference was supposed to be attended by members of Mujahedeen-e-Khalq (MEK); an opposition Iranian group, advocating the overthrow of the Iranian government and dismantling of the ruling regime.
Albania in an answer expelled Iranian diplomats and embassy staff to leave within 24 hours on 7th September. Albania is therefore the first known state ever severing ties with a country over a cyber-attack. After the attack, Albania strengthened its relations with MEK, which further strained relations with Iran and is likely to lead to further attacks.
The Play Ransomware impacts Televerde
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]televerde[.]com), was compromised by Play Ransomware. Televerde is an American multinational sales and marketing organization located in Phoenix, Arizona. The company partners with organizations such as SAP, Adobe-Marketo, GE, Micro Focus, and Interstate Batteries. The compromised data includes private and confidential information such as client documents, budget details, identification records (IDs), payroll information, insurance data, tax records, financial information, and other sensitive data.
The following screenshot was observed published on the dark web:
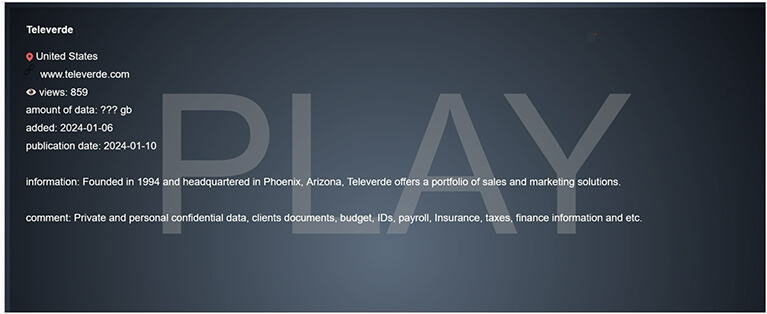
Source: Dark Web
Relevancy & Insights:
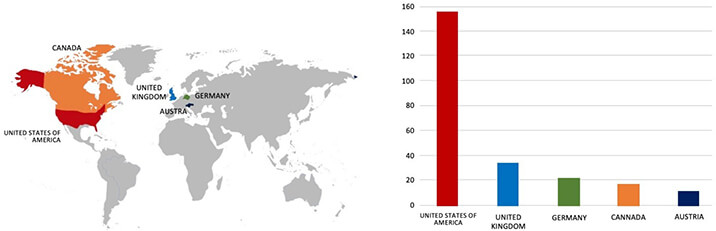
ETLM Assessment:
Our observation indicates that Play Ransomware is now being offered as a service to cybercriminals. CYFIRMA’s assessment remains unchanged: we predict ongoing targeting of US-based companies by the Play ransomware, as depicted in the accompanying graph. However, recent incidents such as the Televerde attack highlight that even other prominent Advertising & Marketing corporations are not exempt from potential targeting.
Vulnerability in GTKWave
Summary:
Impact:
A remote attacker can pass a specially crafted .vcd file to the application, trigger an out-of-bounds write, and execute arbitrary code on the target system.
Affected Products: https[:]//talosintelligence[.]com/vulnerability_reports/TALOS-2023-1805
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
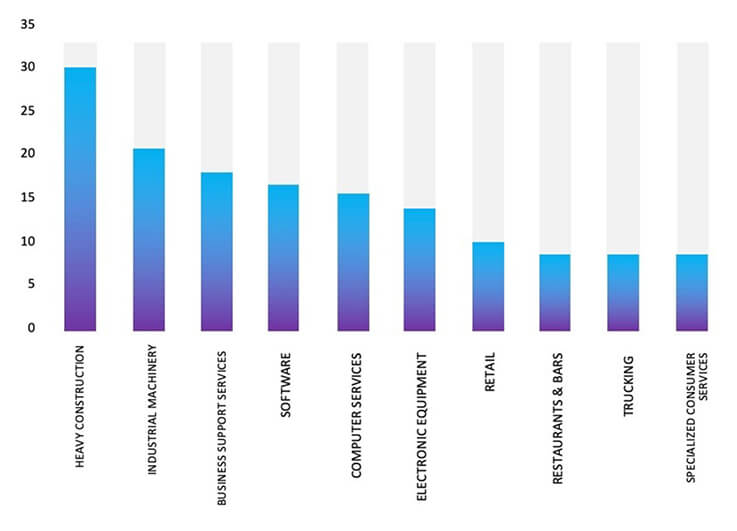
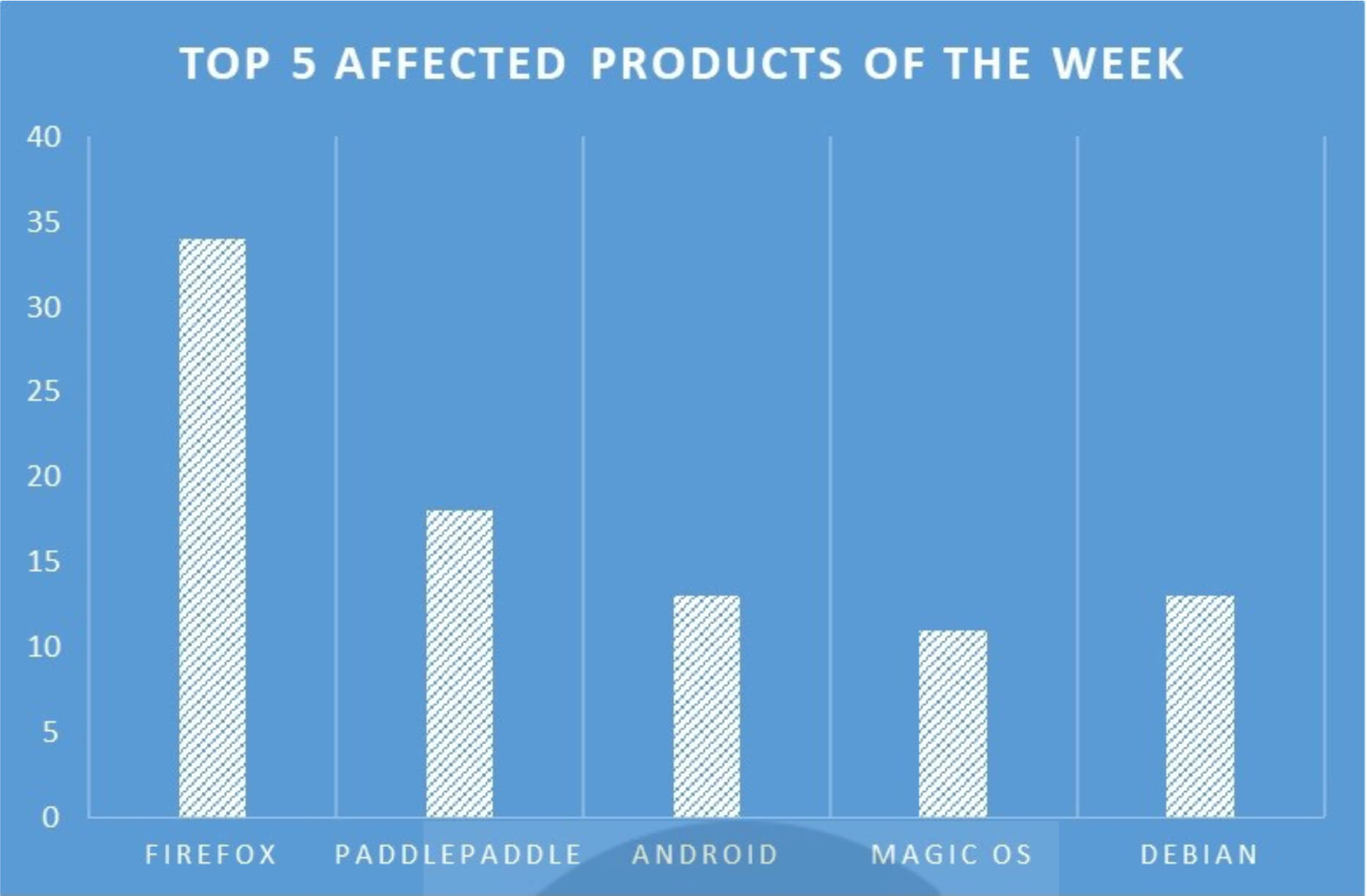
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
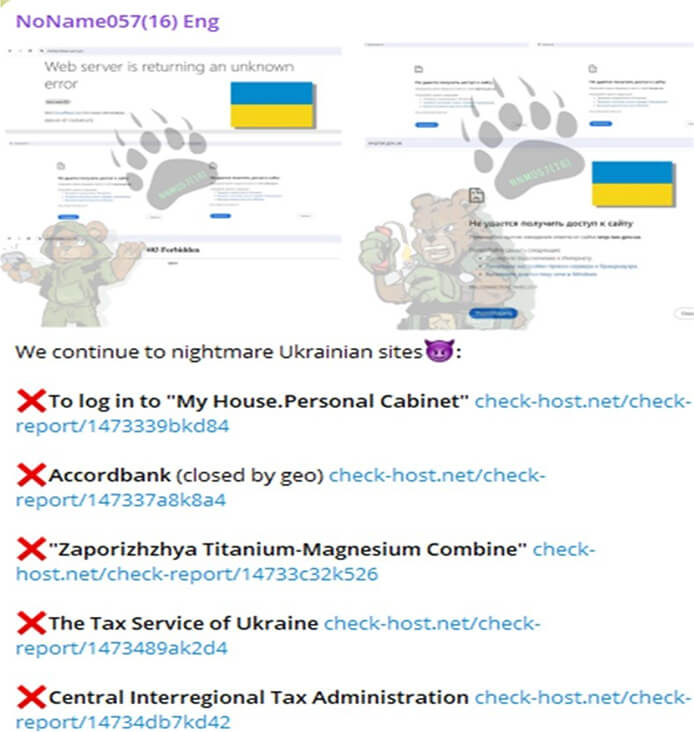
Noname057(16) on Rampage! Claims DDoS Attacks on Ukrainian Government Sites
Summary:
We recently observed that the Noname057(16) hacktivist group has allegedly targeted multiple Ukrainian government websites. The latest victims of the alleged Noname057(16) attack on Ukraine include Accordbank, Zaporizhzhya Titanium- Magnesium Plant, State Tax Service, Central Interregional Tax Administration, Western Interregional Tax Administration, and the Main Directorate of the State Tax Service in Kyiv. The Noname057(16) group has posted a list of their latest DDoS attack victims on their dark web leak portal. Screenshots of the dark web post were shared on Twitter. The websites for Ukraine’s State Tax Service, Central Interregional Tax Administration, Western Interregional Tax Administration, and the Main Directorate of the State Tax Service, displayed bad gateway and error messages on each of the websites.
Relevancy & Insights:
NoName057(16) has reportedly been carrying out Distributed Denial of Service (DDoS) attacks on websites associated with various entities, including governments, news agencies, armies, suppliers, telecommunications companies, transportation authorities, and financial institutions in Ukraine and neighbouring countries that are supportive of Ukraine. Among the recent incidents, it targeted four Polish entities: the Marshal’s Office, Polish Radio, ePUAP, and the Senate.
ETLM Assessment:
NoName057(16) is identified as a pro-Russian hacker group with a focus on targeting NATO and its affiliated entities. The ongoing campaign strongly suggests that the threat actors aim to bolster Russia in its conflict with Ukraine. According to CYFIRMA’s assessment, it is anticipated that the threat actor NoName057(16) will persist in conducting Distributed Denial of Service (DDoS) attacks on Ukrainian organizations, aiming for reputational harm and operational disruptions.
Capstone Financial Group Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential selling of web-shell access related to Capstone Financial Group, {www[.]capfg[.]com}. Capstone Financial Group is a boutique investment bank supporting Automotive Aftermarket and auto-tech companies. They provide buy-side, sell-side, growth funding, and valuation M&A services. The seller is offering web-shell access for $100.

Source: Underground forums
ETLM Assessment:
A threat actor identified as Ddarknotevil is asserting to sell unauthorized web shell access, with the purported sale being promoted on a dark forum. The ongoing campaign strongly indicates that the threat actor is engaging in this activity for financial motives. CYFIRMA assesses that organizations in the USA lacking proper security measures are potential targets for this threat actor.
CYFIRMA Research team observed a potential data leak related to MAKRUZZ, {www[.]makruzz[.]com}. Makruzz is an elite Cruise Company located in Andaman & Nicobar Islands, India. The data for sale encompasses a customer list featuring a diverse range, including affluent businessmen, middle-class individuals, and details of Indian Government servants. Notably, it also includes information about individuals who utilized the service during the G20 summit in India in September 2023. The comprehensive dataset amounts to 17 gigabytes in size.
Furthermore, the seller is offering an additional package, which includes not only the 17 GB of data but also the credentials for all associated bank accounts, each maintaining a minimum balance of 2-3 million. This bundled package is available for
$150. Alternatively, the standalone 17 GB data package is priced at $100.
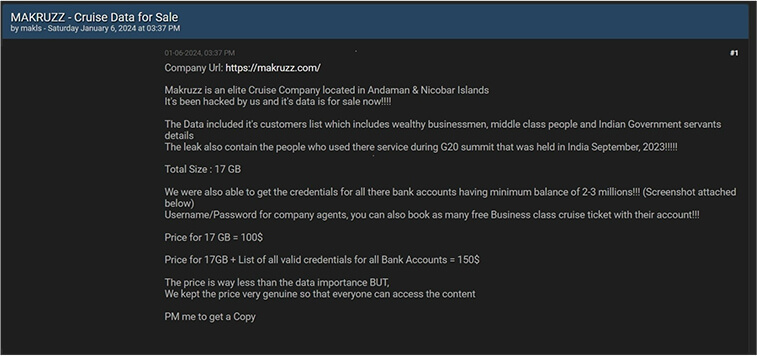
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS