



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found RSA-4096 ransomware while monitoring various underground forums as part of our Threat Discovery Process.
RSA-4096 ransomware
A new strain of ransomware, dubbed RSA-4096, has been uncovered by researchers. The ransomware is seen in the wild by March 2024. The malicious software encrypts data on infected systems and demands payment from victims in exchange for decryption. RSA-4096 belongs to the Xorist ransomware family, known for its sophisticated encryption techniques and extortion tactics.
Files encrypted by the RSA-4096 ransomware have been identified with a distinct “.RSA- 4096” extension appended to their original filenames.
Encryption employed a unique RSA-4096 public key generated.
Following the completion of the encryption process, the ransomware deposited a text file named “HOW TO DECRYPT FILES.txt,” containing instructions for the victim on how to retrieve their encrypted data.
The ransom note issued by the criminals demands a huge ransom payment in Bitcoin within 48 hours. The threat actors also state that failure to comply within the specified timeframe results in permanently deleting all files belonging to the victim.
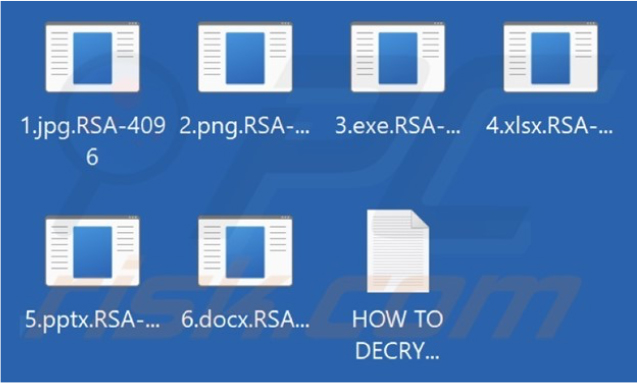
Screenshot of files encrypted by RSA-4096 ransomware (Source: Surface Web)
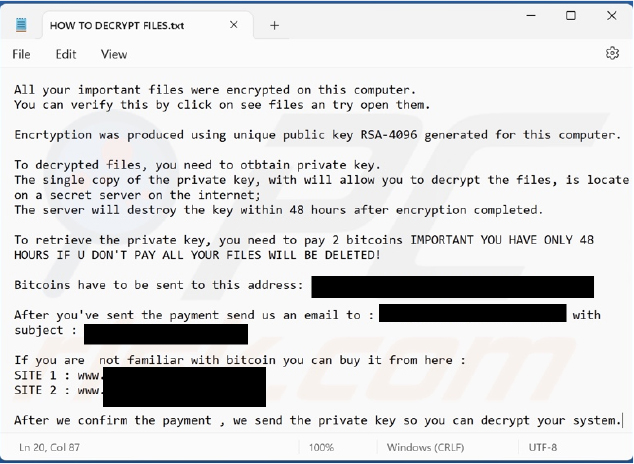
Screenshot of Ransomnote (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/ Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| 2 | TA0003: Persistence | T1547.004: Boot or Logon Autostart Execution: Winlogon Helper DLL |
| 3 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1547.004: Boot or Logon Autostart Execution: Winlogon Helper DLL |
||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.001: Indicator Removal: Clear Windows Event Logs | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1070.006: Indicator Removal: Timestomp | ||
| T1112: Modify Registry | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1056: Input Capture |
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1518.001:Software Discovery: Security Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1056: Input Capture |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Sigma Rule
title: Wow6432Node CurrentVersion Autorun Keys Modification tags:
– attack.persistence
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: selection_wow_current_version_base:
Target Object | contains : ‘\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion’
selection_wow_current_version_keys: TargetObject|contains:
– ‘\ShellServiceObjectDelayLoad’
– ‘\Run\’
– ‘\RunOnce\’
– ‘\RunOnceEx\’
– ‘\RunServices\’
– ‘\RunServicesOnce\’
– ‘\Explorer\ShellServiceObjects’
– ‘\Explorer\ShellIconOverlayIdentifiers’
– ‘\Explorer\ShellExecuteHooks’
– ‘\Explorer\SharedTaskScheduler’
– ‘\Explorer\Browser Helper Objects’ filter_empty:
Details: ‘(Empty)’ filter_edge:
Image|contains|all:
– ‘C:\Program Files (x86)\Microsoft\EdgeUpdate\Install\{‘
– ‘\setup.exe’ filter_msoffice1:
Image: ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe’
Target Object | contains : ‘\Office\ClickToRun\REGISTRY\MACHINE\Software\Wow6432Node\’
filter_msoffice2: Image:
– ‘C:\Program Files\Microsoft Office\root\integration\integrator.exe’
– ‘C:\Program Files (x86)\Microsoft Office\root\integration\integrator.exe’ TargetObject|contains: ‘\Explorer\Browser Helper Objects\{31D09BA0-12F5-4CCE-
BE8A-2923E76605DA}\’
filter_dropbox:
– Details|endswith: ‘-A251-47B7-93E1-CDD82E34AF8B}’
– Details: ‘grpconv -o’
– Details|contains|all:
– ‘C:\Program Files’
– ‘\Dropbox\Client\Dropbox.exe’
– ‘ /systemstartup’ filter_evernote:
TargetObject|endswith: ‘\Explorer\Browser Helper Objects\{92EF2EAD-A7CE-4424- B0DB-499CF856608E}\NoExplorer’
filter_dotnet:
Image|contains: ‘\windowsdesktop-runtime-‘ TargetObject|endswith:
– ‘\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce\{e2d1ae32-dd1d- 4ad7-a298-10e42e7840fc}’
– ‘\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce\{7037b699-7382- 448c-89a7-4765961d2537}’
Details|startswith: ‘”C:\ProgramData\Package Cache\’ Details|endswith: ‘.exe” /burn.runonce’
filter_office:
Image|startswith:
– ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\’
– ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\Updates\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_ms_win_desktop_runtime:
Details|startswith: ‘”C:\ProgramData\Package Cache\{d21a4f20-968a-4b0c-bf04- a38da5f06e41}\windowsdesktop-runtime-‘
filter_vcredist:
Image|endswith: ‘\VC_redist.x64.exe’ Details|endswith: ‘}\VC_redist.x64.exe” /burn.runonce’
filter_upgrades: Image|startswith:
– ‘C:\ProgramData\Package Cache’
– ‘C:\Windows\Temp\’ Image|contains:
– ‘\winsdksetup.exe’
– ‘\windowsdesktop-runtime-‘ # C:\WINDOWS\Temp\{751E2E78-46DC-4376-9205- 99219CDC34AE}\.be\windowsdesktop-runtime-6.0.12-win-x86.exe
– ‘\AspNetCoreSharedFrameworkBundle-‘ # “C:\ProgramData\Package Cache\{b52191c1-a9c0-4b34-9a4e-930c2dd8a540}\AspNetCoreSharedFrameworkBundle- x86.exe” /burn.runonce
Details|endswith: ‘ /burn.runonce’ filter_uninstallers:
# This image path is linked with different uninstallers when running as admin unfortunately
Image|startswith: ‘C:\Windows\Installer\MSI’ TargetObject|contains: ‘\Explorer\Browser Helper Objects’
filter_msiexec:
Image: ‘C:\WINDOWS\system32\msiexec.exe’
Target Object | contains : ‘\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\’
condition: all of selection_wow_current_version_* and not 1 of filter_* fields:
– SecurityID
– ObjectName
– OldValueType
– NewValueType falsepositives:
– Legitimate software automatically (mostly, during installation) sets up autorun keys for legitimate reason.
– Legitimate administrator sets up autorun keys for legitimate reason level: medium.
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Espionage, Data theft, Remote Access
Target Organization: Finance
Target Geography: Asia–Pacific (APAC) and Middle East and North Africa (MENA)
Active Malware of the Week
This week “JsOutProx” is trending.
JsOutProx
Researchers have identified a new variant of JSOutProx, a sophisticated JScript-based Remote Access Trojan (RAT) that combines JavaScript and .NET technologies. This version specifically targets financial institutions and organizations in the APAC and MENA regions. JSOutProx utilizes .NET (de)serialization to communicate with a JavaScript module on the victim’s system. Once activated, the malware enables the framework to install plugins, which carry out further malicious operations on the compromised system. The recent campaigns abuse GitHub and GitLab for distributing malicious payloads, reflecting the actors’ evolving tactics.
Malicious Activity Timeline: Transition from GitHub to GitLab
Technical Analysis
The JSOutProx RAT malware is characterized by sophisticated obfuscation within its JavaScript-based backdoor structure. It includes a modular plugin architecture that allows it to perform various malicious activities, such as executing shell commands, managing file uploads and downloads, running files, modifying the file system, maintaining persistence, capturing screenshots and controlling keyboard and mouse actions. Notably, this malware utilizes the Cookie header field in its command and control (C2) communications. The implants were downloaded and extracted from their archives. Subsequently, they underwent obfuscation using obfuscator[.]io. After deobfuscation, the JavaScript code was successfully decoded for analysis.
First stage implant supports the following commands:
The script utilizes Windows Script Host (WSH) objects like ActiveXObject for malicious purposes, performing operations such as HTTP requests with WinHttp.WinHttpRequest.5.1, executing commands via WScript.Shell, and accessing the file system with Scripting.FileSystemObject. Additionally, it employs WMI to gather detailed information about the victim’s system environment. The implant uses a specific static User Agent for potential tracking purposes:
Communication with command and control (C2C) servers is facilitated using Dynamic DNS URLs, such as:
A notable feature of this malware is its utilization of the Cookie header field in C2C communication. During initialization, the malware collects various information, concatenates them with the delimiter “_|_”, hex-encodes the concatenated value, and sets it in the Cookie header field.
C2C Communications
Researchers have identified concerning details about the recent JSOutProx campaign from April 2, 2024, notably involving IP addresses (185.244.30.218) linked to the Freemesh project. Freemesh redirects to a website dedicated to a non-commercial initiative for free wireless networks. It appears that the threat actor deliberately deployed command and control (C2C) hosts within this infrastructure to exploit and conceal malicious network activity. Specifically, an IP address like 185.244.30.218 is associated with “The Privacy First Project,” a non-profit organization providing IPv4 space to various communities including Freifunk and TOR node operators, with a stated commitment to privacy and no log files. Virustotal historical data indicates extensive malicious activity associated with this IP address and multiple subdomains linked to the JsOutProx infrastructure. Researchers have engaged with the operators of these projects to understand the situation better and have successfully coordinated takedowns of multiple C2C servers to disrupt the new JsOutProx campaign.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the impact of JSOutProx and similar malware is expected to continue posing significant challenges for organizations, particularly in the financial sector. As these threats evolve and leverage platforms like GitHub and GitLab for distribution, organizations may face increased disruptions to operations, financial losses, and reputational damage from data breaches or unauthorized access. Additionally, the geographical scope and range of targets impacted by JSOutProx may expand, posing a broader threat landscape for organizations globally. To address these evolving threats, proactive and comprehensive cybersecurity strategies will be crucial to mitigate the future impact of JSOutProx and similar threats on organizational security and resilience.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Unveiling CoralRaider: The Emerging Threat Actor Targeting Asia and Southeast Asia
Summary:
CoralRaider; a financially motivated threat group originating from Vietnam, has been active since at least 2023, focusing its efforts on victimizing individuals and organizations primarily across Asia and Southeast Asia. Their main objective revolves around seeking financial gains through illicit means, particularly by engaging in data theft activities. To achieve this goal, CoralRaider employs sophisticated social engineering tactics, distributing malicious Windows shortcut files with deceptive filenames to entice unsuspecting victims into opening them. These files serve as the initial infection vector, facilitating the deployment of customized malware payloads such as RotBot and XClient stealer.
Once deployed, these malicious payloads enable CoralRaider to execute various attack techniques, including the theft of credentials, financial data, and social media accounts. RotBot; a customized variant of QuasarRAT, serves as a remote access tool, while XClient stealer, a .Net executable, exhibits extensive information-stealing capabilities targeting social media and financial data. To communicate with their infrastructure and exfiltrate stolen data, CoralRaider leverages Telegram bots as command-and-control servers, enhancing their operational efficiency and evading traditional detection mechanisms.
CoralRaider’s targets span a wide range of industries, reflecting their opportunistic approach, but they demonstrate a particular interest in sectors associated with advertising and online businesses. Their activities have significant implications for victims, including potential financial losses, reputational damage, and compromised security posture. Effective cybersecurity measures, including robust endpoint protection and threat intelligence sharing, are imperative to counter the threat posed by CoralRaider and similar malicious actors operating in the region.
Relevancy & Insights:
CoralRaider; a threat actor from Vietnam, has been active since 2023, targeting victims across Asia and Southeast Asia. Their focus on stealing financial information, login credentials, and social media profiles, including business and advertisement accounts, underscores the need for international cooperation among cybersecurity agencies and governments. The group’s use of Windows shortcut files as the initial vector in their campaign highlights the evolving tactics used by cybercriminals to target a wide range of industries and individuals in multiple countries.
ETLM Assessment:
CoralRaider; a financially motivated threat actor group originating from Vietnam, poses a significant threat to organizations and individuals across Asia and Southeast Asia specifically India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam. Their primary goal is financial gains, leading them to conduct data theft activities targeting credentials, financial data, and social media accounts. Recent indications of active promotion within the Vietnamese cybercriminal community suggest potential collaboration or support networks, amplifying CoralRaider’s capabilities. Operating across diverse industries like Construction, Real Estate, Marketing, and the Internet.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Czech Republic warns of Russia’s cyber sabotage of EU Railways
According to the Czech government, Russia has made thousands of attempts to damage the European railway system since the beginning of the invasion of Ukraine. Moscow is suspected of being behind “thousands of attempts to weaken our systems”, the transport minister said during an EU meeting in Brussels. The Russian hacking campaign includes attacks on critical infrastructure systems, including attacks on signalling equipment and the computer networks of Czech state-owned carrier, Czech Railways. In the past, the Russians have disabled ticketing systems in this way, for example, raising concerns about whether similar attacks are behind serious train accidents caused by faulty signalling equipment. Last March, the EU Cyber Security Agency (ENISA) published its first-ever report on threats to the European transport system. The report mentioned hacking attacks by pro-Russian groups against railways in Latvia, Lithuania, Romania, and Estonia. Czech Railways confirmed the government’s remark and acknowledged the growing number of attacks on its digital infrastructure.
ETLM Assessment:
Russian attempts to destabilize European energy infrastructure have been well documented but interference in transport networks has been less discussed, even though CYFIRMA analysts warned of this danger in this report last year. The Czech National Cyber and Information Security Agency (NÚKIB) has also warned of growing threats of attacks on transport targets in its report last year. The agency has been one of the strictest digital security watchdogs in Europe and was the first to issue a hawkish warning against the use of components from Chinese companies Huawei and ZTE in 5G mobile networks under construction. Russia is using the attacks both as a tool of political war against the West as well as a tactical means of delaying transports of Ukrainian grain to the world market as well as movements of Western equipment towards Ukraine both in civilian and military capacity. The incident shows the growing role of cyber in conflict even or rather especially between countries that are not formally at war and demonstrates the future of political relations, in which cyber will be a major means of the statecraft toolkit, affecting governments and businesses alike.
The Pentagon gets a cyber czar
The US Department of Defense has opened its Office of the Assistant Secretary of Defense for Cyber Policy. Upon confirmation, the new assistant defense secretary for cyber policy (aka cyber czar) Ashley Manning will oversee spending on network operations, outreach to industry, and more. The move is aligned with the recent U.S. Navy cyber strategy, according to which non-kinetic effects rather than missiles, fighter jets, and torpedoes are likely to decide the next war on the high seas. The document reflects the central idea that the next fight against a major adversary will be like no other and that the use of non-kinetic effects and defense against those effects prior to and during kinetic exchanges will likely be the deciding factor in who prevails. But the navy sees it as imperative that cyber warfare is far more than networks and cybersecurity. Cyber warfare is presented as a warfighting discipline that should be considered a core competency that is going to play a key role in modern warfare.
ETLM Assessment:
The inauguration of the “cyber czar” confirms the growing role of cyber in modern conflicts, which often do not distinguish between military and civilian infrastructure and between times of war and peace. The office intends to provide the U.S. military a more civilian-facing role in the realm of cyber policy. The new office is responsible for coordinating the Pentagon’s cyber strategies, overseeing the military’s cyber operational budget, cyber workforce development and private sector outreach, among other areas.
The US military highlights the pivotal role of non-kinetic effects and defense against such effects in future conflicts. The potential for massive cyberattacks by advanced state actors like China looms large, threatening to disrupt critical infrastructure and the internet-powered amenities that underpin modern life. US documents emphasize that cyber warfare extends far beyond networks and cybersecurity issues, yet neither governments nor businesses are adequately prepared to confront this emerging threat.
The 8Base Ransomware impacts the PT Pupuk Iskandar Muda (Pim)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]pim[.]co[.]id), was compromised by the 8Base Ransomware. PT Pupuk Iskandar Muda (Pim) is engaged in industry, trade, and services in the fields of fertilizers, petrochemicals, and other chemicals. The compromised data includes invoices, receipts, accounting documents, personal data, certificates, employment contracts, a substantial amount of confidential information, confidentiality agreements, personal files, and other sensitive documents.
The following screenshot was observed published on the dark web:
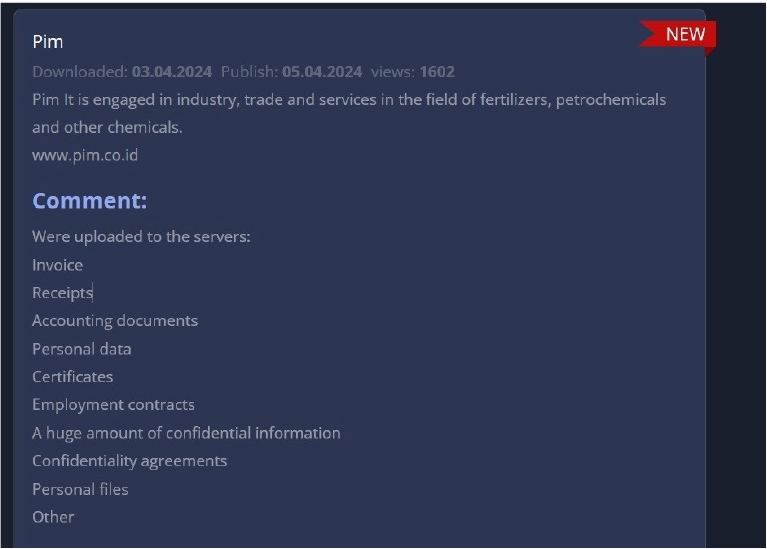
Source: Dark Web
Relevancy & Insights:
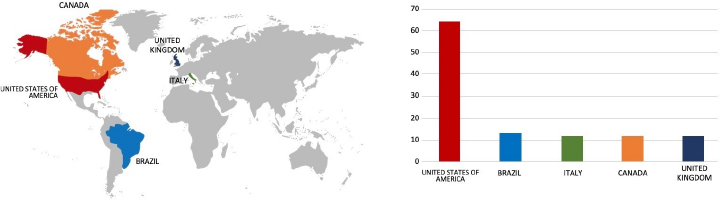
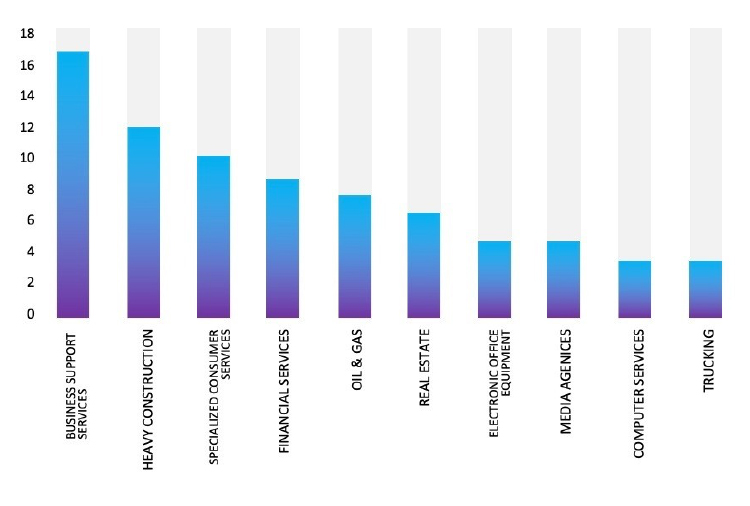
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that 8Base Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on PT Pupuk Iskandar Muda (Pim), a prominent Chemicals, Petrochemicals, Glass & Gases, and Manufacturing company located in Indonesia, underscores the extensive threat posed by this particular ransomware strain in the Southeast Asia region.
The Rhysida Ransomware impacts the Malaysian Industrial Development Finance
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; (www[.]midf[.]com[.]my), was compromised by the Rhysida Ransomware. Malaysian Industrial Development Finance (MIDF), established in 1960 and based in Kuala Lumpur, is a financial development institution to modernize Malaysia’s manufacturing industries. The Group offers financial services including, but not limited to, Investment Banking, Development Finance, Asset Management, and Mezzanine Financing. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data contains unique and valuable information. The total price for the compromised data is set at 8 BTC.
The following screenshot was observed published on the dark web:
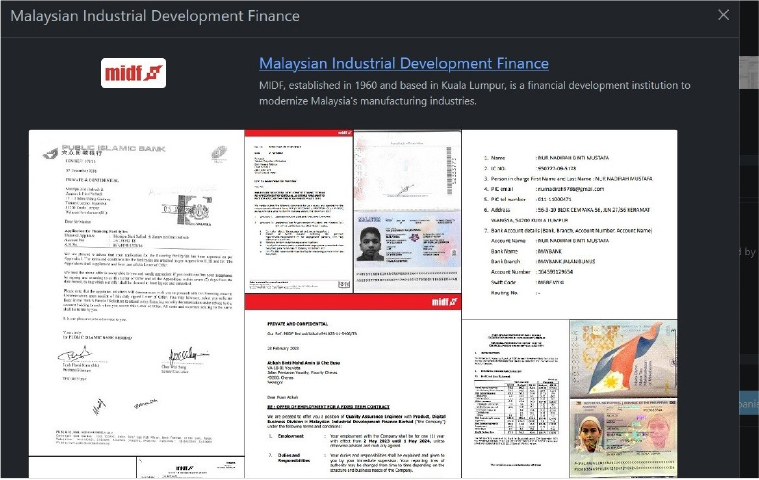
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
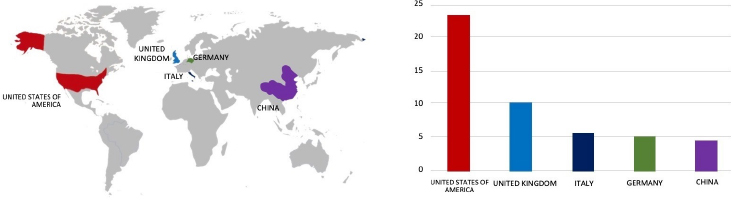
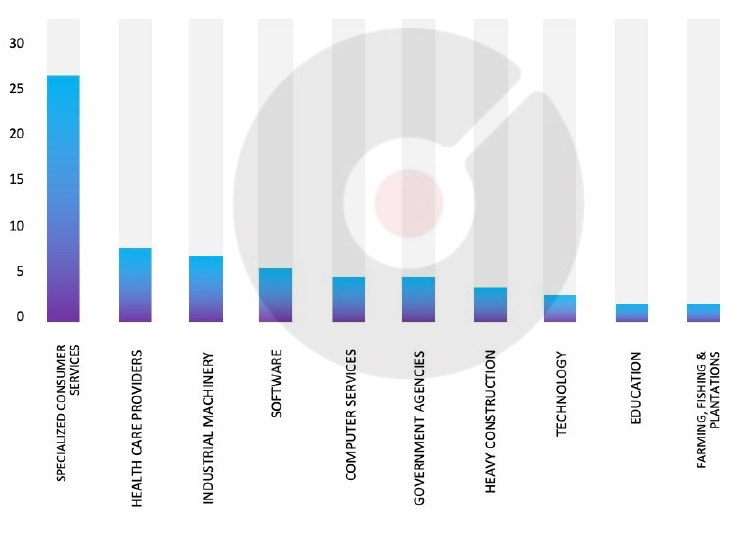
Based on CYFIRMA’s assessment, there is a persistent targeting of global companies by the Rhysida ransomware, as depicted in the accompanying graph. However, recent incidents, such as the attack on Malaysian Industrial Development Finance, highlight the susceptibility of other prominent finance entities to similar targeting. These events emphasize the dynamic nature of the threat landscape, necessitating heightened vigilance among organizations across different sectors to mitigate the risks associated with ransomware attacks. The attack on Malaysian Industrial Development Finance also highlights ransomware groups’ interest in Southeast Asian organizations that are financially strong in the region with exploitable vulnerabilities.
Vulnerability in NVIDIA ChatRTX
Summary:
The disclosed vulnerability allows a remote attacker to perform cross-site scripting (XSS) attacks.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data in the UI. A remote attacker can trick the victim into following a specially crafted link and execute arbitrary HTML and script code in the user’s browser in the context of a vulnerable website.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change the appearance of the web page, and perform phishing and drive-by-download attacks.
Affected Products: http[:]//nvidia[.]custhelp[.]com/app/answers/detail/a_id/5532
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
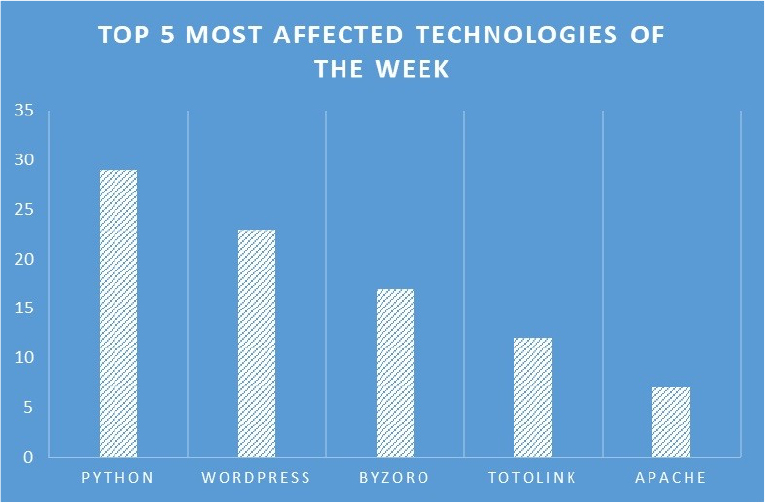
ETLM Assessment:
Given that ChatRTX is utilized by developers and AI enthusiasts for connecting PC Large Language Models (LLMs) to their data, using retrieval-augmented generation (RAG) techniques, the industries that could be affected by this vulnerability span across multiple sectors. This includes, but is not limited to, technology, cybersecurity, education, and any other industry relying on advanced AI tools and applications for development, research, or operational purposes.
Medusa Ransomware attacked and Published data of PT Bank Pembangunan Daerah Banten Tbk
Summary:
Recently we observed that Medusa Ransomware attacked and Published data of PT Bank Pembangunan Daerah Banten Tbk on its website. PT Bank Pembangunan Daerah Banten Tbk was founded in 1992, it is currently owned by the Banten Provincial government and has the status of a regional development bank. Currently, the Company serves customers of deposits, credit distribution (MSME, Consumer Credit, and Commercial Credit), and other services and has been appointed as a partner of the Provincial Government of Banten in local cash management. The total amount of data leakage is 108.47 GB and includes all customer financial information SQL Database.
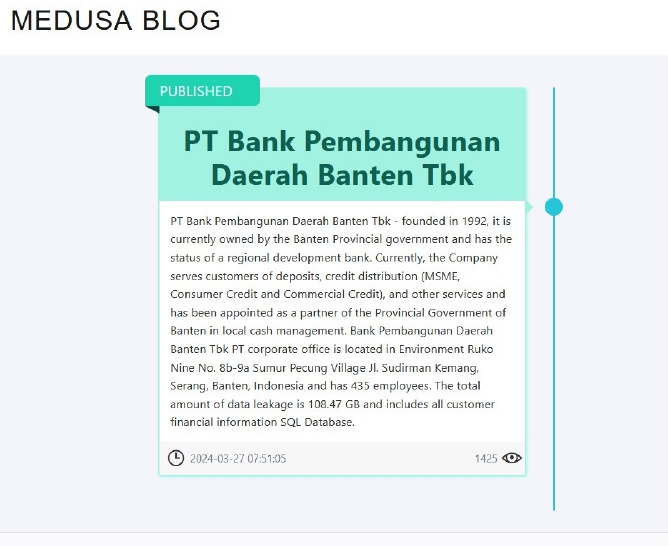
Source: Dark Web
Relevancy & Insights:
Medusa is a ransomware malware family targeting businesses and institutions. Medusa encrypts crucial data, rendering it inaccessible, and attempts to pressure users to pay to regain control of their information. One notable incident involving Medusa Ransomware took place in 2023. The group successfully infiltrated Toyota’s European division, demanding a substantial ransom of $8 million. When negotiations broke down, the attackers proceeded to release the stolen data on their dark web portal.
ETLM Assessment:
Medusa Ransomware first emerged in June 2021 and has since targeted various industries, including Information technology, Finance, education, manufacturing, healthcare, and the retail sector. In 2023 alone, it is reported to have affected over 70 organizations globally, operating under the Ransomware-as-a-Service (RaaS) business model. The cybercriminals behind Medusa Ransomware maintain a dedicated TOR website where they publish information about their victims, accompanied by a countdown clock indicating the time left before the data is released. CYFIRMA’s assessment, relying on the available information about the Medusa ransomware, suggests that the threat is poised to evolve further in sophistication. Future iterations are likely to incorporate advanced evasion tactics, heightened focus on specific sectors and regions, and potentially more intricate methods for disseminating exfiltrated data. Moreover, the ransomware’s persistence mechanisms and anti-detection measures are anticipated to undergo further refinement, presenting continuous challenges for Organizations. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
BANK SYARIAH INDONESIA(BSI) data advertised on the Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to BANK SYARIAH INDONESIA(BSI), {www[.]bankbsi[.]co[.]id}. Bank Syariah Indonesia (BSI) is a state-owned Islamic bank in Indonesia. Threat Actor Offers Unauthorized CASH MANAGEMENT SYSTEM(CMS) Account Access of Bank Syariah Indonesia. A concern about selling has emerged offering unauthorized access to an employee account of Bank Syariah Indonesia’s cash management system. The evidence shared for the accounts indicates that the respective accounts have significant processing power. Among these accounts are DPD Persagi Sulsel and RSU Vina Estetika. The actor has shared the relevant access free of charge.
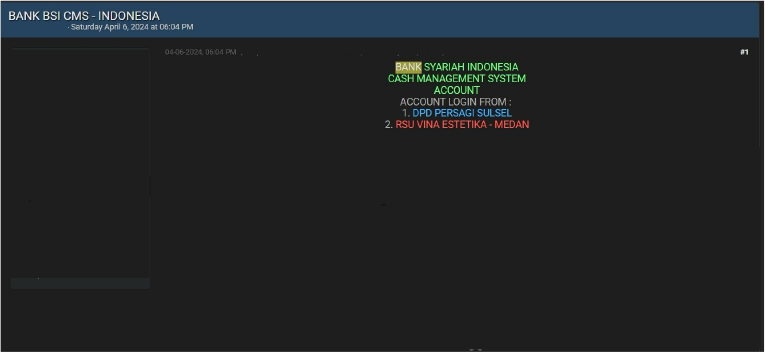
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as Sedapmalam poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by Sedapmalam typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
BADAN PEMERIKSA KEUANGAN REPUBLIK INDONESIA (BPK RI) data advertised on Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to BADAN PEMERIKSA KEUANGAN REPUBLIK INDONESIA (BPK RI), {www[.]bpk[.]gov[.]id}. BADAN PEMERIKSA KEUANGAN REPUBLIK INDONESIA (BPK RI) is a Financial Audit agency in Indonesia. The compromised data includes confidential and sensitive information crucial to the organization. The total size of the compromised data is 200 megabytes.
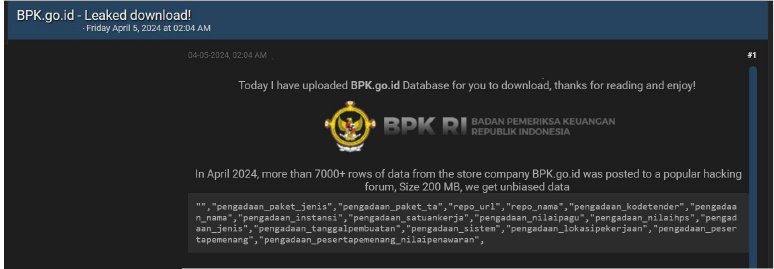
Source: Underground Forums
ETLM Assessment:
A threat actor known as “InterSystems” has surfaced with financial motives, engaging in the active leakage of data belonging to BADAN PEMERIKSA KEUANGAN REPUBLIK INDONESIA (BPK RI) in online forums. The leaked data comprises personally identifiable information (PII), financial records, and other confidential data. This poses a substantial risk to both the affected organization and individuals, underscoring the critical importance of implementing robust cybersecurity measures to protect sensitive information from such malicious activities.
CYFIRMA Research team observed a potential data leak related to the Home Depot, {www[.]homedepot[.]com}. The Home Depot, Inc. operates as a home improvement retailer. The Home Depot stores sell various building materials, home improvement products, and lawn and garden products, as well as providing installation, home maintenance, and professional service programs. The company offers installation programs that include flooring, cabinets, countertops, water heaters, and sheds; and professional installation in various categories sold through home sales programs, such as roofing, siding, windows, cabinet refacing, furnaces, and central air systems. The data breach has exposed the corporate information of 10,000 employees of the company. The compromised data includes both the full names and email addresses of these individuals. The CyberNiggers threat actor group is responsible for the data breach at The Home Depot.
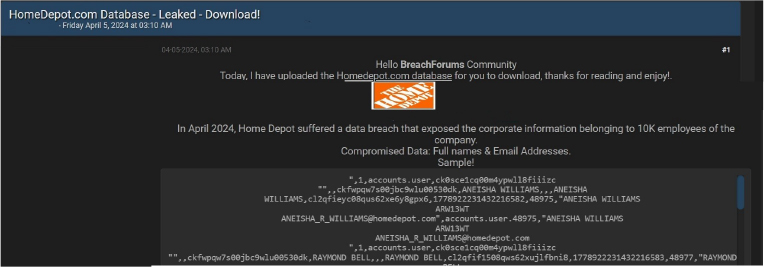
Source: Underground forums
ETLM Assessment:
CyberNiggers threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS