



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found a new DoDo ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy: This ransomware predominantly targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
DoDo ransomware:
The DoDo ransomware is believed to have possibly originated from Chaos Ransomware. A new version of the DoDo ransomware has recently emerged.
The ransomware samples bear the “Mercurial Grabber” file icon, suggesting probable distribution through this method. Mercurial Grabber is an open-source malware builder capable of generating an infostealer configured to pilfer Discord tokens, machine data, Windows product keys, and Chrome passwords from victims’ machines.
Threat actors have been actively leveraging this builder to target victims and extract information using its built-in functionalities.

File icon of the DoDo ransomware samples(Source: Surface Web)
The latest DoDo ransomware samples have been submitted to a public file scanning service from the following countries: France, Germany, India, China, the United Kingdom, and Peru. There is a possibility of victims from these geographies.
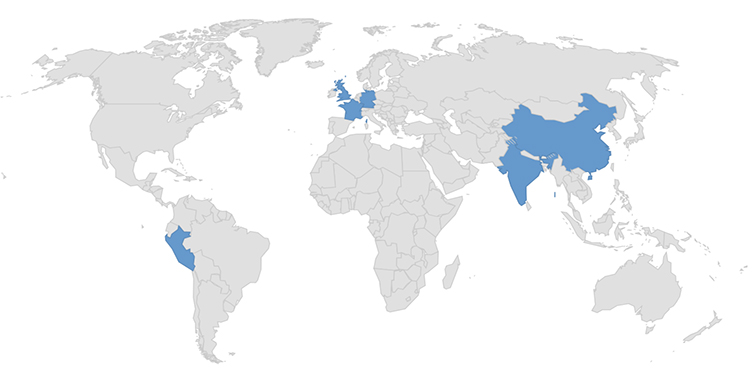
Countries that submitted new DoDo Ransomware samples.
The masquerading of free apps and tools remains a longstanding and effective tactic used by cybercriminals. In this case, the DoDo ransomware disguises itself as the Mercurial Grabber application, potentially targeting malicious attackers or curious users. The surprising abundance of submission sources suggests worldwide users have unknowingly downloaded the fake builder.
While the newer and older DoDo variants have slight differences in their ransom notes and file extensions for encrypted files, they share two common traits, all DoDo ransomware samples were created using Chaos Builder version 3, and they employ the same Bitcoin address for ransom payments. The drawback of Chaos Builder 3 is that it can only encrypt files smaller than 1 MB, rendering larger files unrecoverable unless backups are available. Consequently, for larger files, DoDo functions more like a wiper, as full file recovery becomes impossible even if the ransom is paid.
The older DoDo variants included a ransom note labelled “dodov2_readit.txt” and appended a “.dodov2” extension to encrypted files. In contrast, recent DoDo samples drop a ransom note named “PLEASEREAD.txt,” apply a “.crypterdodo” extension to encrypted files and replace the desktop wallpaper with the same ransom message. Additionally, the attacker has provided a contact email address, potentially for better “customer” service.
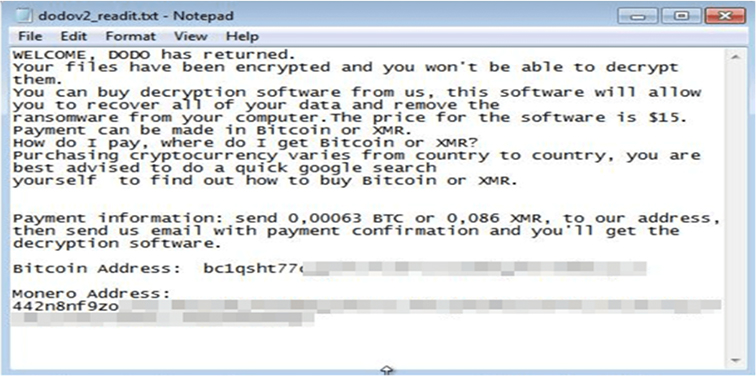
Ransom note dropped by the older DoDo ransomware variants(Source: Surface Web)
Files encrypted by the older DoDo ransomware samples. (Source: Surface Web)
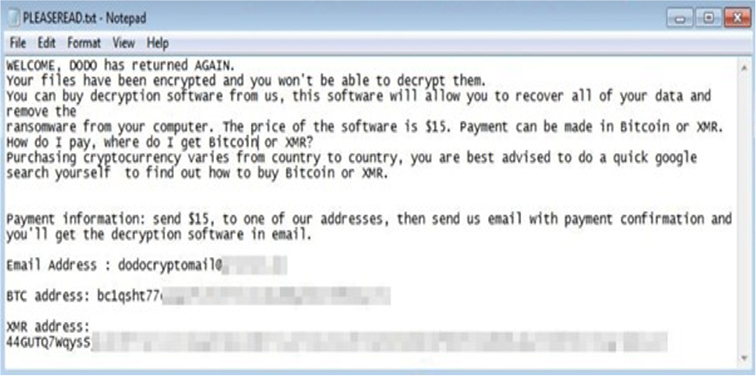
Ransom note dropped by the recent DoDo ransomware samples. (Source: Surface Web)

Files encrypted by the recent DoDo ransomware samples. (Source: Surface Web)
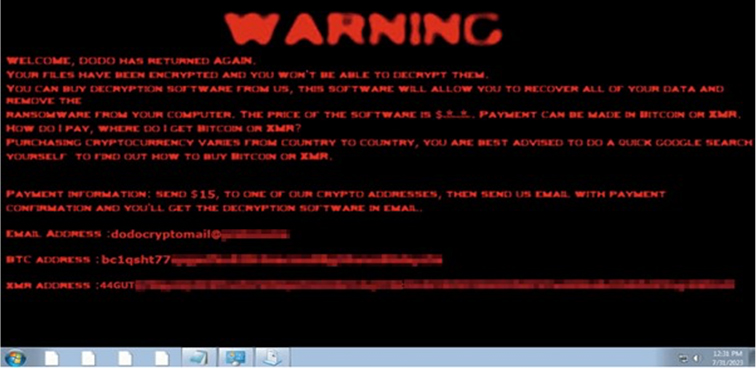
Desktop wallpaper replaced by the recent DoDo ransomware samples. (Source: Surface Web)
Insights :
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 3 | TA0004: Privilege Escalation | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| 5 | TA0007: Discovery | T1012: Query Registry |
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518: Software Discovery | ||
| 6 | TA0009: Collection | T1005: Data from Local System |
| T1115: Clipboard Data | ||
| T1119: Automated Collection | ||
| T1560: Archive Collected Data | ||
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1071.001: Application Layer Protocol: Web Protocols | ||
| 8 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery | ||
| T1491: Defacement |
Sigma Rule:
title: Drops script at startup location
logsource:
service: sysmon
product: windows
detection:
selection:
EventID: 11
TargetFilename:
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.vbs*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.js*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.jse*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.bat*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.url*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.cmd*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.hta*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.ps1*’
– ‘*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\\*.wsf*’
condition: selection
level: critical
(Source: Surface Web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Crypto-Mining Botnet
Objective: Crypto Mining
Target Technology: Linux distributions
Active Malware of the Week
This week “SkidMap” is trending.
SkidMap
Researchers recently discovered a new version of the SkidMap malware is being employed in a fresh campaign that focuses on multiple Linux distributions, such as Alibaba, Anolis, openEuler, EulerOS, Steam, CentOS, RedHat, and Rock. This latest variant of the malware stands out as a significantly enhanced and more dangerous version. Originally identified in September 2019 as a botnet for cryptocurrency mining, the malware has undergone developments, incorporating malicious kernel modules in order to avoid being detected.
Infection Process
Attack Strategy
The attack begins by trying to access an unprotected Redis instance and establishing variables with hidden cron tasks encoded in base64. The cron tasks are designed to download and execute a dropper script (‘b’) using either ‘curl’ or ‘wget’. The cron job runs every 10 minutes to ensure persistence and continued malicious activity. The name ‘HA’ suggests a potential focus on high availability clusters, a technique observed in other Redis malware campaigns.
OS Stage Infection
The dropper script (‘b’) downloaded in the Redis stage aims to infect the host operating system. The script’s main goal is to download a binary executable file (ELF) named ‘gif’ to the ‘/var/lib/’ directory. The script ensures that the backdoor file is in the correct location and matches the expected signature. If the file is incorrect, the script removes the file protection and deletes it to make space for the correct version. The malware adapts its file names, changing from ‘jpeg’ to ‘gif’ in different versions.
Encrypted Packages
After successful deployment, the ‘gif’ executable downloads encrypted packages (‘gold’, ‘stream’, ‘euler’) to a specific directory. The malware decodes these packages and initiates the execution of shell scripts, installation of kernel modules, and placement of other executable binaries. The process includes cleaning logs to cover its tracks using shell scripts. Different passwords are used to decrypt specific packages, adding a layer of complexity to the attack.
Bot Stage
The ‘bot’ ELF executable is a key component of the malware. Upon execution, the ‘bot’ downloads additional files required for the infection process. In the case of the Debian/Ubuntu variant, connections to official resources, such as Canonical, are observed for file downloads. The ‘bot’ employs a multi-layered structure, embedding various binary files within each other. Obfuscation techniques, like fixing malformed UPX headers, are used to hinder analysis. The binary files contain embedded kernel modules, including rootkits with distinct purposes.
The malware involves the deployment of various kernel modules to manipulate and control the host operating system.
Module – mcpuinfo.ko
This module is a critical component of the malware and carries out advanced functions that significantly impact the host OS. The module’s purpose is to deceive and hide the true system load by modifying the behavior of the ‘fake_loading_proc_show’ function. By displaying common and unsuspecting values, it aims to mask the activity of cryptocurrency mining (Miner activity). Some functions within the module are intended for local program use, while others are export functions accessible to other malware components.
Module – kmeminfo.ko
This module is responsible for monitoring network activity using Netfilter hooks. It employs the ‘nf_register_net_hook’ function within the Netfilter framework, which allows the malware to analyze, modify, or drop network packets. Netfilter is crucial for networking-related operations and is utilized by tools like iptables for network packet filtering and manipulation.
Kernel Module – mzoneinfo.ko (?)
There are indications of another potential module named ‘mzoneinfo.ko,’ although its corresponding binary was not found during analysis. This module could have been utilized in previous attacks and might be used in future attacks. The malware’s structure suggests that some components might not have been properly updated. It is important to note that mzoneinfo.ko isn’t a part of any official kernel module.
Miner – Debian/Ubuntu Linux Family Variant
The Miner binary is downloaded to the ‘/tmp/.miner’ directory (or ‘.mimer’ in another variant) and executed from there, spawning hidden processes. The binary’s integrity is verified using MD5 checksums at different steps to ensure it’s not tampered with. These hidden processes, spawned after the execution of the ‘gif’ binary in the ‘/var/lib’ directory, are concealed from system commands like ‘ps,’ ‘pstree,’ and ‘top.’
Miner – RedHat/CentOS Linux Family Variant
This variant avoids downloading a separate miner binary by utilizing the built-in miner from an extracted ‘gif’ binary file. In this case the ‘/tmp/.miner’ will not exist. The malware aims to remain hidden by blocking the execution of a popular forensic tool called ‘unhide,’ making detection more challenging. The malware persists in memory using a spawn-execute-remove mechanism to evade scanners and researchers. Attackers use encrypted packages, like ‘gold8,’ to deliver miners to the system. The malware persists in memory using a similar spawn-execute-remove technique for concealment and evasion.
Miner’s Networking
The specifics of the communication patterns and issues with the Miner’s networking are not fully clear in the analysis. Despite this, the miner successfully establishes a connection to a mining pool after some time following the initial infection.
INSIGHTS
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
Unknown Threat Actor Breaches into UK’s Electoral Commission System
Summary:
In a recent observation, an unknown threat actor made unauthorized access into UK’s electoral commission’s system. The UK’s Electoral Commission disclosed a complex cyber-attack that compromised the personal details of millions of British voters. However, the Commission didn’t disclose technical details and attack type. Initially detected in October 2022, the attack was traced back to server access in August 2021. Personal information was compromised from reference copies of electoral registers, utilized for research and donation checks, affecting those registered to vote in the UK between 2014 and 2022, including names, home addresses, and some overseas voters’ details. Anonymous registrations remained unaffected. The Commission confirmed that the breach wouldn’t impact election security, voter registration, or democratic processes, reducing concerns about potential interference in the upcoming 2024 UK General Election. The breach also exposed the Commission’s email system, revealing further sensitive data like email addresses, phone numbers, and personal images shared with the Commission. Although the breached information was considered low risk for individuals, the Commission adhered to UK General Data Protection Regulation, making the public notified through a notification on the 8th of August on their website. While apologizing to those affected, the Commission collaborated with security experts to investigate the attack and reinforce its systems against future breaches. At present, the culprits behind the breach remain unidentified, leaving questions about their motives and potential consequences.
Insights:
The perpetrators behind the attack remain undisclosed, and the Commission clarified that no entities or persons have asserted accountability for the breach. Although, an eventual cyberattack on the UK electoral register was expected, what raises greater concern is the fact that the breach went undetected for more than a year.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
North Korean cyberespionage against Russian aerospace industry
According to a recently published research, North Korean hackers have successfully penetrated Russian aerospace bureau; NPO Mashinostroyenia, working on rocket designs in Moscow. The news came just shortly after the Russian minister of defense; Sergey Shoigu was welcomed with a bombastic reception in Pyongyang, wherever closer cooperation of the two increasingly isolated countries has been presented to the world. North Korea is among the very few countries that is openly supporting Russia in its war against Ukraine, including deliveries of artillery shells to the Russian military.
Researchers found two instances of a North Korean compromise of the company, one being a compromise on an email server, with the second involving a Windows backdoor called “OpenCarrot,” which has been historically associated with the Lazarus Group. The hack serves as evidence of North Korean determination to advance its missile development program, even off the back of its notional ally, probably counting on Moscow considering North Korean material support too important for taking corresponding measures in return.
Older penetration of Japan’s defense networks by Chinese hackers revealed
Media have recently brought information about a major 2020 Chinese penetration of classified Japanese defense networks. According to the reports, the hackers have obtained “deep, persistent access and appeared to be after anything they could get their hands on — plans, capabilities, assessments of military shortcomings, according to three former senior U.S. officials, who were among a dozen current and former U.S. and Japanese officials interviewed, who spoke on the condition of anonymity, because of the matter’s sensitivity.” The Japanese government offered no comment on the matter but the incident complicated US-Japanese defense cooperation, especially intelligence-sharing, which has grown closer as China adopts an increasingly assertive policy in the Indo-Pacific region.
Wide-ranging cyberespionage campaign by China’s Ministry of State Security
Researchers have recently published a report on an extensive hacking campaign by RedHotel (also known as Charcoal Typhoon or Bronze University), a threat actor most likely run by China’s Ministry of State Security, that’s prospecting targets primarily not only in Southeast Asia but in other regions as well. The activity is marked by unusual scope and intensity. The group has been very active since at least 2019 and has showcased a relentless scope and scale of wider PRC state-sponsored cyber-espionage activity, by maintaining a high operational tempo and targeting public and private sector organizations globally. The group often utilizes a mix of offensive security tools, shared capabilities, and bespoke tooling. RedHotel’s operations have been recorded in more than 15 countries in Asia, Europe, and North America and its targets include academia and research, aerospace industry, government organizations, media, or telecommunications. The group has been focusing particularly on Southeast Asia’s governments and private companies in the sectors outlined above and the groups’ infrastructure for malware command-and-control, reconnaissance, and exploitation points to administration in Chengdu, China. Based on targeting trends, RedHotel likely operates with a mission of both intelligence gathering and economic espionage.
Premier BPO is Impacted by BlackCat Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]premierbpo[.]com), was compromised by BlackCat Ransomware. Premier BPO LLC provides back-office processing services to businesses. Its back-office processing services include B2B and B2C collections, billing, data entry and transcription, employee benefit processing, operational analysis and reporting. The breached data encompasses their entire customer databases, containing an alarming volume of Protected Health Information (PHI) and other confidential data. The compromised data amounts to 57.7 GB in size.
The following screenshot was observed published on the dark web:

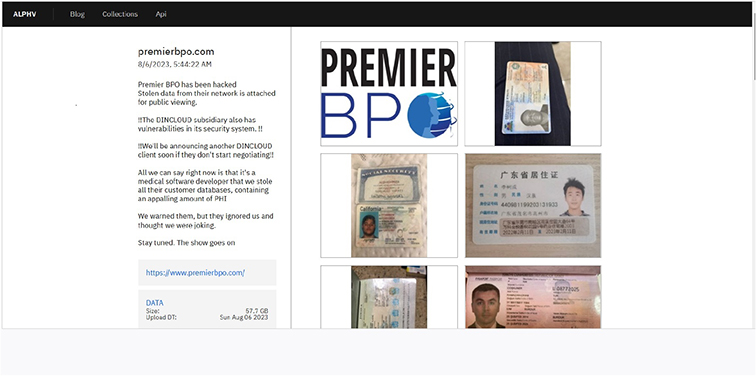
Source: Dark Web
Insights:
Having recorded 312 instances of victimization in the year 2023, the group establishes its standing as one of the most prolific ransomware collectives. Analyzing the geographical focus of their attacks it becomes evident that the group primarily targets organizations situated in the United States.
The group with financial motives, identified as FIN8, has been seen employing an updated variant of a backdoor named “Sardonic” to distribute the BlackCat ransomware.
Vulnerability in Zoom SDK
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Insights:
The vulnerability exists due to application does not properly controlling consumption of internal resources.
Impact:
A remote attacker can trigger resource exhaustion and perform a denial of service (DoS) attack.
Affected Products: https[:]//explore[.]zoom[.]us/en/trust/security/security-bulletin/#ZSB-23029
Russian Hacktivists launch DDoS attacks, causing Spanish websites to be inundated.
Summary:
The most prominent research institute in Spain has fallen victim to a recent cyber assault from Russia. This attack, which lasted for weeks, involved a DDoS campaign that seems to be driven by geopolitical motives. The DDoS barrage, affecting a minimum of 72 websites from July 19 to 30, has been attributed to the highly active hacktivist collective known as NoName057. Following Prime Minister Pedro Sanchez’s visit to Kyiv, during which he expressed his government’s backing for Ukraine, there is speculation that the attacks have impacted various sectors, including banks, telecommunications providers, media outlets, and tourism companies. The websites that fell victim to the attacks encompassed a range of targets, such as La Moncloa, which serves as the official residence of the Prime Minister, the Constitutional Court, the ministries of justice and territorial policy, as well as the Ministry of Defence agency; Isdefe.
Insights:
NoName057 is a notable hacktivist group recognized for their active engagement in various online activities. They have been linked to multiple cyber operations, often involving distributed denial-of-service (DDoS) attacks on websites and online platforms. This group’s motives are diverse and can encompass geopolitical, social, or ideological causes. Their actions have demonstrated a level of technical proficiency and coordination, allowing them to carry out impactful disruptions.
Industrial Safety’s Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Industrial Safety, {www[.]industrialsafety[.]com}. Industrial Safety are a full-service government contractor and a preferred fulfilment partner to Fortune 500 clients. The breached information includes identifiers (id), message identifiers (msgid), messages, date of occurrence (jamtgl), and other sensitive data in SQL format.

Source: Underground forums
Insights:
Constantly seeking financial gains, opportunistic cybercriminals remain vigilant for accessible and weak systems and applications. Most of these attackers participate in clandestine discussions within underground forums, where they engage in the purchase and sale of stolen digital assets. In contrast to financially motivated groups like ransomware or extortion syndicates, who often publicize their attacks, these culprits prefer discreet operations. They exploit unpatched systems or vulnerabilities in applications to infiltrate and exfiltrate valuable data. Subsequently, this stolen data is promoted for sale on underground platforms, finding its way to new owners and being repurposed in subsequent attacks by other perpetrators.
CYFIRMA Research team observed a potential data leak related to MediaMatis, {www[.]mediamatis[.]com}. MediaMatis is a company specialized in dematerialization, development, and integration of ‘business’ solutions for its clients. As a marketing agency, they design and develop applications, accessible via the Internet in ASP and SaaS. The breached information in SQL format includes identifiers (id, id_company, id_role), title, department, alternate department, first name, last name, position, email, password, telephone, mobile phone, LinkedIn, Twitter, Facebook, and other sensitive data.

Source: Underground forums
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION