



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
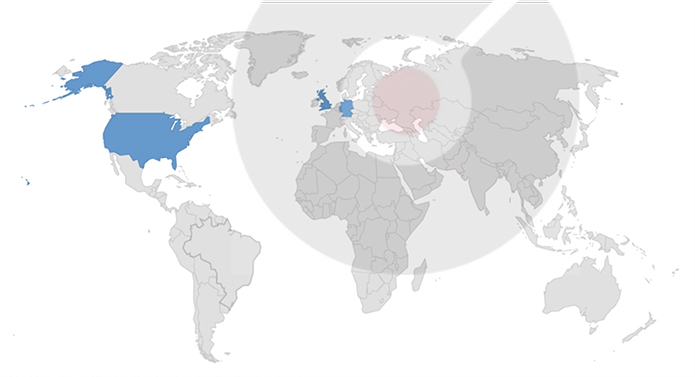
Target Geography: Germany, United States, United Kingdom.
Target Industry: Construction, Education, Pharmaceuticals, Transportation.
CYFIRMA Research and Advisory Team has found a ransomware group known as Hunters International while monitoring various underground forums as part of our Threat Discovery Process.
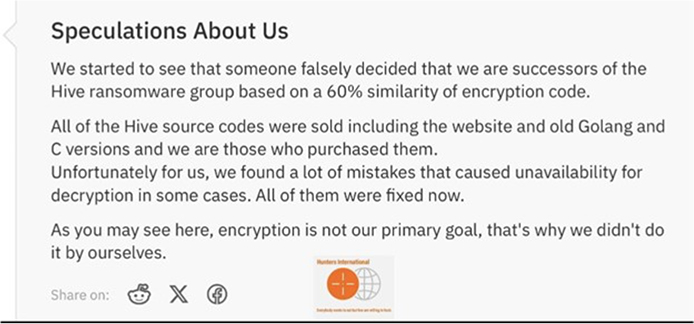
In the latest turn of events, a brand-new player in the world of ransomware-as-a-service has emerged, going by the name of Hunters International. This upstart seems to be using code once linked to the infamous Hive ransomware operation.
This connection naturally gave rise to the suspicion that the previous gang might have rekindled their unlawful endeavors under a new alias. Adding weight to this, a meticulous examination of the newly employed encryptor has revealed a multitude of code resemblances(60%).
Nevertheless, the Hunters International group claims to be a fresh entrant in the ransomware landscape, asserting that they acquired the encryptor source code from the developers of the Hive ransomware.
Screenshot Of Hunters Declaration (Source: Underground Forum)
Additionally, Hunters emphasizes that its primary objective does not revolve around encryption; instead, it centers its operations on data theft, leveraging this stolen information to coerce victims into complying with ransom demands.
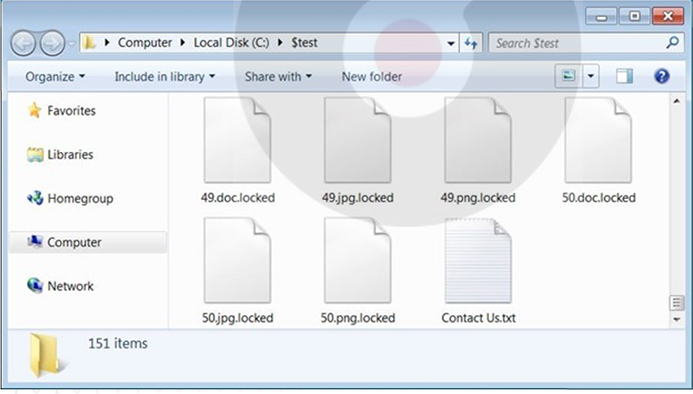
The encryptor used by Hunters International appends the “.LOCKED” extension to files that have undergone encryption.
Screenshot of Files Encrypted by Hunters International Ransomware. (Source: Surface Web)
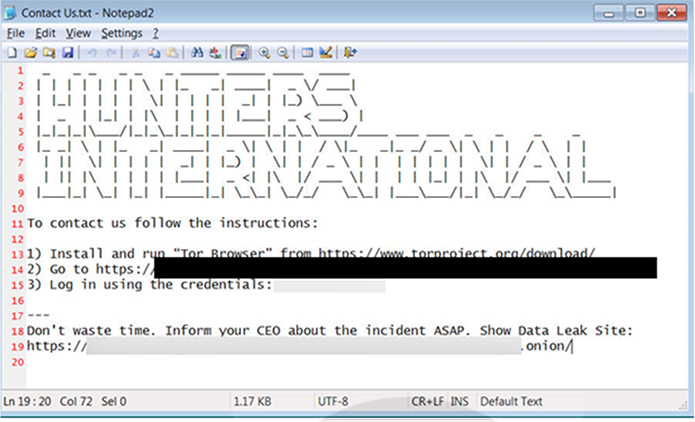
Within every directory, the ransomware deposits a plain text file labelled “Contact Us.txt.” This file contains instructions for the victim to establish contact with the attacker via Tor, using a unique login to access a protected chat page.
The ransom note of Hunters International Ransomware. (Source: Surface Web)
Countries targeted by Hunters International Ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1106: Native API |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence |
T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 3 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 4 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| 5 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1071.001: Application Layer Protocol: Web Protocols | ||
| 6 | TA0040: Impact | T1486: Data Encrypted for Impact |
CYFIRMA’s assessment based on the available information suggests that Hunters International ransomware will persist in targeting a wide range of global industries, with a notable focus on the United States and European countries. Its heightened emphasis on data theft, rather than just encryption, indicates a higher level of sophistication, posing a more significant threat to victims. Ransomware’s advanced ability to detect and evade debugging environments underscores its development maturity. Its design for stealthy operations during idle periods could make detection and mitigation more challenging.
Organizations should enhance their cybersecurity measures and maintain vigilance to effectively counter this evolving threat.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule:
title: Change PowerShell Policies to an Insecure Level – PowerShell tags:
– attack.execution
– attack.t1059.001 logsource:
product: windows category: ps_script
definition: ‘Requirements: Script Block Logging must be enabled’ detection:
cmdlet:
ScriptBlockText|contains: ‘Set-ExecutionPolicy’ option:
ScriptBlockText|contains:
– ‘Unrestricted’
– ‘bypass’
– ‘RemoteSigned’
filter:
# – ParentImage: ‘C:\ProgramData\chocolatey\choco.exe’ Powershell event id 4104 do not have ParentImage
ScriptBlockText|contains:
– “(New-Object System.Net.WebClient).DownloadString(‘https://community.chocolatey.org/install.ps1’)”
– “(New-Object System.Net.WebClient).DownloadString(‘https://chocolatey.org/install.ps1’)”
– ‘\AppData\Roaming\Code\’ condition: cmdlet and option and not filter
falsepositives:
– Administrator script level: medium
(Source: Surface Web)
Type: Information Stealer
Objective: Data theft, Stealing crypto wallets, malware implant
Target Technology: Browsers, Email & Social Media Platform
Target Geographies: Europe, Africa, and the Caribbean.
Active Malware of the Week
This week “NodeStealer” is trending.
Summary
Social media platforms provide significant opportunities for financially motivated threat actors to carry out large-scale attacks on unsuspecting users. Malicious and fraudulent threats are common on social networks, making it essential for users to stay informed about the latest tactics that could jeopardize the security of their accounts, data, reputation, and finances. One prevalent method used by cybercriminals is to exploit ad networks.
Researchers observed a growing trend of cybercriminals using social media networks for malvertising, with the ultimate goal of hijacking accounts and stealing personal data through malicious software. Malvertising campaigns exploit genuine tools and tactics to circulate online ads, wherein cybercriminals implant infected links within standard advertisement networks. They frequently employ attractive content to entice users into clicking on these compromised links.
NodeStealer
NodeStealer is a recently discovered info-stealer that enables threat actors to steal browser cookies and perform large-scale account takeovers. The initial campaign was linked to Vietnamese threat actors, who used JavaScript executed through Node.js to target business users through fake Facebook Messenger communications. This malware allowed attackers to gain control of business accounts and bypass security measures, like two- factor authentication. While its primary purpose was to hijack browser sessions and take over Facebook accounts, the malware has been updated to target additional platforms such as Gmail and Outlook, steal crypto wallet balances, and download more malicious components. It is distributed through Windows executable files disguised as photo albums.
NodeStealer Exploits Facebook Accounts via Deceptive Ads
Researchers discovered that attackers had compromised at least 10 business Facebook accounts, using them to serve malicious ads. These ads introduced a newer version of NodeStealer and used various Facebook profiles that offered access to media files of women. Approximately 140 malicious ad campaigns featured multiple iterations of the same ad. The attackers rotated between a maximum of 5 active ads every 24 hours to avoid user reports. These ads enticed victims with revealing photos of young women and clicking on them led to the immediate download of an archive containing a malicious .exe “Photo Album” file. This file also dropped a second executable written in .NET, responsible for stealing browser cookies and passwords. An estimated 100,000 potential downloads were identified through Ad reach analysis, with individual ads garnering up to 15,000 downloads within just 24 hours. The most affected demographic was males aged 45 and older.
Attack method
Cybercriminals are expanding their attacks beyond hijacking Facebook business accounts to target regular users using unique methods. They exploit compromised business accounts’ ad credit balances to run ads that deliver a malicious payload to their chosen targets.
The attackers create a Facebook page under the name “Album Update” (or similar) with suggestive photos of young women.

After the page is set up, malicious actors begin running ads that promote fake new content and entice users with lewd album covers. Some of the photos advertised appear to have been edited or even AI-generated. Also, attackers use descriptions like “New stuff is online today” to entice users into downloading a media archive. These “Albums” link to repositories storing a Windows executable with updated NodeStealer versions. They exploit Meta’s Ads Manager to target male users aged 18 to 65 from Europe, Africa, and the Caribbean.
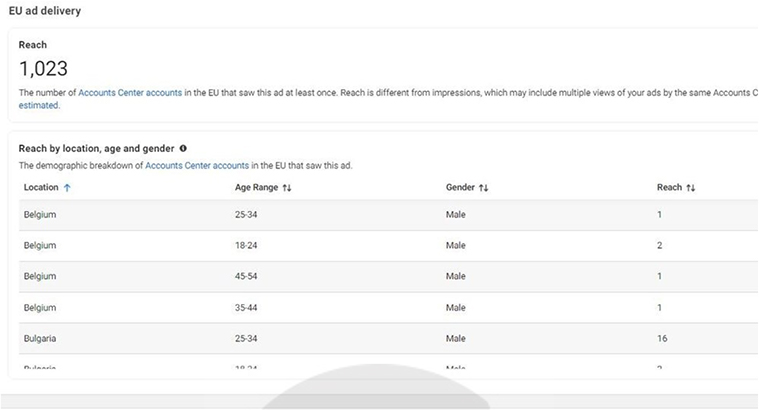
Once in control, the hackers can change passwords and add security measures to lock out the rightful owners, enabling various fraudulent activities while evading Meta’s security defences.
Other variations of the fake profiles
Some of the other names of fake profiles include:
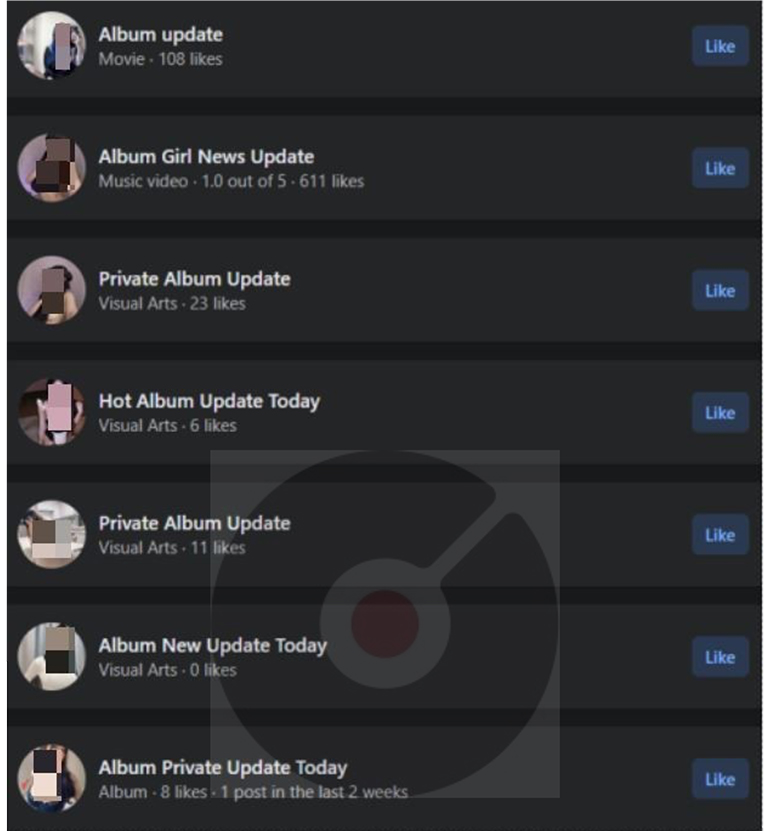
Fig: Fake Profiles
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that NodeStealer’s ongoing evolution and advanced tactics suggest a future with increasingly sophisticated cyber threats. We can anticipate a shift towards more targeted attacks, potentially affecting a wider range of browsers and websites. The exploitation of legitimate business pages for fraudulent activities may rise, prompting businesses to enhance their security measures. The emerging trend of threat actors focusing on Facebook accounts is expected to continue in the future. Such attacks have the potential to cause financial and reputational harm to both individuals and organizations.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Iran-based APT Agrius Targets Israel with Multiple Malware
Summary:
In a recent observation, researchers detected a cyber-attack piloted by Iran-based threat actors. A sophisticated Iranian advanced persistent threat (APT) group known as Agrius, or by various other aliases like Agonizing Serpens, BlackShadow, Pink Sandstorm, and DEV-0022, has been actively targeting educational and technological institutions in Israel. This APT, suspected to have ties to the Iranian government, has a history dating back to at least 2020 and has expanded its operations into Israel, the United Arab Emirates, and even South Africa. Agrius’s recent campaign, spanning from January to October 2023, focused on compromising Israeli organizations with the dual purpose of stealing sensitive personal information and intellectual property, while simultaneously deploying wipers to erase digital footprints. The APT group utilized a range of tools and techniques, including MultiLayer, PartialWasher, and BFG Agonizer wipers, as well as Sqlextractor for data extraction. To gain initial access, Agrius exploited vulnerable web-facing servers and established multiple web shells for persistence. To remain concealed and overcome security measures, the group employed proof-of-concept exploits, pen-testing tools, and custom utilities.
Agrius’s attack also involved the use of publicly available tools for reconnaissance, credential theft, lateral movement, and data exfiltration, including SMB password spraying and brute force attacks. Additionally, they extracted valuable information from SQL databases, such as ID numbers, passport scans, emails, and addresses. The APT group attempted to execute three distinct wipers during their attacks, demonstrating an evolution in their tactics to evade detection and bypass security solutions. Their enhanced capabilities emphasize stealth and evasive techniques, marking a significant escalation in their threat profile.
Relevancy & Insights:
The timing of the detection of this particular threat is intriguing, given the ongoing conflict between Israel and Gaza. Iran, a strong supporter of Gaza and its people due to a shared religious connection, underscores the need for Israel to remain vigilant and proactively counter potential attacks originating from various adversaries.
ETLM Assessment:
The APT group, Agrius, has a primary objective of targeting various industries in Israel. This pursuit is driven by the contentious relationship between Israel and Iran, with Iran attempting to assert dominance over Israel through cyber espionage, by gathering intelligence. Given the ongoing conflict between Israel and Gaza, the likelihood of such cyberattacks against Israel has significantly elevated. In addition to the potential for malware attacks, there is a heightened risk of Distributed Denial of Service (DDoS) attacks from other hacktivist groups, aiming to demonstrate their support for Gaza.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russia targeting Ukraine’s military-industrial complex
Russia state-run hacking group; Turla, operating under the wing of the FSB intelligence
agency (also known as “Venomous Bear”), has long operated against Ukraine. This APT has recently been observed by researchers employing an advanced and stealthy .NET backdoor” called “Kazuar.” The backdoor has been used against the Ukrainian defense sector, the Ukrainian CERT reported this summer, where it’s been used to obtain access to a range of sensitive access and information. It hijacks legitimate websites for command-and-control, which renders Kazuar resistant to takedowns, and it also has stealthy and anti-analysis features.
ETLM Assessment:
This activity shift is best explained as an act of traditional espionage, in order to gain knowledge on the transformation of Ukrainian defense industry and its links to Western companies, which are providing know-how necessary for the stated goal of making Ukraine an armoury of Europe in the coming decades. Almost two years since Russia’s full-scale invasion, Ukrainian officials know how essential it is to turbocharge their own industry, innovate at speed and mobilize national resources, in order to fill the gaps of key weapon systems which are in short supply. These include anything from artillery ammunition to cheap attritable drones and air defense missiles. Russia is trying to stay ahead of the developments, gain operational data which it could use in kinetic targeting by its stand-off weapons like hypersonic missiles, since their manufacturing and operating costs require big, non-mobile and valuable targets to employ them effectively. Russia will also likely seek to penetrate Western military-industrial complex, exfiltrate data and maybe even interfere in the production of crucial weaponry, like artillery ammunition or long rage rockets.
Iranian APT working in the interest of Hamas
The cyber phases of the war between Hamas and Israel have been mostly marked by nuisance level hacktivism. However, that is now starting to change. Iranian APTs have weighed in on the side of Hamas in its war against Israel – the MuddyWater threat actor has likely utilized spearphishing in a fresh campaign targeting Israeli civil service with an apparent goal of espionage, although battlespace preparation for subsequent attacks can’t be ruled out either. A sponsor and one of the key allies of Hamas; Iran, has displayed a recent increase in its cyberespionage capabilities, deploying increasingly sophisticated malware against regional rivals, especially Israel, but also Saudi Arabia and other sunni-muslim-majority countries. Another group tracked under the name Agonizing Serpens has been attacking the Israeli tech sector and universities since January, with the latest attacks occurring as recently as October. These attacks were characterized by attempts to steal sensitive data, such as personally identifiable information and intellectual property. But following the data exfiltration, the attackers used a variety of wipers to hide their traces and render the compromised endpoints unusable.
In another campaign a group known as LionTail, which is associated with the Iranian Revolutionary Guard Corps has been targeting local and national government agencies and various institutions in Israel, with the goal of exfiltrating sensitive data on civil defense and government issues, while yet another group associated with Iranian proxies has been trying to hack cameras in Israel, including private cameras near the border with Lebanon.
ETLM Assessment:
The conflict in Gaza has revealed the complex and contradictory forces that shape Iran’s behaviour and interests in the Middle East, which are driven by both ideology and pragmatism. Iran’s proxies in the region, namely Lebanese Hezbollah, Iraqi Popular Mobilization Forces and Yemeni Houthis have all joined the struggle and started a low intensity war against Israel and the U.S., mostly by way of rocket and drone attacks. Hezbollah alone has lost over 50 fighters but the recent speech by its leader Hassan Nasrallah and Iranian supreme leader Ali Khamenei suggest that these attacks are likely meant to show Iran’s strength and deterrence capabilities to Israel and the United States, but also that Iran and its proxies are walking a thin line trying to avoid a direct clash that could harm Iran’s interests and security. Iranian officials have been walking a tightrope between their ideological commitment to the Palestinian cause and their pragmatic calculations of regional interests and risks. Their statements expose the dilemmas and difficulties that Iran confronts in dealing with its friends and foes. But they also reflect their domestic concerns and calculations. This, however, does not apply to the fifth domain, where the risk of high scale physical retaliation seems low. Israel’s National Cyber Directorate confirms this observation and states that the prospect of an intensified Iranian cyber campaign is deeply worrying, since Iran “knows that they can act there [in cyberspace] more freely than in physical space”. We are likely to see a spike in the activity of Iranian APTs attacking Israel and other countries that support Israel in the coming months. Israel seems to have been largely successful in blunting state-directed attacks, since it employs a proactive cyber defensive approach adopted by the Israeli National Cyber Directorate (INCD), as well as the mobilization of the country’s cyber security ecosystem due to the high tech nature of the Israeli economy. However, the same cannot be said of every country supporting Israel and the risk of potential spill out is imminent.
EGCO Group is Impacted by LockBit 3.0 Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, (www[.]egco[.]com), was compromised by LockBit 3.0 Ransomware. The Electricity Generating Public Company Limited or EGCO Group is the first independent power producer in Thailand, established by the Electricity Generating Authority of Thailand (EGAT). The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The breached data includes confidential and delicate information about the company.
The following screenshot was observed published on the dark web:
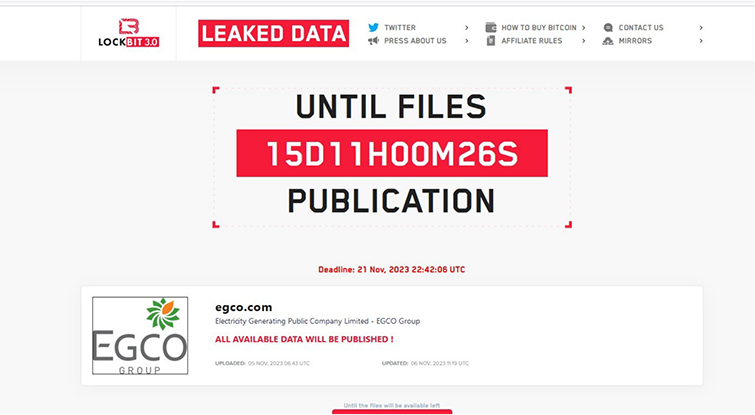
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
CYFIRMA assesses LockBit 3.0 Ransomware to maintain a focus on American businesses and related entities that hold significant amounts of Personally Identifiable Information (PII). However, the recent targeting of EGCO Group highlights the global risk posed by LockBit 3.0.
Summary
The vulnerability allows a remote attacker to execute arbitrary SQL queries in database.
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data in UI layout preferences. A remote user can send a specially crafted request to the affected application and execute arbitrary SQL commands within the application database.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to read, delete, modify data in database and gain complete control over the affected application.
Affected Products: https[:]//github[.]com/glpi-project/glpi/security/advisories/GHSA-mv2r- gpw3-g476
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
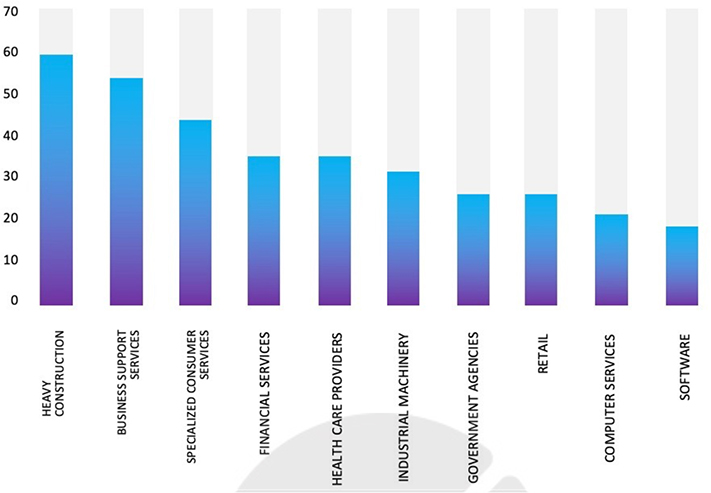
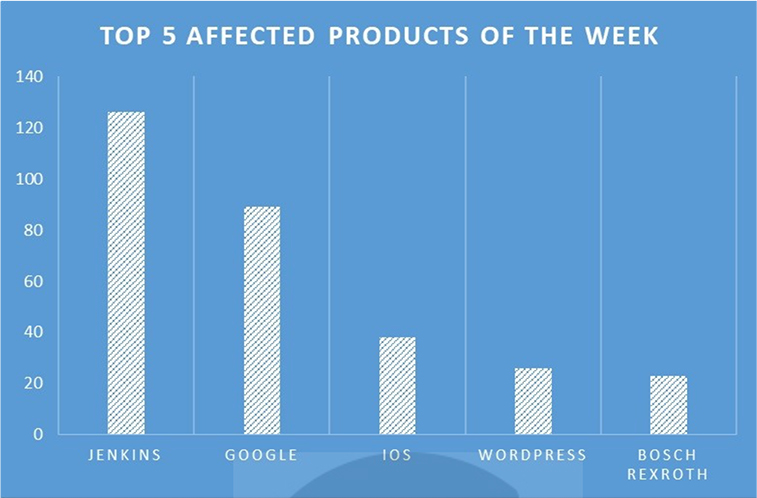
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Russian hackers targeted Dutch public transport chip card website
Summary:
The website of public transport chip card (OV chip card) company Translink was unavailable on Saturday (4 November 2023) due to a DDoS attack (Distributed Denial of Service), according to a spokesperson for the public transport chip card company. In the attack, the computer systems were bombarded with data traffic until they could no longer cope and collapsed. The spokesperson stated that due to a DDoS attack, the website is currently inaccessible. They mentioned an initial attack on Friday (3 November 2023), but it was successfully repelled by implementing suitable measures. Despite this, travellers can continue to check in and out as usual by utilizing their chip cards. The attack was claimed by the pro-Russian hacktivist group; NoName05716, which attacked Dutch organizations in retaliation for supporting Ukraine in the war with Russia.
Relevancy & Insights:
The website of Translink; a public transport chip card company, became unavailable on Saturday (4 November 2023) due to a DDoS attack, leading to temporary inaccessibility. The DDoS attack was claimed by the pro-Russian hacktivist group; NoName05716, purportedly as a response to Dutch organizations’ support for Ukraine in the ongoing conflict with Russia.
ETLM Assessment:
CYFIRMA assesses that pro-Russian threat actors will continue to target Dutch and other NATO countries, in an effort to cause reputational damage and general disruption.
Vengreso Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Vengreso,
{www[.]vengreso[.]com}. Vengreso is a Virtual Sales and Instant Messaging platform, utilized by professionals globally. Vengreso provides instruction, consultation, and implementation of digital selling tactics, relied upon by B2B brands, including Proofpoint, Seismic, Woodruff-Sawyer, Juniper Networks, and others. The compromised data comprises of names, emails, hashed passwords, profile pictures, StripeIDs, login dates, and other confidential information.
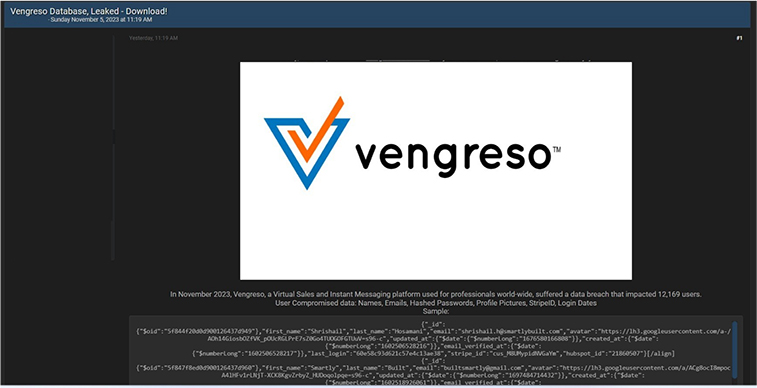
Source: Underground forums
Relevancy & Insights:
Driven by financial incentives, cyber attackers persistently target vulnerable and inadequately secured systems and software applications. A significant number of these malicious actors operate within hidden online communities, engaging in discussions related to cybercrime and the illicit trade of stolen digital assets. Distinguishing themselves from other financially motivated groups, such as ransomware or extortion collectives that often publicize their attacks, these cybercriminals prefer to maintain a low profile. By exploiting unpatched systems or vulnerabilities in software and hardware, they illicitly gain access and abscond with valuable information. Subsequently, they market the stolen data on clandestine forums, where it is either resold or repurposed by other malicious entities for their own unlawful ends.
ETLM Assessment:
The United States of America continues to rank among the top targets for cybercriminals worldwide. According to CYFIRMA’s assessment, U.S. institutions lacking strong security measures and infrastructure will likely remain at a heightened risk of potential cyberattacks.
CYFIRMA Research team observed a potential data leak related to the Ministry of Education Saudi Arabia, {www[.]moe[.]gov[.]sa}. The Ministry of Education, Saudi Arabia is a facility that provides educational training and degrees in health and science fields for students in Saudi Arabia. The breached data includes names, phone numbers, addresses, emails, and other sensitive information.
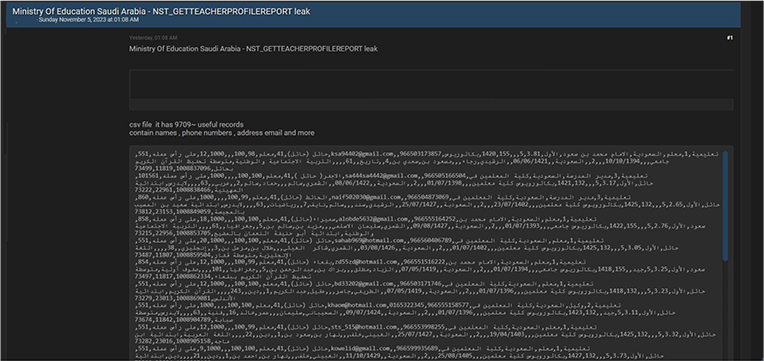
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS