



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Repair ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Repair ransomware.
In late April 2024, researchers uncovered a ransomware dubbed “Repair”, which is identified as a member of the notorious MedusaLocker ransomware family.
Since appearing in September 2019, MedusaLocker ransomware has attracted notice for its focus on healthcare and finance sectors, while also impacting various other industries. Operating under a Ransomware-as-a-Service (RaaS) model, it encrypts files using sophisticated techniques like AES and RSA, rendering them inaccessible to users.
Perpetrators then demand payment for decryption keys, amplifying the threat.
MedusaLocker has become infamous for its multiple variants, each identifiable by unique extensions attached to encrypted files. The introduction of “Repair” represents a fresh phase in its changing strategies.
Repair ransomware encrypts the files and adds a “.repair” extension to the encrypted files. Upon completing the encryption process, the Repair ransomware generates an HTML file named “How_to_back_files.html,” which houses the ransom note. This ransom note not only demands payment for decryption but also employs double extortion tactics, threatening victims with the potential of data leaks.
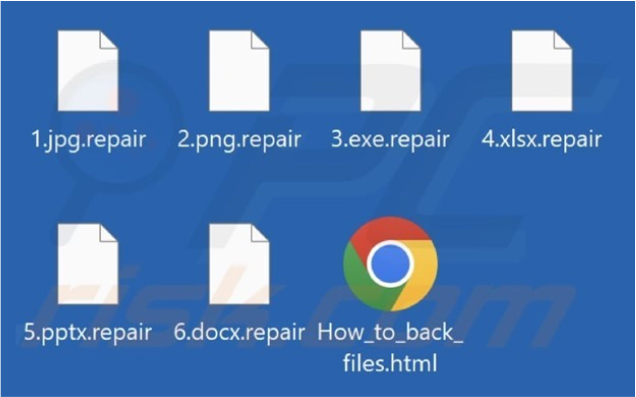
Screenshot of files encrypted by ransomware (Source: Surface Web)
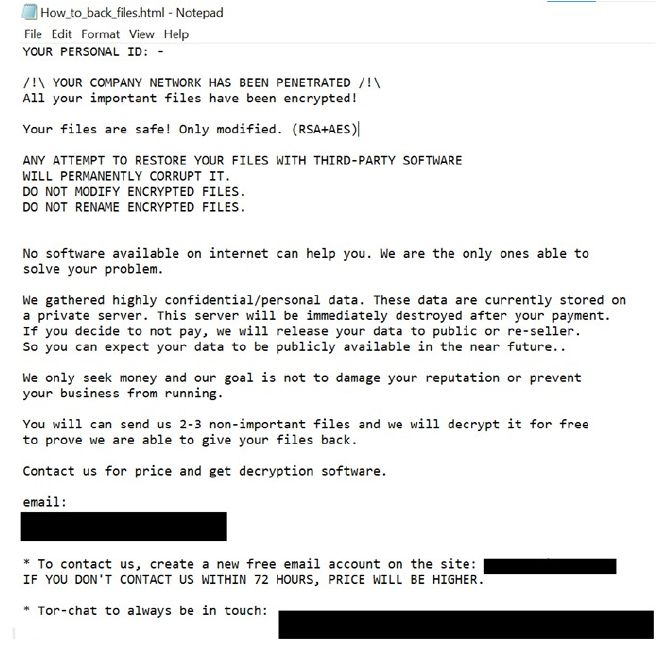
Screenshot of Text presented in Ransom note (Source: Surface Web)
The ransom note from the “Repair” ransomware communicates a clear message that it will target the company rather than individuals and encrypt all crucial files using RSA+AES encryption, making restoration without the attackers’ assistance impossible and any attempt to do so with third-party software risks permanent corruption. The note emphasizes the exclusivity of the attackers’ decryption capability, warning against file modification or renaming.
Additionally, it reveals that highly sensitive personal data has been obtained and stored on a private server, which will be destroyed upon payment. However, refusal to pay will result in the data being made public or sold.
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T147.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 3 | TA0004: Privilege Escalation | T1134.004: Access Token Manipulation: Parent PID Spoofing |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1548: Abuse Elevation Control Mechanism | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070: Indicator Removal | ||
| T1112: Modify Registry | ||
| T1134.004: Access Token Manipulation: Parent PID Spoofing | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1548: Abuse Elevation Control Mechanism | ||
| 5 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| 6 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1614: System Location Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1056.001: Input Capture: Keylogging |
| T1074: Data Staged | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that MedusaLocker ransomware, operational since 2019, has consistently targeted various sectors globally, including healthcare, finance, and IT services. Looking ahead, Repair ransomware, a variant of MedusaLocker, is expected to evolve with sophisticated evasion tactics, posing potential risks to businesses of all scales. The likelihood of this new variant targeting major industries worldwide remains significant. Vigilance and strong cybersecurity measures are essential to mitigate these threats effectively.
Sigma Rule
title: Process Creation Using Sysnative Folder tags:
– attack.defense_evasion
– attack.privilege_escalation
– attack.t1055 logsource:
category: process_creation product: windows
detection: sysnative:
– CommandLine|contains: ‘:\Windows\Sysnative\’
– Image|contains: ‘:\Windows\Sysnative\’ condition: sysnative
falsepositives:
– Unknown level: medium
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Information Stealer
Objective: Infiltration, Data Exfiltration
Target Technology: macOS, including iCloud Keychain, Apple Notes, Web Browsers, Crypto Wallets, Discord, FileZilla, Steam, and Telegram.
Active Malware of the Week
This week “Cuckoo” is trending.
Cuckoo
Researchers have identified a new information-stealing malware known as Cuckoo, targeting Apple macOS systems. Disguised as a legitimate music conversion application named DumpMediaSpotifyMusicConverter, this malware poses a serious threat due to its advanced capabilities combining infostealing and spyware functionalities. It infiltrates macOS systems by hijacking resources to collect and exfiltrate sensitive data to a remote command-and-control server controlled by malicious operators.
Attack Strategy
The researchers examined a file named DumpMediaSpotifyMusicConverter, also known as upd, a universal Mach-O binary compatible with both Intel and ARM-based Macs. This file was discovered on the dumpmedia[.]com website, ostensibly offering applications to convert music from streaming services to MP3 format. Upon downloading and analyzing the DMG file for the Spotify version of the application, researchers discovered suspicious behavior during installation. Unlike typical macOS applications, users were instructed to right-click and select Open instead of dragging the app to the /Applications folder.
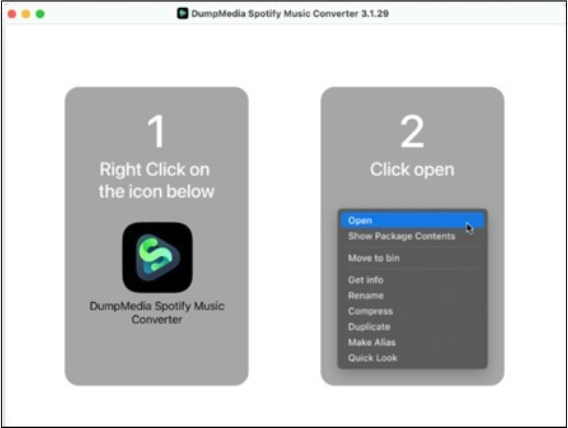
Upon inspecting the application bundle by selecting “Show Package Contents” instead of “Open,” researchers discovered a Mach-O binary named upd within the macOS folder. This raised suspicions because such binaries would bear the name of the application. In addition, within the Resources folder of the bundle, they found another application bundle named DumpMedia Spotify Music Converter, which seemed to be the legitimate application bundle. Further investigation into the upd file revealed that it was signed adhoc without a developer ID. This implies that Gatekeeper, macOS’s security feature, would initially prevent the app from running and prompt the user to manually authorize its execution.
Running the Application
After allowing the application to run, researchers observed that it initiated a bash shell and began gathering host information using the system_profiler command to extract the hardware UUID. The malware’s strings were XOR-encoded, and a subroutine decoded the output of the system_profiler command. The decoding process involved loading a pointer to the XOR-encoded string and a key for decryption. Once decoded, the string was passed to a function that executed commands using popen(). The decoded UUID was saved for later use. The malware used a similar XOR encoding method for all commands passed to popen(). Subsequently, the application created a duplicate of itself named DumpMediaSpotifyMusicConverter, stored it in a hidden folder within the /Users directory, and occasionally appeared as either upd or DumpMediaSpotifyMusicConverter. The original malware then removed the quarantine flag from itself and the copied file using the xattr -d com.apple.quarantine command.
Locale Check
After querying for the UUID, the Cuckoo malware checks the system’s LANG environmental variable. It retrieves this value using the getenv() function and compares it against specific locales within an If statement to determine its further actions. The obtained LANG value, typically en_US.UTF-8, is then formatted using snprintf() to truncate it to five characters followed by a semicolon (e.g., en_US;). The If statement employs the strstr() function to search for the formatted LANG value within a list of prohibited locales.
Additionally, it includes another function call to _sem_open() as part of its evaluation criteria.
if (_sem_open(&_/mtx-%.2 and UUID, 0x200) != -1 &&
_strstr(&hy_AM;be_BY;kk_KZ;ru_RU;uk_UA;, &localeReturn(en_US;)) == 0)
The malware creators intended to avoid infecting devices in five specific countries:
If the current system’s locale does not match any of these prohibited locales, the malware proceeds to open the legitimate SpotifyMusicConverter application.
Creating Persistence
This malware’s behavior deviates from typical stealers by incorporating persistence features more commonly associated with spyware. It decodes the necessary strings using an XOR function to prepare for creating and populating a plist. After decoding, the malware checks for the existence of ~/Library/LaunchAgents; if absent, it creates this directory. To establish persistence, the malware duplicates itself and saves it to a newly created folder within the user’s home directory using NSGetExecutablePath() to obtain its binary path and create the necessary folder structure. The fcopyfile() function is then employed to copy the binary to this new location. To ensure persistence, the application utilizes launchctl to load a LaunchAgent for a plist derived from the application. Upon inspecting the plist, it’s revealed that the objective is to execute a login script every 60 seconds. The setup of persistence involves further XOR decoding of strings and using snprintf() to replace values in format strings used to construct the plist.
Privilege Escalation
The malware prompts the user for their password using osascript with the message “macOS needs to access System Settings,” without explicitly stating that a password is required. Upon entering the correct password, upd stores it in a file named pw.dat located at ~/.local-UUID/, the same directory as the copied and renamed upd.
The malware employs a tactic called PasswordCapture() to test the captured password. This function builds and executes a script to parse the returned text value, which is then passed to a passwordChecker() function along with the user’s password obtained from getpwuid(getuid()). The passwordChecker() function uses Core Services Identity functions to authenticate the password and writes the result to the pw.dat file. To proceed, the malware requires the user to accept TCC (Transparency Consent and Control) prompts for access to the Finder, microphone, and downloads. It then gathers more host information by executing commands such as sw_vers, system_profiler SPHardwareDataType, and ps aux to obtain details about macOS version, hardware, and running processes. Lastly, the malware sets a variable for the Desktop folder path using osascript and mutes the computer’s volume as part of its operations.
Spying and Infostealing Capabilities
This malware conducts targeted file queries associated with specific applications to gather comprehensive system information. The primary engine of the malware categorizes collected information by keywords observed in network communications.
The function runIT() at address 0x100016024 exemplifies the malware’s capabilities:
Each function follows a pattern where encoded strings are decoded using an XOR function, paths to relevant files are created, and file pointers are obtained for data collection. The malware possesses capabilities to execute various commands, including extracting hardware information, capturing running processes, querying installed applications, taking screenshots, and harvesting data from iCloud Keychain, Apple Notes, web browsers, crypto wallets, and apps like Discord, FileZilla, Steam, and Telegram. These actions reflect a comprehensive approach to data exfiltration and system reconnaissance.
TCC Reset
Following the collection of data from third-party applications, the malware initiates a call to tccutil, decoded and executed via popen(), to reset the TCC database specifically for AppleEvents permissions. This action is puzzling because it typically prompts users for permission. Afterward, the malware executes another osascript command related to the Desktop. Once this process is complete, data collection shifts focus to Apple applications. The malware copies files related to Safari, Notes, and Keychain to temporary locations in /var/folder, determined using getenv(TMPDIR).
Specific data is targeted from Apple applications:
Additional File Capture and Screen Capture
Following the previous data collection actions, the malware extends its reach to locate various file-type extensions within the Desktop and Document directories. It reverses its previous action of muting the computer, presumably to prevent audio notifications during screen capture activities.
The malware executes the SCREENCAPTURE() function, invoking the screencapture command with arguments specifying the file type (.jpg) and storage path for screenshots. This command is decoded and executed via popen() to capture and save screenshots. It is suspected that the system is muted during screen capture to avoid user detection, although this action prompts TCC permissions. Notably, there is uncertainty regarding the completeness of the screenshot functionality, as there were no observed cross-references indicating what triggered these functions within the malware.
Opening the Actual Converter Application
The malware disguises its activity by copying a legitimate application from its resource folder to the /Applications directory. It achieves this by locating the legitimate app within its own Resource directory using CFBundleCopyResourceURL() and then executing cp (copy) and open commands to launch the application. This process is intended to conceal the malicious behavior, making it appear as though a legitimate file is being executed to avoid user suspicion.
Network Communication and Data Exfiltration
This malware uses sockets and the curl API to establish communication with its Command and Control (C2) server for data exfiltration. After socket function calls, the malware employs the send() function to transmit data, including the machine UUID captured during the initial execution of the malware, to the IP address 146.70.80.123. The purpose of this communication is to check the UUID on the C2 server to determine if the malware has already been executed on the host. During subsequent runs, the malware halts after removing the quarantine flag, suggesting it recognizes previous executions. However, disconnecting from the internet before subsequent runs allows the malware to proceed as if it were the first execution, bypassing this detection mechanism.
Curl Usage
The malware utilizes the curl API to facilitate communication with its Command and Control (C2) server by posting information. It configures curl using curl_easy_setopt() function calls, decoding the target URL and passing it along with the flag 0x2712 for setup. This setup allows the malware to interact with the specified URL for data transmission and other communications with the C2 server.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the discovery of malware like Cuckoo highlights the evolving threat landscape for macOS users and organizations. This type of advanced malware is likely to become more widespread and may target macOS users on a larger scale in the future. As cybercriminals refine their tactics, macOS users may face heightened risks of malware infections and compromised system security, potentially leading to disruptions, data breaches, and unauthorized access to sensitive information. Organizations relying on macOS systems could experience significant disruptions and reputational damage from the infiltration of sophisticated malware like Cuckoo. To address future risks effectively, organizations may need to invest more in advanced cybersecurity defenses tailored specifically for macOS environments, emphasizing proactive measures to mitigate evolving threats.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
Security Awareness training should be mandated for all company employees. The training should ensure that employees:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Unveiling APT42: Iran’s Cyber Espionage Campaign
Summary:
APT42, a notorious cyber espionage group with ties to the Iranian state, operating under the alias Mint Sandstorm, has recently been identified as orchestrating a highly sophisticated social engineering campaign. This campaign revolves around the impersonation of journalists to infiltrate networks and gather intelligence, particularly targeting high-profile experts in Middle Eastern affairs.
Geographically, APT42’s operations span across strategic regions such as the United
States, Israel, Europe, and the Middle East. Within these areas, their targets encompass a diverse range of industries, including but not limited to non-governmental organizations (NGOs), media outlets, academia, legal services, and activist groups.
The initial phase of their attack involves meticulously crafting personas as credible journalists to establish trust and rapport with their targets. Once trust is established, APT42 utilizes various means to exploit this connection and gain unauthorized access to victim networks.
Their arsenal includes custom backdoors like TAMECAT and NICECURL. TAMECAT functions as a PowerShell toehold, allowing the execution of arbitrary commands within compromised systems. On the other hand, NICECURL, a VBScript backdoor, serves the purpose of downloading and executing additional modules for data mining and command execution, thereby providing APT42 with a wide range of capabilities within compromised networks.
The primary motive driving APT42’s activities is to further Iran’s intelligence objectives, particularly those aligned with the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO). By targeting influential individuals and organizations involved in Middle Eastern affairs, APT42 aims to gather valuable intelligence, influence decision-making processes, and ultimately advance Iran’s strategic interests in the region.
Relevancy & Insights:
APT42; the Iranian state-backed hacking group, utilizes highly targeted spear-phishing and social engineering techniques to establish trust with their victims, facilitating access to email accounts and the installation of malware. Their operations encompass three main categories: credential harvesting, surveillance, and malware deployment. While credential theft remains their primary objective, they also engage in surveillance activities, particularly through malware, to monitor individuals of interest to the Iranian government. Additionally, APT42 demonstrates versatility by incorporating custom backdoors and lightweight tools into their operations, suggesting broader strategic objectives beyond mere credential theft. The group has previously targeted industries such as education, government, healthcare, and pharmaceuticals, indicating a wide- ranging and adaptable approach to achieving their goals.
ETLM Assessment:
APT42; a cyber espionage group believed to operate under the sponsorship of the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO), demonstrates a significant threat to both Western and Middle Eastern regions. With a primary focus on policy and government sectors, media organizations and journalists, as well as NGOs and activists, APT42 employs sophisticated tactics, particularly spear-phishing campaigns, to harvest credentials. Their operations span diverse industries, including academia and legal services, indicating a broad strategic interest. APT42’s modus operandi emphasizes the establishment of trust and rapport with targets before attempting to steal credentials. Additionally, they deploy malware such as custom backdoors like NICECURL and TAMECAT to supplement their activities. This assessment underscores the need for robust cybersecurity measures to mitigate the threat posed by APT42’s state-sponsored cyber espionage activities.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers target UK Ministry of Defense
As per government-acknowledged reports, a suspected Chinese threat actor compromised the UK Ministry of Defense’s payroll system, gaining access to personal and financial information belonging to more than a quarter of a million current and former armed forces members. According to the office of the UK Prime Minister, there are indications that a malicious actor has compromised the armed forces’ payment network and the Ministry of Defence has already taken the network offline and provided employees with assistance.
ETLM Assessment:
The office of the Defense Secretary has not directly attributed the hack to China, although research analysts believe Beijing was to blame for the incident. CYFIRMA analysts believe the attack to be a classic example of state espionage, with Chinese government hackers probably looking at the financial records of employees and trying to single out potentially vulnerable employees, who could be singled out for further HUMINT action with a view to potentially deliver government secrets to Beijing.
North Korea’s hackers targeting Western media organizations
A joint advisory from the FBI, the NSA, and the US State Department has recently warned that the North Korean threat actor Kimsuky is exploiting weak DMARC policies as part of its spearphishing campaigns. As per the advisory, Pyongyang hackers are trying to exploit the vulnerability to send spoofed emails as if they came from a legitimate domain’s email exchange. The North Korean cyber actors have conducted spearphishing campaigns posing as legitimate journalists, academics, or other experts in East Asian affairs with credible links to North Korean policy circles. North Korea leverages these spearphishing campaigns to collect intelligence on geopolitical events, adversary foreign policy strategies, and any information affecting North Korean interests by gaining illicit access to targets’ private documents, research, and communications.
ETLM Assessment:
North Korean cyber operations have increased in sophistication over the past two years, and our researchers noted last year in a research report that Pyongyang’s threat actors seem particularly interested in stealing information related to maritime and missile technology research, given the emphasis the Kim regime puts onto developing a full nuclear triad. The interest in media is most likely related to Pyongyang’s interest in the media links to intelligence and government bodies providing media houses with advance clues of the US policy. The heavily sanctioned regime in North Korea is hungry for the off-limits technologies it cannot obtain on the open market and for any information on the Western policies towards the country following its bid to support Russia in its military support to Russia in its war in Ukraine. Pyongyang has sold at least a million artillery rounds to Moscow during the past year and the regime is possibly scanning for the planned reaction of Western governments in this matter.
The Underground Ransomware impacts the Frencken Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; (www[.]frenckengroup[.]com), was compromised by the Underground Ransomware. Frencken Group is a global integrated technology solutions company that’s fully committed to providing complete and integrated one-stop solutions in partnership with its valued customers. The Frencken Group serves customers in Europe, Asia, and the US through a global network of operating subsidiaries. The compromised data comprises documents spanning information technology, human resources, finance, and other categories of sensitive and confidential information. Its total size is approximately 439.4 gigabytes.
The following screenshot was observed published on the dark web:
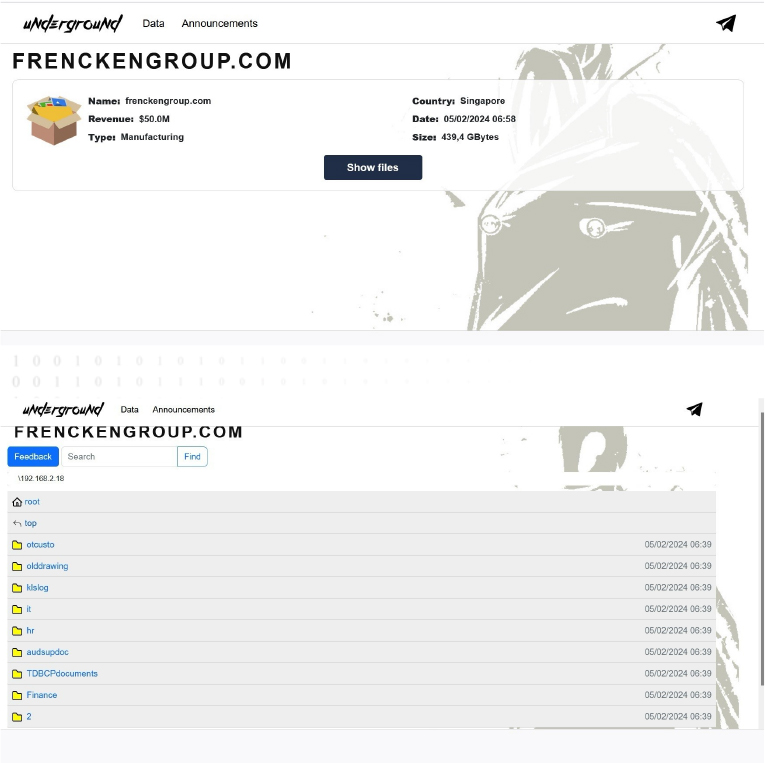
Source: Dark Web
Relevancy & Insights:
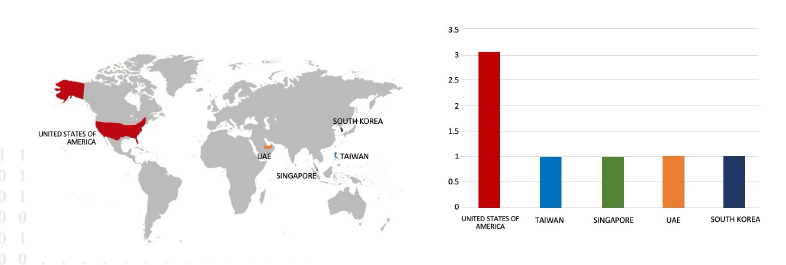
The RansomHub Ransomware impacts the ExtraCo
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE); (www[.]extraco[.]ae), was compromised by the RansomHub Ransomware. Extra Co is a leading manufacturer in the Middle East offering many products and services in the fields of fibreglass composites, prefabricated houses, interior furnishings, fit-outs, structural and aesthetic precast, and metal works. The data that has been compromised has not yet surfaced on the leak site, suggesting ongoing negotiations between the affected party and the ransomware group. The compromised data encompasses sensitive and confidential information pertinent to the organization. The total size of the compromised data is approximately 20 gigabytes.
The following screenshot was observed published on the dark web:
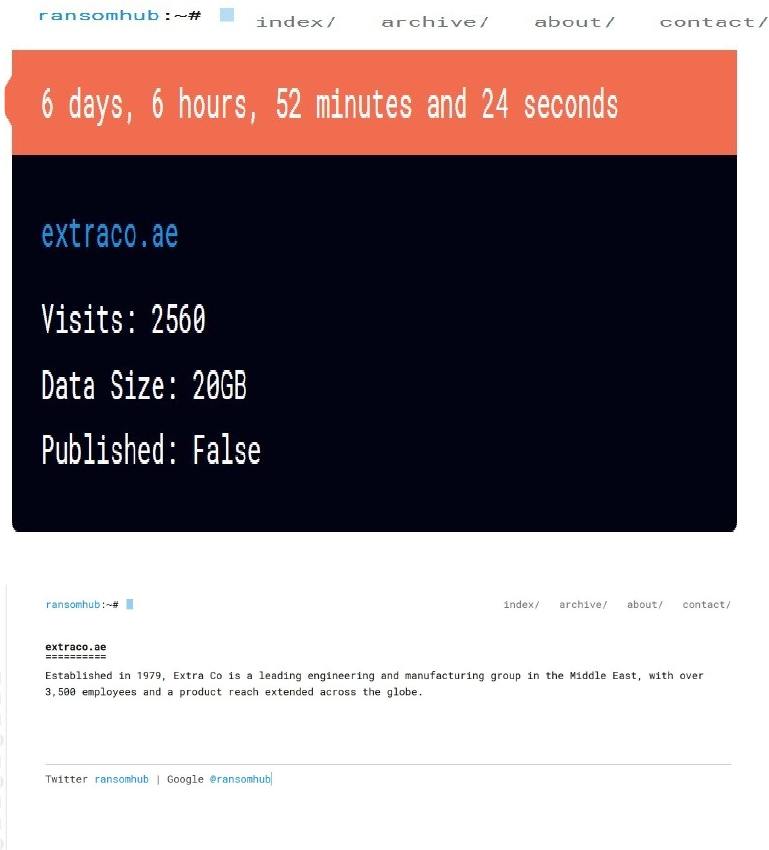
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The RansomHub group seems to be a recently emerged ransomware group, likely with roots in Russia. Due to the benefit it offers its affiliates and the strict controls it enforces, they could be vying for the leadership position amidst pressure from security forces to major players like LockBit and ALPHV. However, their ransomware strains appear to be just a revised version of an old sample for now. An interesting part is that this strain is also written in the Golang language. Based on CYFIRMA’s assessment, RansomHub Ransomware targets worldwide organizations. The attack on ExtraCo also highlights ransomware groups’ interest in Asian organizations financially strong in the region with exploitable vulnerabilities.
Vulnerability in Tinyproxy
Summary:
The vulnerability allows a remote attacker to gain access to potentially sensitive information.
Relevancy & Insights:
The vulnerability exists due to an uninitialized variable while parsing HTTP requests.
Impact:
A remote attacker can send a specially crafted HTTP request and gain unauthorized access to sensitive information on the system.
Affected Products: https[:]//talosintelligence[.]com/vulnerability_reports/TALOS-2023-1902
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
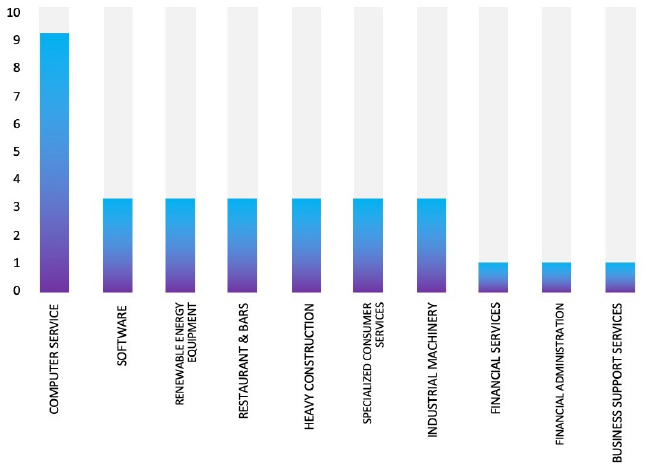
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
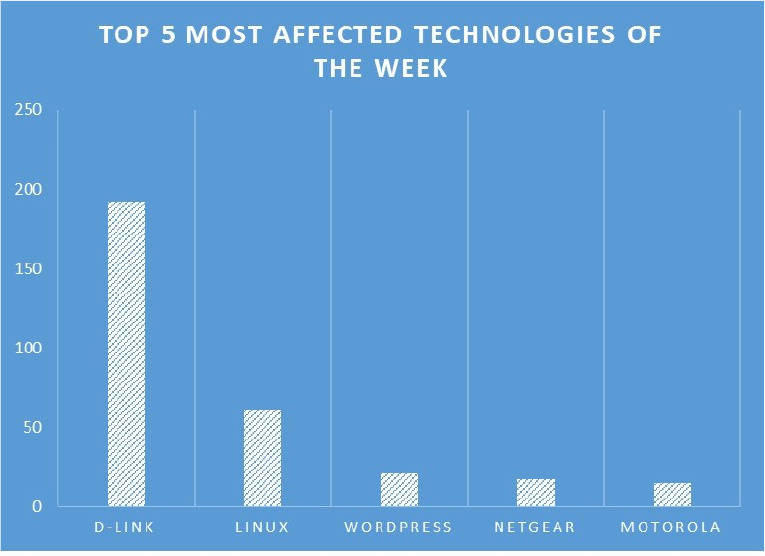
ETLM Assessment:
Tinyproxy, a nimble HTTP/HTTPS proxy daemon designed for POSIX operating systems, delivers swift performance in a compact form. Suited for embedded deployments lacking resources for larger proxies, it finds utility globally across industries such as technology, finance, healthcare, and beyond.
Space Bears Ransomware attacked and Published data of Mr Bean
Summary:
Recently we observed that Space Bears Ransomware attacked and Published data of Mr Bean on its darkweb website. Mr Bean(www[.]mrbean[.]com[.]sg) is the leading chain soya bean food & beverage retailer in Singapore today. With more than 60 stores in Singapore & Asia, Mr Bean offers a variety of soya bean drinks and snacks. Young and old can enjoy refreshing ice-blended flavored soya drinks, ice creams, pastries, and more. The data leak, following the ransomware attack, encompasses a broad spectrum of sensitive and confidential information pertinent to the organization.
Source: Dark Web
ETLM Assessment:
The newly emerged Space Bears Ransomware has declared 7 victims in its inaugural ransomware operation, marking a significant milestone for the group. These victims are distributed across 7 countries: Germany, Norway, the US, South Africa, Ecuador, Morocco, and Singapore. The hackers have publicized evidence of the breaches on their recently established leaked website. Ongoing evaluations conducted by CYFIRMA reveal that Space Bears Ransomware is targeting nations in Asia, America, and Europe, driven by an unwavering quest for considerable financial gains through ransomware activities.
EdcComp Indonesia data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to EdcComp Indonesia, {www[.]edccomp[.]com } in an underground forum. EdcComp Indonesia is an online consumer electronics & computer retail store. The compromised data includes customer information such as Name, Calling Code, Mobile Number, Email Address, Blacklist Status, Total Amount Spent, Total Number of Orders, Address, Group Membership, First Order Date, Last Order Date, Gender, Date of Birth, WhatsApp Contact, Instagram Handle, Facebook Profile, Notes, Creation Time, etc. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.
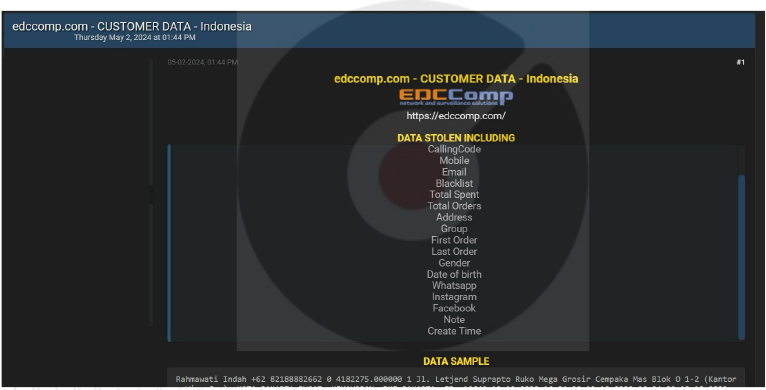
Source: Underground Forums
PT. PROLABIOS MITRA ANALITIKA – INDONESIA data advertised on a Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to PT. PROLABIOS MITRA ANALITIKA – INDONESIA, {www[.]prolabios[.]com} in an underground forum. PT. PROLABIOS MITRA ANALITIKA (PMA) was built to be one of the distributors in Indonesia with a passion for fulfilling the need for products or services. The compromised data comprises Vendor, Customer, and Employee information, encompassing Display Name, Company Name, Title, First Name, Middle Name, Last Name, Email Address, Mobile Number, Phone Number, Fax Number, Billing Address, and other sensitive and confidential details. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as ‘Sedapmalam’ poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by ‘Sedapmalam’ typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data leak related to The Post Millennial(www[.]thepostmillennial[.]com). The Post Millennial is a media and internet platform that provides various reports on issues such as Canadian politics, business, local provincial news, analysis coverage, and opinion pieces. The breached data includes sensitive information such as Emails, Usernames, Full Names, Display Names, Phone Numbers, and other confidential details. The volume of the breached data stands at 7.5 gigabytes.
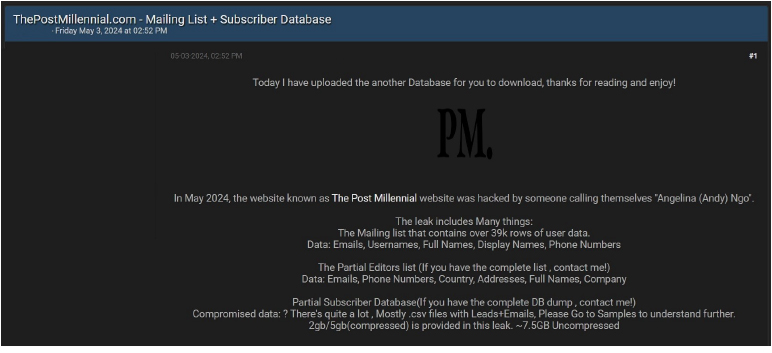
Source: Underground forums
ETLM Assessment:
DevEye threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
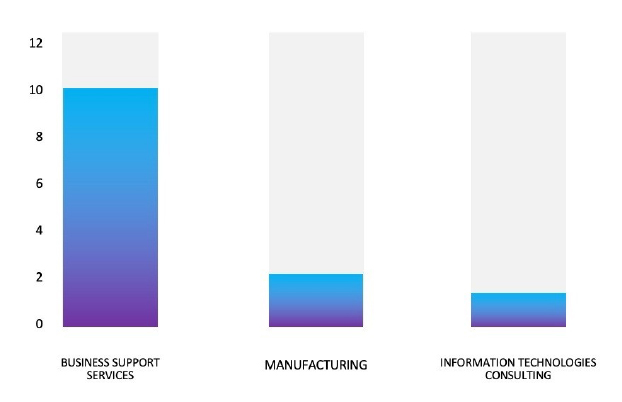
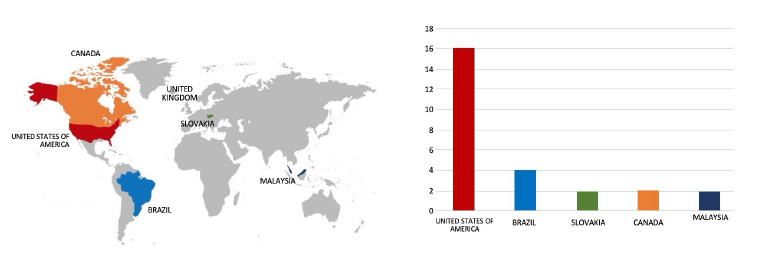
Please find the Geography – Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.