



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found RdpLocker Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
RdpLocker Ransomware
CYFIRMA Researchers recently identified the RdpLocker ransomware.
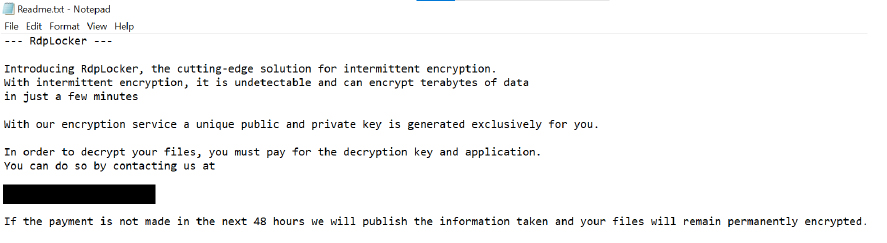
RdpLocker is a ransomware variant that encrypts files on a victim’s system, appending the “.RdpLocked” extension to the original filenames. It leaves behind a ransom note titled “Readme.txt,” containing contact details and instructions for file recovery.
The ransomware additionally alters the desktop wallpaper.
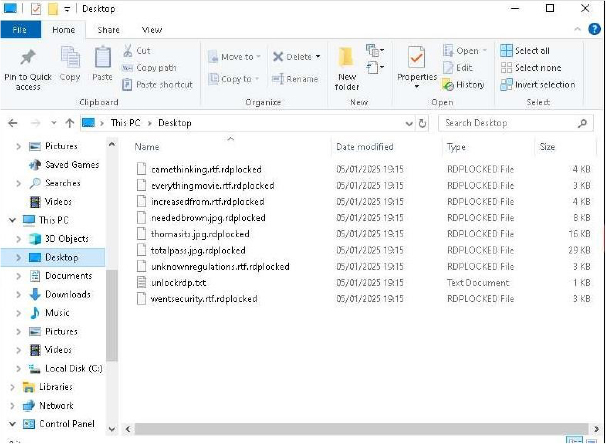
The ransom note informs victims that RdpLocker employs advanced intermittent encryption, enabling it to encrypt large volumes of data efficiently. It explains that a unique public-private key pair has been generated for the victim.
To regain access to their files, victims are instructed to purchase the decryption key and application by contacting the attackers. The note further threatens that failure to pay within 48 hours will result in the publication of the stolen data, leaving the encrypted files permanently inaccessible.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | ID | Technique/ Sub-Technique |
| Execution | T1106 | Native API |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution : Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Command and Control |
T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment predicts a potential escalation in RdpLocker ransomware activities worldwide, targeting key sectors such as manufacturing, finance, and healthcare. These industries, reliant on critical infrastructure and sensitive data, present lucrative opportunities for attackers. Mitigating these threats requires implementing robust cybersecurity measures, including advanced endpoint protection, regular data backups, proactive network monitoring, and comprehensive employee awareness training.
Sigma Rule
title: CurrentVersion Autorun Keys Modification tags:
– attack.persistence
– attack.t1547.001 logsource:
category: registry_set product: windows
detection: current_version_base:
TargetObject|contains: ‘\SOFTWARE\Microsoft\Windows\CurrentVersion’ current_version_keys:
TargetObject|contains:
– ‘\ShellServiceObjectDelayLoad’
– ‘\Run\’
– ‘\RunOnce\’
– ‘\RunOnceEx\’
– ‘\RunServices\’
– ‘\RunServicesOnce\’
– ‘\Policies\System\Shell’
– ‘\Policies\Explorer\Run’
– ‘\Group Policy\Scripts\Startup’
– ‘\Group Policy\Scripts\Shutdown’
– ‘\Group Policy\Scripts\Logon’
– ‘\Group Policy\Scripts\Logoff’
– ‘\Explorer\ShellServiceObjects’
– ‘\Explorer\ShellIconOverlayIdentifiers’
– ‘\Explorer\ShellExecuteHooks’
– ‘\Explorer\SharedTaskScheduler’
– ‘\Explorer\Browser Helper Objects’
– ‘\Authentication\PLAP Providers’
– ‘\Authentication\Credential Providers’
– ‘\Authentication\Credential Provider Filters’
filter_all:
– Details: ‘(Empty)’
– TargetObject|endswith: ‘\NgcFirst\ConsecutiveSwitchCount’
– Image|endswith:
– ‘\AppData\Local\Microsoft\OneDrive\Update\OneDriveSetup.exe’ # C:\Users\*\AppData\Local\Microsoft\OneDrive\Update\OneDriveSetup.exe
– ‘\AppData\Roaming\Spotify\Spotify.exe’
– ‘\AppData\Local\WebEx\WebexHost.exe’
– Image:
– ‘C:\WINDOWS\system32\devicecensus.exe’
– ‘C:\Windows\system32\winsat.exe’
– ‘C:\Program Files\Microsoft OneDrive\StandaloneUpdater\OneDriveSetup.exe’
– ‘C:\Program Files\Microsoft OneDrive\Update\OneDriveSetup.exe’
– ‘C:\Program Files (x86)\Microsoft OneDrive\Update\OneDriveSetup.exe’
– ‘C:\Program Files\KeePass Password Safe 2\ShInstUtil.exe’
– ‘C:\Program Files\Everything\Everything.exe’
– ‘C:\Program Files (x86)\Microsoft Office\root\integration\integrator.exe’ filter_logonui:
Image: ‘C:\Windows\system32\LogonUI.exe’ TargetObject|contains:
– ‘\Authentication\Credential Providers\{D6886603-9D2F-4EB2-B667- 1971041FA96B}\’ # PIN
– ‘\Authentication\Credential Providers\{BEC09223-B018-416D-A0AC- 523971B639F5}\’ # fingerprint
– ‘\Authentication\Credential Providers\{8AF662BF-65A0-4D0A-A540- A338A999D36F}\’ # facial recognizion
– ‘\Authentication\Credential Providers\{27FBDB57-B613-4AF2-9D7E- 4FA7A66C21AD}\’ # Trusted Signal (Phone proximity, Network location)
filter_edge:
Image|startswith:
– ‘C:\Program Files (x86)\Microsoft\EdgeUpdate\Install\’
– ‘C:\Program Files (x86)\Microsoft\EdgeWebView\’
– ‘C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe’
filter_dropbox:
Image: ‘C:\Windows\system32\regsvr32.exe’ TargetObject|contains: ‘DropboxExt’ Details|endswith: ‘A251-47B7-93E1-CDD82E34AF8B}’
filter_opera:
TargetObject|endswith: ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Opera Browser Assistant’
Details: ‘C:\Program Files\Opera\assistant\browser_assistant.exe’ filter_itunes:
TargetObject|endswith: ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\iTunesHelper’
Details: ‘”C:\Program Files\iTunes\iTunesHelper.exe”‘ filter_zoom:
TargetObject|endswith:
‘\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\zoommsirepair’
Details: ‘”C:\Program Files\Zoom\bin\installer.exe” /repair’ filter_greenshot:
TargetObject|endswith: ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Greenshot’
Details: ‘C:\Program Files\Greenshot\Greenshot.exe’ filter_googledrive1:
TargetObject|endswith: ‘\Software\Microsoft\Windows\CurrentVersion\Run\GoogleDriveFS’
Details|startswith: ‘C:\Program Files\Google\Drive File Stream\’ Details|contains: ‘\GoogleDriveFS.exe’
filter_googledrive2: TargetObject|contains: ‘GoogleDrive’ Details:
– ‘{CFE8B367-77A7-41D7-9C90-75D16D7DC6B6}’
– ‘{A8E52322-8734-481D-A7E2-27B309EF8D56}’
– ‘{C973DA94-CBDF-4E77-81D1-E5B794FBD146}’
– ‘{51EF1569-67EE-4AD6-9646-E726C3FFC8A2}’
filter_onedrive:
Details|startswith:
– ‘C:\Windows\system32\cmd.exe /q /c rmdir /s /q “C:\Users\’
– ‘C:\Windows\system32\cmd.exe /q /c del /q “C:\Users\’ Details|contains: ‘\AppData\Local\Microsoft\OneDrive\’
filter_python:
TargetObject|contains: ‘\Microsoft\Windows\CurrentVersion\RunOnce\{‘ Details|contains|all:
– ‘\AppData\Local\Package Cache\{‘
– ‘}\python-‘
Details|endswith: ‘.exe” /burn.runonce’ filter_officeclicktorun:
Image|startswith:
– ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\’
– ‘C:\Program Files\Common Files\Microsoft Shared\ClickToRun\Updates\’
Image|endswith: ‘\OfficeClickToRun.exe’
filter_defender:
Image: ‘C:\Program Files\Windows Defender\MsMpEng.exe’ filter_teams:
Image|endswith: ‘\Microsoft\Teams\current\Teams.exe’ Details|contains: ‘\Microsoft\Teams\Update.exe –processStart ‘
filter_ctfmon:
Image: ‘C:\Windows\system32\userinit.exe’ Details: ‘ctfmon.exe /n’
filter_AVG:
Image|startswith: ‘C:\Program Files\AVG\Antivirus\Setup\’ Details:
– ‘”C:\Program Files\AVG\Antivirus\AvLaunch.exe” /gui’
– ‘”C:\Program Files (x86)\AVG\Antivirus\AvLaunch.exe” /gui’
– ‘{472083B0-C522-11CF-8763-00608CC02F24}’
filter_aurora_dashboard: Image|endswith:
– ‘\aurora-agent-64.exe’
– ‘\aurora-agent.exe’
TargetObject|endswith: ‘\Microsoft\Windows\CurrentVersion\Run\aurora- dashboard’
Details: ‘C:\Program Files\Aurora-Agent\tools\aurora-dashboard.exe’ filter_everything:
TargetObject|endswith: ‘\Microsoft\Windows\CurrentVersion\Run\Everything’
Details|endswith: ‘\Everything\Everything.exe” -startup’ # We remove the starting part as it could be installed in different locations
condition: all of current_version_* and not 1 of filter_* falsepositives:
– Legitimate software automatically (mostly, during installation) sets up autorun keys for legitimate reason
– Legitimate administrator sets up autorun keys for legitimate reason level: medium
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Backdoor | Objectives: Espionage, Data theft, Remote Access| Target Technology: Windows OS | Target Organizations: Internet Service Providers (ISPs) & Government | Target Geography: Middle East
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “EAGERBEE” is trending.
EAGERBEE
Researchers discovered a new variant of the EAGERBEE backdoor targeting ISPs and governmental entities in the Middle East. EAGERBEE is sophisticated malware that incorporates advanced components, including a unique service injector designed to embed the backdoor into active services. Subsequent analysis revealed previously undocumented plugins deployed after the backdoor’s installation, enabling a wide range of malicious activities. These included deploying additional payloads, accessing file systems, executing command shells, and more. The plugins were categorized by functionality into groups such as Plugin Orchestrator, File System Manipulation, Remote Access Manager, Process Exploration, Network Connection Listing, and Service Management.
Attack Method
The exact method used by attackers to gain initial access remains unknown. In earlier incidents, attackers exploited the Microsoft Exchange ProxyLogon vulnerability (CVE-2021- 26855) to gain access. In this case, researchers observed the attackers executing commands to deploy a backdoor injector, “tsvipsrv.dll,” alongside the payload file “ntusers0.dat.” The SessionEnv service was then utilized to execute the injector. The service injector is designed to target the Themes service, enabling it to deploy the EAGERBEE backdoor. It loads the backdoor into memory from a file and uses a small piece of code to activate it within the service process. Once the backdoor is successfully injected and operational, the injector ensures everything appears normal by cleaning up and restoring the service to its original state.
Following this initial deployment, the EAGERBEE backdoor, identified as “dllloader1x64.dll” on infected systems, exhibited advanced capabilities. It began by gathering critical system details such as the computer’s NetBIOS name, OS version, processor architecture, and IP addresses. The backdoor includes a built-in mechanism to check the day and time before executing. It compares the current system day and hour to a predefined schedule, where “0” represents the start of the week, “6” the end, “00” the start hour, and “23” the end hour. If the current time doesn’t match the hardcoded schedule, the backdoor pauses for 15 seconds before checking again. However, in observed instances, it was configured to operate continuously, running 24/7. Its configuration, either stored in a public directory or hardcoded, included the command-and-control (C2) server details, which guided its next steps.
The backdoor further established communication with the C2 server by creating a TCP socket and adapting to proxy settings if available. Once connected, it transmitted the collected system information to the server, which responded with a payload known as the Plugin Orchestrator. Carefully designed, the backdoor activated this payload only after verifying it against a unique hardcoded value, ensuring precise execution while keeping its activities stealthy. This seamless chain of infection highlights the attackers’ sophistication and their focus on persistence and stealth.
Plugin Orchestrator
The EAGERBEE backdoor downloads a payload called the Plugin Orchestrator, a DLL file known as “ssss.dll.” This orchestrator is responsible for managing and executing various tasks on the compromised system. Once activated, it collects detailed system information, such as:
After gathering this data, the orchestrator reports it to the attackers’ command-and- control server. It also checks whether the current process has elevated privileges, and then gathers more detailed information about running processes, including:
Once the information is transmitted, the orchestrator awaits further commands from the attackers to carry out additional actions on the system.
Plugins
The EAGERBEE backdoor uses plugins in the form of DLL files, each of which contains three key methods. The plugin orchestrator first loads the plugin into memory and then initializes it by setting up necessary structures. Finally, the orchestrator activates the plugin’s core functionality. Each of the plugins is responsible for receiving and carrying out commands from the orchestrator, allowing the attackers to perform various malicious tasks on the infected system.
File Manager Plugin – This plugin carries out a variety of file system tasks, such as listing drives, files, and folders on the system. It also supports actions like renaming, moving, copying, and deleting files, as well as adjusting file and folder permissions through ACLs. Additionally, the plugin can read from and write files to the system, and even inject additional payloads into memory.
Process Manager – This plugin handles various process-related tasks, including listing active processes on the system, launching new modules and executing command-line commands, and terminating running processes.
Remote Access Manager – This plugin enables and maintains remote connections, allowing attackers to gain command shell access to the infected system. The attackers initiate the command shell by injecting cmd.exe into the DllHost.exe process.
Service Manager – This plugin oversees system services, handling tasks such as installing, starting, stopping, deleting, and listing them.
Network Manager – This plugin provides a list of the network connections active on the system.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the EAGERBEE malware is expected to become increasingly pervasive and sophisticated in the coming years. Attackers will likely continue refining their tactics, focusing on stealth and persistence to avoid detection. While it currently targets ISPs and governmental entities in the Middle East, EAGERBEE may expand its reach to encompass a wider range of industries and geographical regions. As the malware evolves, it could adapt its methods of infiltration, potentially compromising a broader spectrum of sectors worldwide. With the growing complexity of both legacy and modern systems, EAGERBEE’s advanced components, such as service injectors and plugins, could enable attackers to bypass emerging security measures, resulting in more frequent and successful breaches. In light of the expanding interconnectedness of systems worldwide, organizations will be required to reassess and strengthen their cybersecurity strategies to address these increasingly sophisticated and evolving threats.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
UNC3569: A Persistent Cyber Threat Actor with Ties to China
SUMMARY
UNC3569 is a China-nexus cyber threat actor that has targeted sectors including telecommunications, energy, technology, and gaming since at least June 2023. Its activities align with Chinese state intelligence priorities, particularly surveillance of Hong Kong democracy activists and gathering industrial intelligence. The group’s operations, which utilize advanced malware and novel infrastructure tactics, suggest a focus on intelligence collection and counterintelligence. While historical evidence ties the group to activities from 2021, its ongoing evolution in tactics signals long-term strategic goals.
UNC3569 has focused its operations in regions such as Taiwan, Indonesia, and Hong Kong. Intrusions into telecommunications networks, specifically targeting Call Data Records (CDRs), demonstrate the group’s interest in critical intelligence. In December 2024, UNC3569 advanced its operations by using the KEYPLUG malware family, incorporating new domains and leveraging Gcore Labs CDN for obfuscation, a tactic uncommon among similar threat actors.
The attack lifecycle includes reconnaissance, likely through commands like “net group,”and potential weaponization through tailored payloads. Delivery mechanisms are speculated to include spear-phishing emails and supply chain compromises. For exploitation, specific methods remain unidentified, but installation involves deploying malware families such as KEYPLUG, ShadowPad, PlugX, TumbleDown, and others for persistence and lateral movement. Command-and- control infrastructure is managed via ORB networks, with domains registered through providers that mask their activities.
The group’s strategic objectives focus on monitoring dissidents, gathering intelligence from key sectors, and accessing telecommunications data for counterintelligence
Insights and Relevancy:
UNC3569’s past attacks trace back to 2021, with evidence linking the group to espionage operations targeting telecommunications, technology, and energy sectors, alongside surveillance of Hong Kong democracy activists. These initial operations often involved deploying sophisticated malware like ShadowPad and PlugX, which enabled remote access and persistence within compromised networks. The group’s primary objective was intelligence gathering, particularly from high-value sectors that align with Chinese government interests.
The most recent activities in December 2024, including the use of KEYPLUG malware and new command-and-control infrastructure, show a clear continuation of UNC3569’s strategic objectives. The group’s evolving tactics—like leveraging Gcore Labs CDN to obfuscate operations—reflect a shift towards more advanced operational security measures. This is consistent with their historical pattern of adapting to detection and enhancing the stealth of their intrusions.
By maintaining a focus on sectors such as telecommunications and energy, as seen in prior attacks, UNC3569’s activities align with their broader goal of acquiring sensitive information for Chinese state interests. The use of tailored malware and infrastructure techniques in both past and current campaigns highlight the group’s sustained and evolving threat.
ETLM:
UNC3569 is a China-nexus threat actor focused on intelligence collection and counterintelligence, aligning with Chinese state priorities. Their targets include Taiwan, Indonesia, and Hong Kong, with a particular focus on Hong Kong democracy activists. The group primarily targets industries such as telecommunications, energy, technology, and gaming, often aiming to access sensitive information, including Call Data Records (CDRs) from telecommunications networks.
UNC3569 has used various malware families over time, including KEYPLUG (its primary command-and-control tool), ShadowPad, PlugX, and TumbleDown for persistence and lateral movement. They employ novel techniques, like using legitimate infrastructure (e.g., Gcore Labs CDN), to obfuscate their operations and evade detection.
The group’s evolving tactics suggest a shift towards more sophisticated and stealthy operations. Moving forward, UNC3569 is expected to continue refining its strategies, particularly in high-priority geopolitical regions. Organizations in targeted sectors must bolster defenses, focusing on detection, malware defense, and threat intelligence sharing.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE FRAMEWORK | ||
| Tactic | Technique ID | Technique |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1046 | Network Service Discovery |
| Lateral Movement | T1021 | Remote Services |
| Collection | T1213 | Data from Information Repositories |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1485 | Data Destruction |
New Details on Chinese Breach of US Treasury Department
Media reports revealed that Chinese hackers infiltrated workstations in the US Treasury Department’s Office of Foreign Assets Control (OFAC) and the Office of the Treasury Secretary. OFAC oversees the enforcement of economic sanctions on foreign entities and individuals. Beijing likely sought information on potential sanctions targeting Chinese entities which are helping Russia, Iran and Venezuela circumvent US sanctions. The breach, which occurred last month, was facilitated by the hackers acquiring an API key for BeyondTrust’s Remote Support SaaS product. According to the Treasury Department, the attackers accessed unclassified information from the compromised systems.
ETLM Assessment:
The revelation that Beijing successfully targeted the core of America’s federal system comes as the government struggles to also address widespread and coordinated cyberattacks on U.S. telecommunications networks by Chinese- backed groups. Hackers, including those from Salt Typhoon, infiltrated telecom systems to access call data and text messages of an undetermined number of Americans. To date, Chinese hacking groups have been identified within at least nine U.S. telecom networks.
The reported Chinese espionage targeting U.S. telecoms and the Treasury Department follows a period of relative calm in U.S.-China relations during the closing phase of President Joe Biden’s term. This period of improved ties included a meeting between Biden and Chinese President Xi Jinping at the APEC summit in Peru last month, a rare prisoner exchange in late November, and a renewed agreement on science and technology cooperation earlier this month. However, Beijing continues to deny its responsibility for the cyber-attacks.
US telecoms say they’ve contained China’s Salt Typhoon attacks, new Volt Typhoon activity
AT&T and Verizon say they’ve completely ejected China’s Salt Typhoon hackers from their networks, after weeks of presence by Chinese attackers, who were able to access data belonging to millions of Americans. Meanwhile, the office of US deputy national security adviser for cyber and emerging technology, said that a ninth telecom company discovered it was breached by the campaign without naming the company. The breach was found after the federal government issued a guide to help telecoms identify Salt Typhoon’s TTPs.
Meanwhile researchers have published new findings on the Chinese APT Volt Typhoon and its hack of Guam’s Power Authority (GPA) from 2022. GPA is the only power utility on the US island territory and is crucial for US military operations. The threat actor used unique strains of malware to infiltrate it as well as numerous other entities on the island and worryingly has reportedly gained access to sensitive defense networks meant to be impregnable.
ETLM Assessment:
Last year campaigns by Volt Typhoon and Salt Typhoon have been focused on the countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has been especially targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. As we have warned in an earlier report, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way it could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting of critical infrastructure on Guam could affect U.S. military operations in significant ways.
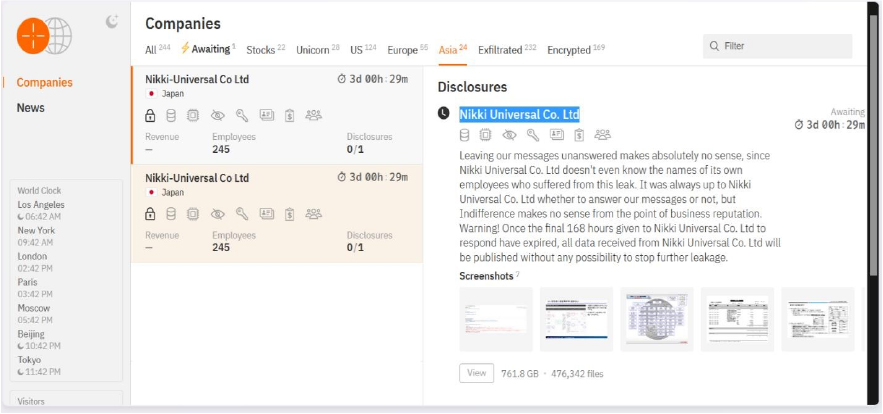
The Hunters International Ransomware Impacts Nikki-Universal Co Ltd
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Nikki-Universal Co Ltd(www[.]n-u[.]co[.]jp), was compromised by Hunters International Ransomware. Nikki-Universal Co., Ltd. (N-U) is a manufacturer and sells Refining & Petrochemical catalysts for UOP processes and environmentally friendly catalysts. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The scale of the data exposure measures approximately 761.8 GB, comprising a total of 4,76,342 discrete files.
Relevancy & Insights:
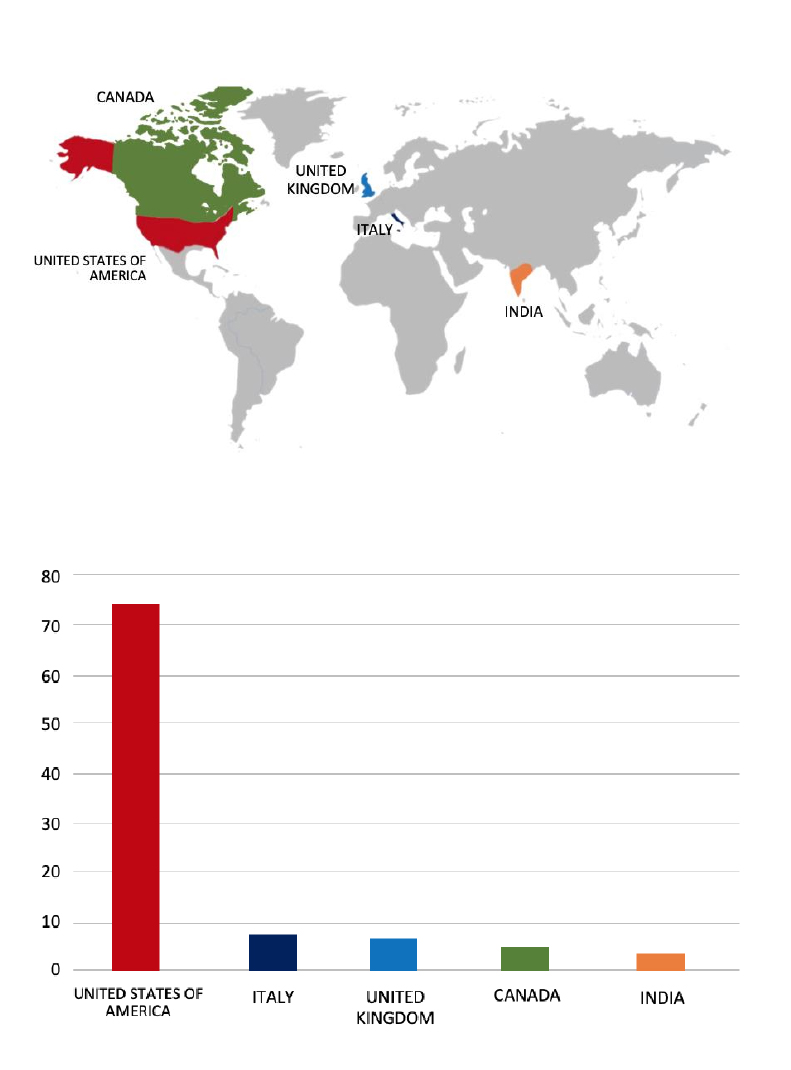
ETLM Assessment:
According to CYFIRMA’s assessment, Hunters International ransomware represents a significant threat within the ransomware landscape due to its sophisticated tactics and focus on double extortion strategies. Organizations are advised to enhance their cybersecurity measures by implementing robust backup solutions, conducting regular employee training on phishing awareness, and maintaining updated security protocols to mitigate risks associated with this evolving threat actor. Continuous monitoring of Hunters International’s activities will be essential for understanding its impact on global cybersecurity efforts.
The RansomHub Ransomware Impacts PSC Corporation
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; PSC Corporation (www[.]psccorporation[.]com), was compromised by RansomHub ransomware. PSC Corporation manufactures, distributes, and markets a diverse range of quality and value-for-money consumer products for everyday needs. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 378 GB.
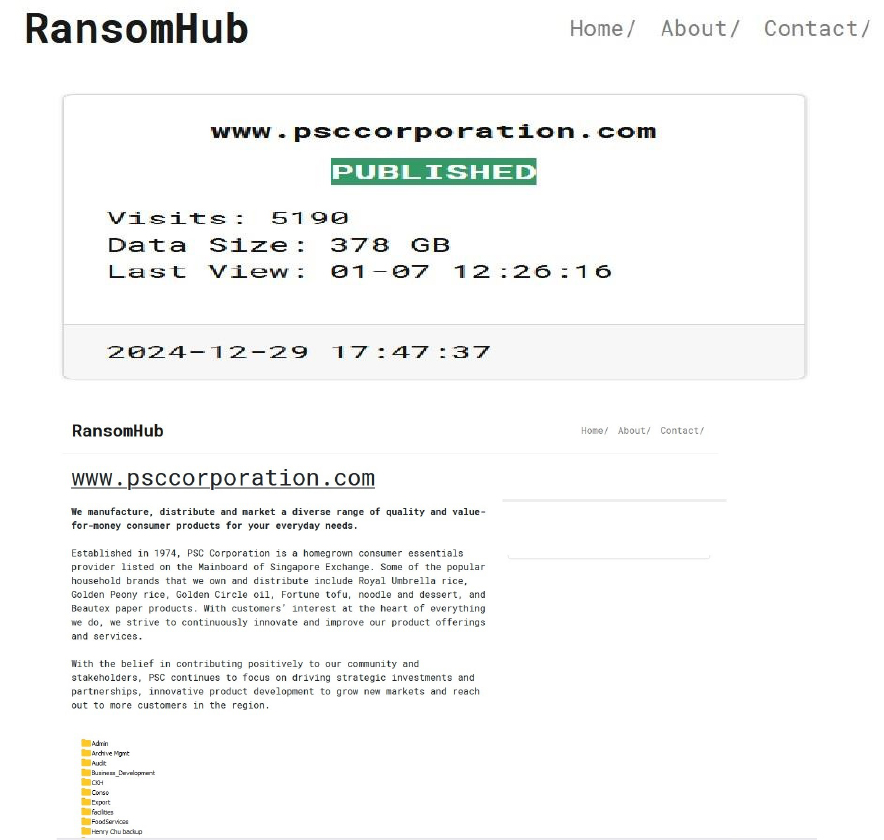
Relevancy & Insights:
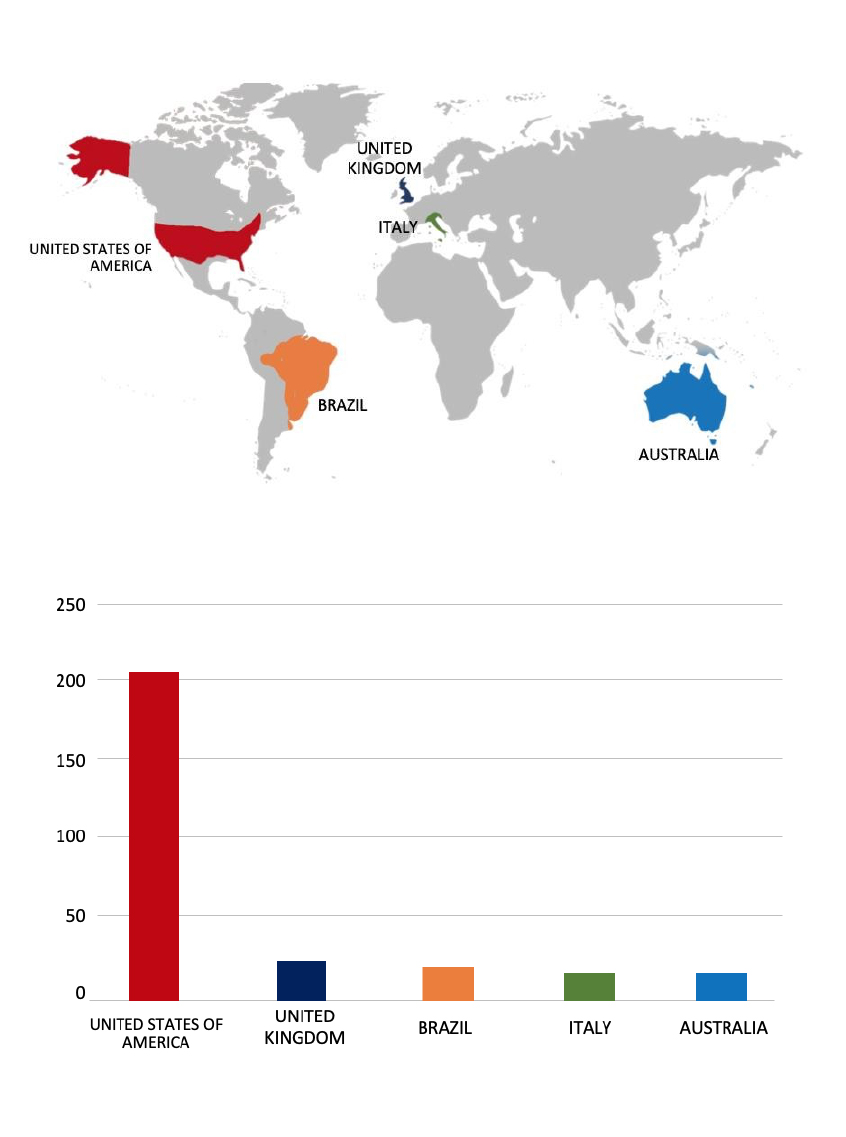
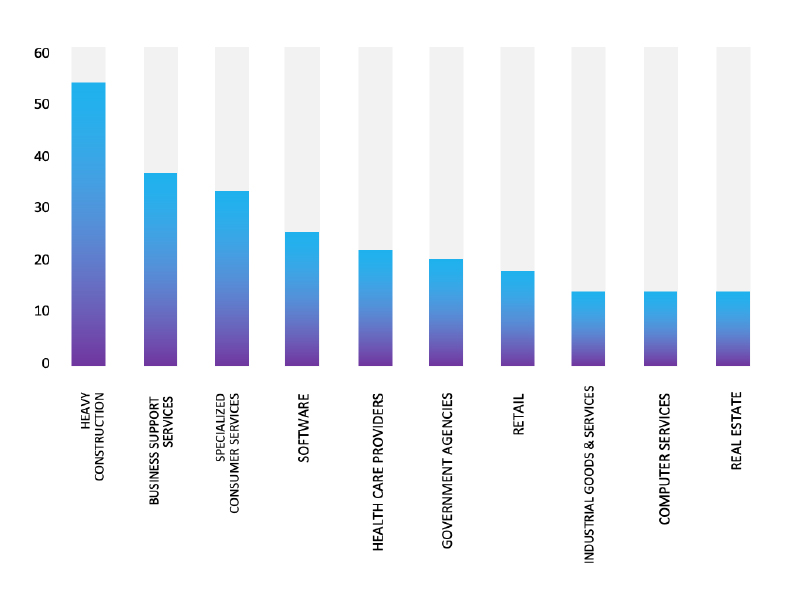
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on PSC Corporation, a prominent Manufacturing company from Singapore, highlighting RansomHub’s significant threat presence in Southeast Asia.
Vulnerability in SakolaWP Plugin
Relevancy & Insights: This is due to the registration function not properly limiting what roles a user can register as.
Impact: Succesful exploitation of the vulnerability makes it possible for unauthenticated attackers to register as an administrative user.
Affected Products: https[:]//www[.]wordfence[.]com/threat- intel/vulnerabilities/wordpress-plugins/sakolawp-lite/school-management-system- sakolawp-108-unauthenticated-privilege-escalation
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
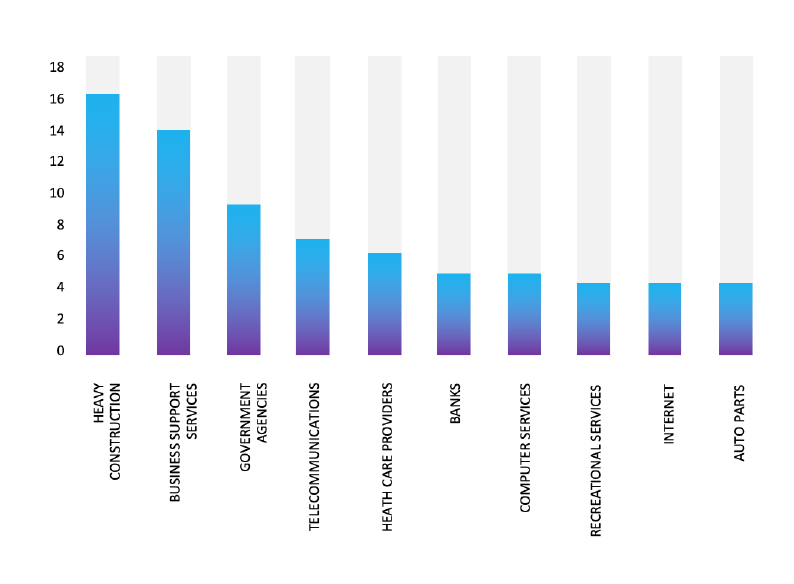
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
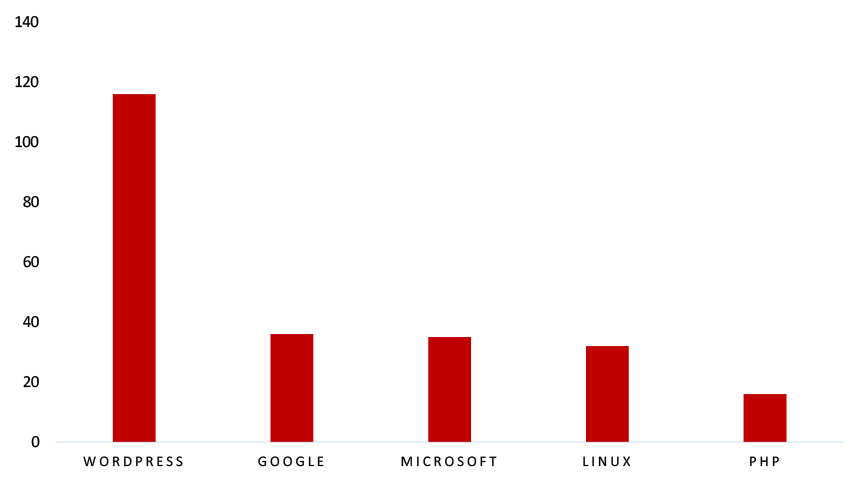
ETLM Assessment
Vulnerability in SakolaWp, a WordPress School Management System plugin, can pose significant threats to user privacy and security. This can impact educational institutions globally, including schools, colleges, and training centers. Ensuring the security of SakolaWp is crucial for maintaining the integrity and protection of sensitive data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding the management of daily school activities, including classes, teachers, students, parents, attendance, exams, and other critical operations, across different geographic regions and sectors.
APT 73 Ransomware attacked and published the data of Bank Rakyat Indonesia (BRI)
Summary:
Recently, we observed that APT 73 Ransomware attacked and published the data of Bank Rakyat Indonesia (BRI)(www[.]bri[.]co[.]id) on its dark web website. Bank Rakyat Indonesia (BRI) is one of Indonesia’s oldest and largest banks, focusing on microfinance and serving the country’s rural and urban communities. The ransomware attack resulted in a data leak containing confidential and sensitive organizational information. The compromised data was subsequently sold to a third party by the APT 73 ransomware group.
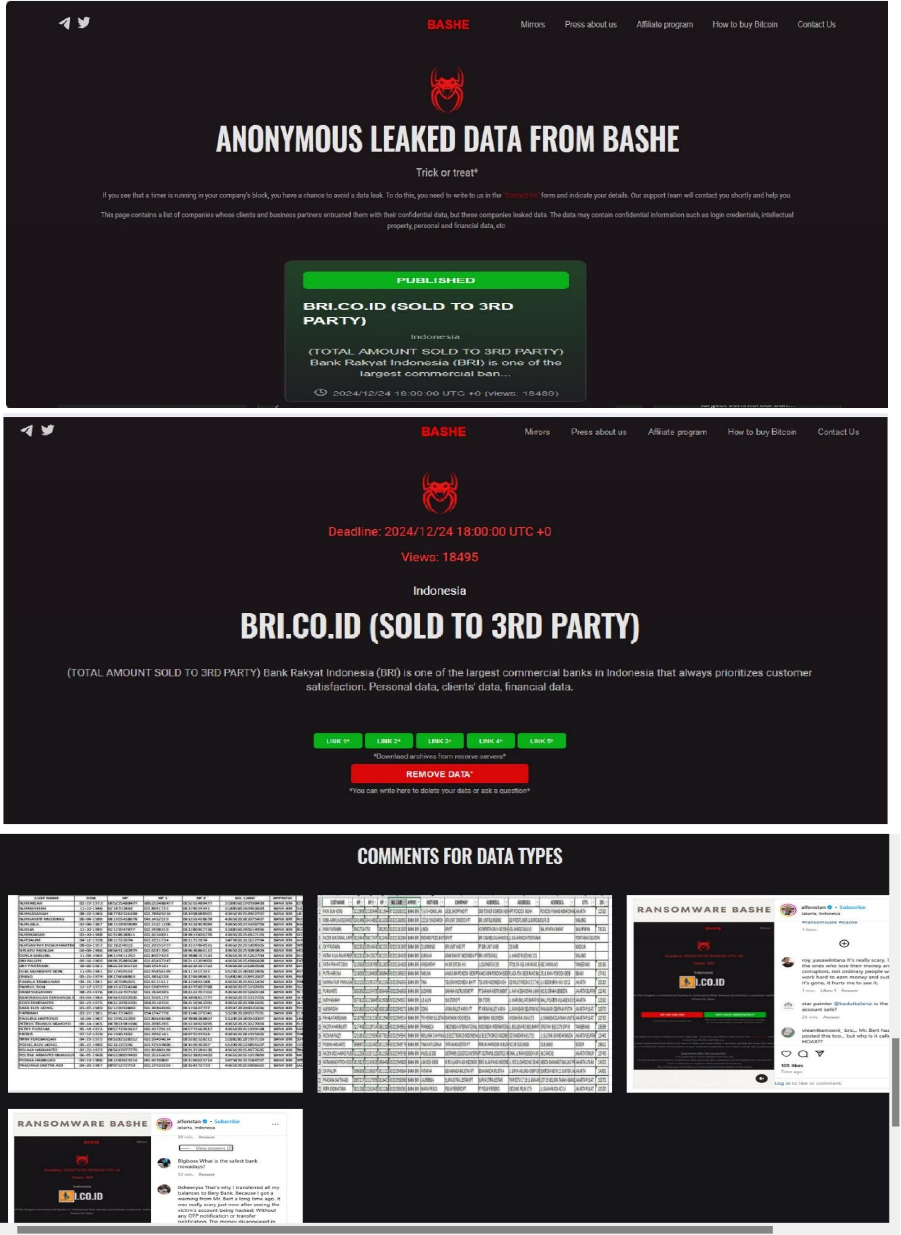
Relevancy & Insights:
ETLM Assessment:
APT73 Ransomware represents a significant addition to the roster of active ransomware groups, leveraging tactics reminiscent of more established players like LockBit while targeting business services across multiple countries. Organizations are advised to implement robust cybersecurity measures, including regular updates and employee training on recognizing phishing attempts, to mitigate risks associated with this emerging threat actor.
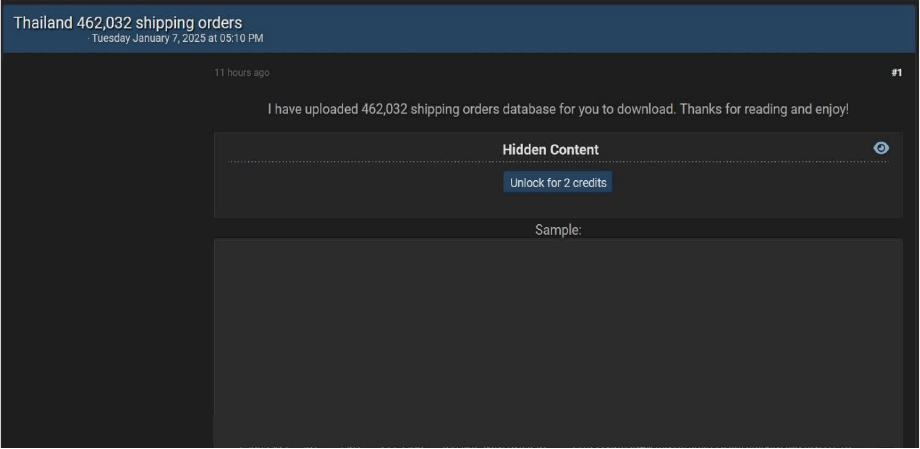
Thailand Shipping Order Data Advertised on a Leak Site
Summary: A significant data breach allegedly exposed over 462,000 shipping order records in Thailand, raising serious concerns about the security of logistics systems and the privacy of customer information.
The leaked records reportedly contain sensitive details related to shipping orders, potentially including customer names, addresses, and order tracking information. Such an incident highlights vulnerabilities within logistics networks and underscores the critical need for robust cybersecurity measures in the shipping and transportation sector.
The breach has been linked to a threat actor identified as “Ddarknotevil.”
Persatuan Dokter Gigi Indonesia Data Advertised on a Leak Site
Summary:
A data breach claims to expose sensitive information from the database of the Indonesian Dental Association (Persatuan Dokter Gigi Indonesia). The Persatuan Dokter Gigi Indonesia (PDGI), or Indonesian Dental Association, is the sole professional organization representing dentists across Indonesia. This raises concerns about the privacy and security of professional and personal data.

Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat actor “Ddarknotevil” represents a notable threat within the cybercriminal landscape, particularly through their involvement in high-profile data breaches and sales of stolen information. Organizations are urged to enhance their cybersecurity defenses and remain vigilant against such threats to safeguard their sensitive data and maintain customer trust. Continuous monitoring of threat actors like Ddarknotevil is essential for effective incident response strategies in an evolving cyber threat environment.
Recommendations: Enhance the cybersecurity posture by:
Recently, a data breach has allegedly compromised the database of the Philippine Statistical Association Inc. (PSAI), raising serious concerns about the security of institutional data. The breach reportedly includes sensitive information that could impact organizational operations and the privacy of individuals associated with PSAI.
Incidents like this underline the vulnerability of institutional databases to cyberattacks, especially in the absence of robust security measures. The potential misuse of leaked data poses significant risks, including identity theft, financial fraud, and reputational damage.
Organizations are encouraged to strengthen their cybersecurity frameworks by employing advanced encryption techniques, conducting regular security audits, and fostering a proactive approach to data protection. Affected individuals should remain vigilant for potential unauthorized access to their personal or professional data.
This breach serves as a wake-up call for institutions to prioritize data security and adopt comprehensive measures to mitigate risks in an increasingly digital world. The breach has been linked to a threat actor identified as “Hagsg.”
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
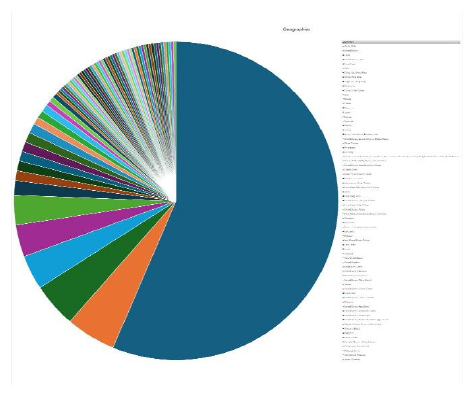
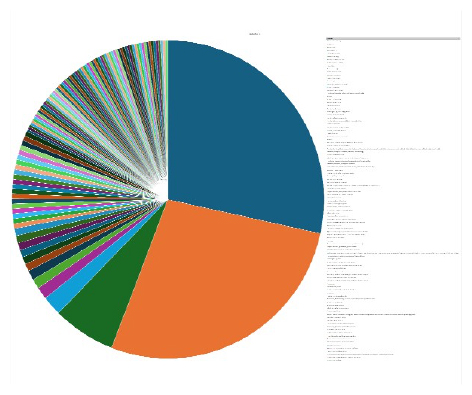
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.