


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found LockZ Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
LockZ Ransomware
LockZ is a ransomware strain that encrypts files and appends the “.lockz” extension to affected files. It also modifies the desktop wallpaper and places a ransom note named “@[email protected]”
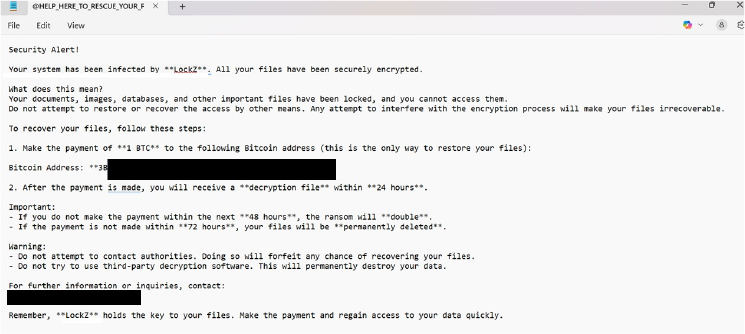
The ransom note informs victims that their system has been compromised and that all files—including documents, images, and databases—have been encrypted. It warns against self-recovery attempts, claiming such actions could result in permanent file loss.
To regain access, victims are instructed to pay 1 BTC to a designated Bitcoin address. Attackers promise to provide a decryption file within 24 hours of payment. The ransom will reportedly double if not paid within 48 hours, and files are said to be permanently deleted after 72 hours.
The note discourages contacting law enforcement or using third-party recovery tools and includes an email address for further communication.

Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.001 | PowerShell |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| PrivilegeEscalation | T1055 | Process Injection |
| PrivilegeEscalation | T1055.003 | Thread Execution Hijacking |
| PrivilegeEscalation | T1547 | Boot or Logon Autostart Execution |
| PrivilegeEscalation | T1547.001 | Registry Run Keys / Startup Folder |
| PrivilegeEscalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Software Packing |
| Defense Evasion | T1027.004 | Compile After Delivery |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1055.003 | Thread Execution Hijacking |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Bootkit |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hidden Files and Directories |
| Defense Evasion | T1564.003 | Hidden Window |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Defense Evasion | T1620 | Reflective Code Loading |
| CredentialAccess | T1003 | OS Credential Dumping |
| CredentialAccess | T1539 | Steal Web Session Cookie |
| CredentialAccess | T1552 | Unsecured Credentials |
| CredentialAccess | T1552.001 | Credentials In Files |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | System Checks |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s prediction, based on available intelligence, indicates that LockZ ransomware is poised to become a more evasive and persistent threat in the near future. Its focus on the widely deployed Windows platform, combined with high ransom demands, suggests a clear targeting of enterprises in sectors such as finance, healthcare, and manufacturing. The ransomware’s capabilities—including debug environment detection and extended sleep intervals—highlight its growing sophistication and intent to evade analysis and delay detection. These features increase the likelihood of successful encryption before intervention, underscoring the need for heightened vigilance and proactive defense across critical industries.
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule
title: Dot net compiler compiles file from suspicious location threatname:
behaviorgroup: 1
classification: 7 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*\windows\microsoft.net\framework*\csc.exe*/noconfig
/fullpaths*\appdata\local\temp*’ condition: selection
level: high
(Source: Surface web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer | Objectives: Stealing sensitive information, Data exfiltration | Target Technology: Windows OS | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Gremlin Stealer” is trending.
Gremlin Stealer
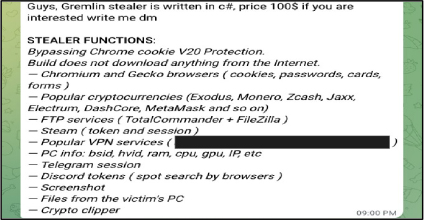
Researchers have uncovered a newly emerging malware known as Gremlin Stealer, a C#-based information stealer that has been making waves since mid-March 2025. The malware’s operators have been actively promoting it through Telegram, signaling a clear intent to attract cybercriminals seeking powerful data theft tools. Gremlin Stealer is designed to quietly infiltrate victims’ systems and extract a broad range of personal and sensitive information. This includes browser cookies, credit card details, clipboard content, crypto wallet data, and credentials for services like FTP and VPNs. Once collected, the stolen information is sent to a remote server controlled by the attackers, where it can be viewed, shared, or potentially sold. The rise of Gremlin Stealer highlights the continued evolution of information-stealing malware and the growing role of online platforms like Telegram in facilitating malicious activity.
Gremlin Stealer – Sales and Advertisement on Telegram
Gremlin Stealer claims to be capable of extracting data from a wide variety of software applications, positioning itself as a versatile tool for information theft. It is actively promoted through a Telegram channel, where its authors regularly share updates, highlighting that the malware is still under active development. A promotional post on this channel showcases Gremlin Stealer’s capabilities and serves as a central hub for its distribution, signaling ongoing efforts to expand its reach among cybercriminal circles.
Technical Analysis
The initial infection vector for Gremlin Stealer remains unknown. However, the malware is advertised as being capable of targeting a wide range of applications to extract sensitive user data. Ongoing updates shared via Telegram indicate that the stealer is under active development, with its capabilities likely to expand over time. The following are the stealer’s functions:
Basic features include:
Stealing functionality targets the following:
Bypassing Chrome cookie V20 protection
One of the key features highlighted for Gremlin Stealer is its ability to bypass Chrome’s cookie v20 protection, allowing it to access cookie-related data despite Google’s security updates aimed at blocking such techniques. This method, commonly seen in other stealers, enables Gremlin to retrieve sensitive browser information. Once collected, the stolen cookies—along with details like domain, name, value, path, and expiration date—are written into a text file stored in the LOCAL\_APP\_DATA folder. This file is then prepared for upload to the malware’s server.
Chromium and Gecko Browsers
Gremlin Stealer is designed to search for cookies and saved passwords across a wide range of Chromium- and Gecko-based browsers. Once collected, this data is written into a file for later exfiltration. To handle newer security measures like Chrome’s “v20” cookie encryption, the malware uses a specific function to bypass these protections in Chromium- based browsers, with a similar mechanism in place for Gecko-based browsers as well.
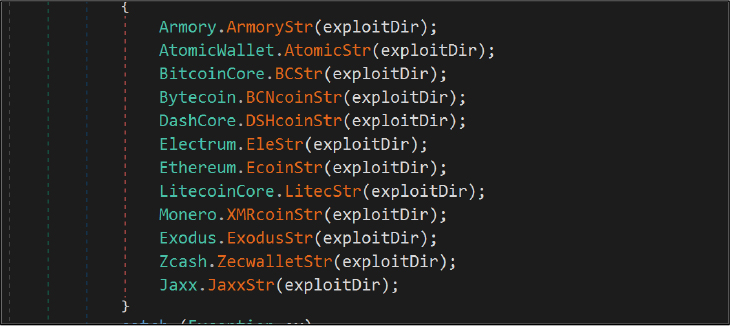
Cryptocurrency Wallet Stealer
Gremlin Stealer targets various cryptocurrency wallets by scanning specific directories for related files. For instance, when looking for a Litecoin wallet, it checks the system registry, and if a match is found, it copies the wallet.dat file to a temporary location. The malware also searches for files linked to known cryptocurrency domains and duplicates them for future exfiltration. Additionally, it creates a hash list to represent the data it plans to extract.
FTP & VPN Credentials
Gremlin Stealer is also designed to extract login credentials from FTP services, targeting usernames and passwords stored by applications like TotalCommander. In addition, it collects account details and configuration files from widely used VPN clients, expanding its reach into more secure areas of user data.
Telegram and Discord Sessions
Gremlin Stealer also focuses on capturing session data from messaging platforms like Telegram and Discord, allowing it to extract sensitive information and upload it to a server controlled by the attacker.
System Information
Gremlin Stealer gathers system details such as the PC username, clipboard contents, processor info, and hardware ID, and compiles this data into a text file for later exfiltration.
Credit Card Information Stealing
Gremlin Stealer is also capable of stealing credit card information from infected systems and sending the collected data directly to its server.
Uploading Stolen Data to Gremlin Stealer’s Server
Gremlin Stealer creates a dedicated folder under the LOCAL_APP_DATA directory where it stores various types of stolen information in plain text files. This includes saved passwords, cookies, autofill data, screenshots, system details, Discord and Telegram sessions, FTP and VPN credentials, and cryptocurrency wallet data. All this information is bundled into a ZIP archive, which is then sent to the attacker’s server via a Telegram bot using a hard-coded API key. The transfer occurs through an HTTP POST request, delivering the full archive of stolen data from the victim’s Windows device.
Published Stolen Data from Gremlin Stealer’s Victims
The group behind Gremlin Stealer asserts that they have uploaded significant amounts of stolen data from victims to a server. This server is likely a configurable portal provided with the malware for easy access and management of the stolen information.

The Gremlin Stealer website currently hosts 14 ZIP archives containing stolen data from its victims, with options for users to either delete or download the files. Based on timestamps, the malware has been active since March 2025.
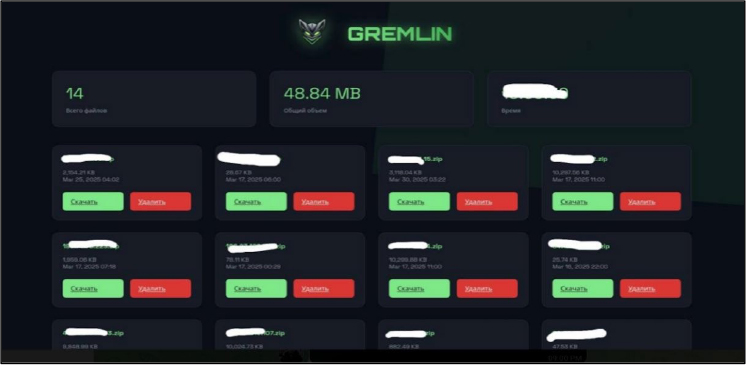
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as threats like Gremlin Stealer become more accessible and easier to deploy, the malware is poised to expand its reach, targeting a broader global audience and a more diverse range of victims. Its user-friendly design may attract even less-skilled attackers, enabling them to steal personal data, commit fraud, or misuse digital identities with minimal effort. With its built-in system for storing and organizing stolen data, there’s potential for the rise of underground marketplaces where such information is sold and recycled for future attacks. As its operators continue to refine and promote the malware, we could see it integrated into larger cybercriminal ecosystems or offered as part of malware-as-a-service packages. In the long run, this shift toward easier, automated tools may make large-scale data theft more routine and coordinated—posing lasting risks to digital trust and global online safety.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Pahalgam Attack Unveiled: APT36’s Strategic Use of Decoys to Target Indian Government
Summary:
A recent cyber-espionage campaign has been uncovered leveraging the theme of the April 22, 2025, Pahalgam terror attack to target Indian government and defense personnel. The operation combines credential phishing and malware deployment through malicious documents and deceptive domains mimicking official Indian entities. The attack centers around phishing PDFs, including filenames like “Action Points & Response by Govt Regarding Pahalgam Terror Attack.pdf,” which contain masked content and embedded URLs leading to spoofed login pages. These URLs, such as jkpolice[.]gov[.]in[.]kashmirattack[.]exposed, closely resemble legitimate Indian government domains to harvest credentials of officials using @gov.in or @nic.in email addresses.
The PDF documents were created shortly after the real-world incident, demonstrating the attacker’s rapid response to exploit sensitive geopolitical events. An additional PowerPoint macro-enabled add-on file (.ppam) with a matching lure name has also been identified. This file contains embedded executables that determine the target’s Windows version and install a variant of the Crimson RAT while opening a decoy document to avoid suspicion. The payload, disguised as a .jpg file, is dropped under a dynamically named directory and communicates with a command-and-control server at 93[.]127[.]133[.]58.
The Crimson RAT used in the attack supports over 20 commands for surveillance and data exfiltration, including taking screenshots, listing directories, downloading or deleting files, and maintaining persistence. All compiled payloads bear timestamps from April 21, 2025, indicating premeditated deployment before the terror event. The fake domains used in this campaign were registered within days of the incident, hosted on infrastructure linked to various ASNs known for cyber operations.
The adversary has impersonated numerous Indian defense and government organizations, creating domains such as iaf[.]nic[.]in[.]ministryofdefenceindia[.]org and email[.]gov[.]in[.]departmentofdefenceindia[.]link. These actions form part of a broader pattern of disinformation and espionage aimed at exploiting politically sensitive themes like Kashmir. This campaign presents significant risks, including compromised government systems, unauthorized data access, and disruption of sensitive operations. Technical defenses must focus on macro restriction, phishing detection, anomaly monitoring, and threat intelligence integration to counter such persistent threats.
Relevancy & Insights:
Transparent Tribe (APT36), a Pakistan-linked APT group, has once again demonstrated its consistent operational behavior through a recent campaign exploiting the “Pahalgam Terror Attack” theme. This campaign reflects the group’s strategic focus on Indian government and defense personnel by capitalizing on current, sensitive geopolitical developments. By crafting phishing documents embedded with malicious links and deploying Crimson RAT via macro-enabled PPAM files, the group continues to follow a well-established modus operandi. Fake domains mimicking official Indian entities such as Jammu & Kashmir Police and the Indian Air Force are being used to steal credentials and enable further infiltration— showcasing their blend of social engineering and technical deception.
Historically, APT36 has employed similar techniques. They have used PPAM (PowerPoint add-in) files embedded with OLE objects to deliver malware for years. Additionally, spoofed domains mimicking Indian defense infrastructure and exploiting emotionally or politically charged topics—such as the Kashmir conflict and military movements—have been a recurring strategy. This consistency in their TTPs (tactics, techniques, and procedures) highlights their long-term operational patterns and underlines the relevance of the current incident within their broader threat landscape.
ETLM Assessment:
Transparent Tribe (APT36), a Pakistan-linked threat actor, has launched a campaign targeting the Indian government and defense personnel using phishing documents themed around the April 2025 Pahalgam terror attack. These documents are designed to lure victims into clicking on malicious links embedded in PDFs and PowerPoint files, which then lead to fake login portals mimicking legitimate government domains. The campaign uses credential phishing and macro-enabled files to deploy Crimson RAT, a malware previously associated with APT36. The group targets Indian military, defense, government, and research sectors, with operations geographically focused on India. They exploit human vulnerabilities through social engineering rather than specific software flaws. The Crimson RAT used in this campaign allows full remote access, data exfiltration, and system control. The documents and malicious infrastructure are themed around ongoing sensitive topics, particularly related to Kashmir, to maximize psychological impact. APT36 has consistently used domain impersonation and weaponized documents to support cyber espionage and intelligence collection. This campaign is consistent with their established tactics, techniques, and procedures (TTPs), indicating continuity in objectives and operational style.
Strategic Recommendations:
Tactical Recommendations
Operational Recommendations
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1203 | Exploitation for Client Execution |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1113 | Screen Capture |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
Many Fortune 500 companies have hired North Korean operatives
According to a recent report on North Korea’s efforts to obtain remote IT positions at foreign companies, these fraudulent workers are now using AI tools to cheat on coding tests and technical interviews. The threat actors are also using deepfake technology to bypass ID checks. The primary goal of these workers is to earn a paycheck for Pyongyang, though they also occasionally use their access to conduct espionage or launch financially motivated attacks. While many initially thought the issue was confined to the crypto industry or even tech firms, multiple experts said it has grown far beyond that. There are now hundreds of Fortune 500 organizations that have hired these North Korean IT workers. Most of them have at least dozens, if not hundreds, of applications from North Korean IT workers.
In many cases, the workers managed to evade detection by using a mix of artificial intelligence and quick thinking—rapidly answering questions and relying on ChatGPT for translations. After securing the job, they would claim a family emergency requires their work laptop to be shipped to a different address than the one provided on their application.
These laptops are then sent to U.S.-based “laptop farms,” where Americans— sometimes knowingly, sometimes not—are paid modest fees to host the devices, install remote access software, and ensure they remain powered on. Many of the individuals operating these laptop farms are unaware they’re assisting North Koreans, often believing they are supporting Chinese business operations.
ETLM Assessment:
North Korean cyber operations are increasingly sophisticated. DPRK’s state hackers both collect intelligence and generate revenue for the state and for themselves.
These efforts appear to be financially motivated not only by hackers themselves but by the state, which treats these fraudulent job applications as a major source of hard currency revenue.
Trump administration to ‘change the script’ on offensive operations
A senior White House official said that the Trump administration aims to “destigmatize and normalize” the use of offensive cyber capabilities as a legitimate tool of national power. “It’s not offense for offense’s sake,” said Alexei Bulazel, senior director for cyber on the National Security Council, during a keynote at the RSA Conference. “It’s about being able to respond in kind if we’re targeted by foreign aggression, or to support conventional military operations with cyber offense.”
His remarks offer some of the clearest insight yet into how the Trump administration plans to approach offensive cyber operations—an increasingly central piece of U.S. national security strategy. Following the 2024 election, Trump’s incoming team emphasized a shift toward a more aggressive cyber posture, especially in the wake of Chinese hacking campaigns that infiltrated U.S. telecom companies and positioned China to potentially disrupt critical infrastructure. Officials argued the U.S. must impose greater costs and consequences on adversaries.
ETLM Assessment:
So far, Trump administration’s policy specifics have been scarce. Much of the attention has instead focused on internal changes, including efforts to downsize the Cybersecurity and Infrastructure Security Agency (CISA) and the recent firings of Gen. Timothy Haugh, who led U.S. Cyber Command and the NSA, along with one of his top deputies.
But now top NSC officials openly state that: “There’s a lot we could do to impose costs,” and “I think previous administrations have been reluctant to go there. This is our opportunity to rewrite the script, to update the offensive cyber playbook. … You have people who’ve been handcuffed for years …It’s time to unleash that talent.”
This could mean the following weeks and months might see the similar level of cyber action states like China and Russia typically employ, coming from the United States.
Canadian power company hit by a cyberattack
Halifax-based electric utility Nova Scotia Power and its parent company Emera have shut down parts of their IT networks while responding to a cyberattack. The attack disrupted the utility’s customer care phone line and online portal, but did not affect physical operations, according to a company statement.
ETLM Assessment:
While the attack in Canada has not caused damage to the grid itself and the electricity generation and distribution operations, the recent blackout in Spain has been the worst in recent decades in all of Europe. As of writing, a cyberattack seems unlikely as the ultimate cause of the blackout, however, the case highlights the increasing vulnerability of interdependent grid operations in the 21st century, while hostile actors like China and Russia are making inroads to critical infrastructure virtually everywhere.
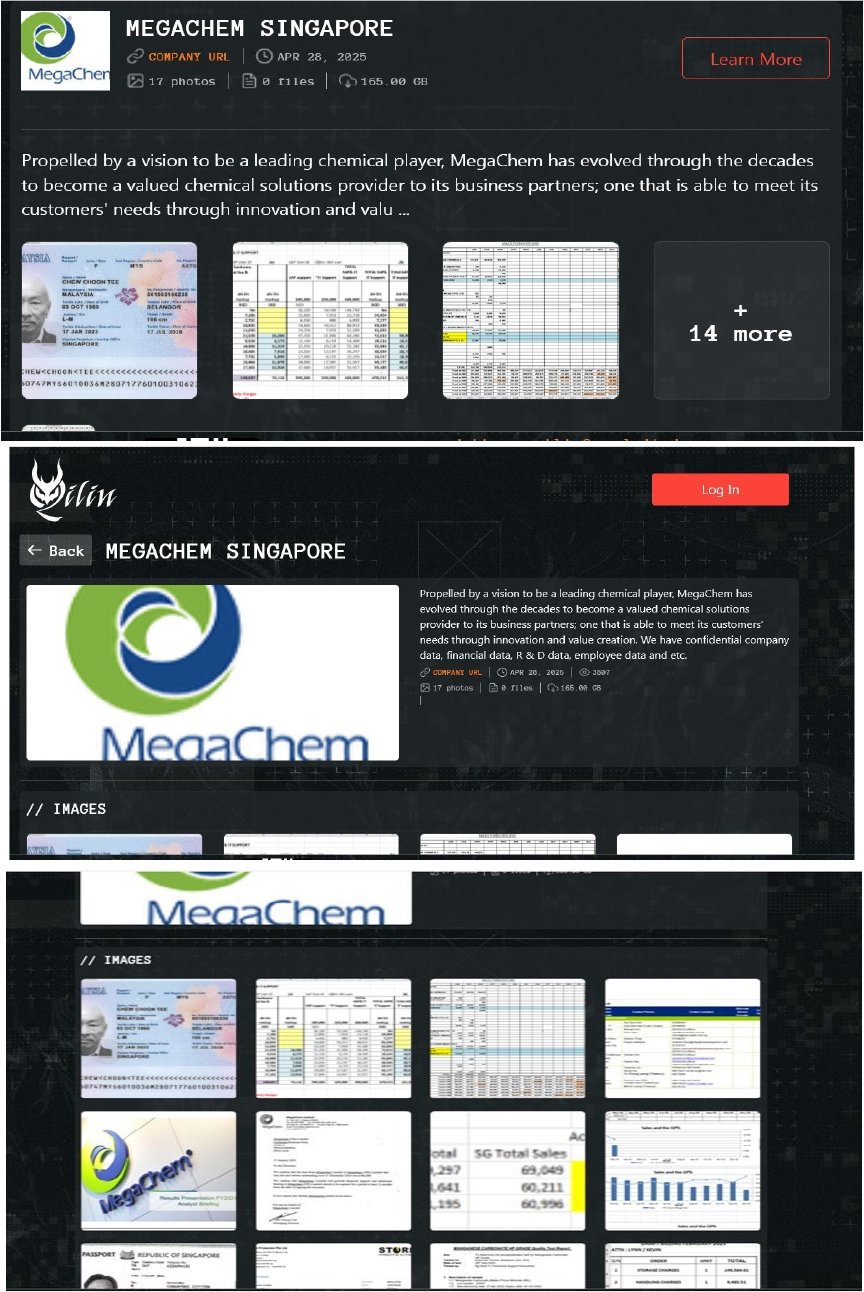
The Qilin Ransomware Impacts Megachem Singapore
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; Megachem Singapore
(https[:]//www[.]megachem[.]com[.]sg/), was compromised by Qilin Ransomware. MegaChem Singapore Limited is a well-established, Singapore-based specialty chemical solutions provider with a comprehensive service offering that includes contract manufacturing and global chemical distribution. The compromised data contains confidential company data, financial data, R&D data, employee data, etc. The total size of the compromised data is approximately 165 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
The Lynx Ransomware Impacts Runtec Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Runtec Co., Ltd (https[:]//www[.]runtec[.]co[.]jp/), was compromised by Lynx Ransomware. Runtec Co., Ltd. is a Japanese logistics provider, specializing in temperature-controlled transportation and storage of food products. It ensures fast, reliable delivery across Japan while actively adopting eco-friendly technologies and digital innovations to improve the efficiency and safety of its operations. The compromised data consists of confidential and sensitive information related to the organization. The total size of the compromised data is approximately 500 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
Vulnerability in External Image Replace Plugin for WordPress
Relevancy & Insights:
The vulnerability exists due to insufficient validation of the file during file upload in the “external_image_replace_get_posts::replace_post” function.
Impact:
A remote user can upload a malicious file and execute it on the server.
Affected Products:
https[:]//www[.]wordfence[.]com/threat- intel/vulnerabilities/id/ee1624fd-d98b-4953-99dc-a952dda48aa1?source=cve
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
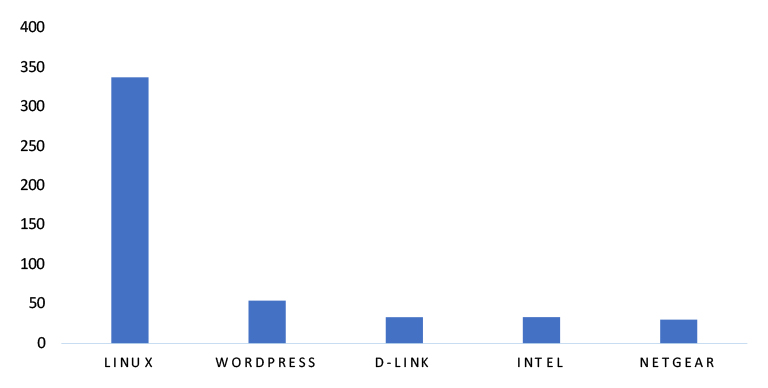
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in the External Image Replace plugin for WordPress can pose significant threats to user privacy and security. This can impact various industries globally, including media, publishing, education, and beyond. Ensuring the security of the External Image Replace plugin is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding image processing workflows, preventing unauthorized file manipulations, and ensuring secure content delivery across different geographic regions and sectors.
NightSpire Ransomware attacked and published the data of PT Pupuk Indonesia
Summary:
Recently, we observed that NightSpire Ransomware attacked and published the data of PT Pupuk Indonesia(https[:]//www[.]pupuk-indonesia[.]com/) on its dark web website. PT Pupuk Indonesia is one of Asia’s largest fertilizer producers, operating as a state-owned holding company that oversees a diverse group of subsidiaries in fertilizer and pesticide production, chemical manufacturing, industrial support, logistics, and trading. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The total size of the compromised data is approximately 200 GB.
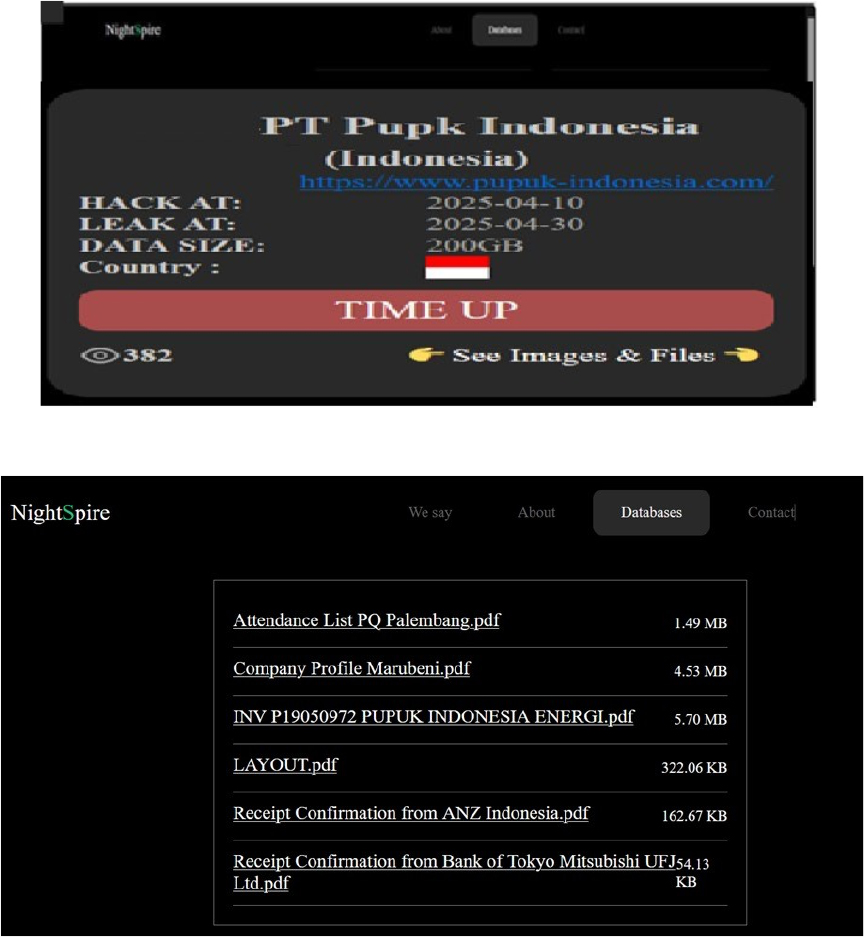
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
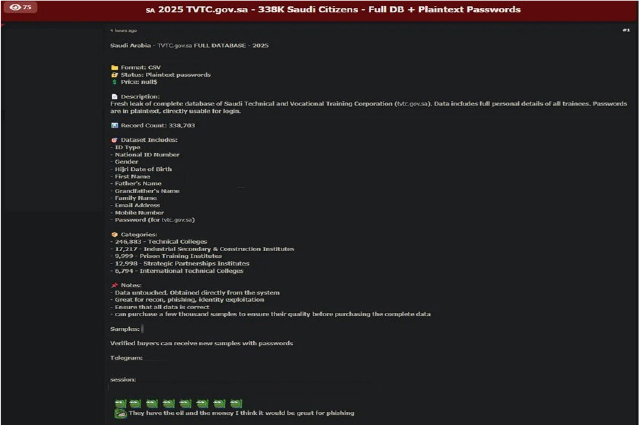
Technical and Vocational Training Corporation, Saudi Arabia Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor operating under the alias NO8LO has allegedly listed a database for sale on Dark Forums containing personal data of over 338,000 Saudi citizens affiliated with the Technical and Vocational Training Corporation (TVTC, tvtc[.]gov[.]sa). The leaked data is reportedly in CSV format and includes plaintext passwords, national ID numbers, contact information, and detailed personal identifiers.
The actor claims the data was obtained directly from TVTC systems and is untouched. It is being marketed for phishing, identity exploitation, and reconnaissance purposes. Multiple institutional categories are affected, including technical colleges, industrial institutes, and prison training centers.
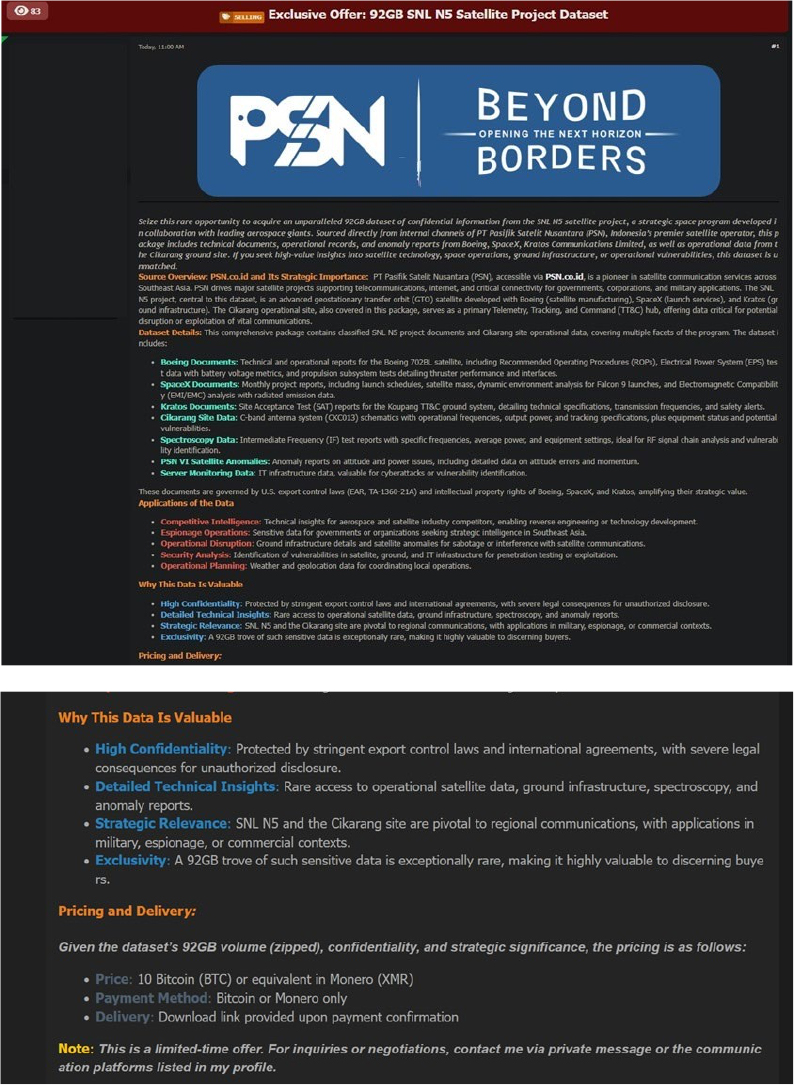
PT Pasifik Satelit Nusantara (PSN) Indonesia’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to PT Pasifik Satelit Nusantara (PSN) (https[:]//www[.]psn[.]co[.]id/) in an underground forum. PT Pasifik Satelit Nusantara (PSN is a pioneer in satellite communication services across Southeast Asia. PSN drives major satellite projects supporting telecommunications, internet, and critical connectivity for governments, corporations, and military applications. The data sale has been traced back to a threat actor known as “Sentap.”
Dataset Details:
This comprehensive package contains classified SNL N5 project documents and Cikarang site operational data, covering multiple facets of the program. The dataset includes:
These documents are governed by U.S. export control laws (EAR, TA-1360-21A) and the intellectual property rights of Boeing, SpaceX, and Kratos, amplifying their strategic value.
Pricing and Delivery:
Given the dataset’s 92GB volume (zipped), confidentiality, and strategic significance, the pricing is as follows:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “Sentap” has been implicated in several data breaches, with credible reports indicating involvement in unauthorized access and the attempted sale of stolen data on dark web forums. The emergence and activity of “Sentap” highlight the ongoing and evolving risks posed by cyber threats originating from the dark web. In light of these developments, it is imperative for organizations to maintain a robust cybersecurity posture, including continuous monitoring, threat intelligence integration, and proactive defense strategies to safeguard critical data assets.
Recommendations: Enhance the cybersecurity posture by:
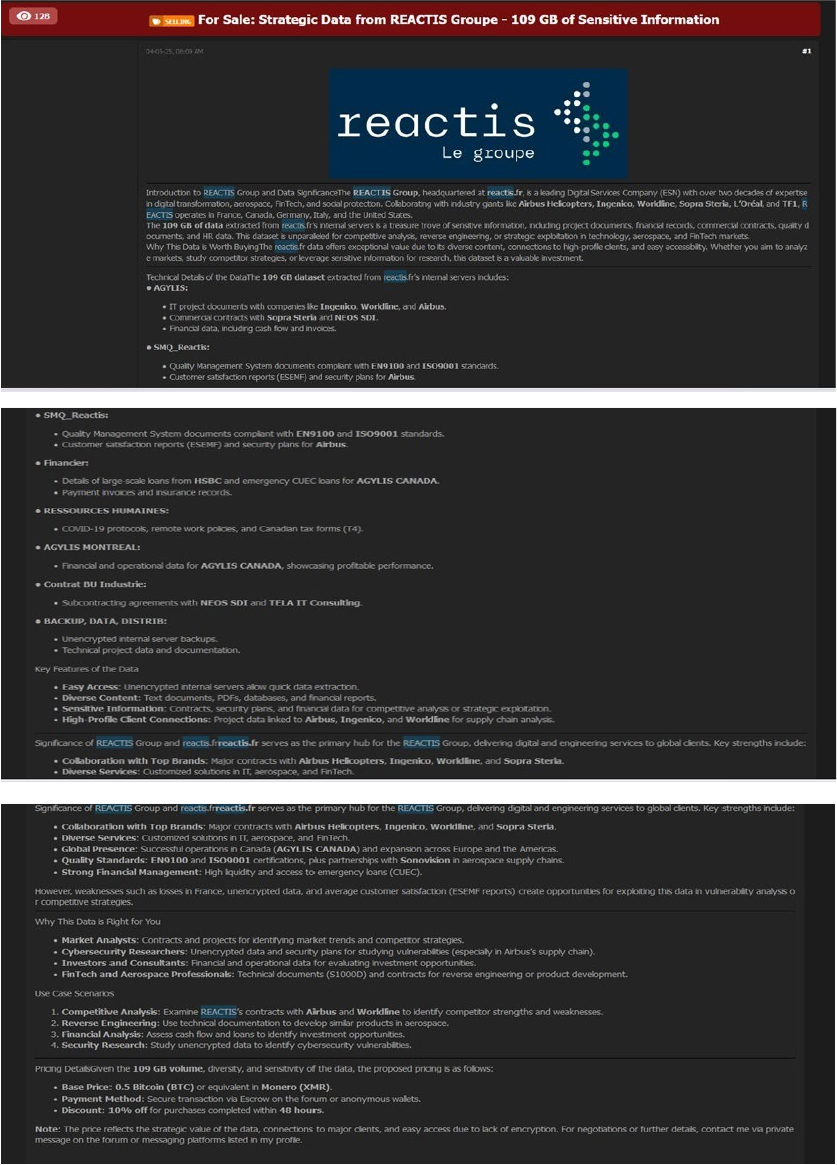
The CYFIRMA Research team observed a data leak related to REACTIS Group(https[:]//www[.]reactis[.]fr/) in an underground forum. The REACTIS Group is a leading Digital Services Company (ESN) with over two decades of expertise in digital transformation, aerospace, FinTech, and social protection. Collaborating with industry giants like Airbus Helicopters, Ingenico, Worldline, Sopra Steria, L’Oréal, and TF1. REACTIS operates in France, Canada, Germany, Italy, and the United States.
The 109 GB of data extracted from Reactis[.]fr’s internal servers is a treasure trove of sensitive information, including project documents, financial records, commercial contracts, quality documents, and HR data. This dataset is unparalleled for competitive analysis, reverse engineering, or strategic exploitation in technology, aerospace, and FinTech markets. The data sale has been traced back to a threat actor known as “Sentap.”
Technical Details of the Data: 109 GB dataset extracted from Reactis [.]fr’s internal servers includes:
AGYLIS:
SMQ_Reactis:
Financier:
RESSOURCES HUMAINES:
AGYLIS MONTREAL:
Contrat BU Industrie:
BACKUP, DATA, DISTRIB:
Pricing Details: Given the 109 GB volume, diversity, and sensitivity of the data, the proposed pricing is as follows:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
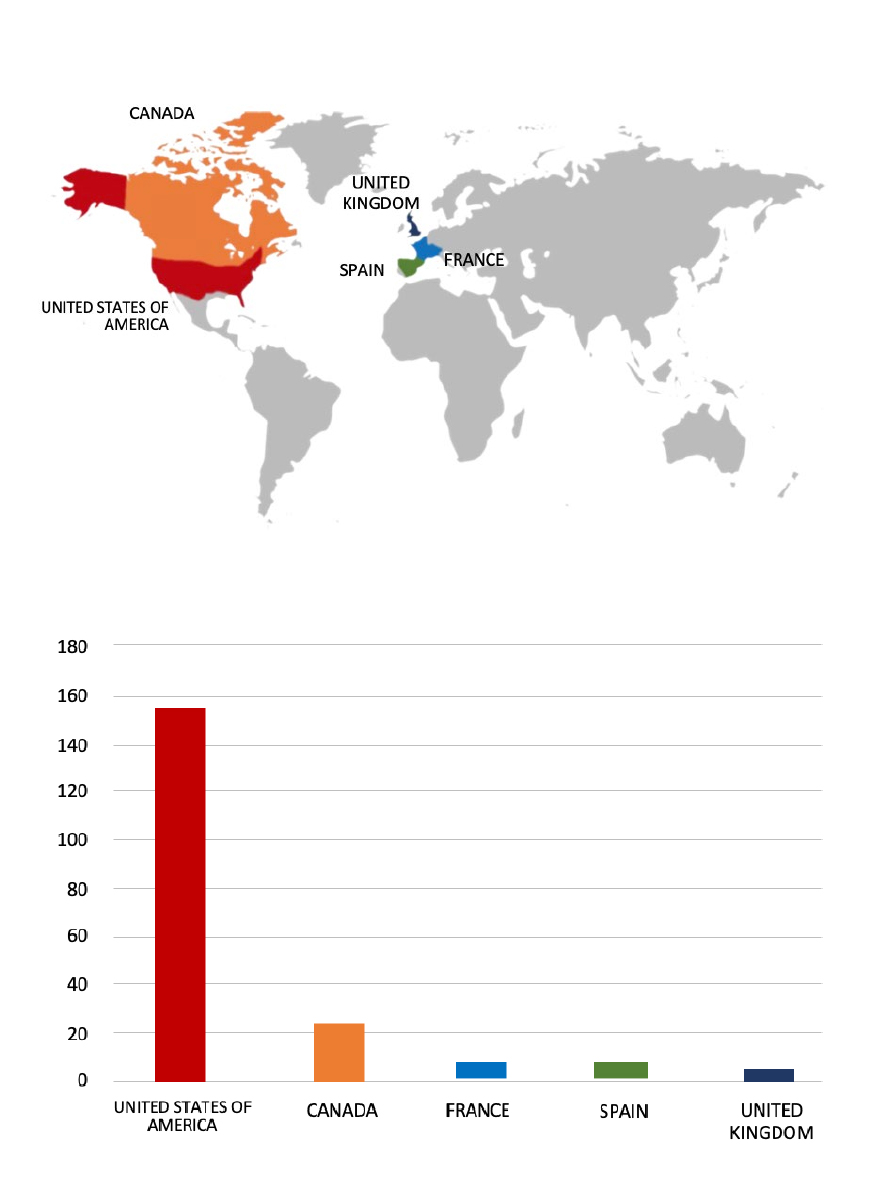
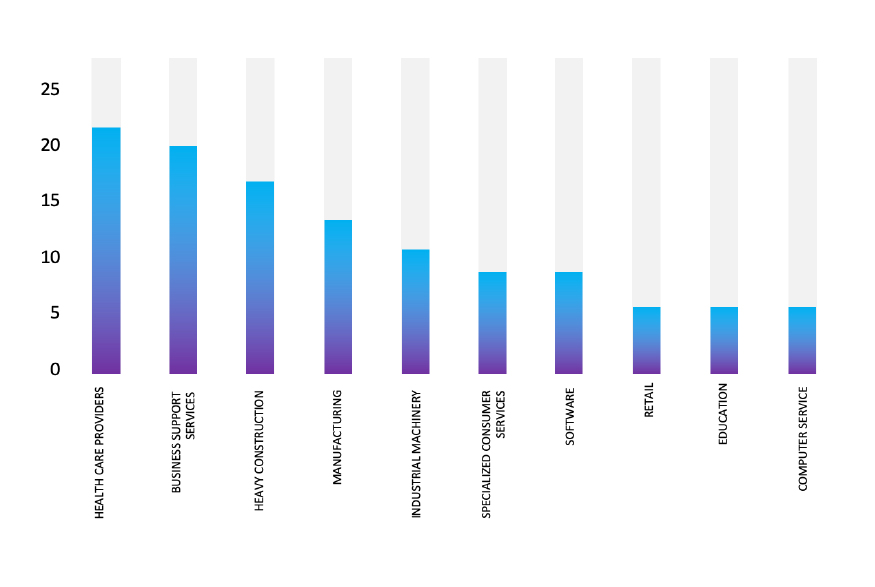
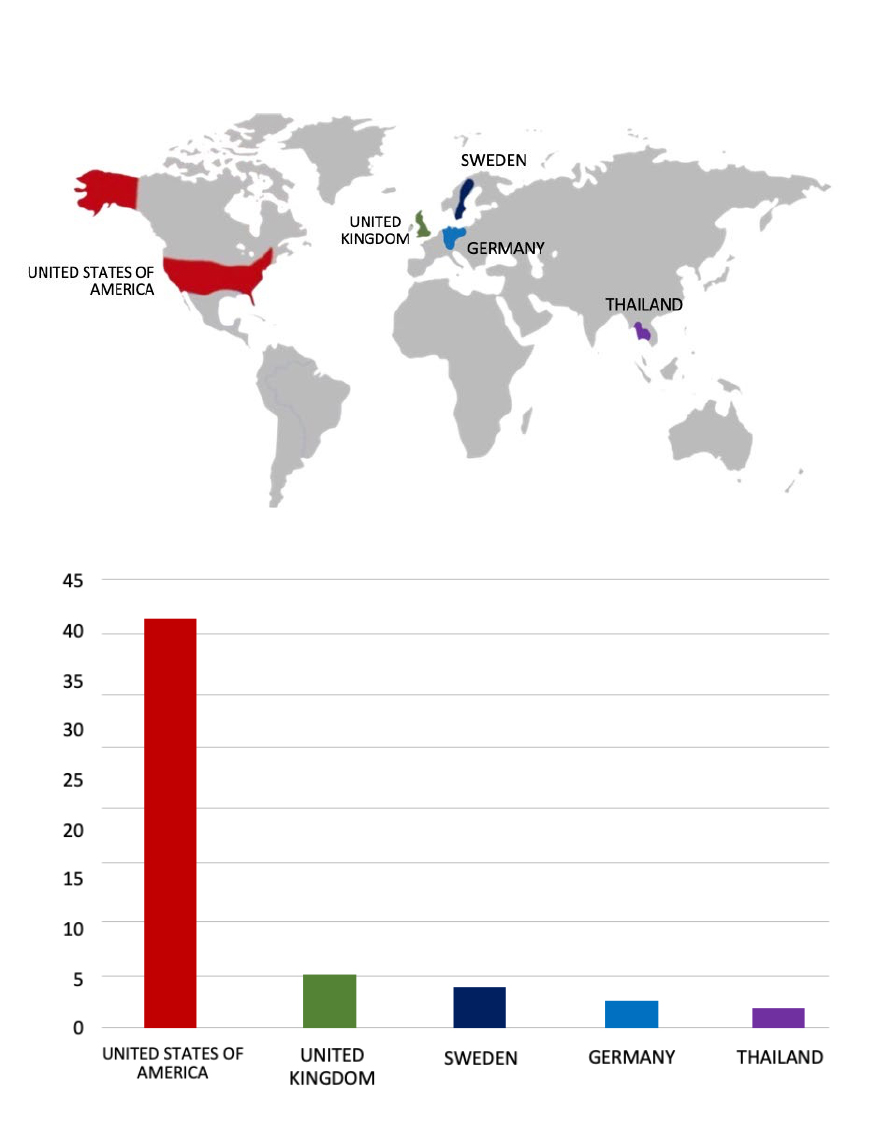
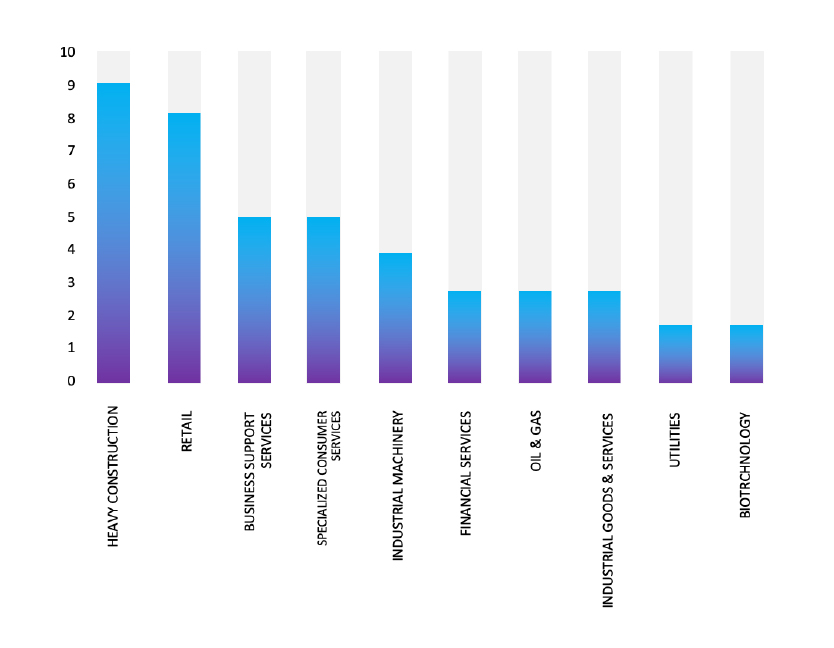
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
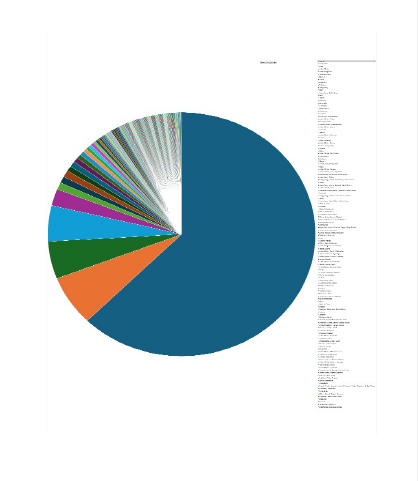
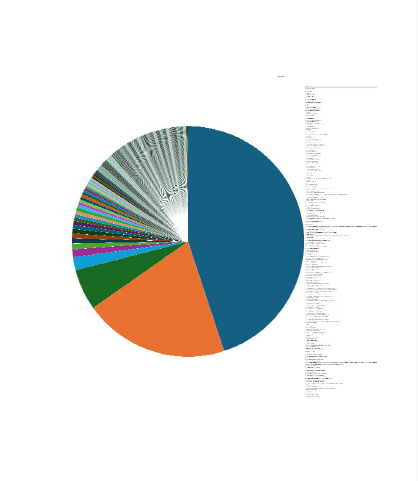
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.